Account takeover (ATO) fraud involves a criminal gaining unauthorized access to a user’s account and using it for some type of personal gain. With the large number of accounts people have online, an increase in activities like online shopping and banking, and the frictionless payment systems many businesses have in place, the environment is ripe with opportunity for criminals looking to make some cash. One report cited account takeover fraud as responsible for losses of $5.1 billion in 2017 alone.
While ATO fraud can be costly for both businesses and individuals, there are ways to prevent it. For example, businesses can put measures in place to detect unusual activity and alert customers to account changes. Customers can follow best practices such as using strong passwords and enabling two-factor authentication where possible.
In this post, we describe what account takeover fraud is, including examples, how to spot it, and steps to prevent it happening to you or your customers.
What is account takeover fraud?
Account takeover fraud can involve any type of online account, including ecommerce, social media, and online banking accounts. Commonly targeted accounts are those from which a criminal can steal money. For example, a hacker might gain access to an online banking account and send funds to their own account. A fraudster could take over a social media account and invent a reason to request money from family and friends of the victim.
Ecommerce sites are particularly handy for criminals. Frictionless payment systems where all billing information is stored can make it convenient for customers to make purchases, but also make it very simple for criminals to jump in there and treat themselves. If a hacker discovers the login info, they can simply go in, change the shipping address, and start making purchases.
Both businesses and customers end up losing as a result of account takeover fraud. Businesses lose money to chargeback requests and suffer a damaged reputation. Customers typically endure monetary losses, but may also lose time spent trying to resolve issues, and could even suffer damaged relationships with others, for example, in the case that social media accounts are taken over. In 2017, ATO fraud involved an average resolution time of 16 hours and an average cost of $290 out of pocket.
Account takeover fraud is sometimes referred to as a form of identity theft because the criminal is effectively posing as the victim when they log in to an account. However, others argue that the two are separate. With account takeover, the fraudster is using an existing account, whereas in identity theft, they would open up a new account while posing as the victim.
How do criminals get credentials in the first place?
Cybercriminals can get the information they need to take over your account in a number of ways. Here are some of the most common:
Data breaches
One common scenario is a data breach in which a list of usernames (and potentially accompanying passwords) is leaked. These lists go on sale on the black market, meaning any number of criminals could be using them at the same time.
If a username and password for one account is known, hackers can use automated systems to try the same combination on a list of popular online platforms. This is referred to as credential stuffing, and is the reason it’s so important to use a different password for every account.
If only a username or email address is known for a particular platform, a criminal might use a brute force or similar attack to try to guess the password.
Read more: Biggest data breaches in history
Phishing attacks
Another common method to obtain credentials is through a phishing attack. These attacks may occur via email, over the phone, or via text message, but the gist is that the fraudster is trying to get you to hand over your login information.
For example, a phishing email might pose as a customer support message that persuades you to click a link to a phishing site (a fake website designed to phish for information). Here, you’re prompted to enter your login information, which is then stolen by criminals.
Phone scams
While some phone scams are geared toward phishing for information, some callers will directly try to take over your account while you’re on the phone. An example of an account takeover scam initiated over the phone is an iteration of the tech support scheme.
For example, the criminal poses as a Microsoft representative and persuades you that your computer has a virus and needs to be fixed. You hand over remote access to your device, and the criminal can access any accounts you have credentials stored for. They may purport to be “testing” accounts and access them in plain sight, or they could use the remote access to install spyware (more on that below).
The victim isn’t always the one targeted in a phone scam and many criminals target company customer support representatives instead. For example, customer service representatives for banks or wireless carriers may be duped into providing fraudsters with enough information to persuade another rep to grant them control of the account.
See also: Phone scam statistics
Account recovery
In this case, an account takeover leads to more account takeovers and involves an attacker already having access to your email or phone account. Since most platforms verify account holder status through email or phone number (often giving you the option), all an attacker needs to reset your password on other platforms is access to one of those accounts. This also works in bypassing two-factor authentication if a code is sent to the email address or via SMS.
Spyware
Specific types of malware downloaded onto your device from malicious email links or attachments or malvertisements could expose your credentials. Some spyware takes regular images of your computer sessions, while keyloggers record every keystroke, exposing your usernames and passwords.
Related: Best free spyware removal tools
Stolen documents or skimmed numbers
Account numbers are often a card number, for example, your online banking username may be your client card number. This can be discovered from a bank statement found in the trash, a stolen wallet, or through skimming. The latter is where small machines read the card number at an ATM or a point of purchase, for example, a gas pump. Once the account number is known, the password can be guessed using a brute force attack.
