Both SentinelOne and CrowdStrike Falcon are relatively new brands but both have risen to prominence in the cybersecurity industry. Both are hybrid on-premises/cloud-based systems that users access through a web browser. Both require agents to be installed on the equipment to be monitored.
The Software-as-a-Service model deployed by both SentinelOne and CrowdStrike Falcon lessens the amount of processing that has to take place on the device. However, that remote server activity is limited to analysis and the bulk of the protection work still takes place on the device. The cloud-based console makes it very easy to monitor the security of a large number of endpoints from one central location.
The field of security software has been going through big changes over the past decade. Traditional anti-virus systems have been superseded by more complex bundles of protection software.
It is no longer enough to just check for known malicious software. Hackers have adopted new strategies that include breaking into networks both manually and through automated processes. They can retain access to the system for years, keeping their presence a secret by altering system and log files to remove traces of their activities. Hackers don’t need to create bespoke software because they can deploy the standard, legitimate software already installed on the target device to explore files and databases and reap sensitive data.
SentinelOne and CrowdStrike use AI machine learning techniques to protect endpoints from intrusion. While focusing on activities, neither has completely abandoned the task of searching for malicious software. Malware detection is now one of a number of checks that each package deploys.
These two endpoint protection systems use similar architecture and strategies, so it is difficult to choose between them. However, examining their procedures in more detail, it is possible to note fundamental differences between the two. Let’s take a look at the features of each so that you can see which meets your needs more precisely.
SentinelOne
SentinelOne was founded by cybersecurity professionals who spotted a gap in the market between straightforward AVs and the tailored, consultancy-based cybersecurity protection that big-budget organizations enjoy. The company operates offices in North America, Europe, the Middle East and the Far East.
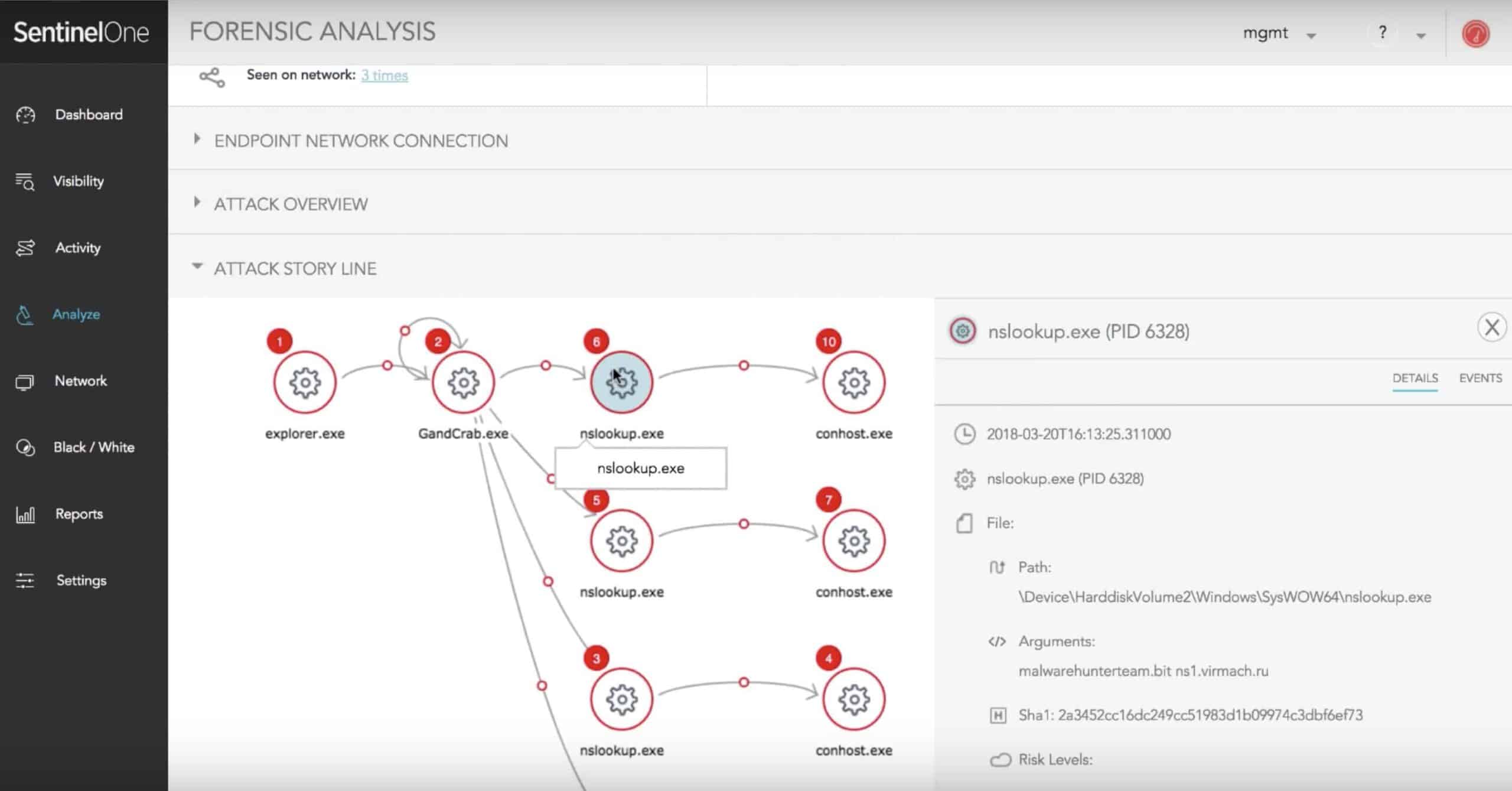
The SentinelOne website presents the software as a threat protection system. However, they haven’t overlooked malware detection. An agent on the protected device performs all of the work, while reporting back to a management console at the SentinelOne servers.
The agent uses AI machine learning techniques to establish normal activities on the device and then identifies deviations from that norm. The protection system establishes rollback points and identifies log file statuses. Unusual processes indicate potential threats that require further attention.
Artificial Intelligence is a major feature of SentinelOne. The initial phase of investigation deploys “static AI” procedures. That just means that the system executes a series of checks to identify potential weak points in a system and log them for monitoring. The threat monitoring phase uses “behavioral AI,” which is the anomaly detection system.
