Systems administrators have been used to managing fleets of desktops for decades now. The tools available for monitoring office desktops have become very sophisticated, enabling all of those machines to be managed centrally. But then laptops came along and the staff wanted to access the server through mobile devices when they were out in the field – requiring different systems management services.
Here is our list of the best Unified Endpoint Management tools:
- NinjaOne Mobile Device Management (EDITOR’S CHOICE) This MDM adds iOS and Android management on to the main endpoint management service for Windows, macOS, and Linux to create a UEM. This is part of a cloud-based remote monitoring and management platform for use by IT departments and managed service providers. Get a 14-day free trial.
- N-able N-central (FREE TRIAL) A complete remote monitoring and management platform that is suitable for centralized system management by IT departments or Managed Service Providers. Start a 30-day free trial.
- ManageEngine Endpoint Central (FREE TRIAL) A monitoring, management, and security package for endpoints that includes special tools for managing mobile devices. It installs on Windows Server or cloud platforms. Get a 30-day free trial.
- BlackBerry UEM A suite of tools to manage desktops, mobile devices, and IoT devices. It is available for installation on Windows Server or as a SaaS platform.
- Citrix Endpoint Management A virtualization-linked UEM solution that enables devices and user profiles to be managed separately.
- VMware Workspace ONE A user-focused virtual desktop system that enables all endpoints to be managed centrally.
- Cisco Meraki A cloud-based endpoint management system that can enroll home-based desktops and mobile devices as well as office equipment.
The operating methods of connections from mobile devices are different from the system procedures for desktop connections. Laptops, smartphones, and tablets require different security procedures because they can be taken out of the office building. They can be lost or stolen much more easily than desktop computers. They need to be tracked and wiped remotely when mislaid.
All of the special requirements of mobile devices meant that separate software was developed to manage their connections. This later development of mobile device management systems meant that systems administrators got used to deploying separate monitoring and management tools for mobile devices while carrying on with familiar systems for desktop management.
The evolution of endpoint management
Unified endpoint management puts an end to switching between monitoring tools in order to manage all of the devices that a business’s employees use to access the network and servers. In recent years, IoT devices have come onto the scene – especially in the field of security cameras. Any device that contains a processor and is connected to the internet creates potential security problems.
All devices need to be patched and protected from hackers. The traffic crossing a network needs to be identified by the endpoint, no matter what type of device that endpoint is. Therefore, it is increasingly necessary to centralize the monitoring and management of all types of devices that a business employs. This need has created a market for unified endpoint management.
About unified endpoint management
Unified endpoint management integrates all of the special extra functions needed for mobile devices into network and endpoint management systems.
Unified Endpoint Management (UEM) is a bit of a misnomer because one of the key aspects that anyone needs from UEM is monitoring. So, it should really be called UEMM. A typical UEM system is able to integrate with network monitoring software. The system should enable all management and maintenance actions for all of the devices owned by a company to be performed from one central location.
A UEM should provide the ability to set up devices with a suite of software. It should allow the user to create profiles that include software bundles suitable for each job description and it should also manage user access rights to both devices and software.
Despite the unity of UEM, there are always going to be different administration needs for different types of devices. So, UEMs usually have different screens for different device types. For example, device tracking won’t be available for desktop computers. So, rather than treating all devices as equal, a UEM provides all of the functions needed to monitor and manage all devices within one dashboard – albeit across several screens.
Recommended UEM systems
A recent trend in the provision of system monitoring tools is to move them out to the cloud and deliver them on the Software-as-a-Service model (SaaS). Given that mobile devices could be anywhere in the world, it makes sense that the monitoring and management tool should work equally well no matter where the server that runs it is located.
Cloud-based UEMs are very good a providing centralized infrastructure management for multiple sites. Extending the logic of that capability, these tools are also very suitable for Managed Service Providers (MSPs) that need to manage multiple sites for multiple clients. So, even if a business doesn’t have many mobile devices in operation, it is a good idea to consider this monitoring and management route to future-proof the IT support team’s tools – those mobile devices will start to creep in.
