Insider threat detection is one of a number of recent developments in cybersecurity. The problem of insider threat has become so great that the US government set up the National Insider Threat Task Force (ITTF) in September 2011. The Task Force’s main remit is to establish an insider threat detection and prevention policy for government agencies. You need to ensure that your organization is taking similar steps to prevent insiders from sabotaging your system or stealing sensitive data.
Here is our list of the five best insider threat detection tools:
- ManageEngine Endpoint DLP Plus EDITOR’S CHOICE Protects files that contain sensitive data and triggers a user activity tracker if data access patterns change. Runs on Windows Server. Download a 30-day free trial.
- SolarWinds Security Event Manager On-premises package log manager and a SIEM with threat detection measures that extend to identifying suspicious user account activities. Runs on Windows Server.
- UnderDefense MAXI MDR Provides a Security Operations Center for a company in a managed security service package that includes both intrusion detection and insider threat detection.
- Endpoint Protector by CoSoSys SaaS package that protects endpoints running Windows, macOS, and Linux and it includes a range of threat detection methods. Spot and block intruders, malware, insider threats, and account takeovers with this system.
- Teramind DLP Cloud-based data loss prevention system identifies and protects sensitive data and then searches for intruders and insider threats.
What is an insider threat?
Everyone can understand the concept of a threat to a system. Most cybersecurity tools aim to block hackers and malware from attacking a network or other company resources. An insider is someone who is authorized to use the company’s system.
While outsider attacks can include many software-based systems, such as remote access Trojans, DDoS attacks, ransomware, spyware, and viruses, insider threats are almost exclusively manual processes. An insider might damage the system by deleting data, removing programs, or altering system configurations but the main focus of an insider threat is data theft.
While damage to or removal of system software can be a problem, there are very few account holders in a business who have the ability to perform these actions in a meaningful way. For example, an employee who uninstalls the productivity suite from their own workstation isn’t really causing much damage to the organization. Corporate-wide applications, such as a web server, or database systems, can only be tampered with by a very limited number of people within the IT department.
Small businesses are more vulnerable to sabotage by their limited number of employees and associates because the smaller software packages utilized by these businesses tend to have fewer distinctions between operators and administrators. Still, even in small businesses, the focus of insider threats is on data issues.
What insiders pose a threat?
There are eight types of employees who pose a threat to an organization:
- Disgruntled employee – A person who feels that they have been unfairly treated by the business, passed over for a promotion, denied overtime pay or expenses, or harbors resentment towards a supervisor or section manager.
- Leaver – A person who has been enticed away by a rival business might be induced to take business data away with him to benefit the new employer.
- Fifth columnist – An employee who has a political bias against the company and its activities and seeks to undermine the profitability or viability of the business.
- Manipulated individual – Someone who is put under social or moral pressure to work against the interests of the business.
- Negligent employee – Someone who doesn’t intend to sabotage the business or disclose information but causes damage through a negligent failure to follow best practices and is likely to be indiscrete with data or system access credentials.
- Overspender – A person who needs more money than she earns and is liable to seek to make money by selling company data.
- Former employee – A person who has left the company but whose system access has not been revoked.
- Whistleblower – A person who seeks to gain moral reward by disclosing a company’s trade secrets.
Minimizing insider threats
Before approaching insider threat detection, an organization needs to implement system controls that make data theft or system damage harder to achieve. Minimizing the potential for employee actions is the first phase of insider threat management.
A strategy for reducing the potential for insider threats falls into two categories:
- Identity and access management (IAM)
- Data loss prevention (DLP)
These two topics are explained in depth below.
Identity and access management
Identity management involves the creation of user accounts that can then be applied to resources. User account management is an effective deterrent to insider threats if it is implemented thoroughly.
Identity management tasks include the creations of levels and types of users. This requires the definition of different types of access required by different business roles. The general user population should fall into one category. This category could be split further by department. So, finance department users and HR staff will need access to different software packages, for example.