Once a threat has been identified, protection measures swing into action. These procedures don’t involve AI but call on a library of action scripts. An anomalous process gets stopped, a damaged file gets rolled back, a suspicious user gets suspended and an IP address that is the source of suspicious activity gets blocked from access.
Although the presentation of SentinelOne states that the AI element of the tool removes the need for signature databases, the coding of the AI engine itself involves a certain amount of reference information. The fundamental identifier of AI is that its actions are optionally selected from a range of possible alternatives based on probability, effectively creating a database of code. Those procedures are derived from the records of previous attack strategies.
Examining the description of the system, it seems that the agent software in SentinelOne is a much more important component of the protection system than the remote server. The agent acts as the antimalware software, while the server element is more of a reporting tool.
A big advantage of this architecture is that it doesn’t require a constant connection through to the server in order to operate. This could be vital in the event of a system-wide attack that disables the network or blocks access to the internet.
Data that should be sent to the server for analysis can be stored and uploaded once a network attack has been resolved and contact becomes possible again. However, in the meantime, the protection procedures of SentinelOne continue to be fully operational.
Pros:
- Leverages AI to identify new and evolving threats
- Offers great data and workflow visuals in the admin console
- Can automatically rollback damaged files from ransomware or infection
- Endpoint agents can function even if their connection to the C&C server is broken
Cons:
- Would like to see a trial rather than a demo before purchasing
CrowdStrike Falcon
CrowdStrike Falcon is available in four editions: Falcon Pro, Falcon Enterprise, Falcon Premium, and Falcon Complete. The Falcon title refers to a threat protection platform. The platform is a suite of utilities, each of which implements a separate protection strategy. The number of modules that are included in each edition marks the difference between each service plan.
As the name suggests, Falcon Complete includes the whole lot. It also comes with a team of technicians to run the system for you. It is a managed service. At the other end of the range, Falcon Pro includes the least number of modules.
Those modules are:
- Falcon Prevent The antivirus software included in all editions.
- Falcon Intelligence The threat intelligence engine included in all editions.
- Falcon Insight Endpoint detection and response. Not included with Falcon Pro.
- Falcon Overwatch Threat hunting. Not included with Falcon Pro.
- Falcon Discover An IT hygiene module. Not included in Pro or Enterprise.
- Falcon Device Control An optional extra module that monitors all attached devices.
Already, we can see a major difference between the two endpoint security packages. CrowdStrike Falcon offers a menu of modules, whereas SentinelOne is an all-in-one total solution.
