We use the internet for pretty much everything these days, including connecting with friends, working, banking, entertainment, shopping, dating, and more. With our communication moving more and more online, unpleasant behaviors such as cyberbullying and online harassment are also becoming more common. This combined with online scams can lead to users feeling unsafe. In this article, we’ll explain the most common types of online harassment as well as how to keep yourself safe online.
By discussing a range of studies and statistics we will demonstrate the different experiences of online culture based on gender. We’ll also reveal how attitudes to online harassment can vary between men and women.
What dangers do users face online?
Women face many of the same dangers as men online. For example, things like phishing schemes, ransomware attacks, and various types of online fraud are commonplace for everyone. However, statistics show you are much more likely to experience some types of online abuse if you are a woman. Below we take a look at the online scams which target women more frequently than other genders.
Online harassment
Online harassment is loosely defined as the use of the internet to threaten, harass, or embarrass an individual or group. It can come in different forms and many of the other topics we discuss here such as cyberbullying, cyberstalking, and doxing fall under the umbrella of harassment.
Women tend to encounter sexualized forms of online harassment at higher rates than men. These can include things like sexualized bullying, unwanted sexual requests, revenge porn, and sextortion.
A 2017 study by Pew Research Center found that 21 percent of women aged 18 to 29 had experienced online harassment. The figure for men was less than half of that at nine percent. More than half of women in the same age group had received explicit images that were not requested.
Attitudes towards online harassment differ by gender with 70 percent of women and 54 percent of men believing it’s a “major problem.” And while 50 percent of women say that offensive content online is too often excused as not a big deal, 64 percent of men think it’s taken too seriously. More men (56 percent) tend to think it’s important to speak their minds freely online while women (63 percent) value feeling safe and welcome on the internet.
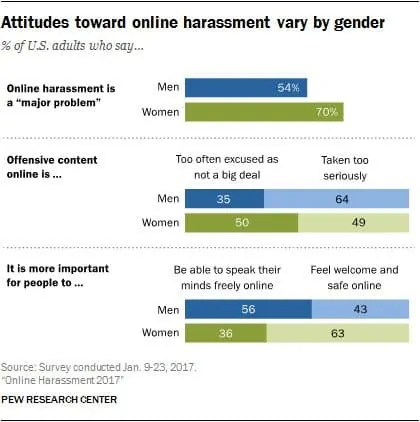
What’s more, of women who have experienced online harassment, 35 percent say it leaves a strong impression and that recent encounters have been either very or extremely upsetting. The figure for men is less than half at 16 percent.
Cyberbullying
Online bullying involves any type of bullying that occurs in the digital world, for example, through social media networks or forums, or via emails or text messages. Cyberbullying can happen to anyone, but it’s especially common among teenage girls. Female students are three times as likely to be bullied online or via text than male students.
Catfishing schemes
With the increased popularity in online dating, there are a ton of schemes out there targeting unsuspecting victims looking for love. While many men fall victim to dating scams, the majority of victims are women.
A popular tactic used in dating scams is catfishing. This is where scammers create fake profiles that they believe prospective victims will trust and fall for easily. For example, they might create a fake profile of a doctor or member of the military.
These scams typically end up with the perpetrator swindling the victim out of money or property, or in some cases, roping them into some type of illegal activity.
Cyberstalking
Cyberstalking (also called online stalking) may be defined slightly differently according to various countries’ laws, but it generally involves using electronic means to harass, bully or threaten victims.
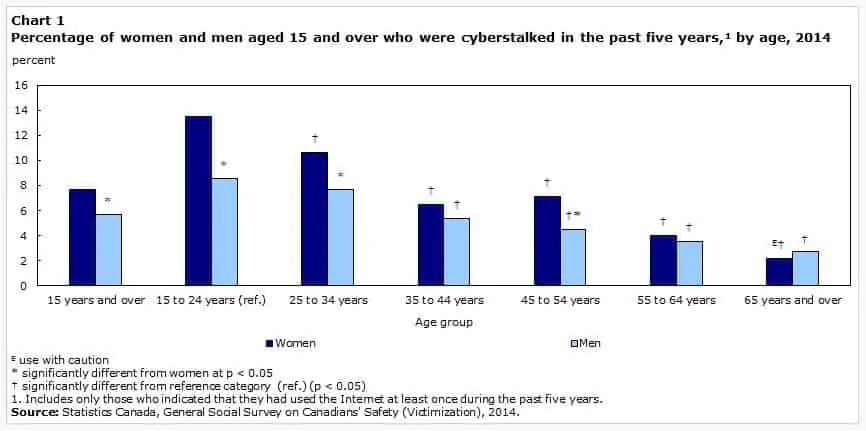
This crime impacts a surprisingly large number of men and women, but victims are more often female. A Canadian study found that the most likely targets are women in the 15–24 age group.
Sextortion
As you can probably guess from the name, online sextortion is extortion involving material (typically images or videos) of a sexual or intimate nature. Sextortion can take a variety of different forms, but the motivation is usually sexual gratification or monetary gain.
A 2019 study found that males are more likely to be targeted when the motivation is financial greed, while the victims in sextortion for sexual gratification crimes are almost always female.
An alarming 2017 study by Thorn revealed that 45 percent of sextortion perpetrators followed through on their threats. The same study found that 40 percent of victims met the perpetrators online.
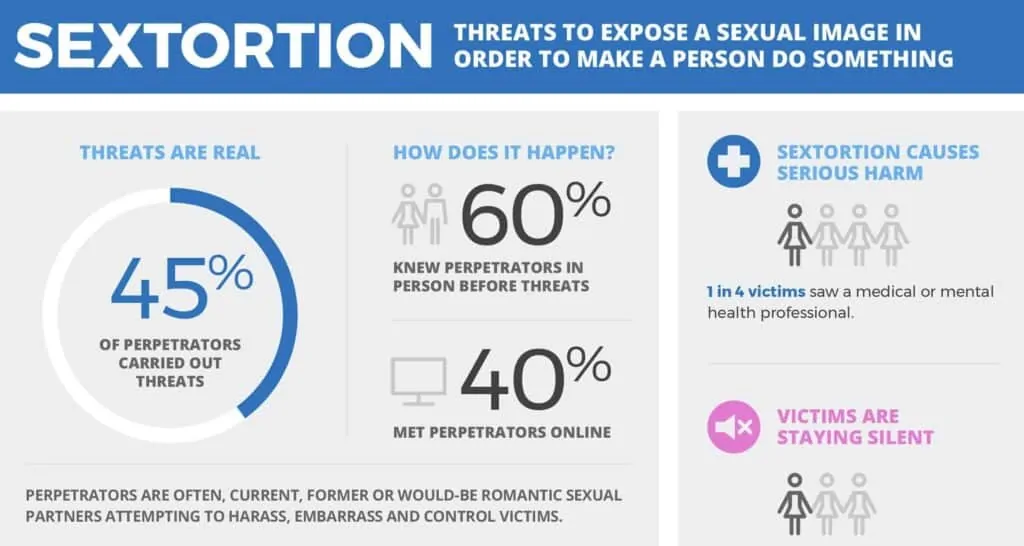
Sextortion can cause serious harm to the victim with one in four seeking help from a medical or mental health professional.
