Operational Technology (OT) is a branch of cybersecurity that focuses on securing systems and devices that are networked with physical machines. The need for OT Security increases as organizations leverage more IoT-based devices and rely on technology such as Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) to enhance their business.
When many people hear about the Internet of Things, they may think about their smart speakers or internet-connected light bulbs. OT Security is responsible for much more sensitive devices such as fuel pumps, electrical control switches, sewage treatment plants, and even the electrical grid. A failure or cyber-attack on these systems could cause widespread effects on everyone who relies on these services, and even a loss of life in the worst possible situations.
Here’s our shortlist of the seven best OT Security vendors:
- Forcepoint EDITOR’S CHOICE – A cloud-based system that plans and then implements a secure overlay network, integrating underlying infrastructure into a universal addressing, security management, and monitoring system.
- SCADAfence – Uses non-intrusive deployments requiring zero downtime.
- Nozomi Networks Guardian Sensors – Discovers and monitors industrial control systems, operation technology, and IoT devices.
- SigaGuard – Monitors electrical signals rather than packets for wider monitoring abilities.
- Honeywell – Assigns risk scores for easy threat prioritization.
- Kaspersky Industrial CyberSecurity – Provides holistic monitoring and end-user education.
- Darktrace – Leverages artificial intelligence to secure any protocol or technology.
- Dragos – Can be used as a managed service and features 21+ partnerships.
With the stakes so high, OT Security vendors not only have to stop attacks but also have a set of automated procedures to isolate other systems and ensure any damage done can be quickly stopped and reversed.
How is OT Security Different From IT Security?
IT Security heavily focuses on securing information systems, databases, and user access through networks using internet protocol. Traditionally businesses have allowed information in and out of their network through the placement of firewalls that are sometimes paired with a proactive system such as a SIEM.
OT Security is primarily used to secure industrial systems and networks from cyberattacks or internal threats from rogue employees. This industrial IoT usually includes ICS and SCADA networks that may now have internet-facing access to remotely monitor or control physical systems on the plant floor. In the past industrial systems operated primarily on an intranet and did not have connectivity to the outside world.
While IT and OT security may seem similar, they are significantly different. One of the biggest differences is that OT Security covers networks and devices that used to be part of a closed system, and never accessible to the outside world. In IT Security a breach may result in the loss of information, whereas a breach of an industrial system may cause a pipe to burst, or a centrifuge to spin out of control.
As these physical devices become internet-accessible both IT and OT security need to be applied harmoniously in a way that secures the industrial network and ensures no unauthorized changes can be made either internally, or externally.
What Are Some Features Of OT Security?
OT Security has many layers, but most often starts with analyzing the industrial networks’ traffic. From a network perspective, these systems are isolated from everything else, lowering the total volume of network traffic that needs to be inspected and analyzed.
With less traffic, baselines can be created faster and monitors can be set to alert to suspicious activity or changes. Many OT Security vendors use a combination of behavioral analytics and baseline analysis to alert and sometimes even deploy automation to rectify an issue.
For example, these two technologies can detect if specific employees are accessing machines in a way they shouldn’t, or attempting to modify controls they are not authorized to change. If these actions are detected an alert can be sent immediately to a supervisor and their account can be temporarily locked until a more thorough look is taken into the situation.
Much of this automation and monitoring is designed to alert to an attack that may be in its early stages, giving you a chance to stop it before it is completely underway. In addition to this monitoring, many OT Security solutions come with tailored access control solutions that cater to ICS and SCADA systems.
These security features can monitor and directly communicate with industrial control systems allowing for in-depth access control, policy-based rulesets, and reports for auditing. Many of these OT Security vendors have scalable solutions that can secure a few dozen, to a few thousand sensors and industrial machines.
If you’re looking for OT Security vendors it’s important to look for solutions that can be implemented without causing downtime or risking non-compliance. Managing the jump from a closed industrial system to an internet connection one requires a vendor or tool that has the ability to provide IT and OT security convergence seamlessly.
