Many system monitors rely on event logs as an information source. You can also benefit from this data and there are many free and paid system management tools that will run off your event log store. SIEM tools, for example, require event log storage in order to function.
However, if you just want to collect and store event logs, there is no need to pay for all of the functionality included in comprehensive security tools or system monitoring software.
All you need to start exploiting event log information is an event log server that can store event log messages in a meaningful file and directory structure.
Here is our list of the nine best remote event log management software:
- SolarWinds Security Event Manager EDITOR’S CHOICE Log-based SIEM tool that has strong log file management features. The event log management services in this tool make it a good option for those requiring record storage for data standards compliance. Download a 30-day free trial.
- ManageEngine EventLog Analyzer (FREE TRIAL) An on-premises log management system that provides audit trails for data protection standards compliance. Runs on Windows Server and Linux. Start a 30-day free trial.
- ManageEngine Log360 (FREE TRIAL) A SIEM package that includes a log collection and management service with automated and manual data analysis tools. Runs on Windows Server. Start a 30-day free trial.
- Papertrail (FREE TRIAL) A cloud-based system that includes analysis features and file archiving.
- Loggly (FREE TRIAL) A log analyzer that can be used to consolidate event log messages from several sites.
- Paessler PRTG Log Monitor (FREE TRIAL) An all-in-one network, server, and applications monitor that can collect event log messages from any site.
- Datadog Log Collection & Management A SaaS log manager that can receive and file event log messages and works well in combination with the Datadog Ingest for archiving.
- Logstash A free data gathering tool that forms part of the Elastic Stack (ELK).
- Sematext Logs A hosted implementation of ELK with a highly customized interpretation of Kibana. It can be subscribed to just for log management.
Event log management
Log files are also important for data security compliance standards. You need to capture and store all log messages, including event logs, in order to prove compliance. Not only do you need to store those messages, but you need to be able to make them available for searches by a compliance auditor at a moment’s notice.
Event log management involves more than just capturing and filing event log messages. You also need to be able to retain those messages for long periods – the exact retention period depends on the data security standard that you are implementing.
A standard commercial Windows-based system generates a lot of event messages each day. Storing these messages results in a large volume of data. So, you also need to be able to archive older files, while making it possible to bring them back to current storage on demand. The event log manager you choose should include searching and viewing feature and also be able to rotate logs so each file is of a manageable size.
The event log manager should have a meaningful strategy on log file storage structures and file naming conventions to make the Event logs from a particular part of the system on a specific day easy to locate.
The Best Remote Event Log Management Software
Our methodology for selecting event log management software
We reviewed the market for remote event log management systems and analyzed tools based on the following criteria:
- Opportunity to consolidate event logs from multiple sites
- Connection security for internet-based data transfers
- Logfile management
- Log viewer
- Analysis features
- A free trial or a demo service for a no-cost assessment period
- Good value for money, represented by an efficient, time-saving log management tool that is reasonably priced
With these selection criteria in mind, we have identified competent event log collectors that can centralize the management of log files
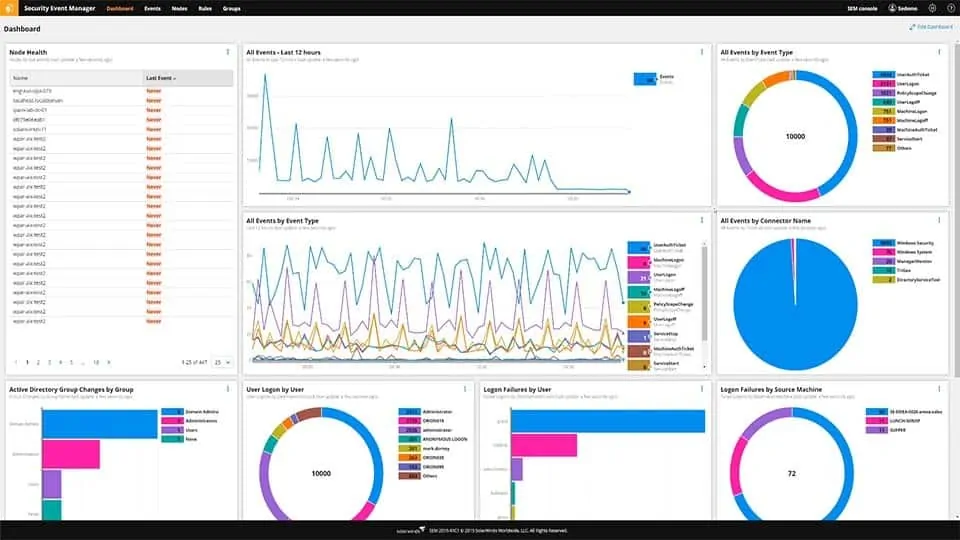
1. SolarWinds Security Event Manager (FREE TRIAL)
SolarWinds offers a number of tools that manage event logs. Of these, the Security Event Manager is the best option. However, as with all free versions, that solution has limitations. The main reason why any business would need to step up from the Event Log Collector to the Security Event Manager is that the log collector lacks an archiving feature.