The Best UEM Tools
Our methodology for selecting Unified Endpoint Management systems
We reviewed the market for UEM tools and assessed the options based on the following criteria:
- Compatibility with all major endpoint operating systems
- Mobile Device Management (MDM)
- Software profiles
- Automated onboarding and wiping
- Self-service enrollment
- A free trial or a demo for an opportunity to try before you buy
Value for money from a Unified Endpoint Management system that is offered at a price that gives a good deal with respect to the functions it includes
1. NinjaOne Mobile Device Management (FREE TRIAL)
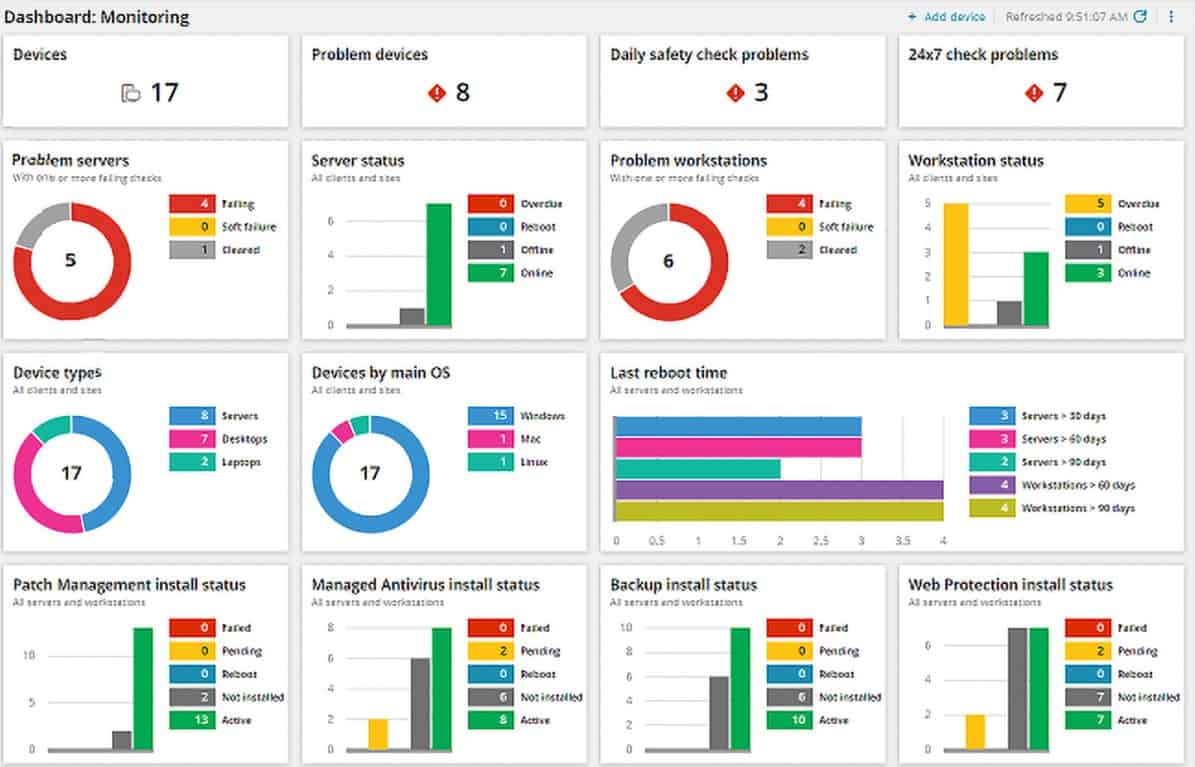
The NinjaOne Mobile Device Management service looks after mobile devices running iOS and Android. This combines with the computer management features of the NinjaOne RMM package to create a UEM. The on-premises computers that this system can watch over can be running Windows, macOS, or Linux. The RMM provides all of the remote monitoring and management tools that a central team of technicians needs to support IT systems on multiple sites.
Key Features:
- Multi-tenant architecture for MSPs
- Manages devices running iOS and Android
- Partners with an endpoint manager for computers
- Pre-set profiles for rapid onboarding
- Remote operations
Why do we recommend it?
The NinjaOne Mobile Device Management system is able to manage mobile devices whenever they are in the world – users don’t have to bring those devices into the office in order to get them set up. There is no chance of an employee sneaking off with a corporate mobile because the NinjaOne MDM shows on a map where every device is.