The best OT Security vendors
Our methodology for selecting an operational technology security system
We reviewed the market for OT security tools and analyzed the options based on the following criteria:
- Interoperability with industrial systems
- Risk scoring for headless devices
- Zero trust access
- Traffic tagging
- Behavioral analysis for anomaly detection
- A free trial or a demo system to get a way to assess the package before paying
- Value for money from a reliable service at a fair price
Using this set of criteria, we looked for protection systems for industrial devices that quite often don’t have native security or user accounts.
Let’s now take a look at some of the best OT security vendors and see exactly how their solutions can help secure IoT and industrial systems.
1. Forcepoint
Forcepoint offers a suite of security services that encompass OT Security as well as user, data, and edge protection. Within this suite, Forcepoint offers specialized security for critical infrastructure and IoT environments.
Key Features:
- Seamless IT/OT integration
- Byte-level content inspection
- SIEM integration
Why do we recommend it?
Forcepoint is a network security package that can implement a range of strategies that include SASE and ZTA. What these acronyms mean is that you can control access to devices and applications through network device settings and you can also construct virtual secure networks across the internet, including industrial machinery.
The critical infrastructure service enables companies to enable OT security quickly whether the environment is already networked, or in a transitional stage. The service works to map out and create network boundaries and plan how cloud and remote access controls will work for your critical systems.
Through Forcepoint’s Data Guard, you can connect older devices and industrial machines to your private network to enable information sharing and the creation of insights that weren’t otherwise possible. Data Guard uses byte-level content inspection and data validation to ensure data is secure and untampered while in transit.
Data pulled from lower-level network devices can be aggregated into a single environment for security monitoring and management. If your organization already uses a SIEM platform, this data can be pulled quickly into the system for auditing and alert purposes. Forcepoint allows you to bring both IT and OT security together in a way that gives you a single pane of glass to view all of your physical and digital assets.
The methodology behind the technology involves creating layers of security and separating the IT network from operation controls without impacting productivity or limiting operators from doing their jobs.
Who is it recommended for?
This isn’t specifically an OT system, which means that you can construct shop floor security controls into your entire business system. Integrate multiple sites and cloud services into a single virtual network and gain central control over industrial systems remotely. The flexibility of this system makes it suitable for any business.
Pros:
- The interface is simple and easy to learn
- Utilizes a combination of fingerprinting and behavioral analysis to stop threats
- Can contain threats through a cloud-based sandbox environment
- Offers robust SIEM integrations
Cons:
- Must contact sales for pricing
Pricing for Forcepoint’s Infrastructure OT Security services is not available on its site. You can schedule a demo or request pricing on its website.
EDITOR'S CHOICE
Forcepoint is our top pick for an OT security vendor because it offers ways to plan and implement the implementation of hybrid networks that include traditional office systems with IoT and industrial devices. Create your network across sites through internet links but ignore the underlying medium and apply consistent security measures across environments. Wrap your entire business IT system with a defined boundary and patrol it with edge services. The package provides ongoing performance and security monitoring with alerts.
OS: Cloud-based
2. SCADAfence
SCADAfence focuses on providing cybersecurity for critical infrastructure by protecting both OT and IoT assets. Through continuous software-based monitoring, behavioral analytics, and threat detection, SCADAfence is able to provide full coverage of industrial networks while providing visibility into security events and infrastructure insights.
Key Features:
- Non-intrusive deployment
- Deep Packet Inspection
- Adaptive baseline analysis
Why do we recommend it?
SCADAfence specializes in OT and IoT device protection. The distance between these two types of equipment is becoming increasingly difficult to detect and so grouping security for them makes sense. This also means that you can get a common platform of security measures for your on-site cameras and your shop floor equipment.
Implementing OT security into a network with existing firewalls and security features can be challenging. SCADAfence acknowledges this problem by complimenting these security measures with internal visibility, monitoring, and alerting. During installation, SCADAfence uses port mirroring in networked switches to provide a non-intrusive deployment so there is no impact to productivity or downtime on any of the target machines.
With the scale in mind, the SCADAfence platform can provide coverage for even the largest and most complicated network architecture with deep packet inspection and filtering. Once packet inspection is in place, SCADAfence recognizes assets on the network and begins monitoring for anomalous behavior, areas of non-compliance, and potential threats in progress.
