File activity monitoring software tools use deep packet inspection to see how users are interacting with files throughout the network.
Controlling access to sensitive files should be a component of any complete cybersecurity strategy. Stopping unauthorized individuals from stealing confidential data is important for preventing sensitive information from being stolen.
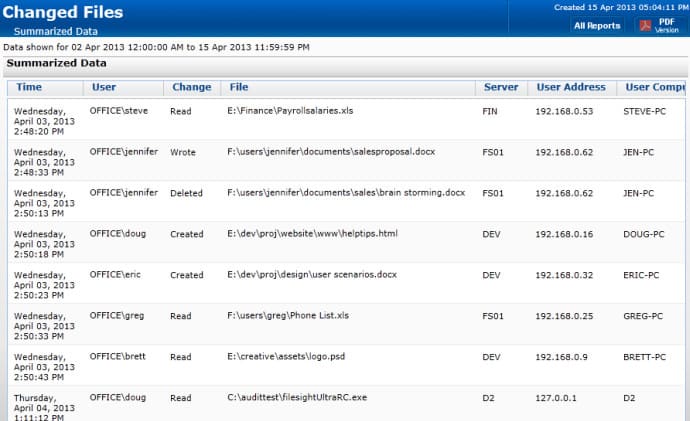
File monitoring software shows who accessed a file, when, and what they did.
Here is our list of the best file activity monitoring software tools:
- ManageEngine ADAudit Plus EDITOR’S CHOICE This package relates actions on a server to the user accounts in Active Directory, it implements user activity tracking for insider threat detection, and it protects AD objects from tampering. Available for Windows Server, AWS, and Azure. Start a 30-day free trial.
- SolarWinds Server & Application Monitor (FREE TRIAL) A server management tool that includes file tracking utilities. See real-time stats on individual files as well as drive metrics. Download the 30-day free trial.
- Site24x7 Infrastructure (FREE TRIAL) This cloud-based system monitor includes monitoring routines for all types of servers, including those used for storage. This includes services to add extra protection to stores of sensitive data. Start 30-day free trial.
- ManageEngine Endpoint DLP Plus (FREE TRIAL) This software package provides protection for files on multiple sites and tracks the users that access sensitive data. Runs on Windows Server. Start a 30-day free trial.
- ManageEngine DataSecurity Plus A file monitor that tracks file access and changes per user.
- Teramind A file activity monitor that records the users that access or modify any file on the system.
- PA File Sight A real-time file monitoring system that logs the source of any file-changing activity.
- FileAudit A real-time file monitoring system that includes alerts to key supervisors.
Related post: Best File Integrity Monitoring (FIM) Tools
The Best File Activity Monitoring Software Tools
Our methodology for selecting a file monitoring tool
We reviewed the file activity monitoring market and analyzed tools based on the following criteria:
- Logging of all file access events
- Registration of user account and the date of time of any access
- The ability to identify only certain files or directories for protection
- The option to set alerts on file changes
- A backup facility that automatically restores tampered files
- The ability to black file copies
- An option to try the service for free as an assessment
- A price set at a fair value for the quality of services offered
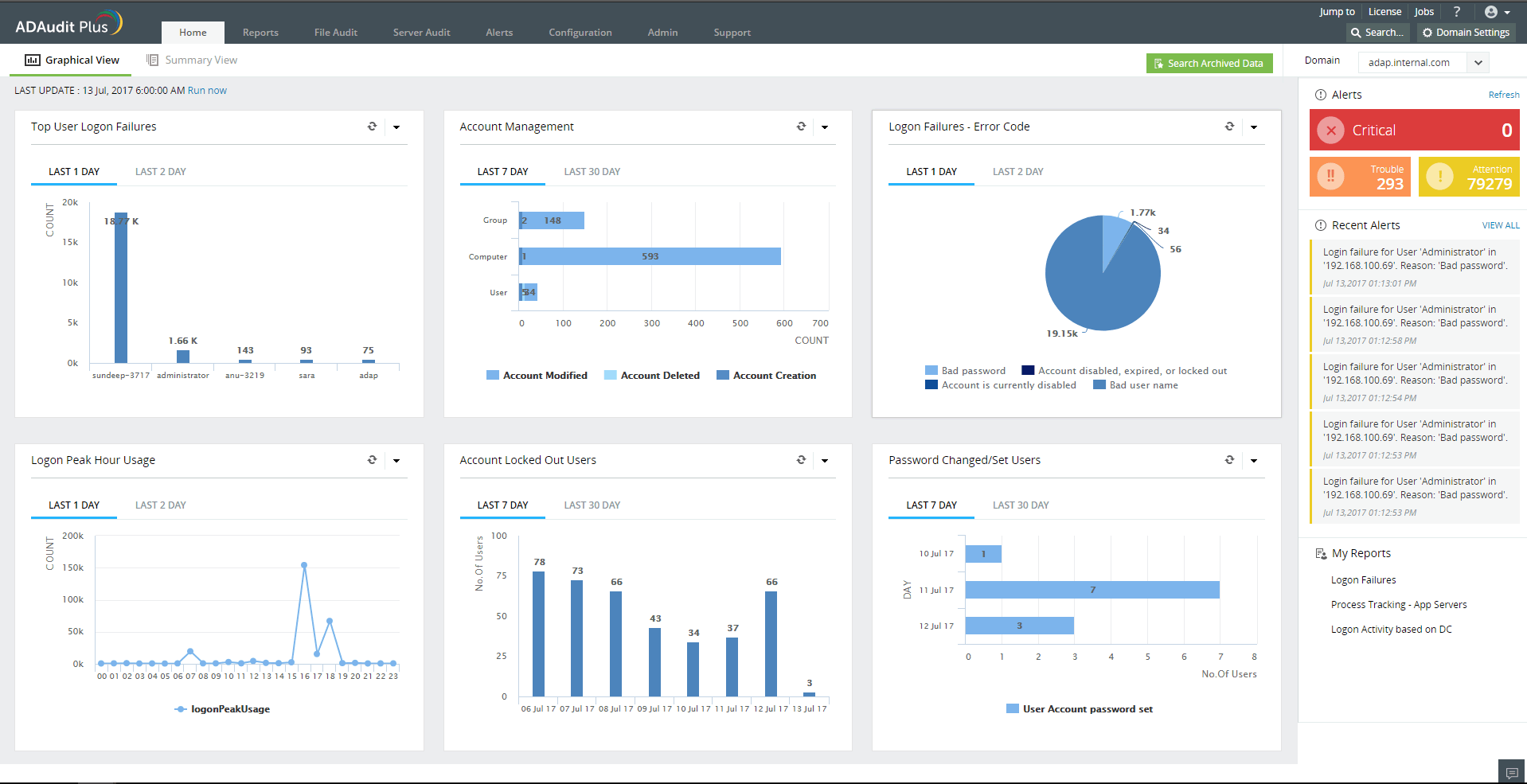
1. ManageEngine ADAudit Plus (FREE TRIAL)
ManageEngine ADAudit Plus is a tool for ensuring data integrity by tracking user activities on servers, particularly on files. While this system doesn’t include a sensitive data discovery and classification service, it will protect sensitive data along with all other files.
Key Features:
- User Behavior Analysis: Creates a baseline of regular activity per user
- Alerts on Unusual Activity: Sudden changes in behavior could indicate account takeover
- File Activity Monitoring: Records the user involved in a file access or content changes
Why do we recommend it?
ManageEngine ADAudit Plus is a package of activity recording services. The name implies that the system operates on Active Directory. However, this is misleading because the tool lays down user activity records, referencing AD for user identities. This is a file activity monitoring tool that can be used for data loss prevention.
ADAudit Plus is available for AWS and Azure as well as for Windows Server. Each deployment will scan Active Directory and note its current status. If changes are made to objects in that system, the ADAudit Plus service raises an alert, which enables you to reverse those changes, which might include the addition of user accounts.