Revenge porn
Similar to sextortion, revenge porn typically involves the sharing of intimate images or videos without the subject’s permission. Revenge porn usually follows the disruption or dissolution of a romantic relationship and the perpetrator is the partner or ex-partner of the victim. They will share images or videos or the victim publicly or with select individuals, often with the motivation to control or punish the victim by causing embarrassment or shame.
A UK study by SWGfL focusing on the gender of callers to a revenge porn hotline found that almost three in four (73 percent) were female.
However, it also found that the vast majority of male callers were actually victims of sextortion, inferring that the portion of female callers reporting revenge porn was more like nine out of 10.
Doxing
Doxing (sometimes spelled “doxxing”) involves someone making your personal information public. There are many variations on doxing and many reasons why someone might be doxed, including to intimidate, harass, or extort them. Shared information might include phone numbers, email addresses, home addresses, Social Security numbers, sensitive photos, information regarding family members or employment, and much more.
According to a 2020 Wiley publication on doxing:
While both women and men experience doxxing, women, especially minority group women, are more likely to have their private information posted online and receive greater amounts of unwanted, vitriolic messages.
In the next few sections, we’ll provide advice to help you navigate the online world safely. There’s a lot to cover, so we’ve split the tips into several groups: social media, dating sites, harassment at work, and cyberstalking. First, let’s look at social media.
We spend a huge amount of time on social media sites. While this can have its benefits, it can open the door to risks. Social media platforms encourage us to share a ton of personal information, potentially exposing it to strangers or acquaintances who we wouldn’t normally share it with in real life.
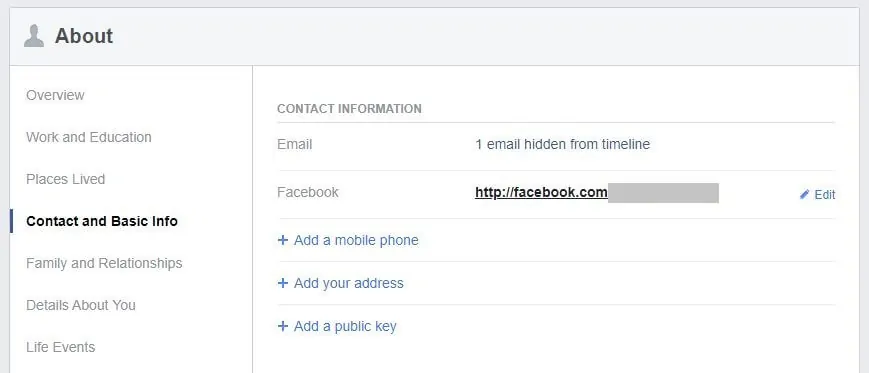
For example, Facebook asks for a ton of information on signup, including contact information, work and education details, and information about family, relationships, and life events.
So what does this mean? All this personal information makes it easy for cybercriminals to find out information about victims. They can discover details about where people live, work, go to school, shop, bank, dine out, vacation, and much more, simply by following their social media accounts.
Snoopers can also see who their victim’s family and friends are and learn about their relationships with them. They even have access to photos and videos of their target.
On top of being able to collect this information, they have a multitude of ways to communicate with their victim and the victim’s contacts. While in the past we were limited to email and perhaps one or two instant messaging systems, we now have multiple email accounts, private messaging within every platform, posts, comments, likes, and more.
All of this information and access makes it far easier to carry out a plethora of malicious activities, including cyberbullying, cyberstalking, online harassment, sextortion, and more.
Here are some tips for staying safe while using social media:
1. Use multiple profiles where possible
Most of us face a dilemma when deciding how much information to share online. These days, job descriptions often include an expectation to have a social media presence. Those who are self-employed will find it crucial to put their business (and by default, themselves) in the public eye via social media. So how do you make sure you’re accessible to colleagues, contacts, clients, and customers without giving up your privacy?
One solution is to have separate social media profiles for your work and personal life. For the former, you can choose a professional image and only post and comment about things that are relevant to your job or business. You can be less strict with your privacy settings to ensure you’re still discoverable by potential employers or clients.
For your personal profiles, on the other hand, you can use the strictest privacy settings each platform allows and ensure that only your closest friends and family can see what you post. This way, you can publish your family pictures and funny anecdotes without having to worry about colleagues, clients, or potential employers seeing too much. That said, it’s worth thinking carefully about what you post online as even things that are intended to be private can be leaked.
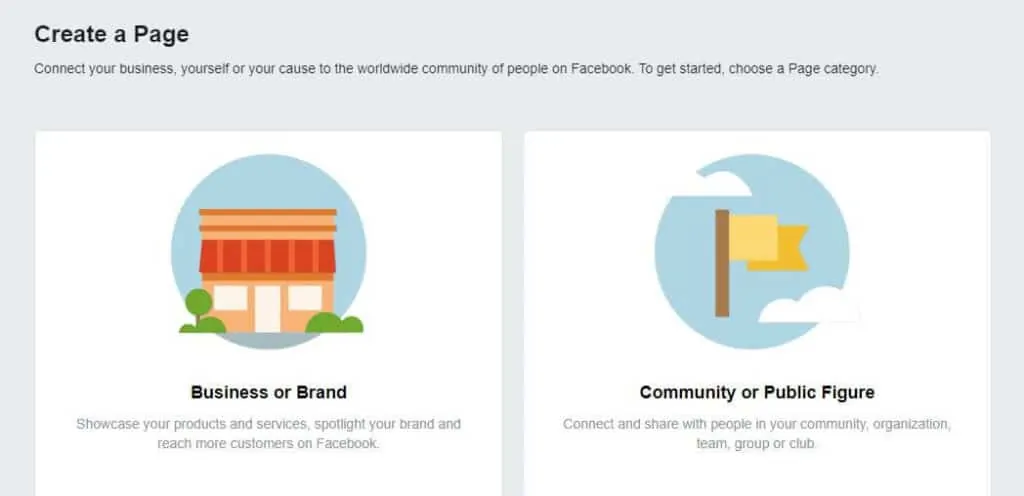
This doesn’t mean you need to have multiple profiles for all platforms. For example, LinkedIn is more suitable for business, so one professional profile makes sense. Instagram may be just for personal use, unless you’re a business owner, in which case you’ll likely want a professional presence there too. Facebook is a bit tougher as you should technically only have one profile. One way around this is to create a Page instead of a Profile for your professional persona.