All assets on the network are mapped out to create a virtual inventory of the entire IoT environment. During this time an adaptive baseline is created to better identify abnormalities, as well as insure a performance gauge against the network’s current state.
Who is it recommended for?
This system is good for big industrial sites with a variety of equipment from different suppliers. The tool looks for outdated firmware and updates it and it will also check on configurations. IoT devices have become big targets for botnet infections and OT systems could go that way too if not properly secured.
Pros:
- Specializes in secure physical infrastructure
- Supports highly complex network designs and access controls
- Can support IoT implementations
- Uses packet inspection and behavior analysis to detect threats
Cons:
- Best suited for enterprise networks supporting critical infrastructure
SCADAfence is available for demo upon request.
3. Nozomi Networks Guardian Sensors
Nozomi Networks Guardian Sensors is an industrial network performance monitor. It is able to detect industrial devices, called industrial control systems (ICSs) and operation technology (OT) systems as well as IoT devices. While ICSs and OT are found on the shop floor in the form of networked machine controllers and programmable systems, IoT devices can be anywhere around the premises, such as security cameras. Some IoT devices that need to be monitored can even be offsite.
Key Features:
- Device discovery
- Asset inventory creation
- Also monitors cloud and virtual systems
Why do we recommend it?
Nozomi Networks Guardian Sensors are collectors for environmental conditions that protect industrial control systems, IoT devices, OT equipment, and other It systems. These sensors are available both as physical devices and virtual appliances. While providing readings, the system also maps and scans each device, providing patch management and configuration control.
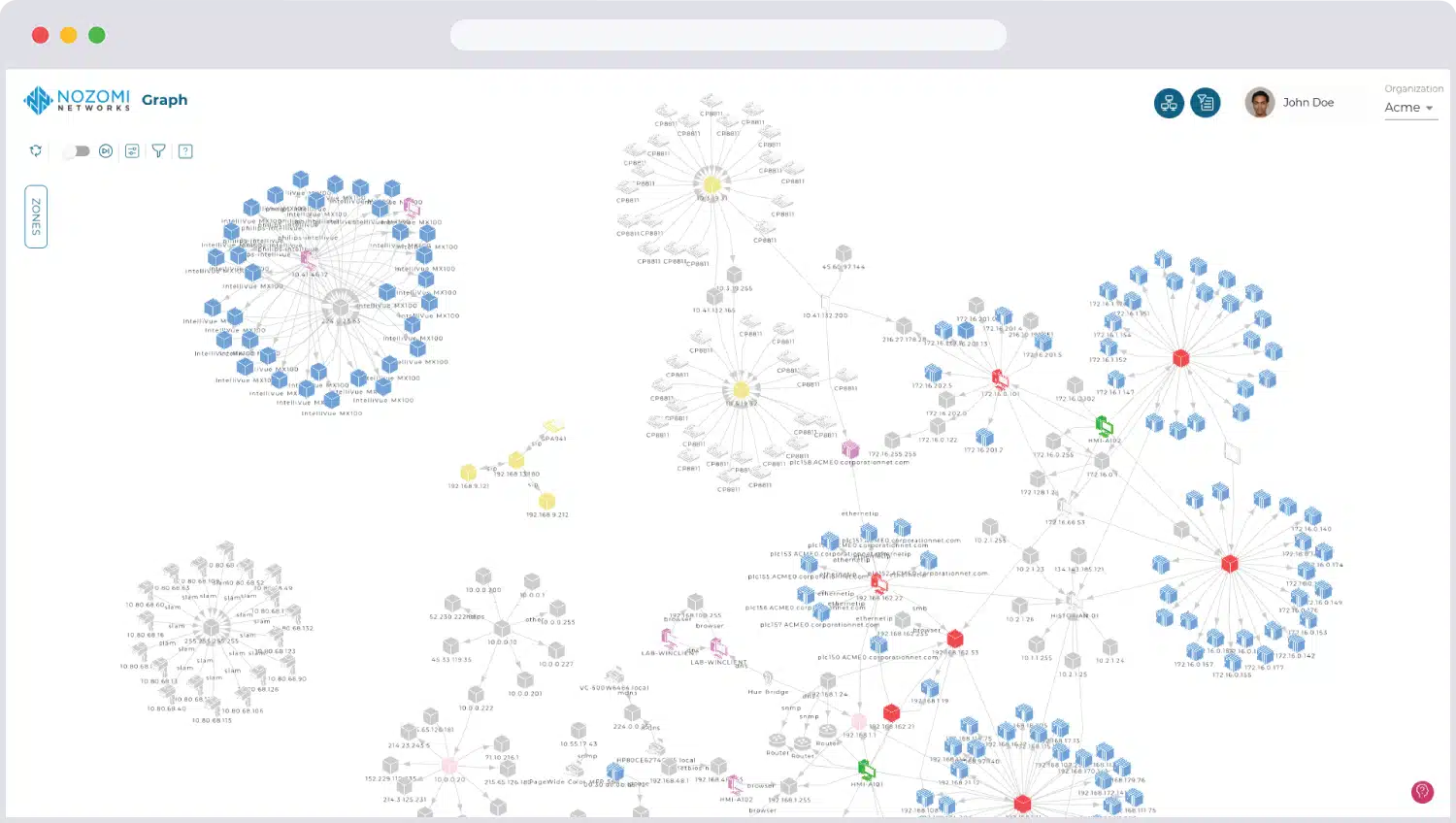
The Nozomi system scours an industrial network and discovers all of the intelligent devices that are connected to it. The system can also scan wireless systems and identify IoT devices. Each encountered device is queried for its attributes and the information gathered in this process is entered into a device inventory.
The monitor is able to compose a network topology map based on the network inventory and connection details relayed by each device. Each successive performance status checks constantly update both the inventory and the topology map.
Performance monitoring looks at traffic throughput and protocol activity. The system can then identify unexpected or abnormal behavior and that causes the Nozomi service to generate an alert. This notification of a problem draws the attention of system technicians to implement troubleshooting investigations.
