Identity and Access Management (IAM) tools are vital for overseeing and controlling access to an organization’s IT resources, ensuring that users can only access what they are authorized to. These tools provide a systematic framework for creating and enforcing access policies, determining which users have the appropriate permissions to access specific resources at any given time.
IAM systems manage user identities and permissions, playing a key role in safeguarding sensitive data and preventing unauthorized access. They simplify tasks such as onboarding new users, adjusting permissions, and removing access when it’s no longer needed. By centralizing access control, IAM tools enhance both security and operational efficiency.
IAM tools assist organizations in meeting regulatory and compliance standards by providing audit trails, reporting features, and access monitoring. With these systems, security protocols are followed and enables organizations to quickly respond to potential security incidents. Overall, IAM tools help organizations maintain secure, compliant, and efficient IT environments.
Here is our list of the best IAM tools:
- ManageEngine AD360 EDITOR’S CHOICE This is an on-premises system that provides a group of ManageEngine access rights systems in a bundle. Get AD management functions and user activity tracking to ensure data protection standards compliance. Run s on Windows Server. Get a 30-day free trial.
- NordLayer (GET DEMO) This system security product implements application-centric security that includes an identity and access management service. This is a cloud-based platform.
- ManageEngine ADManager Plus (FREE TRIAL) This software package offers a way to unify the management of many AD instances, across utilities, such as file systems, Microsoft 365, and Skype. Runs on Windows Server. Start a 30-day free trial.
- Microsoft Azure Active Directory – From the makers of the most used operating system platform, which means it can easily be implemented on most networks and integrates well with existing access control systems.
- Oracle Identity Cloud Service – A cloud IAM is from another major technology company that specializes in database software and middleware and knows the importance of securing its products and the data on it; it comes with advanced features.
- SolarWinds Access Rights Manager An AD interface that also provides security features, such as data loss prevention and threat hunting. This tool also provides logging and auditing tools for data standards compliance.
- IBM Security Identity and Access Assurance – another major IAM that works well in on-premises, cloud, and hybrid networking environments; it works well in the background without monopolizing resources.
- SailPoint IdentityIQ – an identity management solution that works in both cloud and on-premises environments which also uses AI and machine intelligence to ensure future-proof security.
- Ping Identity – a popular choice, this IAM is an advanced solution that works for any device and can handle millions of accounts making it a favorite among financial and banking institutions.
The best IAM tools
Basically, a good IAM tool should be able to answer three questions:
- Who is allowed access? All accounts need to be verified before they are granted any access.
- Which account should have access to what? It should be able to allocate the correct roles and privileges to each user account and allow them the exact required rights and nothing more.
