
Need to know more about ransomware, including how to prevent ransomware and how to remove it following an infection? In this post, we explore why ransomware is a dangerous security threat for businesses and individuals alike. We also offer targeted strategies you can use right now to reduce your risk of getting hit with ransomware, as well as your next steps should you get infected with encryption malware.
What is ransomware?
Once a rare and obscure form of malware, ransomware now has an outsized impact on almost everyone. According to Verizon’s 2023 Data Breach Investigations Report, ransomware accounts for up 24% of all breaches. Figures from Sophos suggest that 66% of organizations were subject to ransomware attacks in 2023, with a mean recovery cost (excluding ransom payments) of $1.82 million.
With these types of attacks making headlines almost daily, the first thing we need to ask is: What is a ransomware attack?
At a basic level, ransomware is just another form of malware. It’s a malicious program intended to infect and disrupt the normal operation of a computer system.
However, there are two key features of ransomware that distinguish it from most other forms of malware:
- Instead of stealing data, ransomware is designed to prevent you from accessing it.
- Instead of selling or using your stolen data, cybercriminals try to force you to pay a ransom to regain access to your data.
Where malware has traditionally been focused on stealing data, ransomware is about extortion. Outside of this, the methods cybercriminals use to infect computers with ransomware are the same as any other malware.
That being the case, you could get infected with ransomware if you:
- Download it from a malicious email attachment or link.
- Load it onto your machine from a USB flash drive or DVD.
- Download it while visiting a corrupted website.
Hackers can also load ransomware onto a system if they hack into a system using brute force, or if they use stolen login credentials.
How does ransomware work?
Ransomware’s function is relatively simple. There are multiple types of ransomware designs, but all are essentially encryption programs. Once installed on a system, the program executes and encrypts the type of files it was programmed to target.
Occasionally, ransomware writers could be out to target only a selection of file types, such as Word documents or Excel sheets. More often than not, however, hackers take a broad approach that involves encrypting every file within a system or server.
How do I know if I have ransomware?
Losing access to system files is a clear sign of a ransomware attack. Ransomware shuts down select system functions or denies access to files. In the case of Windows machines, it usually disables your ability to access the start menu (that way you can’t access antivirus programs or try to revert to Safe Mode).
Ransomware serves no purpose unless the attacker makes it clear that you’re infected and provides instructions for how to unblock your system. Given that, most ransomware will come with a message (on your screen or emailed to you) that your system has been encrypted. This message typically includes the ransom demand and information for how to pay the ransom (typically in Bitcoin or some other cryptocurrency).
You may see something like this:
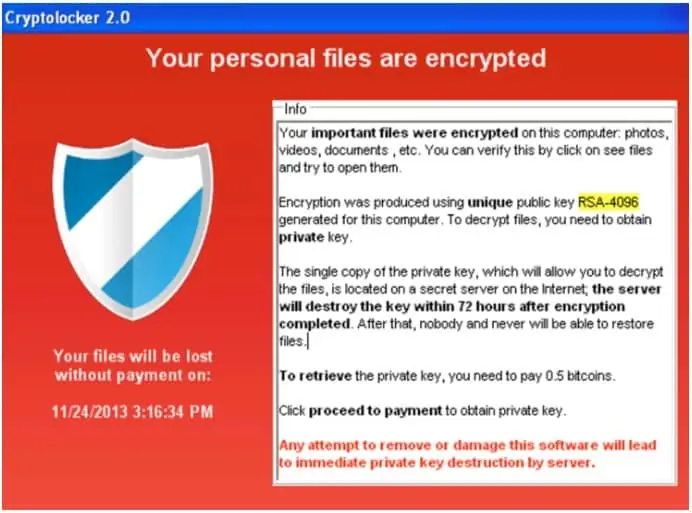
Again, encryption is the go-to method for ransomware writers. This type of malware encrypts files on your device so they cannot be opened without the proper decryption key or password. Only the attacker will have this information (although sometimes they don’t).
Any file can be encrypted with ransomware, although most ransomware won’t attempt to encrypt all types of files. Some newer forms of encrypting ransomware have even taken to encrypting network shared files as well, a dangerous development for businesses in particular.
Until you clear the ransomware from your machine (or pay the demanded ransom and hope the criminal either clears it for you or gives you the decryption key), you won’t have access to those files or critical systems. Some ransomware will even demand that you pay up within a certain amount of time, or else the files will stay locked forever or the virus will completely wipe your hard drive.
What you read above is a bit of a high-level explanation. If you need a more detailed technical explanation of how ransomware works to encrypt data, we recommend this excellent Medium post on the top from Tarcísio Marinho.
