Interactive Application Security Testing (IAST) is an advanced security testing method used to identify vulnerabilities in web applications during runtime, while they are being interacted with by users or automated test cases. Unlike traditional security testing methods like Static Application Security Testing (SAST) or Dynamic Application Security Testing (DAST), IAST works in real-time and provides deeper insights by analyzing an application from the inside out, as it is running.
IAST operates by integrating with the application’s runtime environment, such as a web server or application server. It continuously monitors and analyzes the application’s behavior while it is being tested or used. This approach allows IAST tools to detect vulnerabilities as they emerge during typical application use, whether through user interactions or automated functional tests. IAST provides detailed vulnerability reports, helping developers identify and fix security flaws more effectively and earlier in the development process.
The key advantage of IAST is its ability to combine the benefits of both SAST and DAST. While SAST scans the source code and DAST tests the application from the outside, IAST bridges the gap by combining code-level analysis with real-world application behavior. This hybrid approach results in more accurate and comprehensive vulnerability detection, without the need for manual code inspection or the complexity of a full penetration test.
IAST tools typically integrate with existing development pipelines, including Continuous Integration (CI) and Continuous Deployment (CD) environments (CI/CD). This ensures that security testing is a seamless part of the development lifecycle, promoting a “shift-left” security approach where security is built into the application early rather than being an afterthought.
Overall, IAST helps organizations achieve faster, more efficient application security testing, reduces false positives, and enhances the overall security posture of applications by providing actionable insights directly from within the running environment.
IAST Explained
IAST is a methodology of application testing where code is analyzed for security vulnerabilities while an application is running. IAST tools deploy agents and sensors in applications to detect issues in real-time during a test. The application can be run by an automated test or by a human tester to find vulnerabilities in the application.
To help the user find coding issues the IAST tool will highlight the segments of code that feature vulnerabilities. Highlighting the code allows the developer to see what code they need to change to remove the vulnerability.
Why is IAST Important?
The importance of using application testing and IAST cannot be overstated. The 2017 Verizon Data Breach Investigations Report found that 29.5% of breaches were caused by web application attacks. Cyber attackers are turning to application layer attacks to get through network defenses. Once they have broken through they can cause damage to sensitive data and put important services out of action.
If you don’t have any defenses in place to protect against application attacks, you’re at high risk of falling victim to a cyber-criminal. Testing models like IAST are critical for finding and eliminating the vulnerabilities an attacker would be looking for.
IAST gives you an opportunity to fix known vulnerabilities before any bad actors can use them as an entry point. To put it another way, application testing helps you to find an entry point and close the door before anyone has a chance to open it.
IAST vs SAST vs DAST: Application Testing Methodologies
IAST isn’t the only type of application testing used today. Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) are two other methodologies used to test applications. Each model is different with its own advantages and disadvantages.
SAST or static analysis is where source code is scanned while the application isn’t running. SAST tools can scan code segments and discover vulnerabilities. Once a problem is found the tool highlights it and provides an onscreen recommendation so that a developer can take action to remedy the issue.
SAST tools are widely used because they are easy to deploy and can detect problems in the source code. These solutions also have a low rate of false positives making it easy for developers to make improvements. SAST tools are used early in the Software Development Lifecycle (SDLC) so that developers can address vulnerabilities ahead of the release.
DAST is a model of testing where applications are scanned while they are running. DAST solutions don’t have access to the source code but allow you to perform a penetration test to find configuration errors and validation issues that attackers use during an SQL injection attack.
DAST is great for penetration testing but it doesn’t highlight source code vulnerabilities like DAST. IAST builds on the foundations laid by DAST and SAST to offer automated scanning. Essentially, IAST is a hybrid solution that combines the best of both solutions. An IAST tool can listen to applications in real-time and highlight errors that make it effective for addressing issues efficiently.
One of the key advantages IAST tools have over other testing methodologies is that they are easy to deploy and scalable, meaning that they fit well within larger environments. Automation functions also allow it to integrate into CI/CD workflows that automate the software delivery process.
The benefits of IAST
As an application testing model, IAST has many advantages over other forms of testing.
