Instead of going into the finer details on what encryption is (don’t worry, we’ve got an overview below), we’re delving into some key encryption stats. We’ve got some juicy facts and figures about how encryption has played its part over the past decade and some of the things to watch out for.
If you’re ready, let’s get going.
What is Encryption?
Okay, the basics. Encryption involves sending information converted into secret code, known as cryptography. When information is encrypted in computing, the true meaning of the data is hidden until it reaches the recipient, with encrypted text known as ciphertext. Once it reaches the intended recipient, encryption algorithms decode the information to reveal the contents. Unencrypted text is referred to as plain text, meaning no encoding occurs.
Phew! Enough of the computer science lesson. Let’s get into a real-world example.
Let’s say you have a customer invoice saved somewhere on your server containing credit card details. You obviously wouldn’t want the wrong people getting their hands on this sensitive information. The data is encrypted at rest to avoid this happening, which roughly translates into altering your customer data into a different data form.
When data is encrypted at rest, an algorithm is used to ensure anyone without the encryption key cannot understand the data as they have no means of decoding it. The customer data remains secure by only allowing authorized personnel to access the files.
Encryption Stats You Need to Know About
1. Cost of a mega data breach has grown significantly
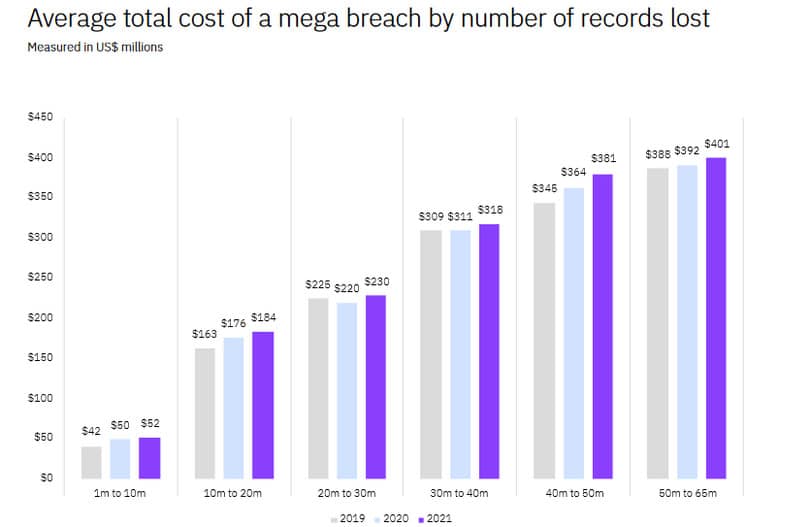
A data breach affecting more than one million compromised data records is rare, but not unheard of. IBM’s cost of a data breach 2021 report found that the average cost for 50 million to 65 million records involved in a data breach is an eye-watering $401 million.
2. There’s a shortfall of organizations fully encrypting internet communications
The 2020 Use of enterprise encryption technologies worldwide survey by Statista found that 56% of enterprise respondents said their internet communications had extensive encryption deployed. 27% had only partially deployed encryption for their internet communications.
3. Companies leave sensitive files open to attackers
A staggering 53% of companies left over 1,000 sensitive files and folders unencrypted and open to all of their employees, a 2019 global data risk report by Varonis found.
4. Protecting passwords is at an all-time high
Cybersecurity Ventures estimated over 300 billion passwords worldwide would need to be protected in 2020.
5. Organizations aren’t updating legacy passwords
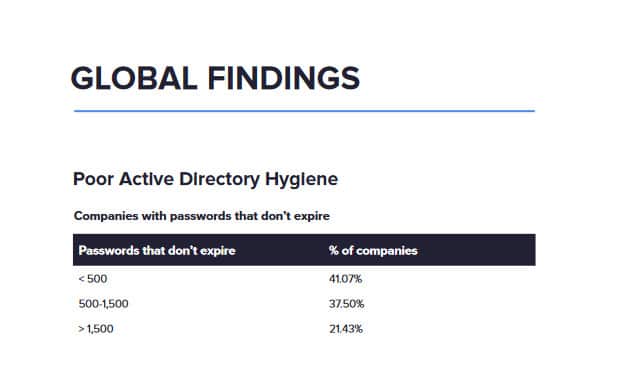
A Varonis 2021 financial data risk report found that around 21.43% of companies worldwide have 1500+ account passwords that don’t expire.