By defining the requirements of different job titles, the system administrator can arrive at a set of user profiles. Each profile will be defined by the software that user group needs, the hardware resources they will need to access in order to work, and the data stores that group needs to access. Profiles will be further refined by the level of access to data that each need – read-only, or editing rights.
User profiles that include higher permission levels should be assigned to a very limited number of users. Technician profiles should be highly restricted and those technician profiles that enjoy full superuser privileges should be allocated to only a few members of the organization.
Data loss prevention
Data loss prevention measures are more important for a limited type of data. Companies only store data because it is useful. However, some data types are more important than others. If your industry is subject to legal constraints over data disclosure or industry standards, such as PCI-DSS or HIPAA, you need to focus your highest data loss prevention efforts on the types of data specified in the standards that your company is obliged to follow.
Data loss prevention involves locating all stores of sensitive data and placing extra tracking and protection measures in those locations. As all of the data held by the business is important, all data access events need to be tracked.
Insider threat management
Insider threat management is the process of combining identity and access management with data loss prevention.
There is no system that can give you a 100 percent guarantee that you will never suffer an insider threat. Even if your IT system is the tightest possible, you will still face the threat of pen and paper. As well as effective insider threat IT controls, you will also need to implement physical access controls on your premises, staff profiling, and in-person employee monitoring.
You can refine your insider threat management strategy by implementing transaction monitoring.
User and entity behavior analytics
Automated monitoring systems can easily track every event that occurs in the IT system. However, identifying which event is a security threat is a difficult proposition. Fortunately, a field of competence called user and entity behavior analytics (UEBA) helps with that task.
UEBA is an AI tool and is an advanced type of machine learning. A UEBA system records every transaction that occurs, particularly those that involve access to data. Over time, the UEBA system defines a standard of normal behavior. Once the UEBA system has been operating long enough to make a reasonable estimate of standard behavior, it is easier to spot suspicious behavior.
You can’t issue an instruction to a computer to tell it to look out for suspicious activity because it is almost impossible to define what is and what isn’t “suspicious”. UEBA focuses on working out what regular behavior looks like and then raises an alert when anything that deviates from that standard occurs. This tool enables system security specialists to focus on likely insider threats rather than trying to watch every single transaction.
Event logging
As no system is 100 percent foolproof it is a good idea to hope for the best, but plan for the worst. You need to put in place systems that will enable you to investigate insider threats once they have occurred. Even if you put very stringent controls in place, someone might just get around them one day.
Logging everything that happens generates a large amount of data. However, storage is very cheap these days so the cost of keeping all of those log messages is minimal. If records of all events are in storage, they can be searched for indicators of an attack. If you ever discover that an insider is trying to steal data or you find out that a data loss event has just occurred. You need to search through logs to look at all of the past activity of that user because it is unlikely that you just happened to catch her at her first attempt.
If you need to show compliance to a data security standard, event logging is a requirement and not an option.
Triage
Triage involves focusing your efforts on the most likely source of a threat. UEBA and automated activity tracking help you to identify likely malicious user accounts. Once those candidates are identified, you should apply very close scrutiny to their activities. You can’t sack someone on suspicion of malicious activity; you need proof.
Document controls
Documents and slide presentations not only contain data but they are a key method of sharing corporate strategies. Electronic files are easy to copy and send out in emails or take out of the building on a memory stick.
The first layer of protection against data theft through documents is to scan all outgoing emails for attachment and block USB sockets on workstations.
Not all email attachments are data theft attempts – it is an accepted business practice to send out quotes, orders, invoices, proposals, sales pitches, and receipts as attachments. Therefore, outgoing attachment scanning needs to be sophisticated.
The further line of defense for document control lies with fingerprinting. If key documents are leaked, it should be easier to trace the insider responsible if all document access and distribution systems mark each copy with an identifier.