In this section we’re going to look at some of the main benefits of IAST:
- Low false-positive rate
- Fast testing
- Easy to deploy
- On-demand feedback
Low false-positive rate
IAST can automatically scan through code to find vulnerabilities without false positives. That means all the code that is highlighted to the user is genuinely faulty and needs to be rewritten.
When using an IAST the user knows that the highlighted code segments and recommendations are legitimate so they can take action to address them immediately. Low false positives stop developers from wasting time investigating functional code.
Fast Testing
The automation included with IAST solutions speeds up the testing process through automatic testing. Even the largest applications can be tested in a matter of hours when the software only scans new or edited code. Faster testing is also sped up further through onscreen recommendations.
The user can view highlighted code segments and recommendations to easily find ways to improve application security quickly and efficiently. Faster testing and recommendations come together to speed up the application testing process significantly.
Easy to Deploy
IAST platforms are ready to deploy out-of-the-box. They don’t need any custom configurations in order to function. That means you can implement an IAST solution and start scanning immediately.
They are also inherently scalable, and able to work well with both large and small applications. The fast deployment and low maintenance scanning capabilities of IAST solutions help to drive the SDLC forward painlessly.
On-Demand Feedback
IAST solutions provide on-demand feedback in a way that static and dynamic testing tools cannot. You can run a scan and receive actionable feedback in a matter of seconds. DAST and SAST scans usually take place periodically, which means there is a lot of time between when applications are tested.
Continuous scanning provides instant feedback that a developer can use to improve the application now. That means less time and money wasted on waiting for code to be scanned and less time exposed to vulnerabilities.
IAST Tools
Every IAST tool on the market takes a slightly different approach to discovering application vulnerabilities. The biggest difference between IAST products is the application programming language that they use. When searching for an IAST tool it is important to pick one that matches the programming language and framework of the applications that you use.
Our methodology for selecting IAST tools
We reviewed the market for IAST systems and analyzed the options based on the following criteria:
- Test automation for development or operations environments
- Options to launch and interactive scan on demand
- Manual tools for testing walk-throughs
- Integration into development environments
- CI/CD pipeline integration with results fed into issue trackers and project management tools
- A free trial or a demo option to enable an assessment before buying
- Value for money from a testing system that includes other tools, such as DAST
In addition, you should select a tool that can monitor vulnerabilities in any open source code that you use. Many products use Software Composition Analysis (SCA) to identify open-source entry points.
Here is our list of the top IAST tools:
- Invicti EDITOR’S CHOICE A vulnerability scanner that includes IAST checks and specializes in testing Web applications. This tool is particularly useful for testing during CI/CD pipelines. Available as a cloud platform service or for installation on Windows and Windows Server.
- Acunetix A choice of packages that offer on-demand or continuous vulnerability scanning. Editions are suitable for penetration testing development teams or IT operations. Offered as a hosted SaaS package or for installation on Windows, macOS, or Linux.
- Datadog Application Security Management This cloud-based package provides security testing for applications under development and threat detection for live Web applications.
- Seeker IAST This is a scanner for web applications that uses active verification and data tracking to check for vulnerabilities. This is a cloud-based service.
You can read more about each of these IAST systems in the following sections.