Related: How to start Windows 7/8/10/11 in safe mode
Types of ransomware
Ransomware has been around since the 1980s, but many attacks today use ransomware based on the more modern Cryptolocker trojan. File-encrypting ransomware is increasingly the most common type. Additionally, many hackers now employ double-encryption techniques that employ two types of malware to lock files.
According to Malwarebytes, there are several categories of ransomware that you may still encounter:
Encrypting ransomware
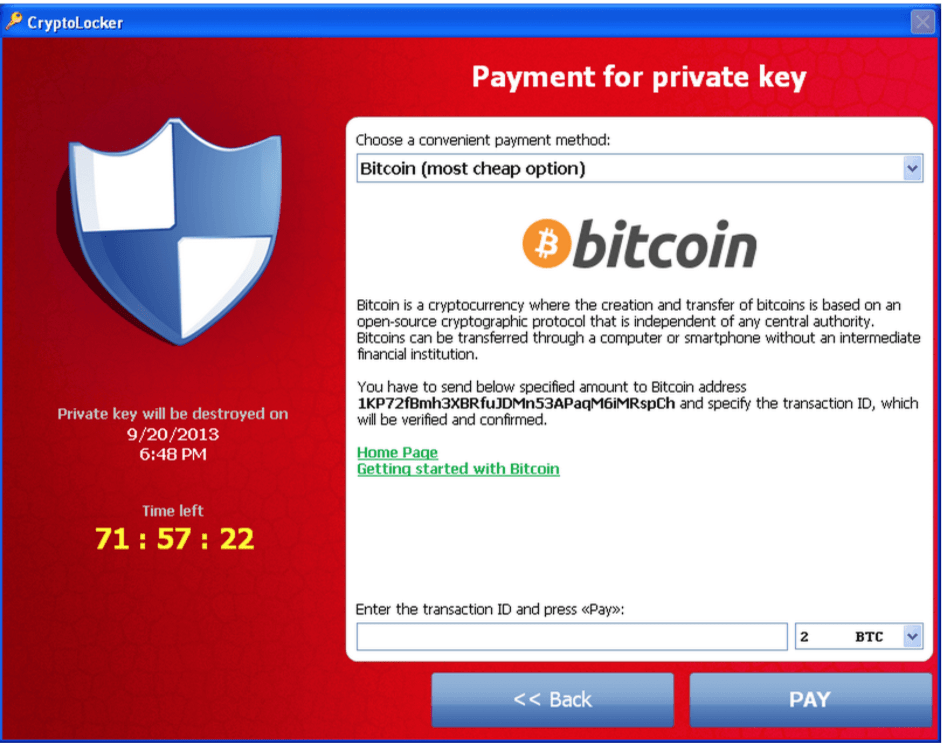
If ransomware finds its way onto your machine, it’s likely going to be of the encrypting variety. Encrypting ransomware is quickly becoming the most common type due to a high return on investment for the cybercriminals using it, and how difficult it is to crack the encryption or remove the malware. This is a favorite among hackers because most antivirus tools simply don’t work to prevent it and can’t effectively remove the encryption after an infection.
Encrypting ransomware will completely encrypt the files on your system and disallow you access to them until you’ve paid a ransom, typically in the form of Bitcoin. Some of these programs are also time-sensitive and will start deleting files until the ransom is paid, increasing the sense of urgency to pay up.
On this type of ransomware, Adam Kujawa, Director of Malwarebytes Labs, had this to say: “It’s too late once you get infected. Game over.”
Online backup can be a great help in recovering encrypted files. Most online backup services include versioning so you can access previous versions of files and not the encrypted ones
Scareware
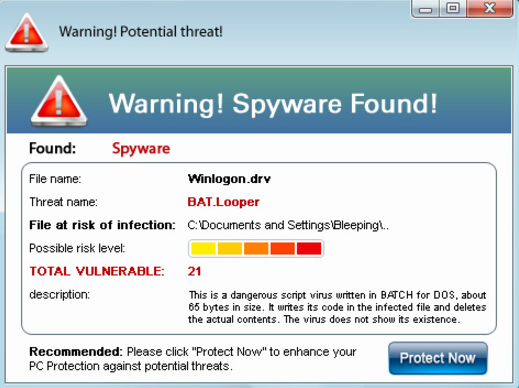
Scareware is malware that attempts to persuade you that you have a computer virus that needs removal right away. It will then try to get you to clear the virus by buying a suspicious and typically fake malware or virus removal program. Scareware is highly uncommon these days, but some of these viruses do still exist out in the wild. Many target mobile phones.
