Maintaining online anonymity is no easy task. Today’s ad-driven and heavily surveilled internet ecosystem endeavors to accomplish the exact opposite result. Be it for national security or to sell you a smartphone, governments, and companies want to know everything they can about you. To shake them off your trail is no simple matter.
Being anonymous definitely has its benefits, and certain freedoms come with being unrecognizable and untraceable, but it also requires sacrifice. Many of the conveniences of the modern web were built around profiling, tracking, and analyzing user behavior.
Bearing that in mind, there are some steps you can take to protect your privacy when using the internet. We’ll lay those steps out for you in this article, along with the tools you’ll need to stay anonymous and hidden online.
What’s the difference between online privacy and anonymity?
The terms “privacy” and “anonymity” are often used interchangeably, but there is a subtle distinction between the two.
When you are anonymous, your identity is hidden. This means that no one can know who you are, where you come from, or what you do. Anonymity is often used for security purposes, such as when conducting financial transactions or accessing sensitive information.
Privacy, meanwhile, is about keeping your information private. This means that only you can access it, and no one else can see it. Therefore, privacy is vital for protecting your personal information from prying eyes.
Tor
No anonymity checklist would be complete without Tor. This network of volunteer nodes around the world is synonymous with anonymity. Tor, short for “the onion router”, allows you to encrypt your internet traffic and, each time you connect to a web server, route that traffic through a random array of nodes before heading to the final destination.
There are dozens of ways to use Tor from many different devices, but the Tor Browser is the most popular. Simply installing this Firefox-based application on your Mac, PC, or Android device will allow you to browse the web anonymously. iOS users don’t have any official support from the Tor project, but Onion Browser seems like a decent option.
Tor does have a few downsides. For one, it’s slow. Tor isn’t suitable for streaming video or torrenting files. You can browse the web, and that’s pretty much it due to the lack of volunteer resources and competing traffic from other users.
Secondly, even though your internet traffic is encrypted and untraceable, an internet service provider can still detect whether or not you are using Tor. This alone might be enough to raise suspicions, as Tor is often used for criminal activity online. Your ISP could choke your bandwidth, send you a cease and desist letter, or report you to the authorities even if you haven’t done anything wrong.
For this reason, we advise Tor users to use an obfuscation tool like Obfsproxy, turn on a VPN when using Tor, or both. Obfsproxy is a Tor project that makes encrypted Tor traffic look like normal, unencrypted traffic so that it doesn’t draw undue attention. More on VPNs further down.
Finally, there’s considerable speculation that the US government successfully used traffic analysis on Tor on at least a few occasions that led to arrests, including that of the infamous Dread Pirate Roberts of the Silk Road illicit goods marketplace. Rumor has it that governments also operate and monitor activity on several Tor exit nodes. None of these allegations come with concrete evidence, so take it with a big grain of salt.
Live OS
A browser is suitable for escaping targeted advertisements and occasional visits to the DarkNet, but those who require complete anonymity will need a more nuclear option. While no one can track your browsing activity on Tor Browser, for instance, chances are you’ve still got other applications running in the background. These applications–word processors, video players, update managers–send data to the web. Rumor has it that authorities have used unencrypted error reports from the Windows operating system to find people. Windows 10 includes a litany of tracking software that’s enabled by default.
You could disable all of those settings and uninstall all of your applications, but that’s not very practical. Instead, we recommend a live operating system. Live operating systems can be installed on USB drives or DVDs. By tweaking a few settings in your computer’s bootloader, you can launch an entirely independent operating system from a thumb drive on your everyday laptop.
Tails is the official live OS from the Tor Project. All internet traffic–not just web browsing–goes through the Tor Network. The OS leaves no trace on your computer, and all instant messages, emails, and files are encrypted. It’s simple to use and is designed to be idiot-proof.
If Tails doesn’t seem suitable for whatever reason, another option is Whonix. Whonix isn’t an independent live OS. Instead, it runs in a virtual machine on your existing operating system. It has all the advantages of Tails (it also uses the Tor Network), plus it is designed so that IP address leaks–which can be used to track users–are impossible. The downsides are that it takes a reasonably powerful computer to run a virtual machine, and it’s rather complicated to set up.
Other options are also on the table. Kali, Qubes, and ZeusGuard are all alternatives to Tails and Whonix worth considering. Do your research and figure out what’s best for you.
What about private/incognito browsing?
Most mainstream web browsers like Chrome, Firefox, Edge, and Safari come with an option for “private” or “incognito” browsing. This opens up a special browser window that doesn’t store cookies, record your browsing history, or keep other identifiers.