2. Provide minimal or even false information
Social media platforms will invite you to input a ton of personal information when you’re setting up an account. But you should question how much of this you need to provide. Unless you’re a business, there’s no need to offer up a phone number or postal code, and you should try to ensure that your email address is not made public. Unless you love an onslaught of birthday wishes from random acquaintances, providing your birth date is rarely necessary.
If information is required to create an account, you could provide false information, for example, a different birthdate and different version of your name.
Do you like to complete surveys and quizzes? Be extremely wary of what information you might be giving up. For example, some surveys doing the rounds on Facebook ask you to post personal information on your status. Things like your first pet’s name, your mother’s maiden name, and other seemingly harmless tidbits are often used as security questions to get into various accounts.
Even if they’re private quizzes that you don’t share publicly, they could be dangerous from a privacy standpoint. At the least, the survey provider can learn your IP address, location, operating system, device type, and the websites you visit before and after visiting the survey site.
Depending on what information you provide or is made public by others (for example, information associated with your IP address), they could also learn more personal details, including your name, address, email address, phone number, as well as information about your education, income, and health. In fact, the answers people input into health surveys can even impact their ability to qualify for medical insurance.
3. Tighten your privacy settings
We discussed above having separate personal and professional accounts and potentially using different privacy settings for each. Thankfully, most social media networks are improving their privacy options. That said, you still need to be vigilant about adjusting your settings, as the default options are often very lax.
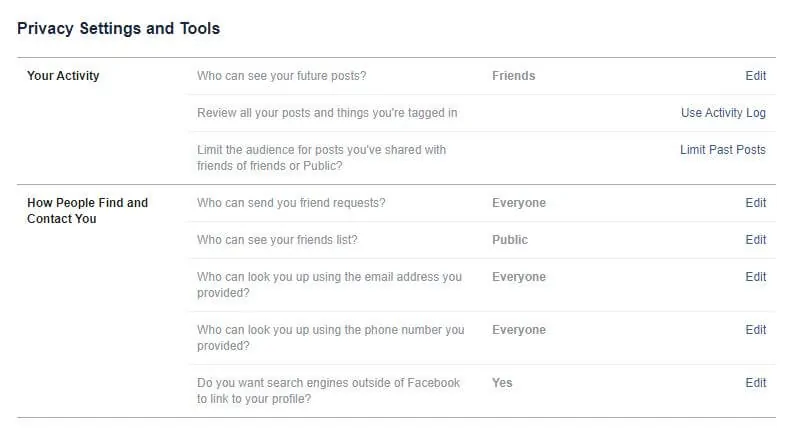
Take Facebook as an example. When you first set up a Facebook account, by default, anyone can see your friends list, and any other Facebook user can send you a friend request. In addition, people can look you up based on your email address or phone number, and search engines such as Google and Bing can link to your profile.
Thankfully, it’s quite straightforward to go in and change all of these options to levels you’re comfortable with. That said, for some platforms, you may need to visit multiple sections or tabs to make all the adjustments you need.
Bear in mind that privacy options are subject to change and you may miss an email informing you of these adjustments. It’s prudent to check your privacy settings regularly to ensure you’re not inadvertently sharing more than you would like.
4. Don’t share your location
One problem that affects even the most privacy-conscious user is that we’re not always aware of what we’re sharing. Take geotagged photos. The photos we post are often published alongside metadata that tells the viewer exactly where and when the image was taken.
This can help a snooper determine where you live, work, go to school, shop, or dine, and where you tend to be at a given time. It could even help a stalker track you in real-time and lead to online harassment being taken offline.
“Checking in” to places like bars and restaurants on Facebook or adding a location to your Tweets can have similar implications. Also, think carefully before RSVPing publicly to an event that’s being promoted on social media. This can tell a snooper in advance where you’re going to be.
5. Report abuse to the platform
If you’re experiencing any issues of inappropriate or criminal behavior on social media, most platforms including Instagram, Twitter, Facebook, LinkedIn, and TikTok offer avenues for reporting such instances.
Although, it’s worth noting that there have been many complaints of problems not being dealt with in a timely manner (or at all) on most platforms. So, unfortunately, we can’t assume that anything will be done.
6. Block or restrict users
Since reporting isn’t always effective, you may want to block the offending person completely. Again, many social media platforms allow you to do this. There is usually an option to block a user in a dropdown menu on their profile. You may be asked for a reason, but you’re not required to provide one.
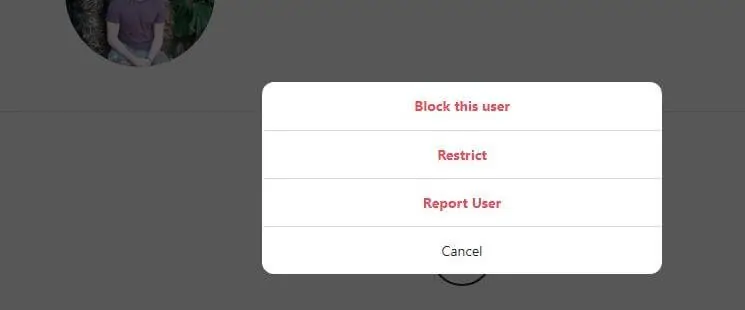
You may find yourself in a situation where you want to block a user, but don’t feel comfortable doing so. For instance, you might be trying to avoid antagonizing an ex-partner or dealing with a sensitive situation with a colleague. In these cases, you may be able to take advantage of some platforms’ settings that enable you to restrict access to your account by some users.
For example, users you choose to restrict on Instagram can’t see if you’re online or whether or not you’ve read their messages. In addition, you won’t receive notifications about comments from that person and their comments on your posts are only visible to you and others if you choose so. Facebook’s restricted lists work a little differently — anyone you add to your list will only be able to see your public information and any post you’ve tagged them in.
