Hackers claim to have stolen 700,000 guest records belonging to Choice Hotels, one of the largest hotel chains in the world. Comparitech collaborated with security researcher Bob Diachenko to uncover the unsecured database, which was left exposed and accessible to anyone with an internet connection.
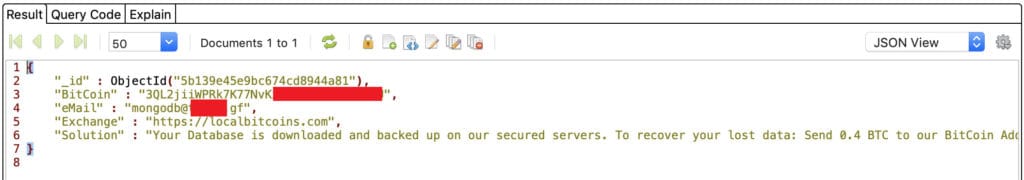
Diachenko immediately notified the company of the exposed MongoDB instance, but it appears malicious actors got to it first. They left a ransom note demanding 0.4 Bitcoin, or $3,856 as of time of writing.
The database held 5.6 million records. However, Choice Hotels told Comparitech in an email that the majority of records were “test data, not associated with real people.” About 700,000 of the records included details of actual guests including names, email addresses, and phone numbers.
The company says the data was hosted on a vendor’s server, and no Choice Hotels servers were accessed. “The vendor was working with the data as part of a proposal to provide a tool,” a company representative tells Comparitech.
Choice Hotels responded to Comparitech via email and included the following statement:
“We have discussed this matter with the vendor and will not be working with them in the future. We are evaluating other vendor relationships and working to put additional controls in place to prevent any future ccurrences of this nature. We are also establishing a Responsible Disclosure Program, and we welcome Mr. Diachenko’s assistance in helping us identify any gaps.”
The company is continuing its investigation as of time of writing.
Timeline of the breach
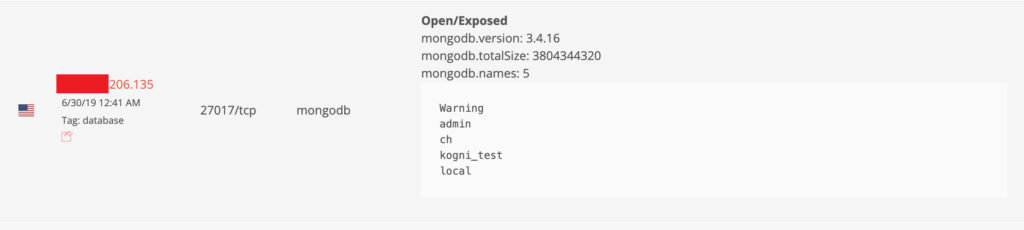
The MongoDB database was made publicly available with no password or other authentication required to access it. Here’s what happened:
- June 30: The exposed database was first indexed by search engine BinaryEdge.
- July 2: Security researcher Bob Diachenko discovered the database and immediately notified Choice Hotels about the exposure. It already contained the ransom note. Choice Hotels says it unintentionally filtered the email so that it was not read.
- July 2: Database access was secured.
- July 28: Diachenko sent a second notification and Choice Hotels began its investigation of the incident.
The database was left exposed for four days.
The ransom note left by hackers was already in place by the time Diachenko discovered the database. Diachenko hypothesizes that the note was left by an automated script targeting publicly accessible MongoDB databases. He surmises that the script intended to wipe the database after copying it, but failed.
Diachenko determined information in the 3.8 GB MongoDB database belonged to Choice Hotels based on the nature of the records, internal admin contact information containing the @choicehotels.com domain name, and the name of the exposed database: “ch”.
What information was exposed?
The unsecured server instance held multiple databases containing a wide range of information, totaling more than 5.6 million records. Choice Hotels says the majority of the database was comprised of test data, including any fields that reference payment card data, passwords, and reservation information.