While polling for status reports from all devices, the Nozomi system also performs vulnerability scanning. Issues that are discovered during both status and vulnerability scans are color-coded by severity in the Nozomi console and prioritized for resolution.
Who is it recommended for?
Any industrial or flow processing system can benefit from this system. The package includes sensors for operations activity and environmental risk as well as software for asset management and configuration protection. You can also use this system to spot traffic anomalies that could represent an attack.
Pros:
- Discovers and documents all industrial and IoT devices
- Provides a network map, which is constantly updated
- Implements live performance monitoring
- Includes vulnerability management
- Prioritizes discovered errors for resolution
Cons:
- No on-premises option
The Nozomi Network Guardian Sensors system is a cloud-based SaaS package. You can get a demo of the Nozomi system to assess it for yourself.
4. SigaGuard
SIGA creates visibility into IoT networks and IT devices using accurate real-time sensors combined with a centralized monitoring and security platform. SIGA not only uses this information to provide OT security, but to reduce the need for human intervention by automating security responses.
Key Features:
- Sensors supported by 10+ integrations
- Electrical signal monitoring
- Regulatory reporting
Why do we recommend it?
SigaGuard is a network TAP. It is a Physical Layer system that recreates packets and then compares the results to the data that arrives at the console. This is an important protection against the hacker strategy that inverts sensor results in the receiving software to con an operator into making inappropriate interventions.
SIGA is flexible and can be used in any industry such as energy, manufacturing, water treatment, or building management. The platform is designed to cover OT security as well as provide real-time business intelligence, reporting, and asset management all in as a single service.
Rather than using packet inspection, SIGA monitors raw electrical signals in the physical process to help support visibility into devices and pair that information with security insights for a deeper understanding of how the industrial side of your network is operating.
Currently, SIGA uses ICS and sensor technology that is supported by Honeywell, Siemens, GE, Schneider, and six other companies. These sensors can help close the gap between OT and IT by networking them through an alert control system. This system monitors for abnormal fluctuations or suspicious events that may signal a cyber attack is underway.