6. Tightening encryption tactics decreases the financial implications of attacks
By using robust encryption and enforcing cybersecurity tactics, businesses can save on average $1.4 million for each attack, reports the Ponemon Institute.
7. API gateway encryption decreases the likelihood of a data breach
The Imperva 2020 Cyberthreat Defense Report showed that 93% of companies plan to or already have API gateway encryption in place to avoid a data breach.
8. Data without encryption is compromised more often
Seven million unencrypted data records are compromised every day, according to the world in data breaches report by Varonis.
9. Poor encryption results in lengthy recovery periods after a breach
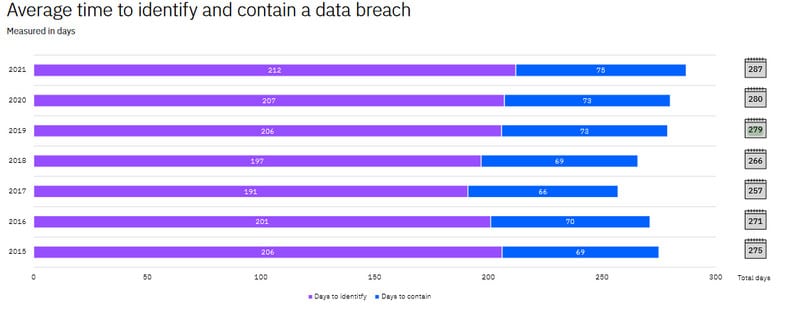
IBM’s cost of a data breach report estimates that it takes 287 days to detect and contain a data breach caused by substandard encryption in 2021.
10. More websites are using the default HHTP protocol
The historical trends survey by W3 Techs shows that the default HTTPS protocol is used by 77.5% of all websites.
11. Consumer data is the top reason to encrypt
Entrust’s Global Encryption Trends report found that customer data is listed as the top encryption priority among the enterprises surveyed. However, only 42% of respondents use encryption to secure their customer data in 2021.
12. Organizations struggle to locate cloud-stored sensitive data
Entrust’s 2021 report also showed 65% of enterprises don’t know where sensitive data is stored across multiple clouds. Two or more cloud solutions are used by 2 out of three organizations.
13. Businesses with consistent encryption strategies highest in 16 years
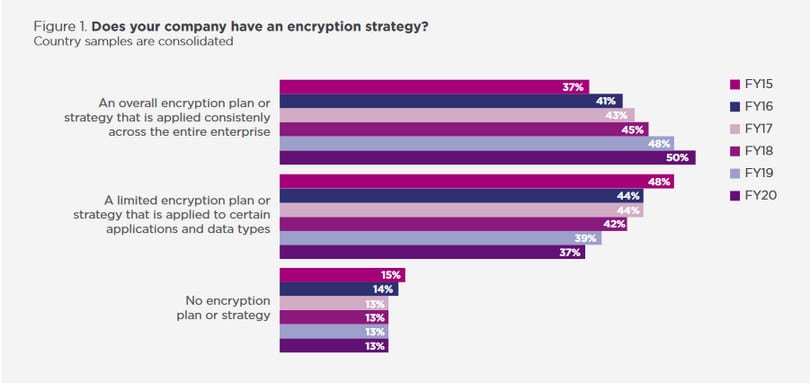
The Ponemon Institute reached a new milestone, with 50% of organizations revealing they have a consistent encryption strategy. This is the highest figure in the history of the study.
14. Managing keys is regarded as a painful process
56% of respondents in the Ponemon Institute’s study rate encryption key management as painful. This suggests the process of key management is challenging for most.