Key Features:
- Unified Log Management: Centralizes collection of Windows and Syslog messages for streamlined analysis.
- Broad Compatibility: Seamlessly integrates with various applications for comprehensive monitoring.
- Log Centralization: Aggregates logs efficiently, simplifying data management.
- Advanced SIEM: Offers sophisticated security information and event management capabilities.
- Detailed Log Analysis: Facilitates manual examination of logs for in-depth insights.
Why do we recommend it?
SolarWinds Security Event Manager is a SIEM and it is also a log server. This system can collect Windows Events and also Syslog messages from operating systems and applications. No matter what format messages have when they arrive at the log server, they are converted to a common format for searching and storage.
One of the main reasons any business has to store event log records is in order to comply with data security standards. This requires those event log messages to be stored for a very long time – the mandatory retention period differs from standard to standard.
The Security Event Manager isn’t just limited to collecting log messages from Windows environments. It is also able to collect Syslog messages and firewall log data. The log message server gathers messages through a series of “connectors”. Each connector specializes in a specific log messaging standard, so if you only want to gather Event messages, you would just activate that connector.
All collected messages are filed in an accessible folder structure with parallel validity checks performed on each message as it arrives. Log files are protected from tampering through file integrity monitoring.
As well as log file management and archiving, the Security Event Manager includes a log record viewer. This includes sorting and searching features, which are necessary utilities that your business will have to provide to compliance auditors. This feature and pre-written reports support compliance to HIPAA, PCI DSS, SOX, ISO, NCUA, FISMA, FERPA, GDPR, GLBA, NERC CIP, GPG13, and DISA STIG.
Who is it recommended for?
This tool is able to collect messages from remote sites and cloud platforms as well as from the LAN to which its host is connected. The software for the Security Event Manager runs on Windows Server and it can accept messages from other operating systems if you set it as your software’s log destination.
Pros:
- Comprehensive Integration: Caters to enterprises with extensive support for various log sources.
- Ease of Use: Filters logs without requiring complex query knowledge, enhancing user accessibility.
- Rapid Deployment: Features numerous templates for quick start-up and minimal customization.
- Network Anomaly Detection: Historical tools identify unusual activity, aiding in security management.
Cons:
- Professional Learning Curve: Geared towards experts, necessitating a period of learning for full proficiency.
The SolarWinds Security Event Manager installs on Windows Server. Although it is on-premises software it is not limited to operating on the local network. It is able to receive event messages from remote sites. You can access the Security Event Manager on a 30-day free trial.
EDITOR'S CHOICE
SolarWinds Security Event Manager is our top pick for remote event log management because it includes archiving, a log file viewer, and pre-written reports that all help prove data security standards compliance. Message validation and log file integrity monitoring add extra security features to this log management system that will delight any compliance auditor.