Data outflow controls
Under data loss prevention systems, sensitive data is located and tracked with tighter controls. Those controls should pay particular attention to any attempt to send out those data types attached to an email or copy them onto a memory stick. This applies triage to data movement tracking.
Activity monitoring
All of the above insider threat management strategies rely on activity tracking. Analytical tools need to be applied to event logging systems to join together a series of actions that could contribute towards a data loss event. This is because data theft typically involves several steps. Each of those steps in isolation could seem innocuous. It is only when those events are linked together that the theft becomes apparent.
All of the elements listed above contribute to an effective activity monitoring strategy. Controls on user accounts implemented through an identity and access management strategy limit the accounts that need to be thoroughly monitored. Data loss prevention techniques that identify the stores of sensitive data let activity monitors know which parts of the system to focus on.
So, if a user account with high permission rights accesses a store of sensitive data, you’ve got an activity that needs to be tracked closely. What that user account does next is very important. You don’t want to lock down access to sensitive data completely because that data is stored for reference and without it, many of your company’s departments would cease to function. You don’t want to block those superuser accounts either – they were created for reason.
Activity monitoring uses triage to trip a monitor when access to sensitive data occurs, raise an alarm when a subsequent action falls outside of the normal pattern of working behavior (established by UEBA), and applies scrutiny and investigative procedures that scan through event logs.
Insider threat management tools
You have a lot of data to protect and a lot of activities to watch. Naturally, you can’t do all of that manually. Fortunately, your entire insider threat management strategy can be implemented with just a few specialized tools. Here are two tools that demonstrate how two areas of specialization can cover all of the tasks you need to perform in your insider threat detection system.
Our methodology for selecting insider threat detection and mitigation tools
We reviewed the market for systems that will spot and block insider threats and we analyzed the options based on the following criteria:
- User behavior analysis (UBA) or a user and entity behavior analytics (UEBA) service
