DAST software, which stands for Dynamic Application Security Testing, probes websites and other internet-facing applications to find security weaknesses. This is a specialized vulnerability scanner that can help you tighten up your protection against cyberattacks.
There are many ways to search out security weaknesses. Vulnerability scanners look at the software that runs on a system and also scans the settings of hardware. These tools use a central registry of discovered weaknesses and look for incidences of them when they scan the sites of their clients. Software checking usually just extends to reading version numbers, which show which updates have been installed. Keeping operating systems patched and software packages updated is one of the major recommendations that cybersecurity experts proffer.
Here is our list of the best DAST tools:
- SOOS EDITOR’S CHOICE This cloud-based application testing system can be used for continuous testing in a CI/CD pipeline and also as a domain scanner for operations technicians. Each subscription gets unlimited seats. Access a 30-day free trial.
- Invicti An impressive DAST system that lets your IT department keep a check on possible vulnerabilities to attack. This tool is particularly desirable for businesses that need to show compliance to HIPAA or PCI DSS. Available for installation on Windows or Windows Server or as a cloud service.
- Acunetix A dashboard of automated DAST that is suitable for use by the IT technicians of medium-sized to large enterprises. Available for Windows, macOS, and Linux.
- Intruder This vulnerability scanner is available in three editions that provide external scanning, internal scanning, continuous testing, and Web application security testing with DAST.
- Appknox A cloud-based vulnerability and penetration testing service that is specially designed to test mobile environments.
- Veracode Dynamic Analysis This is an easy-to-use test automation solution that integrates well into the DevOps cycle. It is a cloud-based service with strong person-to-person involvement with service engineers.
- Detectify EASM Platform A testing tool supported by ethical hackers that lets small business owners run their own DAST exercises. Delivered from the cloud.
- Rapid7 InsightAppSec A cloud-based DAST solution provided by a highly experienced cybersecurity consultancy.
- Checkmarx A cloud-based application testing platform that offers DAST. You can also combine this with the Checkmarx SAST to get a full CI/CD security testing suite
- HCL AppScan DAST, SAST, and IAST solutions for web apps and services plus processes for mobile apps. Available for Windows and Windows Server or as a cloud-based service.
- GitLab Ultimate A suite of CI/CD DevOps support platform that includes a DAST system. Offered as a cloud-based subscription service.
- AppCheck An automated application testing platform delivered from the cloud and performance for development projects.
Dynamic Application Security Testing is a little more involved than vulnerability scanning because it watches the software while it runs. This is an automated penetration testing system because DAST systems don’t just wait for users to run the software, they run it in a test and try out combinations of input actions to see where security weaknesses lie.
The main targets of a DAST system are those protocols that drive the World Wide Web: HTTTP and HTML. These two protocols offer a front door to attackers. However, SAST doesn’t just look for a way in; it also tries several different types of attacks, such as SQL injection.
Implementing DAST
DAST systems are usually used on live applications. They help a business to check their websites and backend services to make sure that new attack vectors haven’t managed to damage the security of their already-operational systems. SAST can also be used during the acceptance testing phase for a new Web page.
DAST looks at a Web application while it is running – it approaches from the outside and tries to get in. The reverse strategy to this is to look at the code and try to work out how it could facilitate an attack. Services that perform that inside analysis are called SAST, which stands for Static Application Security Testing. In this guide, we will look at DAST systems and leave SAST for another day.
When operating a DAST strategy, you need to examine how outsiders would try to break through and damage your Web applications. Therefore, the best location to host the testing software is a remote server. DAST is ideally suited to SaaS (Software as a Service) operations. However, if you prefer to buy software and host it yourself, there are on-premises solutions available, too.
For more details on exactly how DAST operates, see the Comparitech guide, What is DAST? Right now, we are going to jump into recommendations of the best DAST tools.
The best DAST tools
Our methodology for selecting a DAST tool
We reviewed the market for dynamic application security testing systems and analyzed the options based on the following criteria:
- Integration into CI/CD pipelines
- Continuous testing
- Black box unit testing
- Integration testing
- Issue tracker integration
- A free trial or a demo package for a no-cost assessment opportunity
- Value for money, represented by a comprehensive testing system at a fair price
Using this set of criteria, we looked for dynamic application security testing packages that can be used by application development teams and IT operations technicians.
Using this set of criteria, we looked for dynamic application security testing packages that can be used by application development teams and IT operations technicians.
You can read more about each of these options in the following sections.