7. Look out for doxing
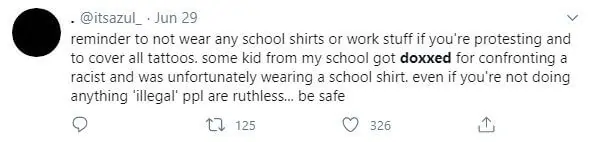
As discussed earlier, doxing involves the unauthorized publication of personal information and can be used as a means of online harassment, including cyberbullying, cyberstalking, or sextortion. Doxing is often targeted towards people suspected of crimes or involved in political activism — even attending a protest or rally can make you a target — but it’s by no means limited to these cases.
Of course, it’s difficult to stay informed about whether some of your personal information is doing the rounds online. Perpetrators often take steps to cover their tracks and may go to great lengths to ensure the victim doesn’t find out the information has been leaked at all.
Many doxing victims will find out by being alerted by family members or friends who have seen the publicized information, images, or videos. If you do have any inkling this may be happening to you, some quick searches should help to uncover what, if anything, has been revealed.
If you discover you are being doxed, the best course of action is to contact the platform on which the information has been posted so that it may be removed. Depending on the nature of the doxing, it could be considered a crime, and if so, should be reported to law enforcement.
One common form of doxing on social media involves the creation of a fake account. The perpetrator may pose as their victim for a number of reasons, for example, to shame or embarrass them, or incite hatred. Common tactics include posting explicit images or sharing hate speech. If you spot a fake account (posing as you or someone else) it should be reported to the relevant platform.
How to stay safe on dating sites
Romance scams prey on people who are hoping to find love or companionship. In the US, romance scams account for larger financial losses than any other internet crime. In 2018, the median reported loss to a romance scam was $2,600, which was seven times higher than for other online frauds. And in 2019, victims lost over $200 million to romance scams.

While anyone can be targeted in these schemes, data from a UK study found that 63 percent of victims of romance scams are females. What’s more, the same study found that women lose twice as much money in these schemes as men.
Romance scams generally follow a similar pattern, whereby a fake suitor will show interest in their victim and hook them into believing they are in a serious relationship. Once the stage has been set, the scammer might start asking for money, explicit images or videos, or help with illegal activities.
We provide tips below for using dating sites safely, but bear in mind romance scams aren’t limited to these platforms. It’s common for people to find love on social media so scammers hang out there too, hoping to find their next victim. As such, it’s also important to follow the above advice about staying safe on social media.
It’s also worth noting that scams aren’t the only risks posed by online dating. These platforms are also home to predators who could become emotionally or physically abusive either while communicating online or once you meet up in person.
Here’s how to stay safe when using online dating sites:
1. Do your homework
These days, with so much information available online, it can be quite simple to do a bit of digging around a potential suitor. If you find yourself getting acquainted with someone you met online (or offline for that matter), it’s a good idea to do some research.
Social media is often a good place to start, but you can use other sources to find out if they really are who they say they are. For example, checking a site like LinkedIn can help you compare images and confirm a place of employment and education. Just bear in mind that a scammer could have set up multiple social media profiles to corroborate their fake identity. So you may need to look closely to see if everything seems legitimate.
A common trick used by catfishers is to steal someone else’s images. You can use image search tools like Google image search and TinEye to check that an image hasn’t been used elsewhere. Sites like Scamdigger and Romance Scam post profile images and names that are used frequently by scammers, so it’s worth checking those too. There are even some Facebook groups that post information about scams that are doing the rounds.
You can also check BeenVerified, Whitepages, Spokeo, TruthFinder, and other public records databases. Some dating site users have even been known to hire a private detective to ensure they’re not being duped.
Granted, none of this sounds very romantic, but doing some digging can save you a lot of heartache. The saying that love is blind can be true and falling hard for someone can really cloud your judgment. As such, it’s best to do your research early on in a relationship, well before you become emotionally committed.
2. Don’t include personal information on your profile
While you want to be as genuine as possible when using dating sites, there’s no need to give away a ton of information. You can keep your profile as limited as possible and even use a different version of your real name.
Be generic with information such as likes and dislikes and try not to give away information about your precise address. Use a separate email address, one that doesn’t include your real name.
3. Don’t leave the dating app
Dating apps are improving in terms of promoting online privacy and safety. But to reap these benefits, you need to stay on the app. This can be tough as cybercriminals will often try to quickly earn your trust and suggest that you move to a different platform. They realize that dating sites closely monitor for scams, so the incentive is there to move to a more private forum, such as a social media site.
On that note, you shouldn’t add a potential love interest on social media until you really trust them. As discussed above, social media apps can provide them with a ton of information about you. This can be used to increase their chances of successfully scamming you.
4. Look out for red flags
There are often telltale signs that someone isn’t legitimate, but other red flags can be more subtle. Here are a few things to look out for:
Requests for money
These often have a sense of urgency, for example, to help with a medical or legal matter. As a simple rule, you should never give money to someone you meet online. Note that probing questions will often be met with accusations of paranoia, a common reverse psychology tactic used to gain your trust.
Coming on strongly
Known as love bombing, scammers will often bombard would-be victims with passionate texts and phone calls, and even send marriage requests within a very short timeframe.
Asking to carry out suspicious activities
If someone asks you to accept or deliver a package on their behalf, this should be a huge red flag that they are asking you to participate in something illegal.
Canceling video calls or in-person meetings
Obviously someone who isn’t who they say they are will avoid a face-to-face video call or in-person meeting. Scammers will often use outlandish excuses to dodge a call or cancel a meeting.
Poor English
While this doesn’t apply to every situation, you may question why someone who claims to have a college education or military training in a predominantly English-speaking country doesn’t have a good grasp of the English language.
A change in tone or grammar
Fraudsters often work in teams, so a change in the type of language they use could be a signal that multiple people are behind the profile. Also, watch out for the way they use emoticons and any inconsistencies or repetition in stories.
Requests for sexually explicit images or videos
While this is becoming more acceptable on dating platforms, it’s a common tactic for scammers to push to obtain images and videos they can use for leverage later.
Claiming to work and live in various locations
This guise is often used to cover the fact they are calling from different places, may be difficult to contact at times, or don’t know the answers to basic questions about where they are. Some job titles that work well for scammers include military personnel, oil workers, or engineers. These provide good cover as to why they move around a lot or are difficult to contact or meet up with.