Start 30-day Free Trial: solarwinds.com/security-event-manager
OS: Windows 10 and later, Windows Server 2012 and later, Cloud-based: Hypervisor, AWS and MS Azure
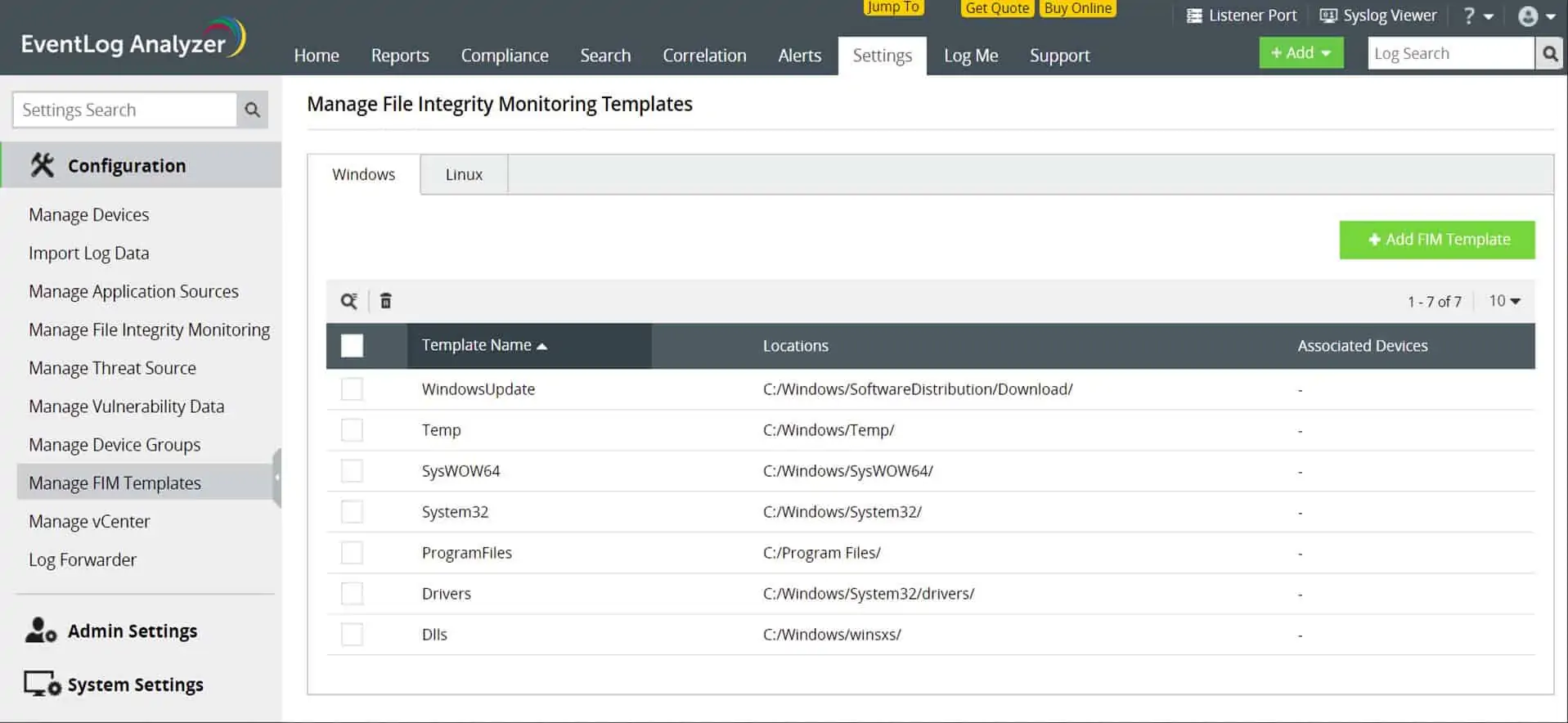
2. ManageEngine EventLog Analyzer (FREE TRIAL)
ManageEngine EventLog Analyzer is a log management system that provides data collectors, a log server, a consolidator, and a filing system. The package is able to merge records written in different formats, which include Windows Events and Syslog. Arriving messages are displayed in the console of EventLog Analyzer and log records can also be read back into the data viewer of the dashboard from files.
Key Features:
- Log Consolidation: Centralizes and merges different log formats for simplified management.
- Insightful Analysis: Offers statistical tools for in-depth log examination and understanding.
- Comprehensive Analyzer: Equipped with tools for detailed log data analysis, enhancing security insights.
Why do we recommend it?
ManageEngine EventLog Analyzer is a close competitor to the SolarWinds tool. It is able to collect Windows Events and Syslog messages from around the network and from cloud platforms. The service is able to accept logs sent from software packages and it will convert all logs into a standard format for searching and storing.
The data viewer in the package includes analytical features, such as search, group, and sort. This supports the manual analysis of data. The package also includes automated analysis in the form of statistical data, such as message arrival rates per type and source. The package includes templates that provide prewritten threat detection rules.
The identification of a problem or a threat triggers alerts. These can be forwarded as emails, SMS messages, or posts to PagerDuty or Slack. This enables the support team to get on with other tasks, leaving the EventLogAnalyzer to monitor standard activity.