The file integrity monitor ties in with Active Directory. Thus, when a user accesses a file, the ManageEngine service logs that action. It also logs whether changes were made to the file during that session.
A major incentive to get ADAudit Plus is to comply with data security standards. The tool includes a compliance reporting module that can be tailored to the expectations of SOX, HIPAA, PCI-DSS, FISMA, and GLBA.
Who is it recommended for?
This package is suitable for businesses that need to prove protection standards compliance. The software runs on Windows Server, AWS, or Azure. There are two paid editions: one for LANs and the other for WANs. There is also a Free edition but that just processes data collected during the free trial of the paid versions.
Pros:
- Refers to Active Directory: Can use either Active Directory or Azure AD to verify file access permissions
- USB Tracking: Logs file movements onto and off a USB memory stick
- Compliance Reporting: Provides GDPR reports
Cons:
- Focused on Windows: This system works almost exclusively on Windows-based systems
The ManageEngine ADAudit Plus runs on Windows Server, AWS, and Azure. There are three editions for ADAudit Plus: Free, Standard, and Professional. The Free edition will monitor 25 workstations, while the Standard edition will monitor activity on servers as well as workstations. The Professional edition adds on Active Directory monitoring. You can get the Professional Edition on a 30-day free trial.
EDITOR'S CHOICE
ManageEngine ADAudit Plus is our top pick for a file activity monitoring service because it offers user activity monitoring that references AD account data to make user identification easier than combing through a series of IDs and IP addresses. This system also protects records in Active Directory – any intruder that wants to pose as a user just has to get in there and alter or create a user account record. Your user activity tracking system is only going to provide accurate logging if the AD data is kept clean. This system can operate with Azure AD as well as your on-premises Active Directory implementations. It records logon events, including failed attempts, which could indicate a brute force password cracking attempt. This is a good tool for the detection of insider threats and account takeovers.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/products/active-directory-audit/download.html
OS: Windows Server, AWS, and Azure
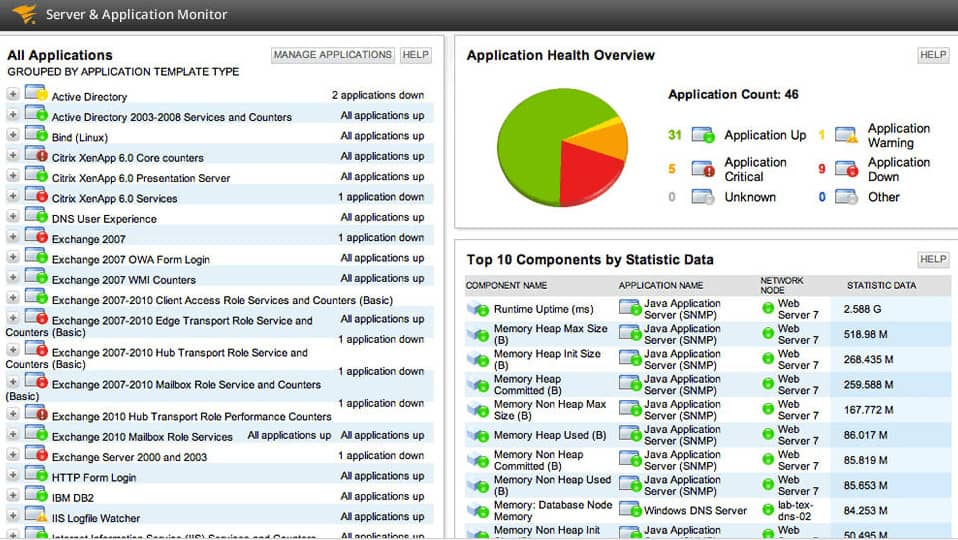
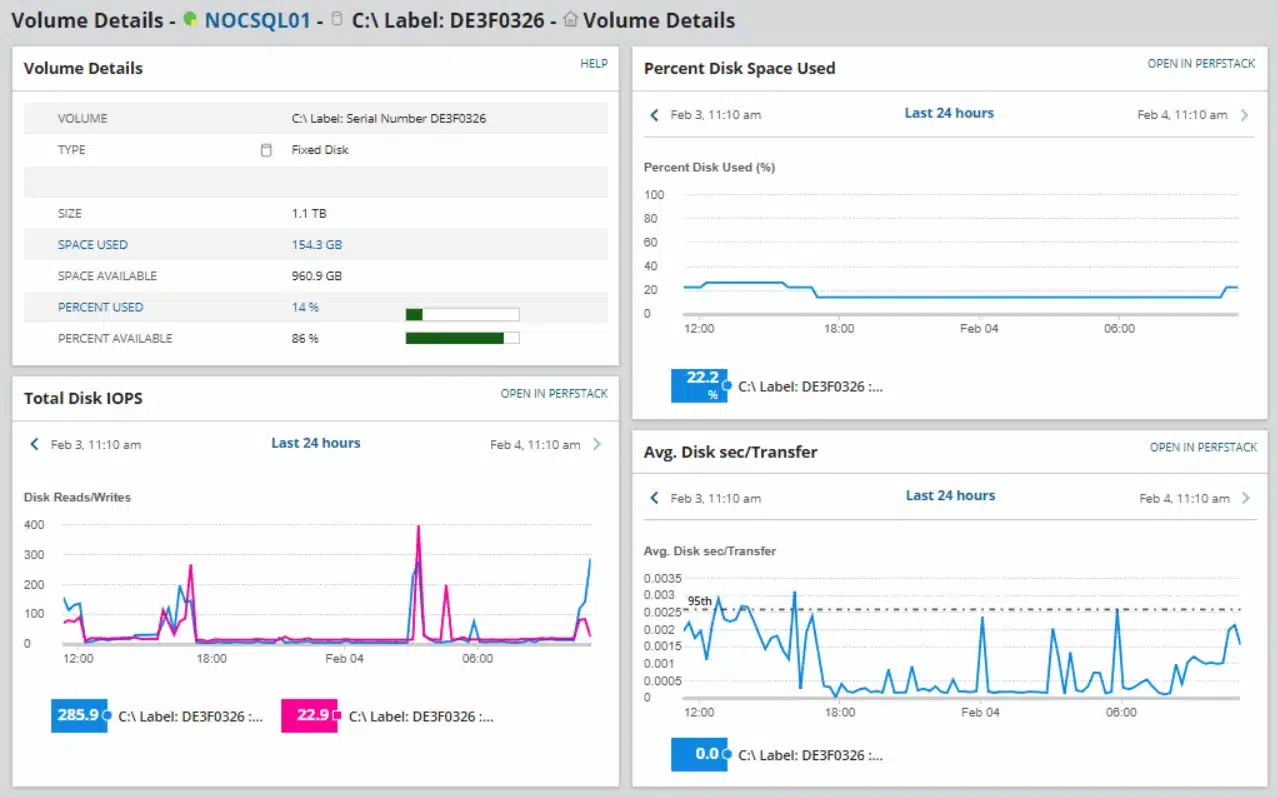
2. SolarWinds Server & Application Monitor (FREE TRIAL)
SolarWinds Server & Application Monitor is an application and file monitoring tool that tracks file changes in real-time. From the dashboard, you can view file characteristics like content, size, age, and count. These monitors keep you updated on changes within the network. For example, file age monitor tells you when the file was last modified.
Key Features:
- On-Premises Software: Runs on Windows Server
- Tracks File Changes: Maintains monitors on files
- File Attributes: Logs file size, age, and name
- Folder Monitoring: Notes changes in file counts
- Checksum Tracking: Stores the MD5 checksums of files
Why do we recommend it?
SolarWinds Server & Application Monitor provides tracking for server activity to ensure that resources do not run out. Part of the functions of the tool involves counting files and if the count unexpectedly changes, there could be unauthorized activity. This is a particularly important function for guarding archives and log file directories.
