Sensitive data refers to information that must be protected to prevent harm to individuals, organizations, or systems. It includes details that, if disclosed, could compromise privacy, security, or confidentiality. Sensitive data often encompasses Personally Identifiable Information (PII), such as names, Social Security numbers, financial information, health records, and biometric data. PII is a subset of sensitive data, specifically focusing on data that can identify an individual. Besides PII, there are other types of sensitive data like reports, APIs, IPs, and more.
The first step to safeguard sensitive data is to identify them, and based on their characteristics or patterns, classify and store them in a safe place. Though it is possible to manually do this classification, it can be time-consuming, error-prone, and may open security risks. To avoid these problems, organizations turn to sensitive data discovery tools.
These tools can address the following pain points in an organization.
- Organizations store data in multiple locations, and it’s hard to know where sensitive data is located.
- Failure to protect sensitive data can lead to regulatory fines.
- Increases the risk of data breaches and the legal consequences that may come with it.
- Lack of sensitive data classification can lead to blind spots, hindering the ability of organizations to manage them. In particular, managing access and permissions to these resources can become difficult.
- Audits can be slow and error-prone.
Sensitive data discovery platforms address the above pain points and safeguard your sensitive data from unauthorized access and leaks. However, the key is to choose the right tool that best fits your organization’s needs. In this article, we have laid out all the information you need to select an appropriate tool, along with a list of the most sensitive data discovery tools that work well across different environments.
Here is our list of the best sensitive data discovery tools:
- ManageEngine Endpoint DLP Plus EDITOR’S CHOICE A bundle of data protection services that include sensitive data discovery and categorization. The console offers templates to simplify data protection policy creation. Available for Windows Server. Get a 30-day free trial.
- ManageEngine DataSecurity Plus (FREE TRIAL) This package of data protection tools includes a Data Risk Assessment module that locates, protects, and tracks sensitive data. It is available for Windows Server. Start a 30-day free trial.
- N-able Risk Intelligence This data breach vulnerability assessment tool includes PII data discovery along with other security tightening systems, such as a permissions analyzer. This is a cloud platform.
- Spirion Sensitive Data Manager A tracker and manager for sensitive data that can locate sensitive data stores on the local network, remote sites, and on cloud systems. Available for installation on Windows Server or as a SaaS package with device agents for Windows, macOS, and Linux.
- iDox.ai Sensitive Data Discovery This platform provides a tailored discovery service for HIPAA, PCI DSS, SOX, FISMA, GDPR, PIPEDA, and CCPA. The package runs on Docker, AWS, and Azure and you can also access it as an API.
- Thales CipherTrust Data Discovery and Classification This cloud platform launches searches for sensitive data on your local and remote sites and also on the cloud.
- Datadog Sensitive Data Scanner This cloud-based system is able to scan servers for sensitive data instances according to the patterns that you set up, then redact it or log access to it.
- Azure Information Protection This service from the well-known cloud platform tracks your sensitive data no matter where it is – it doesn’t have to be on an Azure server.
- Mage iDiscover An AI-based tracker for sensitive data that categorizes data for GDPR, CCPA, and HIPAA requirements, among other standards. This is a cloud platform.
If you need to know more, explore our vendor highlight section just below, or skip to our detailed vendor reviews.
Βest sensitive data discovery tools highlights
Top Feature
Endpoint DLP with discovery and policy templates, containerization, centralized controls
Price
Annual subscription $795 for 1 user and 100 workstations, perpetual license $1,987 for same tier, higher with more workstations users add-ons
Target Market
Mid to large companies needing endpoint-based sensitive data protection
Free Trial Length
30-day free trial
Additional Benefits:
- Provides comprehensive real-time protection for sensitive data
- Controls who can access sensitive data and how they interact
- Prevents accidental and intentional transfer to untrusted and unverified applications
- Simplifies audit processes with detailed compliance reports
- Protects sensitive data by tracking user activity data access and file movements
Features:
- Discovers and classifies sensitive information across endpoints
- Builds policies with a template library and adaptable standards
- Uses containerization to label trusted apps and block untrusted apps
- Monitors USB devices emails and cloud platforms
- Installs on one device then reaches all computers, centralizes controls
Top Feature
Unified console for discovery classification file monitoring and DLP, auto-classification and real-time alerts
Price
Negotiated pricing
Target Market
SMBs to enterprises needing comprehensive data discovery
Free Trial Length
30-day free trial
Read more ▼
Top Feature
Risk quantification with sensitive data discovery and financial impact scoring
Price
Negotiated pricing
Target Market
IT teams and compliance officers
Free Trial Length
Free trial available, duration not disclosed by the vendor
Read more ▼
Top Feature
CADIA-powered AnyFind discovery across endpoints and cloud, low false positives
Price
Negotiated pricing
Target Market
Security ops teams
Free Trial Length
Demo available upon request
Read more ▼
Top Feature
Compliance focused discovery with AI NLP detection and redaction across 47 plus formats
Price
Public cloud $200/hour, remote support for private cloud and on premises $600/hour
Target Market
Enterprises and legal teams
Free Trial Length
7-day free trial
Read more ▼
Top Feature
ML driven discovery and classification across hybrid environments, agent or agentless, low false positives
Price
Cost depends on amount of data scanned
Target Market
Large enterprises and data privacy teams
Free Trial Length
Demo available upon request, duration not disclosed by the vendor
Read more ▼
Top Feature
Real time log and pipeline scanning with configurable patterns, redaction and hashing
Price
Free, Pro $15, DevSecOps Pro $22, Enterprise $23, DevSecOps Enterprise $34 USD per host per month, starting prices, add ons available
Target Market
DevOps security teams cloud native organizations
Free Trial Length
14-day free trial
Read more ▼
Top Feature
Enterprise data labeling with automatic discovery and classification across cloud and on premises
Price
Negotiated pricing
Target Market
Large enterprises
Free Trial Length
Free trial 90 days
Read more ▼
Top Feature
AI powered discovery across structured and unstructured data on premises and cloud, low false positives
Price
Negotiated pricing
Target Market
Mid size enterprises
Free Trial Length
Demo available upon request, duration not disclosed by the vendor
Read more ▼
Key Points to Consider While Choosing the Best Sensitive Data Discovery Tools
Many factors go into the process of selecting a sensitive data discovery tool that fits well with your organization’s size, needs, operations, and tech stack. Below are some aspects to consider.
- The tool you select must cover all types of sensitive data, and not just PII. Know the types of sensitive data that your organization handles and see if the tool covers all of them.