- How are they using that access? Once users are allowed access, they need to be monitored to see if there are any problems with accessing resources or if accounts are being used with malicious intent.
An IAM should also offer the following features:
- Cross-application and cross-network authentication
- Enforce password and use policies with ease
- Ease of implementation and administration of the tool
- Reduce IT costs by cutting time spent on administering user accounts or completely replacing manpower by taking the job to the cloud
- Ability to work with all systems on a network including legacy ones
- The capability of handling thousands – if not millions – of accounts spread across the globe, and without a glitch
- Help achieve compliance with regulations like HIPAA and GDPR which require strict security rules
Our methodology for selecting identity access management tools
We reviewed the market for identity access management software and analyzed the options based on the following criteria:
- A service that can interface with Active Directory or LDAP implementations to improve user account management
- A system that is able to analyze device permissions to improve security
- A single point of access to manage several access rights management instances
- User activity monitoring
- Tight access controls to the IAM itself.
- A free trial for a risk-free assessment period or a money-back guarantee
- Value for money in the toolset offered for the price
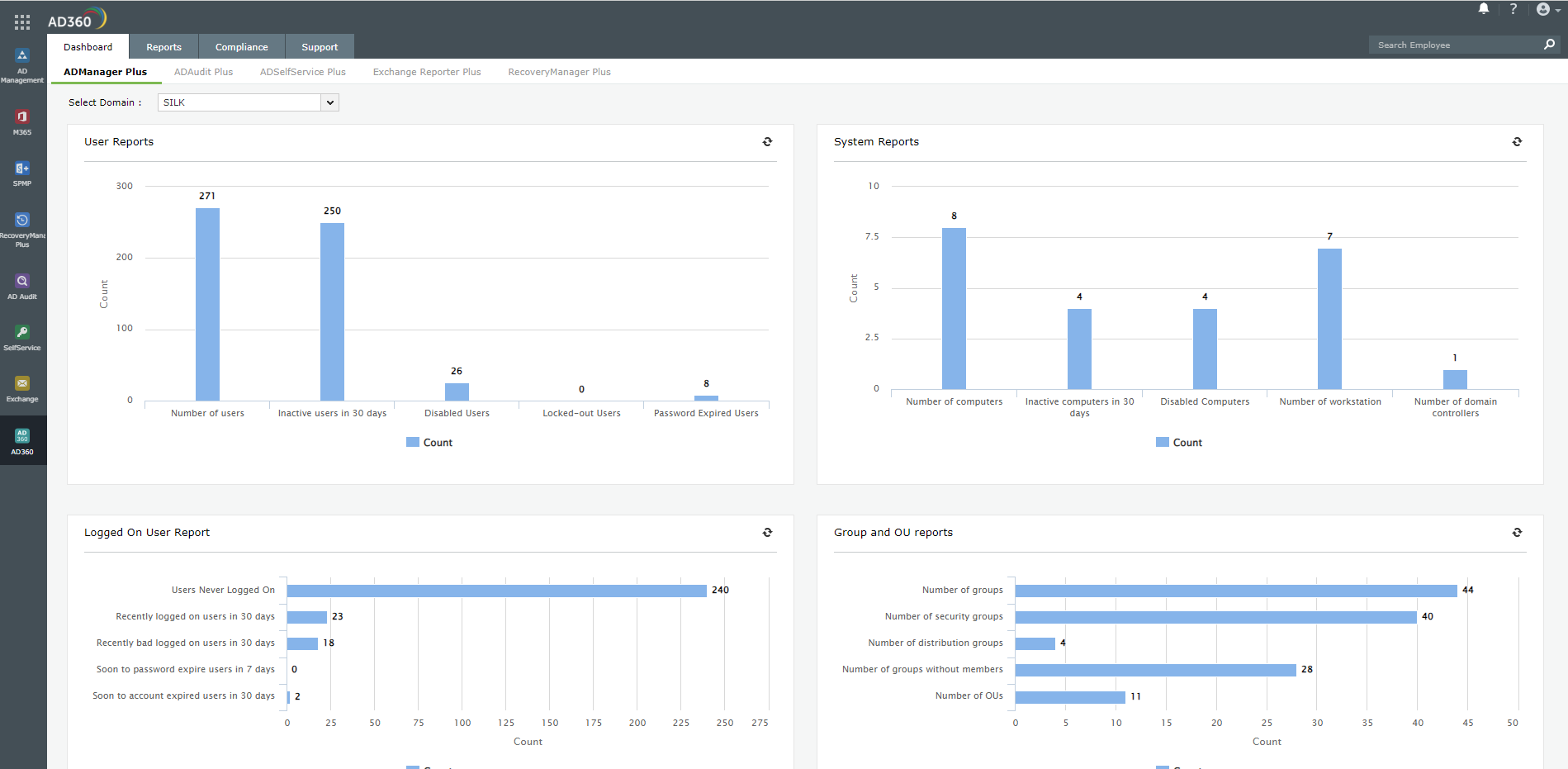
1. ManageEngine AD360 (FREE TRIAL)
Tested on: Windows Server
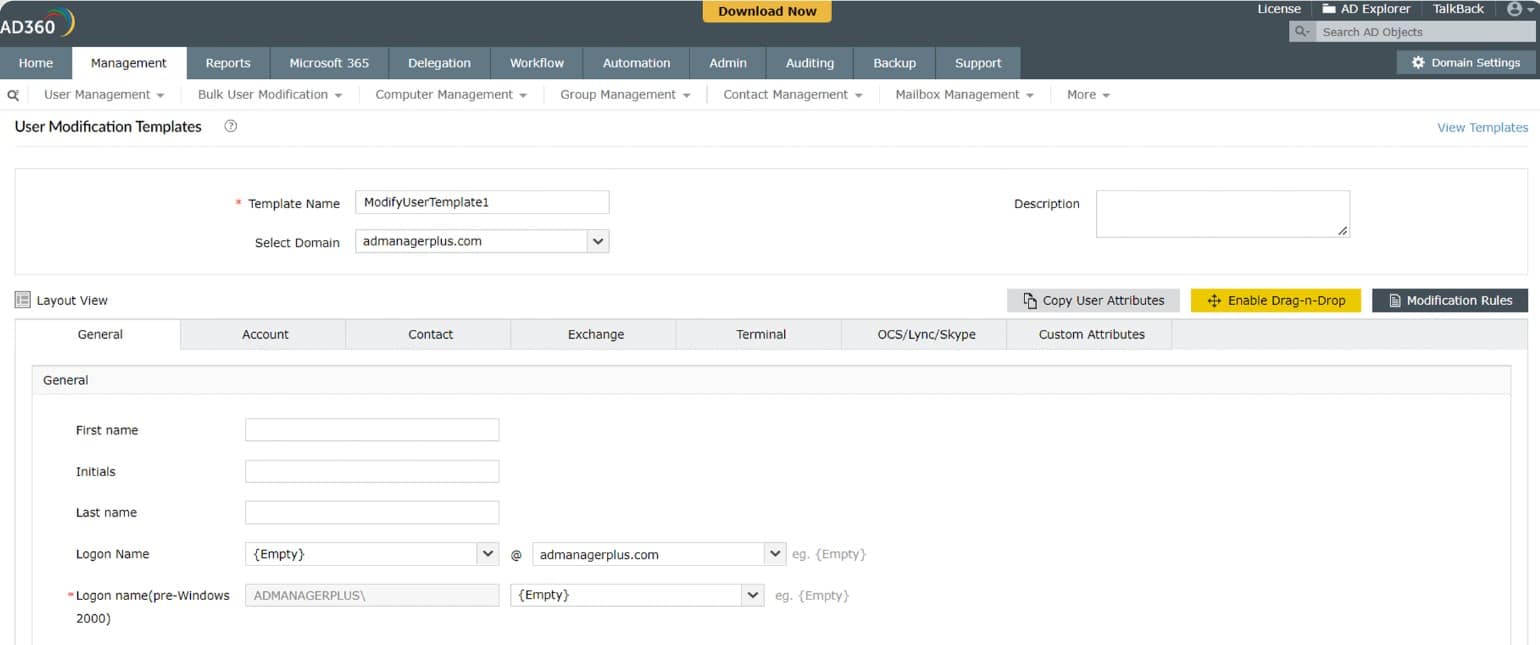
ManageEngine AD360 is a pack of important access rights management tools that are available individually from ManageEngine. The two most important units in this bundle are ADManager Plus and ADAudit Plus. As the names of all of these tools indicate, the AD360 package is focused on enhancing the functions of Active Directory.
Key Features:
- Manages Multiple Domains: Provides a single front end for multiple DCs
- AD User and Group Management: Prompts granular groups for more precise permissions management
- Bulk Account Management: Upload and update many accounts with a single command
- Manages Cloud Application Access: Manages accounts for Microsoft365, Google Workspace, and Skype for Business
- Manages Cloud AD: Look after Azure AD with this package
Why do we recommend it?
ManageEngine AD360 is a package of tools that help you clean up your user accounts and device permissions in Active Directory and also exploits those account details for security monitoring. The system looks after cloud applications that are dependent on Active Directory and can also manage Azure AD. You can use this package to implement a single sign-on environment.
There are a number of other user account management features in the AD360 package. One of the most visible of these is its self-service portal that allows users to reset their passwords themselves. This feature will greatly reduce the number of calls that your Help Desk has to deal with.
Other account-related systems include a format for implementing multi-factor authentication and security policy enforcement in the form of password complexity rules and password rotation requirements. The system will also identify abandoned accounts, which can then be suspended. All of these user account management features contribute towards data protection standards compliance for PCI DSS, HIPAA, SOX, FISMA, and GLBA.
