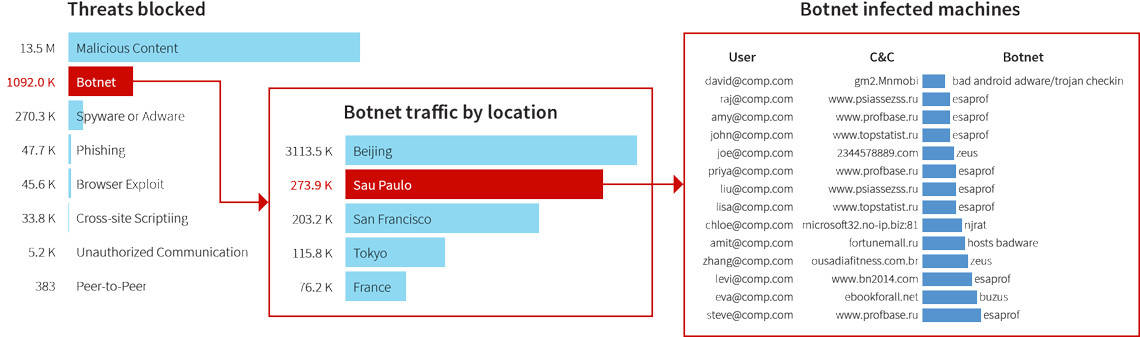
Network security monitoring has become a complicated task because of the wide range of attack vectors that hackers now have at their disposal.
Here is our list of the best network security tools:



- OSSEC – Best for teams needing open-source host intrusion detection
- CrowdStrike Falcon Insight – Best for businesses that need a scalable package
- SolarWinds Security Event Manager – Best for large businesses with on-site networks
- Intruder – Best for companies with higher budgets
- Endpoint Protector – Best for businesses that store and use sensitive data
- Nessus Vulnerability Scanner – !Best for businesses poting for widely-adopted tools
- ZAP – Best for companies that don't need professional support
- Zscaler Cloud Firewall – Best for businesses that need cloud-based firewall protection and access control
- Burp Suite – Best for penetration testers
- Teramind DLP – Best for businesses that store PII.
New attack strategies appear regularly, making traditional system defense software ineffective. A better strategy is to deploy security monitoring systems that don’t rely on a process of pattern matching.
Old security tools that just compare packet content to a list of known strategies quickly become outdated and need to be updated constantly. Smarter network security tools assess regular activities on a network and then lookout for anything that is different, which is called an anomaly. These AI-based tools are more sustainable in the ever-changing landscape of cybersecurity.
Network Security Tools Categories
Securing a network requires a multi-layered approach, each with its own set of tools and strategies tailored to specific security needs. These methods address vulnerabilities across various points in a network infrastructure, combining them to create a robust defense system. The key strategies and corresponding tools include:
- Firewalls: These are the first line of defense, designed to block known threats and unauthorized traffic at the network’s boundary. Firewalls filter incoming and outgoing traffic based on predefined security rules, ensuring that only legitimate data packets gain access.
- Reverse Firewalls: Primarily used for data loss prevention (DLP), reverse firewalls monitor and control outbound data, ensuring sensitive information does not leave the network without authorization. This tool is essential for protecting intellectual property and preventing leaks.
- Intrusion Prevention Systems (IPS) and Security Information and Event Management (SIEM): These tools detect and respond to anomalous behavior that may bypass firewalls. IPS focuses on identifying and neutralizing threats in real time, while SIEM collects and analyzes security data to provide a comprehensive overview of potential vulnerabilities.
- VPN and Edge Services: Virtual Private Networks (VPNs) and edge services channel internet traffic through external proxies, safeguarding onsite resources from external threats. They encrypt data transmissions, ensuring secure remote access and protecting against interception.
- Endpoint Detection and Response (EDR): EDR solutions transform endpoints into security monitoring stations, detecting malicious activities and providing real-time insights into network health.
These strategies highlight four critical monitoring locations:
- Offsite, using edge services to secure external traffic.
- At the network boundary, with firewalls blocking unauthorized access.
- On the network, utilizing packet sniffers and IPS tools.
- On endpoints, leveraging EDR to detect and mitigate threats locally.
By deploying these tools effectively across these locations, organizations can create a comprehensive and dynamic defense against evolving cyber threats.
Network security strategies
Thorough network managers are advised to use a combination of tactics. This is because even the most reliable security system can be bypassed. By implementing several strategies, you will cover every possible security threat. For example, a firewall will block known infected software from entering the network but it won’t stop a disgruntled employee from mailing out your client list to a rival.
Blended strategies require preparedness as well as blocks on malware, malicious activity monitoring, attack shutdown, and system reviews. You need to implement network security by:
- tightening up vulnerabilities to reduce risk
- controlling access to the network
- monitoring traffic to spot attacks in progress
- take action to stop an attack
- reviewing data to identify past attacks that slipped through the net
- and adjusting the security and monitoring systems according to past experience
The Best Network Security Tools
As there are so many different network security tasks and tools for each of them, this review lists exceptional tools that fall into each of the defense strategies that you will need to deploy. None of them cover every aspect of system security, so you will need to implement several of them.
Our methodology for selecting a network security tool
We reviewed the market for network security systems and analyzed tools based on the following criteria:
- Network discovery to identify all paths and devices
- Activity baselining, preferably with Machine Learning
- Adaptable anomaly detection
- Alerts for suspicious activity to attract technicians
- Extensive reports and logging
- A free trial or a demo account that enables a cost-free assessment
- Value for money from a tool whose vigilance will save the expenses involved in system recovery
With these selection criteria in mind, we identified candidate network monitoring systems that are worth trialing. We looked for utilities that will install on Windows Server and Linux plus SaaS platforms.