Hacking over unsecured wifi
Many people think nothing of logging in to free wifi while at a cafe, mall, hotel, or airport. But these networks are often unsecured and represent a great opportunity for hackers to steal your information. A common attack over these networks is a man-in-the-middle attack in which the hacker intercepts the contents of your internet traffic.
This could expose any information you send, including credentials for various platforms and payment information on ecommerce sites. A Virtual Private Network (VPN) can help protect your wifi connections by encrypting your web traffic.
What are attackers trying to do?
Perpetrators of account takeover fraud have many and varied motives. The exact reason for wanting to take over a given account will depend on the type of account. Fraudsters might have any number of reasons for wanting to take over say, a social media or ecommerce account.
Here are some of the different things criminals can get up to once they have access:
- Credit card fraud: Attackers might be after your credit card details for use in credit card fraud. While this is common with ecommerce sites, it’s also possible for many other accounts where your credit card information is stored, such as subscription media services or toll companies.
- Merchant account fraud: Common with ecommerce sites and a form of credit card fraud, the criminal simply orders goods through your account and changes the shipping address.
- Bank account fraud: With access to your bank account, an attacker can transfer funds to another account, among other things.
- Loyalty fraud: This involves using or transferring points from loyalty or reward sites. One of the main reasons loyalty fraud is reportedly on the rise is that people don’t monitor their loyalty accounts as much as they would their bank or credit card statements. That is, points aren’t viewed as money by customers, but they are by criminals.
- Resell credentials: Username and password combinations may be posted for sale on the black market.
- Credential stuffing: This is where the username and password pairing for one platform is used to try to access accounts in other popular platforms. This can be done using an automated system.
- Harvest data: The criminal might be looking to find out more information about the victim, including social security number, address, phone number, and credit card information for use in other fraud such as identity theft. When taking over email or social media accounts, they can read private messages, learn about relationships with various individuals, and lots more.
- Take out loans: Access to financial accounts can be used to take out loans and even mortgages in your name. (This is technically new account fraud or identity theft but often occurs as a result of account takeover fraud).
- Monetary requests: By taking over your social media account, the attacker can pose as you and make requests to family and friends, for example, for money.
- Extortion: Criminals might hold your account hostage and ask you for money, goods, or services, in exchange its return.
Once a criminal has access to an account, they usually very quickly try lock the real user out by changing the password, recovery email, two-factor authentication settings, and security questions, and logging out of other devices. At that point, the only way to get your account back is by contacting the business. By the time you get to speak to a customer service representative, chances are the criminal has already done what they came to do.
Account takeover fraud examples
Now that we know what attackers might be trying to do, let’s take a look at some examples of how account takeover fraud works.
Cloud email account takeovers
A March 2019 Proofpoint report highlights the growing problem of cloud email account takeover attempts. The study looked at Office 365 and G Suite cloud accounts over six months, monitoring more than 100,000 unauthorized logins. It found more than two percent of active user accounts were targeted by attackers, and out of every 10,000 active user accounts attacked, 15 were successfully breached by hackers.
Most of these attacks originated in Nigeria or China, with the primary aim often being to target businesses by launching internal or external phishing attacks from trusted accounts. If the user has the required access, however, the account takeover may be used to move money or data.
Bank account takeover
In 2018, a BBC report described how a woman lost more than £4,000 when her Royal Bank of Scotland account was taken over. In this case, the criminal didn’t use online banking to access the account, but rather used a little charm and savvy (aka social engineering) to persuade one of the bank’s customer service representatives to approve a fraudulent transfer of £4,318.
In this case, the fraudsters were able to outsmart the bank on a couple of levels, but the fraud still should have been detected. After the perpetrator called to make a change to the account, the bank called the victim on her landline number as a standard precaution. The savvy criminal had already diverted the number to their own cellphone. During the call, the fraudster requested two transfers to other accounts. The first was allowed, but the second was disallowed due to incorrectly answered security questions. However, the bank didn’t recall the first and the victim lost her money.
Eventually, the bank admitted the mistake and refunded the amount, but the ordeal wasted a lot of time for both the bank and the victim. Various forms of bank account takeover fraud are very common, with more than 100,000 reported cases of bank account takeover fraud in the UK last year.
Facebook account takeovers
A 2017 report details the Facebook account takeovers of an emergency room doctor and a gym owner, but these are just a couple of many such examples. In these specific cases, it’s suspected that the people who took over the account were simply unable to open their own account, perhaps due to their location or having been blocked. Other reasons for takeovers could be to solicit family and friends, harvest information, or spread hate speech under the victim’s name.