But that is not enough to keep you anonymous online. These privacy modes merely protect your privacy from other users on the same device or who log into your browser using the synchronization feature. So you can prevent your spouse and kids from seeing what sites you visited, but it won’t hide your online activity from your internet service provider, apps, or websites.
You can pair private browsing with a VPN for improved anonymity and privacy. The VPN will prevent your activities from being tracked and recorded by your ISP and other third parties. However, Tor browser is still recommended for maximum anonymity.
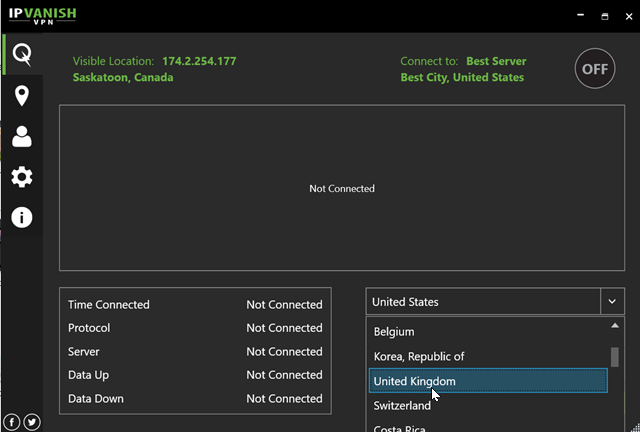
Logless VPN
A VPN, or virtual private network, encrypts all of a device’s internet traffic and then routes it through an intermediary server in a location of the user’s choosing. The end result is that the device’s IP address is masked and third parties–including ISPs–cannot monitor traffic.
Most VPN providers utilize shared IP addresses on their servers. Multiple users–dozens, hundreds, and even thousands–are assigned a single IP address. This makes it nearly impossible to trace the activity of a single person in the pool.
VPNs are built for privacy and not anonymity, however, so we caution against using them alone if you want to remain hidden truly.
Using a VPN requires a certain degree of trust in your VPN provider and the entities that host their servers. Very few VPN providers own their own physical server infrastructure. Your traffic is encrypted on your local device and remains encrypted until it arrives at the VPN server. It is then decrypted before being sent to its destination. For a brief moment, your activity is visible to the VPN provider.
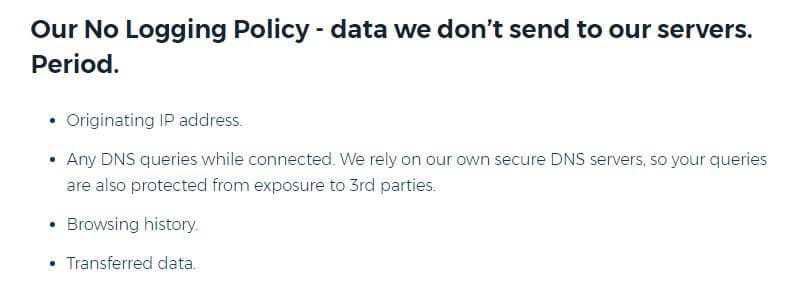
This is why we highly recommend logless VPNs. Branded with a “logless”, “no-logs”, or “zero-logs” policy, this means that the VPN provider does not store any information about the content of users’ traffic. Assuming the VPN provider is telling the truth, that’s a good thing.
But it’s not so simple as that. Some VPN providers claim to be logless, but in reality, they still store metadata. Depending on how anonymous you want to be, this is a nuance to be wary of. Metadata doesn’t contain any information about the contents of your traffic, but it can include details such as when you used the VPN, for how long, how much data was transferred, and even your original IP address. Always skim through a VPN provider’s privacy policy for devilish details like these.
Even the few true zero-logs VPNs out there require customers to trust them. There’s no way of knowing whether they are being honest and how they will react when faced with a government subpoena. For the highest level of anonymity, then, avoid VPNs based in the United States and Europe, where data retention laws and government intelligence agencies could put your data at risk.
Also, try combining your VPN with Tor. Simply running Tor Browser while connected to the VPN makes tracing the user twice as difficult. VPNs can also be configured manually in live operating systems like Tails.
Related:
Logless DNS
When a URL is entered into a browser, a request is sent to a DNS nameserver to look up the IP address that matches the URL. This enables two computers on the internet, such as your phone and a website, to find each other and establish a connection. This process usually takes place in a fraction of a second.
Even when using a proxy like a VPN, these DNS requests can be sent outside the encrypted tunnel to the default nameserver. By default, DNS requests usually go to and are recorded by a nearby server operated by the user’s ISP.