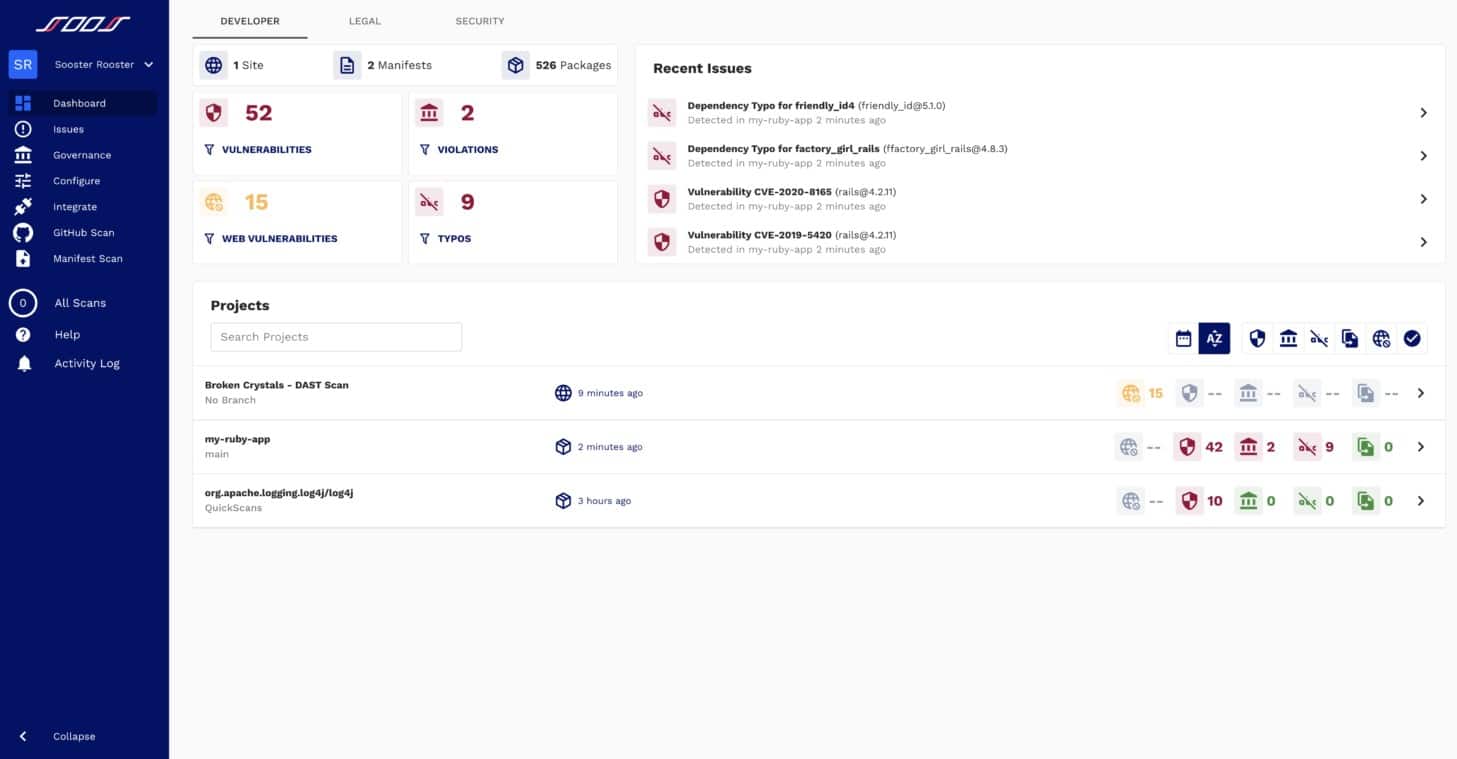
1. SOOS (FREE TRIAL)
SOOS is a dynamic application security testing tool that partners with a software composition analysis system. The package of the DAST and SCA systems provides comprehensive testing facilities for any DevOps environment. The DAST can provide continuous testing in a CI/CD pipeline and it is also available for use by the operations team as a domain scanner.
Key Features:
- Application Security Posture Management Platform: Delivered from the cloud
- Code Security Scanning: Software composition analysis and static application security testing
- Infrastructure Verification: For containers and infrastructure-as-code
- Code Execution: Dynamic application security testing
- Unified Dashboard: Integrates all security features into a single dashboard for easy management and monitoring
Why do we recommend it?
SOOS is a flexible DAST that also provides SCA and can be used by both development and operations teams. Scheduled sweeps or on-demand scanning highlights vulnerabilities in live Web applications and a continuous testing mode allows the system to act as a testing service in a CI/CD pipeline.
The lower SOOS package is just a software composition analyzer. This looks for open-source code and APIs within Web applications and makes sure that they do not have known vulnerabilities. Oftentimes, the developers of any vulnerabilities are aware of the issue and have probably already brought out a new version to shut down the issue. Where this is the case, SOOS will recommend an update to fix security issues.
The DAST part of the upper package provides sandboxing, which occurs in a Docker environment, so you need to make sure that you install Docker before trying to run this tool. The testing software itself operates on the cloud platform of SOOS.
The DAST and SCA services can be plugged into your development management system. The package has integration for a list of development systems, including Azure DevOps, Jenkins, and TeamCity. You can also use it with Bamboo, Bitbucket, Jira, and GitHub Issues for issue tracking.
SOOS continues to be useful when your Web application goes live. Operations technicians get a domain scanner, which they can run on demand or on a schedule to ensure that no new issues arrive with the system.
Who is it recommended for?
This system is suitable for use by businesses that develop and support their own Web applications. Examples of typical users would include companies that provide APIs for other developers to use and SaaS providers. The tool is a SaaS package so its charges are levied on a subscription.