The popularity of Facebook makes it a massive target for cybercriminals. What’s more, even though Facebook has reporting methods in place, victims often have a very hard time getting Facebook to respond to account takeover reports, meaning criminals are able to use the accounts for prolonged periods.
Plus, Facebook has a less-than-stellar security resume and many breaches have been reported over the years. In September 2018, a bug in Facebook’s code put 50 million user accounts at risk by allowing hackers to steal access tokens. These tokens keep users logged in and can allow hackers to break into accounts. In April 2019, 22,000 email address and password pairings were made available for public viewing.
Facebook account takeover is such a big problem that Facebook increased its “bug bounties” for account takeover vulnerabilities in 2018. Researchers can earn up to $40,000 for finding vulnerabilities that can result in a full account takeover.
Even the CEO of Facebook is not immune to account takeover; Mark Zuckerberg has had multiple social media accounts taken over several times, with attackers simply wishing to prove a point.
Instagram account takeovers
Facebook isn’t the only social media site targeted. A 2018 report highlighted an issue with Instagram account takeovers with attacks originating in Russia. This widespread campaign saw details associated with the accounts changed by hackers. For example, names, profile pictures, and email addresses were altered. Passwords were also changed such that users were completely locked out of their accounts.
The problem is that once the email address is changed, Instagram’s normal recovery methods (which use email) no longer work. As with Facebook, users have had problems getting Instagram to resolve issues, and in many cases, simply give up. This leaves the criminal to do what they want with the account. In this case, one suspected reason for the hijacking was to use the accounts as part of a spam bot, for example, to promote adult content.
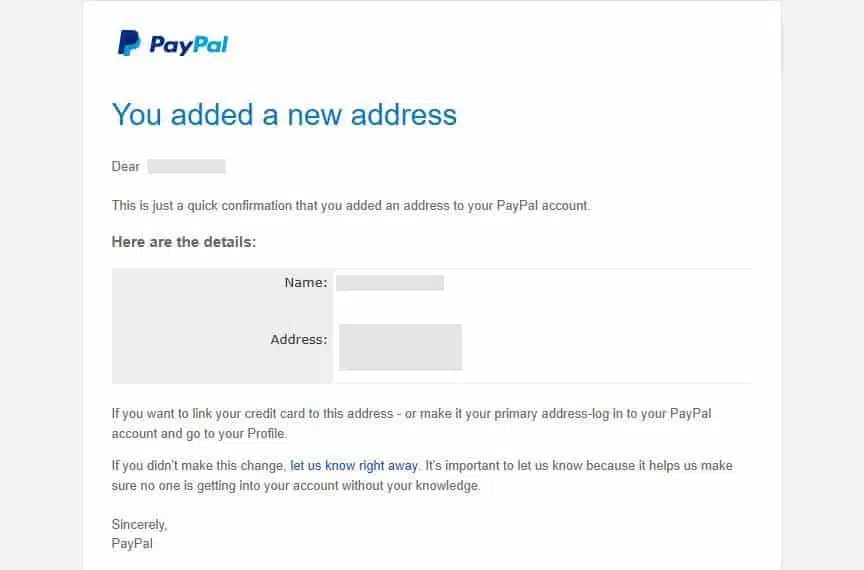
PayPal address change
This example is an incident I recently experienced. I am signed up to the Have I Been Pwned website which notifies me in case my email is involved in a known data breach. A couple of months ago, I received an email telling me my email was involved in a recent breach. However, it was for an old email address that I don’t have associated with any important accounts, or so I thought.
A few days later I got an email from PayPal, regarding an old account that I no longer use:
Someone had managed to go in and add an address, even though the account had been locked a long time ago. PayPal is usually so strict about changes that even I would have trouble making changes to this account. The fact that a fraudster could so easily make an amendment is unnerving to say the least. Presumably the criminal planned to purchase goods through the account and have them shipped to the new address.
Note that this was on a weekend so I didn’t read the email until about 24 hours after it hit my inbox. Thankfully, there was no current payment method linked to the account, but had that been active, the intruders could have caused a lot of damage before I noticed what was happening. Needless to say, I notified PayPal and closed the account immediately to prevent further misuse.
Phone number takeover
This type of account takeover fraud is gaining popularity and it’s probably one of the more stressful to deal with. Often referred to as SIM swapping, a criminal takes over someone’s phone number by transferring it to another wireless carrier.
The process is typically carried out via a series of calls to customer service representatives of the victim’s existing wireless carrier. Using social engineering, the criminal can glean enough information to convince a representative on a subsequent call that he or she is the real account holder.