Falcon Prevent is a next-generation AV system. Like SentinelOne, this module removes the need for the traditional malware signature database. Also, like SentinelOne, this function is implemented by an agent resident on the endpoint. This protection can continue even when the endpoint is isolated from the network and cannot contact the CrowdStrike server. However, CrowdStrike emphasizes the lightweight nature of its agent, having little impact on the CPU of the protected endpoint.
The Falcon Prevent module performs most of the protection activities available in SentinelOne. It explores the device for weaknesses and checks off known points of vulnerability. It establishes a baseline of normal activity and then looks for deviations from that pattern. It then shuts down rogue processes and blocks access to suspicious users and IP addresses.
Falcon Intelligence is where the CrowdStrike system deviates from the SentinelOne solution. This is a threat analysis system that occurs in three locations: on the endpoint, on the CrowdStrike server, and within the CrowdStrike expert team. Essentially, once an attack has been detected and dealt with, the software on the endpoint records what happened and which procedures shut down the attack and then prioritizes the detection of that event for ongoing protection.
The records of that threat, how it occurred, and how it was blocked are uploaded to the CrowdStrike server, where the behavior of the attack on one endpoint for one customer is pooled with results uploaded by other clients. Thus, with data aggregation, the server processes of the Falcon Intelligence system can alert what seems to have become a coordinated global attack and identify new attack strategies.
Cybersecurity specialists employed by CrowdStrike get access to this aggregated data and perform further analysis to make sure that the software hasn’t missed anything. The results of this analysis might cause the company to redesign parts of its system. The analysis also provides source material for advisory notifications circulated to customers and warnings that can be issued to the wider business community.
Falcon Insight aims to detect Advanced Persistent Threats. In an APT, a hacker gains access to a system, creating an apparently valid user account or acquiring an abandoned account. This allows the intruder to gain long-term access to all of the resources of the system and the data contained within it.
Falcon Overwatch provides the services of a human threat hunting team. The publicity for this service explains that the CrowdStrike specialists will proactively hunt for threats within your environment.
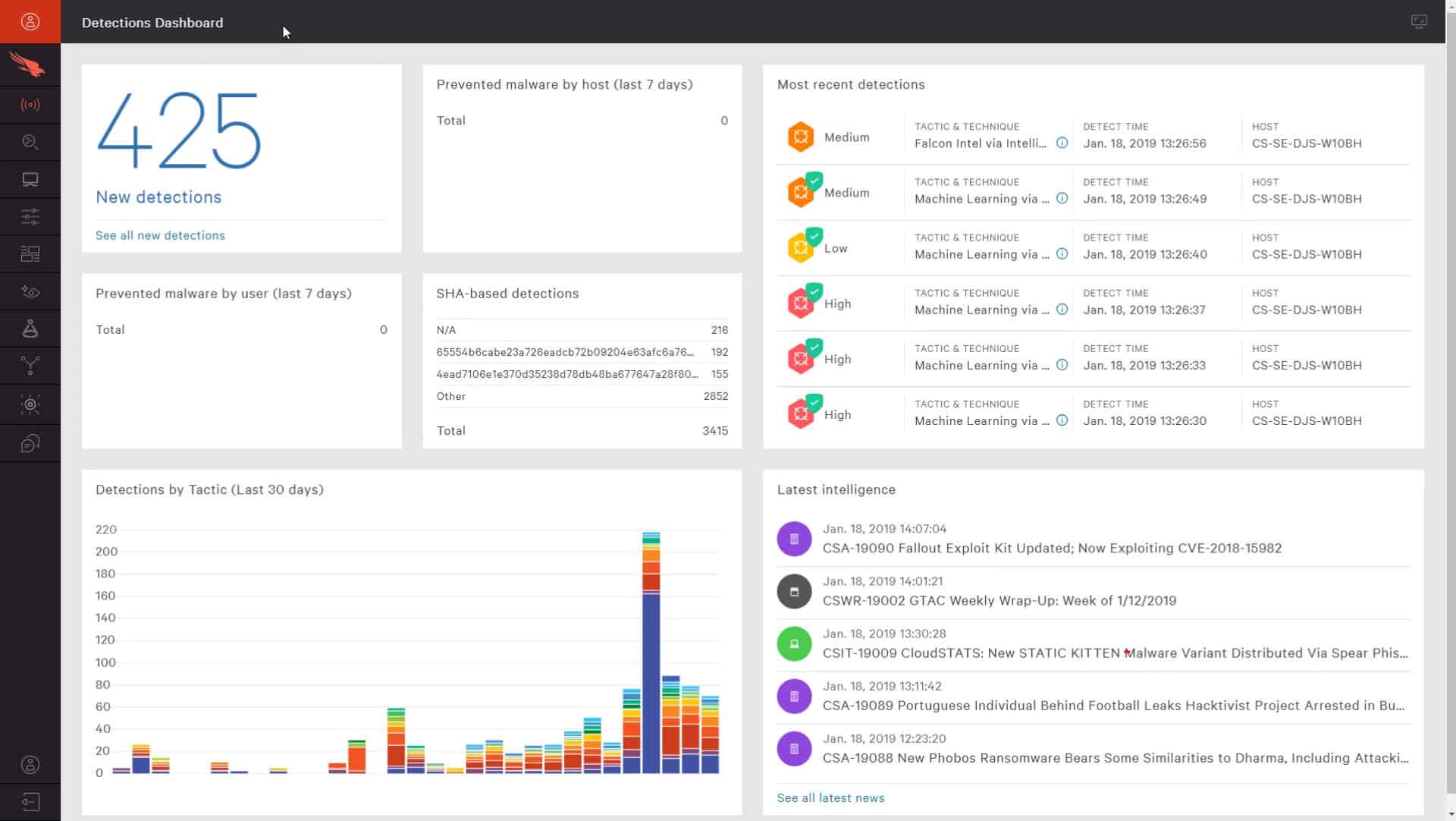
On the face of it, this service is a little worrying and is probably not explained very well. It sounds as though these remote experts will randomly log into your endpoints and explore their files and services, much in the way that a hacker would. This would amount to unwanted intrusion that would invalidate your system protection measures for data security standards compliance, so the explanation of the service is probably misleading.