- A reliable data discovery tool must detect sensitive data accurately, with a low false positive rate. It helps if the tool uses advanced technologies like AI, ML, pattern recognition, NLP, and context-aware detection.
- Your chosen tool must comply with the mandatory and voluntary regulatory standards your organization follows.
- It is good to have automation capabilities and policy-based scanning features, as they improve accuracy without additional work for your employees.
- Know your tech stack and make sure your data discovery tool integrates with it for smooth data flows.
- Look for a comprehensive tool that also takes steps to secure sensitive data after identifying it. This can include strategies like access controls, hashing, encryption, etc.
- The data discovery platform must support custom rules and policies, so you can make changes based on your operations.
To dive deeper into how we incorporate these into our research and review methodology, skip to our detailed methodology section.
Organizations that handle sensitive data have significant legal, ethical, and operational obligations to safeguard it. Data protection regulations like the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and Health Insurance Portability and Accountability Act (HIPAA) impose strict requirements on how sensitive data is collected, processed, stored, and shared. Non-compliance can result in substantial fines, legal penalties, and reputational damage.
To meet these obligations, organizations must implement strong data protection measures, such as encryption, access controls, and secure storage. Equally important is identifying where sensitive data resides within their systems. Sensitive data discovery is a critical step in this process. It involves scanning databases, file systems, and other data repositories to locate and classify sensitive information.
Sensitive data discovery tools assist organizations by automating this task, reducing the risk of oversight and human error. These tools often employ advanced techniques like pattern recognition, AI, and machine learning to identify sensitive data in structured and unstructured formats. They also support compliance efforts by generating reports and providing insights into potential vulnerabilities.
By leveraging sensitive data discovery tools, organizations can gain better visibility into their data landscape, enabling them to implement comprehensive protections and maintain compliance with applicable regulations, ultimately reducing risks associated with data breaches and misuse.
As it is so important to protect PII from accidental disclosure or inappropriate use, this information requires an extra security process in addition to the access controls imposed on all company data stores. Knowing where the stores of PII are, is step one in controlling access, so sensitive data discovery tools are fundamental to the protection of PII.
Many business processes will require access to PII. For example, the sales department will need information about customer habits, the dispatch office will need address information and the financial office will be responsible for processing payments. This means that customer information can be spread over several storage locations. Distributed systems for global operations might have local data stores in each branch. So, there can be many places where PII is held.
Management of sensitive data
There is a strong business case for centralizing data stores. However, that is a separate issue to the protection of sensitive data. If you can centralize data you can eliminate redundancy. You can also control access better because you only need to have one instance of supervisory software running.
Whether you intend to move sensitive data or leave it in its many current locations, you first need to identify it. To find sensitive data, you need to locate all data and categorize it. Even “sensitive data” is not one category – there are many types of sensitive data. So, a sensitive data discovery tool needs to be able to categorize data as well as locate it.
The best sensitive data discovery tools
A sensitive data discovery tool has a finite requirement. You would expect that the discovery process should be ongoing. Ordinarily, it can be expected that PII will always be stored in the same locations, so once several servers and folders have been identified, they will probably be the only places to continue to look. However, PII data needs to be tracked, and sensitive data discovery tools can play a part in tracking the distribution – authorized or otherwise – of that data.
As the discovery of sensitive data is just one step in the process of protecting PII, the best tools for the job should be integrated into data management systems that perform a wide range of administration tasks, not just locating stores of sensitive data.
The best strategy to aim for when looking for sensitive data discovery tools is to get a system that forms part of a wider data security service. This will provide the best value for money and also reduce the number of interfaces that the system administrator needs to open to fully manage data.
1. ManageEngine Endpoint DLP Plus (FREE TRIAL)
Best for: Endpoint-based sensitive data protection.
Relevant for: Mid to large-sized companies.
Price: The annual subscription starts at $795 for one user and 100 workstations, while the perpetual license for the same is $1,987. Costs go up with more workstations, users, and add-ons.
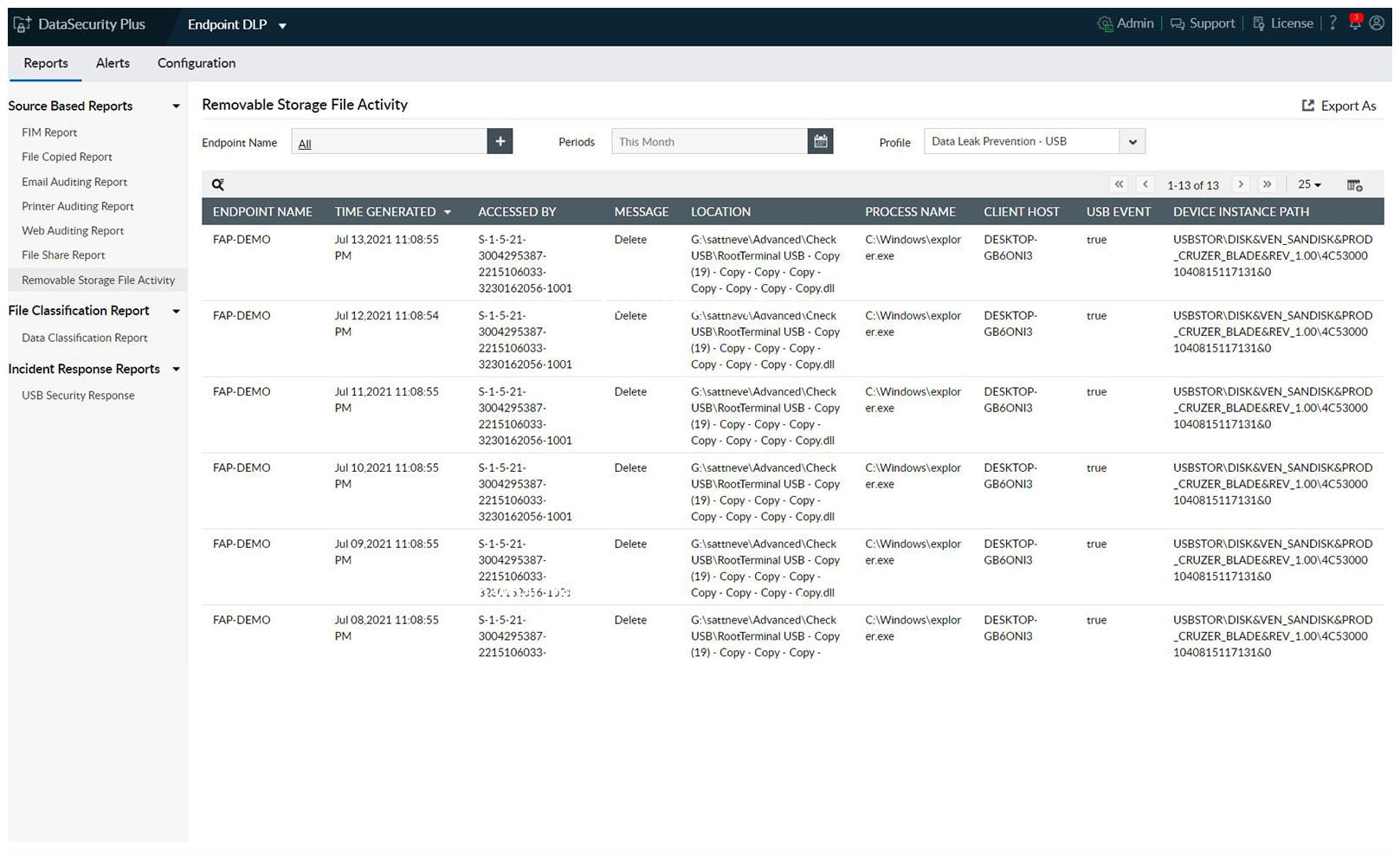
ManageEngine Endpoint DLP Plus is a data protection system that includes sensitive data discovery. The package will also help you to formulate a data security policy that extends to user activity monitoring, device control, and data movement scrutiny. Endpoint DLP Plus installs on one device on your network and then reaches out to all other computers, centralizing controls.
