Two databases containing user information and messages ostensibly from the secret sharing app Whisper were exposed on the web without a password or any other authentication required to access them, according to Comparitech researchers.
One of the databases appears similar to a Whisper database leaked in March 2020, which contained user’s messages and locations. The second database is a list of user account information. Although none of the exposed information can be used to directly identify people, it does include age, location and other details that could be used to unmask users.
Comparitech’s head of security research Bob Diachenko discovered the data sitting unprotected on December 22, 2021. He immediately sent an alert to Whisper, and the data was secured about three days later.
Whisper did not acknowledge the incident as of time of publication and Comparitech was unable to reach the company for comment after multiple attempts. We therefore can’t be certain that Whisper is responsible for the exposure.
Diachenko identified more than 50 IP addresses pointing to the exposed Elasticsearch database. This observation led him to conclude that the data was most likely part of Whisper’s native infrastructure and was not exposed by a malicious third party.
Timeline of the exposure
The data was exposed for at least three days before being secured. Here’s what we know happened:
- December 22, 2021 – The databases were indexed by search engines.
- December 22, 2021 – Diachenko discovered the database and immediately sent an alert to Whisper as per our responsible disclosure policy.
- December 25, 2021 – The databases were no longer publicly accessible.
- Januray 21, 2022 – Comparitech contacted Whisper via email for acknowledgment of Diachenko’s disclosure and fact checking. We never received a response. Follow ups via social media likewise never got a reply.
We do not know if any unauthorized parties accessed the data while it was exposed, but our honeypot experiments show it normally takes just a few hours for attackers to find and steal unprotected data.
What data was exposed?
Each of the 50+ IP addresses pointed to two Elasticsearch clusters:
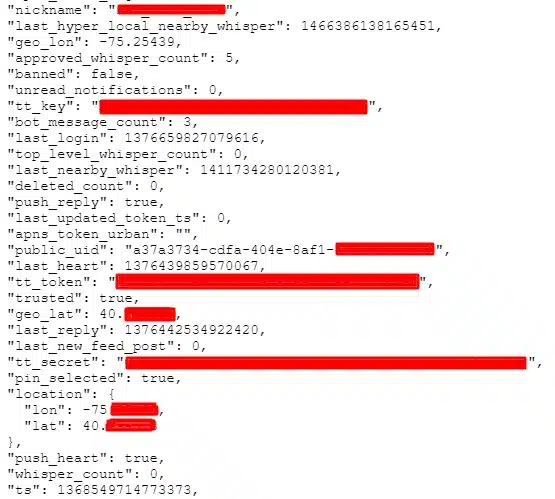
The “users” cluster contained 361 million records. Each record contained some or all of the following info:
- Username and nickname
- User ID numbers
- Several shared secrets, secret keys, and tokens
- User’s geolocation
- Engagement statistics such as number of posts, likes, and timestamps of the user’s most recent interactions
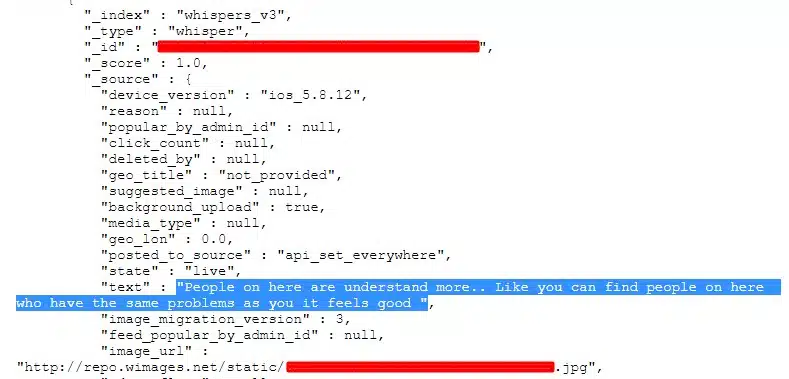
The “whispers_v3” database contained 1.2 billion records, each with some or all of the following info:
- Message contents
- Message timestamps
- Username
- Geolocation
- URLs of attached images
Timestamps on a sample of data collected by Comparitech were dated between 2013 and 2016.
Dangers of exposed data
Whisper is an anonymous secret sharing app where users can share intimate messages and posts. Given that anonymity is the app’s main selling point, users have an expectation of privacy.
The data, if genuine, exposes Whisper user’s supposedly secret messages along with their geolocation and other information. Although no names, email addresses, or other directly identifying information was exposed, a determined attacker could potentially use the available data to find and identify users. That could lead to blackmail, stalking, harassment, or other crimes.
About Whisper
Whisper launched in 2012 on Android and iOS. The free app allows users to “anonymously” post and share messages and videos. It reached 10 million monthly active users in April 2015. The company is currently owned by MediaLab, which also owns Kik messenger and the Imgur image sharing site.
The company drew heavy criticism in 2014 when the Guardian reported that the company gathered location data on its users, including some who had opted out.
In 2017, Whisper laid off 20 percent of its staff, lost its entire board of directors, and saw its COO leave.
In March 2020, the Washington Post reported that Whisper exposed its message database on the web, revealing 900 million user records from the app’s release in 2012 to then-present day.
Why we reported this incident
Our cybersecurity research team routinely scans the internet for unprotected databases that contain personally identifiable user information. When we discover such a database, we immediately launch an investigation to find out to whom the data belongs, who might be affected, and the possible consequences for end users.
After determining who is responsible for the data, we send an alert as per our responsible disclosure policy so that the database can be secured as soon as possible. In this case, the data was secured but our disclosure was not acknowledged. Once the data has been secured, we publish a report like this one to raise awareness about cybersecurity and curb harm to end users.
Other data incident reports
Comparitech has published several data incident reports like this one:
- Sex cam site Stripchat exposes user, model info on the web
- Personal info of 106 million international visitors to Thailand exposed online
- 35 million US residents’ personal details exposed on the web
- India visa agency exposes 6,500 traveler’s visa applications on the web
- Prison phone service Telmate exposes messages, personal info of millions of inmates
- Social media data broker exposes nearly 235 million scraped profiles
- 42 million Iranian “Telegram” phone numbers and user IDs were breached
- Details of nearly 8 million UK online purchases leaked
- 250 million Microsoft customer support records were exposed online
- More than 260 million Facebook credentials were posted to a hacker forum
- Almost 3 billion email address leaked, many with corresponding passwords
- Detailed information on 188 million people was held in an unsecured database