If this happens when using a VPN, it’s called a DNS leak. Many VPN providers offer DNS leak protection, which ensures that all internet traffic, including DNS requests, are directed through the VPN. These VPNs typically operate their own DNS servers, which won’t record which websites you visit if they meet the logless criteria outlined above.
Even if a VPN advertises DNS leak protection, that statement often only applies to IPv4 DNS leaks. IPV6 DNS requests can still travel on the default network and be picked up by both web servers and ISPs. It would be great if more VPNs would set up IPv6 DNS servers to handle this situation, but at the moment, the best solution is simply to disable IPv6 in the device’s internet settings. This tool checks for IPv6 and IPv4 DNS leaks.
If the VPN you use lacks DNS leak protection, or you aren’t using a VPN at all, try opting for a public no-logs DNS server. You can change your device’s DNS settings so that requests aren’t sent through your ISP. We recommend DNS.WATCH or OpenNIC.
Burner emails
It should go without saying that remaining anonymous online means not logging into any of your existing accounts. But since many apps and websites require users to sign up, you’ll need an email address or two.
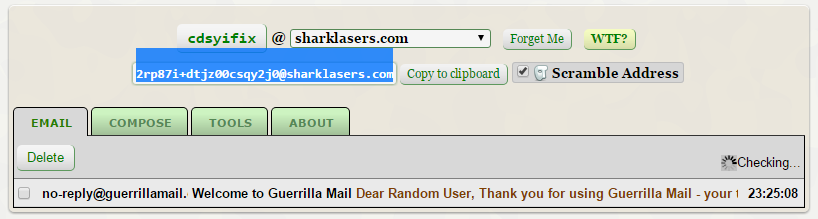
Several services offer free fake and burner email accounts. For one-off registrations and messages, we recommend Guerilla Mail. No registration is required, and it includes a password manager to help remember the passwords associated with those accounts.
For a more long-term untraceable email account, the best option is probably Proton Mail. This end-to-end encrypted service is open-source and uses zero-knowledge apps for web and mobile.
Zmail is another alternative. It allows you to send emails from fake addresses.
Never use your own email account when trying to be anonymous. Don’t even read your email or log into the account. If you want to send encrypted emails from a burner account, you’ll have to set up new PGP or S/MIME keys.
Cryptocurrencies
If you want to make an anonymous purchase or donation, cryptocurrencies are superior to PayPal and, obviously, credit cards. That doesn’t mean that you can just open up a Bitcoin wallet with a big exchange like Coinbase and start spending, though.
There’s a big misconception that Bitcoin is always anonymous, when in fact, the very nature of blockchain technology means every transaction is tracked and verified. This publicly available ledger can be analyzed so that the wallets you use and your transactions can be linked to your identity.
By analyzing the activity that is visible to anybody on the public blockchain, an observer may well be able to link your personal identity with all of the wallets you use and, therefore, your entire transaction history. In a way, this makes Bitcoin even less private than a bank account.
To get around this, use wallets that change your Bitcoin address after each transaction. This makes you harder to trace. Use a bitcoin mixing service, which pools your bitcoins with other people’s and mixes them up before making a payment to the receiver.
Perhaps the most difficult part is anonymously buying bitcoins in the first place, as doing so requires fiat currency. Private deals and peer-to-peer exchanges like LocalBitcoins are not for the careless, but they are the best means of anonymously getting your hands on coins.
Remember that Bitcoin isn’t the only player in town, although it is the biggest. Monero is popular for being largely untraceable. Litecoin, DarkCoin, Ethereum, and Dogecoin are popular as well.
Search engines
Google keeps track of every search query and the links you click on. If you’re using Tor, this doesn’t matter so much, but it’s still a good idea to opt for an alternative.
DuckDuckGo is perhaps the most popular search engine that doesn’t track or profile users. It can be set as the default search engine in your browser.
DuckDuckGo is a fully independent browser, so, let’s be honest, the results won’t be as good as Google’s. Luckily, there’s a way to get Google results without Google.
StartPage removes all your identifying information and submits a search query to Google on your behalf. It doesn’t log or track user activity. All search results are displayed with a proxy link beneath them, allowing you to click through to any site while retaining your privacy through a proxy.
File transfers
The moment might arise when you need to anonymously send a file that’s too big for an email attachment. If you’re a whistleblower who wants to leak a large trove of damning documents to the public, uploading the files to Dropbox won’t do.
FileDropper is a simple and convenient solution that allows uploads of up to 5GB with no registration required. WeTransfer is another option that allows files up to 2GB without signing up. For these types of services, upload a file and then send the link to whoever you want to receive it.