The fast-track system configuration of SolarWinds Server & Application Monitor makes it ideal for SMEs. After installing the software the program will start to automatically discover connected devices. In less than an hour, you can have a functional file monitoring platform with monitoring templates included out-of-the-box.
Of course, you don’t have to catch everything in real-time: SolarWinds Server & Application Monitor does it for you. Monitors like the file count monitor alert you if the number of files within a directory exceeds the configured threshold. The alerts function highlights potentially malicious activity so that you can take a closer look. Alerts can be customized so that you choose what parameters should be used.
The SolarWinds Server & Application Monitor identifies all activity on files in real-time, while also keeping track of all server resource utilization. The monitor includes an alerting system so key technical staff can get on with other tasks without missing key events occurring on the file system and the server in general.
Who is it recommended for?
SolarWinds Server and Application Monitor isn’t a dedicated file integrity monitor but it does notice file creation or deletion actions. This is a supplementary service, while the main focus of the package is to prevent applications from performing badly by watching their activities and spotting server resource shortages.
Pros:
- Folder Alerts: Place limits on file counts per folder and alert if this threshold is approached or hit
- File Alerts: Get an alert if specific files are changed
- File Server Monitoring: Track the performance of and activity on file servers
- Multiple Platforms: Scans across the network to monitor physical, virtual, and cloud servers
- Crosses OSs: Runs on Windows Server but can access other servers running other operating systems
Cons:
- Windows Only: This software won’t run on Linux
If you require a file monitoring solution with application monitoring capabilities then SolarWinds Server & Application Monitor is highly recommended. SolarWinds Server & Application Monitor starts at a price of $2,995 (£2,349). There is also a 30-day free trial.
You can enhance file activity tracking by also using the SolarWinds Log Analyzer. You can buy both the Server & Application Monitor and the Log Analyzer in the Log and Systems Performance Pack. Both tools appear in a single console, so you don’t have to keep switching windows in order to keep track of events on your system. The pack installs on Windows Server. Download the 30-day free trial.
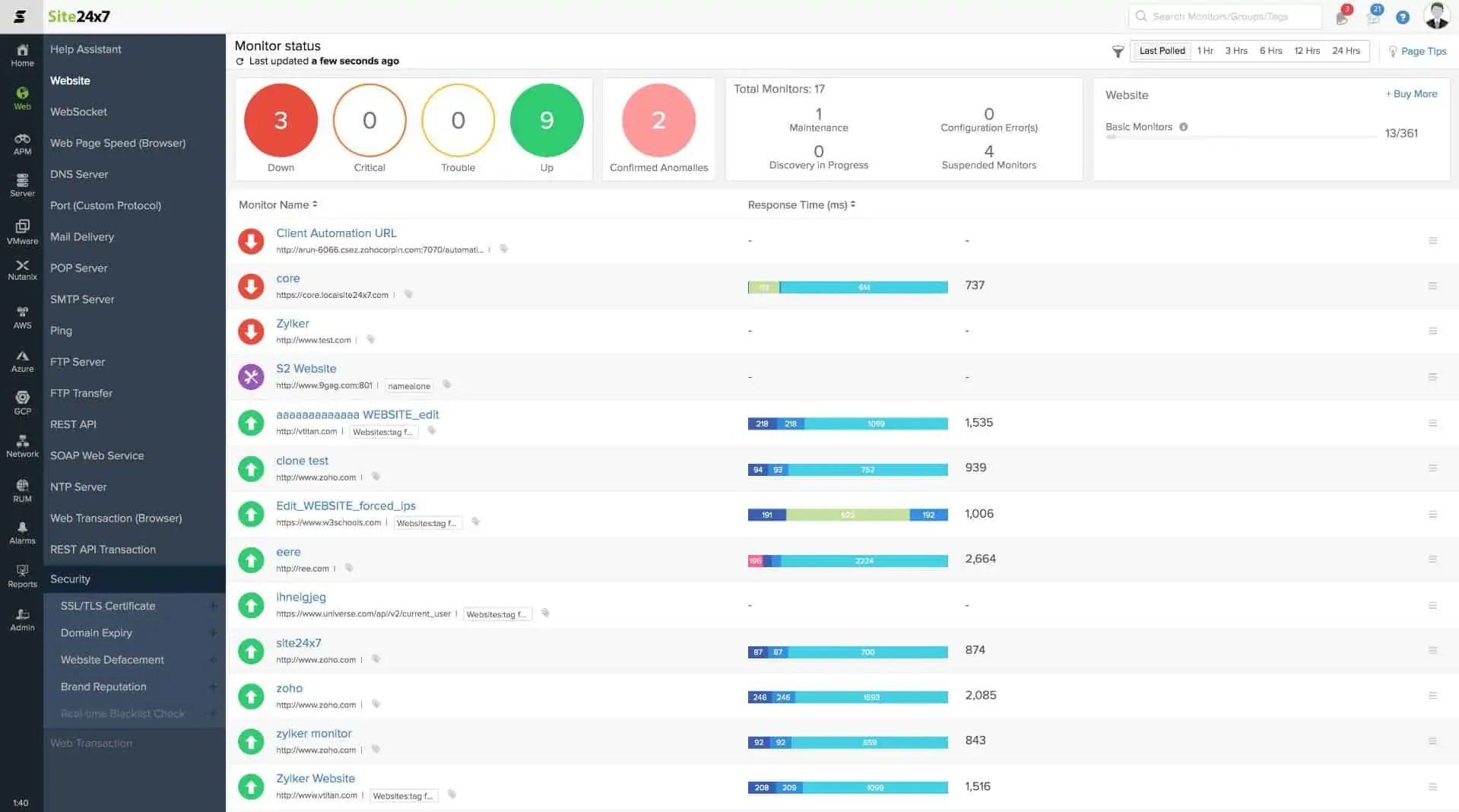
3. Site24x7 Infrastructure (FREE TRIAL)
Site24x7 is a cloud-based system monitoring platform that covers networks, servers, and applications. The service is packaged in different bundles and Site24x7 Infrastructure is one of them. This is a flexible plan and you choose which aspects of physical and virtual infrastructure you want the tool to monitor. One of the options is its file monitoring capabilities.
Key Features:
- Cloud-Based: A SaaS platform
- Full Stack Observability: Monitors networks, servers, and applications
- Tracks File Changes: The administrator specifies files for special monitoring
- Folder Monitoring: Sets folder size limits and alerts when that level is approached
Why do we recommend it?
Site24x7 Infrastructure watches over servers and services and it includes a file activity monitor. This tool is good for tracking the activities of users around stores of sensitive data. The system watches over file storage space and makes sure that there is still enough available for natural file creation processes, such as log file creation.
The file and directory monitoring system in Site24x7 includes comprehensive tools for protecting stores of sensitive data. This is an excellent data loss protection service because it includes active checks on changes in files as well as general file storage performance statistics.
The system can be set to pay extra attention to specific directories. It will track any changes to files including file permission changes – which is a sign of hacker activity. In this mode, the Site24x7 service will raise an alert and write to a log every time files are created, deleted, or modified in a nominated directory. The service also scans directories to highlight files that have not been accessed in a long time, which lets you know which files are good candidates for archiving or deletion.
This service will perform general monitoring tasks on file storage, such as tracking the growth rate of directories and recording metrics such as the number of files per directory or per device. You can centralize the monitoring of all of your servers in one overview that offers a drill-down path to see statistics on each individual location.
Who is it recommended for?
Site24x7 provides packages of monitoring systems, so you don’t just get the Infrastructure Monitoring system, you also get network monitoring and application monitoring, plus other utilities, such as log management. This makes the tool great value for money because it covers all of your monitoring needs.