You can read more about each of these security tools in the following sections.
1. ManageEngine Vulnerability Manager Plus (FREE TRIAL)
Vulnerability scanning is an essential preventative network security task. There are many ongoing maintenance tasks that network managers need to conduct and some of these are necessary in order to keep the system secure.
Key Features
- System hardening: Checks operating systems and software
- Automated patching: The patch manager gets populated automatically by the vulnerability scanner
- Access rights management assessment: Looks for default passwords and inactive accounts
- Multiple platforms: Scans devices running Windows, macOS, and Linux
- Network device management: Discovers network devices and assesses them for risk
Why do we recommend it?
ManageEngine Vulnerability Plus is a close rival to the Intruder system. This package provides a vulnerability scanner and a patch manager to update the out-of-date software that the scanner discovers. It can also automatically fix configuration problems. This system can be run continuously at no extra cost.
Apart from vulnerability scans, you need to keep all operating systems patched and software updates applied. These patches and updates are often written in order to address newly discovered “exploits”. ManageEngine Vulnerability Manager Plus includes a Patch Manager to keep your software secure. It also has a Configuration Manager that standardizes the setup of network devices and blocks unauthorized changes. Configuration management is another important task to keep a network secure.
Vulnerability Manager Plus combines vulnerability scanning with tools to address issues that the scan identifies. These extend to access rights analysis and password management features. Other tools include firewall auditing and service hardening, such as browser security enhancements.
Who is it recommended for?
There isn’t a cloud version of this tool and it only runs on Windows Server. Only the top plan includes the patch manager, but the lower-paid plan will provide automatic configuration management. There is a Free edition that provides the lower plan’s services for up to 25 devices.
Pros:
- Value pack: Combines vulnerability scanning with tools to fix discovered problems
- Fast security protection: Automated remediation playbooks
- Configuration change blocking: Configuration protection
- Software management: Updates more than 500 applications and software packages
- Free edition: Looks after up to 20 workstations and five servers
Cons:
- Only available for Windows Server: No software for Linux or macOS
ManageEngine offers Vulnerability Manager Plus in three editions: Free, Professional, and Enterprise. The Free version will manage networks connecting up to 25 computers. The Professional edition doesn’t have the system limit and it also has specialized processes for managing the security of servers. That version only covers the network on one site; the Enterprise edition is designed to serve WANs. The software for Vulnerability Manager Plus installs on Windows and Windows Server and you can get it on a 30-day free trial.
EDITOR'S CHOICE
Vulnerability Manager Plus is our top pick for a network security tool because it will proactively identify and mitigate vulnerabilities across an organization’s IT infrastructure. With cyber threats constantly evolving, it’s essential to have a tool that not only identifies vulnerabilities but also helps prioritize remediation efforts based on risk, ensuring that your network stays secure and compliant with industry regulations. One of the standout features of Vulnerability Manager Plus is its extensive vulnerability scanning capabilities. The tool can scan a wide range of operating systems, applications, and devices, providing detailed reports on potential weaknesses. It also continuously monitors the network for new vulnerabilities, ensuring real-time awareness of emerging threats. What sets Vulnerability Manager Plus apart is its actionable remediation features. It doesn’t just alert administrators to vulnerabilities; it also offers built-in patch management tools to deploy security patches directly from the platform. This streamlined process helps reduce the time between detection and resolution, minimizing the risk window for exploitation. The tool provides a user-friendly interface, detailed risk assessments, and reporting capabilities that make it easy for both IT teams and security professionals to understand and address vulnerabilities.
Download: Get a 30-day FREE Trial
Official Site: https://www.manageengine.com/vulnerability-management/download.html
OS: Windows Server
2. ManageEngine Log360 (FREE TRIAL)
ManageEngine Log360 is a SIEM system that also performs file integrity monitoring and provides compliance reporting for HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA. The package includes a central log server and a library of data collection agents. Install one agent on each device on your system – there are also agents for cloud platforms.
Key Features:
- Log manager: Consolidates different log message standards
- Threat intelligence feed: A list of blacklisted IP addresses
- Compliance reporting: HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA
Why do we recommend it?
ManageEngine Log360 is a megapack of ManageEngine tools and it includes the EventLog Analyzer, which is a log manager and a SIEM. This central security service is able to collect network data to contribute to the source information of the threat detection service. This system can also write firewall rules to block intruders.
The log server of Log360 shows messages live in the console as they arrive and also stores them to file. The system gets a threat intelligence feed of the latest hacker strategies and that improves the Log360 threat detection process.
The Log360 system raises an alert when it identifies suspicious activity. You can get those alerts forwarded to your technicians through a service desk tool. Log360 works with ManageEngine ServiceDesk Plus, Jira, and Kayoko.
Who is it recommended for?
Log360 collects log data from endpoints, cloud platforms, and SaaS packages. It is a very large tool and it doesn’t offer a Free edition, which its components do. So, small businesses would be better off looking at the EventLog Analyzer. Large businesses would benefit the most from this package.
Pros:
- A SIEM tool: Has its own log manager
- Threat alerts: Notifications can be channeled as tickets into Service Desk systems
- Good for hybrid systems: Monitors cloud platforms as well as on-premises assets
Cons:
- No SaaS option: Only available for Windows Server
The ManageEngine Log360 server runs on Windows Server. You can assess the package with a 30-day free trial.