Key Features:
- Sensitive Data Identification: Discovers and classifies sensitive information across endpoints, reinforcing data security.
- Customizable Security Policies: Supports the formulation of bespoke data protection strategies with adaptable standards.
- Robust Access and Transfer Controls: Implements data access and transfer restrictions to mitigate risks of unauthorized sharing.
- Comprehensive Compliance Documentation: Facilitates the creation of detailed compliance reports, simplifying audit processes.
Unique Business Proposition
It combines data discovery with endpoint security to provide comprehensive real-time protection for your sensitive data. Using this tool, organizations can control who can access sensitive data and how they interact with it. It can be extended to cover USBs, email, cloud storage, and more.
Feature in Focus: Data Containerization
This feature identifies and isolates sensitive data by tagging the trusted applications as “secure.” After this labeling, any data processed by these applications is considered sensitive, and the data cannot be transferred to untrusted and unverified applications. This mechanism prevents the accidental and intentional transfer of data to malicious applications.
Why do we recommend it?
ManageEngine Endpoint DLP Plus is a bundle of ManageEngine tools and the data discovery part of the package is supplied by DataSecurity Plus, which you can buy as a standalone product. Endpoint DLP Plus includes additional tools to protect data through containerization.
The first step in managing sensitive data with this tool is to set up a security policy. This process is supported by a library of templates. After selecting a suitable match for your needs, you can adjust your chosen template to fine-tune the system’s data protection strategy. This dictates what constitutes ”sensitive” data and it can be tailored to a data protection standard.
The system will then scour all of the endpoints on your network and identify data stores containing matches for your chosen data protection definition. The system is able to spot combinations of fields that represent PII even if they are not collected in a formal storage format, such as a database or spreadsheet. This technique is called “fingerprinting.”
Once a store of sensitive data has been identified, all access to it is tracked. It is also possible to nominate trusted applications that regularly originate or access sensitive data. Data exports from these tools can be blocked. The system will also watch over USB devices and data movements in emails and out to cloud platforms.
Who is it recommended for?
ManageEngine has provided a complete package for data protection with this bundle and that completeness makes it ideal for businesses of all sizes. Small businesses would get sufficient service from the Free edition, which will cover data management of 25 devices. That’s a generous allowance and it provides all of the features of the paid service – crucially, the eDiscovery service is in there.
Pros:
- Advanced OCR Scanning: Employs OCR to scan document images, broadening the scope of sensitive data detection.
- Predefined Classification Presets: Simplifies data categorization with ready-to-use templates aligned with specific standards.
- USB and Email Monitoring: Enhances control over data transfer through meticulous monitoring of USB devices and email communications.
Cons:
- Windows Server Exclusive: Availability limited to Windows Server, restricting its use in diverse IT environments.
ManageEngine Endpoint DLP Plus has a free version, which is limited to monitoring 25 endpoints. The full package is called Professional and it can be extended to cover multiple sites from one console. The software package installs on Windows Server and the tool is available for a 30-day free trial.
EDITOR'S CHOICE
ManageEngine Endpoint DLP Plus is our top pick for a sensitive data discovery tool because the package can be easily tailored to specific data protection standards. The system discovers sensitive data and then categorizes it to allow the creation of fine-grained access controls. The system is supported by a library of policy templates that speed up the definition of a data security strategy. After you have your security requirements defined, the tool will track user activity, data access, and file movements to protect the sensitive data that your system holds.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/endpoint-dlp/download.html
OS: Windows Server
2. ManageEngine DataSecurity Plus (FREE TRIAL)
Best for: Comprehensive data discovery.
Relevant for: Organizations of all sizes, from SMBs to enterprises.
Price: Negotiated price.

ManageEngine DataSecurity Plus is a software package that includes three modules. You can buy just one of the modules as a standalone service or all three in a package. Those modules are File Server Auditing, Data Leak Prevention, and Data Risk Assessment. The sensitive data discovery tool of this package is contained in the Data Risk Assessment module.
Key Features:
- Comprehensive Discovery and Classification: Efficiently locates sensitive data, facilitating robust data management practices.
- File Access Monitoring: Offers detailed insights into data access patterns, enhancing security protocols.
- Data Movement Regulation: Ensures strict controls over data transfers, preventing unauthorized distribution.
- Web Application Surveillance: Monitors web applications for potential data exfiltration threats.
Unique Business Proposition
DataSecurity Plus combines sensitive data discovery, classification, file monitoring, data leak protection, and other advanced security features into a single console. It can scan more than 50 types of files and databases to prevent the leak of sensitive data. It also supports auto-classification, reporting, and real-time alerts.
Feature in Focus: PII Scanner
As the name suggests, the PII scanner scans personal data, like credit card numbers, passports, IPs, and national IDs, across different file formats. Based on this analysis, administrators can create policies to streamline access while allowing authorized personnel to quickly identify data using regex, labels, and filters.
Why do we recommend it?