Pros:
- Log File Access: Record the user account involved and the content that changed
- Alerts for Folder Creation: Also writes to a log file if a directory is created
- Log File Monitoring: Alerts if log files get corrupted
- Cross-Platform Monitoring: Monitors servers running Windows and Linux and also cloud platforms
Cons:
- Cloud Only: No on-premises version
Site24x7 is a subscription service and you can get it on a 30-day free trial.
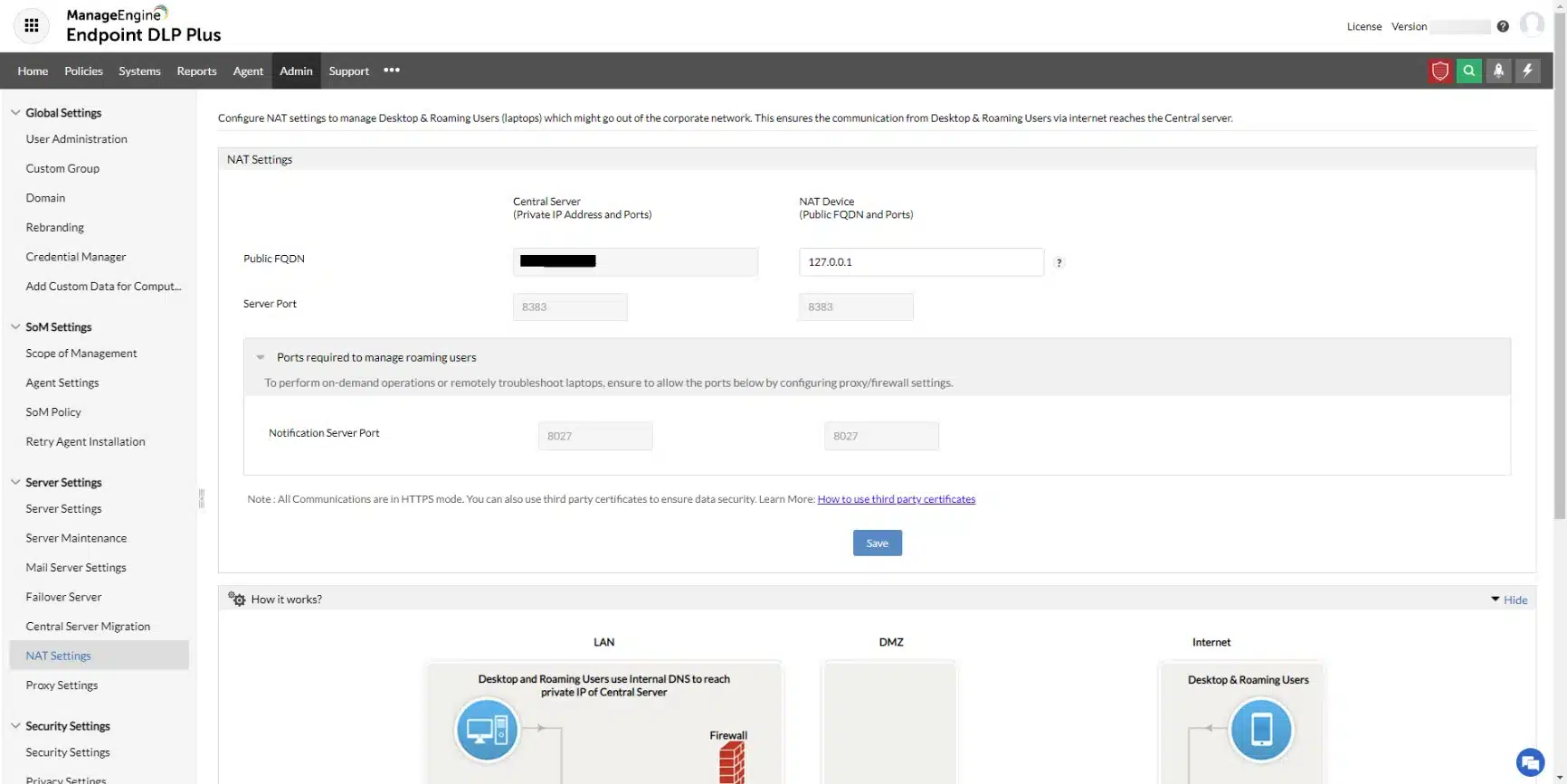
4. ManageEngine Endpoint DLP Plus (FREE TRIAL)
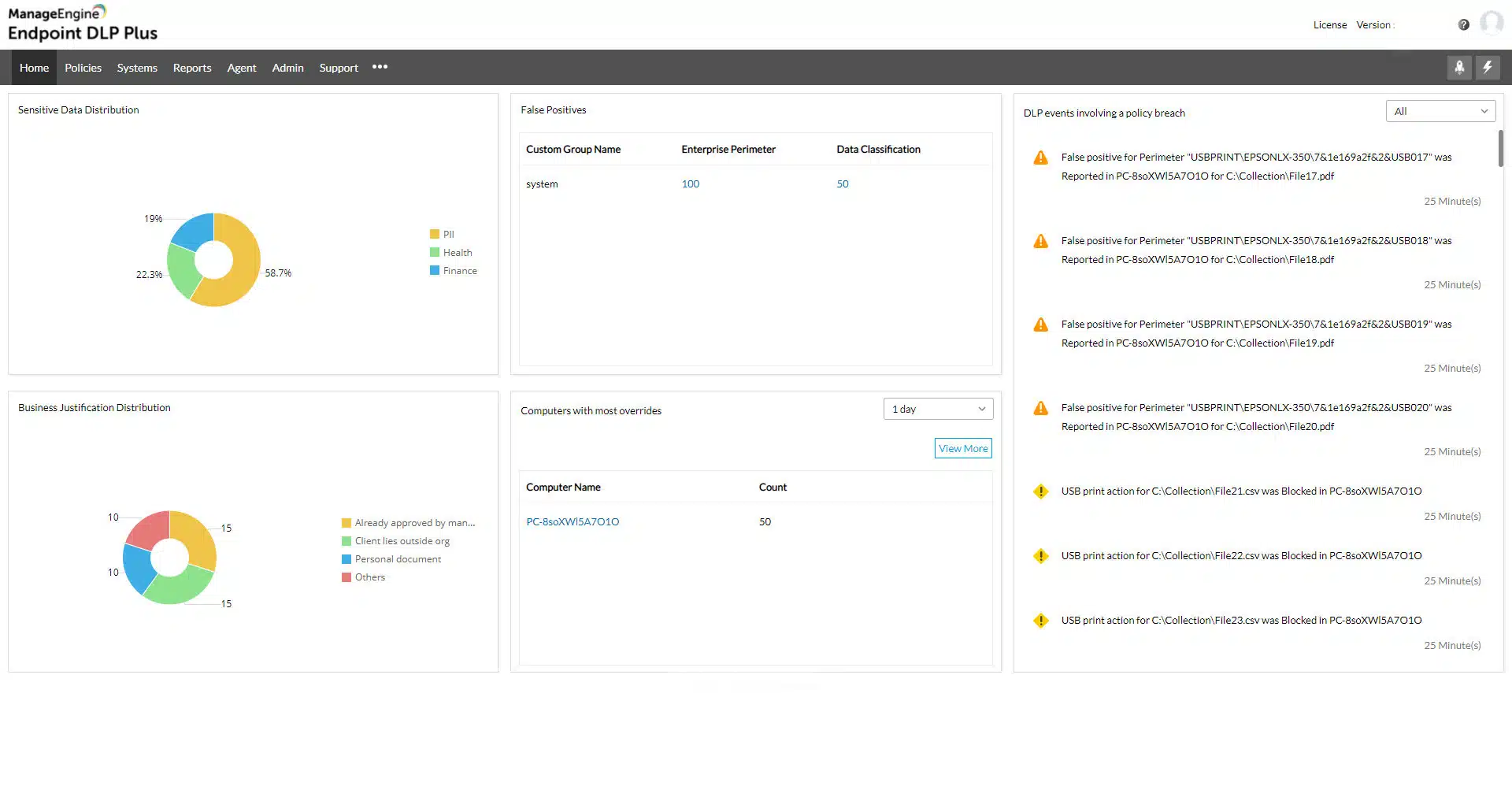
ManageEngine Endpoint DLP Plus provides protection for the files that hold sensitive data and controls the movement of those files while tracking user activity. This system can be adapted to identify data based on a specific data protection standard, such as PCI DSS, HIPAA, or GDPR.