3. Site24x7 (FREE TRIAL)
Site24x7 is a platform of system monitoring and management tools that includes network security tools designed to provide comprehensive protection and monitoring for businesses of all sizes. It offers a suite of features that address critical aspects of network security, including vulnerability management, firewall monitoring, and network configuration management.
Key Features:
- Network Configuration Manager: Tracks and manages configurations of network devices.
- Firewall Vulnerability Management: Continuously scans firewalls for known vulnerabilities, outdated firmware, and misconfigurations.
- Automated Vulnerability Scanning: Automatically identifies and prioritizes vulnerabilities across the network.
Why do we recommend it?
The Site24x7 has three features that provide network security: firewall performance checks, network configuration manager, and a firmware vulnerability scanner. These systems operate continuously and will raise alerts if security issues are detected. Alongside these functions, the platform also implement continuous performance monitoring for all IT assets.
The Network Configuration Manager allows administrators to track and manage configurations of network devices, ensuring compliance with security policies, detecting unauthorized changes, and streamlining device configuration backups. This is particularly beneficial for organizations looking to reduce configuration errors and maintain a secure network environment.
The Firewall Vulnerability Management unit enables proactive security monitoring by continuously scanning firewalls for vulnerabilities and misconfigurations. It identifies potential threats and outdated firmware versions, allowing businesses to patch vulnerabilities and strengthen their defenses before any security breaches occur. The system automatically alerts administrators about vulnerabilities and assists in prioritizing remediation efforts to ensure the security of critical network assets.
By tracking firewall logs and analyzing traffic patterns, Site24x7 provides deeper insights into the overall health of the network, helping organizations respond quickly to emerging threats. The Firmware Vulnerability Manager provides that same level of security for all network devices and also IoT equipment. , including firewalls, routers, and switches, helping teams take corrective actions quickly to prevent breaches.
Who is it recommended for?
Site24x7’s network security service is recommended for businesses of all sizes, particularly those with complex network infrastructures that require constant monitoring and protection. It is ideal for industries such as finance, healthcare, telecommunications, and manufacturing. In these sectors, safeguarding sensitive data and ensuring compliance with regulatory standards are critical. Additionally, managed service providers (MSPs), data centers, and large enterprises with diverse and distributed networks will benefit from This platform.
Pros:
- Comprehensive Network Device Monitoring: Providing insights into uptime, traffic flow, CPU usage, memory utilization, and network latency.
- Traffic Analysis and Security Event Detection: Monitors traffic flows, identifies anomalies, and provides insights into network security.
- Real-Time Alerts and Notifications: Sends instant alerts to administrators about critical vulnerabilities, configuration changes, or firewall performance issues.
Cons:
- No Automatic Patching: The system detects firmware problems but doesn’t fix them automatically.
Site24x7’s proactive monitoring, real-time alerts, and vulnerability management make it an excellent choice for organizations looking to enhance their security posture, prevent breaches, and optimize their network configurations. You can assess the platform with a 30-day free trial.
4. OSSEC
OSSEC is a Host-based Intrusion Detection System (HIDS). This type of security strategy examines log files for signs of malicious activity. OSSEC stands for “Open Source HIDS Security.” It is a free system but is owned by TrendMicro.
Key Features
- A free tool: The paid version is called Atomic OSSEC
- Extensible with free detection rules: Get rules from the community or write your own
- Automated remediation actions: Attach actions to detection rules
Why do we recommend it?
OSSEC is a host-based system rather than a network-based detection system. However, the malicious activity that is detected on a device can be shut down by blocking that source’s access to the network through updated firewall rules. This system is highly respected and managed by Trend Micro to keep it up to date.
The OSSEC system works on a databank of detection rules. These are called “policies” and they can be written by the user or acquired from other users for free through a community listing website and message board. The user community is also the primary source for help and tips on using OSSEC. The lack of a professional support system for the tool might put off some corporate users. However, Trend Micro offers support contracts for a fee.
Existing policies can be adapted and set up to trigger actions, which gives the service the power to automate attack mitigation. Typical actions include interfacing to firewalls in order to block access to specific IP addresses or update the access rights manager to block user accounts. This possibility makes OSSEC an Intrusion Prevention System (IPS).
Who is it recommended for?
Any business would benefit from OSSEC and the fact that it is free makes it appealing to small businesses. However, the tool lacks a user interface and it is difficult to set up, so owner-managed businesses just won’t have the technical expertise on the payroll to get the system running.
Pros:
- One of the first SIEM systems to be created: It is still well-maintained
- Highly respected and built to enable customization: An open-source package
- A host-based intrusion detection system: Sifts through log messages
Cons:
- No frontend: Look at the free OSSEC + system instead
A big problem with OSSEC is that it doesn’t have a user interface. However, it is easy to set it up to feed data to Kibana or Graylog. OSSEC installs on Windows, Linux, macOS, and Unix.
5. CrowdStrike Falcon Insight

CrowdStrike Falcon Insight is a combination of a SIEM system and endpoint detection and response (EDR). The EDR part of the system is fulfilled by instances of Falcon Prevent. By opting for Falcon Insight instead, you get a fully coordinated enterprise-wide security system rather than a collection of endpoints with individual AVs to manage.
Key Features
- A hybrid system: Cloud service with on-site agents
- Protects endpoints: Combines SIEM with endpoint detection and response
- Remediation actions: Coordinates actions across a fleet of endpoints
Why do we recommend it?