The NinjaOne platform is hosted in the cloud and the dashboard can be accessed from anywhere through any standard Web browser. The tool manages devices remotely, so you don’t need to have all mobiles on your desk to set them up. The console for the MDM lets you create a library of device profiles. Pick a profile and assign it to a device to get that mobile onboarded automatically. The system will set up its configuration and install all approved apps.
The package blocks users from installing their own favorite apps on corporate devices. It is also possible to completely limit the functions of a device into kiosk mode for use in retail environments. The central administrator can track each device and also access it for troubleshooting. The dashboard enables locking and wiping for lost and stolen devices.
Who is it recommended for?
The multi-tenant architecture of this platform makes it suitable for use by managed service providers. Each account holder can set up sub-accounts to hold the data of clients. However, the sub-accounts are not compulsory, so the package is just as good for IT departments running their own company’s IT assets. The service is particularly intended to run multiple sites from one location.
Pros:
- Provides monitoring and management for computers and mobile
- Security monitoring for mobile devices
- Software management and patching for workstations and servers
- Remote access for troubleshooting
- Enables tracking, locking, and wiping of mobile devices
Cons:
- You need to register for a quote, no public price list
NinjaOne doesn’t publish its prices but you can examine the entire RMM package with a 14-day free trial.
EDITOR'S CHOICE
NinjaOne Mobile Device Management is our top pick for a UEM tool because it teams up with the computer monitoring and management services in the main RMM package. This gives you controls over devices running Windows, macOS, Linux, iOS, and Android. This package is able to monitor and manage devices wherever they are in the world. The administrator console shows on a map the location of each device. Lost or stolen devices can be locked or wiped by the administrator. This system is able to monitor multiple sites in one account and MSPs can use it to manage the systems of multiple clients.
Download: Start a 14-day FREE Trial
Official Site: https://www.ninjaone.com/freetrialform/
OS: Cloud-based
2. N-able N-central (FREE TRIAL)
N-central is a product of the N-able’s MSP division. This part of the system tools provider’s operations supplies monitoring and management services for managed service providers (MSPs). However, many of these systems work just as well for the IT departments of multi-site organizations. N-central is a SaaS platform that includes all of the tools that IT professionals need to support IT resources and users.
Key Features:
- Designed for MSPs
- Mobile device management
- Desktops with Windows, macOS, and Linux
- Software inventory
- Software whitelisting
Why do we recommend it?
N-able N-central is a SaaS platform of remote monitoring and management tools. A great feature of this system is that it includes a great deal of automation in both monitoring and management divisions. The platform includes more than 650 automation scripts. The tool can look after endpoints running Windows, macOS, and Linux.
The monitoring system built into this system covers networks, servers, applications, and endpoints. As with most UEMs, it includes separate screens for the management of desktops and mobile devices. The on-site infrastructure monitoring and management services include a remote access function that enables all devices to be onboarded and set up from one central location. The service also includes a backup and restore system and patch management that covers servers and desktops.
The desktop and laptop services in the N-central system extend to an Endpoint Detection and Response system (EDR) to improve system security. Technicians can gain remote access to each device for the implementation of automated maintenance routines or for manual troubleshooting. These services cover devices running Windows, macOS, and Linux.
Who is it recommended for?
This system is intended for use by larger managed service providers and IT departments. Buyers of this service will need to add on a remote access package and MSPs will also need a professional services automation (PSA) plan. There is another N-able RMM system available, called N-able N-sight, which is designed for smaller MSPs.
Pros:
- Excellent monitoring dashboard, great for MSPs or any size NOC teams
- Scalable cloud-based deployment
- Monitor for anywhere via a web browser
- Automatic asset discovery makes inventory management easy, even on busy networks
- A wide variety of automated remote administration options make it a solid choice for helpdesk support
Cons:
- The platform can take time to fully explore all of its features and configuration options
N-able N-central is a subscription service and you can access it on a 30-day free trial.
N-able N-central includes an excellent security system as well as comprehensive monitoring and management services for all types of endpoints. N-able N-Central has integrated EDR software provided by Bitdefender to keep all Windows, macOS, and Linux devices secure and includes tracking, locking, and wiping utilities for mobile devices. IT professionals can use N-central to support corporate IT resources and it is also designed as a tools platform for MSPs.