An open profile
If someone’s profile indicates that someone isn’t picky about the age or location of their potential love interest, then they may just be open-minded. On the other hand, they could be a romance scammer casting their net as wide as possible.
5. Use a unique photo
Just as you can do an image search using photos of your potential matches, a scammer can do the same for you. If you use the same image across sites, this can help people find your social media profiles easily.
Ideally, you should use a different image for all of your dating and social profiles, but at the very least use a different image for dating sites than you do for social media.
Note that using a unique photo can deter some snoopers, but it may not be an entirely reliable solution. A 2011 study run by Carnegie Mellon University found that facial recognition technology could be used to identify people in dating site profile images. While there are calls for bans on facial recognition due to privacy concerns, the technology is still in use and could fall into the wrong hands.
6. Be extremely cautious about sending intimate photos
Sending intimate images and videos or other forms of “sexting” is becoming far more common. For many people, it has simply become part of the online dating process. But the fact that “everyone is doing it” doesn’t make it any safer. If images fall into the wrong hands, they can be used in any number of ways against you, for example, in sextortion or revenge porn.
This isn’t to say you shouldn’t partake in the practice of sending intimate images at all. Just be very cautious. Here are some tips:
- Only send intimate images and videos to someone you completely trust.
- Make sure your face or other identifying features such as a tattoo are not visible in the photos. Note that blurring out these features is a good idea, but it may not be effective — this type of editing can often be reversed to some extent with the right tools.
- Ensure that any other identifying information is not visible in the picture or video, for example, a photo on the wall in the background or an envelope with an address on it.
- Consider using apps designed to minimize your exposure. One example is Drunk Locker which locks your apps so you can’t sext when drunk or high. You could also use apps like Diskreet and SnapChat that delete photos from the recipient’s phone after a certain period of time. Although, it’s worth noting that the recipient can still take screenshots.
- Save your photos securely using an app like Gallery Lock. This will save your selected photos in a hidden password-protected folder. Storing photos on your PC? Tools like VeraCrypt will encrypt your files so that even someone with access to your device won’t be able to view them.
7. Report and block suspicious profiles
Dating sites clearly don’t want scammers and predators using their platforms. It’s quite simply bad for business. Most have very clear avenues for reporting suspicious profiles. For example, Match.com provides clear guidelines on when and how to report inappropriate behavior.
As with social media platforms, you can also adjust your privacy settings and block other users who make you feel uncomfortable. As long as they’re not able to find you on other platforms (which they shouldn’t be if you follow the above precautions), then you never have to hear from them again.
8. Take precautions if meeting someone
If you do decide to go ahead and meet someone who you’ve met on a dating site in person, it’s important to avoid putting yourself in a dangerous situation. Here are some things to consider:
- Always meet in a crowded place. If your date tries to change the location at the last minute, it’s better to cancel and reschedule.
- Let someone know where you’re going and ask them to check in with you during the date. Better yet, have them stay close by during the first date.
- If you feel uncomfortable at any point, leave. Have an excuse ready such as an early morning.
- Use apps that enable your friends or family members to keep tabs on your location such as Life360 or Kitestring, or an SOS app like Siren GPS that will help you quickly call emergency services.
9. Report fraud or other criminal activity
If you believe that a crime has taken place, be sure to report it to your local police department. We also have a dedicated post explaining how to report various types of fraud depending on where you are in the world.
How do deal with online harassment at work
We hear about harassment in the workplace all the time, but it’s only the most extreme cases that make the news or gossip circle. The reality is that harassment takes place at work more frequently than many of us might think. Most cases remain private and are even “swept under the rug” to save company image.
Plus, many instances of harassment are never reported, often because victims fear the repercussions, feel ashamed, or because it happens so subtly that they don’t know if it constitutes harassment or if they should report it.
The majority of women (60 percent) have experienced “unwanted sexual attention, sexual coercion, sexually crude conduct, or sexist comments” in their place of work. However, 75 percent of employees who experience harassment never complain about it to their employers, and 90 percent don’t file a formal complaint.
Online harassment at work can take various forms and may be combined with offline harassment. Here are a few examples:
- Sharing images or videos of a sexual nature
- Sending messages or emails that contain suggestive content
- Making comments or telling jokes or stories that are explicitly sexual in nature or have a sexual undertone
- Badgering for a date
- Requests for sexual favors in exchange for benefits such as a promotion
- Using sex-specific derogatory language
Of course, it’s not just co-workers who harass women in the workplace. Clients, customers, and other industry connections could all be involved too. Self-employed women are often targets of harassment as well.
Here are our top tips for anyone dealing with harassment in the workplace:
1. Keep a record of all online and offline interactions
One of the problems with harassment at work is it’s difficult to know what types of interactions you should report and how to report them.
A good rule of thumb is that if any interaction makes you feel uncomfortable, it constitutes harassment. That said, harassment can be very subtle, and you may find yourself questioning whether the underlying tone was intended as you perceived it. It’s common that people don’t want to report a single instance, especially if they’re not sure of their perception of the situation.
Some companies will draft a sexual harassment policy, which makes it easier to categorize what’s happening, although things are rarely black and white.
Regardless of whether you want to report it right away or not, you should make a record of the interaction. This way, if you decide to report, you will have evidence. If the instance occurred online or via text message, take screenshots and save any pertinent information in a folder. Just be sure to save it somewhere that only you have access to, that is, not in a shared folder or on a shared online system like Google Drive.
If the interaction takes place in person, this can be more difficult to prove, but you can still keep a record. Immediately after the interaction takes place, make a note of what happened, exactly where and when it occurred, and whether there were any witnesses. You can send the information to yourself in an email so that you get an official time and date stamp on the record.
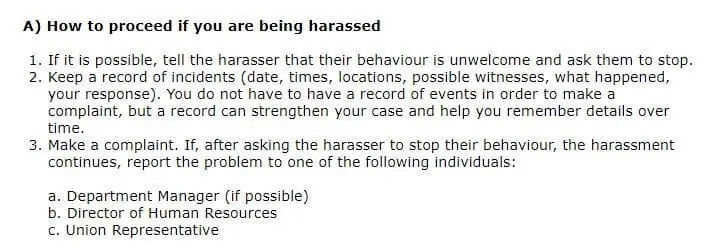
2. Report the harassment internally
If the harassment is taking place within a company where you are an employee, you can report it to the relevant personnel within the company. Companies that have a sexual harassment policy will often have some sort of complaints procedure to follow.