Remember to access the site using Tor and share the links using a burner email or some other anonymous method, as the website might well be gathering information on site visitors despite the fact that registration isn’t required.
Choose your browser extensions carefully
The Tor Browser has very little support for extensions, and there’s a good reason for that. Advertising companies are getting smarter about how they track users. One of the most advanced methods is called fingerprinting. By gathering information about your web browser–what extensions are installed, what device you use, what language you read in, etc–ad tech companies can create a “fingerprint” that identifies a user. Fingerprints are superior to IP addresses because they don’t change if a user switches wi-fi networks or connects to a VPN.
Many extensions can help maintain your privacy–ABP, Disconnect, Privacy Badger, HTTPS Everywhere, etc–but they also contribute to a more well-formed fingerprint. This is one of several reasons it’s so difficult to be anonymous on a popular browser like Firefox or Chrome.
If you want to test how well your browser protects you from tracking, head over to the Panopticlick website. This tool made by the Electronic Frontier Foundation (EFF) can show you in excruciating detail how an ad agency can identify your browser using a unique fingerprint.
Besides fingerprinting, browser extensions can communicate with servers in the background without your knowledge, potentially logging metadata that could help identify you and your online activity.
Read more: 75+ free tools to protect your privacy online
Encrypted communications
Besides email, you’ll also want to cover your tracks when sending messages and making calls. Encryption is more focused on privacy than anonymity; even if a message is encrypted, a snoop still knows who the sender and receiver is. But if you’re going through the trouble of being anonymous, you might as well take every precaution.
Signal is the premier app for encrypted voice calls on smartphones. It also includes instant messaging. Users can verify the identities of their contacts by comparing key fingerprints.
Encrypted backup
Even anons need to back up and store large files and sometimes allow other people to access them. Stay away from Google Drive and Dropbox, as these contain no real privacy protections such as encryption and aren’t anonymous at any rate.
Backups are best done locally to an encrypted external hard drive. Crashplan offers a free version of its software that makes this easy.
If you want a cloud solution, it will require trusting a provider. Seek out a “zero-knowledge” service that allows you to set your own encryption key. SpiderOak, iDrive, BackBlaze, and Crashplan all offer this option, which prevents the provider from decrypting your files.
If you insist on using Google Drive, Dropbox, or some other unencrypted storage provider, you can always encrypt your files before uploading them to the cloud.
Secure your webcam
It’s been proven that webcams can be remotely activated and used to spy on users. The head of the FBI and Mark Zuckerberg both go so far as to put tape over their webcams for this very reason.
Webcams are usually remotely activated through malware, so a real-time virus scanner and regular system scans can prevent this from happening. If your laptop has an LED light that turns on whenever the webcam is active, make sure it’s enabled. If you don’t want to put tape on your webcam, make sure you close the laptop when not in use.
Learn more about securing your webcam here.
Secure your wifi router
Many of us never bother changing the settings that our wifi routers came with from the factory. Unsecured routers can make users extremely vulnerable to nearby snoops. Routers can be used to intercept, read, and modify internet traffic. If you’re on someone else’s wifi network, be sure to use a VPN.
If you want to remain anonymous, it’s important to change the router’s login credentials, update the firmware, set the strongest level of encryption (usually WPA2), restrict inbound and outbound traffic, turn off WPS, disable unused services, check port 32764, enable and read logs, and log out of your router when finished.
You can learn more about how to take all of these steps and more in our guide on securing wireless routers.
iOS and Android are not optimal for anonymity
If you’re choosing between iOS and Android based on which is more anonymous, go with Android. But don’t get comfortable and think you can be totally anonymous on either.
It is far more difficult to be anonymous on a smartphone than on a computer. Anonymity tools for Tor just haven’t matured to a point where they work well on mobile yet. Apple and Google are too deeply embedded in these devices.
There are no official Tor browsers for iOS. There are no live operating systems that can be utilized by smartphones like TAILS for desktops.
Smartphones have IMEI numbers, MAC addresses, and possibly vulnerable firmware that cannot be altered and can be used to identify a specific device when connected to the internet. Because Android is usually modified by manufacturers, it’s difficult to audit and keep up with each device’s potential vulnerabilities. Apple and Google have the power to track almost every iOS and Android phone, respectively.
Apps constantly communicate with servers over the internet, passing data back and forth that could be used to track users. Even something as basic as a keyboard could be used to monitor activity. Cameras and microphones can be hacked into to spy on users. Any time a device receives a signal from a cell tower, the device’s location can be traced. Simply put, there’s just too much that could go wrong on Android and iOS that the user cannot see.