A scareware virus typically won’t encrypt files, although it may attempt to block your access to some programs (such as virus scanners and removers). Nevertheless, scareware is the easiest to get rid of. In fact, in most cases, you can remove scareware using standard virus removal programs or other methods without even entering Safe Mode (although this may still be necessary or recommended).
Screen locker (or lock-screen viruses)
Screen lockers will put up a warning screen that limits your ability to access computer functions and files. These can be installed onto your machine or exist within a web browser. They’ll typically come with a message claiming to represent a law enforcement organization and try to convince you that you’ll face severe legal consequences if you do not pay a fine immediately.
This type of virus can be installed in numerous ways, including by visiting compromised websites or by clicking on and downloading an infected file contained in an email. When installed directly onto a computer, you may have to perform a hard reboot to regain access to your system. However, you may also find that you’re still greeted with the screen lock message even when the operating system loads up again.
Screen lockers tend to lock you out of your menu and other system settings, but don’t always block access to your files. Some of the malware’s primary attack methods prevent you from easily accessing your virus removal software, and at times may even prevent you from restarting your computer from the user interface.
Screen lockers are another good reason why having cloud backup is extremely important. While the screen locker won’t encrypt or delete your files, you may find yourself forced to perform a system restore.
The system restore may not delete your important files, but it will return them to an earlier state. Depending on the restored states, that may still result in a lot of lost data or progress.
Regular online backups will help prevent data loss that performing a system restore does not guarantee, especially if the virus has been hiding on your system for much longer than you realized.
How to prevent ransomware
Decrypting files encrypted with ransomware is incredibly difficult. Unless you pay the ransom and receive the decryption key from the attacker (NOT RECOMMENDED), decrypting the ransomware is effectively impossible Most ransomware these days will use AES or RSA encryption methods, both of which are functionally impossible to crack with brute-force methods.
To put it in perspective, the US government also uses AES encryption standards. Information on how to create this kind of encryption is widely known, as is the difficulty in cracking it.
The best method to fight ransomware is remove the risk of infection. The considerable cost and difficulty of decrypting without paying a ransom mean your best strategy is prevention.
Protection against ransomware can be accomplished by shoring up weaknesses in your system, network, or organization and changing the type of behaviors that put you or your business at risk of a ransomware attack.
Ransomware prevention best practices
- Invest in solid data backup. This is hard to understate. Data backup is the single best thing you can do. Even if you do get hit by ransomware, having effective and consistent data backup means your data will be safe, regardless of which type of ransomware you’re attacked with.
- Invest in effective antivirus software. In this case, you don’t just want malware or virus cleaners, but software that will actively monitor and alert you to threats, including inside web browsers. That way, you’ll get notifications for suspicious links, or get redirected away from malicious websites where ransomware may be housed.
- Never click on suspicious email links. Most ransomware spreads through email. When you make it a habit of never clicking on suspicious links, you significantly lower your risk of downloading ransomware and other viruses.
- Protect network-connected computers. Some ransomware works by actively scanning networks and accessing any connected computers that allow remote access. Make sure any computers on your network have remote access disabled or utilize strong protection methods to avoid easy access.
- Keep software up-to-date. Updates to Windows and other operating systems and applications often patch known security vulnerabilities. Updating in a timely manner can help lower the risk of susceptibility to malware, including ransomware.
- Invest in ransomware protection tools. Particularly useful for small businesses and for network administrators to monitor and respond to emerging threats. Many antivirus tools now include anti-ransomware solutions that use behavioral analysis to stop ransomware viruses from running before they start the encryption process.
What to do if you catch ransomware mid-encryption
Encryption is a resource-intensive process that requires a significant amount of computational power. If you’re lucky, you may be able to catch ransomware mid-encryption. This takes a keen eye and knowing what an unusually large amount of activity looks like (and sometimes sounds like). Ransomware will typically operate as a background process to avoid detection, making it easy to miss the malicious activity before you can stop it.
Additionally, the virus doing the encryption will likely be hiding inside another program, or have an altered file name that is made to look innocuous. You may not be able to tell which program is performing the action. However, should you discover what you think is a ransomware virus in the midst of encrypting files, here are a couple of options:
Place your computer into hibernation mode
This will stop any running processes and create a quick memory image of your computer and files (and saved to the hard drive). Do not restart your computer or take it out of hibernation. In this mode, a computer specialist (either from your IT department or a hired security company) can mount the device to another computer in a read-only mode and assess the situation. That includes the recovery of unencrypted files.
Suspend the encryption operation
If you can identify which operation is the culprit, you may want to try suspending that operation.
In Windows, this involves opening up the Task Manager (CTRL + ALT + DEL) and looking for suspicious operations. In particular, look for operations that appear to be doing a lot of writing to the disk. For macOS users, you can do this from Activity Monitor (CMD + SHIFT + U, then open the Utilities folder to find the Activity Monitor).