CrowdStrike Falcon Insight is a hybrid system that aims at protecting endpoints with a central controller in the cloud and substantial agents resident on each endpoint. The data collection system effectively surrounds the network and events detected on endpoints highlight the presence of intruders on the network.
The central service is cloud resident and it makes sure that each endpoint agent is kept up to date. Not only does it ensure that the software is fully updated but it constantly updates those instances with new detection strategies.
The endpoint agents offer full protection and will continue to operate even when they are disconnected from the network and unable to communicate with the central controller. Those agents assess the activities on the endpoint and all of the user accounts that are active on them. This is a UEBA service that establishes a baseline of normal behavior and raises an alert when it encounters an activity that deviates from that standard. The agents also upload log messages and activity reports to the central controller.
The central unit searches through the received data for indicators of compromise. The service also receives a threat intelligence feed that shares the attack experiences of other CrowdStrike customers. The coordinating function of the cloud module acts like an in-house threat intelligence feed, sharing activity summaries between agents.
Who is it recommended for?
CrowdStrike Falcon Insight is a scaleable package because you simply extend the coverage of the service by buying another endpoint unit. This module is called Falcon Prevent and it can continue to operate if the protected endpoint is disconnected from the network. However, the system is probably too expensive for small businesses.
Pros:
- Unifies endpoint activity tracking: Gets a view of the whole enterprise
- Focuses effort: Implements triage to home in on suspicious activities
- Centralized threat hunting: It can cover multiple sites
Cons:
- Doesn’t interact with third-party tools: The Falcon XDR coordinates with other security systems
The endpoint agents for CrowdStrike Falcon Insight are available for Windows, macOS, and Linux. You can get a 15-day free trial of Falcon Prevent, which gives you all of the functionality of the endpoint agents.
6. SolarWinds Security Event Manager
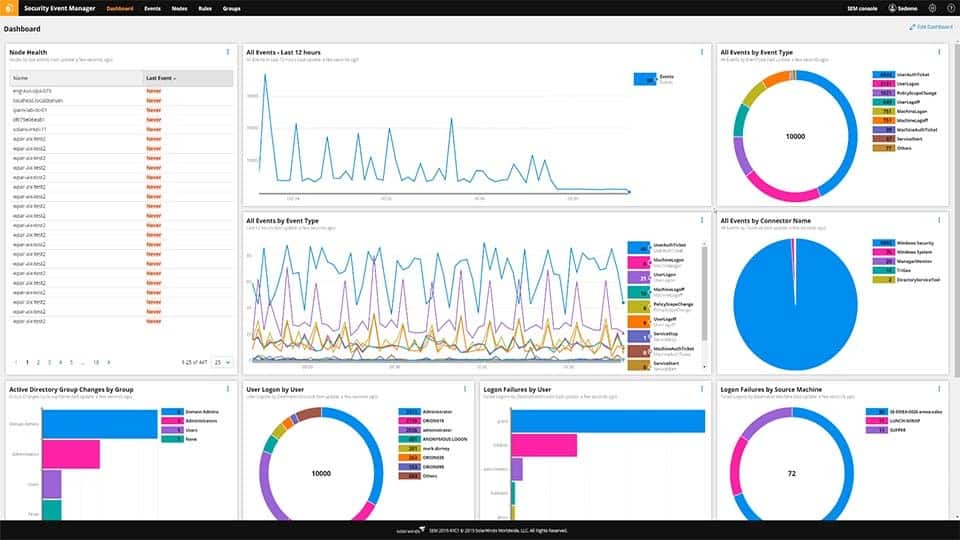
The Security Event Manager from SolarWinds is a SIEM system that scans events on a network and watches out for anomalies that are indicated by a live threat intelligence feed. This network security tool extends to all devices connected to the network. It collects all log messages and manages their layout, creating a common format. Those records are then filed while also being analyzed by the tool.
Key Features
- On-premises software: Runs on Windows Server
- Collects system logs: Standardizes different message formats into one layout
- Searches for suspicious activities: Automated threat hunting
- A classic SIEM: Scans activity data from cloud services as well as on-premises software
- Files messages for auditing: Messages can be recalled for manual analysis
Why do we recommend it?
SolarWinds Security Event Manager is an on-premises system that runs on Windows Server. The system gathers network activity data as well as logs from endpoints and then searches through that pool of event information to identify a security breach. The tool can also implement automatic responses in concert with other systems.
The message-checking service receives live reporting information from all points on the system. As these records are processed, the Security Event Manager scans for signs of intrusion or other malicious activity. Some typical attacks can be spotted by looking at one event, while others are only made apparent by a pattern of seemingly unrelated incidences. So, in order to provide a full network security service, the tool works both on live data and historical records.
In order to reduce the incidences of “false positive” reporting, the Security Event Manager makes a record of normal traffic patterns and activities. This is an AI-based machine learning technique known as User and Entity Behavior Analysis (UEBA).
As well as detecting suspicious activity, the Security Event Manager is able to implement actions to close it down. This service takes the form of blocking communications from specified IP addresses or suspending a user account that appears to have been hijacked. The mitigation automation is activated by the user, so it can be left to just an alert if you want to investigate a problem before implementing a solution manually.
Who is it recommended for?
This is a solution for large businesses. The tool can collect logs from cloud services but it is more focused on those systems that are on-site, such as networks. You should already have access rights management tools and firewalls on your network and endpoints and the SolarWinds system interacts with these.