The appropriate place to report harassment is usually the Human Resources (HR) department, although many companies do not have one. In this case, you’ll need to report it to your manager or another senior employee. If you’re a unionized employee, it may be appropriate to make your complaint to a union representative.
Reporting harassment can feel uncomfortable, but it may be the most productive way forward. In many cases, there are repeat offenders and your coming forward could corroborate someone else’s claims.
3. Report elsewhere if applicable
What if the harassment is coming from someone outside of the company such as a client? In this case, you should still inform HR or other appropriate personnel in your own company. It may be tempting to take matters into your own hands, for example, by going directly to the offender’s superiors at another company. But having no internal report of the matter could cause issues within your own company.
Again, the perpetrator could be a repeat offender, and letting your company know provides an opportunity to find out if anyone else has been impacted by their behavior. Of course, if your own company refuses to support you and take action against the offender, then reporting to their superiors is a reasonable course of action.
If you’re self-employed and have no one to report the harassment to, then you have no choice but to deal with the matter as you best see fit. It’s still important to keep records of the harassment so you can report the offender to their own company and file a complaint with your local police if you deem a crime has been committed.
4. Report abuse on LinkedIn
We briefly discussed LinkedIn in the social media section above but it’s worth delving into this platform a bit deeper here as it pertains to sexual harassment in the workplace.
As Vice’s Jessica Phillips writes:
It should go without saying that women shouldn’t have to self-censor their professional portfolios to prevent voyeurism or unwanted come-ons.
However, sexual harassment targeted at women via private messages on LinkedIn is a problem the company is well aware of and trying to fix.
One of the issues with LinkedIn is the nature of the platform goes against the values of the more privacy-conscious among us. Because it’s a professional networking site versus a social networking site, people tend to be more open to connecting with people they don’t already know, as it may help their career. The nature of the platform means it makes sense to have public profiles so that people can find you for networking or job opportunities.
Another unique thing about LinkedIn compared to other social networking sites is that it pays to share more information. You want to broadcast everything you’ve achieved in terms of education and career and reveal exactly who you’re working for and where you’re located. Plus, the information needs to be accurate; with your LinkedIn profile serving as your resume, it’s not the appropriate place for misinformation.
Sexual harassment on LinkedIn often occurs under the guise of job opportunities. This is particularly concerning for freelancers, many of whom are continuously corresponding with potential clients looking for new work. One example was a writer who was having a conversation about a job prospect with a Seattle Times reporter. After the conversation escalated to the line “there is so much cum on your face,” the writer complained and the reporter was suspended.
If you experience harassment on the platform, we recommend reporting to LinkedIn (and any other appropriate parties) immediately and blocking the offender.
Dealing with stalkers or abusive partners
Although it may not seem as serious, cyberstalking can impact victims as much as online stalking does. Indeed, the psychological profiles of online stalkers have been found to closely match the profiles of offline stalkers. That said, there are some different trends, including the fact that cyberstalkers are less likely to physically approach their victim (although many use offline tactics) and are more likely to be an ex-partner.
Cyberstalking can seriously impact women emotionally and sometimes physically. And if the stalker is careful about covering their tracks, it can be difficult to prove. Cyberstalkers usually make contact with their victim, for example, via email, text, or social media, but this isn’t always the case.
Here are some steps you can take if you’re concerned about cyberstalking:
1. Research yourself
One of the most effective things you can do to protect your privacy online is to put yourself in the position of a potential stalker. If you wanted to find out about yourself, what information is available?
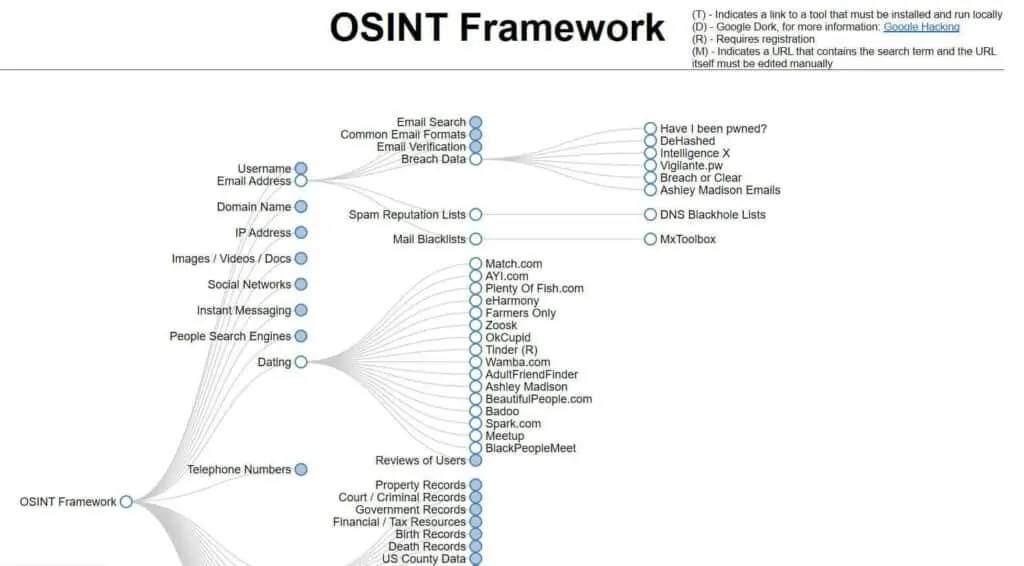
Search engines like Google or Bing are a good place to start, but bear in mind there are many more resources available to conduct people research. For example, the OSINT (Open-Source Intelligence) framework provides a blueprint for this very task. It maps out all the places you can discover information about people online, including social networking sites, people search engines, and vehicle records.
The OSINT framework has many positive uses, such as helping police learn more about potential suspects, or assisting in missing person cases. However, it can also be used by stalkers and other cybercriminals to discover a trove of information.
If stalkers are using this, then it makes sense for you to do the same. You can use the framework to find out what information is available about you online. You can then take the necessary steps to remove this information where possible. This can be a tedious task, so you may want to consider using a service like DeleteMe or PrivacyDuck that can have the information removed on your behalf.
After all this effort, it goes without saying that you should avoid posting any new personal information online. This is especially true of anything that discloses realtime information such as your location or who you’re with.