Pros:
- Software Bill of Materials Management: SBOM includes third-party software management
- Three Plan Levels: SCA, DAST, and SBOM
- SCA in All Plans: The DAST and SBOM plans include the SCA package
- Integration with Development Management Tools: Continuous testing in a CI/CD pipeline
- Issue Management: Pushes tickets with fix details directly into Jira and GitHub Issues from the SOOS web dashboard
Cons:
- Limited Free Plan: The Community Edition provides SCA but not DAST
SOOS is a subscription service with four plans. You can get an SCA Community Edition for free and the lowest-paid plan also provides an SCA service. The middle plan provides SCA and DAST – it is available for a 30-day free trial.
EDITOR'S CHOICE
SOOS is our top pick for a DAST tool because it offers comprehensive security coverage that can easily be integrated into modern development workflows. It offers security vulnerability insights to Web application developers. One of the primary reasons SOOS excels is its ability to perform automated, real-time security scanning without disrupting the development process. This allows organizations to continuously monitor for vulnerabilities in their web applications and APIs while maintaining agile development cycles. SOOS automatically identifies a wide range of vulnerabilities, including common threats like SQL injection, cross-site scripting (XSS), and security misconfigurations, providing developers with immediate, actionable feedback. This seamless integration into the CI/CD pipeline makes it easy for teams to incorporate security checks at every stage of development, ensuring vulnerabilities are caught early in the lifecycle. SOOS offers strong coverage, scanning not only web applications but also APIs, which are often a target for cyberattacks. With the growing reliance on APIs in modern software architectures, the ability to test both is crucial for comprehensive security. The tool’s thorough scanning of both front-end and back-end components ensures vulnerabilities are detected regardless of where they reside. SOOS uses automated vulnerability prioritization, helping developers focus on the most critical issues first. Its intuitive interface makes it user-friendly even for teams without deep security expertise, while detailed reports clearly outline vulnerabilities and how to address them.
Download: Get a 30-day FREE Trial
Official Site: https://app.soos.io/register
OS: Cloud-based
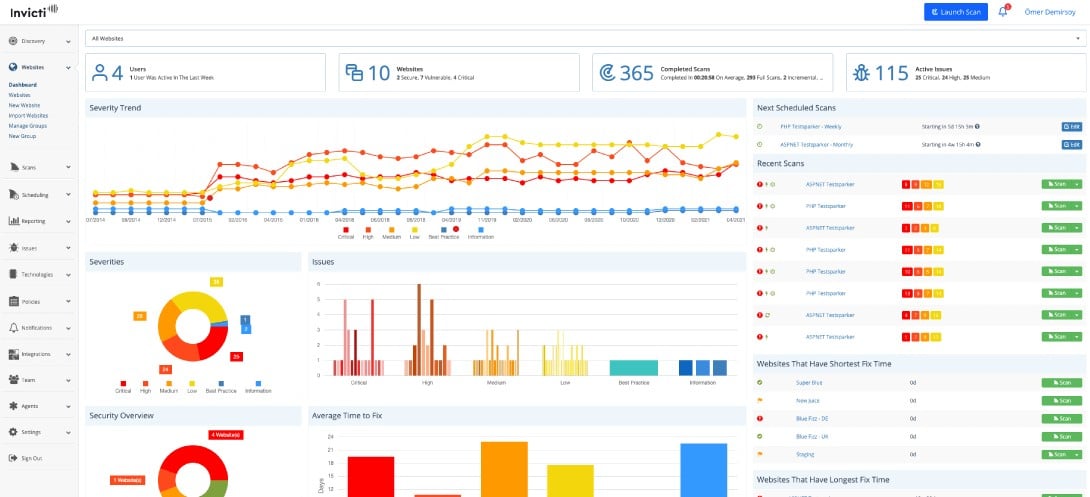
2. Invicti
Invicti – formerly Netsparker – is an interactive application security testing package (IAST), which includes DAST processes. It is presented in plans that make it suitable for use as a vulnerability scanner, as an automated pen testing tool, and as a continuous testing system.
Key Features:
- Web Application Discovery: Can be used to test live applications
- Interactive Application Security Testing: Scans code and runs it for tests
- Development Testing: Set it up as a continuous tester
Why do we recommend it?
Invicti provides a testing tool for development teams and for operations technicians. You can use this system on-demand or on a schedule to check the security of live systems or set it up within your CI/CD pipeline framework as a continuous tester. This is an IAST system, but it implements DAST procedures as well.
The two plan levels of Invicti cater to businesses of different sizes and complexity. The Invicti Pro plan is aimed more at pen testers and operations teams, although it does also include features to support development. This package is aimed at businesses that have up to 100 Web assets to manage and are interested in spotting and remediating vulnerabilities in live systems.
The Invicti Enterprise plan is for larger enterprises that perform a lot of development and management of Web applications. This tool includes a PCI DSS compliance enforcer and it has integrations with more development management tools to provide more choice when setting up a CI/CD pipeline.
Both plans are suitable for DevOps deployment and neither places a limit on the number of scans that can be performed each month with the service. The Enterprise plan provides a more corporate structure with more user account types, a great degree of team management, and integration with productivity and collaboration tools.
Who is it recommended for?
The two plans of Invicti make this system suitable for mid-sized (Pro) and large (Enterprise) Web application developers and managers. Both editions are available on a SaaS platform but subscribers to the Enterprise plan can choose to download the software package and run it on Windows Server.
