There are many points of vulnerability on a network and a lot of different approaches to system security. Ultimately, the endpoints that serve users directly are key to the success of the enterprise and must be protected. Symantec Endpoint Protection focuses on keeping these user devices safe.
Symantec Endpoint Protection was the second-largest seller in the endpoint security market in 2024, only five percent behind Trend Micro, according to Datanyze.
The success of this security software stems from the scale of the Symantec corporation and its heavy investment in development and marketing.
Symantec antivirus & anti-malware market strategy
The strategy of the IT security market has shifted dramatically over the past few years. Traditional anti-virus and anti-malware products have become outdated, thanks to new attack vectors created by the hackers of the world. Simply checking processes on a computer against a database of known viruses no longer provides sufficient protection.
Symantec was one of the early leaders in the antivirus industry and has struggled to keep ahead of cybersecurity issues. Firewall products for the residential market have become less lucrative since the expansion of the use of home Wi-Fi routers, which integrate NAT firewalls. The inclusion of the free Windows Defender in its operating system by Microsoft has removed public interest in paying for antivirus systems. Symantec needed to find new security markets before all of its profitability vanished.
Symantec History
Symantec Corporation has been in business since 1982. The company has had to completely revise its product family at several points in its history and each time has successfully avoided getting trapped into dying markets and dead-end hardware commitments.
Symantec spotted the potential of PCs in 1984 and ditched its range of mainframe software, completely shifting its market niche over from database products to report generating systems. Up until 1990, the company diversified its product base, producing utilities for spreadsheets, a memory card for PCs and a compression program. All of these products were dumped once the company acquired Peter Norton Software in 1990.
Symantec had already got into antivirus by the time it acquired the Norton family of products. Its protection system was the leading antivirus system for Macs. Peter Norton Software also had a diversified product list, but its antivirus system was the only one to carry forward.
Symantec developed the Norton brand for residential security products and its own name for business security systems. In 2014, the company started an AI project to move the company away from the traditional antivirus model towards AI-driven intrusion detection methods.
Symantec Endpoint Protection
Symantec launched its Endpoint Protection product in 2007. Already realizing that straightforward antivirus systems were no longer treated with respect in the emerging field of cybersecurity, the company needed to beef up its credentials with more complex systems for business security.
Antivirus was still at the core of Symantec Endpoint Protection, but the package included other legacy products in an attempt to shore up weaknesses in the antivirus approach.
This was a short-term “shock and awe” approach to dazzle potential customers with a bundle of products that outweighed the packages offered by competitors. This bought the company time to re-code the entire antivirus product, which was reviewed as being sluggish, unwieldy, and taking up too much disk space. The stripped-down code of Endpoint Security took up a fifth of the disk space of its predecessor, Symantec Corporate Edition 10.0.
Symantec Endpoint Security was more of a marketing triumph than a technological advancement. However, reading the market is Symantec’s greatest strength and it is the ability of the company’s board to spot trends and their willingness to unsentimentally bin products for new approaches that made the business a market leader.
The board spotted the rise in managed services and produced a managed version of Symantec Endpoint Protection in 2009. It marketed an edition targeted at small businesses in 2010. In 2011, it worked in the growing business trends of Cloud services and produced a virtualization-friendly Endpoint Protection service. The MSP service and the cloud-based signature database evolved into an automated Software-as-a-Service version of Symantec Endpoint Protection in 2016.
The introduction of AI
Despite almost annual overhauls of Symantec Endpoint Protection, the system was little more than an antivirus package. At its core, the product still used the old service model of a central research lab that detected new attacks and identified processing signatures. Those signatures were then rolled out to the onsite signature databases on client computers that provided source material to the constantly running virus detection system on each protected device.
Traditional antivirus methods require a central pool of experts. The distribution of threat database updates over the internet introduces a potential security weakness. The delay between hackers inventing a new virus, and the experts in the lab spotting it, means that antivirus users are always vulnerable. This is particularly the case since the hacker community has reorganized into fully managed organizations with product pipelines of their own.
AI for real-time protection
Essentially, Symantec Endpoint Protection was running on outdated technology and relying on the company’s marketing department to put a shine on it. That is, until version 14, which introduced AI.
Industry chatter had been pointing towards the need for new approaches to cybersecurity since the beginning of 2010. Research in universities in the USA, the UK, Germany, and Russia started to filter out into the wider world through research papers and cybersecurity conference presentations and Symantec jumped on the field as both a way forward or as a minimum, a nice marketing edge.