ManageEngine DataSecurity Plus already got a mention in this article as part of the Endpoint DLP Plus bundle. DataSecurity Plus isn’t offered as a single package. Instead, it is made up of four modules, which you can buy separately. The eDiscovery service is contained in the Data Risk Assessment package. You also get file integrity monitoring with this unit. Add on the Data Leak Prevention service to get almost exactly the same set of services that Endpoint DLP Plus gives you.
The sensitive data discovery tool seeks out all stores of PII and Protected Health Information (PHI) and then categorizes all instances in terms of vulnerability. As well as looking for sensitive data, this service looks for obsolete files that have not been accessed for a long time. Being aware of this type of data gives you the option of either archiving it or deleting it. The service also examines file permissions and access rights to devices and folders, presenting them to you for analysis and decision-making.
The full package of DataSecurity Plus includes File Integrity Management (FIM), which tracks all changes to files, which also includes those that hold sensitive data. You don’t have to apply FIM to all files – you decide which directories should have this service enabled. The FIM is connected to an alert system so you will be notified whenever a protected file is changed or deletion is attempted.
The DataSecurity Plus system is also able to block USB devices or allow them but monitor which files are copied onto them, selectively blocking files that contained identified sensitive data. That graded control can also be applied to the email system – you can choose to block attachments or just block sensitive data files from being sent out by email.
Who is it recommended for?
Any business would get value for money out of DataSecurity Plus. However, it is necessary to compare it to Endpoint DLP Plus before purchasing. Confusingly, there is also data loss prevention in the Log360 package from ManageEngine. You can get a free trial of Endpoint DLP Plus and also of DataSecurity Plus. Small businesses would probably prefer the Endpoint DLP option because it has a Free edition, which DataSecurity Plus doesn’t have.
Pros:
- Versatile Data Store Analysis: Capable of identifying sensitive data across various storage solutions.
- Granular Access and Block Options: Provides nuanced control over data access and movement, bolstering data protection.
Cons:
- Platform Restriction: Exclusively available for Windows Server, limiting its applicability in non-Windows environments.
ManageEngine DataSecurity Plus is a software package that installs on Windows Server. You can get it on a 30-day free trial to run it through its paces.
3. N-able Risk Intelligence
Best for: Risk quantification.
Relevant for: IT teams and compliance officers.
Price: Negotiated price
N-able Risk Intelligence offers a good deal because it is more than just a sensitive data discovery tool. This service scans Windows and macOS devices connected to your network and identifies security weaknesses, such as out-of-date software. It also examines the security surrounding email systems.
Key Features:
- Security Vulnerability Detection: Identifies system weaknesses and outdated software, enhancing overall security posture.
- Customizable Data Scans: Offers both pre-set and tailor-made scans for comprehensive sensitive data discovery.
- Risk Assessment Reports: Generates detailed risk analyses, highlighting potential data breach impacts.
Unique Business Proposition
Using a combination of sensitive data discovery and financial risk scoring, N-able Risk Intelligence can find unprotected PII and map it to potential breach costs. Based on this financial mapping, admins can prioritize the security of PII that is the most expensive. This approach works well when resources are limited.
Feature in Focus: Monetary Liability Estimation
To identify the monetary liability estimate of unprotected PII, this tool takes into account PII type and the number of violations. This feature moves away from just PII protection and supports data-driven decisions and compliance.
Why do we recommend it?
N-able Risk Intelligence is part of a platform of tools that are designed for use by managed service providers as part of their work looking after the systems of client companies. This is purely a detection and analysis system – it doesn’t include active data access monitoring. Although it would be nice to see protection implementation bundled in, the risk assessment services are extensive and go beyond the discovery of sensitive data. You also get financial assessments and some great reports to pass on to clients to show that your MSP is earning its fees.
The vulnerability scanner uses the Common Vulnerability Scoring System (CVSS) to identify the latest threats and attack strategies of hackers and then checks each device to close down the entry points those strategies exploit. This vulnerability sweep touches on all devices connected to your network.
The sensitive data discovery tool in the N-able Risk Intelligence package offers pre-formatted scans and also allows for customized scans. It searches for email addresses, license plate numbers, bank accounts, social security numbers, ACH data, and credit card numbers. The system produces a risk report for each type of PII that it discovers.
Who is it recommended for?
As stated above, N-able is designed for use by MSPs. However, the IT operation department of large multi-site organizations would also benefit from the use of this tool. Smaller businesses would be more likely to encounter this tool if it is in use by the MSP that they choose to run their IT services.
Pros:
- MSP-Friendly Design: Ideal for managed service providers with its remote monitoring and management capabilities.
- Financial Impact Evaluation: Provides assessments of potential financial losses due to data breaches, adding value to MSP services.
Cons:
- MSP Focus: Primarily designed for MSP use, which may limit its direct applicability for in-house IT teams.
N-able offers a wider system administration service that includes security software. N-able Risk Intelligence can be integrated into an N-Able remote monitoring and management plan. This system is hosted as a SaaS system.
4. Spirion Sensitive Data Manager
Best for: Accurate enterprise-wide discovery.
Relevant for: Security ops teams.
Price: Negotiated price.
Spirion Sensitive Data Manager installs agents on the devices on your site and can also implement agentless monitoring of cloud platforms. This data discovery tool is available as a SaaS package or for installation on Windows and it gives you a data management strategy. The service is geared around reducing the attack vulnerabilities of sensitive data storage. This system looks for intellectual property, as well as PII, PHI, and credit card information.
Key Features:
- Holistic Data Management Platform: Integrates several tools for effective data protection and compliance.
- Integrity Monitoring: Includes file integrity management to track unauthorized changes to sensitive files.
- Vulnerability Scanning: Assesses system vulnerabilities to prevent potential data breaches.
Unique Business Proposition
The company claims a 98.5% accuracy in detecting structured and unstructured sensitive data spread across multiple environments, endpoints, and applications. It supports hybrid deployment, which means it can scan your cloud and on-premises environments to reduce false positives. Also, it integrates well with existing tech stacks.
Feature in Focus: CADIA-powered AnyFind
CADIA is a context-aware engine that can recognize PII, PHI, and other types of sensitive data. It uses algorithms and human tuning to achieve low false-positive rates. Furthermore, administrators can define data patterns and use dynamic classifications to identify sensitive data across different storage repositories.
Why do we recommend it?
Spirion Sensitive Data Manager is an on-premises package, just like the two ManageEngine options. This service includes discovery and classification for different types of sensitive data and protects discovered data stores with file integrity monitoring (FIM). An interesting feature of Sensitive Data Manager is that it also provides recommendations for reorganizing your system to improve data security.