Pros:
- Integration with Development Management Tools: Can interface with JIRA
- Interacts with Repositories and Bug Trackers: Connects to GitLab and Bugzilla among others
- Compliance Management: Enforces PCI DSS
Cons:
- On Premises for Windows Server: Not a cloud-based system
Although it is officially an IAST tool, Invicti also implements dynamic testing procedures, so it’s fine to consider this on your shortlist of DAST systems. Both systems provide compliance reporting for HIPAA and PCI DSS, however, the higher plan is particularly strong on PCI DSS enforcement. Access the Invicti free demo to get to know the system.
3. Acunetix
Acunetix Vulnerability Scanner is another long-standing and widely used DAST system. The service offers a dashboard of tools that will execute vulnerability scans of websites and web services on demand.
Key Features:
- On Premises System: Available for Windows, macOS, and Linux
- Vulnerability Scanning: For live Web applications and APIs
- Continuous Testing: For applications under development
Why do we recommend it?
Acunetix is advertised as a vulnerability scanner but it is actually an IAST system and provides an optional network vulnerability scanner through the integration of OpenVAS. So, you can use this tool in two ways: ignore the option to use OpenVAS and integrate the DAST into your development framework or implement the system as a scanner.
Although the dashboard tools are very well laid out, making them usable by non-technical operators, the price of this utility probably puts it out of the range of hard-pressed small businesses. This is more a tool that middle-sized and large businesses would use. The package is sold in three editions: Standard, Premium, and Acunetix 360.
Each higher plan has more features with the top edition offering a complete security testing service for DevOps environments. All versions scan for the OWASP Top 10 and are particularly strong at detecting cross-site scripting and SQL injection.
Who is it recommended for?
This system can be used to test your entire system for vulnerabilities, which is a suitable strategy for consumer businesses. The tool can be used by application providers as a DevOps testing system, Development teams working to requirements laid down by commissioning clients can use the tool for security testing of completed work.
Pros:
- Combines IAST and DAST: Both interactive and dynamic application security testing
- Will Integrate into a CI/CD Pipeline: Connects to project management systems. Bug trackers, and repositories
- Prioritizes Vulnerabilities: Creates a task list for fixes
Cons:
- No Price List: Contact the Sales Department for a quote
The software for all Acunetix editions needs to be downloaded and installed on site. It is available for Windows, macOS, and Linux. You can get a demo of the system to assess its suitability for your business.
4. Intruder

Intruder is an automated, dynamic cloud-based vulnerability management solution that seamlessly scans your infrastructure, web applications, and APIs. It delivers actionable, context-driven results, so you can fix the most critical security issues first. With regular vulnerability scans and proactive monitoring for emerging threats, Intruder provides round-the-clock defense, reducing your exposed attack surface.
Key Features:
- Attack Service Manager: External and internal scanning
- Ad-Hoc Scanning: A hosted OpenVAS implementation
- Automated and Scheduled Scanning: A hosted implementation of Tenable
- Web Application and API Scanning: For DevOps teams
- Set Up as a Continuous Tester: For CI/CD pipelines
Why do we recommend it?
The three plans of Intruder can all be enhanced by DAST for Web application and API scanning. Even the lowest plan can have DAST licenses added, so you don’t have to go all the way up to the top plan to get Web application and API security testing.
The Web application and API testing services of Intruder are delivered as add-ons to any package. So, you buy licenses for the number of DAST instances that you need to run, which equates to the total number of Web applications and APIs that you have. It is not unexpected that you should add on extra licenses over time as you develop or adopt new Web applications and APIs.
The Essential edition provides an external attack surface scan and is a great choice if you are starting with vulnerability management or need to meet compliance requirements. The Pro plan involves more comprehensive features, and you can use that to set up as many scheduled scans as you like as well as benefit from automated cloud and Emerging Threat Scans. This plan implements internal network scanning as well as external attack surface scanning. The top plan, Premium, includes the services of a rapid response team in addition to the internal and network scanning offered by the Pro version.
Those two top plans can be set up as continuous testers in a CI/CD pipeline and you can also use them for assurance testing of any third-party APIs that you will be integrating into your own systems. The DAST testers will continue to secure your Web applications once they go live.
All of the elements of the Intruder service can be integrated with third-party tools to promote project management and team effort. These include Slack, Jira, Gitlab, Github, ServiceNow, and Zapier. You can store your functions on AWS, GCP, or Azure.
Who is it recommended for?
You don’t need to be a developer of Web applications to use Intruder because it is available as an external attack surface scanner, which is suitable for any enterprise. However, DevOps teams that create and manage APIs and Web applications will use the DAST add-ons for their system security.
Pros:
- Vulnerability Management: Identifies security weaknesses
- Links to Project Management Services: Integrates with Jira
- Integration with Service Desk Systems: Automation for live system testing
- Integration with Bug Trackers: For use in development projects
- Cloud-Based System: Can be activated just by entering a URL in a website
Cons:
- Not Officially a DAST Tool: Known for code scanning rather than code execution
The Intruder system is hosted in the cloud and you access it through the service’s website. However, if you take the network scanning option, you will need to install an agent on every device that you want protected. You can assess this service with a 14-day free trial.