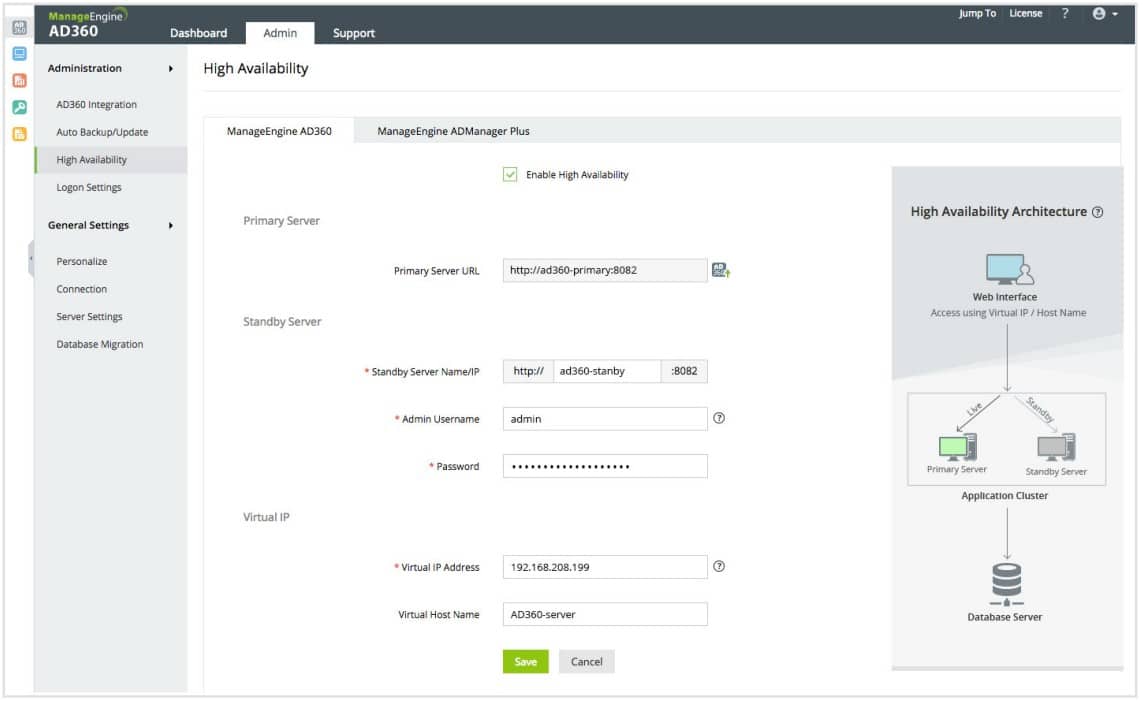
The security features of this package include AD lockdown, which records any changes made to account details so that they can be reversed. The system can also be directed to notify an administrator by email every time a change is made to records within a DC. The package also provides an overall backup service for your AD and Azure AD systems.
The user behavior analytics (UBA) sector of the AD360 provides is major system security feature. This comes from the ADAudit Plus unit. The service records all the activities of each user and establishes a baseline of normal activity. The system will raise an alert if that pattern suddenly changes.
The UBA system is a mechanism for identifying insider threats, account takeovers, and duped phishing victims. It is possible to set up automated responses, which suspend an account in Active Directory if it has been identified as a threat.
Who is it recommended for?
This package has two plan levels that make it accessible for all sizes of businesses. The lower plan, called the Standard Edition, starts at $595 per year. This is the best deal available for small businesses because there isn’t a Free Edition for this package.
Pros:
- Audits AD Accounts: Scans for abandoned accounts
- Creates a Single Sign-On Environment: This is an option available to administrators not a mandatory part of the package
- Multi-Factor Authentication: 19 different authentication factors
- Anomalous Behavior Detection: Identifies insider threats and account takeovers
- Self-Service Portal: Lets users reset their own passwords
Cons:
- Windows Server Only: No option for Linux and no SaaS version
ManageEngine provides two editions for this package: the Standard edition is aimed at mid-sized companies and the Professional edition is designed for large organizations. There is no free version, so small businesses should look at the Standard edition. You can examine AD360 by accessing a 30-day free trial.
EDITOR'S CHOICE
ManageEngine AD360 is our top pick for an identity access management (IAM) tool because it is a suite of tools that enhance security, streamline administration, and improve user experience. It offers strong features for managing user identities, access controls, and authentication, making it a versatile solution for businesses of all sizes. One of AD360’s important strengths is its integration with Active Directory (AD), allowing organizations to leverage existing infrastructure while adding advanced IAM capabilities. It provides centralized management for user provisioning, role-based access control (RBAC), self-service password resets, and multi-factor authentication (MFA). The ability to automate tasks like user account creation, modification, and deletion simplifies administrative workflows and reduces the risk of human error. AD360 offers strong auditing and reporting capabilities, ensuring compliance with industry standards and regulations like GDPR, HIPAA, and SOX. Its user-friendly interface and customizable workflows make it easy for both administrators and end users to manage their access and security settings. With comprehensive support for both on-premises and cloud environments, AD360 adapts to modern hybrid IT infrastructures. Its scalability, ease of deployment, and cost-effective pricing make it an excellent IAM solution for organizations looking to enhance security while minimizing administrative overhead.
Download: Start a 30-day FREE Trial
Official Site: https://www.manageengine.com/active-directory-360/download.html
OS: Windows Server
2. NordLayer (GET DEMO)
NordLayer is a new product from the company behind NordVPN. This system is an advancement on a typical VPN service because it implements Zero Trust Access (ZTA) by integrating an Identity and Access Management service into the package.
Key Features:
- Cloud Identity and Access Management: This feature enables administrators to enforce security policies, streamline user authentication processes, and ensure secure access to cloud resources.
- Workforce Identity: NordLayer’s workforce identity feature focuses on securing and managing the identities of employees, contractors, and other users within an organization’s network.
- Secure Vendors: It helps to secure interactions with third-party vendors, partners, and suppliers by providing secure access controls and encrypted communication channels.