1. Invicti
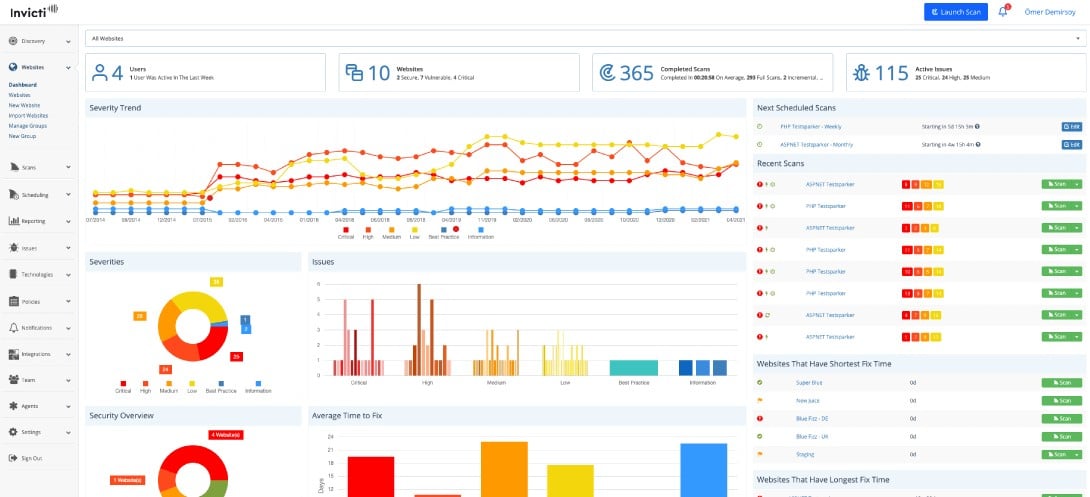
Invicti – formerly Netsparker – is a SaaS platform that offers DAST, SAST, and IAST scanning of Web applications. Those applications can be running live or under development, so the system is a very good choice for use in DevOps environments.
Key Features:
- Comprehensive Scanning Techniques: Combines DAST, SAST, and IAST for thorough web application scanning.
- Vulnerability Detection: Identifies vulnerabilities in web applications with precision.
- CI/CD Pipeline Integration: Seamlessly integrates into continuous integration and continuous delivery pipelines.
- AI-Based Analysis: Utilizes artificial intelligence for heuristic detection of potential issues.
- Flexible Deployment Options: Available as a cloud-based service or for on-premises installation.
Why do we recommend it?
Invicti has many uses. It can be run as a vulnerability scanner for live applications, used by penetration testers, run to verify third-party APIs during selection for a development project, or set up as a continuous tester in a CI/CD pipeline. AI processes extend the tester’s capabilities.
The Invicti vulnerability scanner can be run on demand or set to operate continuously. The service is able to integrate with project management tools and issue tracking services, so it works well as part of a CI/CD pipeline. The scanner doesn’t just work through a list of vulnerabilities because it uses AI-based heuristic detection services to spot potential problems with modules that are under development.
When used as a vulnerability scanner for live Web applications, this system checks through the CVE list of known exploits. The system is able to drill down through APIs to check through the backend code that supplies that services’ functions.
Invicti offers the option of getting the software for the vulnerability scanning service and installing it on your own site instead of using the cloud-hosted version. This software package installs on Windows and Windows Server and it is available for assessment through a demo system.
Who is it recommended for?
This tool is aimed at DevOps teams. It can be used at every stage of development and will scan applications once they are live, sending bug reports back to the development team if problems are discovered. The Invicti system integrates into development project management tools for process automation.
Pros:
- Intuitive Interface: Offers a user-friendly, visually engaging interface suitable for various teams.
- Prioritization with Color Coding: Utilizes color coding and automatic threat scoring to aid in prioritization.
- Continuous Operation: Capable of running non-stop, eliminating the need for scheduled scans.
- Penetration Testing Tools: Includes tools for in-depth security testing, beneficial for specialized teams.
- Varied Subscription Plans: Provides multiple package options, catering to organizations of any size.
Cons:
- Complex Feature Set: The broad array of features may require a significant time investment to fully master.
EDITOR'S CHOICE
Invicti is our top choice for web application security testing because it blends seamlessly into DevOps workflows. Offering dynamic, static, and interactive scanning capabilities (DAST, SAST, and IAST), Invicti stands out as a versatile tool for both live applications and those under development. I particularly appreciated its integration into CI/CD pipelines, making continuous security testing a reality for software projects. One of the key strengths of Invicti is its AI-based heuristic detection, which goes beyond traditional vulnerability scanning to identify potential security risks in modules still in the coding phase. This proactive approach to security is invaluable for teams looking to address issues before they become exploitable vulnerabilities. For DevOps teams tasked with developing and maintaining secure web applications, Invicti’s comprehensive scanning capabilities, combined with its ease of integration and flexible deployment options, make it an invaluable asset. Its intuitive, highly visual interface, coupled with advanced pen testing tools, supports a wide range of security tasks—from routine scans to in-depth penetration testing conducted by internal “red” teams.