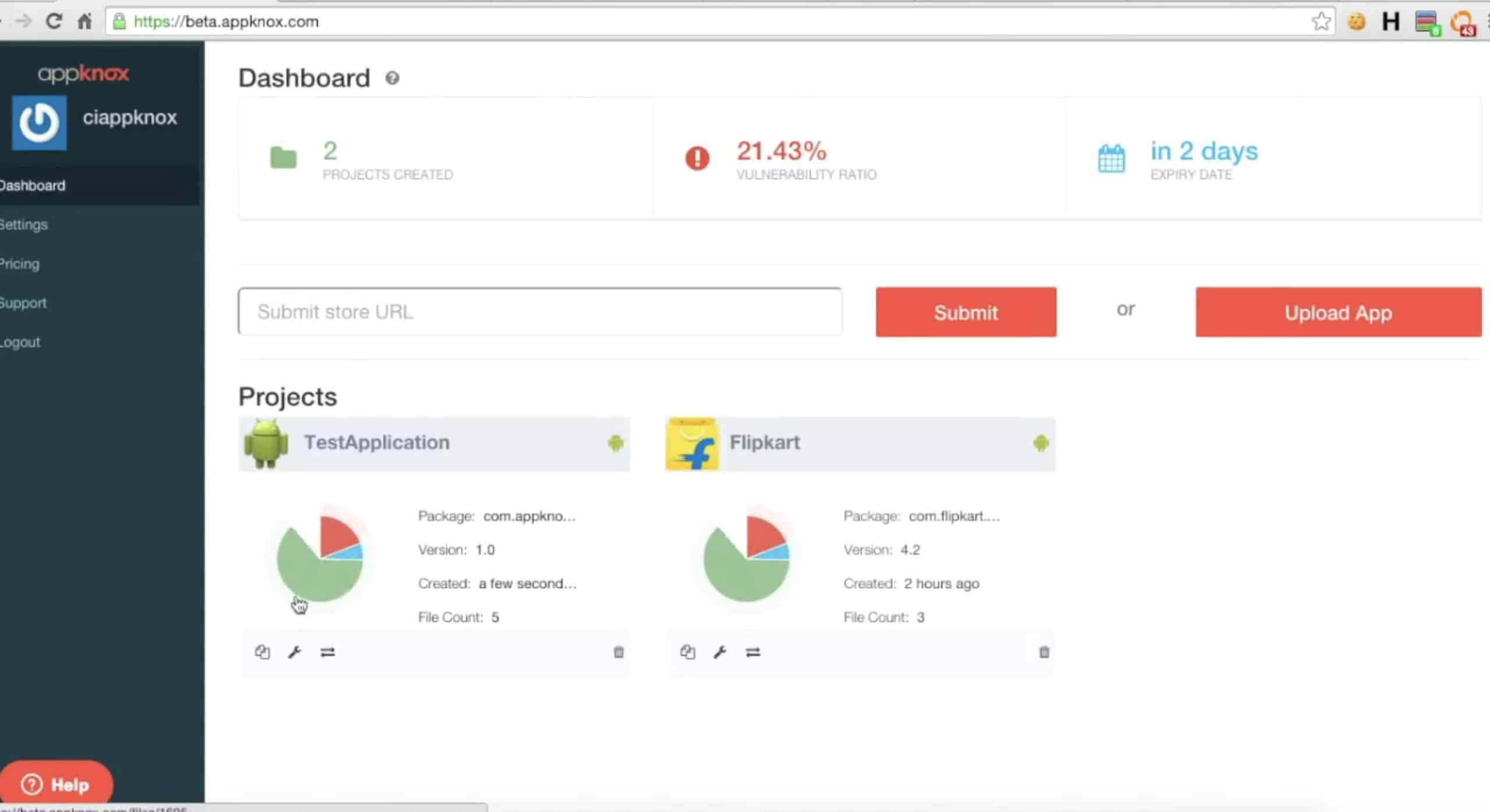
5. Appknox
Appknox is specifically designed to test mobile app environments. It is a cloud-based vulnerability and penetration testing service that is specially designed to test mobile environments. This is a DevOps system that supports the creation, testing, release, and maintenance of mobile apps.
Key Features:
- Mobile Application Security Testing: Identifies and scans all of the microservices behind mobile apps
- SAST and DAST: Both static and dynamic application security testing
- API Testing: Security assessments for those plug-ins that you don’t host or control
Why do we recommend it?
Appknox is a very similar service to the Invicti system and it provides both DAST and SAST strategies for DevOps teams. This system’s organization into plans is obscured by the fact that the company doesn’t publish a price list. So, you might be able to get just the DAST or just the SAST.
The DAST service offered by Appknox is a vulnerability scanner. This is available in three editions, which are all charged for on a subscription per app per month. These plans are called Essential, Professional, and Enterprise. All plans include both static scans (SAST) and dynamic scans (DAST). This is a great combination that is particularly suitable for a CI/CD environment where code can be in constant flux.
Who is it recommended for?
The typical user of Appknox would be a company that provides Web applications to other businesses and delivered them on a subscription basis. That is, a developer that also runs the applications on behalf of clients. Appknox also offers a pen testing consultancy service.