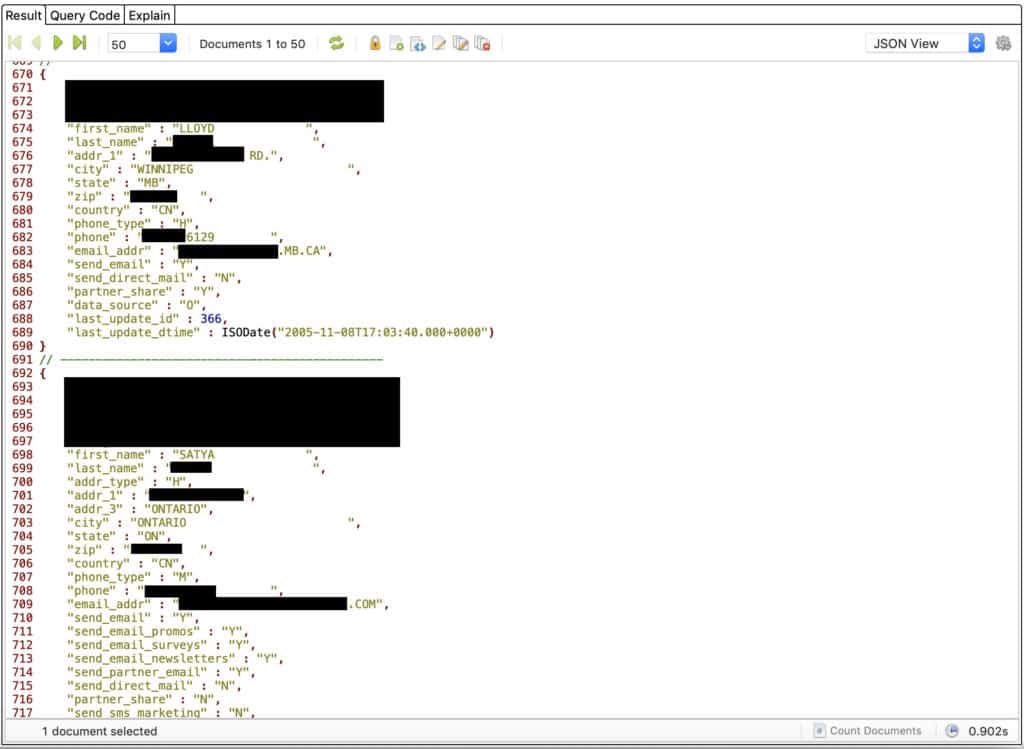
The MongoDB instance contained a table of 2.4 million records labelled “privacy log”, which Choice Hotels says contained the bulk of the 700,000 real customer records. They included a mix of:
- Full names
- Addresses
- Phone numbers
- Email addresses
- Consent statuses
Dangers of exposed data to users
Choice Hotels says any fields containing passwords, reservation details, and payment information only contained fake test data.
The biggest threat to Choice Hotels customers is phishing. Using the personal information contained in the exposed database, scammers can craft targeted phishing emails. These emails might impersonate Choice Hotels or a related company and ask users to hand over more sensitive information either through email or on a phishing site.
Scammers can address users by name and include detailed personal information to make the message more convincing. Aside from emails, scammers might also send phishing messages to users’ phones through SMS texts.
Choice Hotels customers should also be ready for an increase in targeted spam to their phones and email accounts.
Unprotected MongoDB databases can also be hijacked to spread malware or ransomware. Diachenko says cybercriminals could manage the whole system, infect it with malware, remotely access the server resources, and even execute code to steal or destroy data held on the server.
About Choice Hotels
Choice Hotels is a hospitality franchisor based in Maryland that owns a range of hotel brands including Comfort Inn, MainStay Suites, Econo Lodge, and Cambria Hotels, among others. The company has franchised some 7,000 properties in 41 countries.
In April 2012, Choice Hotels suffered a data incident that affected customers in California and New Hampshire. Sensitive customer information including credit card numbers, drivers license numbers, passport numbers, and Social Security numbers were improperly added to database fields. That data was passed to the company’s marketing partners, resulting in sensitive information being printed on marketing envelopes mailed to customers. That incident affected less than 0.001 percent of guest stays, according to the company.
How and why we discovered this breach
Comparitech’s security research team scans the web for misconfigured and vulnerable databases with the aim of alerting responsible organizations and making the internet a safer place for everyone.
Bob Diachenko uses his extensive cybersecurity knowledge and experience to track down and analyze data that’s been accidentally or purposefully exposed. When he finds a leak, he immediately takes steps to notify the organization responsible for the data so they can secure it.
Our investigation then continues and we learn about the nature of the data and to whom it pertains. We report our findings to raise awareness among affected consumers so they can take any necessary actions or precautions. We undertake this initiative to limit malicious access to personal information and mitigate harm if the data does fall into the wrong hands.
Previous reports
Comparitech and Diachenko teamed up to uncover multiple data leaks and breaches, including:
- 7 million records of K-12 students
- 188 million personal data records from people search sites
- 300,000 records belonging to cryptocurrency exchange QuickBit