Key Features:
- Sensitive Data Discovery: Can be tailored to specific data protection standards
- Control of Data Movements: Emails, cloud uploads, file transfer protocols, and USB sticks
- Granular Controls: Operates permissions by user groups
Why do we recommend it?
ManageEngine Endpoint DLP Plus is a data loss prevention package. It scours all data stores for sensitive data and then classifies the instances that it finds. The process can be adapted to suit the requirements of a specific data protection standard. The tool then controls all movements of that sensitive data.
The DLP package routinely scans all endpoints for instances of sensitive data and categorizes all examples that it finds. The base package operates on a LAN but that functionality can be extended to multiple sites. Files that are found to contain sensitive data are protected by containerization, which makes them impossible to access directly or move.
Within the console for Endpoint DLP Plus, the administrator needs to define a list of trusted applications. These will be able to get access to the contents of protected files and they should themselves be protected by access rights credentials. Data access actions within these applications get logged with each instance attributed to a user account. If data access is unusual, an alert is raised and all of the activities of that account get logged for an investigation into an insider threat or account takeover.
Data movements are also tracked and controlled, while not banned. In some instances, copying or transferring files and extracts is necessary, so specific users are permitted to perform specific actions. These controls extend to USB devices, print queues, email systems, and cloud upload facilities.
Who is it recommended for?
This system will appeal to businesses that need to comply with a data protection standard, such as PCI DSS, GDPR, or HIPAA. There is a Free edition that will scan up to 25 endpoints. That is suitable for small businesses. The paid package can operate over a LAN or a WAN. The software runs on Windows Server.
Pros:
- Data Identification: Keywords, regex, and fingerprinting
- Insider Threat Detection: User behavior analytics
- Data Containerization: Protects files with encryption
Cons:
- Windows Software: Not available for Linux
Endpoint DLP Plus runs on Windows Server. You can get the Free Edition to manage data on up to 25 computers. The paid plan is called the Professional Edition and you can get it on a 30-day free trial. If you decide not to buy at the end of the trial, the package switches over to the Free Edition.
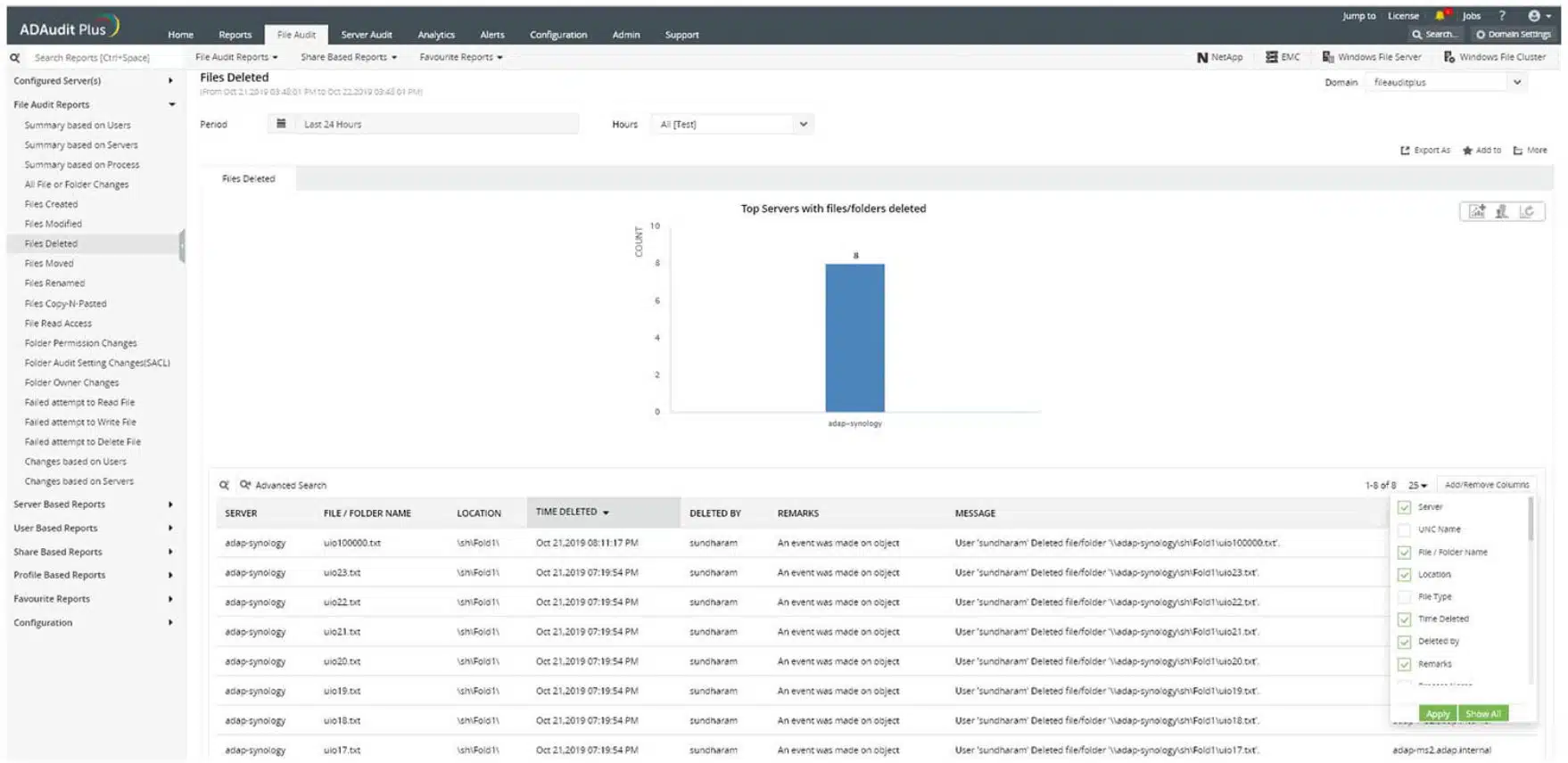
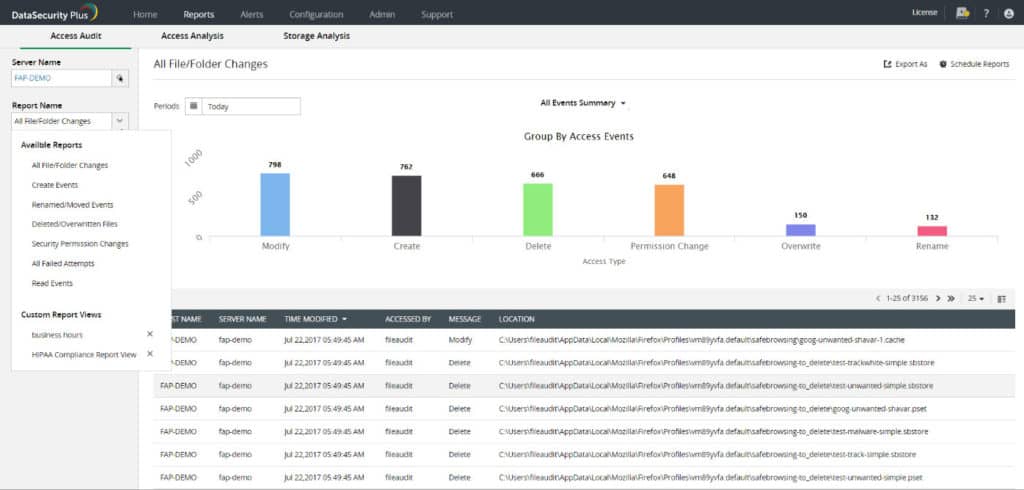
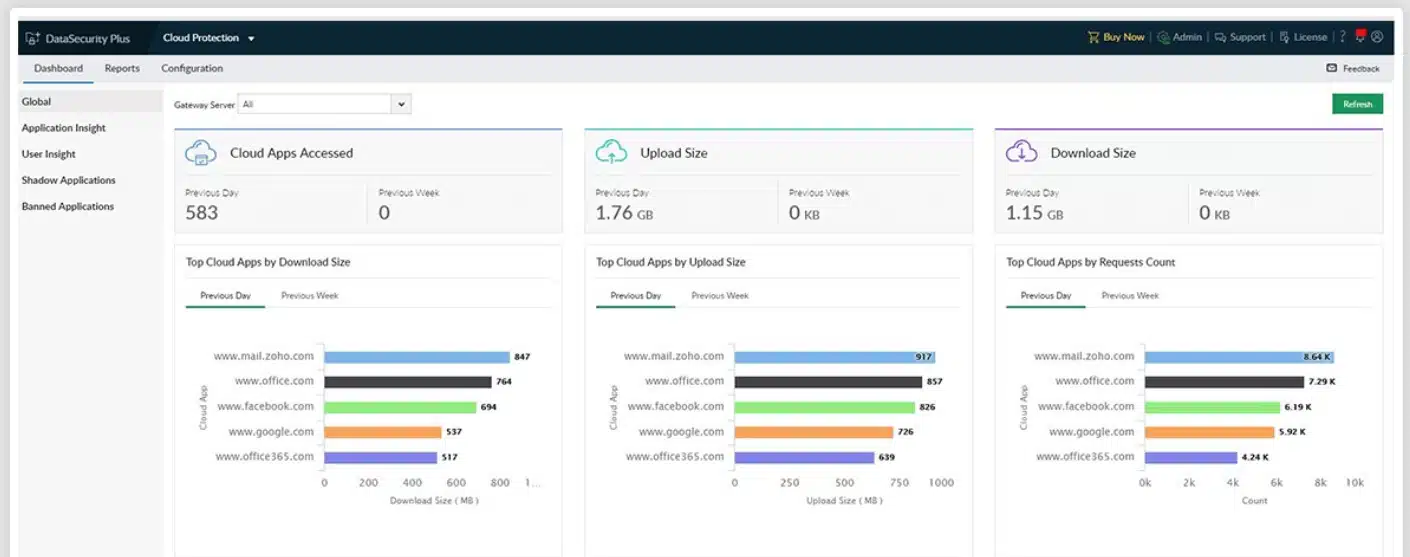
5. ManageEngine DataSecurity Plus
ManageEngine DataSecurity Plus is a file monitoring software platform that displays file and user activity on a network. You can see who accessed the file, when, and what they accessed. There are also several visual displays like graphs and pie charts that show you a more complete overview.
Key Features:
- Data Risk Assessment: Sensitive data discovery and classification
- File Server Auditing: File access logging