Pros:
- Live Application Scanning: Included in all plans
- Continuous Testing: Scanning for applications under development in the top two plans
- A Cloud Platform: The option to download and self host the system
Cons:
- No Price List: No free trial
The Appknox system is hosted, so there is no need to install any software or maintain a host for the testing system. The company also offers source code reviews by cybersecurity experts, security certifications, and SDK testing as added extras. There is also a penetration testing add-on available.
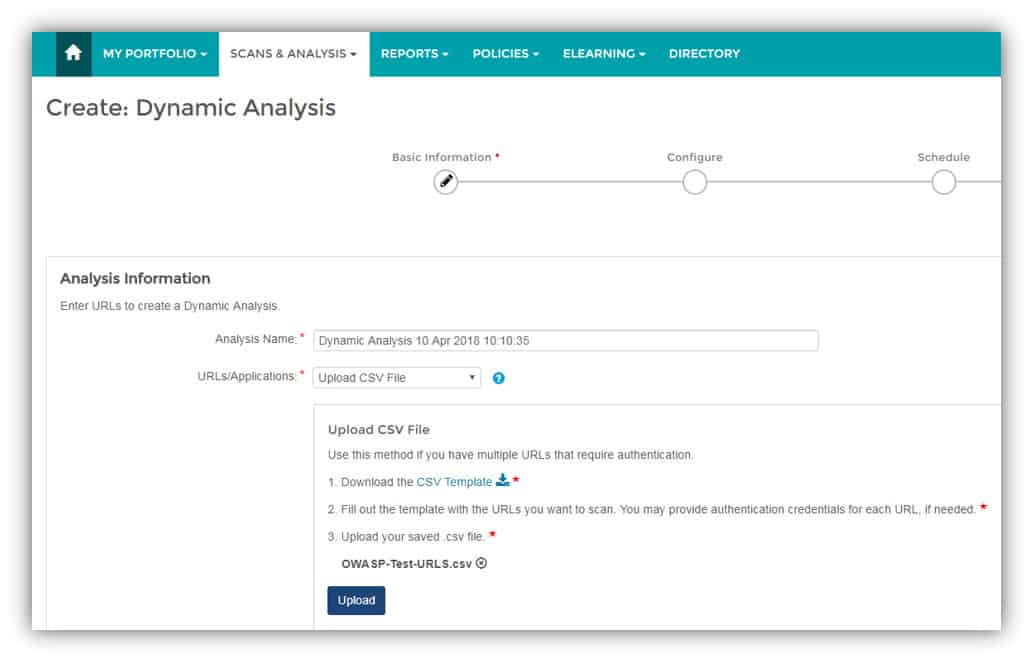
6. Veracode Dynamic Analysis
Veracode Dynamic Analysis is a very easy-to-use DAST service that integrates well into a DevOps environment for web applications and websites. This vulnerability scanner includes a scripting system that lets you set up a test that can get through login screens on your web system.
Key Features:
- Vulnerability Scanning: Assurance for live Web applications and APIs
- Development Testing: Continuous testing
- Based in the Cloud: Fits with cloud-hosted functions and code repositories
Why do we recommend it?
Vercode Dynamic Analysis is a platform of security testing systems that provides DAST, SAST, and SCA modules. The need for each of these systems depends on the type of Web applications you manage. For example, if your code is accessible, SAST and SCA are possible; if not, you need SAST.
In order to start a scan, you just need to enter a URL to test in the console for the DAST service. It is also possible to load up a list of URLs to get a sequenced test that can run without your attendance. It is possible to link a call to the tester into a development workflow, so newly developed code can get tested and rolled out automatically.
Who is it recommended for?
The Veracode system can be used for vulnerability scanning, penetration testing, and for continuous testing in a CI/CD pipeline. The way you deploy the tools by selecting integrations and deciding on whether to run them on-demand or on a schedule dictates how their usage is defined.
Pros:
- SAST and SCA also Available: Static code analysis offered by other Veracode modules
- Explanations of Discovered Weaknesses: Includes guidance on how to fix the problems
- Vulnerability Prioritization: Categorizes weaknesses as high, medium, and low priority
Cons:
- No Price List: No free trial
Veracode Dynamic Analysis is a cloud platform and you can assess it on a demo.
7. Detectify EASM Platform
Detectify is a team of ethical hackers that put together an automated DAST system, first for their own use, and then for release to the wider business community.
Key Features:
- Attack Surface Scanning: Launched from an external location
- Continuous Scanning: A cheaper on-demand option is available for small businesses
- Web Application and API Testing: DAST for development pipelines
Why do we recommend it?
Detectify EASM acts as a consolidator for an army of independent white hat hackers. The company packages vulnerability discoveries into its vulnerability scanner and pays each discoverer a royalty when a specific vulnerability is detected in a subscriber’s system. You pay a fee per asset rather than per identified weakness.
EASM stands for External Attack Surface Management. The platform organizes its scanner into two categories: Application Scanning and Surface Monitoring. The Surface Monitoring scans look for ways into your system and the Application Scanning service scans each of your Web applications for known weaknesses. The platform looks for the OWASP Top 10 and also compiles a list of weaknesses that were identified by the freelance penetration testers who are affiliated with the Detectify scheme.
