Comparitech is appealing to all app developers who use Firebase to check their configuration urgently.
Firebase is used by an estimated 30 percent of all apps on the Google Play Store, making it the most popular storage solution for Android apps.
4.8 percent of mobile apps using Google Firebase to store user data are not properly secured, allowing anyone to access databases containing users’ personal information, access tokens, and other data without a password or any other authentication.
Comparitech’s security research team led by Bob Diachenko examined 515,735 Android apps, which comprise about 18 percent of all apps on Google Play.
In that sample, we found more than 4,282 apps leaking sensitive information. If we extrapolate those figures, an estimated 0.83 percent of all Android apps on Google Play leak sensitive data through Firebase. That’s roughly 24,000 apps in total.
We notified Google on April 22 and provided a report detailing our findings.
A Google spokesperson responded to Comparitech, saying:
“Firebase provides a number of features that help our developers configure their deployments securely. We provide notifications to developers about potential misconfigurations in their deployments and offer recommendations for correcting them. We are reaching out to affected developers to help them address these issues.”
Although our team only examined Android apps on the Google Play Store, Firebase is a cross-platform tool used across several operating systems and platforms. These misconfigurations likely impact many more apps beyond Android.
What data is exposed?
The vulnerable applications identified by our team have been installed 4.22 billion times by Android users. Given the average smartphone user has between 60 and 90 apps installed, the chances are high that an Android user’s privacy has been compromised by at least one app.
The exposed data included, but was not limited to:
- E-mail addresses: 7,000,000+
- Usernames: 4,400,000+
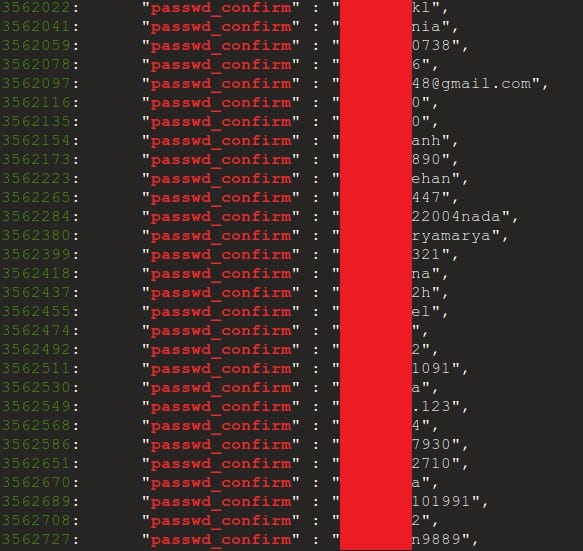
- Passwords: 1,000,000+
- Phone numbers: 5,300,000+
- Full Name: 18,300,000+
- Chat messages: 6,800,000+
- GPS data: 6,200,000+
- IP addresses: 156,000+
- Street addresses: 560,000+
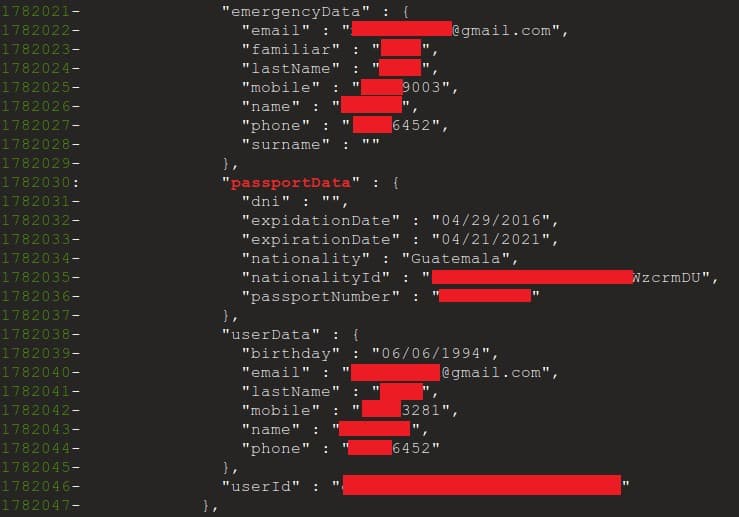
Other data ranged from credit card numbers to photos of government-issued identification.
By Google Play category, games exposed their databases most frequently, followed by education apps:
Most exposed databases gave attackers write access
Of the 155,066 Firebase apps analyzed, 11,730 had publicly exposed databases. 9,014 of them even included write permissions, which would allow an attacker to add, modify, or remove data on the server, in addition to viewing and downloading it.
Write access could allow an attacker to:
- Inject data into an application – allowing hackers to add a fake headline to a popular news app for example.
- Phish and scam application users
- Spread malware
- Corrupt the application database
Of the 11,730 publicly exposed databases, 4,282 leaked user information. The rest were empty or contained no user information, but were still vulnerable to attack.
Google scrubs exposed databases from search results
A common Firebase misconfiguration allows attackers to easily find and steal data from storage. By simply appending “.json” to the end of a Firebase URL, the attacker can view and download the contents of vulnerable databases.
A December 2019 report shows that Google scrubs these vulnerable database URLs from its search results. However, they are still indexed by other search engines like Bing.
Methodology
To find exposed databases, our security team searched each app’s resources for strings of text indicating that Firebase is being used, such as those ending in “.firebaseio.com”.
Firebase provides a simple REST API to access stored data. All of the data is stored in JSON format, so public databases can be accessed by making a request to the database URL appended by “.json”.
For example: https://example.firebaseio.com/.json
If the database is publicly exposed, this request will return the full contents of the database. Otherwise, it returns an “access denied” message.
Some of the databases were too large for one download request, so researchers used a “shallow” keyword option to limit the depth of the response, iterating only through keys and downloading the database chunk by chunk.
Researchers also checked for write access by making a PUT request to create a new node with some value and then deleting it.
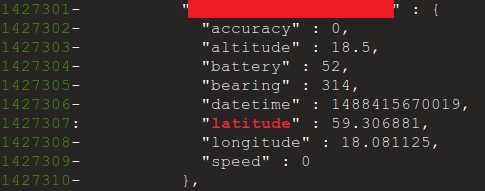
To analyze data stored in exposed databases, researchers searched for patterns corresponding to sensitive information such as email addresses, phone numbers, passwords, secret tokens, etc. They then manually checked collected information for false positives.
Empty (but still vulnerable) databases were removed from results.
All the accessed data was destroyed and the research itself is fully compliant with white hat standards and procedures.
Our recommendations
For app developers, most Firebase misconfigurations are entirely avoidable. We recommend developers follow the guidelines in Google’s own Firebase documentation.
Those recommendations include:
- Implement proper Firebase Database Rules
- Prevent unauthorized users from accessing sensitive information
- Don’t store passwords in plain text
For users:
- Don’t reuse the same password across multiple accounts. Use a password manager to generate and store strong random passwords
- Use only trusted applications with a high number of reviews and installs
- Be aware of what information you share with an application
- Do not share sensitive personal information such as home address, photos of government ID, Social Security numbers, etc
About Firebase
Firebase is Google’s mobile app development platform. It was launched in 2011 and acquired by Google in 2014.
App developers use Firebase for:
- Authentication
- Hosting
- Cloud storage
- Realtime databases
- Analytics
- Messaging
- Admob integration
- Machine learning




Hi
Thank you for this report. I found it very informative.
Where can the public get a list of the affected applications so we can decide if we want to continue to use them or not?
Google is handling disclosure of the issue to all affected app developers, but we can’t guarantee all of them will take action. So in order to protect end users, we are not releasing the list of apps.