Alerts can create tickets for a security team, or deploy automated responses. In addition to real-time alerts, regulatory reporting and asset performance insights can be saved or sent out automatically depending on your needs.
Who is it recommended for?
This system is useful for critical infrastructure, such as pipelines or pressure systems that can be seriously damaged if sensor readings are corrupted either through connection errors or malicious actions. This package can be used by in-house security operations teams or managed security service providers.
Pros:
- Supports automation across complex critical infrastructure
- Provides regulatory monitoring and security automation
- Supports enterprise integrations
Cons:
- Better suited for industrial IoT networks
You can view a demo of SIGA in action upon request.
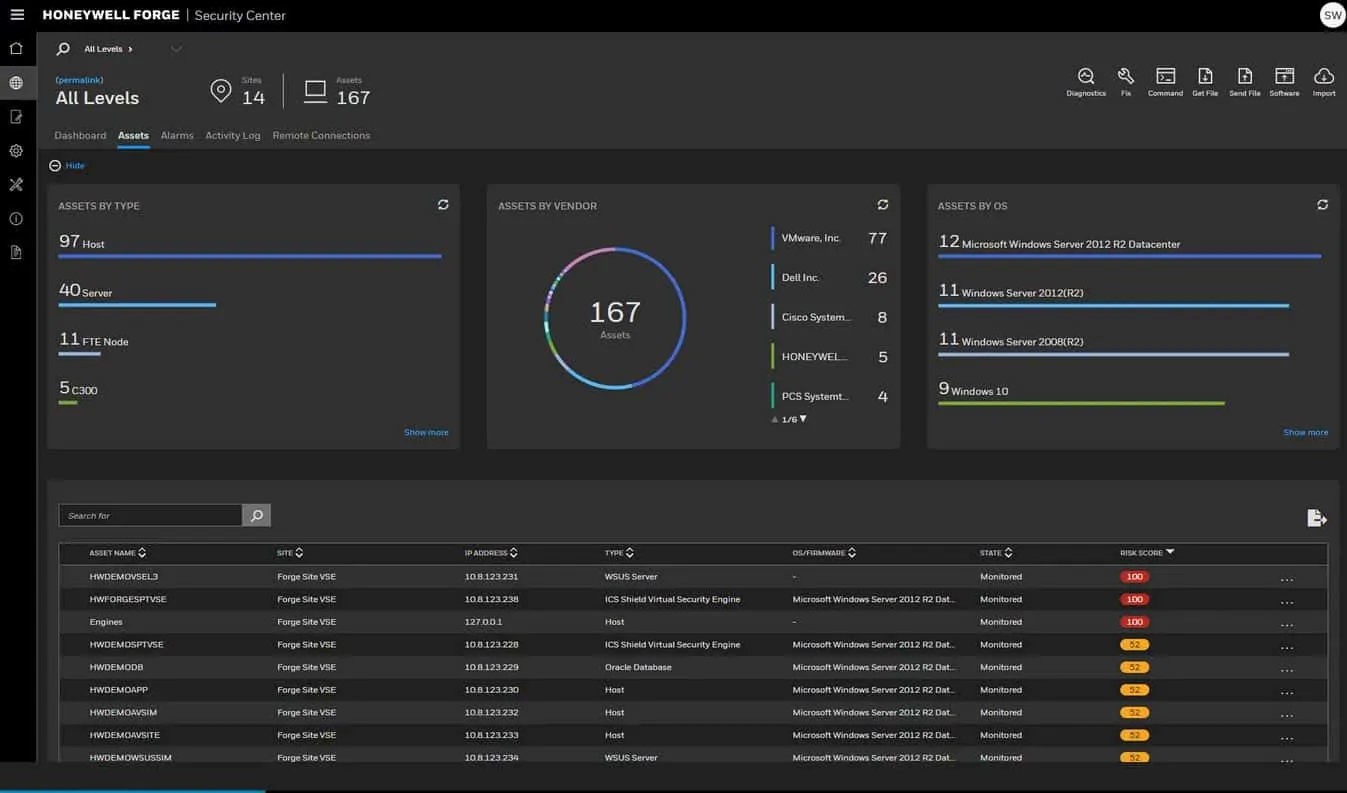
5. Honeywell Forge Cybersecurity
Honeywell Forge Cybersecurity platform works to secure every endpoint in the IoT chain and bring that data together in a way that makes business safer and more efficient. Honeywell offers solutions for virtually any sized business or level of cybersecurity maturity.