- Identity Compromise Protection: NordLayer offers identity compromise protection measures to safeguard against identity theft, unauthorized access, and account takeover attacks.
Why do we recommend it?
NordLayer provides an easy way for businesses to implement the new and confusing strategy of ZTA. Users who have had access to a typical commercial VPN in the past will instantly understand how to use the access app and opening a permitted application is as simple as clicking on a name in a menu. The setup for this system is equally easy to implement.
The ZTA system of NordLayer works on the scenario that many employees now work outside the office while others work on-premises. So, the remote worker needs to get secure access into the company network – this is where the remote access VPN comes in.
The second complication of modern office systems is that many commonly used applications are now delivered as SaaS packages. So, remote workers often don’t need access to on-premises systems but could easily just access those cloud services directly from their location.
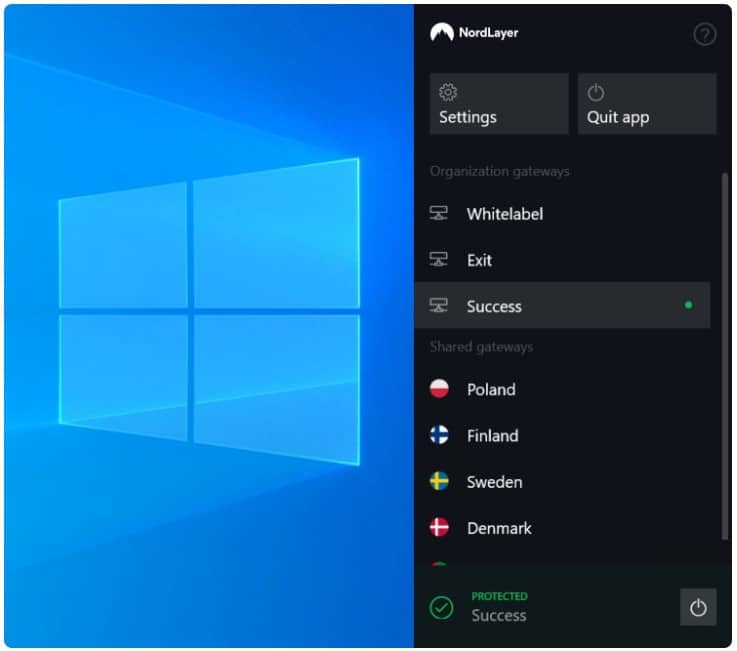
The NordLayer solution treats all workers equally no matter where they are. Each gets an access app on their computer. Which starts up a VPN. The app also lists the applications that the user can access. This is the IAM part of the system. This menu controls access and derives the user’s credentials from the access app in a single sign-on mechanism. So, the user signs into the access app and then doesn’t have to sign in again for each of the permitted services.
The system works as a cloud-based hub. The administrator accesses a console on the NordLayer cloud server and sets up user accounts. The next step is to populate a list of applications and allocate each to a number of users. This gets interpreted into the application menu in each user’s access app.
Who is it recommended for?
The typical NordLayer business customer will be a smaller company that has gotten through the Covid pandemic successfully with users working from home and who have many employees who want to continue to work remotely. It is very common these days for businesses to use SaaS packages. For example, Google Workspace and Microsoft 365 are two very widely used cloud-based packages. The NordLayer system simplifies how an administrator deals with the need to unify access procedures in hybrid on-premises/cloud environments.
Pros:
- Biometric Authentication: It provides a high level of security by relying on unique physical traits like fingerprints or facial recognition to verify users.
- Centralized Billing and Automated User Management: Centralized billing makes financial processes easier, and Automated user management reduces administrative overhead by automating user provisioning, de-provisioning, and access control processes.
- Cloud Firewall (FWaaS): It offers advanced threat detection and prevention capabilities, granular control over network traffic, and simplified management.
- Single Sign-On (SSO): You can access multiple applications and services with a single set of credentials to reduce the risk of password fatigue and security vulnerabilities.
Cons:
- Server Setup Can be More Difficult for End Users: The setup process for servers may require technical expertise and can be challenging for end users who are not familiar with server configuration and management.
NordLayer provides free user apps for Windows, Linux, macOS, Linux, Android, and iOS. There isn’t a free trial for this system but it is possible to get a demo of the NordLayer system.
3. ManageEngine ADManager Plus (FREE TRIAL)
Tested on: Windows Server, AWS
ManageEngine ADManager Plus is a system that can provide a front end for multiple instances of Active Directory. Those AD implementations can cover different services, such as NTFS storage, Microsoft 365, and your network permissions system.
Key Features:
- One-Click Provisioning: Easily create user accounts or provision access to systems and applications with just one click.
- Granular Access Management: Fine-tune and control access permissions at a detailed level. You can specify exactly what resources or data users can access to maintain security.
- Ready-Made Reports: These reports are readily available, making it easy for administrators to analyze data and make informed decisions.
- Secure Delegation: This feature ensures that only authorized individuals can perform specific tasks, maintaining control and reducing the risk of unauthorized access.
Why do we recommend it?
ManageEngine ADManager Plus is a similar tool to the SolarWinds package above. This is an on-premises system that provides a substitute front end for Active Directory management. The system can manage and coordinate multiple DCs, whether they are connected or managed separately.
Unifying all of your AD systems into one console enables you to create consistent user accounts across environments and keep control over who has access to what. This is a particularly useful requirement for businesses that need to prove data privacy standards compliance.
Centralizing the management of Active Directory in your enterprise enables you to ensure that there is consistency in IAM across environments and resources and ADManager Plus includes guides to support the creation of a meaningful access management strategy.
The ManageEngine ADManager Plus system is offered in three editions and the first of these is Free. The Free edition is limited to managing 100 objects and it will give you full user account and device permission coordination across instances, just like the paid versions. You also get more than 200 report templates with this edition.
All versions of ADManager Plus run on Windows Server. Those who want cloud services can get this system in the Marketplace of AWS and also Azure. The two paid editions are Standard and Professional. While the Standard edition gives you all of the instance coordination services you need to centralize all account management functions in one console. The higher plan, which is the Professional edition, includes workflow automation, server management, and GPO control.