The tool is flexible and can be suitable for a range of environments. Its ease of use makes this cybersecurity tool a good choice for small businesses. It is a cloud platform, so you don’t need to have a host or IT staff to maintain the software. On the other hand, it is also a sought-after tool by DevOps teams that both create and maintain websites and web services.
Who is it recommended for?
The tool is structured so that it can be integrated into a CI/CD pipeline for continuous testing. It can also be launched on a schedule or on demand to test live applications. The system is intended for use by the producers of subscription Web apps rather than by their consumers.
Pros:
- DNS Testing: Examines supporting services as well as applications
- A Proprietary List of Vulnerabilities: Detectify gathers a list of vulnerabilities from freelance penetration testers around the world
- Asset Discovery: The platform finds all of your Web assets and implements scans on them
Cons:
- Priced in Euros: You can’t pay in dollars or pounds
Detectify is a subscription service, hosted in Sweden and charged for in Euros. You can access a two-week free trial of the system.
8. Rapid7 InsightAppSec
Rapid7 has produces a cybersecurity platform that is made up of a suite of tools. It is a cloud-based system, so the processing power and storage needed by these services are all included in the price. InsightAppSec is the DAST module of this collection.
Key Features:
- Black Box Testing: Dynamic application security testing for Web applications
- Vulnerability Explanations: Details of the discovered weakness
- Attack Replay: Store a DAST test with its negative results to rerun it on the fix
Why do we recommend it?
Rapid7 InsightAppSec is a DAST service from the highly respected Metasploit penetration testing tool and the widely-used Nexpose vulnerability scanner. So, this system comes from a winning stable. The tool is implemented as a continuous tester for development teams. A nice feature is its attack demonstrator to explain the discovered weakness.
The Rapid7 DAST solution checks for the OWASP TOP 10 and more. It looks for more than 95 different vulnerabilities that include cross-site scripting, cross-site request forgery, and SQL injection. The remote location of the system makes it ideal for giving an external view of your web presence. However, it is also able to scan applications that are private within your own system, such as applications that are still under development.
The user interface for this DAST tool is very well presented and the setup process to enroll straightforward. However, this system probably wouldn’t be suitable for small businesses because of its cost. This is a security testing system for businesses that have a lot of web-based applications that need to be kept secure. The standards compliance reporting in Rapid7’s system creates another big attraction for larger companies.
Who is it recommended for?
Although this system can be plugged into a development management framework, it isn’t exclusively intended for development teams – it can also be used by operation teams to test live owned and third-party Web apps. The compliance reporting function is another important feature.
Pros:
- Prioritizes Discovered Weaknesses: Includes guides for fixes
- Development Security Testing: Can be integrated into a CI/CD pipeline
- Compliance Reporting: For HIPAA, PCI DSS, and SOX
Cons:
- Stronger for Testing Operational Applications: Doesn’t provide the integrations with development management tools that are available with the other systems on this list
Rapid7 offers potential customers the opportunity to use the system for free for 30 days.
9. Checkmarx
Checkmarx runs an interactive application security testing (IAST) platform. It is an automated testing system that can be integrated into the CI/CD pipeline and includes DAST and SAST functions. The company offers its DAST and SAST services as standalone modules as well. The IAST system is a cloud-based service that is pricey and is probably only accessible for larger application development businesses.
Key Features:
- A Suite of Testing Tools: Includes DAST, SAST, SCA, and software supply chain security (SSCS)
- Infrastructure Testing: Scans supporting technologies, such as containers and infrastructure-as-code
- Open Source Vulnerabilities: Identifies the participation of open source components that have known security weaknesses
Why do we recommend it?
Checkmarx offers DAST, SAST, and IAST packages but promotes the IAST solution of having the qualities of both DAST and SAST but with faster detection methods. The IAST system searches for the OWASP Top 10 and then also examines logical failures in cohesion that could open up further weaknesses.
The dynamic testing processes of Checkmarx will run new code and check for OWASP Top 10 vulnerabilities. The service then cycles faulty code back through the development workflow or pushes it onto the production path depending on the outcome of the security tests. Vulnerabilities that the system looks for include SQL injection, cross-site scripting, cross-site request forgery, and path traversal. This is a cloud-based system.
Who is it recommended for?
The integrations with development management automation tools make this a great system for development teams. However, the tool can also be used to check on the security of live Web applications, so operations teams could use it, too. The high price of this system makes it inaccessible for all but the largest businesses.
Pros:
- Suitable for Development Testing: Integrates with development tools
- Useful for Operations Teams: Scans live Web applications and APIs
- Hosted on the Cloud: Well suited to testing cloud-hosted applications
Cons:
- No Price List: No free trial
10. HCL AppScan
The DAST service of HCL AppScan assists compliance to HIPAA and PCI DSS and it is available in three versions: AppScan Standard and AppScan Enterprise for installation and AppScan Cloud, which is a SaaS system.
Key Features:
- Provides a Choice of Testing Strategies: SAST, DAST, IAST, and SCA
- Tests Web Applications and API: Features for both development and live application testing
- Can Apply SAST, DAST, and IAST to the Same Application: Provides multiple analysis tests
Why do we recommend it?
HCL AppScan is a matrix of products with DAST, SAST, and IAST options available for on-premises hosting or as a cloud SaaS package. So, the first thing you need to sort out with this platform is exactly which functions you need and where you want to access them.