Key Features:
- Follows NIST and industry-standard guidelines
- Features risk scoring
- Real-time and historical data collection
Why do we recommend it?
Honeywell Forge Cybersecurity discovers all equipment on a network and creates an asset inventory. It then performs a risk assessment on each device. The package then implements continuous monitoring for anomalous network traffic. Two multi-site systems add on the management of communicating remote monitoring over the internet.
With scalability in mind, Honeywell uses NIST SP 800-82 and other leading international standards to ensure your company is within compliance and leveraging best practices against OT security threats.
At a glance, Honeywell Forge provides insights into your network by creating events paired with a risk score. From this score, you can drill down and identify exactly what your risk factors are, and see what predetermined security policies may be in violation. This methodology helps IT security teams quickly view and prioritize assets that may be the most vulnerable.
Remote access into your industrial network can be standardized and audited through role-based and device-specific privileges. This extends into securing OT-centric files or data with built-in threat detection that inspects and monitors files in transit.
Proactive monitoring allows for both real-time alerting and historical data collection that can be integrated into a SIEM product. Different alerts can be set up depending on the type of event. For example, security events can be routed to the security team, where maintenance events such as a low oil level can be routed to a maintenance team member.
Who is it recommended for?
Honeywell is a solid brand and this system will appeal to existing customers of the company’s IT systems. This is a straightforward traffic monitoring system that has been applied to industrial sites. The Fircepointr and SCADAfence systems offer more innovative security solutions.
Pros:
- Excellent user interface – great for NOC dashboards and teams
- Offers NIST standard reporting and vulnerability prioritization
- Supports real-time data collection – great for enterprises using SIEM products
- Provides a variety of integrations for alerting and notifications
Cons:
- Is a better general OT vendor
Pricing and further information can be provided by the Honeywell sales team.
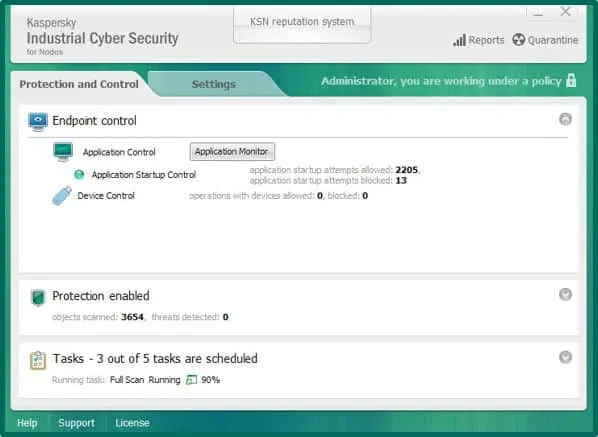
6. Kaspersky Industrial CyberSecurity
Kaspersky is known for its suite of security products that cover dozens of different threats and business needs. Industrial CyberSecurity aims to connect processes, people, and technology in a way that is both safe and easy to manage.
Key Features:
- Education for in-house teams
- SCADA specific monitoring and protection
- Holistic monitoring based on the sensor
Why do we recommend it?
Kaspersky Industrial CyberSecurity is a complicated platform of multiple units. This system covers devices and networks and it also ties in with Kaspersky’s office systems security products. This is a difficult system to set up because it has a lot of moving parts but once it’s working, the system console makes sense of everything.
With over a dozen integrations and partnerships, Kaspersky Industrial CyberSecurity offers OT security for enterprise-level industrial businesses. The platform holistically uses sensors and systems to monitor key assets as well as provide business intelligence.
Designed to secure every layer of the industrial network, Kasperksky has security solutions for monitoring and protecting SCADA servers, human interface machines, programmable logic controllers and endpoint workstations.
Through industrial endpoint protection on each sensor, Kapsersky can monitor for breaches, anomalous behavior, and insider threats. Outside of the OT security service, Kaspersky also provides training for IT, OT, and C-level members for your organization to increase cybersecurity awareness and assist teams in-house.