There are also templates in the package that produce compliance reports from the collected log data.
Who is it recommended for?
Two editions of this system make it suitable for a mid-size business with a single LAN and for a large company with a WAN. There is also a Free edition that is limited to collecting logs from five sources. The software installs on Windows Server or Linux and it is also available as a SaaS package.
Pros:
- Compliance Assistance: Facilitates meeting regulatory standards with predefined reporting templates.
- Secure Audit Trails: Maintains an accurate and secure log of all network activities for auditing purposes.
- Effective Log Management: Ensures efficient log collection, storage, and analysis for enhanced operational integrity.
- Real-Time Monitoring: Displays log messages live for immediate insight into network health and security.
- Historical Trend Analysis: Utilizes historical data to identify patterns and potential security threats.
Cons:
- No Cloud Solution: Lacks a cloud-based version, limiting flexibility in deployment options.
ManageEngine EventLog Analyzer installs on Windows Server and Linux. It isn’t limited to collecting logs from its host, so if you run the package on Windows Server, you can also collect logs from Linux systems across the network. You can get a 30-day free trial of the EventLog Analyzer.
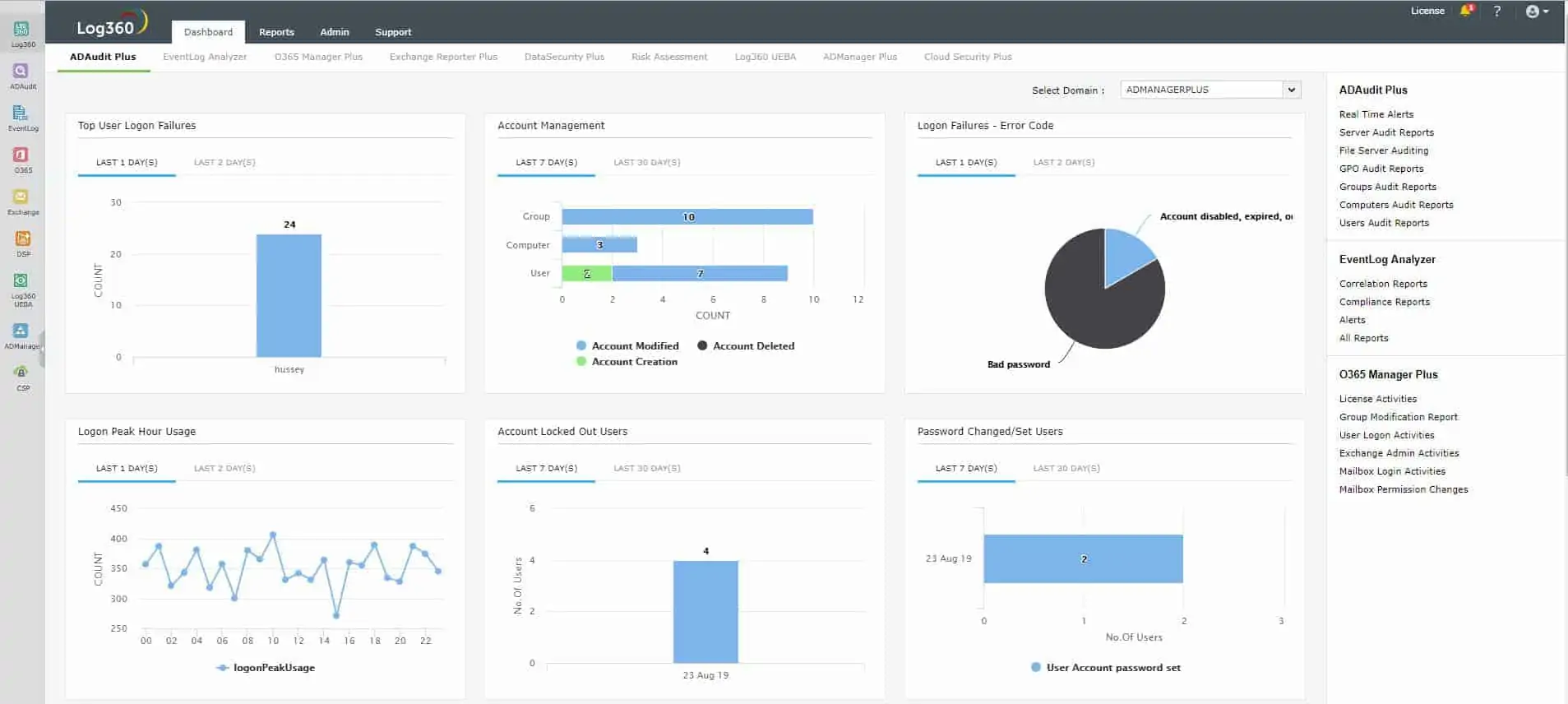
3. ManageEngine Log360 (FREE TRIAL)
ManageEngine Log360 is a security information and event management (SIEM) package that focuses on detecting intrusion on a network and its endpoints. The tool performs this task by gathering and consolidating log messages from around the network. So, as well as a security tool, this package provides a log management system.