ManageEngine ADManager Plus covers Google Workspace accounts as well as Active Directory for system access, Microsoft 365, Microsoft Exchange Server, Skype for Business, and Azure AD. This system can help system administrators unify the records in many different instances in AD across sites and on cloud platforms as well. The sys admin uses the ManageEngine dashboard to create, update, suspend, and delete accounts and permissions and that tool rolls out those changes to all AD instances behind the scenes. This package helps with compliance management for a list of data privacy standards.
Who is it recommended for?
Like the SolarWinds system, ManageEngine ADManager Plus runs on Windows Server. However, ManageEngine also provides the option of running the system on AWS or Azure. So, this would be a good option for businesses that don’t want to run their own on-premises servers.
Pros:
- User Account Creation by Template: ADManager Plus allows for quick and consistent creation of user accounts based on predefined templates, ensuring uniformity and efficiency.
- Streamlines New Hire and Termination Processes: It simplifies the onboarding and offboarding of employees, saving time and reducing errors.
- Generates Report Logs for AD Cleanup: It provides detailed reports to identify and clean up unnecessary or outdated Active Directory entries, enhancing system efficiency and security.
Cons:
- Office 365 Configuration Limited to Individual Users: Some users noticed that managing Office 365 settings may be cumbersome, as configurations are limited to each user rather than being applied universally.
You can assess ManageEngine ADManager Plus with a 30-day free trial.
4. Microsoft Azure Active Directory
Microsoft joined the IDaaS (Identity as a Service) market in 2014 and it eventually led to Azure Active Directory. The fact that it is a Microsoft product makes this the IAM tool perfect for its operating system and the servers that run them; it offers best-in-class integration with Windows Server Active Directory.
Key Features:
- Passwordless and Multiple-Factor Authentication: This includes methods such as biometric authentication (e.g., Windows Hello), security keys, or one-time passcodes sent via SMS or email.
- Unified Admin Center: The unified experience simplifies administrative workflows, enhances visibility and control over identity-related resources, and improves overall efficiency in managing Azure AD environments.
- Privileged Identity Management (PIM): This feature reduces the risk of insider threats, enhances accountability, and strengthens overall security posture by minimizing prolonged exposure to privileged accounts.
- Conditional Access: It allows you to define access policies that dynamically adjust access permissions and security requirements in real time, depending on the context of the sign-in attempt.
Why do we recommend it?
As a product from Microsoft, the Azure Active Directory service is definitive. Not only will it provide AD for your Azure services but it will connect to your on-premises AD instances, so you can unify identity and access management for your hybrid system.
Azure Active Directory is Microsoft’s cloud-based comprehensive IAM cloud solution. It can manage the access rights of thousands of login accounts with ease. It also allows for one authorization credential which allows all members of an organization to access and launch their cloud apps, without any restrictions from the operating system of their choice.
Because it is a Microsoft product, Azure AD smoothly integrates with existing, on-premises AD domain and any applications running in the cloud and remote users that connect via the internet.
With Azure Active Directory users can log in and access resources in:
- External resources: this IAM provides a robust set of capabilities to manage users and help them securely access cloud applications and services like Microsoft Office 365, the Azure portal, and thousands of other SaaS applications as well as numerous other non-Microsoft SaaS applications.
- Internal resources: it also manages access of local applications on a corporate LAN or intranet as well as private cloud apps that have been developed in-house
Azure AD is for:
- IT administrators: they can use it to control access to apps and resources, based on internal business requirements.
- App developers: they can use it as a standards-based approach for adding single sign-on (SSO) authentication to their apps, allowing it to work well with a user’s pre-existing credentials; this IAM tool also provides APIs that can help build personalized UI experiences with existing organizational data.
- Microsoft 365, Office 365, Azure or Dynamics CRM Online subscribers: anyone using one of these applications or SaaS is already using Azure Active Directory by default; this means, they can immediately start managing access to other integrated cloud apps.
You can purchase it as a stand-alone application, but it is also an integral component of Microsoft 365, Office 365, Azure, and Enterprise Mobility + Security.
Microsoft offers Azure Active Directory for free as well as premium with additional features.
Who is it recommended for?
This is the first choice for identity and access management if you run your systems on the Azure platform. If you have both on-premises and Azure systems, you can link your Windows Server AD with your Azure AD and manage both either from Azure or from Windows Server.
Pros:
- Application Modernization: Azure Active Directory (AAD) facilitates modern application development, allowing seamless integration with cloud-native and hybrid applications.
- Digital Transformation with AI, ML: AAD has advanced capabilities for identity management because it uses technologies like artificial intelligence (AI) and machine learning (ML) to enhance security and user experiences.
- Big Data and Analytics: Azure Active Directory provides robust authentication and access control mechanisms, enabling organizations to securely manage and analyze large volumes of data across various platforms and applications.
Cons:
- Availability Zones for All Regions: Lack of availability zones in all regions impacts high availability and disaster recovery strategies for organizations operating in certain geographical areas.
5. Oracle Identity Cloud Service
Oracle’s Identity Cloud Service (IDCS) is an IAM that comes as part of Oracle Public Cloud (OPC) – Oracle Cloud, for short – which is its free cloud service catering to businesses’ needs ranging from data storage and networking services to application testing space and much more.
Key Features:
- Identity Governance and Administration (IGA): It allows central management user identities, access privileges, and entitlements across hybrid IT environments.
- Identity Federation and Single Sign-On (SSO): It supports industry-standard protocols such as SAML, OAuth, and OpenID Connect for authentication and SSO experiences for users.
- Adaptive Authentication and Risk-based Access Controls: It involves contextual factors such as user behavior, device characteristics, location, and transaction patterns to calculate risk scores.
- Identity Analytics and Threat Detection: It uses advanced analytics, machine learning algorithms, and behavior-based anomaly detection techniques to identify abnormal access patterns.
Why do we recommend it?
Oracle Identity Cloud Service is an impressive IAM for businesses that use my different platforms. The system provides a unified interface for access rights management on the Oracle Cloud platform and it will also interface to Active Directory on Windows Server, Azure, and AWS plus other cloud systems.