You can suspend operations from there. It’s better to suspend the operation instead of killing it, as this allows you to investigate the process in more detail to see what it’s actually up to. That way you can better determine whether you have ransomware on your hands.
If you do find that it’s ransomware, check which files the program has been attacking. You may find it in the process of encrypting certain files. You may be able to copy these files before the encryption process has finished and move them to a secure location.
You can find some other great suggestions by security and computer professionals on Stack Exchange.
Ransomware removal: How to remove scareware and screen lockers (lock-screen viruses)
Screen lockers are more troublesome to remove than scareware but are not as much of a problem as file-encrypting ransomware. Scareware and lock-screen viruses are not perfect attackers and can often be easily removed at little to no cost.
Of the options available for removing screen locking viruses, consider these two:
- Perform a full system scan using a reputable on-demand malware cleaner.
- Perform a system restore to a point before the scareware or screen locker began popping up messages.
Let’s look at both of these in detail.
Option 1: Perform a full system scan
This is a fairly simple process, but before performing a system scan, it’s important to choose a reputable on-demand malware cleaner. One such cleaner is Zemana Anti-Malware. Windows users could even use the built-in Windows Security (formerly Windows Defender) tool, although it’s occasionally less effective than third-party antivirus software.
To perform the full system scan using Zemana Anti-Malware, do the following:
- Open your Zemana Anti-Malware home screen.
- From the home screen, change the scan type to Deep
Before running a scan, we recommend setting a restore point. Setting a restore point is a good best practice for virus scans, in general, just in case a critical error occurs during the scanning process. Your virus scan might tag and remove some files or program that aren’t problems (Chrome extensions often come up as problematic, for example), making a system restore necessary to get them back.
On a Windows computer:
- Type in “restore point”.
- Select Create a restore point from Control Panel.
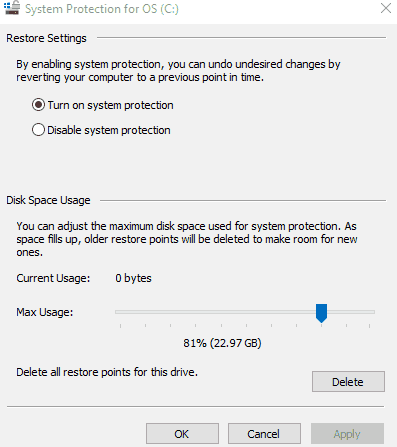
- Select Create, then type a description of the restore point, such as “pre-malware scan”
- Additionally, you may want to go to Configure to turn on System Protection. This will start automatically creating restore points in the future, and allow you to choose how much space is dedicated to backups
On a macOS computer:
No need! Your macOS computer automatically creates restore points using Time Machine.
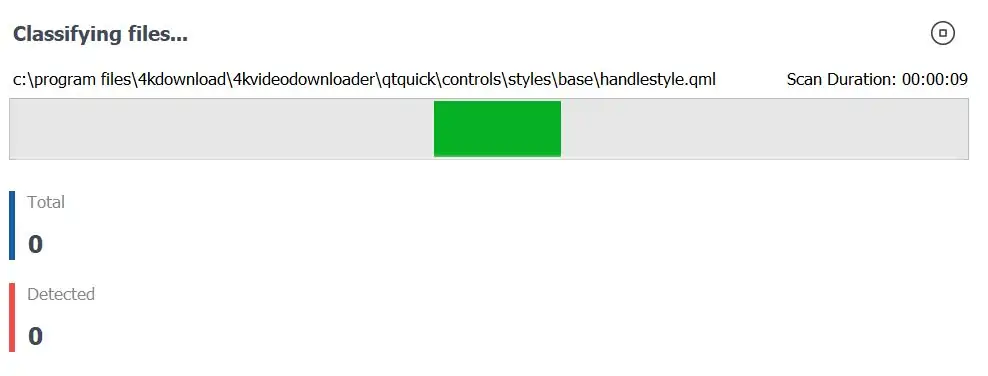
With your restore point secured, you can now click on Scan Now to begin the malware scan.
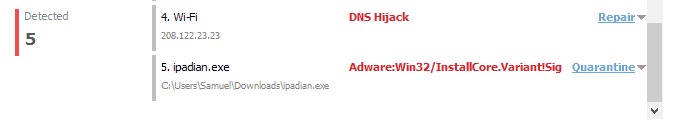
In my case, a recent Zemana system scan revealed a potential DNS hijack. Yikes! (It also misclassified a few programs as being malware and adware, so be careful to make sure to check which files you’re cleaning and quarantining properly.)