Key Features:
- Unified Log Management: Centralized log collection and analysis for comprehensive network surveillance.
- Advanced Analytics: Utilizes statistical methods to dissect data, enhancing threat identification.
- Proactive Threat Hunting: Employs sophisticated mechanisms to detect and alert on potential security breaches.
Why do we recommend it?
ManageEngine Log360 is a super bundle of five ManageEngine modules that are also available individually. These are ADAudit Plus, EventLog Analyzer, M365 Manager Plus, Exchange Reporter Plus, and Cloud Security Plus. The inclusion of EventLog Analyzer gives the package log management capabilities.
The Log360 system is very similar to ManageEngine’s EventLog Analyzer (above) except that it also takes live network activity data as an input. The log collector can interact with applications to extract activity data as well as picking up the standard Windows Events and Syslog messages that circulate around your network.
The package includes prewritten searches that automatically sift through arriving data. It is also possible to create your own threat detection rules. Searches are enhanced by a threat intelligence feed, which enables the threat detection system to focus on indicators of current hacker attack campaigns.
Remediation automation is implemented by forwarding notifications through service desk tools, such as ManageEngine ServiceDesk Plus, Jira, and Kayoko. This lets your ticket management system’s routing rules deliver threat notifications through to the relevant specialist technician.
Who is it recommended for?
This is a very large package and so, is commensurately expensive. Not all businesses will need all of the features in the package. For example, if you don’t use Microsoft 365 or Exchange Server, you would be better off just getting the EventLog Analyzer by itself.
Pros:
- Comprehensive Security Suite: Combines multiple ManageEngine tools for a robust security and log management solution.
- Customizable Threat Detection: Offers flexibility in crafting threat detection rules, bolstered by a threat intelligence feed.
- Seamless Service Desk Integration: Automates alert forwarding to service desk tools, streamlining the remediation process.
- Rich Data Insight: Extracts and analyzes performance data from applications, aiding in informed decision-making.
Cons:
- Limited Platform Compatibility: Excludes support for Linux environments, restricting its applicability.
ManageEngine Log360 will run on Windows Server. However, it can also collect logs from Linux computers across the network. You can examine the Log360 system with a 30-day free trial.
4. Papertrail (FREE TRIAL)
Papertrail is a SaaS log manager, so, as a cloud-based system, it can gather event log messages from all of your sites. The service is a log aggregator, which means that it standardizes and centralizes all log messages wherever they came from and in whatever format. It is able to store Syslog messages as well as event log messages and can put them both into a common format.
Key Features:
- Cloud-Based Agility: Offers a scalable, cloud-hosted log management solution.
- Log Harmonization: Standardizes diverse log formats for unified analysis.
- Secure Log Storage: Provides log archiving capabilities within a cloud infrastructure.
Why do we recommend it?
Papertrail is a log server with a data viewer and it is hosted in the cloud. Plans include storage capacity and so you would consolidate all the incoming logs and save them on the same platform. The system’s data viewer includes analytical tools, such as search, sort, and group.
Once log messages have been standardized and filed, they can easily be searched and sorted through the Papertrail search facility.
Papertrail operates both a live store and an archive facility. Archives can be brought back for searching at any time, which is great for pleasing compliance auditors. The length of time that log files are current or retained in archives depends on the plan you choose.
Papertrail is available in six plans with data processing capacities ranging from 1 GB to 25 GB per month. Log files are held live for one or two weeks and archives are held for one year. It is also possible to ask for a customized service that adjusts these features.
Who is it recommended for?