The processes in the Spirion Sensitive Data Manager will help you with compliance to GDPR, CCPA, HIPAA, and PCI DSS. The data discovery module of the Sensitive Data Manager is called AnyFind. It can find sensitive data on all of your infrastructure – on all sites and all platforms. You can see where all of the data is stored through the dashboard of the system, which is hosted on Spirion servers and can be accessed through any web browser. That information gives you options over whether you are going to consolidate your data storage in one place or implement a distributed system.
The next phase in sensitive data management is classification and that task is carried out by the Watcher module. As well as identifying sensitive data, this examines vulnerability levels and recommends tightening access rights to specific files. A module called Spyglass helps you apply security procedures to your sensitive data stores. This includes FIM and data loss protection processes.
Who is it recommended for?
The flexibility of the tool’s deployment option gives Spirion Sensitive Data Manager a wide pool of potential clients. The system is very thorough and small businesses might not need all of the capabilities of the package when there are free alternatives available. Mid-sized businesses that manage sensitive data will find that Spirion meets all of their needs.
Pros:
- Flexible Deployment Options: Available both as a cloud service and on-premises, catering to various business needs.
- Customized Data Protection Strategies: Offers tailored discovery and classification for enhanced data security.
Cons:
- Complex Tool Suite: Requires navigating through multiple components, potentially complicating deployment and management.
The Spirion system offers value for money because it provides all of the services you will need to protect sensitive data and comply with data protection standards. Spirion offers a demo of the Sensitive Data Manager.
5. iDox.ai Sensitive Data Discovery
Best for: Compliance-focused discovery.
Relevant for: Enterprises and legal teams.
Price: Public cloud mode costs $200/hour, and remote support for private cloud and on-premises mode costs $600/hour.

iDox.ai Sensitive Data Discovery is a suitable discovery service for businesses that need to comply with the bank card standard, PCI DSS, the health data system, HIPAA, SOX, the financial reporting standard, FISMA, for US federal agencies or the personal data standards GDPR, PIPEDA, and CCPA.
Key Features:
- Compliance-Oriented Discovery: Targets compliance needs like PCI DSS, HIPAA, and GDPR through precise data identification.
- Intellectual Property Protection: Efficiently locates and classifies trade secrets and proprietary information.
- Project Management Tools: Simplifies oversight of sensitive data discovery projects with integrated management features.
Unique Business Proposition
iDox uses AI, machine learning, and natural language processing to identify sensitive data across structured and unstructured sources. It also classifies data based on regulatory standards like HIPAA, GDPR, and more. It is flexible, and supports both cloud and on-prem deployments.
Feature in Focus: Redaction and PII Detection:
Using advanced algorithms, iDox can scan 47+ types of file formats to detect PII and PHI with high accuracy. Beyond detection, it can also redact sensitive data without changing the context. This feature makes iDox a good choice for healthcare and financial institutions.
Why do we recommend it?
iDox Sensitive Data Discovery is part of a platform of data security systems that also includes a redaction suite. The system lets you know where the stores of sensitive data are and that search will be tailored to a specific data standard. It will also look for trade secrets and intellectual property.
This tool can be integrated into other software systems through an API. You have the option of accessing the package on AWS Marketplace or Azure Marketplace. It is also possible to download the software and run it on your own server. The system runs on Docker.
The iDox.ai system is ISO 27001 accredited. This means that the platform provides the highest levels of security and confidentiality. Discovered sensitive data is protected by encryption and even administrators are not able to get access to it without registered authorization. iDox is also SOC 2 Type II certified.
Businesses that manage personally identifiable information are required to enforce protection in order to win contracts and get insured. The first step of this process is to identify where that type of data is stored. This is the service that you get from iDox.ai
Who is it recommended for?
This package is suitable for a wide range of businesses because its installed software package is easy to run and its API provides more complex solutions for businesses that want a customized service. Integrating a data discovery service into other tools is difficult when you are dealing with standalone sensitive data discovery tools but that task is a lot simpler with the iDox.ai API.
Pros:
- Comprehensive Compliance Support: Streamlines adherence to multiple regulatory standards, facilitating easier compliance management.
- Redaction Capabilities: Includes a redaction suite, enhancing data privacy and security.
- ISO 27001 and SOC 2 Certified: Ensures high security and confidentiality standards for data protection.
Cons:
- Lacks DLP Features: Does not incorporate data loss prevention, limiting its scope in preventing data breaches.
The iDox.ai system is evolving and the company is bringing online extra features, such as data movement tracking, compliance reporting, integrated redaction, and Active Directory integration. You can try iDox.ai with a 7-day free trial.
6. Thales CipherTrust Data Discovery and Classification
Best for: Sensitive data visibility.
Relevant for: Large enterprises and data privacy teams.
Price: The cost depends on the amount of data scanned.
Thales CipherTrust Data Discovery and Classification is a cloud-based service that can search through all of your data stores on all of your sites plus on the cloud. This tool is part of a suite of data security services that is called the CipherTrust Data Security Platform.
Key Features:
- End-to-End Data Classification: Automates the discovery and categorization of sensitive data across multiple environments.
- Robust File Encryption: Employs encryption to secure data at rest and in transit, ensuring comprehensive protection.
- Adaptive Access Controls: Implements dynamic access controls based on data sensitivity and user authorization.
Unique Business Proposition
Thales CipherTrust offers data discovery, classification, and remediation for both on-premises and cloud environments. It’s a flexible tool, as it supports both agent-based and agentless deployments. With pre-built regulatory templates, custom profiling, and visual dashboards, this platform reduces risks and improves compliance with different standards.
Feature in Focus: ML-driven Classification
CipherTrust leverages advanced technologies like pattern recognition and machine learning to classify sensitive data into 250 different categories and with a low false positive rate. This classification enables IT admins to create custom policies to safeguard all kinds of sensitive information without restricting access to authorized users.
Why do we recommend it?
Thales CipherTrust Data Discovery and Classification is part of a platform of data security tools that includes transmission encryption services. So, you might end up buying several of the modules on this system. The Thales system offers a full data protection system as an alternative to data loss prevention strategies that rely on activity monitoring. Other sensitive data management tools in the package include a data redaction service.
The sensitive data discovery tool provides a service needed by businesses that follow GDPR, CCPA, LGPD, PCI DSS, and HIPAA. The system can analyze all types of data storage, not just file stores. It is also able to examine databases and other big data storage systems. Unstructured data is also a target for the search facility. The search utility can explore all of your sites plus cloud storage services for sensitive data.