Pros:
- Log-based SIEM: Can also ingest SNMP reports from network devices
- User and Entity Behavior Analytics for baselining: Tracks standard behavior per device and user
- Anomaly detection: A method for identifying zero-day attacks
- Alerts for threats: Alerts appear in the dashboard and can be forwarded as notifications by SMS and email
- Automated responses: Set up playbooks to trigger actions off alerts
Cons:
- No SaaS version: Only available for on-premises installation or to run on a cloud account
SolarWinds Security Event Manager runs on Windows Server and it is available on a 30-day free trial.
7. Intruder
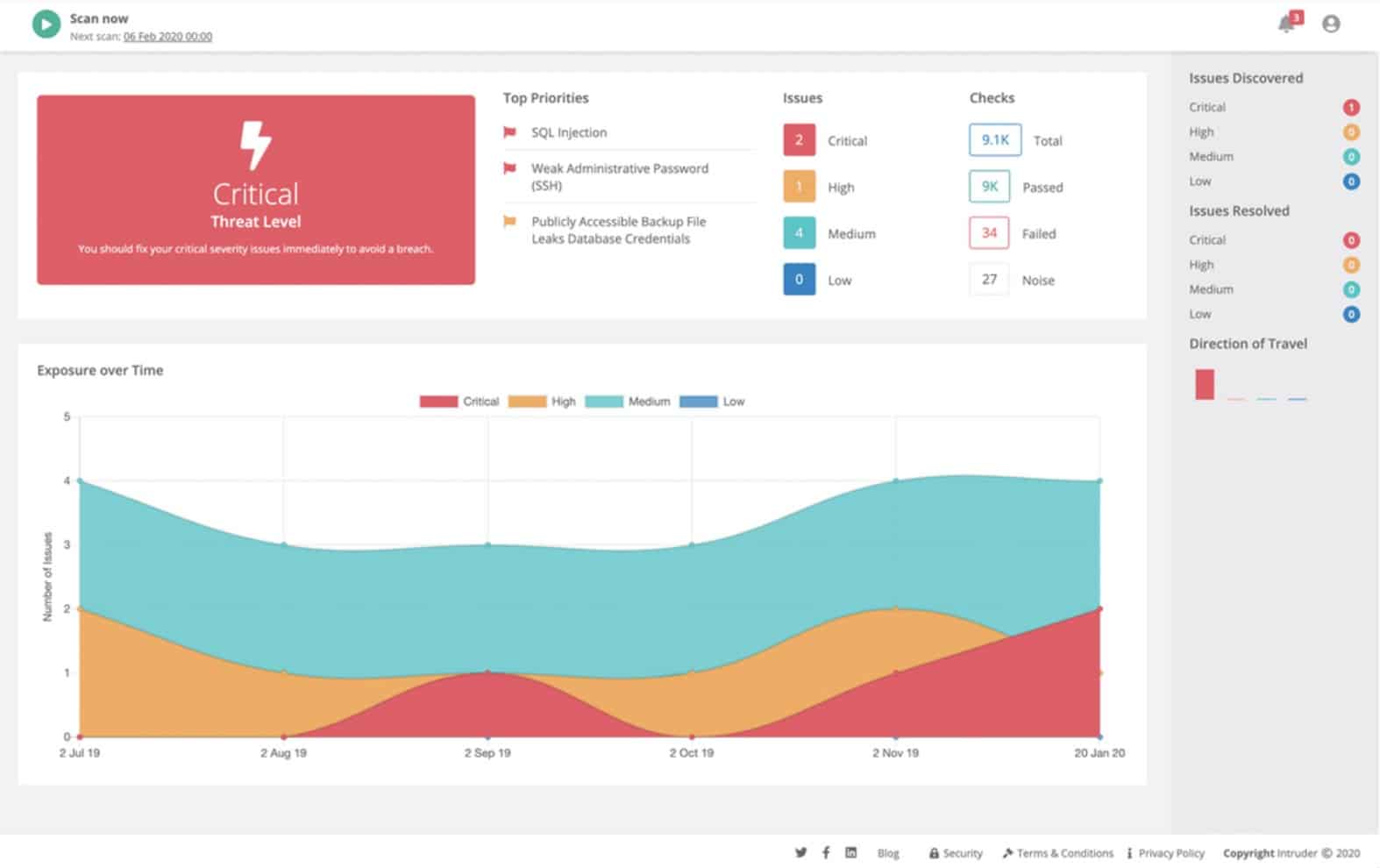
Intruder is a cloud-based security tool that performs constant vulnerability checks on a monitored system. On enrollment, Intruder performs an extensive system sweep, highlighting security issues. Thereafter, the service promptly rechecks the monitored system whenever it receives updated threat information. This ensures immediate response to emerging threats, allowing for proactive scanning and continuous monitoring, rather than relying on a once-per-month update schedule.
Key Features
- Cloud-based: No need to host the software
- Vulnerability scanning: Looks for security loopholes
- Attack surface reduction: Includes cloud service scanning
Why do we recommend it?
Intruder is a cloud-based service that scans networks bother externally and internally to detect security weaknesses. The extent and frequency of the scans that you get depend on which plan you choose. This system can spot misconfigurations on network services, gateways, and endpoints and helps you fix them.
Threat updates trigger new sweeps automatically, ensuring continuous monitoring. It’s important to note that while new hardware or software in the system may not be automatically detected, our platform mitigates this by proactively monitoring the network and automatically launching vulnerability and network scans. This saves valuable time for technical teams and ensures timely detection of network changes.
Who is it recommended for?