There is a Free edition, which acts as a trial version for all of the plans because it allows a throughput of 16 GB in the first month but then drops to 50 MB per month after that. Fortunately, the lowest plan is not too expensive and it includes a throughput of 1 GB of data per month.
Pros:
- Scalable Infrastructure: Eliminates the need for physical infrastructure investment, facilitating easy scaling.
- Enhanced Data Security: Ensures data is encrypted both during transmission and at rest for added security.
- Automated Backups: Integrates backup and archiving seamlessly into the service, simplifying compliance.
- Comprehensive Detection: Leverages both signature-based and behavioral anomaly detection for thorough monitoring.
- Accessible Trial: Includes a free version to test the service before committing to a paid plan.
Cons:
- Learning Curve: Requires time investment to fully leverage all available features and options.
There is a free trial version of Papertrail, which makes data searchable for 48 hours and retains archives for seven days. This has a throughput of 16 GB for the first month, then 50 MB per month thereafter. Learn more about what you get with the free trial.
5. Loggly (FREE TRIAL)
Loggly is a cloud-based service that is able to gather log records from any site, including event log messages. The service is charged for by subscription and there is even a free service.
Key Features:
- Cloud Flexibility: Enables log collection from diverse environments including cloud and mobile.
- Broad Compatibility: Supports logs from various systems and programming languages.
- Free Access: Offers a no-cost version for basic log management needs.
Why do we recommend it?
Loggly, like Papertrail, is a SolarWinds product and the two systems are very similar. This system can receive logs from Windows, Linux, cloud servers, and Android devices. The tool is also able to collect logs from application programming languages, including Python, PHP, and Java. It will collect messages from ISS and Apache Web servers.
The Loggly system consolidates log file messages so they are converted into a common format before being written to a file. The user is able to view all log messages as they arrive and then those records are available for sorting, searching, and viewing in the Loggly dashboard. The retention period for analysis depends on the plan.
The free version of Loggly is called Lite. It will process 20 MB of data per day and retains records for seven days. The Standard version handles up to 1 GB of data per day and has a 15-day retention period. The Pro version is adjustable and will process between 1 GB and 100 GB per day. The retention period can be set between 15 and 30 days. The Enterprise plan is a customized service, so processing and retention limits are set by negotiation.
If you are looking for a remote event log manager for data standards compliance, you would need to go for at least the Pro version. This is because the lower versions don’t include any archiving systems. With the Pro version, you can store your archives in your own Amazon S3 account.
Who is it recommended for?
This system has a more generous Free edition than that offered by Papertrail because it will process 200 MB of data per day. All plans have throughput capabilities set at a daily rate instead of Papertrail’s monthly rate. So, you get a lot more capacity with this system but its rates per month are a lot higher.
Pros:
- Versatile Cloud Service: Facilitates scaling without the need for additional on-site hardware.
- Simplified Setup: Designed for quick deployment and ease of use.
- Comprehensive Log Coverage: Captures logs from a wide range of sources, including cloud platforms.
- Immediate Data Insights: Allows for real-time log analysis and monitoring.
- Generous Free Tier: Provides a robust free version with daily data processing allowance.
Cons:
- Limited Trial Period: A more extended trial period would be beneficial for thorough evaluation.
Both the Standard and Pro plans are available for a 14-day free trial.
6. Paessler PRTG Log Monitoring (FREE TRIAL)
Paessler PRTG is a collection of monitoring utilities. Each of them is called a “sensor”. One of the sensors in the package is called the Syslog Receiver Log Sensor. This tool collects event log messages and files them. The service can store messages and access them for up to 365 days.
Key Features:
- Multi-Site Collection: Gathers logs from various platforms and locations.
- Real-Time Statistics: Tracks log arrival rates for immediate insights.
- Complimentary Plan: Includes a free option for basic monitoring needs.
Why do we recommend it?
Paessler PRTG Log Monitoring is implemented as a WMI Event Log Sensor and a Syslog Receiver Sensor. While you can collect and store Syslog messages, the WMI sensor only records statistics about the throughput of Windows Events. A direct Windows Event sensor was deprecated due to enhanced security procedures in the Windows Events mechanism.
It is possible to watch Syslog messages as they arrive. Records can be loaded into a viewer in the PRTG dashboard for searching and sorting. This facility is ideal for those who need to provide access to records to a compliance auditor. The system doesn’t include an archive mechanism.