- Coordination with access rights management systems
- Ability to track activity on all parts of the system
- Detection of illogical movements, such as logging in from different countries
- Detection of abandoned accounts to reduce account takeover incidents
- Free trial or a demo package to enable a pre-purchase assessment
- Value for money from a threat detection system that can spot intruders as well as suspicious insiders
These are not the only tools in their fields but we consider them to be the best.
1. ManageEngine Endpoint DLP Plus (FREE TRIAL)
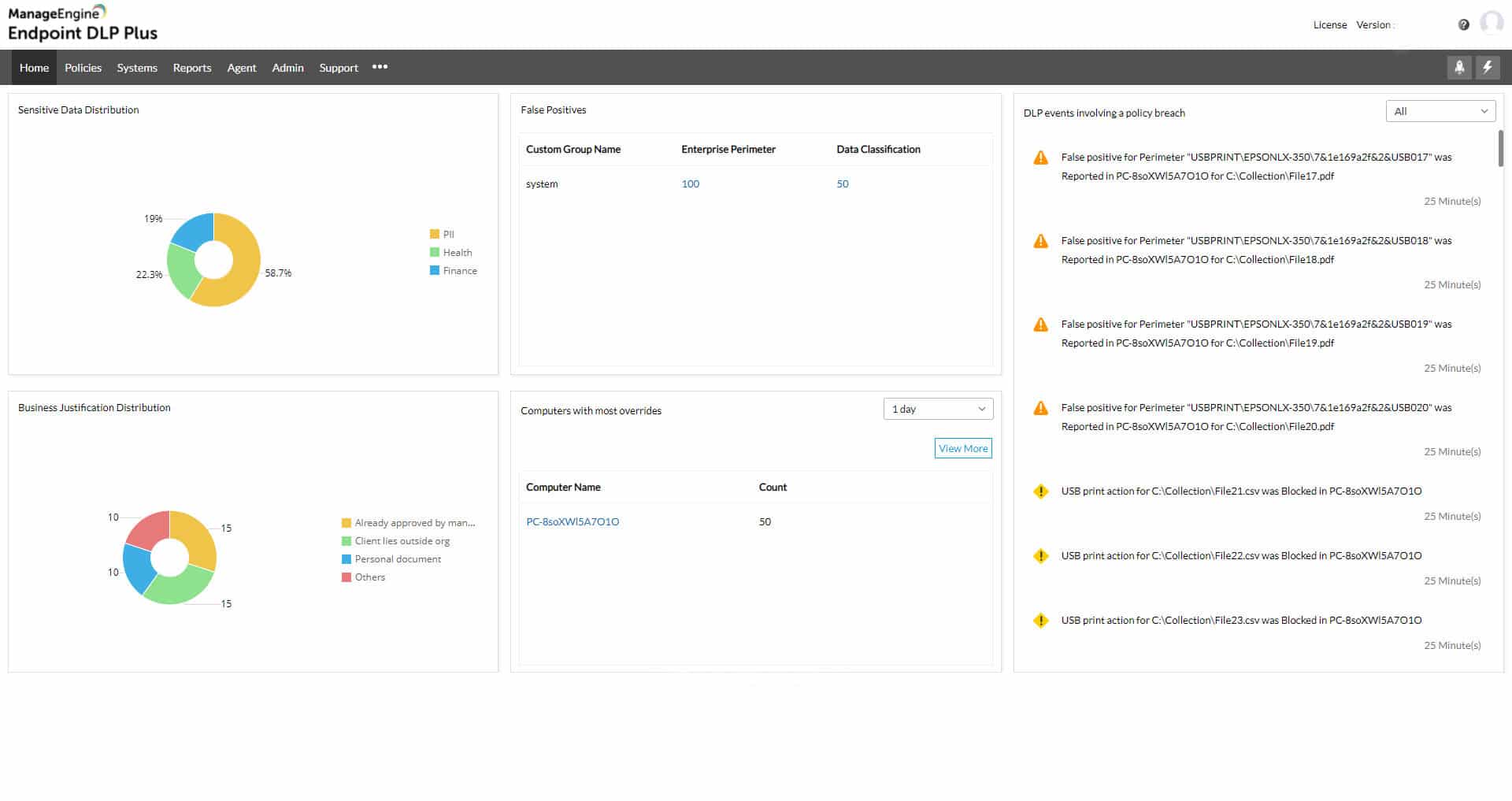
ManageEngine Endpoint DLP Plus is an on-premises software package that provides blocks against intrusion and scrutiny for insider threats. After scanning your system for sensitive data and categorizing it, Endpoint DLP Plus fences off the files that hold that data with containerization.
Key Features:
- Sensitive Data Protection: For PII and IP
- Discovers and Categorizes Data: Creates a catalog
- Containerizes Data: Protected access
- User Activity Tracking: Looks for insider threats and account takeovers
Why do we recommend it?
ManageEngine Endpoint DLP Plus is a protection system for sensitive data. This tool scans all of your servers, cloud accounts, and storage devices for data and then categorizes those instances according to a specific standard’s requirements. Those files are then protected with containerization and all activities related to them are controlled and logged.
Containerization makes direct access to the file’s contents impossible. So, if an intruder has managed to access an insecure server, it still won’t be possible to get to the file. The DLP system allows access to contents through a trusted application. You define in the settings of the ManageEngine tool which applications are to be used for which data types.
The applications that you approve for data access should have their own access rights requirements. Therefore, only authorized users can get access to those applications and the protected data. Data access events from within the application are logged and attributed to a user account. This enables retrospective analysis of data usage. However, suspicious data access activity, which falls outside of the user’s normal pattern of activity triggers an alert and deeper activity tracking.
The routines of Endpoint DLP Plus are useful for spotting account takeover as well as insider threats. Data movements are controlled with respect to the normal usage rights of the user account. These controls extend to print jobs, USB devices, email systems, and cloud upload facilities.
Who is it recommended for?