The three plans of the Intruder service make the system accessible to businesses of different sizes. However, its cheapest plan is probably still too expensive for small businesses. The cloud-based scanner gives you external scanning but you can upgrade to a higher plan and get scans within your network as well.
Pros:
- Choice of regular or monthly scans: Depends on the chosen plan
- Emergency checks on the discovery of a new threat: The server scans for that newly discovered weakness
- Customizable automation rules: Create playbooks for automated responses
Cons:
- The cheaper plans don’t have all the security features: You would need the top plan for full protection
Intruder is charged for by subscription and is available in three editions: Essential, Pro, and Vanguard. The Essential plan doesn’t include on-demand testing, however, it includes unlimited ad hoc on-demand scans. This allows administrators to promptly assess new software or hardware additions without having to wait for the monthly scan. Additionally, the Pro plan offers both automatic and on-demand scans, while the Vanguard edition includes the services of human penetration testers. Intruder is offered on a 14-day free trial.
8. CoSoSys Endpoint Protector
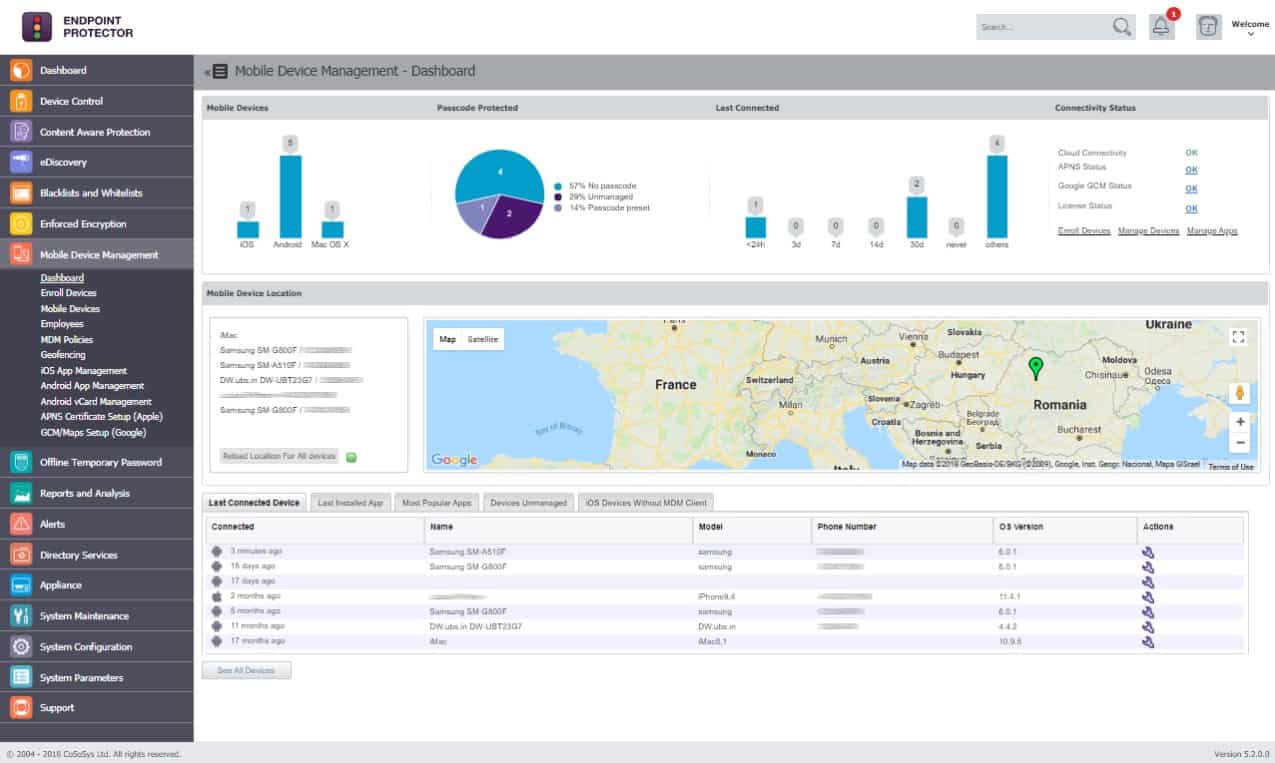
Endpoint Protector by CoSoSys watches over all of the devices on a network from its cloud location. The system requires that each monitored endpoint has an agent installed on it. With the agent in place, the system administrator can command a sweep of all devices for locations of data storage. The service then categorizes data by a sensitivity ranking.
Key Features
- A SaaS platform: Also available as a service on AWS, GCP, and Azure and for download as a virtual appliance
- On-site agents: Install an agent on each endpoint
- Sensitive data discovery: Suitable for GDPR, SOX, HIPAA, PCI DSS, NIST, GLBA, and CCPA
- Data loss prevention: Scans data movements
- Device control: Blocks or allows peripheral devices
Why do we recommend it?
CoSoSys Endpoint Protector implements network security by gathering activity data on each connected device. Malicious activity on the network is aimed at your endpoints and particularly data. When data is moved onto the network for exfiltration, the system will raise an alert if the user account involved is not authorized for such an action.
The Endpoint Protector system allows system administrators to define security policies that vary the allowed actions of different user groups and employee statuses. The controls over data access can also be varied per department. Thus, different types of data can be accessed and/or changed in different ways according to the user. Inappropriate data access attempts will trigger alerts.
Utilities on the network can also be monitored. This extended to communication with printers and USB devices. Again, the degree of control over the movement of data over memory sticks or through printing can be varied according to the sensitivity rating of that information.