- Data Movement Tracking: Through emails, peripherals, or cloud uploads
Why do we recommend it?
ManageEngine DataSecurity Plus is a very similar package to the Endpoint DLP Plus system. With this tool, you get sensitive data discovery and classification and also control over data movement channels. The tool also manages file servers to ensure junk temporary files are cleared out and that file access permissions are sufficiently controlled.
For instance, you can see a pie chart of All File and folder changes which is broken down into Create, Delete, Modify, Permission Change, Overwrite, Rename, and Move. You can also view the most active users, most accessed files, and most modified files within the file server.
One premium feature included with ManageEngine DataSecurity Plus is file access analytics. File access analytics highlight access trends, monitor access times and detect anomalous file access. For example, the tool can identify if a file was accessed outside of working hours and if the user was authorized to access the content.
The built-in auditing and regulatory compliance of ManageEngine DataSecurity Plus are also extremely useful. The tool is compliant with PCI DSS, HIPAA, GDPR, SOX, GLBA, and FISMA. By auditing access privileges you can better control access to files and ensure you don’t leave yourself open to penalties or other liabilities.
Who is it recommended for?
This tool, like Endpoint DLP Plus is good for those businesses that need to prove compliance with data security standards. It also tracks Web services and identifies when workers are spending time on non-business sites, such as social media systems. The package includes four modules, which are charged for individually.
Pros:
- Controls Data on Cloud Systems: Identifies shadow copies of files
- Ransomware Detection: Identifies malware by behavior
- File Copy Protection: Prevents sensitive data files from being copied
Cons:
- Software for Windows Server: Not available for Linux
For ManageEngine DataSecurity Plus file server auditing the price starts at $745 (£584) per year. The price includes file integrity monitoring, tracking file interactions, alerts, detect/quarantine ransomware and more. You can download the 30-day free trial version.
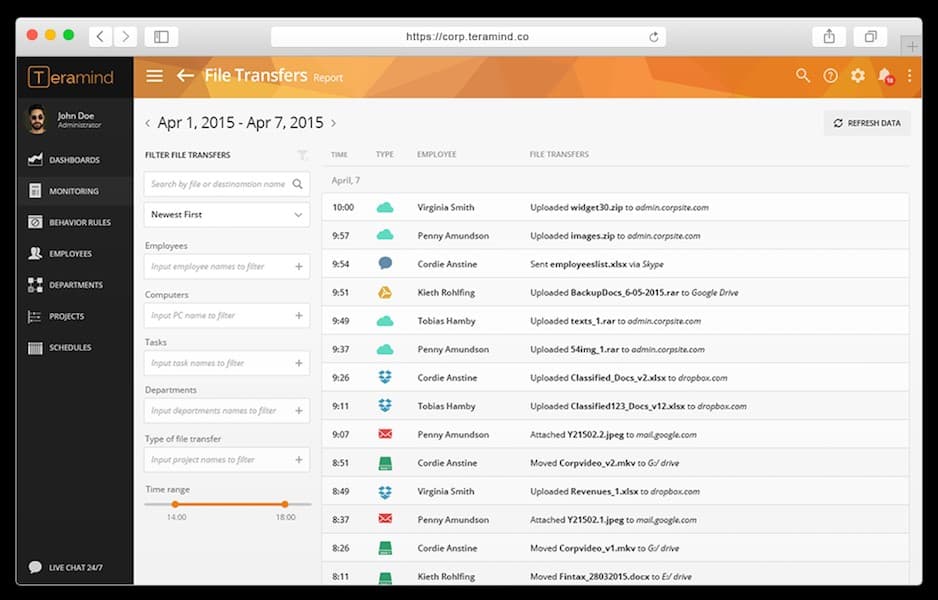
6. Teramind
Teramind is a file activity monitoring software designed specifically for user activity monitoring. The product monitors file access, creation, deletion, and write operations. User activity is monitored through screen recording and textual logs so you can take a closer look at user activity to verify its legitimacy.
Key features:
- Behavior Analysis: Focuses on insider threats
- Tracks User Access: Records Web and application access
- Content-Based Access Controls: Some users are blocked from accessing files with sensitive data
Why do we recommend it?
Teramind is a cloud platform that provides data loss prevention by focusing on insider threats. This remit also extends to combating account takeover. Data theft or sabotage requires the use of genuine user accounts. That makes intruders and disgruntled employees difficult to spot. This service deploys user behavior analytics to identify suspicious activity.