OS: Cloud-Based, On-premises software available for Windows and Windows Server
2. Acunetix
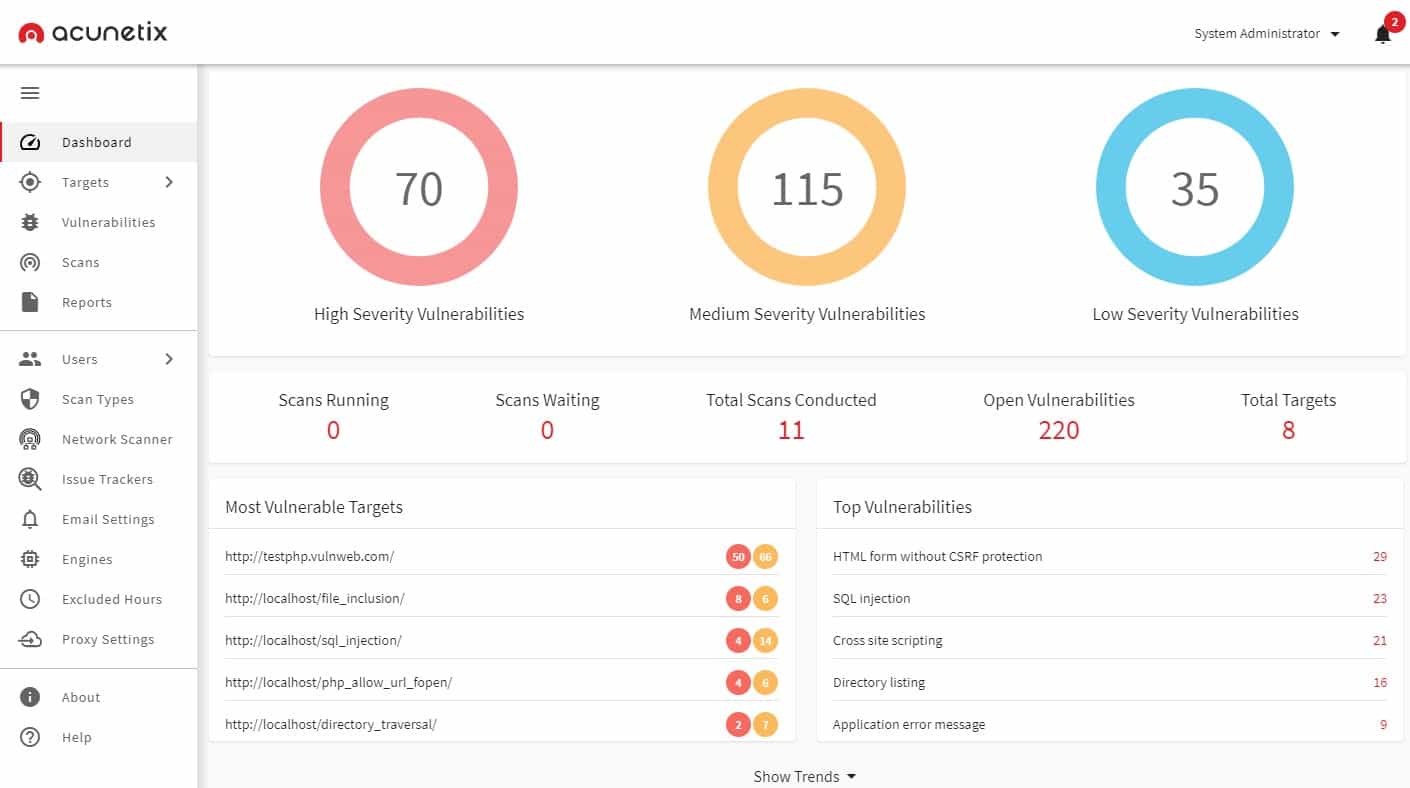
Acunetix is a vulnerability scanner that includes a module called AcuSensor that implements IAST. The service also includes DAST processes and static code scanning to provide SAST. AcuSensor combs through code written in JavaScript, PHP, and .NET framework.