To perform a full system scan using Windows Security, do the following:
- Perform a quick system search for “Windows Security”
- Access Windows Security and click on the shield icon on the left
- Click on Scan options
- Switch to Full Scan
- Click on Scan now
Microsoft continually improves its built-in Windows antivirus software, but it’s still not as good a solution as an on-demand third-party tool option like Zemana or many other high-quality antivirus programs. Note that any third-party AV tool you install will automatically disable Windows Security.
When dealing with screen-locking ransomware, you may need to enter Safe Mode to get the on-demand virus removers to work or to run your system restore properly. Even some scareware can at times prevent you from opening your virus removal programs, but they usually can’t prevent you from doing so while you’re in Safe Mode. If you’re having trouble getting your computer to restart in Safe Mode (a distinct possibility if you have a screen locker), check out our guide on How to Start Windows in Safe Mode.
Option 2: Perform a system restore
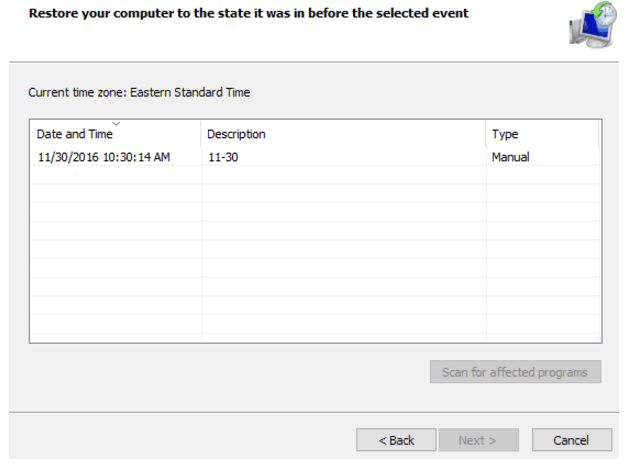
Another option is to perform a system restore to a point before the scareware or screen locker began popping up messages. If you’re using Windows, this option is only available if you have your computer set to create system restore points at preset intervals, or that you’ve performed this action yourself manually.
(Those accessing this guide as a preventative measure against ransomware should refer to Option 1 where we talk about how to create restore points on Windows.)
If you don’t have any recent restore points for your Windows machine (or any at all), this option won’t be helpful for you if you are currently working through a virus infection.
- If it shows that you already have a backup in place, select the backup files from the most recent restore point or from whichever restore point you desire.
The backup restoration process may take several minutes, especially if the amount of data being restored is significant. However, this should restore your file system to a point before the virus was downloaded and installed.
Note that both a scan and a restore can have delayed reaction times, so it’s a good idea to do both.
Indiana University also provides a helpful knowledge base with a few advanced methods for more troublesome scareware. We also recommend checking out our Complete Guide to Windows Malware and Prevention. It will walk you through the process of malware removal and what that process looks like with several different programs.
Ransomware removal: How to remove file-encrypting ransomware
Once encrypted ransomware gets onto your system, you’re in trouble if you want to keep any unsaved data or anything that hasn’t been backed up (at least without paying through the nose for it). Paying the ransom is tempting, but it’s not always effective. According to Sophos’ 2021 State of Ransomware report, companies that paid a ransom typically only got back around 65% of their data. Just 8% got back all of the data that was held for ransom.
Considering the risks of paying the ransom, if you’re hit with a nasty piece of encrypting ransomware, don’t panic and if you can at all avoid it, don’t encourage ransomware hackers by paying up. You have two alternative options for ransomware removal:
- Hire a professional ransomware removal service: If you have the budget to hire a professional and decide that recovering your files worth the money, this might be the best course of action. Many companies, including Proven Data Recovery and Cytelligence, specialize in providing ransomware removal services. Note that some charge even if the removal is unsuccessful, while others don’t.
- Try to remove the ransomware yourself: This is typically free to do and may be a better option if you don’t have the resources to hire a professional. Recovering your files yourself will typically involve first removing the malware and then using a tool to decrypt your files.
If you’d like to resolve the issue yourself, try these steps:
Step 1: Run an antivirus or malware remover to get rid of the encrypting virus
Important note: Removing the encrypting ransomware virus is not the same as decrypting files. If you’ve been hit by ransomware, you will still need to decrypt or restore the files using other tools.
Refer back to the malware/virus removal instructions provided in the scareware/screen locker removal section above. The removal process in this step will be the same, with one exception: WE STRONGLY ENCOURAGE YOU TO REMOVE THIS VIRUS IN SAFE MODE WITHOUT NETWORKING ACCESS.