This package is designed for use by companies that manage sensitive data. It ensures that only those workers and processes that need to touch classified data actually get access to it and that use is only within the correct context. A Free edition will monitor data on 25 computers.
Pros:
- Approves Trusted Applications: Bans all other software
- File Integrity Monitoring: Logs all file access activity
- Device Control: USB sticks, printers, and other peripherals
- Email Scanning: Looks for sensitive data in the contents and attachments
Cons:
- Not a SaaS Package: Only available for Windows Server
Endpoint DLP Plus installs on Windows Server and there is a Free Edition to manage data on up to 25 computers. The paid plan is called the Professional Edition and it can be extended to clever multiple sites from one console. You can get a 30-day free trial of the Professional Edition. If you decide not to buy at the end of the trial, the package switches over to the Free edition.
2. SolarWinds Security Event Manager
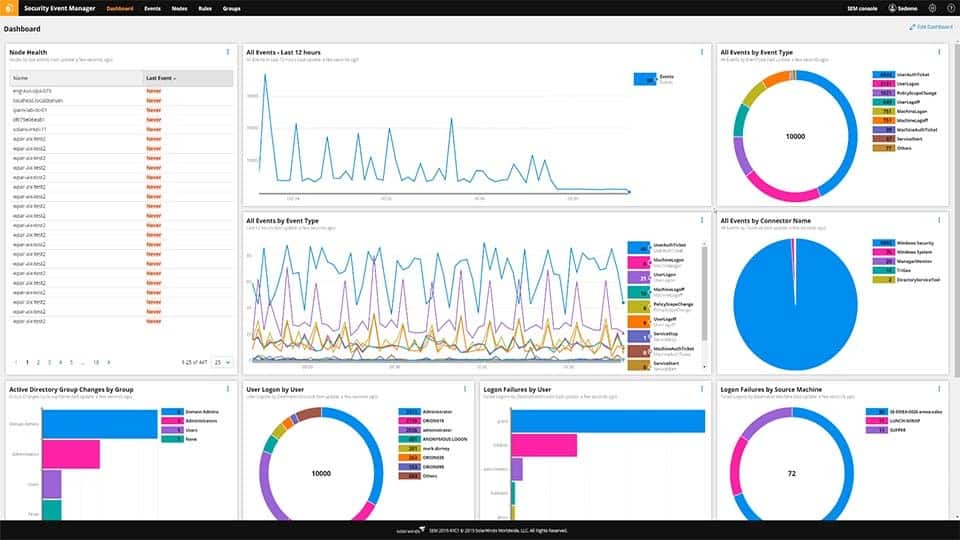
The Security Event Manager from SolarWinds is a category of security software called SIEM. It collects and searches through log messages to look for threats – both intrusion and insider threats.
Key Features:
- SIEM: Threat hunting based on log messages and network activity
- User and Entity Behavior Analytics: Looks for insider threats and account takeovers
- Automated Responses: Interfaces with third-party security tools
- Privileged Account Management: Protects admin passwords
- Compliance Management: PCI DSS, GLBA, SOX, NERC CIP, HIPAA
Why do we recommend it?
SolarWinds Security Event Manager is a system-wide activity monitor that collects and manages logs as well as sifting through their data for signs of all types of threats. The tool can be set up to run automated responses to insider threats or intrusions, such as suspending an account in Active Directory.
Log messages are generated constantly and reading them provides a source of live activity data. The Security Event Manager collects log messages from every part of the system and puts them in a common format. This enables the SIEM to search through logs looking for event correlations – patterns of different events that combine to indicate a security breach.
The SEM uses UEBA to establish a baseline of normal behavior against which can identify anomalies. When a potential insider threat event is detected, the SEM raises an alert, drawing attention to that user account. All log records are stored to enable historical analysis. So, once a user account is identified as displaying suspicious behavior, all activities of that user up to that point can be recalled.