Who is it recommended for?
This system is suitable for large organizations that have a lot of technicians on staff. It is particularly useful for companies that need to flow information back and forth between the office and the shop floor because all of the movements present opportunities for malicious intervention.
Pros:
- Supports industrial endpoints and IoT infrastructure
- Great for smaller OT networks
- Has a vast repository of tools for new users
Cons:
- Could use a more visual interface
You can reach out to the Kaspersky team for a demo of their platform.
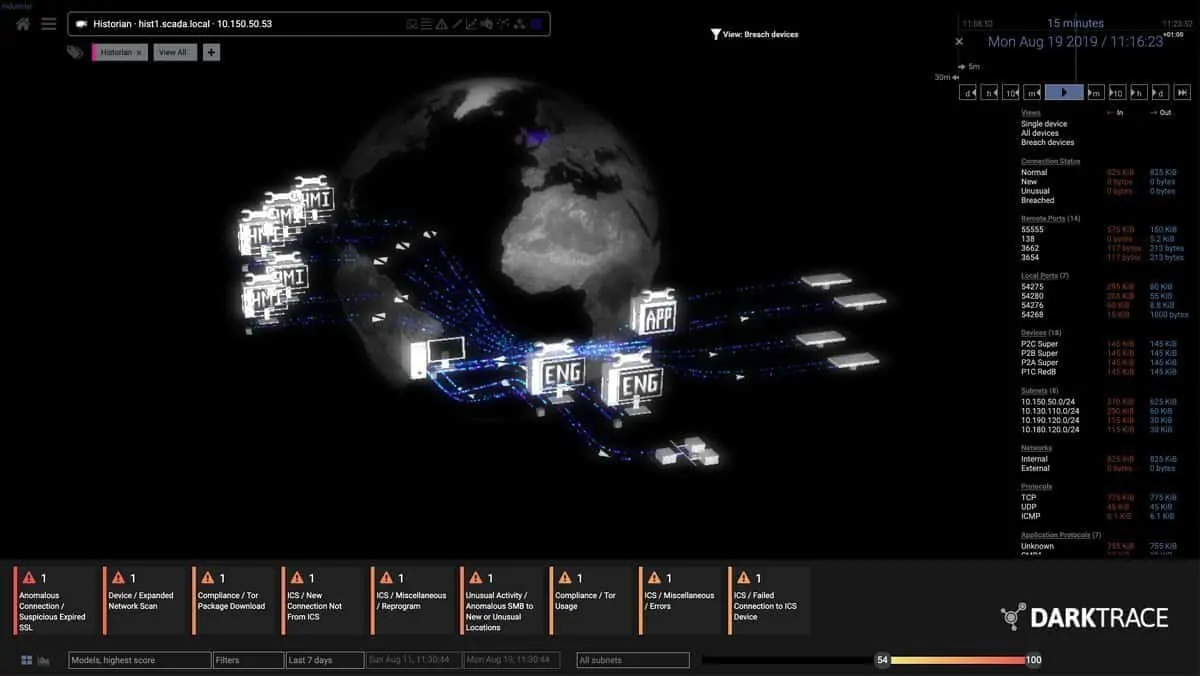
7. Darktrace Industrial Immune System
Darktrace is a cloud-based OT security platform that uses self-learning artificial intelligence to cover entire networks, including IoT assets. For industrial security, the Darktrace Industrial Immune System works by monitoring the baselines of hundreds of networks in the industrial space to see what “normal” looks like.
Key Features:
- Leverages artificial intelligence
- Integrates with older technology
- Provides a suite of additional security features
Why do we recommend it?
Darktrace Industrial Immune System is part of an anomaly detection system that uses AI to profile each user and each device on a network. This is a technique that is known as User and Entity Behavior Analytics (UEBA). Darktrace was a pioneer of this methodology, which is now widespread.
It uses this information to track and detect anomalous behavior as it plays out. Each time an attack is found and stopped the system learns what to look for next time, remembers how it operated, and how it can defend against it.
