Controlling who can access a folder is the best practice. Setting folder permissions ensures that sensitive information is protected from snoopers who shouldn’t have the authorization to change or even access the content. At the same time, configuring permissions lets users who have the right to access a folder to do so securely.
What are permissions in Active Directory?
Permissions in Active Directory are access privileges that you grant to users and groups that permit them to interact with objects. An administrator assigns permissions to a user or a group so that they can access or manage a folder.
Permissions in Active Directory are divided into standard permissions and special permissions. Standard permissions give the user privileges such as read, write, and full control. Special permissions give the user different abilities such as allowing the user to modify object permissions or owners.
How to set folder security permissions in Active Directory
The process of setting folder permissions is simple and you can choose to assign folder access to users and groups. In this section, we’re going to look at how you can assign permissions from within Active Directory through the Group Policy Management Console (GPMC).
Creating a Group Policy through the Group Policy Management Console
The GPMC provides group policy settings that you can use to configure security permission. One of the simplest ways you can use the program is to create a group policy object. A group policy object is a group of settings that you create with the Group Policy Object Editor that can restrict the access of users to particular files.
To create a new group policy object follow the instructions below:
- Click Start > Administrative Tools > Group Policy Management. The Group Policy Management Console will display.
- Right-click on the Group Policy Objects icon and select New. The New GPO window will display.
- Enter a Name and leave the Source Starter GPO option set as (none).
- Right-click on the GPO you just created and select Edit GPO. The Group Policy Management Editor window will display.
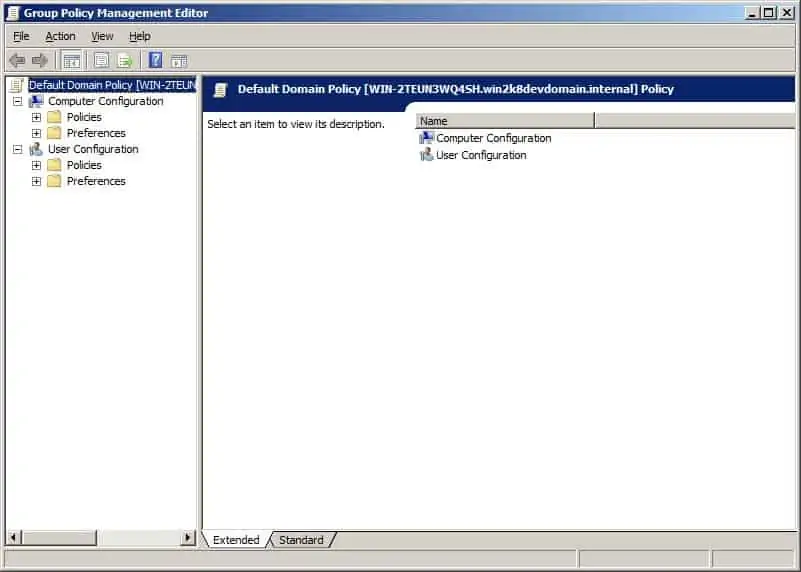
- Go to Computer Configuration > Policies > Windows Settings >Security Settings and right-click File System> Add File. The ‘Add a file or folder’ dialog box will display.
- Locate the folder or file you want to assign permissions to and click on it. Now press OK.
- Once the Database Security window comes up, click the Advanced button to display the Advanced Security Settings window.
- In the Permissions tab, you can assign permission for a new or existing user. To create a new user click Add. If you want to select an existing user, select the user and press Edit.
- Once the Permission Entry box opens you can view a list of permissions that you can choose to Allow or Deny, as well as determine where those permissions will Apply. Click on the Apply to the drop-down menu to choose where you want to apply the permissions.
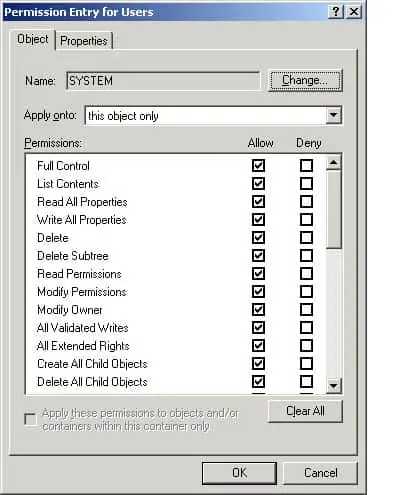
- In the Permissions list view, check the permissions that you want to assign to your object. Now press OK.