The release of Symantec Endpoint Protection 14 in November 2016 was an early pay-off for the company’s AI R&D effort, which began in 2014. It saved the product from being steamrolled into oblivion by the innovative new contenders in the cybersecurity market, such as Darktrace, Sophos, and Fortinet.
While the new dogs in the fight were leaner and attractive, Symantec had a well-established brand and a very large marketing budget.
Symantec didn’t complete its AI platform, called Targeted Attack Analytics, until 2018, but the taster of this machine-learning tactic that was built into Symantec Endpoint Protection 14 generated plenty of press attention and kept the company at the head of the market.
Symantec Endpoint Protection methodology – the game-changer
Symantec Endpoint Protection 14 is a game-changer in the business’s cybersecurity strategy.
The tool integrates new approaches to endpoint protection. The traditional model of a research lab sending out threat database updates has evolved into a hybrid on-premises/cloud configuration. The information flow has become a two-way channel.
Each installation is a research center. The machine learning element of the software detects threats, examines its previous findings, identifies new viruses, and isolates them. It then uploads its findings to the central system on the cloud. This new threat discovery is then disseminated to all other Symantec Endpoint Protection installations throughout the world. There are currently 175 million of them.
This architecture is almost a Peer-to-Peer (P2P) model applied to research, which is a very practical and efficient use of client and provider resources. The big difference between this communication architecture and P2P is that the central server is a mediator, which means that it is still following the traditional client-server model.
Symantec as part of Broadcom
In 2020, Broadcom announced its acquisition of Symantec’s Enterprise Security business, which included Symantec Endpoint Protection (SEP), a widely used security product for protecting endpoints from threats. The purchase, valued at approximately $10.7 billion, marked a significant shift in the cybersecurity landscape, as Broadcom, primarily known for its semiconductor and infrastructure software businesses, entered the security sector in a major way.
Broadcom’s decision to acquire Symantec’s enterprise division was part of a broader strategy to expand its software portfolio, particularly in high-demand sectors like cybersecurity. Since the acquisition, there have been some notable changes to Symantec Endpoint Protection (SEP).
Broadcom has focused on maintaining the core functionality of SEP while integrating it into its broader software offerings. Symantec Endpoint Protection continues to provide advanced features like real-time threat detection, behavior analysis, and proactive defense against malware, ransomware, and zero-day attacks. Broadcom has emphasized improvements in SEP’s performance, including optimizing its cloud-based management platform, making it easier for IT teams to deploy, configure, and monitor endpoints.
While Broadcom has largely preserved the product’s core features, it has also pushed for deeper integration with its broader security and enterprise solutions, offering improved scalability and management options. Additionally, Broadcom has worked on enhancing SEP’s integration with other security tools to provide more comprehensive protection in complex environments.
It must be noted that some customers have expressed concerns about the future development of Symantec’s consumer products, as the focus post-acquisition has been on the enterprise sector, leading to speculation about changes to customer support and long-term product evolution.
On-premises operating systems activity
The on-premises software for Symantec Endpoint Protection installs on hosts running Windows, macOS, or Linux. It has four main activities:
- Vulnerability identification
- Attack prevention
- Breach detection
- Threat remediation
Each of these strategies might sound like new names for old methods. However, the use of AI in each phase means that operations are executed with different methods to those used in traditional AV systems.
Vulnerability identification
The “pre-attack” duties of the endpoint protection system include identifying potential security weaknesses on an endpoint. Obvious targets here include USB sockets, communication services, communication software, such as browsers, and services on the computer that potentially provide entry points for malware.
Vulnerability assessment aims for attack surface reduction. It is a continuous process that sets up and maintains the utilities of the malware protection systems, such as memory space for sandboxing and quarantine. The security base check detects any new hardware or software vulnerabilities as they are added to the device.
Attack prevention
The attack prevention activities of Symantec Endpoint Protection equate to the traditional work of firewalls. The aim here is to block any new viruses from getting on to the endpoint. In the new methodology, the Symantec software blocks exploits, which are discovered vulnerabilities in software. This is a patch management system as well because exploits are usually closed down by software manufacturers with updates.
The attack prevention software guards all entry points to the computer, including the network card and USB slots.
Breach detection
Breach detection is the main activity of a classic antivirus system. There is an element of firewall work in this category of tasks. The breach detection system looks for coding signatures, patterns of behavior and sequences of program activation in order to spot threats. This is a little more than the classic case of checking against a virus signature database because it examines behavior as well. This is because an intruder can execute trusted software already on the system for malicious purposes.
The breach detection system triggers a response and implements lockdowns, kills malicious processes and quarantines suspicious new software.