2. Inform friends that you are being stalked
A common tactic used by online stalkers involves infiltrating your friends to find out more information about you. They may do this under the guise of a fellow friend or could even pose as you. Stalkers may also threaten to share information, images, or videos with your friends and family.
You should let people close to you know that you’re experiencing issues with an online stalker so they can be on the lookout for any suspicious communication. This way, they can tell you right away if the stalker does contact them, and they’ll know not to share information with anyone who requests it.
3. Don’t accept a request from someone you don’t know
This may seem obvious, but people get curious. Once you accept a social media friend or connection request from someone, depending on your settings, they may have access to a whole bunch of information about you.
The problem is that not everyone is who they say they are, and that friend request could be from a cybercriminal posing as someone else entirely.
4. Look out for suspicious emails and text messages
Social media isn’t the only avenue people use to stalk you. Emails and text messages may be used too. A couple of scenarios to be aware of are:
- A fraudster posing as a person or company you’re familiar with and sending emails or text messages to phish for information such as personal details or credentials to various accounts.
- A snooper sending an email or text message that contains spyware. This type of malware can work in various ways, for example, it could be used to steal images from your computer, record videos using your webcam, or find out passwords to enable the sender to hack into your various accounts.
If you have any suspicions about the origin of a text message or email, it’s important not to click on any links or attachments. Attachments are often hidden malware and links might send you pages that look like legitimate websites but are designed to steal your information (phishing sites). Note that you can check the URL a link will send you to by hovering your cursor above the link.
5. Scan your device for spy apps
Concerned that there is already malware on your device? If so, then your antivirus software hasn’t picked it up. But there are other tools you can use to check. Here are a few top-rated free malware removal tools that will scan your system and remove spyware:
Note that many spy apps are legitimate in which case they won’t be picked up by antivirus software or malware removal tools. As such, it’s a good idea to regularly review the apps installed on your device, especially those that have access to your microphone, camera, and location.
To avoid having spyware installed on your device in the first place, make sure it is always on you and never left anywhere someone else has access to it.
6. Cover your webcam
Unfortunately, there have been a large number of reported cases of webcam hacks. One prominent instance was the case of Luis Mijangos who pleaded guilty in a sextortion case involving hundreds of women. Mijangos hacked his victims’ computers (using malware that they unknowingly downloaded) and recorded intimate videos of his targets.
This sheds light on the unfortunate reality that even if you think your webcam is switched off, someone could still be using it to secretly record you. To avoid becoming a victim of revenge porn or sextortion as a result of webcam hacking, a simple trick is to always keep your camera covered when you’re not using it.
Many laptops now come with slide covers for built-in webcams. You can also purchase a cover separately or simply cover the camera with a piece of opaque tape. If you use a standalone webcam that doesn’t have a cover, you can turn it towards a wall or object when not in use.
7. Beware of deepfakes
While webcam hacking is a concern, cybercriminals now have the technology to skip this step altogether and simply create fake videos of their targets. The term “deepfakes” is derived from “deep learning” and “fakes.” Deepfake technology uses advanced machine learning to create extremely realistic-looking videos and images.
Deepfakes have the potential to wreak social and political havoc by making it look like someone has said or done something they haven’t. Some viral examples include a video of President Obama dissing President Trump and one of Mark Zukerburg explaining the “true” motivations behind Facebook. Unsurprisingly, one of the most common uses for deepfakes is non-consensual pornography, with many celebrities being featured in fake videos.
But it’s not only politicians and celebrities who can be targeted by deepfake creators. The technology is rapidly becoming more advanced and accessible. As such, it could be relatively straightforward for cybercriminals to use deepfakes featuring their victims in sextortion or revenge porn attacks.
While there isn’t a lot you can do to prevent deepfakes being made, there are laws in the works in some regions that will ban the creation of deepfakes. This will hopefully stem the accessibility and spread of this technology. One slightly positive aspect of all this is that the existence of deepfakes calls into question the validity of real videos. This could provide a cover for anyone dealing with the exposure of real sensitive videos who could claim that these are in fact fakes.
8. Change your home wifi password
If you share a home network with others, there’s a chance that someone with enough tech-savvy could snoop on your internet traffic. This applies to anyone who has access to your home network, not just those inside your home. For example, an ex-partner or a roommate’s friend who has used your wifi in the past could sit within range and snoop on your internet activity. If you’ve never changed your password from the default, this opens up your home network to attacks from strangers too.
If you’re at all concerned about someone intercepting your traffic, you should use a VPN to encrypt your data and make it unreadable. Note that you can even configure a VPN to your home router to ensure that all of the internet-connected devices in your home are protected.
Other steps you can take to secure your home router include installing updates, setting the encryption level to WPA2 or WPA3 (the highest level), and switching off Wi-Fi Protected Setup (WPS).
Additional steps to protect your online privacy
We’ve covered a lot of advice in the above sections, but there are still a few more things you can do to lock down your digital privacy and ensure you stay as safe as possible online.
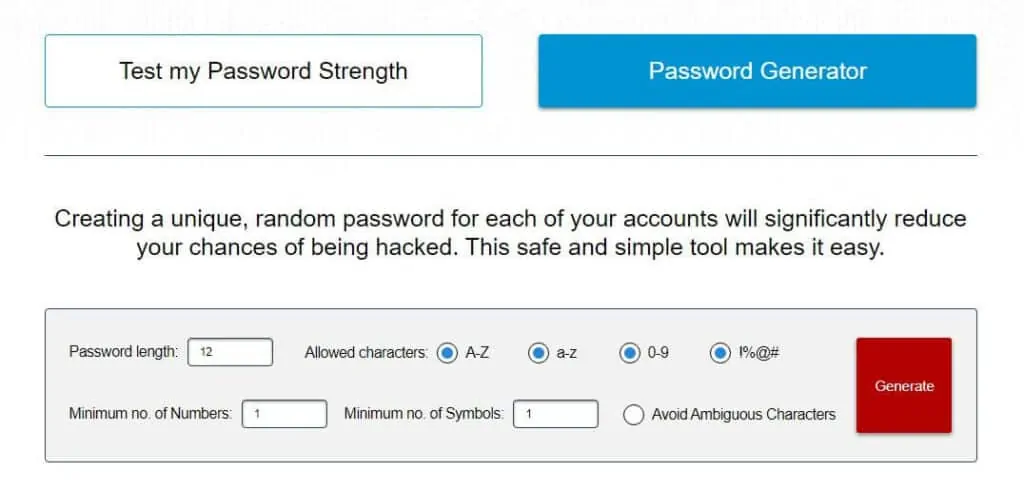
1. Use strong passwords
If your passwords are easy to guess, then you’re a prime target for account takeover fraud. It also makes it very easy for someone targeting you to peek inside your email and social media accounts and harvest information about you.