IDCS helps organizations get better, centralized control of users’ access to their local digital assets, PaaS, and SaaS.
The IDCS is a highly scalable IAM service because it is built on micro-services that run their own processes when connecting to assets or while working with data. This makes it an ideal choice for businesses that are always transforming or growing.
When IDCS is combined with Oracle Identity Manager (OIM) – which oversees the lifecycle of identities from start to finish – they form the ultimate IAM solution for any environment – cloud, on-premises, and hybrid.
The need for IDCS becomes apparent when, for example, an organization has Oracle PaaS as well as other custom-built, on-premises applications that need to be provided with SSO functionality. With this IAM they get one that caters to any device: mobile, tablet, laptop, or desktop on any network architecture.
And that’s not all; Microsoft operating systems are everywhere – it is the most used operating system in the world. A business that needs to integrate such a system into Oracle Cloud, or vice versa, can use Microsoft Active Directory (AD) Bridges to, well, build a bridge between AD and ICDS.
This means ICDS synchronizes with AD – and whenever there is a new, updated, or deleted user or group record in AD, the change is updated in the ICDS records.
And it’s not just with AD; this IAM platform offers innovative scalability with a suite of industry-leading platforms, applications, and services – including identity management solutions – like:
- Social media platforms: Facebook, Twitter, Google
- SaaS: AWS, Google Suite, Slack
- Web or native apps: by using SDKs for Android, iOS, JAVA, Python
Finally, IDCS is a joy to work with and it makes the life of administrators easier with features like:
- Customizable UIs: apart from simply sending out notifications and password policy messages, admins can customize the interfaces of sign-in pages and even the IDCS console itself.
- Self-service password, profile management: administrators can create separate self-registration profiles, approval policies, or applications in IDCS.
- Easy syntax and GUIs: human-readable role, access, and rights assignments make it easy to manage accounts and assets.
This IAM service is enabled, for free, and works seamlessly across the whole Oracle Cloud infrastructure.
Who is it recommended for?
Businesses that use Oracle Cloud will need this tool to control access to resources on the platform. If you don’t have an Oracle Cloud account with services there, you probably wouldn’t use this system.
Pros:
- Works Fine with Hybrid Cloud Methodology: You can integrate with hybrid cloud environments, across on-premises and cloud-based applications.
- Stable Solution with Good Technical Support: IDCS offers a stable and reliable identity management solution backed by strong technical support from Oracle to ensure smooth operations and timely assistance for any issues.
- Direct Access to Give Authentication: IDCS provides direct access to authentication mechanisms, enabling efficient and secure authentication processes for users accessing various applications and services.
Cons:
- Migrating/Replicating Issues: Some users noticed it lacks in terms of comparing schema and attributes side-by-side, potentially leading to complexities or inefficiencies in migration tasks.
There is a free version of Oracle Identity Cloud Service for customers that subscribe to Oracle Software-as-a-Service (SaaS), Oracle Platform-as-a-Service (PaaS), and Oracle Cloud Infrastructure only.
6. IBM Security Identity and Access Assurance
IBM Security Identity and Access Assurance is a “silent” IAM that works in-sync with an organization’s processes and operations so users on the network won’t even notice it is running in the background.
Key Features:
- Deep-Risk Assessments: By conducting deep-risk assessments, organizations can proactively identify and mitigate security risks, strengthen their security defenses, and ensure compliance with regulatory requirements.
- Automated Turnkey Solutions: These turnkey solutions include pre-configured templates, workflows, and best practices for common IAM use cases such as user provisioning, access control, and authentication.
- Multi-Cloud Enterprise: This ensures consistent enforcement of security policies, access controls, and governance standards across the entire multi-cloud ecosystem, helping organizations mitigate security risks and maintain compliance in complex cloud environments.
Why do we recommend it?
The IBM Security Identity and Access Assurance system implements Zero Trust Access by managing VPN connections and controlling access to SaaS packages. This is an easy-to-use service that does, however, require quite a bit of work to set up.
This service controls access to multiple platforms, including cloud and on-premises systems. The tool will also manage VPN credentials. The IBM system is good for compliance reporting and threat intelligence because it tracks all activity per user, protects sensitive data stores, and spots anomalous behavior, which could indicate account takeover. Account lifecycle management is taken care of through on-boarding, inactive account detection, and notifications for removal at the point of an employee’s departure.
This is in contrast to other approaches to IAM that put security in the face of the user. With “silent security” identity and access management are done quietly, in the background, without interfering with systems’ performance or a good UX on a network.
A feature that stands out with this IAM is its ability to protect privileged accounts. It allows for the protection and management of privileged accounts in an organization with enterprise-grade password security and privileged access management.
It also discovers, secures, and manages these “super” accounts’ passwords to protect them from abuse and misuse.
For organizations that want to take their security to the next level, this IAM also offers password-less authentication by supporting login methods like using biometrics, Face ID, Touch ID, email, or SMS one-time-passwords, and soft tokens.
The story doesn’t end with logging and monitoring, this IAM goes on to monitor user accounts. It can discreetly verify users’ identities when they log in and as they remain in session. It uses AI and analytics to make smarter, better-informed decisions to modify users’ access, in case there are outliers or accounts with conflicting privileges.
Who is it recommended for?
This system is great for businesses that use cloud services, such as Microsoft 365 instead of hosting applications on their own servers. You aren’t restricted to managing systems on IBM Cloud with this tool because it is offered as a standalone service that will reach out to other platforms.
Pros:
- Progressive Profiling (CIAM): Enables organizations to gather and update customer profile data gradually over time, providing better insights into customer preferences and behavior while improving user experience and personalization.
- Automated Data Privacy Consent: It includes managing user consent for data processing activities to make sure it meets privacy regulations such as GDPR.
- Bridging from On-Premises to Cloud or Hybrid: You can easily connect applications and data from on-premises environments to the cloud or hybrid infrastructure.
- Reverse Proxies: It hides the internal network structure and provides additional layers of defense against malicious attacks.
Cons:
- Can be Slow and Sluggish: Some users find this tool slow, particularly reverse proxies, which may suffer, leading to delays or sluggishness in accessing applications or services.