There is also a notifications system to keep you updated on developments in the network. For example, the notifications system tells you when files are uploaded to the cloud either as an email attachment or through a cloud service like Google Drive, Dropbox, or OneDrive. You also can block uploads to the cloud storage if you believe an activity is malicious in nature.
Who is it recommended for?
Teramind is priced per technician and there are three plans that make the system suitable for use by businesses of all sizes. This is a cloud-based package and so you don’t need to find server space or maintain the software. All of these factors make this an affordable system for data protection.
Pros:
- Selective Controls: Doesn’t block authorized users from doing their jobs
- Redaction: Prevents employees from seeing data without deleting it
- Optical Character Recognition (OCR): Can identify words in images
Cons:
- User Scrutiny: Mainly built to spy on employees
Teramind is available as an on-premises or cloud-based solution. Each has three product versions: Teramind Starter, Teramind UAM, and Teramind DLP. The on-premises versions start at $60 (£47) per month for 10 endpoints up to $150 (£117) per month for 10 endpoints. The cloud-based versions start at $60 (£47) per month for five users up to $150 (£117) for additional content-based data exfiltration rules.
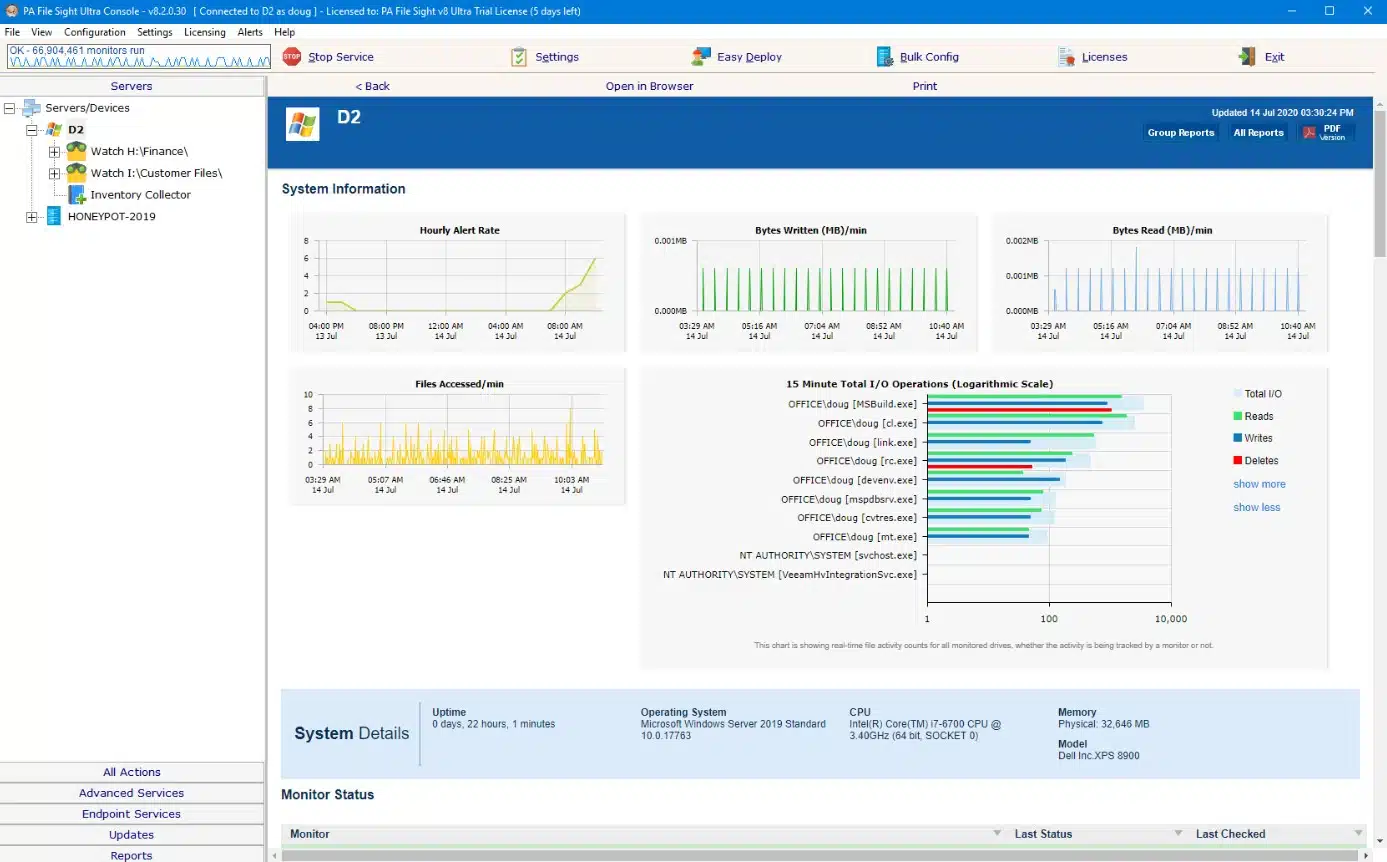
7. PA File Sight
PA File Sight is a file monitoring solution with real-time file monitoring capabilities. The software monitors for file creation, deletion, modification, and movement of files. It also monitors the IP address, data/time and computer name of the interactions to help identify different users and spot suspicious activity. You can start monitoring as soon as you finish the setup process, which can be completed in just a matter of minutes.
Key Features:
- Protects Files: Blocks changes to files by unknown programs
- Application Whitelisting: Maintains a list of authorized software and blocks all others from running
- Controls User Actions: Blocks actions, such as file copying according to the user’s status
Why do we recommend it?
PA File Sight provides data protection. It looks out for ransomware activity and also blocks unauthorized access to files or movements of data. The system works by fencing all files and preventing all programs from running. The administrator then whitelists specific applications and they should have their own access credentials requirements.
The program also has automated alerts. PA File Sight alerts you on changes made to files so that you can detect log tampering. Alerts come with a range of supporting information including user account, user IP address, computer name, target file, what the activity was and the date/time. Having this information available to refer to helps to put all the necessary information in one place so that you can start to address an attack.
When it comes to auditing, PA File Sight is an excellent choice. Not only is it compliant with PCI, HIPAA, FISMA AC-19, SOX, and ISO 27001/27002, but it also has reports. Reports can be generated in text, HTML, PDF or .CSV. Reports show specific users, specific time range, and the time period.
There are two versions of the product available to purchase: PA File Sight Ultra, and PA File Sight Lite. The Lite version starts at $199 (£156.18) for 1-9 licenses and can monitor file activities, and generate alerts. The Ultra version starts at $599 (£470 )for 1-9 licenses and can do everything the Lite version can but adds integration for Microsoft SQL Server, reports, advanced alerts, and the ability to block external drives.
Who is it recommended for?
Businesses that need to protect data from attacks need this tool. That description encompasses just about every business currently in operation because loss or damage to operational data can mean ruin to a business. For example, ransomware can prevent a business from continuing. This software runs on Windows Server.