The Security Event Manager is able to implement incident response actions automatically. It can suspend an account, eject a memory stick, block all outgoing emails from a user and log that user off the system. The option to trigger automatic responses is up to the system administrator – an alternative approach would be to let the system raise alerts and then leave the response to a decision-maker once further analysis has been carried out.
Who is it recommended for?
This is an on-premises package that can automatically collect activity data from all around an IT system. It is able to simultaneously process data from many technologies. Therefore, very large organizations get the best value from this service. The software package runs on Windows Server.
Pros:
- Wide Range of Integrations: Gathers activity data directly from software
- Simple Log Filtering: No need to learn a custom query language
- Dozens of Templates: Allow administrators to start using SEM with little setup or customization
- Log Management: Collection, consolidation, and filing
- Historical Analysis Tool: Helps find anomalous behavior and outliers in the network
Cons:
- No SaaS Option: An on-premises package for Windows Server
SolarWinds Security Event Manager installs on Windows Server and it is available on a 30-day free trial.
3. UnderDefense MAXI MDR
UnderDefense is a managed detection and response service (MDR) that provides a team of cybersecurity technicians on a service contract. The system is a SaaS package that implements security scanning. However, the package also provides the services of a cybersecurity team to manage the software and read through alerts.
Key Features:
- Managed Security Service: A team of cybersecurity technicians
- Threat Detection: Automated and manual attacks
- Cybersecurity Consultancy: Advice for system acquisition
Why do we recommend it?
UnderDefense MAXI MDR is a flexible package rather than an off-the-shelf solution. The UnderDefense experts will assess your company’s cybersecurity needs, acquire the right software and services, and set them all up for you. The group then provides ongoing supervision, or an on-call advise service – it’s up to you.
The UnderDefense team manages your existing security software or will advise on which tools to get. The company offers an on-demand service for companies that already have a cybersecurity team. In this option, your people can call UnderDefense experts to give their opinions about suspicious activity on your system and what actions they should take.
The UnderDefense team will link together your existing systems and integrate your firewalls, antivirus packages, and access rights manager so that all systems feed data into the threat detection service and can also receive back instructions to shut down those attacks.
This security solution will guard against all type of threats, which includes intrusion, automated attacks, account takeovers, phishing attacks, and insider threats. The service also provides log management and automated reporting for data protection standards compliance.
The Managed Detection and Response service provides experts to run your cybersecurity systems and take remediation action. This team will help you buy, set up, and run all of your cyber defense requirements, not just insider threat detection. You will need a complete protection system for your data and resources, which includes intrusion detection, malware blocking, and ransomware defense. Insider threats are particularly difficult to defend against and the supply of tools in this field is a fast-moving challenge. It is a lot easier to spot a rogue device or an account takeover than it is to identify dangerous actions by an authorized user. Whether your employees are disgruntled and destructive, duped by a con artist, or looking for a way to make money by selling sensitive data, you will need an expert eye to supplement the automated techniques of detection tools.
Who is it recommended for?
The UnderDefense team provides the expertise that many companies can’t afford or just can’t hire. Cybersecurity experts are in short supply and in many areas just aren’t available for any price. The UnderDefense team manages your security remotely – they won’t come to your site and you don’t have to provide them with office space.
Pros:
- Remote Operations: Runs its own Security Operations Center
- Service Options: Full coverage or on-call advice
- Bespoke Service: Flexible, tailored solution
Cons:
- No Free Trial: Request a demo instead
You can start with UnderDefense by getting a free account. This gives you access to utilities, such as a Dark Web scanner, a compliance guide, and a risk assessment template library. You can also access the free demo.
4. Endpoint Protector by CoSoSys
Endpoint Protector is a data loss prevention system that is hosted in the Cloud. Insider threat defense is a key service in this security system. The Endpoint Protector service implements three strategies to block insider threats; device activity tracking, data sensitivity classification, and application usage monitoring.
Key Features:
- Allow Listing: Blocks all software by default
- Access Rights Management: Link users to applications and files
- Activity Logging: Creates accountability
Why do we recommend it?