Endpoint Protector’s dashboard shows live events across the network. The extent of the systems data control is not limited to one LAN. The service can also monitor data flows in many locations, including in the homes of telecommuters.
Who is it recommended for?
CoSoSys doesn’t publish a price list, which makes its affordability difficult to judge. The service is particularly relevant for businesses that store and use sensitive data. The cloud hosting of this package means that you don’t breed to worry whether you have a suitable server to run the software.
Pros:
- Enroll endpoints anywhere: The SaaS package can manage endpoints anywhere
- Variable security policies: Adapt to different zones of trust
- Sensitive data discovery and classification: Protects PII
- Live activity monitoring: Shown in the system dashboard
- Alerts for unauthorized data access or movement: Get alerts by email
Cons:
- No price list: You have to contact the sales team for a quote
The Endpoint Protector system is offered in a hosted package as a SaaS. The system can also be accessed as a service on AWS, Azure, and Google Cloud Platform. It is possible to get the software for Endpoint Protector and install it on your site as a virtual appliance. There isn’t a free trial available for Endpoint Protector. However, you can access a free demo to assess the software for free.
9. Nessus Vulnerability Scanner
Nessus is one of the leading vulnerability scanners. Its system sweeps check both hardware and software. The tool particularly focuses on device configurations, open ports, and password controls. The system monitors server processes and network traffic, looking for abnormalities.
Key Features
- System security hardening: Scans for known security weaknesses
- Penetration testing tool: No longer free to use
- Hardware option: Store on a USB stick
Why do we recommend it?
Nessus Vulnerability Scanner has been downloaded and used by a lot of businesses in the past. However, this was due to a free edition, which is no longer available. The tool is managed by Tenable, which has created another product family of vulnerability scanners called Tenable.
Nessus is available in two editions: Nessus Expert for in-house use and Nessus Professional for consultancies. Both packages are delivered with Community access for support and have options for professional support as paid add-ons. The Expert edition has more features, such as external attack surface scanning. The producer of Nessus also offers another vulnerability scanning range under the brand name Tenable.
Who is it recommended for?
The Nessus system is available in editions for businesses and consultancies. The business version is called Expert and it is advertised as being suitable for small businesses. However, the price is high and will probably be beyond the budget of most small enterprises. This is a tool for big businesses.
Pros:
- The most widely-used vulnerability scanner in the world: Can run on Windows, macOS, or Linux
- Checks configuration weaknesses and software versions: Produces a vulnerability assessment
- The vulnerability database is constantly being expanded: The system is well-maintained
Cons:
- The free version is no longer available: That option could be the reason that the tool had a high usage statistic
Both editions of Nessus are available for Windows, macOS, and Linux. There is also a portable device available that can plug into any system to scan – that is suitable for use by consultancies. You can get a 7-day free trial of either Nessus edition.
10. ZAP
ZAP is an open-source system that is a fork of Paros Proxy – another very popular network security tool. ZAP stands for Zed Attack Proxy and until recently, this free software was managed by the Open Worldwide Application Security Project (OWASP). Since August 2023, the system has been managed by The Software Security Project.
Key Features
- Free to use: An open source system run by the Software Security Project
- Security testing tool: Works as a penetration testing tool
- Operates between a Web server and a Web browser: Checks for Web application vulnerabilities
Why do we recommend it?
OWASP Zed Attack Proxy (ZAP) is a free, open-source tool for Web application security scanning. This system starts up a proxy server between your browser and the Web server, capturing traffic as it passes from one side to the other. It will scan the Web application for weaknesses and enable the tester to launch typical hacker attacks.
Despite acting as a proxy, this system is a remote service. It is downloadable software that you need to host yourself. The purpose of the system is to protect a web system from hacker interference. The method of this service is to analyze a web page, looking for SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) attacks. It also scans for faulty authentication and session management, system configuration weaknesses, poor access control, unprotected APIs, known vulnerabilities, and sensitive data exposure.
Who is it recommended for?
OWASP ZAP is a very widely-used penetration testing tool. The gold standard of penetration testing goals is the OWASP Top 10, so the ability to test for those weaknesses with a tool produced by the definers of those vulnerabilities is an opportunity that no one can pass up.
Pros:
- Created by the people who defined the OWASP Top 10: Responsibility has since been moved to another organization
- Offers lots of customizations through plug-ins: You can also adjust the code if you want
- Good for ensuring the security of Web-based assets: Not a system for endpoint scanning
Cons:
- No professional support: Has a strong community
This network security software is free to use and is extensible by plug-ins, which are also available for free. Those add-ons as well as tips and support are available from the user community. The software runs on Windows, macOS, Linux, and BSD Unix.
11. Zscaler Cloud Firewall
Zscaler is a “firewall as a service” (FWaaS). It runs as an edge service and can monitor a distributed fleet of devices. You don’t need to limit the application of this service to one network in one building. The service creates a virtual network that can extend across the internet to reach its users wherever they are.
Key Features
- Comprehensive defense: Protects LANs and virtual networks
- Can cover multiple sites: Also provides traffic management measures between sites and cloud services
- SaaS service: An edge system that connects to sites over VPNs
Why do we recommend it?
Zscaler Cloud Firewall is part of a rapidly expanding platform of services that aims to provide a complete Zero Trust Access solution. The Cloud Fireaall is a Firewall-as-a-Service (FWaaS). It protects on-premises systems as well as cloud services from external malicious traffic. It partners with an access hub for user authorization.