A WMI Event Log Sensor calculates statistics about Windows Event generation, but it doesn’t collect Windows Event messages. It is possible to set a threshold of throughput that acts as a warning level, triggering an alert.
Who is it recommended for?
Since the deprecation of the Event Log sensor, you can only monitor event message generation rather than collect them. However, as a workaround, you could channel your Windows Evernts through a forwarder that will convert them into Syslog messages, then the PRTG system will be able to receive them.
Pros:
- Customizable Monitoring: Offers adaptable sensors for tailored monitoring solutions.
- Generous Free Offering: Supports comprehensive monitoring with an allowance of up to 100 sensors.
- Flexible Deployment: Available in both on-premises and cloud configurations.
- Holistic Monitoring: Ideal for businesses seeking a wide-angle view of their IT ecosystem.
Cons:
- Steep Learning Curve: The platform’s depth and breadth may require significant time to master.
Paessler PRTG is able to include cloud servers and remote sites in its monitoring system. This makes it ideal for centralizing all event log records for a multi-site business. Paessler PRTG is charged according to the number of sensors that are activated. The system is free for up to 100 sensors. You can get a 30-day free trial of PRTG with no limit on active sensors.
7. Datadog Log Collection & Management
Datadog is a cloud-based system monitoring service that is marketed in a series of modules. The service includes two products that are excellent choices for remote event log management. These are Ingest, which collects the log messages and files them, and Retain or Rehydrate, which manages the archives. The Ingest system includes a “live tail” feature, which displays all log messages in the console as they arrive.
Key Features:
- Comprehensive Collection: Centralized log collection across multiple platforms and formats.
- Live Monitoring: Features a “live tail” for real-time log viewing.
- Archiving Capability: Offers modules for efficient log storage and retrieval.
- Application Insight: Specializes in capturing detailed application log data.
Why do we recommend it?
Datadog Log Collection and Management is implemented in two modules. The first of these is called Ingest, which is the traditional log server with a data viewer. This system will collect Windows Events and Sylog messages from operating systems and from software packages. The second service is called Retain or Rehydrate, which manages archiving.
As a cloud-based system, the Datadog Ingest service can collect log messages from anywhere, not just the site of your IT department. It can consolidate records from all sites into a common file or separate messages for each location – it all depends on the way you set the data collection system up. The service isn’t limited to collecting event log messages because it can also collect Syslog messages and proprietary log messages from a long list of vendor equipment and software.
The Ingest system doesn’t store records – you connect it to your own data store, which can be on-premises or in the cloud. The Retain or Rehydrate service does include storage with a retention period of up to 60 days. This length of time isn’t long enough for data security standards requirements, so you will still need to arrange a backup storage server for archives.
Who is it recommended for?
The Datadog system is resident in the cloud and it provides you with storage options. Essentially, the Retain or Rehydrate is a repository service, which you can use alongside the Ingest package. However, it is also possible to point the Ingest system to save your log files to a different platform.
Pros:
- Versatile Logging: Enables real-time monitoring and archival of logs for comprehensive analysis.
- Global Reach: Collects data across all locations, offering a unified view of IT infrastructure.
- Scalable Solution: Adapts to business growth with flexible storage and pricing options.
Cons:
- Limited Trial Period: A more extended evaluation period is desired for thorough testing.
The Log Rehydration service manages access to archive logs, which is necessary for compliance audits. Both Ingest and Retain or Rehydrate are available for 14-day free trials.
8. Logstash
Logstash is part of Elastic Stack, which is also known as ELK. The L in ELK stands for Logstash, the E stands for Elasticsearch, and the K stands for Kibaba. These three tools can be used together or individually, While Logstash is a log file server, Elasticsearch provides record-searching utilities and Kibana is a data viewer and frontend for the whole stack.
Key Features:
- Open Source: Available for free, facilitating cost-effective log management.
- Cloud Integration: Offers a premium cloud service for enhanced log handling.
- Format Flexibility: Harmonizes logs from diverse sources into a standardized format.
Why do we recommend it?
Logstash is the lesser-known log processing partner of the world-famous Elasticsearch. The design behind these modules of the Elastic Stack is that Logstach prepares log messages while Elasticsearch forms applications that mine that data. However, you can use Logstash by itself if you want and just have it for receiving and storing log messages.
The purpose of Logstash is to be a data receiver. You have to set WMI to forward all event log records to your Logstash implementation. So, it is possible to forward event log messages from several sites to one central Logstash receiver. This connection is facilitated by an EventLog plugin for Logstash.