The categorization processes in the Data Discovery and Classification module assess the vulnerability of each piece of data and its importance in terms of data protection standards. This gives you a report on which data stores require heavier protection and suggests methods to improve security.
Categorizing data in terms of data protection standards gives you a better grounding on which pieces of information can be shared with other organizations, in which format, and by what methods.
The console for the service is hosted in the cloud and accessed through any standard Web browser. The screens within the dashboard include data visualizations that make it easy to create presentations to communicate security issues to stakeholders. It is also possible to generate compliance reports from the system.
Who is it recommended for?
The Thales service operates both on-premises and on cloud data stores. So, it is doubly good for businesses that operate hybrid environments and have data on their own servers and on cloud accounts.
Pros:
- Hybrid Environment Compatibility: Efficiently manages data both on-premises and in the cloud, supporting hybrid infrastructures.
- Standard-Specific Tuning: Allows customization to adhere to specific data protection regulations, enhancing compliance.
Cons:
- Opaque Pricing: Lack of transparent pricing information may complicate budget planning for potential users.
Other modules in the CyberTrust Data Security Platform offer encryption solutions to protect sensitive data at rest and in transit and data storage control mechanisms that reduce the number of people who can access sensitive data.
7. Datadog Sensitive Data Scanner
Best for: Real-time log scanning.
Relevant for: DevOps, security teams, and cloud-native organizations.
Price: There are five plans (all priced in USD per host per month); Free; Pro – $15; DevSecOps Pro – $22; Enterprise – $23; DevSecOps Enterprise – $34. These are the starting prices, and you can include the required add-ons.

Datadog Sensitive Data Scanner is delivered from the cloud and provides a flexible service. You need to set up the data formats to search for and that process can be aided by templates that provide standard data types, such as credit card numbers or social security numbers.
Key Features:
- Configurable Data Patterns: Enables users to define specific data types for targeted scanning, increasing detection precision.
- Automated Data Surveillance: Conducts automatic scans to identify sensitive information, streamlining data governance.
- Data Entry Interception: Identifies sensitive data upon entry, reducing the risk of unauthorized access or leakage.
- Data Scrubbing: Offers options to cleanse data streams of sensitive information, maintaining data integrity.
Unique Business Proposition
This tool embeds data discovery into observability pipelines for complete visibility into unauthorized access, data breaches, and more. It can detect and classify sensitive data, and accordingly, redact the leaks or do hashing before storing sensitive data.
Feature in Focus: Redaction and Hashing
A highlight of Datadog is that it streams data as it enters the system, and applies pattern-matching rules to identify sensitive data. Once identified, it redacts the data that has been leaked. Also, it hashes the rest of the sensitive data before storing it.
Why do we recommend it?
The Datadog Sensitive Data Scanner can be integrated into the platform’s Log Manager, APM, or Real User Monitoring service to identify sensitive data as it travels into storage or moves out. This avoids the need to tamper with records and offers better data governance by preserving the original data where needed.
The actions of the Datadog system upon the discovery of an instance of sensitive data depend on the settings that you define. The tool doesn’t scan files but instead operates on data entered into Web forms, accessed through applications, or recorded in logs.
So, when an application accesses a data store, the sensitive data scanner can be set to obscure the sensitive data in the display. You could choose to delete sensitive data from log messages before filing them or showing them in a log management data viewer. In these examples, the working data is left intact – it shouldn’t be necessary to save data in log files, so this instance is a little different.
One option that you can activate is logging by the sensitive data tool. So, whenever a piece of sensitive data is spotted moving into an application, that event and the user account involved can be recorded. This action is important for compliance with GDPR, CCPA, and HIPAA.
Who is it recommended for?
The Sensitive Data Scanner is priced as an individual module. However, it is difficult to imagine how the tool would be used by itself. Instead, this system should be used in conjunction with other Datadog modules. Effectively, it is an add-on for the APM, the Log Manager, or the Real User Monitoring services.
Pros:
- Flexible Data Handling: Provides multiple strategies for managing detected sensitive data, enhancing data privacy.
- Integration with Other Datadog Services: Seamlessly works with Datadog’s monitoring tools for comprehensive oversight.
Cons:
- Dependency on Other Modules: Its effectiveness is significantly enhanced when used with additional Datadog solutions, limiting standalone utility.
You sign up for the Sensitive Data Scanner at the Datadog cloud platform. Consider the system as part of a group of modules on the platform that you might like to try and then get all of them on a free trial to see how you could use this data protection service.
8. Azure Information Protection
Best for: Enterprise data labeling.
Relevant for: Large enterprises.
Price: Negotiated price.
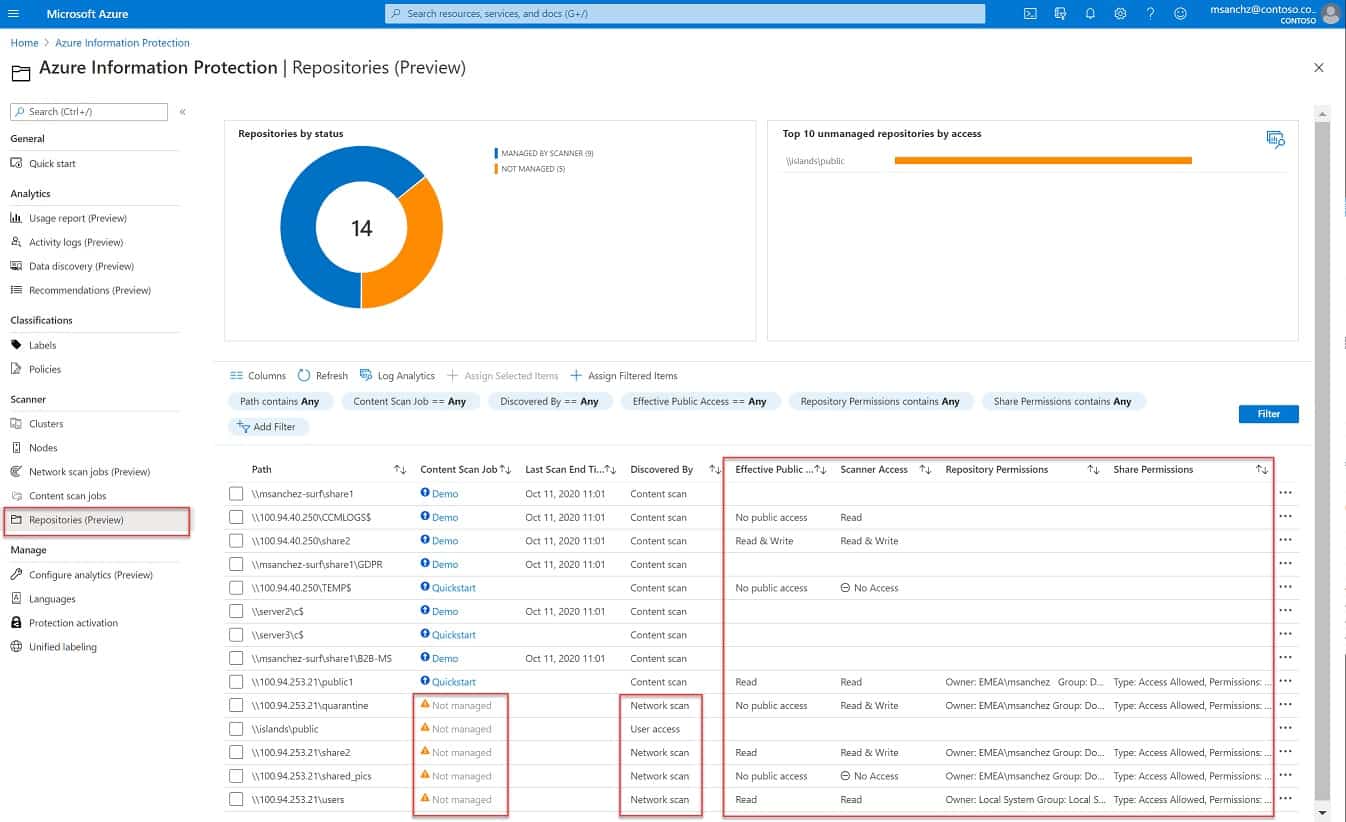
You probably know about the Azure platform and you might even use Azure servers for storage. However, you might not know that Azure offers a menu of services that can be applied to storage and processing virtual server account and are also available to businesses that don’t even use Azure servers.
