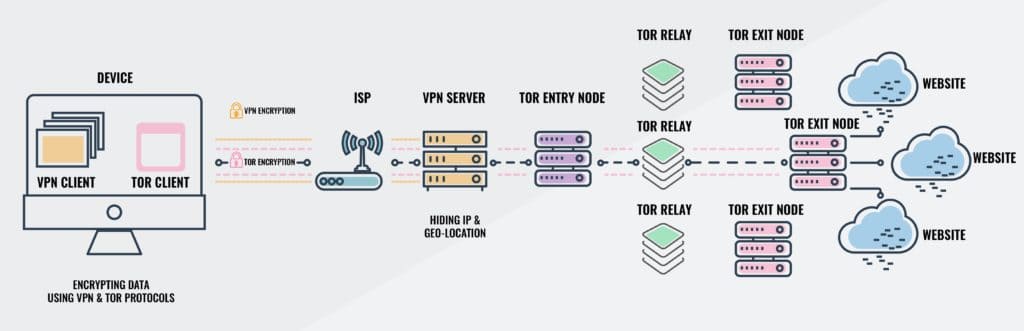
If you’re looking to enhance your online privacy while browsing the dark web, you might want to use a Virtual Private Network (VPN). This setup is called Tor over VPN or Onion over VPN, and it provides an extra layer of security since it hides your real IP address from whoever owns the entry node you’re using.
So how do you set up Tor with a VPN? Easy. Just connect to a VPN first, and then open Tor Browser or your preferred Tor application. Now, there are a couple of issues to be aware of, but we’ll cover these in more detail below.
Quick guide to using Tor with a VPN
For maximum security, it’s important to choose a VPN service with a strict no-logs policy and uncrackable 256-bit AES encryption. NordVPN is our top choice. It provides an extra layer of protection against browser fingerprinting and other cyber threats, plus it has servers specially-configured for Tor (more on these later).
WANT TO TRY THE TOP VPN RISK FREE?
NordVPN is offering a fully-featured risk-free 30-day trial if you sign up at this page. You can use the VPN rated #1 for Tor with no restrictions for a month—that's plenty of time to try browsing the darknet and see if this service is right for you.
There are no hidden terms—just contact support within 30 days if you decide NordVPN isn't right for you and you'll get a full refund. Start your NordVPN trial here.
If you’re inexperienced with Tor, I recommend getting started with Tor Browser. It’s a free Firefox-based web browser that routes all incoming and outgoing traffic through the Tor network without much additional configuration necessary to start browsing.
Here’s how to use a VPN with Tor:
- Download a suitable VPN, making sure to select the correct version for your device, and launch the VPN client.
- Open the VPN app and connect to any server. If there are clearly-labeled Tor over VPN servers, pick one of these. Otherwise, I suggest choosing a server close to your real location as these tend to be the quickest. This is important because Tor is notorious for slow speeds and we want to avoid reducing this even further.
- Once your VPN is connected, launch the Tor Browser.
- That’s it! You’re now protected by both the VPN and Tor browser. In other words, your online activity is shielded with several layers of encryption and can’t be seen by anyone, not even government agencies or malicious actors
How Tor with a VPN works
So what’s happening in the Tor-over-VPN setup, exactly? Here’s what the traffic flow looks like for outbound data:
- Data is encrypted by the VPN
- Data is encrypted again by Tor
- Data is sent to the VPN server
- The VPN decrypts the data, but it is still encrypted by Tor
- Data is sent through a series of nodes on the Tor network
- If visiting a .onion address on the dark web, data is decrypted upon arriving at its destination. If I visit the clear web, data is decrypted at a Tor exit node and forwarded to the website.
Inbound traffic flow is as follows:
- Data is sent from a website, app, or service
- Tor encrypts the data
- The data is sent through the Tor network to the VPN server
- The VPN encrypts the data again
- The twice-encrypted data is sent from the VPN server to the end user device
- Tor decrypts the data
- The VPN decrypts the data again
Why use a VPN with Tor?