A couple of things make this type of attack particularly scary. First, the victim doesn’t realize that their account has been breached until they lose signal on their phone, at which point the hacker is already taking over their other accounts.
That’s the other scary part. With control of a phone number, the attacker can access accounts associated with the number, including email, social media, banking, and investment accounts, among others. If two-factor authentication is used, this can often be bypassed using the phone number, too.
One SIM swap victim reportedly lost millions of cryptocurrency tokens to hackers in January 2018 and sued AT&T for $224 million.
How to prevent and detect account takeover fraud
Both businesses and customers need to work together in the fight against account takeover fraud. In this section, we’ll explain how to spot and prevent account takeover fraud for customers and businesses.
Customers
From a customer standpoint, of course, ideally you want to be proactive and prevent account takeover fraud happening in the first place. Here are some tips for prevention:
- Never use the same password for multiple accounts.
- Use a password manager such as LastPass to generate, store, and autofill strong passwords.
- Sign up to the Have I Been Pwned website to receive notifications of breaches.
- Don’t click on links from suspicious emails as these could lead to phishing sites or download malware.
- Watch out for signs of a phishing email (such as misspelled company name and poor grammar) and phishing sites (including lack of contact information or an about page).
- Use two-step verification (2SV) or two-factor authentication (2FA) where possible. Third-party apps like Google Authenticator and Authy are available for this purpose.
- Only shop on reputable sites and don’t store credit card information if you can avoid it.
- Use a VPN, especially when connected to public wifi.
- Place a security freeze or fraud alert on your credit report with all three national credit bureaus (if you’re in the US). While this doesn’t stop people using existing accounts, it can stop them using your information to open up new accounts.
- Be careful about what you share on social media. If people know what companies you use and where you eat and travel, they’ll have more luck building a profile and knowing which accounts to target with your details.
If you follow these steps, you’ll be well on your way to avoiding having your accounts taken over by malicious actors. That being said, no one is ever truly safe. After all, you’re not in control of how a company handles your data and a breach could land you in trouble.
As such, you need to keep your wits about and look out for possible account takeover scenarios. One of the most obvious ways is to watch out for emails or text messages regarding any changes to your account.
Most platforms notify you of changes by default, but you can check for any relevant settings if you’re unsure. A word of warning though: many phishing schemes involve fake emails related to account activity, so run some checks before you click on any email links.
Also, be aware that someone could change the email on the account such that you don’t receive notifications. For this reason alone, it’s a good idea to check all important accounts, especially those with financial institutions, regularly.
Do you have lots of old accounts? When you’re not using an account anymore, always go back and deactivate or delete it so there’s no chance someone else will take it over once its long forgotten.
Businesses
Account takeover fraud can be seriously costly for businesses. When customers find out they’ve been the victim of account takeover fraud and their credit card has been used to make purchases, they’re often able to make a refund request. Businesses then have to repay the money without getting the product back. The business also has to relay the chargeback request to the payment processing company, and multiple requests can drive up fees. In the long run, this can cost companies millions of dollars.
Aside from the financial impact, when an account takeover can be attributed to flaws in cybersecurity, this can put a huge dent in the company’s reputation. Consumers are becoming more security-conscious and are on the lookout for businesses that have their back when it comes to keeping their accounts and information safe.
It’s in every organization’s best interests to stay on top of things. While a business needs to have measures in place for fraud detection, there are some things that can be done to help prevent fraud in the first place.
A key measure in fraud prevention is having appropriate security protocols in place, both internal and consumer-facing. Following cybersecurity and data protection best practices and having appropriate tools in place can help ensure that you aren’t the cause of a data breach.
On the consumer-facing side, it’s important to have sufficient protocols including notification methods in case of any changes made to an account. You can also implement two-step verification and encourage or even require that users take advantage of it.
When it comes to detection, there are some clear red flags that signal account takeover attempts. Note that tools are available to help detect some of these things, but it’s good to be aware of them in any case. Here are some things to look out for:
- An unusual number of chargeback requests (customers disputing charges on their credit card)
- Hundreds of login attempts on one account
- Mass password reset requests
- Abnormal customer behavior, such as larger purchases than normal or frequent logins
- Multiple changes to an account at one time, for example, address, password, and device
- Transfers of a large number of reward points
Plenty of tools are available to help businesses detect and prevent fraud. In fact, the account takeover fraud detection industry is booming and is set to grow by 18 percent in 2019. Top companies include Zero FOX, Kount, Nadat Security, and Experian. Software uses large data analysis combined with statistical and computational methods to provide swift and precise detection.
See also: Cyber security statistics