There is a chance that the file-encrypting ransomware you’ve contracted has also compromised your network connection. Some variants need to communicate back to the a host server; cutting off that communication can help prevent further action on the part of the hacker that’s infected the system.
Removing the malware is an important first step to deal with this problem. Many reliable programs will work in this case, but not every antivirus program is designed to remove the type of malware that encrypts files. You can verify the effectiveness of the malware removal program by searching its website or contacting customer support.
Step 2: Try to decrypt your files using a free ransomware decryption tool
Again, you should be doing everything you can to avoid paying a ransom. Your next step is going to be to try a ransomware decryption tool. Unfortunately, there is no guarantee that there will be a ransomware decryption tool that works with the ransomware infecting your system. You may have a variant that has yet to be cracked
Kaspersky Labs, McAfee, and several other organizations operate a website called No More Ransom! where anyone can download and install ransomware decryptors, or have ransomware identified.
Kaspersky also offers free ransomware decryptors on its website.
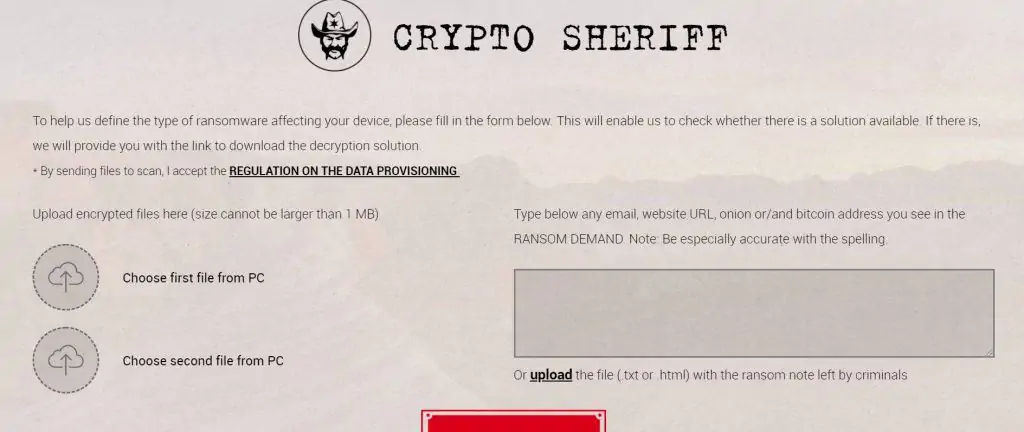
First, we suggest you use the No More Ransom Crypto Sheriff tool to assess what type of ransomware you have and whether a decryptor currently exists to help decrypt your files. It works like this:
- Select and upload two encrypted files from your PC
- Provide a website URL, email address, or onion address, or bitcoin address given in the ransom demand
- If no information was provided in the demand, upload the .txt or .html file with the ransom note
The Crypto Sheriff will process that information against its database to determine if a solution exists. If no suggestion is offered, don’t give up just yet, however. One of the decryptors may still work, although you might have to download each and every one. This will be an admittedly slow and arduous process, but could be worth to see those files decrypted.
The full suite of decryption tools can be found under the Decryption Tools tab on the No More Ransom! website.
Running the file decryptors is usually simple. Most of the decryptors come with a how-to guide from the tool’s developer (many are from Emsisoft, Kaspersky Labs, Check Point, or Trend Micro). Each process may be slightly different, so you’ll want to read the PDF how-to guide for each one where available.
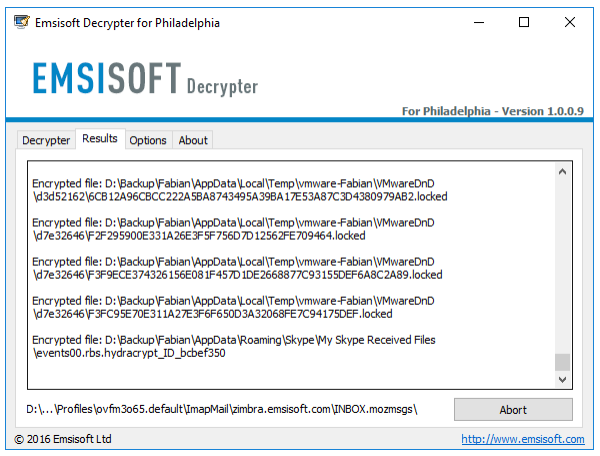
Here’s an example of the process you’d take to decrypt the Philadelphia ransomware:
- Choose one encrypted file on your system and a version of that file that’s currently unencrypted (from a backup). Place these two files in their own folder on your computer.
- Download the Philadelphia decryptor and move the executable to the same folder as your paired files.