Using Tor with a VPN (onion over VPN) offers several benefits over using either of the two tools alone:
- My ISP can’t see that I’m using Tor
- My VPN provider cannot see what sites I visit or the contents of my connection
- I can access both dark web .onion sites and clear web sites
- I can anonymously surf the clear web
- Tor entry nodes cannot see my real IP address
- I have the option to use the VPN by itself with a normal browser for non-sensitive tasks
But, there are also some drawbacks:
- Websites and apps can see that I’m visiting through a Tor exit node. Some sites might block me or not function well as a result.
- My VPN can see my real IP address and knows I’m using Tor
- I could potentially expose data to compromised Tor exit nodes
- Using a VPN and Tor together will significantly slow down my connection
Note that just because a website or my ISP can see I’m using Tor, it doesn’t mean they can see what I’m actually doing. All my data is encrypted and its destination hidden.
What about VPN over onion?
If we switch up the order in which data is encrypted and transmitted, we get VPN over onion. In this setup, traffic first passes through Tor and then through the VPN, instead of the other way around.
VPN over onion is generally considered less secure and is more difficult to set up, usually requiring assistance from the VPN provider.
But VPN over onion does have its advantages:
- My ISP can’t see that I’m using a VPN
- Clear web sites and apps that normally block Tor traffic will be accessible
- My data is less vulnerable to compromised Tor exit nodes and packet discrimination
But on the downside:
- My ISP can see that I’m using Tor
- I can’t visit dark web sites
- My VPN can see my internet traffic
- Tor entry nodes can see my real IP address
Unlike Tor over VPN, I can’t just set up VPN over Tor without help from my VPN provider. VPN over Tor must be configured on the server so that once data reaches the server, it is then channeled through the Tor network. The vast majority of VPNs do not offer this feature.
VPNs with built-in Tor connectivity
A handful of VPNs offer servers speciall designed for Tor traffic. These used to allow you to access dark web sites without the Tor Browser but popular browsers like Firefox and Chrome have since disabled the ability to open .onion links. Still, if you’re looking for a quick way to find the fastest server for Tor, this makes it nice and easy.
NordVPN is a top-rated VPN provider that offers this feature. It follows a strict no-logs policy, something that has been verified by multiple independent audits. Additionally, it has its own security-focused NordLynx protocol designed to address some of the privacy flaws in the base WireGuard protocol.
Tor over VPN: Frequently Asked Questions
Can I get into trouble for visiting dark web sites?
There’s nothing inherently illegal about the dark web in most countries; it’s just a collection of sites that aren’t indexed by regular search engines. That said, .onion sites have a reputation for being associated with illegal activity so even installing the Tor Browser could raise some eyebrows.
To keep yourself as safe as possible, it’s best to only use reputable darknet sites, and avoid opening links if they’re not provided by a service you trust.
Disclaimer: Although we’ve spent hours researching this topic, we are not legal experts. As such, nothing we’ve said above should be taken as legal advice. We encourage you to consult local laws or perhaps even seek a professional’s opinion before attempting to use the dark web if you’re unsure doing so is legal.
Why isn't my .onion link working?
There are multiple reasons you might have trouble accessing a particular .onion site. Here are just a few of the most common:
- You’re not using the Tor Browser
- The site you’re trying to access is no longer active
- You’re trying to visit a site with a short v2 address. Only sites with 56-character v3 addresses still work
- The network you’re using blocks Tor traffic
- Your system’s date, time, or timezone is incorrect
- Your antivirus or firewall is preventing the Tor Browser from working properly
Does Tor make me completely anonymous online?
Tor passes your data through several encrypted nodes, ensuring that only the last one in the chain can see which site you’re accessing. The problem with this is that one organization can set up multiple malicious exit nodes and harvest a great deal of information, redirect users, or steal information.
Using a VPN with Tor helps prevent this by ensuring your data is encrypted before it even hits the Tor network. Your speeds will be reduced even further than normal, but that’s a small price to pay to prevent your cryptocurrency or accounts from being stolen.