The system takes this same learning approach for every device, controller, and user. A pattern of life is recognized over time by the Darktrace system, and deviations are alerted to. Outside of cyberattacks, the system can also identify internal threats, operator error, and mechanical malfunctions.
Since Darktrace uses AI to recognize and understand patterns, the entire platform is protocol agnostic, meaning that it can be used to monitor virtually any protocol or technology. The platform can fully support any business looking to increase its security posture and can integrate with old PCLs or devices without current sensor support.
Outside of OT security, Darktrace can offer security services for email, cloud-based applications, and standard IT network security monitoring.
Who is it recommended for?
Darktrace is known for insider threat detection in office systems. This is now also applied to OT devices. Darktrace can spot unexpected activity, such as changes to the settings of industrial equipment and looks for unauthorized instructions. This is a good option if you want to unite your office and shop floor security systems.
Pros:
- Offers great data and threat visualizations
- Leverages artificial intelligence to monitor complex networks
- Uses baseline analysis to detect threats and other anomalous behavior
Cons:
- Better suited for enterprise networks
You can test out Darktrace through a free 30-day trial.
8. Dragos
Dragos is a robust OT/ICS cybersecurity platform designed to provide professional OT security services as well as platform and threat intelligence training. Designed by ICS practitioners, the Dragos platform starts with best practices out of the box and works to constantly protect and monitor your IoT environment.
Key Features:
- Global intelligence sharing
- Managed service option
- 21+ partnerships
Why do we recommend it?
Dragos is a specialized OT security platform that includes preventative measures and security monitoring. This service includes a vulnerability scanner that checks on misconfigurations in OT devices and identifies outdated firmware. The security monitoring looks for intrusion and it is informed by a threat intelligence feed.
While some platforms just provide alerts to OT security events, Dragos takes it a step further by providing step-by-step instructions on exactly how to handle a threat or security incident. These are called Key Takeaways and are designed to give your security team actionable items to complete to rectify any issues.
There are also labeled Indicators of Compromise (IoC) which are forensic breadcrumbs that can be traced to help identify malicious behavior. IoCs are important when not only documenting threats but also building a legal case against an attacker.
IoCs along with detailed reporting gives you an inside look into adversary behavior and the techniques that were attempted on your network. This information can be used to correct vulnerabilities and identify other possible avenues of attack.
Who is it recommended for?
Any system manager will understand the Dragos methodology because it performs the same techniques on industrial systems that are regularly implemented for office endpoints. This is a thorough solution that ensures OT systems are hardened against attack and it also adapts security monitoring to current attack campaigns.
Pros:
- Uses simple yet intuitive graphics to display network information
- Offers over 21 partnership integrations
- Uses global intelligence sharing to power their threat detection
- Offers tools that provide documentation for legal and forensic investigations
Cons:
- Better suited for enterprise networks
Dragos provides powerful OT security by not only leveraging its global intelligence sharing but through its 21+ strategic partnerships. For companies who are looking to manage their OT Security off-site, Dragos provides OT security as a managed service through its Neighborhood Watch program. This lets the Dragos team manage and stop security threats, update and patch endpoints, and conduct threat hunting on your network.
OT Security FAQs
What is OT cybersecurity?
OT security, or OT cybersecurity, defines a range of technologies, processes, and best practices that combine to protect office and industrial systems and the connections between them. Inputs to the security management service can also include sensor and video detection systems that enable physical protection to be woven into the security system.
What is OT and IoT security?
OT security is designed to protect premises and industrial equipment as well as office networks and their attached devices. Premises equipment extends to IoT devices, so IoT and OT security measures are very closely linked.
What is OT in NIST?
The National Institute of Standards and Technology (NIST) in the USA has created a Special Publication that is entitled Guide to Operational Technology and this explains to businesses how to go about implementing OT security. The code for the publication is SP 800-82r3.


It’s amazing to me that an article like this can get past editors while leaving out the four actual leading ICS Cyber Security solutions with the largest footprint (Claroty, Forescout, Microsoft, and Nozomi Networks). How does this happen?
Nozomi Networks is a worthy contender. Added – thanks.