- Select the file pair and then drag and drop the files onto the decryptor executable. The decryptor will then begin to determine the correct keys needed to decrypt the file.
- This process may take time, depending on the complexity of the program
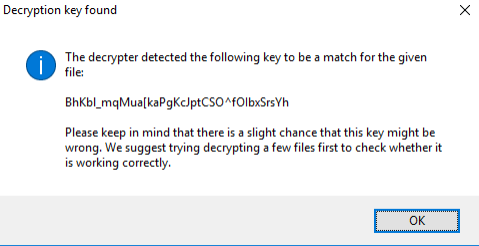
- Once completed, you will receive the decryption key for all files encrypted by the ransomware.
- The decryptor will then ask you to accept a license agreement and give you options for which drives to decrypt files from. You can change the location depending on where the files are currently housed, as well as some other options that may be necessary, depending on the type of ransomware. One of those options usually includes the ability to keep the encrypted files
- You will get a message in the decryptor UI once the files have been decrypted
Again, this process may not work, as you may have ransomware for which no decryptor is available. Still, given there are many decryptors available, it’s best to go this route before paying money for decryption services and long before considering a ransom payment.
Backup option: Wipe your system and perform a complete data restoration from a data backup
Steps 1 and 2 only work when used together. If either fails to work for you, you’ll need to follow this step. Hopefully, you have a solid and reliable data backup already in place. If so, don’t give in to the temptation to pay the ransom. Instead, have an IT professional restore your files and system from data backup.
This is also a reason why bare-metal backup and restoration are important. There’s a good chance your IT professional may need to perform the complete bare-metal restoration for you. This not only includes your personal files, but your operating system, settings, and programs, as well. Windows users may also need to consider a complete system reset to factory settings.
Microsoft provides offers some strategies (mostly preventative) for larger organizations with its Human-Operated Ransomware Mitigation Project.
The history of ransomware
As mentioned, ransomware is not a new concept and has been around for many years. While the timeline below is not an exhaustive list of ransomware, it gives you a good idea of how this form of attack has evolved over time.
- 1989 – “Aids” Trojan, aka PC Cyborg, becomes the first known case of ransomware on any computerized system.
- 2006 – After a decade-busting hiatus, ransomware returns en masse with the emergence of Gpcode, TROJ.RANSOM.A, Archiveus, Krotten, Cryzip, and MayArchive. All are notable for their use of sophisticated RSA encryption algorithms.
- 2008 – Gpcode.AK arrives on the scene. Utilizing 1024-bit RSA keys, it requires a massive effort, beyond the means of most users, to break.
- 2010 – WinLock hits users in Russia, peppering displays with porn until the user makes a $10 call to a premium rate number.
- 2011 – An unnamed Trojan locks up Windows machines, directing visitors to a fake set of phone numbers through which they can reactivate their operating systems.
- 2012 – Reveton informs users their machine has been used to download copyright material or child pornography and demands payment of a ‘fine.’
- 2013 – The arrival of the now infamous CryptoLocker. Ramping up the encryption level, it is incredibly hard to circumvent.
- 2013 – Locker turns up, demanding payment of $150 to a virtual credit card.
- 2013 – Hard to detect, CryptoLocker 2.0 adds the use of Tor for added anonymity for the criminal coder who created it.
- 2013 – Cryptorbit also adds Tor use to its repertoire and encodes the first 1.024 bits of every file. It also installs a Bitcoin miner to milk victims for extra profit.
- 2014 – CTB-Locker mainly targets Russia-based machines.
- 2014 – Another significant development, CryptoWall infects machines via infected website advertisements and manages to affect billions of files worldwide.
- 2014 – A somewhat more friendly piece of ransomware, Cryptoblocker avoids Windows files and targets files under 100 MB in size.
- 2014 – SynoLocker targets Synology NAS devices, encrypting every file it finds on them.
- 2014 – TorrentLocker utilizes spam emails to spread, with different geographic regions targeted at a time. It also copies email addresses from the affected users’ address book and spams itself out to those parties as well.
- 2015 – Another hard-to-detect piece of ransomware, CryptoWall 2.0 uses Tor for anonymity and arrives in a manner of different ways.
- 2015 – TeslaCrypt and VaultCrypt can be described as niche ransomware in that they target specific games.
- 2015 – CryptoWall 3.0 improves on its predecessor by coming packaged in exploit kits.
- 2015 – CryptoWall 4.0 adds another layer to its encryption by scrambling the names of the encrypted files.
- 2015 – The next level of ransomware sees Chimera not only encrypt files but also publish them online when ransoms are not paid.