Threat remediation
Once the immediate threat has been dealt with, the Symantec Endpoint Protection system triggers processes to permanently block the detected attack. This phase includes recourse to the Symantec Targeted Attack Analytics. TAA is the cloud-based element of the protection system and it is this service that propagates news of an attack and its solution to the other 175 million users of Symantec Endpoint Protection.
The remediation process traces through process launches to identify the origin on the computer of a malicious strategy. It aims to target and destroy any persistence processes that will try to revive any killed malicious actions on the computer. All successful attempts are reported back to TAA so that the community of running instances can destroy the suite of malicious software as well.
There is also a human element involved in the threat remediation phase. The technicians at the lab in Symantec work through reports looking for global cyberthreat trends so that they can better tailor the evolution of the Symantec Endpoint Protection software.
Evidence of Broadcom satisfaction with the current state of Endpoint Protection is evidenced by the company’s lack of action to replace its star product. All versions of the software before release 14 have been deprecated – they are no longer supported. Up until 2016, Symantec produced a new version of the package almost every year, but there has been no new version since and version 14 is now eight years old. Broadcom hasn’t moved forward to a new edition since its takeover of Symantec in 2020 – Symantec Endpoint Protection is currently at release 14.3.
This apparent inactivity could also signify that the company sees no threat from competitors. Although the company is officially number two in the endpoint protection market, the one percent market share between it and the market leader, Trend Micro, is almost insignificant. One news item or a well-targeted web promotion could easily swing that lead.
So, where are the challengers?
Symantec Endpoint Protection’s competitors & alternatives
The key competitive threats to Symantec Endpoint Protection’s market share come from a wide range of rivals:
- ManageEngine Vulnerability Manager Plus (FREE TRIAL) – Provides preventative security checks. Start a 30-day free trial.
- Trend Micro Apex One – Currently the market leader.
- CrowdStrike Falcon – Better at cloud-driven endpoint protection.
- Sophos Intercept X Endpoint – Better at using AI for endpoint protection.
- Cylance Protect – An innovative and lean endpoint protection provider.
- Nessus Vulnerability Scanner et al – A formerly free system with a clutch of free imitators.
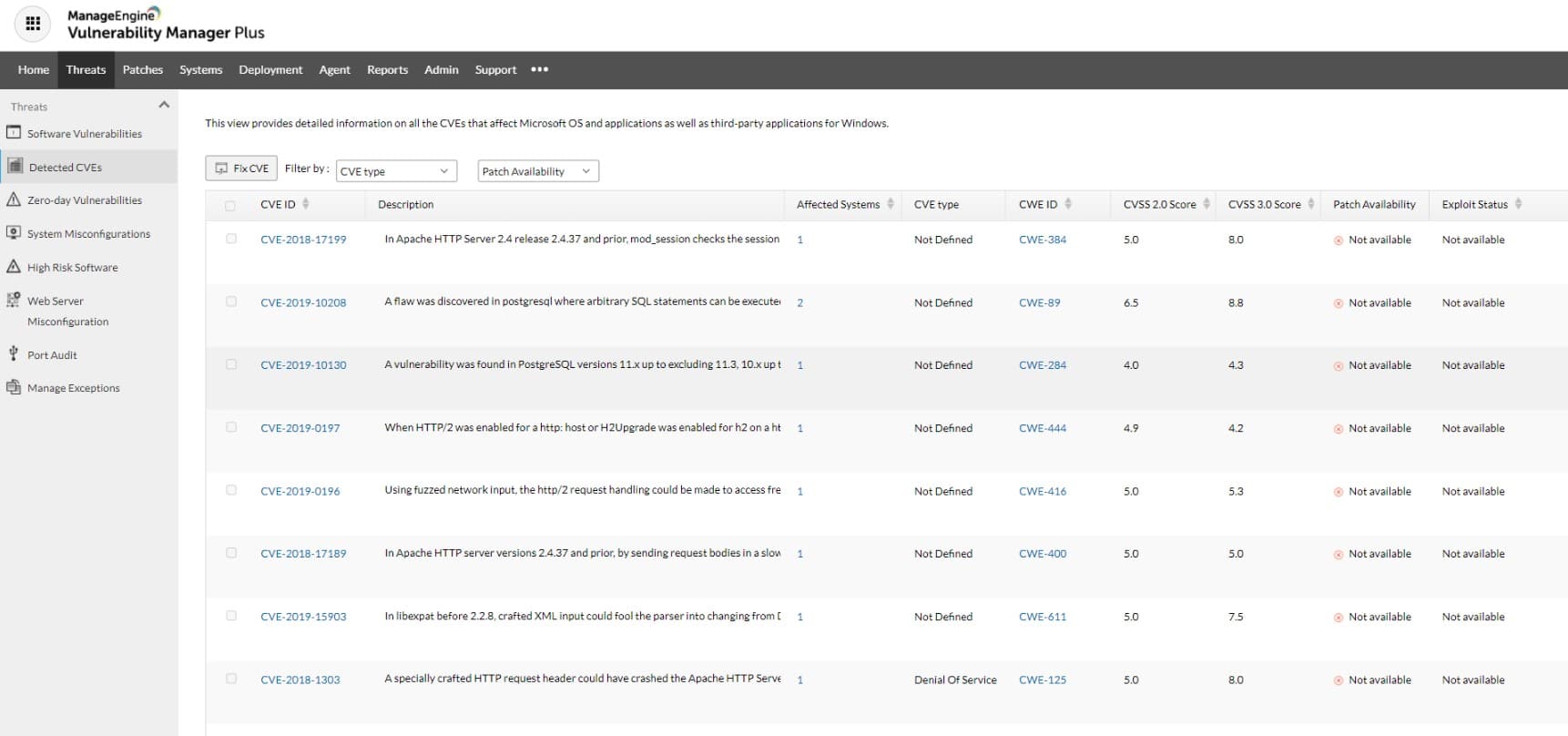
ManageEngine Vulnerability Manager Plus (FREE TRIAL)
Vulnerability Manager Plus takes a different approach to endpoint security. Rather than providing vigilance, this package offers preparedness. The service checks endpoints for weaknesses and will produce a report on system settings that provide exploits for the ingress of malware and intruders. A major weakness on endpoints lies with out-of-date software, so the service has an integrated patch manager that will update operating systems and software packages.