The Zscaler methodology is to protect the connections between a community of users. It doesn’t need those connections to be over a single network – it will protect communications over the internet to anywhere, so it is great for companies that use a lot of home-based telecommuters. It is also very easy to grant system access to BYOD users with the Zscaler service.
Who is it recommended for?
Any business that has remote and roaming users and also deploys cloud-based SaaS packages for all users ends up getting into a nightmare of access control and connection security issues. The Zscaler platform combines both access control and connection protection with the FWaaS as a barrier to outsider traffic.
Pros:
- Secure multiple sites and include individual remote computers: Creates a unified public IP address for incoming traffic
- Easy to set up and use: Suitable for small businesses
- Offers a range of secure virtual networking options: Can implement SD-WAN and SASE
Cons:
- A menu of security options: The full capabilities of the Zscaler stable are much greater than this one product
All of the processing and anomaly detection of the Zscaler system is run on the service’s host; only a small agent program needs to be installed on protected devices. Essentially, Zscaler creates a virtual network through a series of VPNs. However, the service is more complicated than a VPN because it implements security policies as well as enforcing connection privacy.
12. Burp Suite
Burp Suite is a collection of cybersecurity tools that are useful for penetration testing (pen testing). The suite also features a vulnerability scanner for automated network security sweeps. The key strategy of Burp Suite is to simulate an attack on a network and then list the access attempts that proved successful. The results of this exercise can then be investigated further.
Key Features
- Penetration testing tool: Includes reconnaissance and attack modules
- Free version available: Provides services for manual testing
- On-premises package: Available for Windows, macOS, and Linux
Why do we recommend it?
Burp Suite is a widely-used system testing tool that can explore a network for reconnaissance and also launch an attack. The tool is available in free and paid editions but both versions actually receive the same package. Free users will find that automated vulnerability scanning features are turned off.
There is a Community Edition of Burp Suite that is free to use. This version of the software does not include access to a professional support team, so users have to rely on the community for advice. The Community Edition doesn’t include automated tools, such as the vulnerability scanner.
There are two paid versions of Burp Suite. The Professional Edition includes more sophisticated tools for pen testing and also the web vulnerability scanner. The highest version is called Enterprise. This includes repeated vulnerability scanning and scheduling for network security sweeps. This version can also be used for software testing during development.
Who is it recommended for?
This system is one of the definitive tools that every penetration tester is trained to use. The system can also be helpful to hackers. The paid edition is very expensive, so most independent consultants will use the free version. Most of the paid version’s buyers are security consultancies.
Pros:
- Automated vulnerability scanning: Available in the two paid editions
- Data flows: Investigation screens can copy over discovered data into attack utilities
- Can be used for development testing: Continuous testing with the Enterprise edition
Cons:
- The paid version is very expensive: Small businesses would probably opt for the Community edition
Burp Suite is available for installation on Windows, Linux, and macOS. There is no free trial of the vulnerability scanner, but you could access the Community Edition to get a feel for the style of operations of Burp Suite before buying.
13. Teramind DLP
Teramind DLP is a data security tool that is an important data protection system for those businesses that need to get standards accreditation. The Teramind data loss prevention system is written to the PCI DSS, HIPAA, ISO 27001, and GDPR standards.
Key Features
- Data loss prevention: Focuses on malicious insiders
- Activity tracking: Lower plans offer productivity assessments
- Scans outgoing emails: Block unauthorized data movements
Why do we recommend it?
Teramind DLP focuses on preventing data theft or accidental disclosure by authorized accounts. The insider threats could be disgruntled employees or hackers who have stolen or cracked account credentials. The tool scans network activity as well as events on endpoints. The tool can also block data transfers to protect sensitive information.
The Teramind system aims to spot insider threats and block data disclosure. The type of data that has been selected from the settings will be searched across the network to find all instances of that data type. Those data stores are then tracked very closely.
Who is it recommended for?
This system is needed by any business that stores and processes sensitive data, such as personally identifiable information (PII). The insider threat protection also blocks theft attempts by outsiders because access controls on files mean that those external thieves can only get at data through an authorized account.
Pros:
- PII management: Identifies, categorizes, and protects sensitive data
- Compliance management: For PCI DSS, HIPAA, ISO 27001, and GDPR
- Fraud detection: Can apply to customer accounts as well as internal accounts
Cons:
- No on-premises version: Only available as a SaaS package
Insider threat protection involves a constant scan of user activities on the network and company-provided applications. The system monitors emails and other communications, looking for data disclosures. Users that are identified as potential data leakers can then be monitored more closely with extra tools, such as a keystroke logger.
Network Security FAQs
What are the types of network security tools?
Three are many types of network security tools
- Network Access Control (including multifactor authentication)
- Gateway security (including firewalls)
- Web security (including VPNs)
- Wireless security
- Network security policies
- Vulnerability management
- Network penetration testing
- Data loss prevention
- Threat prevention (includes insider threat management, intrusion detection systems and SIEMs)
- Address controls
- Endpoint security (including anti-malware)
- Application Security
- Email security
How does the CVE standard make network security devices and tools more effective?
The Common Vulnerabilities and Exposures program (CVE) is a list of commonly-known system weaknesses. Sharing this information allows network security software to be written in order to catch vulnerabilities and the CVE standard also gives network managers a yardstick by which to measure the effectiveness of network security tools.
Which two basic functions are performed by network security tools?
The two basic purposes of network security tools are to block unauthorized access and to prevent unauthorized actions.