Key Features:
- Cloud and On-Premises Data Management: Searches for sensitive data across various platforms, ensuring thorough coverage.
- Configurable Data Protection Policies: Allows for detailed policy settings, tailoring data security measures to specific needs.
- Integrated Microsoft Office Support: Enhances document security with encryption and access controls within Office applications.
Unique Business Proposition
Azure Information Protection supports the automatic discovery and classification of sensitive information across both cloud and on-premises environments. Its unified console makes it easy for admins to stay on top of sensitive data across multiple environments. Also, it’s integrated with Microsoft Defender helps detect sensitive data on endpoints and prevents data leaks through context-aware policies.
Feature in Focus: Labeling
A notable feature of this tool is its labels, some of which are built-in, while the others can be customized. It tags documents, emails, databases, file shares, and other data sources based on the sensitive data they contain. Accordingly, it applies the security policies and restrictions to protect them.
Why do we recommend it?
The Azure Information Protection service is delivered from the Azure platform but it can reach out to AWS accounts as well as storage on Azure. You can also use this tool to swatch your own servers for sensitive data. This is a very affordable tool that can be used to control data on many sites. Other services in the package include copy tracking and watermarking.
One of those services is the Azure Information Protection system. This package can search for sensitive data on any of your sites or any of your cloud services. The system offers continuous monitoring for emails, document access, and data stores. So, once sensitive data has been located, it will be monitored.
You have to set up a policy for data protection before running a data search with this service. This enables you to specify the type of information that needs to be protected – a decision that will be dictated by the data protection standard that you are following. You can decide what level of control should be applied to sensitive data. For example, you can ban all transfers of the data or decide that only certain personnel should have access and the right to share the data – and who they can share it with.
Documents can be stamped and copies can be enumerated in the metadata to make disclosure tracking easier. It is possible to allow files to be viewed by others but not edited, downloaded, forwarded, or printed.
Who is it recommended for?
A great feature of Azure products is that they are charged for retrospectively on a meter rather than as a subscription, which requires a fixed fee advanced payment. The best thing about this is it is very scaleable. Small businesses don’t have to pay for the average business’s data throughput but only for the actions that they use. The Azure platform has massive capacity that means this system will also work well for very large multinationals.
Pros:
- Flexible Pricing Model: Utilizes a usage-based pricing scheme, offering scalability and cost-effectiveness for businesses of all sizes.
- Advanced Encryption and Tracking: Provides robust file protection and monitoring capabilities, securing sensitive information effectively.
Cons:
- Limited Database Coverage: Does not extend its discovery and protection capabilities to database environments.
The Azure Information Protection service includes an encryption service that you can use to protect all sensitive data stores at rest and in transit. The system can be linked to Active Directory for access control and there is also a cloud-based version of Active Directory available within the Azure platform if you don’t already implement AD.
9. Mage iDiscover
Best for: AI-powered discovery.
Relevant for: Mid-size enterprises.
Price: Negotiated price.