The vulnerability manager also operates on Web servers, which have their own, extra, susceptibilities. In some cases, software packages are in the course of depreciation, and Vulnerability Manager Plus knows about these conditions and warns the system administrator that an alternative needs to be found. You can use the Free edition of Vulnerability Manager Plus to protect up to 25 endpoints. The paid version is available for a 30-day free trial.
Trend Micro Apex One
Trend Micro is currently Symantec’s closest rival. The company has an equal reputation to the Symantec brand and it has an equally well-funded marketing department. Its solution is a very similar blend of traditional AV and AI techniques that helped Symantec to climb the charts.
The biggest threats to Symantec’s crown don’t come from its peers. The new entrants in the market that can outstrip Symantec with innovation and better system delivery will knock Symantec and Trend Micro off the top slots.
CrowdStrike Falcon
CrowdStrike has evolved the Cloud element that Symantec uses solely for threat communication between users. The CrowdStrike Falcon strategy that shifts all processing to the cloud is more suitable for mobile devices and IoT devices – the IT industry’s growth areas. Falcon is available on a free trial.
Sophos Intercept X Endpoint
Sophos has a better AI engine at the heart of its security system than the one developed by Symantec. The Sophos marketing budget is not as large as that of Symantec, but the contender is attracting big investors, making money available.
Cylance Protect
Cylance Protect was designed around AI from the ground up. Cylance’s lack of heritage makes it agile in the marketplace and an attractive brand to startups and innovative SMEs. If the company can breakthrough into the market for large enterprises, Symantec will struggle to maintain its sales targets.
Nessus Vulnerability Scanner
The Nessus Vulnerability Scanner was first developed as an open-source project and it was free. Although this tool is now a proprietary system with a price tag, the availability of its source code enabled a pool of free copycats to enter the endpoint protection market. Those free alternatives undermine the commercial viability of all paid endpoint protection systems.
Innovators such as CrowdStrike Falcon and Cylance Protect have generated a market buzz that makes them attractive right now. Looking at Symantec’s history, there is no doubt that the company will address this competition by overhauling its system again. It will learn from disruptive players and keep ahead of the competition.
Symantec Endpoint Protection FAQs
Is Symantec Endpoint Protection good for home use?
Symantec Endpoint Protection is aimed at businesses. The entire Symantec brand, which is now owned by Broadcom, is aimed at business users. The equivalent system for home use is marketed under the brand Norton, which is a separate company.
Is Symantec Endpoint Protection necessary?
While home computer users can take the risk of not installing endpoint security, businesses can’t be lax about IT asset security. Data leaks can be ruinous and the loss of use of endpoints because of malware infection would require the entire contents of the computer to be wiped and reinstalled.