You can try IBM Cloud Identity for 90-days on a free trial.
7. SolarWinds Access Rights Manager
Tested on: Windows Server
SolarWinds Access Rights Manager checks all of the boxes for a top-drawer IAM tool. This package doesn’t just manage access rights, it also categorizes resource sensitivity, audits resource access, and identifies vulnerable accounts. It is a data loss prevention system and data compliance auditing tool as well as an access rights management system.
Key Features:
- Active Directory Reporting Tool: You can see information about users, groups, computers, and more, which helps you understand how your network is set up and who has access to what.
- Insider Threat Protection: It monitors user activities and behaviors to detect any suspicious or risky actions that could indicate an insider threat.
- Quick Audit Reports: These reports provide ideas about various aspects of your organization’s operations, such as user activity, system changes, and compliance status.
- Automated SharePoint Provisioning: Instead of manually creating each site and assigning permissions, you can define templates or rules that specify how sites should be provisioned.
The main function of the Access Rights Manager is to deliver greater control over user credentials than the standard interface of Active Directory can provide. Although the Access Rights Manager isn’t able to force Active Directory to perform more functions than its interface allows, it is able to extend its capabilities beyond those of AD by examining the relationships between resources and users and examining user account activities.
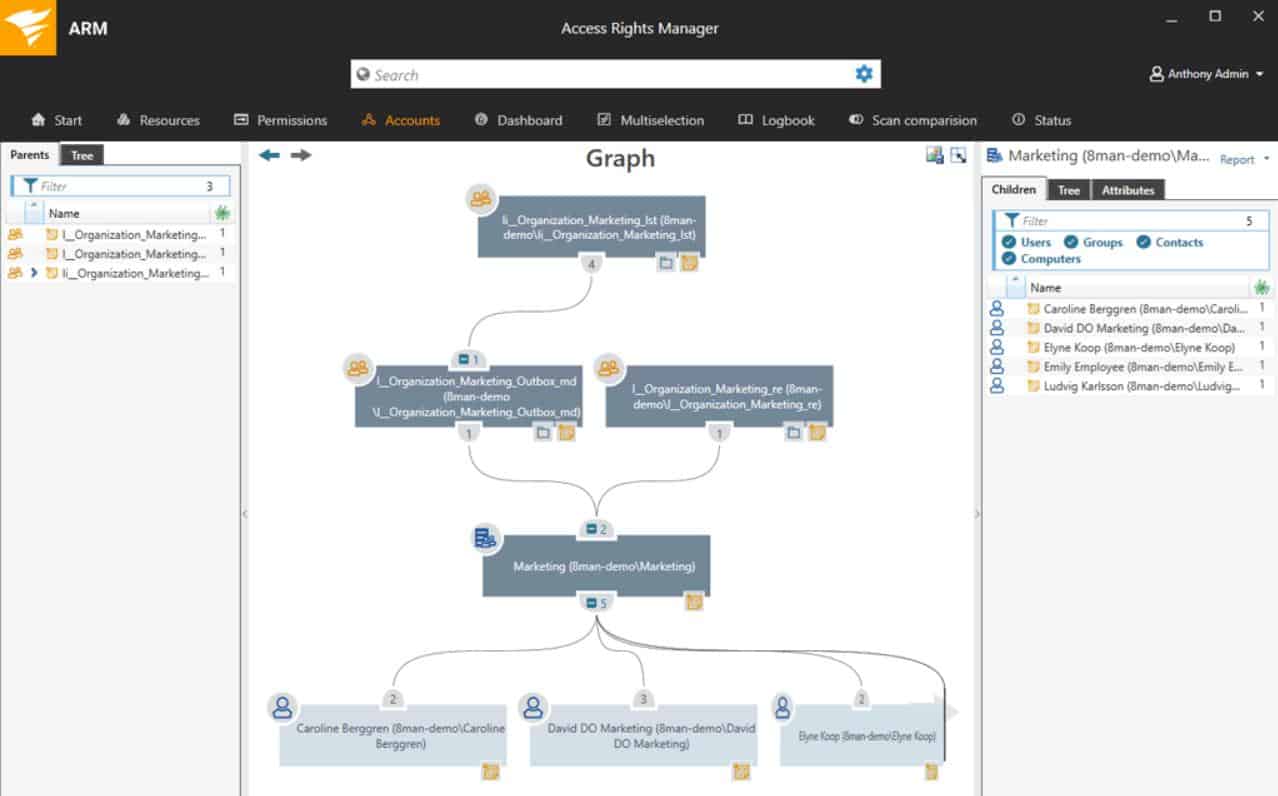
The Access Rights Manager runs on Windows Server and its main focus is on Active Directory, so it manages all of the systems that AD creates access rights for. This includes OneDrive, file servers, Microsoft 365, SharePoint, and Exchange Server. It is also able to manage Azure AD (see next section).
Why do we recommend it?
SolarWinds Access Rights Manager is a good package for you if you struggle to work with the current screens of the native management system of Active Directory. This package provides a new management console for your Active Directory service and then pushes all of the changes that you make in the Access Right Manager through to AD. You can manage multiple instances in one console, perform replication and manage coordination between forests and trees.
SolarWinds Access Rights Manager is suitable for businesses that need to show compliance to data security standards, including:
- GDPR
- HIPAA
- PCI DSS
An analysis module in SolarWinds Access Rights Manager adds cybersecurity threat hunting features. These include insider threat detection through the identification of anomalous account behavior. The service will also identify dormant/abandoned accounts, overlooked, inactive accounts give hackers a better chance of breaking into the system and should be eliminated.
The service logs failed log-in attempts to identify hacker activity and reports on the illogical mapping between account usage and the account holder’s physical location to spot user account that may already have been compromised.
The features in the SolarWinds Access Rights Manager save time and reduce demands on technicians, thus squeezing greater efficiency out of specialist human resources. The tool enables tech management to be centralized and creates a comprehensive enterprise-wide view of all identity-related issues.
Access Rights Manager centralizes Active Directory management and simplifies AD usage. This tool is also an important security system for a business because it includes data loss prevention and insider threat protection.
Who is it recommended for?