- Once you return to the Advanced Security window, go to the Auditing tab. Here you can choose to audit changes to the folder and permissions. You can also go to the Owner tab to configure ownership settings.
- Once you’ve entered your settings click OK. Once the Advanced Security window closes click OK again to close the Database Security window.
- When the Add Object window comes up, you have a number of options: The Configure this file or folder section comes with two sub-options;
Option A) Propagate inheritable permissions to all subfolders and files – The first sub-option means that all subfolders will inherit permissions from the parent folder, but if there’s a conflict then subfolder permissions will take precedence.
Option B) Replace existing permissions on all subfolders and files with inheritable permissions. -The second sub-option means that all subfolder settings will be overwritten by the parent’s settings. Alternatively, you can select the Do not allow permissions on this file or folder to be replaced option and create an entry for the specific folder you don’t want to inherit permissions. If you select the first option, click OK to close the window. - Close the Group Policy Management Editor window and right-click on the domain you want to apply to GPO to and click Link an Existing GPO.
- Once the Select GPO window displays select the name of the GPO you just created from the list and press OK.
- Now go to the Linked Group Policy Objects tab and right-click on Assigning Folder Permissions > Enforced. Now press OK to finish.
Managing AD folder permissions with third-party tools
Active Directory is such an established tool that there is no shortage of tools that integrate to provide a better AD management experience. You can use third-party tools like ManageEngine ADManager Plus to manage folder permissions through an external piece of software.
The advantage of doing this is that you can manage AD through a program that’s more user-friendly, making it easier to manage lots of users and groups. The exact process will depend on the type of program you’re using.
ManageEngine ADManager Plus (FREE TRIAL)
ManageEngine ADManager Plus is an Active Directory management tool that can be used to manage objects, create groups, and more. To manage file permissions do the following:
- Sign in to ADManager Plus.
- Go to AD Mgmt > File Server Management > Modify NTFS permissions.
- Choose which folders you want to enable a user or group access to.
- Now go to the Accounts section and choose the users or groups you want to grant permission to access the folder.
- Finalize the changes by clicking Modify.
You can download the 30-day free trial version of ManageEngine ADManager Plus.
See also: Best AD Management Software
User access best practice: Least Privilege
When assigning permissions to users it is best practice to adhere to the concept of least privilege. Least-privilege user access is about assigning all users the minimum permissions possible. Every permission assigned to an employee should be critical to their day-to-day work. Restricting user privileges will help to minimize your exposure to risks and reduces the likelihood of cyberattacks or data breaches.
To implement least privilege user access then you’ll have to know precisely what every employee needs to have access to. To begin with, start by assigning privileges to individual accounts or groups. Managing a small number of users first will make sure you don’t get overwhelmed.
See also: Best Access Rights Management Tools
AD Security Permissions: A must-have
Implementing Active Directory user permissions is one of the most basic controls you can use to make sure that sensitive information stays private. Making sure that employees only have access to the documents that are relevant to their role eliminates confusion and keeps your data safe.
Protecting your files with user permissions is the bare minimum you should be doing to control access to your data. You never know when a cyber attack will take place and minimizing the users who have access to a file will lower the chance that an attacker will be able to see your information.
AD folder permissions FAQs
What are special permissions in Active Directory?
Special permissions in Active Directory, as opposed to standard permissions, allow you to set customized permissions combinations. Folder permissions grant access to others, either members of the same group as the folder owner or members of any group. Permissions can also allow access to descendant folders.
How does delegation work in Active Directory?
The delegation principle in Active Directory gives users or groups the ability to create or alter objects and grant themselves or others permissions without them needing to have Domain Administrator status. The full name of this service is “delegation of control”.
How many types of groups are in Active Directory?
Active Directory has two types of groups. The first of these is the Distribution group type, which is intended for use with email distribution lists. The second is the Security group type, which assigns permissions to shared assets, such as file folders.