AppScan Standard gives you access to the DAST system itself. There is also a SAST version of AppScan Standard. The AppScan Enterprise bundle includes DAST and IAST and the AppScan on Cloud system includes DAST, SAST, IAST, plus other services.
AppScan Standard is intended for use by cybersecurity experts rather than system administrators. The IAST services of AppScan Enterprise and AppScan on Cloud can be bundled into the CI/CD pipeline to automate code testing and release.
The service looks for OWASP Top 10 vulnerabilities. After a scan completes, the DAST system lists any problems that it found in order of urgency and also recommends solutions for each vulnerability that it finds. This is a useful tool for busy cybersecurity consultancies that support many websites and applications.
Who is it recommended for?
The flexibility of the HCL AppScan package means that it can be useful for a range of businesses. Developers, API and SaaS providers, and Web application consumers can all find a configuration of this platform that they can use. The system also provides compliance reporting for PCI DSS and HIPAA.
Pros:
- Explanations of Discovered Weaknesses: Provides guides on fixes
- IDE Integration: Catch security errors right when they are written by the coder
- Fault Confirmation: Applying multiple test strategies to each application ensures that a real bug has been discovered and not a categorization error
Cons:
- Price Transparency: Costs not upfront until after signup
AppScan Standard installs on Windows and Windows Server and it is available for a 30-day free trial.
11. GitLab Ultimate
GitLab is a cloud-based support system for DevOps CI/CD pipelines. The package of services is available in three editions: Free, Premium, and Ultimate. There is a long list of features for all versions, with successively higher plans including more utilities. The DAST service of GitLab is only included with the top plans, which is the Ultimate package.
Key Features:
- The Top Edition: This is the most comprehensive plan available from the GitLab platform
- Cloud Hosted: Gives you private space for code storage and analytical metrics
- DAST, SAST, and Container Scanning: Provides multiple testing strategies
Why do we recommend it?
GitLab Ultimate is the top plan for GitLab and it provides all of the bells and whistles of this code management system, including its continuous testing service, which is based on DAST. You also get SAST from this cloud-based code repository service that enables you to utilize a geographically dispersed development team.
The DAST system in GitLab includes API scanning and can be launched on-demand or integrated into a schedule. The system also has a SAST code analysis service, which is also the only vibe in the ultimate package. GitLab is offered on a 30-day free trial.
Who is it recommended for?
There is a Free edition of GitLab, which provides a storage directory on the GitLab server. However, you need the Ultimate edition if you want SAST and DAST services. These functions can be automated and triggered as part of the process of transferring an application’s code into the GitLab repository.
Pros:
- Security Risk Mitigation: Tailor scanning to specific risk models
- Creates a Software Bill of Materials: Discovers and records dependencies between units
- An Open Source Vulnerability Database: GitLab hosts a crowdsourced list of weaknesses
Cons:
- DAST is Only Available in the Top Plan: The Free and Premium editions don’t include DAST
12. AppCheck
AppCheck is a security testing platform that was developed by a pen testing consultancy. This is a flexible system that would be suitable for all types of website management scenarios and could be used directly by system administrators for on-demand security checks.
Key Features:
- DAST System: Provides dynamic application security testing for Web applications and APIs
- Infrastructure and CMS Testing: Assesses supporting technologies
- Single Page Application Security Scanning: SPA is a new technique to test the vulnerability of a Web page
Why do we recommend it?
AppCheck is a cloud-based vulnerability scanner that implements DAST. You can activate the scanning service in a number of ways, making it a tool for use when scanning live apps for security weaknesses or a CI/CD pipeline continuous testing service for newly developed Web apps.
The AppCheck system includes a high degree of testing automation and it can be integrated into DevOps workflows managed by CI/CD project management tools, such as JIRA and Team City. Once you pay for a license, there is no limit to the number of tests you can run and the system is available around the clock. Scans don’t just check the security of websites and services. Tests are performed through a browser, not just HTML scanning and they are capable of spotting zero-day vulnerabilities. They also probe all access points and look for weaknesses in the entire software and hardware infrastructure of your system.
Who is it recommended for?
This tool is very adaptable. It can interface with JIRA to become a development testing tool and it can also be implemented as an acceptance testing package for DevOps teams. It can be used to support managed applications or it can be used by consuming businesses to keep an eye on live systems.
Pros:
- DevOps Tool: Integrates with development management systems, such as JIRA
- On-Demand and Automated Scanning: Set up a schedule, define a trigger, or launch it on demand
- Automated Penetration Testing: Implements attack surface scanning for entire systems in addition to the SAST service
Cons:
- No Price List: You can access a free trial
This is a very flexible utility that is delivered from the Cloud. You can try out the system with a free scan.
DAST tool FAQs
What are the DAST tools?
Dynamic Application Security Testing (DAST) tools preview newly created Web applications before they go live. The testing system runs the packages and examines how they react given certain inputs. This is like a vulnerability scanner because the input attempted in these tests are the type of exploits that hackers are known to try.
What makes a DAST tool effective?
DAST tools are only effective if they are provided with a list of hacks to look for. The tester needs to run the new Web application in an environment that is as close to how the application will operate once live. This involves setting up all of the services that the application depends upon and the other applications that rely upon it.