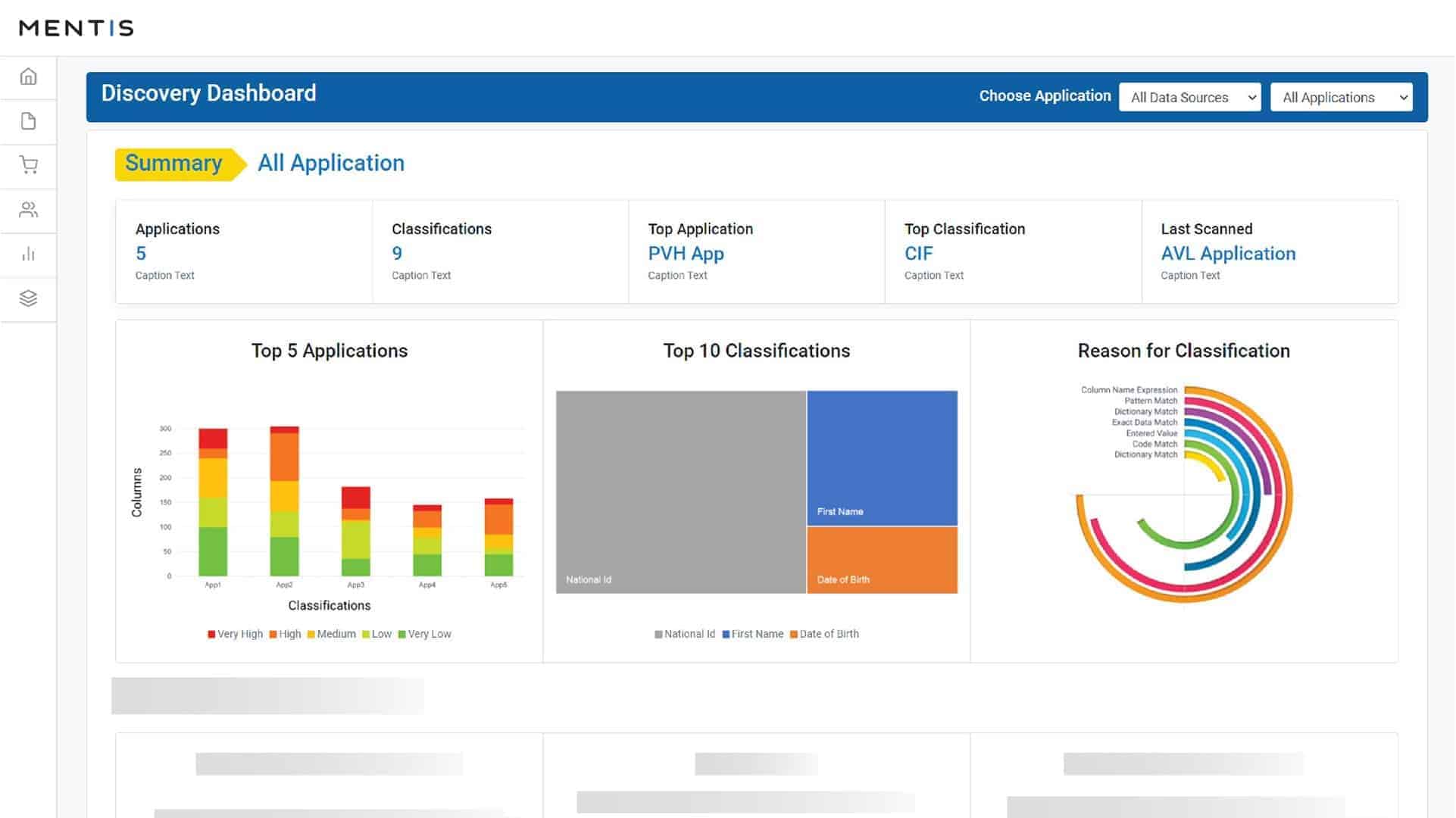
Mage iDiscover can track down structured, unstructured, and BigData stores of sensitive data on-premises and on the cloud. This cloud-based service supports compliance with GDPR, CCPA, and HIPAA.
Key Features:
- Comprehensive Data Coverage: Identifies sensitive data across on-premises and cloud environments, including structured and unstructured data.
- Advanced AI Detection: Utilizes artificial intelligence and natural language processing for accurate data identification.
- Proactive Data Management: Automates workflows for efficient sensitive data protection and compliance alignment.
Unique Business Proposition
Mage iDiscover uses patented AI, ML, and NLP to scan every piece of structured and unstructured data located on-premises or in cloud environments. It supports more than 80 regulatory data types and can classify them with a low false positive rate. It also has an intuitive dashboard for tracking the location and incremental changes of sensitive data.
Feature in Focus: AI-powered Discovery
Made iDiscover goes beyond just pattern-matching and uses advanced AI and ML to locate sensitive data across multiple formats and in different locations. It understands the context and relationships across data elements to identify sensitive data, thereby reducing the rate of false positives.
Why do we recommend it?
Mage iDiscover is a strong competitor to the Thales and Spirion systems. It is able to scan for sensitive data on sites and also on cloud platforms. Although we put Mage last on the list, this review is not ordered in terms of impressive functionality, other than the number one slot, which is reserved for our favorite. This service uses AI to identify adjacencies in data field that need to be combined before they constitute sensitive data that needs to be protected.
After tracking sensitive data, the service assesses the vulnerability of its location and analyzes file permissions. The system dashboard displays all stores of sensitive data so you get a visual record of storage. Sensitive data discovery can be set up as an incremental process, so it will notify you of any new instances that get saved. The system also scours log files and raises an alert if they contain sensitive data.
This system scours databases and unstructured data as well as files in its search for sensitive data. It also analyzes the users that have access permissions on data. It recommends changes to access rights. The service also back-chains through to the applications that store data, offering you the opportunity to change settings and alter storage locations for sensitive data.
This system uses artificial intelligence and natural language processing to spot instances of sensitive data. It implements automated workflows to save you time and take care of sensitive data protection for you.
Who is it recommended for?
Mage iDiscover is suitable for mid-sized companies and businesses of that size should really compare Mage with the Thales and Spirion systems to get a good fit.
Pros:
- AI-Enhanced Identification: Employs AI to detect complex data relationships, improving discovery accuracy.
- Automated Application Configuration: Adjusts application settings to optimize data storage and security practices.
Cons:
- Lack of Trial Option: Absence of a free trial may hinder evaluation of the system’s effectiveness for prospective users.
Mage iDiscover’s built-in capabilities to interface with 35 data management systems, such as database management systems and cloud platforms. You can request a demo to assess the system for yourself.
Our Methodology for choosing sensitive data discovery tools
At Comparitech, we take a practical approach while reviewing different tools and their capabilities. Our goal is to help organizations select the tool that best fits their needs, and to this end, we evaluate the features and do hands-on testing where possible.
To identify the best sensitive data discovery tools, we have considered the following factors.
- How well does a tool cover different types of sensitive data? Does it support structured, unstructured, and semi-structured data? We prioritized tools that can cover all types of sensitive data across multiple environments and formats.
- We looked for tools that come with automated classification and tagging features for better data protection. Labeling features, based on sensitivity and regulatory requirements, were also considered.
- Since many organizations rely on these tools to meet regulatory requirements, we evaluated how each tool supports compliance audits, reporting, and policy enforcement.
- Given the importance of security and privacy in managing sensitive data, our tools come with robust security features to safeguard data from misuse.
- Ease of use is an important feature for this, and this is why most tools on our list are intuitive and require minimal training to use.
Broader B2B software selection methodology
The above aspects that we considered fall in line with our broader B2B methodology, where we consider the features of each tool and their applicability across different use cases and environments. We also try the tool when possible to evaluate how user-friendly it is for different user groups. Additionally, we consider its scalability and performance consistency. Any additional features like report generation and labeling are a big plus. Know more about our B2B methodology.
Why Trust Us?
Our goal at Comparitech is to save time and effort for you. This is why we do in-depth research across multiple areas to provide all the information you require in an easy-to-understand format, so you can simply read through our guide and make the right decision. We know how important this information is for you, and this is why we take a neutral and unbiased approach to provide honest reviews. We are also transparent in how we review the tools.