Endpoint Protector by CoSoSys implements a Zero Trust Access model that blocks all access by default. Data locations are protected and an access rights system defines which applications can access it. From that point, the credentials for those applications are critically important for data protection. The system also logs all activity for auditing.
The Endpoint Protector system monitors devices running Windows, macOS, and Linux. It checks on USB slots to watch file transfer activities and it can block the copying of certain files. The grading of which files require special controls stems from a data classification system. You then set security policies related to different data classifications.
The security policy creation system can distinguish between business departments, user groups, or user statuses. Thus, certain people in a specific department would be allowed to transfer a category of file, while simultaneously, other users would be blocked from, performing such actions.
The application controls in Endpoint Protector watch over activities performed in Microsoft Outlook, Skype, and Dropbox. The service can also monitor the data sent to printers. Thus, all channels for data disclosure are patrolled – memory sticks, emails, chat apps, printers, and file transfers.
Endpoint Protector is offered as a SaaS system. You can opt to get the package as a service on AWS, GCP, or Azure servers. It is also possible to acquire the software for Endpoint Protector and install it on your own system as a virtual appliance.
Who is it recommended for?
This system is very easy to implement and it errs on the side of creating temporary inconvenience by blocking access to data rather than a risk of administrative error allowing data to be disclosed. The package can be implemented by an administrator without special cybersecurity knowledge.
Pros:
- Tracking and Controls: Blocks insider threats
- Custom Security Policies: Attach to the user rather than the machine
- Vulnerability Scanning: Automatically assesses risk
Cons:
- No Free Trial: Access a demo instead
You can request access to the free demo in order to assess the service without risk.
5. Teramind DLP
Teramind DLP is a data loss prevention system that has templates to adapt its operations according to specific data security standards. This is an excellent tool insider threat protection system for businesses that need to comply to the PCI DSS, HIPAA, ISO 27001, and GDPR standards.
Key Features:
- Employee Tracking: The base package focuses on productivity
- Business Intelligence: Looks for non-standard activity
- Sensitive Data Detection: In the two highest plans
Why do we recommend it?
Teramind DLP is one of the higher plans available on the Teramind platform. This business specializes in employee tracking, which is an ideal starting point for insider threat management. The DLP edition adds on sensitive data management and automated responses to shut down insider threats.
As its name suggests, Teramind DLP focuses on protecting data. It is ideal for blocking intruders and insider threats. The tool starts its service by searching all around the IT system for all data stores. It then searches through every data location for specific types of data and categorizes them. This enables the service to focus on specific data, particularly the types of information that a given data security standard aims to protect.
The search for sensitive data continues throughout the systems service life. All events related to identified sensitive data are tracked and logged. While monitoring data stores, the system also analyzes all user accounts. It implements UEBA to get an overall view of normal activity so it can then identify anomalous behavior. Naturally, unusual activities that touch on sensitive data generates an alert.
In addition to data and user monitoring, the service checks data transfers over the network, in emails, and on memory sticks. Any unauthorized activity gets blocked. The system also includes investigative tools for historical data analysis and response methods plus surveillance systems, such as a keystroke logger that can be applied to suspicious user accounts.
Teramind DLP prevents data loss, monitors for data theft events, and then investigates events after they have happened. This is a complete data protection system for insider threat management.
Who is it recommended for?
This system is useful for businesses that don’t have sufficient in-person employee monitoring and whose requirements for sensitive data access make defining appropriate use difficult to convey to staff. While employee training should be the primary avenue for sensitive data management, this tool ensures that everyone gets the message.
Pros:
- Content-Based Behavior Rules: Pre-written security policy templates
- Compliance Management: PCI DSS, HIPAA, ISO 27001, and GDPR
- Free Trial: 7 days for the cloud version and 14 days for the on-premises package
Cons:
- No DLP in the Two Lower Plans: Make sure you pick the right edition