- 2016 – Locky arrives on the scene, named primarily because it renames all your important files so they have a .locky extension.
- 2016 – Located on BitTorrent, KeRanger is the first known ransomware that is fully functional on Mac OS X.
- 2016 – Named for the Bond villain in Casino Royale who kidnaps bond’s love interest to extort money, LeChiffre program takes advantage of poorly-secured remote computers on accessible networks. It then logs in and runs manually on those systems.
- 2016 – Jigsaw will encrypt and then delete files progressively until the ransom is paid. After 72 hours, all files will be deleted.
- 2016 – SamSam ransomware arrives complete with a live chat feature to help victims with their ransom payment.
- 2016 – The Petya ransomware utilizes the popularity of cloud file sharing services by distributing itself through Dropbox.
- 2016 – The first ransomware worm arrives in the form of ZCryptor, which also infects external hard drives and flash drives attached to the machine.
- 2017 – Crysis targets fixed, removable, and network drives, and uses powerful encryption methods that are difficult to crack with today’s computing capabilities.
- 2017 – WannaCry is spread through phishing emails and over networked systems. Uniquely, WannaCry uses a stolen NSA backdoor to infect systems, as well as another vulnerability in Windows that was patched over a month before the release of the malware (more details below).
- 2018 – The Ryuk ransomware emerges and quickly becomes the worst ransomware to hit the market, becoming bigger than and more devastating than WannaCry. According to Trend Micro, Ryuk had the then largest ransom demand of any encryptor, at $12.5 million USD.
- 2019 – The city of Baltimore is hit by a ransomware variant called RobinHood in May. Nearly every server the city used was taken offline. Hackers demanded 13 Bitcoin, which at the time was around $76,000, but at this time of writing (July 2021) is worth over $428,000 USD. The city’s system was not fully restored until the end of the month. To its credit, Baltimore did not pay the ransom but later stated that ransomware remediation cost the city $18 million.
- 2020 – In May 2020, the IT services provider Cognizant was hit with a ransomware attack so large it cost the company between $50 million to $70 million in revenue. This was notably a “Maze” double-threat, as the hackers not only encrypted the data but also created a copy of Cognizant’s data and then threatened to leak the data if their demands were not met.
- 2021 – In May 2021, Colonial Pipeline, a company responsible for transporting fuel for a large percentage of the US East Coast, was hit by a ransomware attack thanks to a compromised password. The attack resulted in reduced fuel capacity in over a dozen states and over two weeks of fuel shortages for millions of people. It was the first time a country’s important infrastructure suffered from a ransomware attack. Colonial Pipeline later admitted to paying the ransom, but in a rare occurrence, the US government later recovered a majority of the ransom money.
- 2022 – The country of Cost Rica suffered several weeks of major ransomware attacks in 2022. These halted automatic payment services, and disrupted tax and customs systems. The attackers, thought to be the Russian-based Conti gang, demanded a $20 million ransom. The Cost Rican government refused to pay the ransom.
- 2023 – The US city of Dallas was attacked in May 2023 by the Royal ransomware gang. The attack forced websites for the police department and city hall offline and caused Dallas courts to close for more than three weeks. Officials did not confirm whether a ransom was paid. In August 2023, the City Council voted to set aside almost $8.6 million to pay for the response to the attack.
Ransomware FAQs
Can you remove ransomware?
Yes, you can remove ransomware. Antivirus software can delete ransomware from your computer or system. However, removing the ransomware won’t decrypt any files that have been encrypted by the ransomware virus that infected your system.
How does ransomware get on your computer?
Ransomware can get on your computer the same way as other malware. Common attack vectors include:
- Installing infected files
- Clicking on links on infected websites
- Plugging unknown USB drives into your computer
- Account or system hacking due to poor password security
- Brute-force attacks from hackers
Should you pay ransomware?
No, you should not pay the ransom if you get infected with ransomware. Paying ransoms not only encourages this type of attack but may not result in the release of your files. It can also be exceptionally expensive. The average ransom demand was $1.54 million in 2023, which is almost double the 2022 figure of $812,380.
What happens if I get ransomware?
If you get ransomware on your computer or network, the malware will begin encrypting your files. Ultimately, it will lock you out of your system and demand payment (often via cryptocurrency) for the release of the files via a decryption key.

Hi. My pc was infected by a virus and all my my files has this ext. File name .gerosan
I dont know what to do anymore. Please help
Hi Jackie!
Sorry that happened to you. Please refer to the bottom of the article regarding removing ransomware. If that doesn’t help (there are a lot of variants out there, and we haven’t covered removal for all of them), try contacting an official ransomware removal service or company, or using an online guide specifically for removing the gerosan ransomware.