While making smartphones completely anonymous might be a futile effort, they can be made significantly more private. Android devices can be encrypted, and iPhones are all encrypted by default. Use VPNs to encrypt internet traffic, and set up a self-destruct sequence if the passcode is entered incorrectly too many times.
Finally, companies like Silent Circle make Android-based smartphones with security first in mind. The Blackphone, for instance, is fully encrypted and runs several “virtual phones” to compartmentalize data. Silent Circle also has a subscription service to make iPhones private. Again, the key difference is that this phone is focused on privacy, not anonymity. While the contents of the phone are protected, the same isn’t necessarily true for the identity of the user.
Related: What is the best VPN for iPhone and iPad users?
Be wary of the Internet of Things
The Internet of Things is the network of devices and objects that are embedded with the ability to connect to or be controlled over the internet – such as smart appliances, music, or lighting systems. These present a whole new wave of opportunities for hackers and snoopers. Security has, unfortunately, been an afterthought for many IoT manufacturers. A simple log of when your smart air conditioner is activated, for example, can tell a lot about a person’s daily routine. Critics have warned against devices like the Amazon Echo, which are always listening for input even when deactivated.
Depending on your online activity, this can be a threat to a user’s anonymity. Use IoT devices with caution.
Make a checklist
No anonymity tool, even Tor, is perfect. But that doesn’t mean they aren’t effective. While a well-funded corporation or government agency could spend huge amounts of time and money running traffic analysis on the Tor network to find the person they are looking for eventually, it’s much more likely that person will make a mistake and drop a clue somewhere along the way.
So how do you avoid making mistakes? The same way surgeons and other high-risk occupations do: with lists. Every time you want to be anonymous online, start from the beginning of your checklist. Write it down on a piece of paper, but don’t include any login credentials or other identifying information. Here’s what one might look like based on everything discussed:
- Connected to a logless VPN
- Connected to the internet through Tor Browser/Tails
- DNS settings are configured to use a logless DNS
- Logged out of all online accounts
- Closed all apps and background services connected to the web
- All tracking in my browser and OS are turned off and blocked
- Emails are sent using burner accounts
- New accounts registered and logged in with burner emails
- Search with DuckDuckGo or StartPage
- Bitcoins are properly mixed and using a third-party wallet
With a standard protocol in place, you can drastically reduce the chances of making mistakes. Don’t be overconfident. Anonymity is something you can get right 100 times, but it only takes one misstep for it all to crumble.
Got more tips? Let us know in the comments.
How to travel anonymously
Traveling anonymously, especially internationally, can be challenging due to the increased use of tracking technologies. However, if you are interested in this, here are some general tips we recommend:
- Use of Pseudonyms: When booking flights or accommodations, consider using a pseudonym, although this may have limitations, especially when boarding flights.
- Avoid Electronic Tracking: Be mindful of your electronic devices, as they can be used to track your movements. Consider using devices that are not easily traceable.
- Minimize Digital Traces: Use a VPN to browse anonymously and consider using a local SIM card instead of relying on finding Wi-Fi.
- Respect Local Laws: Be aware of the laws in the countries you plan to visit, as some countries may have specific requirements for travelers.
- Inform a Trusted Contact: Give a copy of your essential travel details to someone reliable back home so they can keep track of your whereabouts.
It’s important to note that while these measures may help minimize tracking, they could be more foolproof. Always prioritize your safety and be mindful of the potential limitations and risks of traveling anonymously.
FAQs about staying anonymous online
Is it safe to use public Wi-Fi networks?
It is generally not recommended to use public Wi-Fi networks, as they may be insecure and vulnerable to hackers. If you must connect to a public network, use a VPN and avoid sharing sensitive information.
What level of encryption is the most secure?
The most secure level of encryption is 256-bit encryption. This type of encryption uses a key that contains 256 0s and 1s, making it extremely difficult for unauthorized users to decrypt the data or gain access to it. It is widely considered the highest level of security available today, as it would take billions of years for a computer to crack the code. This makes 256-bit encryption a popular choice for organizations and individuals who need to protect sensitive data from cyber criminals or malicious actors.
What information can my ISP see without a VPN?
Without a VPN, your Internet Service Provider (ISP) can see all the websites you visit and any data sent over the internet. They can also track which IP addresses you connect to and potentially monitor your online activity. They can see everything you do online, including emails, web searches, and purchases. A VPN can protect your online data from being monitored by your ISP, as it creates an encrypted connection between you and the internet. This makes it much harder for your ISP to see what you are doing online, keeping your activities private and secure.