All three tools in ELK are free and open source. Kibana is particularly widely used because it can interface for many different data analysis engines. It is probable that you would use Kibana and Elasticsearch to provide access to your stored event log files.
Logstash has capabilities to manage many different types of data so you could end up using it for other record collections and not just event logs.
Logstash is able to split existing files and you can set it up to rotate log files by date or message source. It will even manage a meaningful directory structure to make files easier to manage.
Who is it recommended for?
Logstash is free to use if you download it individually. You can download each of the ELK elements individually for free and then use them as a suite on your own server. However, the suite is also available in a hosted version, for which there is a charge.
Pros:
- Intuitive Interface: Features a user-friendly dashboard for easy navigation and visualization.
- Elastic Stack Integration: Part of a powerful trio, enhancing log analysis capabilities.
- Cloud Compatibility: Efficiently processes logs from major cloud platforms.
- Advanced Search: Utilizes Elasticsearch for sophisticated data filtering.
Cons:
- Plugin Dependency: Requires additional setup for handling various data types.
- Community Support: Lacks direct, paid support, relying on community for troubleshooting.
9. Sematext Logs
Sematext offers a hosted version of ELK. You get Logstash, Elsticstack, and Kibana in this package and it’s a great combo for collecting and managing event log messages from anywhere. It might seem a bit strange that people would pay Sematext for access to ELK, which is otherwise free. However, not all organizations have the skills onsite to install and manage technical software, So, Sematext is a bundle of server, software, and expertise that a non-technical organization would gladly pay for.
Key Features:
- Managed ELK Stack: Offers a hassle-free, hosted ELK solution for comprehensive log management.
- Cloud Convenience: Enables centralized log consolidation and analysis from any location.
- Format Versatility: Harmonizes diverse log data into a unified format for easier analysis.
Why do we recommend it?
Sematext Logs is a third-party system that hosts ELK and that includes Logstash, which is explained above. The Sematext platform provides other packages, such as Synthetic Monitoring for websites and Infrastructure Monitoring, which are formed by pre-written Elasticsearch queries. So, you have the option of building your own applications on top of Sematext Logs or buying an off-the-shelf solution.
Sematext has customized Kibana beyond recognition to create its own dashboard for customers to access data. Arriving event log messages are shown on the screen and pre-written Elasticsearch queries are shown as buttons and controls in the Sematext dashboard. This service is primarily geared towards security monitoring but the system collects and stores log messages as its primary activity.
Who is it recommended for?
Sematext Logs has a free edition, called Basic, which will be of interest to small businesses. Two higher plans cater to mid-sized and large organizations. You can adjust the throughput allowance and the retention period. However, be aware that increasing these factors will increase the price.
Pros:
- Flexible Data Queries: Leverages Elasticsearch for adaptable and powerful data interrogation.
- Broad Log Support: Capable of handling a wide array of log types, including SNMP data.
- Automated Alerts: Facilitates proactive monitoring with threshold-based alerting.
- Accessible Trial: Includes a no-cost version suitable for initial evaluations and small-scale deployments.
Cons:
- No Local Deployment: Lacks an option for on-premises installation, limiting flexibility for some users.
- Dependent on Customized Dashboard: Utilizes a heavily modified Kibana interface for data visualization, which may have a learning curve.
Sematext Logs is a subscription service, available in three plan levels: Basic, Standard, and Pro. The Basic service is free forever but it is limited to processing 500 MB of data per day. Its retention period is seven days. The standard and Pro services have adjustable data throughput and retention periods. The Standard service offers retention for 7 and 15 days and daily throughput volumes of 1, 5, or 10 GB. The Pro plan can go up to 150 GB of data per day and a retention period of up to a year. Both the Standard and Pro plans are available for a 14-day free trial.
Choosing Remote Event Log Software
Most of the software that manages event logs have extra capabilities. In fact, it is difficult to find a tool that just manages event logs. The main market for event log data lies in SIEM systems. They will manage event log messages solely to provide the security inference engine with source data.
In many software packages, log file management is not an end product. You may have to pay for those clever security operations that you might not want or need if you are just looking for a way to manage event log files.
The “remote” part of your requirements should not be difficult to fulfill. Most event log servers operate over a network and any tool that can communicate over a network can connect to other sites across the internet.