Using the same password across multiple accounts is a bad idea too, even if it’s a strong password. Data breaches occur every day and there are huge lists of username and password combinations available online. Criminals use a tactic known as credential stuffing whereby they take these username/password combinations and use them to hack into accounts on various popular platforms.
If you’re having trouble coming up with passwords, our password generator can help.
Worried about remembering them all? Password managers like LastPass, NordPass, and Dashlane are great for storing and autofilling your passwords.
2. Use two-factor authentication
One way to avoid having your accounts hacked is to use Two-Factor Authentication (2FA) or Two-Step Verification (2SV). When enabled, these features add an additional step to the login process. Once you’ve entered your username and password, you will still need to complete a second action to gain access to your account. This could be something like entering a code sent via email or text or using a biometric verification method such as a fingerprint scan.
An increasing number of platforms offer 2FA, but you’ll often have to go into your security settings to enable it.
3. Use a VPN
Virtual Private Networks (VPNs) are very handy tools for protecting your internet traffic from snoopers. A VPN is especially useful if you tend to connect to public wifi frequently. Public networks are typically unsecured and offer opportunities for hackers to intercept wifi users’ internet traffic.
A VPN encrypts your traffic so that it’s unreadable to anyone who intercepts it. We recommend ExpressVPN as it’s highly secure and very fast, but NordVPN and Surfshark are excellent alternatives. You can see more options in our list of best VPNs.
4. Install updates regularly
Updates are a key factor in keeping you safe online. They often contain patches that fix security holes. If you delay updating, you open the door for cybercriminals to take advantage of vulnerabilities in your operating system or application.
Installing an update can seem like a nuisance, especially if it’s a large one that seems to take forever. But most devices enable you to adjust update settings so that they occur automatically at a time that is most convenient to you.
5. Use a firewall and antivirus software
We discussed spyware above, but there are lots of different types of malware out there that cause harm. These can range from viruses that make your computer difficult to use to ransomware that holds your files hostage until you pay a fee. While the impact of malware varies greatly, it’s never a good thing to find it on your system.
One of the first lines of defense against malware is a firewall. This can help stop malware from entering your system by rejecting certain traffic based on security parameters.
In case malicious traffic does get through, a good antivirus software can help. This will prevent software that is known to be malicious from installing on your device. Most antivirus software will also scan your device for existing malware and may be able to help you remove it. Some popular options include offerings from Bitdefender, Norton, and Kaspersky.
7. Consider using encrypted email
We hear a lot about encryption when it comes to messenger apps. Most popular services like WhatsApp and Facebook Messenger give you the option to encrypt your communications. But things are different when it comes to email — mainstream providers don’t provide an encryption option.
This means that if anyone intercepts your emails, the content is fully readable to that person. Encrypting emails is possible, but it requires some tech-savvy. However, there are some providers out there that offer encrypted email services. You’ll have to pay for them, but it might be worth it for peace of mind. Some popular options are Hushmail and Tutanota.
8. Try using the Tor browser
The Tor browser is an anonymity tool that encrypts your internet traffic and sends it through multiple nodes (run by volunteers). Using this tool makes it very difficult for anyone to track you. While the Tor browser has a bad reputation — it’s often used by criminals to conduct illegal activity — it does have its positive uses, including as a safe haven for victims of cyberstalking and other forms of abuse.
Note that Tor will drastically slow your internet connection so it can be impractical, but if you’re after anonymity, it may be worth the trade-off.
9. Secure your IoT devices
An increasing number of devices in our homes are connected to the internet. The list now goes beyond PCs, phones, tablets, and accessories, and extends to things like home assistants and security systems. All of these pose a risk to your privacy when they send or receive information that could expose details about you or your day-to-day life.
Some devices are more dangerous than others. For example, security cameras — like webcams — can be hacked to allow criminals to spy on you and other members of your household. There have even been reports of criminals hacking cameras and communicating verbally with children in their homes.
To protect IoT devices, ensure you install updates regularly. Change all of the default passwords and consider creating new wake words for home assistants. You should also avoid storing any personal information on these devices. Bear in mind that some home assistants are always listening. You may want to turn them off when not in use, or if this is impractical, avoid disclosing sensitive information within “earshot” of your device.
10. Take precautions if you lose your device
With so many people owning smartphones these days, we’re essentially all walking around with mini-computers in our pockets. Aside from enabling us to make phone calls, our phones provide us with access to all of our accounts, including email, social media, eCommerce, banking, and lots more. They also hold thousands of images and videos; even if they’re not of a sensitive nature, you probably don’t want a stranger going through them.
Ideally, you should take precautions in case you lose your device or find it has been stolen. These include installing a finder app such as iOS’s Find My iPhone or Android’s Find My Device, making note of your device’s serial number, and setting up automatic backups.
So what if the dreaded happens: your device is gone and you’re unable to find it using the finder app? We cover this topic in-depth in What to do if your phone is stolen, but here are some tips:
- File a police report, even if you think there’s little chance of getting your device back. It may be necessary for insurance purposes and in some countries, reporting to police will add your device to a blacklist so it won’t work with any networks.
- Lock your phone remotely. The finder apps mentioned above give you the ability to do this. They will usually let you remotely erase your device too, if this will give you more peace of mind.
- Call your provider to suspend your service so that no one is able to rack up charges on your behalf.
- Change the passwords for any accounts associated with your phone. If a thief is able to unlock your phone, they will have access to any accounts that you’re automatically logged into on your phone. They may be able to change the password on those accounts. It’s worth bearing in mind that two-factor authentication or two-step verification may not be of help here if the second step involves a text message or email, both of which they will have access to on your phone.
- Contact your bank to find out if there is any recent activity on your credit cards. Also, monitor all accounts (especially financial, social media, and ecommerce) over the coming weeks and months to check for any suspicious activity.
11. Discuss issues with others
Finally, to help ensure we all stay as safe as possible, it’s important to talk about online harassment. Many of us spend a good chunk of our time using the internet for work, entertainment, socializing, and more, so it makes sense to talk about online activity as much as we would other aspects of our lives.
Discuss online privacy and security with friends, family members, and co-workers. Be especially diligent about educating seniors and children about online safety.