Key Features:
- Comprehensive Scanning Approaches: Offers IAST, DAST, and SAST to cover all bases in vulnerability scanning.
- Internal and External Scanning: Conducts both external and internal examinations of applications for thorough security assessments.
- Automated Scans: Enables automatic scanning for vulnerabilities, streamlining the security process.
- Manual Testing Aids: Provides tools for manual testing, offering a balanced approach to vulnerability detection.
Why do we recommend it?
Acunetix is both a rival and a stablemate to Invicti. This tool has all of the capabilities of its competitor but has slightly more leanings towards vulnerability scanning. You can integrate the free OpenVAS into Acunetix to extend its vulnerability management capabilities to network scanning. This system can also be set up for development testing.
The Acunetix system can be launched on demand or set up to run continuously. You can use the system to scan live Web applications and APIs. This service looks for more than 7,000 known vulnerabilities, including the OWASP Top 10. There is also an edition of Acunetix that will scan networks. This has a list of more than 50,000 system weaknesses to look for.
Acunetix is marketed in three editions: Standard, Premium, and Enterprise. The Standard version only offers manually launched vulnerability scans. All plans are suitable for use to scan Web applications but the Premium edition is the plan that also includes network scanning. You can access the system as a hosted cloud-based service or acquire it as a software package for installation on Windows, macOS, and Linux.
Who is it recommended for?
The differences between Acunetix and Invicti are subtle and any business that is considering a development application security testing system should trial both of them. Both tools can be integrated into development systems for testing and bug reporting and both will test all the way through the DevOps lifecycle into production.
Pros:
- Versatile Environment Support: Compatible with Windows, macOS, and Linux, ensuring flexibility in deployment.
- Tool Integration: Seamlessly integrates with OpenVAS and other tools for extended capabilities.
- Misconfiguration Detection: Identifies and alerts on security misconfigurations, enhancing overall protection.
- Automated Threat Response: Utilizes automation to immediately address threats and prioritize issues based on severity.
Cons:
- Lack of Trial Option: A trial version for comprehensive testing and evaluation would be beneficial.
3. Datadog Application Security Management
Datadog Application Security Management (ASM) is a new tool on the constantly-expanding Datadog cloud platform. Until mid 2022, this system was known as Hdiv Detection. Datadog doesn’t mention the term “IAST” anywhere in its marketing for this package. However, this is what the tool does. Datadog divides the service into two units: Application Vulnerability Management and Application Threat Management.
Key Features:
- Development-Phase Testing: Focuses on identifying vulnerabilities during the software development process.
- Comprehensive Vulnerability Scanning: Scans applications for vulnerabilities to maintain security integrity.
- Detailed Code Analysis: Performs in-depth analysis of code to detect potential security issues.
Why do we recommend it?
The two units of the Application Security Management package provide options for businesses to choose development testing, vulnerability scanning, or both. This system focuses on microservices that are hosted on serverless cloud systems. Those units could be your own modules of functions supplied as libraries or APIs by third parties.
Datadog already has an Application Performance Monitoring unit. This module has moved away from monitoring software, in general, to specifically tracking the activity of Web applications through distributed tracing and code profiling. The ASM units are add-ons to the APM rather than standalone units.
Who is it recommended for?
One of the biggest reasons to recommend this tool is that it is part of the Datadog platform of system monitoring and management modules. The need to have the Datadog APM running in order to use either ASM unit means that current users of the APM are the most likely businesses to choose the Application Security Management systems.
Pros:
- Seamless Integration: Integrates flawlessly with other Datadog monitoring systems for comprehensive oversight.
- SIEM Tool Compatibility: Capable of forwarding reports to SIEM tools for enhanced security incident management.
- CI/CD Pipeline Compatibility: Fits into continuous integration and continuous delivery pipelines, enhancing DevOps workflows.
Cons:
- Dependent on Other Services: Requires Datadog’s APM and other modules for full functionality, limiting standalone use.
- Different Focus Areas: The Application Vulnerability Management unit is more closely aligned with IAST than the Application Threat Management module, affecting selection based on specific needs.