In reality, the cybersecurity team doesn’t need to break into your endpoints because the agent software reports back on security breach events and that information should be enough source material for the analysts of Falcon Overwatch to work on. This service aims to fine-tune threat management procedures to reduce threat detection false positives.
Falcon Discover is a vulnerability scanner that searches through an endpoint, logs all of its software, file storage, user activity, and access events, and identifies weak points in the system, such as abandoned accounts. This is an extra service that SentinelOne doesn’t have.
Falcon Device Control isn’t included in any of the Falcon editions but is an optional extra. This specifically monitors USB ports. It identifies each USB device that gets connected to the endpoint and allows an administrator to specifically authorize that device for use with the endpoint. All USB devices that haven’t been approved get blocked from attaching to the operating system.
Pros:
- Offers products that can fit any size network and budget
- Sysadmins can choose options from different modules, allowing them to customize their endpoint security
- Can be configured to monitor for compliance (HIPAA, SOX, etc.)
- Lightweight agents take up very little system resources in the background
Cons:
- Could benefit from a longer trial period
CrowdStrike Falcon is available on a 15-day free trial.
SentinelOne and CrowdStrike Falcon
SentinelOne is roughly the equivalent of Falcon Pro, the entry-level edition of CrowdStrike Falcon. Both of these security options are able to work independently and are implemented through the agent software that needs to be installed on the endpoint. Essentially, in both cases, this is on-premises software with a management console that is hosted on the service’s remote server.
Both services do away with the need for a central research lab and a team of expert analysts. That strips out a lot of the storage requirements of traditional AV systems because there is no signature database involved in searching for threats. In both cases, the agent behaves more like an endpoint-bound system information and event management tool (SIEM) rather than an old-fashioned AV-firewall combo.
The cloud-based consoles of both SentinelOne and CrowdStrike Falcon enable system managers to gain overviews of threats occurring on individual endpoints and aggregated activity data across all endpoints in the organization that are being protected.
The higher plans of CrowdStrike Falcon – Enterprise and Premium – add on human expert activities and automated intelligence sharing among the CrowdStrike user community. These activities make the CrowdStrike service very similar to the activities of endpoint protection systems offered by traditional AV providers. For example, Falcon Insight and Falcon Overview make CrowdStrike Falcon the equivalent of the Symantec Endpoint Protection package.
By offering different editions, CrowdStrike is attempting to compete with the different threat protection strategies implemented by various competitors. For a direct comparison between CrowdStrike Falcon and SentinelOne, focus more on the Falcon Pro edition.
Fortunately, both of these packages are available on free trials. You can get a free trial of CrowdStrike Falcon Pro and a free demo of SentinelOne. Give each a try and leave a message in the Comments section below to share your opinions with the community.