15. Files transferred to the cloud are often unencrypted
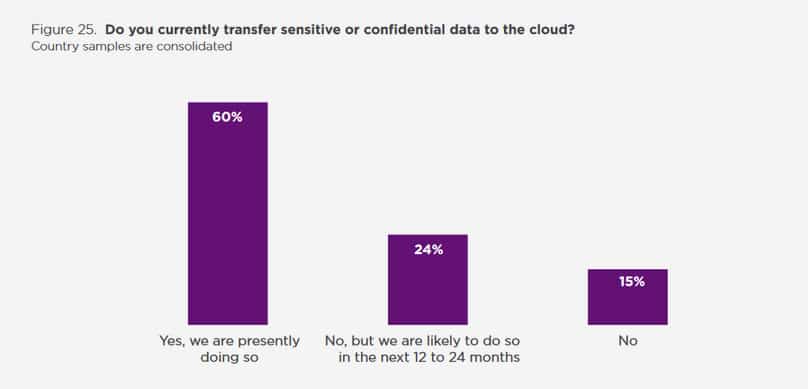
In Ponemon’s 2021 report, 60% of surveyed organizations revealed they transfer sensitive files to the cloud regardless of whether they are encrypted or unreadable via data masking or tokenization. Another 24% say they aim to encrypt sensitive files in the next two years.
Key Elements of Encryption
Encryption protects the data being sent and received from third parties. It applies to a range of day-to-day activities that you might not have considered. These include encrypting a credit card transaction used to purchase something online. When someone uses an ATM, a layer of encryption is used to authenticate your details before making a cash withdrawal. When you use your smartphone (like Apple Pay) to buy something, there’ll also be encryption to process the payment.
Information, key management, and the encryption engine are the main elements of an encryption process. The purpose of the encryption is to disguise the message, so at the beginning of the process, the sender should determine the best key variable to use to make the encoded message unique. Symmetric and asymmetric are the most common ciphering techniques used.
Asymmetric ciphers usually use public key infrastructure, consisting of two logically linked but different keys: public and private. This method’s most widely used example is RSA, which allows a message to be encrypted with a public or private key. Anyone can use the public key to encrypt a message, but only the private key can decrypt it.
Symmetric ciphers use secret single encryption keys. Unlike asymmetric encryption, the same key can be used to encrypt and decrypt data. These keys are often referred to as shared secrets, as the key needs to be shared with the recipient systems to enable decryption of the message.
Symmetric ciphers are more efficient, so asymmetric ciphers are often used to privately encrypt and exchange symmetric keys.
The consequences of Poor Encryption
Weak encryption such as the cryptography method used in MD5 and SHA1 hashing can lead to a range of issues such as brute force attacks, easily allowing attackers to intercept and steal your data.
One such attack on data is known as a man-in-the-middle attack. A MITM involves an attacker placing themselves between a conversation exchange between two entities. The third party (the hacker) relays messages without the other two parties knowing. Using a MITM with the example of a chat message exchange, the hacker could read the messages without the other parties knowing.
Unencrypted Internet Reveals Everything About You!
Did you know that your ISP (Internet Service Provider) records everything you get up to online? No jokes here!
When you use the internet, regardless of whether you’re on a desktop PC, your laptop, a smartphone, or tablet, your internet activities are visible to your ISP and anyone else spying on your connection.
When you hook up to the web, you are assigned an IP address by the guys you pay for your broadband. That IP address acts as an identifier personal to you, meaning the websites you visit, the files you download, the games you play, or the movies you stream are all being traced back to you.
Additionally, when you go to your local coffee shop and connect your laptop to public wifi, there’s no wi-fi encryption (like WPA2 that you’d expect with your home wi-fi) meaning the websites you visit could be visible to attackers.
Fortunately, there’s a way of encrypting your connection – we’re talking about using a VPN (Virtual Private Network) to assign you an anonymous IP address that’s untraceable by anyone.
I’d recommend NordVPN due to its robust encryption and ease of use. Sign up for a NordVPN account, install the app on the device you want to encrypt your internet for, and surf like nobody’s watching.