The Application Vulnerability Management unit is closer to an IAST than the Application Threat Management module and it is considerably cheaper. You would need to examine either of these systems in conjunction with the Datadog APM and Code Profiling services. You can get a 14-day free trial of any or all Datadog modules.
4. Seeker IAST
Seeker IAST is another IAST tool that uses active verification and data tracking to analyze web-based applications. Active verification technology can automatically test known vulnerabilities and assess whether they are exploitable. The main difference between this platform and other solutions is that Seeker IAST can determine whether a vulnerability can be exploited by an attacker.
Key Features:
- Exploitability Analysis: Delivers detailed explanations of potential attack vectors, enhancing understanding of vulnerabilities.
- Integrated IAST and SCA: Combines Interactive Application Security Testing (IAST) with Software Composition Analysis (SCA) for comprehensive coverage.
- Seamless CI/CD Integration: Integrates smoothly into continuous integration and continuous delivery pipelines, supporting DevOps practices.
Why do we recommend it?
Seeker IAST from Synopsis is a typical IAST service code scanning and verification and vulnerability testing that can be applied all the way through the DevOps cycle. The service generates a list of vulnerabilities that need to be dealt with and orders them by priority. The package also protects sensitive data.
The Seeker IAST application provides you with a real-time view of the top security vulnerabilities in your applications. With almost zero-false positives you can be certain that the vulnerabilities you see are legitimate. The program also has an SCA solution called Black Duck Binary Analysis onboard, which can identify vulnerabilities in open-source software.
Integration is where Seeker IAST is at its strongest. There are native integrations, web APIs, and plugins to help your DevOps team to onboard the program straight into your environment. Likewise, these features mean the software fits neatly into your CI/CD workflow.
Who is it recommended for?
The sensitive data protection features of this package make it pretty unique. So, businesses that develop and manage Web applications that are expected to deal with PII are the primary market for this system. The Seeker IAST tool contributes towards compliance with GDPR and PCI DSS.
Pros:
- Intuitive and Visual: Features a user-friendly dashboard with excellent visual representations of vulnerabilities.
- Prioritized Vulnerability Ranking: Automatically and accurately ranks vulnerabilities to focus remediation efforts effectively.
- Extensive Integration Options: Provides robust documentation and a wide range of plugins for easy integration into existing systems.
Cons:
- Quote-Based Pricing: Requires contacting sales to get a pricing quote, which may delay the decision-making process.
If you’re looking for a solution that’s easy to use with lots of integration and an SCA, Seeker IAST is an excellent choice. However, you will have to request a quote from the sales team.
What is IAST? A Cybersecurity Essential
Application testing is no longer an option, it’s a must-have. Enterprises that are using or deploying applications need to monitor them to make sure there are no entry points for attackers to exploit. It only takes one vulnerability for an attacker to breach a network and wreak havoc.
Most companies wouldn’t leave a computer unprotected so they shouldn’t do the same with an application. Application attacks are a reality now and enterprises have to adapt to stay secure.
Deploying an IAST platform can go a long way towards closing down any entry points into your network and making sure your applications are secure. Taking the time to develop a secure application will help to reduce the chance of downtime or damage to personal data.
IAST tools FAQs
What is the best IAST tool?
The four best Interactive Application Security Testing (IAST) tools are:
- Invicti
- Acunetix
- Hdiv Detection (IAST)
- Seeker IAST
What is IAST technology?
IAST is “interactive application security testing.” The technology is a form of vulnerability scanner that can also be used as a penetration testing tool and for pre-release rests in a CI/CD pipeline. IAST systems combine the operations of dynamic application security testing (DAST) and static application security testing (SAST). A SAST system scans through code and looks for known security mistakes that can provide hackers with an opportunity to compromise the applications. A DAST service runs a module and watches its behavior, specifically its function calls to other modules, the resources that it accesses, and its outputs.
What is IAST stands for in application security?
IAST stands for Interactive Application Security Testing. It is an automated system testing method that is designed for use with applications that are designed to run on the Web and particularly systems that are composed of microservices.