Pros:
- Protects Against Ransomware: Malware isn’t allowed to run
- Selectively Block Access: Controls access to cloud platform and USB devices
- Activity Alerts: Draws the administrator’s attention to risky user behavior
Cons:
- Available for Windows Server: Won’t run on Linux
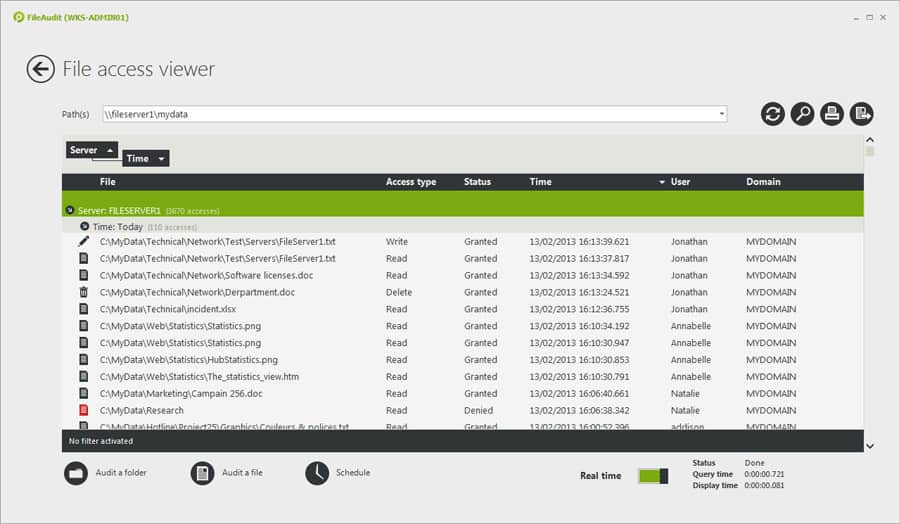
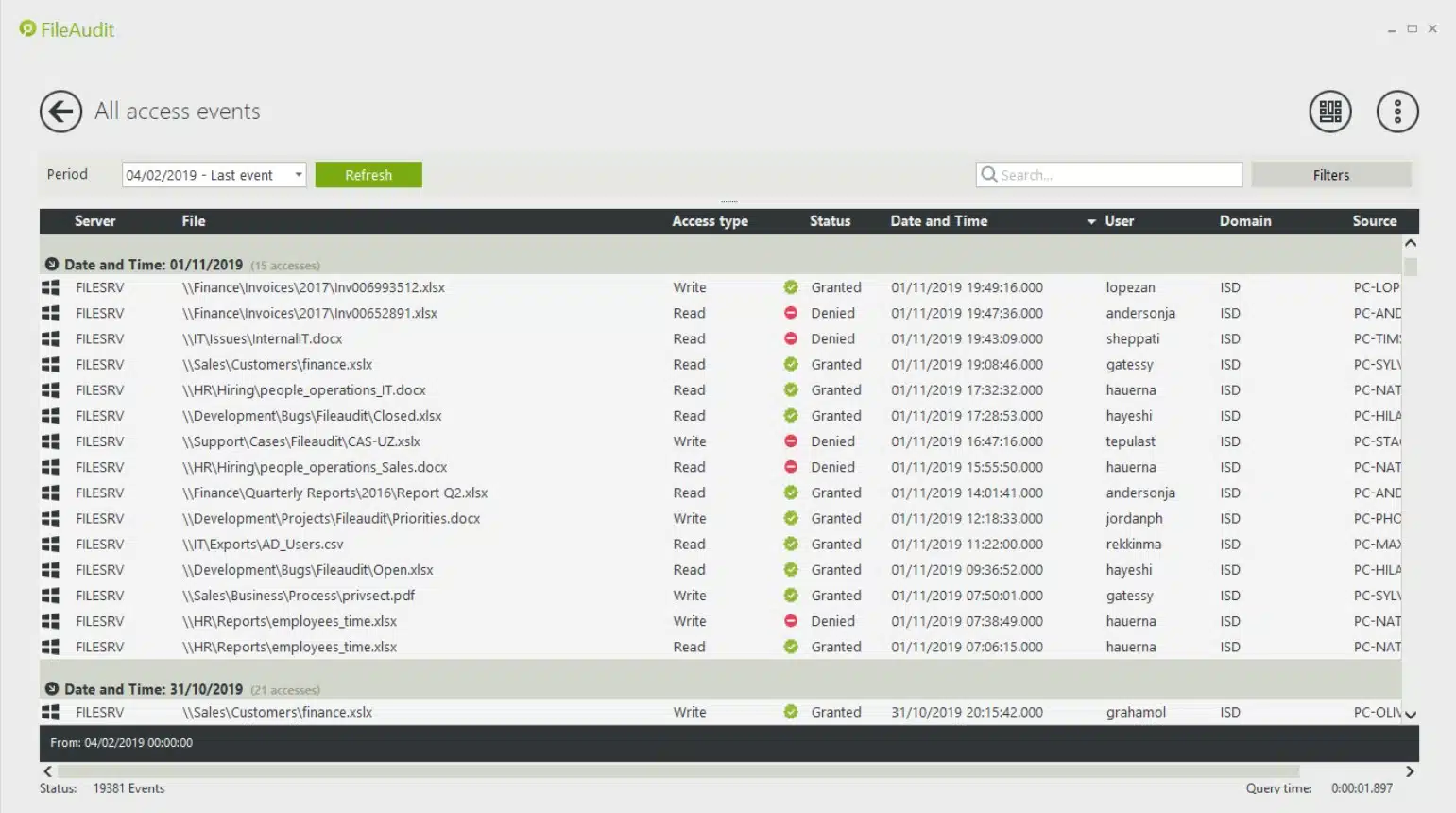
8. FileAudit
FileAudit is a real-time file monitoring tool that has been designed to help monitor how employees interact with files. The platform monitors file changes, read-write, deletion, and ownership. Having this information on hand makes sure that you can immediately discover and address cyberattacks before the damage is done.
Key Features:
- Tracks File Access: You can tailor this activity to specific files or specific locations
- Identifies Endpoints: Records the device that file access was made from
- Logs Activity: Records both successful and blocked file access events
Why do we recommend it?
IS Decisions FileAudit is a software package that protects files on Windows computers and cloud platforms. The system scans files on OneDrive, SharePoint Online, Google Drive, Dropbox, and Box. this system tracks user activities and spots irregular activity when accessing files. It also tightens up permissions and access rights.
There are also automated email alerts to notify you about user actions. Alerts are generated for certain events like the deletion of a file or if a user has been denied access to a file. Staying on top of this information helps to diagnose suspicious behavior as early as possible.
There are four versions of FileAudit available to purchase: Team, Small, Medium, and Enterprise. The Team version costs $50 (£39) per month for 100 users and one server. The Small version costs $85 (£66) for 500 users and three servers.
Who is it recommended for?
You will need to be running Windows on all of your on-site files servers, specifically, this tool operates on the NTFS system. The cloud platform protection is an add-on service for which there is a fee. You can’t have the cloud protection system by itself. The four plans for the system cater to businesses of all sizes.
Pros:
- NTFS Permissions Tracking: Records changes to the permissions system
- Cloud Scanning: Extends monitoring to cloud drives, such as Dropbox, Sharepoint Online, OneDrive, and Google Drive
- Log Analysis: Data viewer with analytical tools
Cons:
- Operates on Windows Server and Cloud Platforms: Doesn’t protect data on Linux servers
The Medium version costs $140 (£109) for 1000 users and five servers. The Enterprise version supports over five servers with more than 1000 servers (but you’ll need to contact the sales team directly). You can download the free version here.
Selecting the right file activity monitoring software
File activity monitoring is part and parcel of document management in an enterprise environment. Tools like SolarWinds Server & Application Monitor and ManageEngine DataSecurity Plus have been built with this purpose in mind. Each tool is easy to use with simple configuration and an overhead perspective of file interactions.
The file access analytics feature included with ManageEngine DataSecurity Plus is useful for those enterprises that want to automate some of their threat detection. Automation pays dividends to response time when reacting to malicious activity.
File Activity Monitoring Software FAQs
What is File Integrity Monitoring?
File integrity monitoring is an ongoing automated process that validates the status of files held on a system through indicators such as file size and last modified date. Any changes to files should be logged and unauthorized changes rolled back.
Why is deep packet inspection vital to file activity monitoring?
Deep packet inspection is a network monitoring part of file integrity monitoring. It is able to add information about the user who tries to modify a file, such as location and home device.
Can file activity monitoring prevent data loss?
File activity monitoring is able to add to existing DLP technology by protecting the contents of files and monitoring access to it. Thus, it is able to catch unauthorized file access, blocking theft, deletion, corruption, or alteration of the contents.