This package simplifies access rights management for complicated organizations. Its services would probably be too extensive for the needs of small businesses. This is an on-premises package for Windows Server
Pros:
- File Server Permissions Management: SolarWinds Access Rights Manager offers robust tools for managing file server permissions so you can easily control access to sensitive data and resources.
- File Server Audits and Alerts: You can track changes to your file server permissions and receive alerts in real time when unauthorized access or modifications occur.
Cons:
- Alert Types and Settings: Many users find the tool does not have enough alerting features and lacks in terms of customization options.
SolarWinds offer the Access Rights Manager on a 30-day free trial.
8. SailPoint IdentityIQ
SailPoint’s IdentityIQ is its flagship IAM solution. IdentityIQ is well-regarded for its strong identity governance and provisioning capabilities. It can be used as both a stand-alone, on-premises installation or as an Identity-as-a-Service (IDaaS) solution.
Key Features:
- Automate Provisioning Tasks: Instead of manually setting up accounts and permissions for each user, It can automatically provision access based on predefined rules or policies.
- Understand User Patterns: You can analyze and understand how users interact with your systems and data and identify patterns and anomalies.
- Secure Work from Anywhere: By implementing strong authentication and access controls, IdentityIQ helps organizations protect their sensitive information and maintain security even in remote work environments.
Why do we recommend it?
SailPoint IdentityIQ is a standalone IAM that isn’t tied into a specific platform and it is intended as a cloud-based unifier to tie together the disparate access rights systems of different platforms.
The IDaaS option would be the better choice for organizations that prefer their IAM to be handled by professionals without hiring cyber-security experts of their own.
IdentityIQ is able to interface to a long list of applications to manage access to them and it also has control over data stores. Systems that the tool manages access to include Microsoft Azure, Google Cloud Platform, Amazon Web Services (AWS), SAP, and Salesforce. It is possible to import objects from Active Directory, Azure AD, and Ping Identity.
User onboarding can be set up as an automated workflow, which removes the risk of administrators overlooking important steps or keeping new employees off the system through the pressure of work. That onboarding process creation is guided by a wizard.
IdentityIQ is a particularly good choice for businesses that work in sectors that have very strong scrutiny over sensitive data management. For example, it is suitable for use in the health care sector and it can interface with medical industry, such as Cerner Device Connectivity and Epic systems. The IAM can protect access to devices and patient data, even during the movement and exchange of data between applications, securing electronic health records (EHR).
Compliance enforcement and reporting is tailored towards the specific requirements of a standard that you specify in the settings of the IAM. Choices include CCPA, FISMA, GDPR, HIPAA, and SOX.
You can add on another SailPoint package, called Predictive Identity to improve the performance of the IdentityIQ’s access control services through the use of artificial intelligence.
Who is it recommended for?
This is a good choice for companies that operate both on-site applications and SaaS packages. The tool is able to manage compliance for CCPA, FISMA, GDPR, HIPAA, and SOX.
Pros:
- Life Cycle Management: It ensures that all user identities, whether permanent or temporary, are properly managed, reducing security risks and administrative overhead.
- Secures Critical Applications: It easily controls access to critical applications and resources to improve security posture with organizational policies and regulatory requirements.
- Customized Security: Security teams can customize access controls, share information securely, and delegate authority to improve governance and agility in responding to changing security needs.
Cons:
- Automation Issue: In a hybrid model where application automation is not fully rolled out, it leads to duplicate accounts, hence increasing the risk of security breaches and data inconsistencies.
Although SailPoint offers no free version of IdentityIQ, they do have a link where interested clients can ask for a demo.
9. Ping Identity
With Ping Identity we have another market leader in the IAM domain. Its solution is an ideal choice for organizations looking to enhance the security of their cloud-based assets without compromising on its customers’ UI. The tool can also be used to control access to on-premises and hybrid systems.
Key Features:
- Flow Templates for Best-in-Class IAM: Ping Identity offers pre-designed templates for Identity and Access Management (IAM) processes. These templates are proven to be effective and help organizations set up IAM workflows quickly and efficiently.
- Drag & Drop Integrations: This feature allows users to integrate Ping Identity with other applications and systems easily. Instead of writing complex code, you can simply drag and drop components to create seamless connections between different systems.
- Optimize with A/B Testing: By comparing different configurations or approaches, you can identify the most effective methods for managing identities and access.
- Go Fast with Implementation Accelerators: These accelerators include pre-built configurations, guides, and support services that help organizations deploy Ping Identity solutions quickly and efficiently.
Why do we recommend it?
Ping Identity is a similar package to IBM Security Identity and Access Assurance. It can provide a unified console for a number of different access rights managers, enabling single sign-on and it also provides connection security through a companion application.
Ping Identity can be used to authenticate any type of device – mobile, tablet, laptop, or desktop. The tool can integrate with other IAM systems, including Active Directory, Azure AD, CA Technologies, Oracle, and IBM.
Onboarding can span multiple networks, even integrating the user accounts of associated businesses, while enabling separate administration. This could be a useful tool for managed service providers to create user management for client companies.
Companion security tools from Ping Identity include PingAccess for API security, PingDirectory to store user profile information, PingOne to seamlessly integrate applications, and PingDataGovernance for data access management.
The best thing about Ping Identity is that it can be used to manage millions of identities. This is probably why it is one of the most-used IAM systems in the banking and finance worlds.
Who is it recommended for?
If you are looking for a cloud-based IAM service that will connect together different SaaS packages into a single sign-on service, this is a good choice. However, the great power of this system is that it enables you to implement a Zerto Trust Access architecture.
Pros:
- Based on Open Standards: Ping Identity offers flexibility as it adheres to open standards, allowing users to integrate it seamlessly with other technologies as needed.
- Continuous Innovation: The best part is that this tool gets updated on a regular basis to meet the evolving needs of its customers.
- Outstanding Partnership: Ping Identity is praised for its exceptional customer service and support, demonstrating a commitment to its customers’ success from the initial stages through ongoing support.
Cons:
- Limited Customization Options: Some users have found Ping Identity’s solution to be restrictive in terms of customization, mainly due to its proprietary aspects and little support for custom workflows and hooks.