Get a 30-day free trial: n-able.com/products/n-central/trial
Operating system: Cloud-based
3. ManageEngine Endpoint Central (FREE TRIAL)
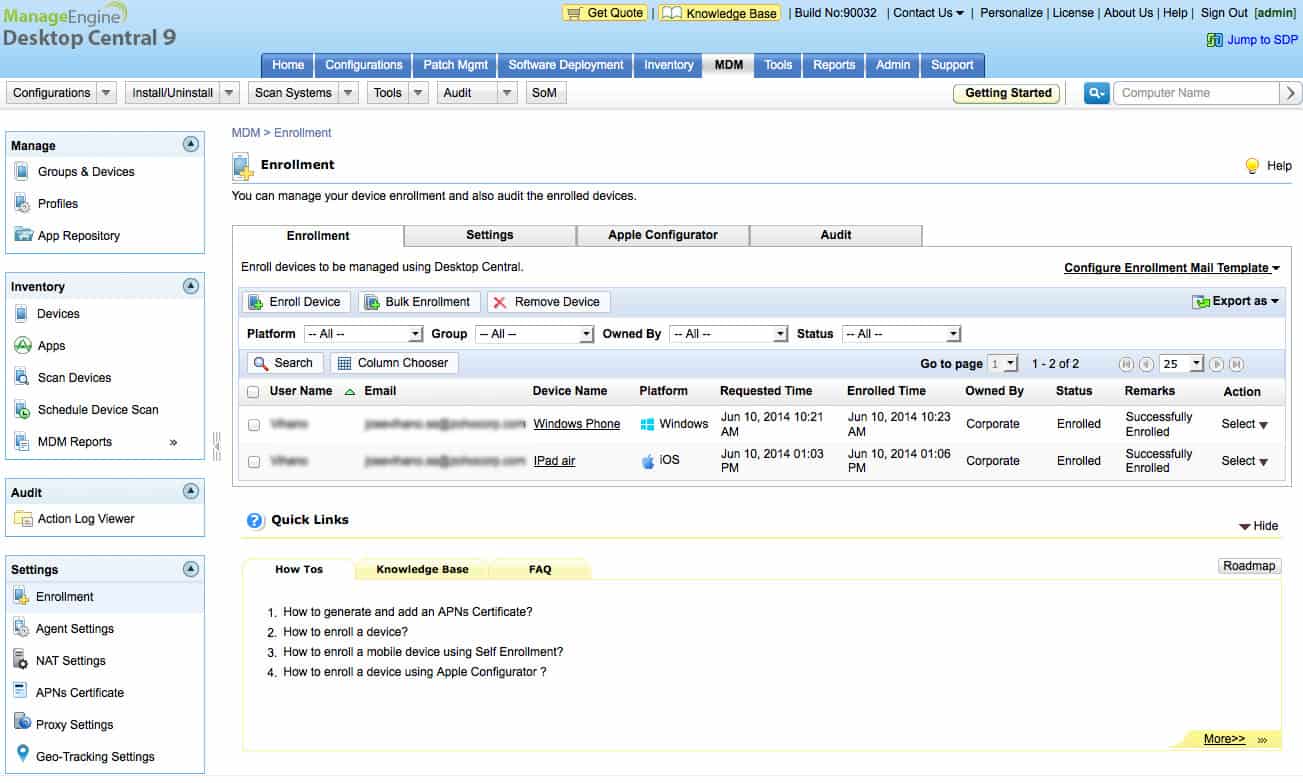
Endpoint Central – formerly Desktop Central – provides a platform for IT professionals to fully manage a company’s IT system no matter where those endpoints are. The software for this system installs on Windows Server and it is also available for installation on Azure cloud servers or an AWS account. The system can monitor endpoints that are on-premises, on remote sites, or out in the field.
Key Features:
- Manages desktops and mobile devices
- Software profiles
- Patch management
- Free edition
Why do we recommend it?
ManageEngine Endpoint Central is an RMM system that is designed for use by IT departments. This system provides monitoring and management utilities for desktops running Windows, macOS, and Linux. The mobile device management unit in the plan manages devices running iOS, Android, Windows, and Chrome OS.
ManageEngine is one of the leading providers of IT infrastructure monitoring services and Endpoint Central is built on the company’s expertise in many different areas of systems management. The service starts by tracking down all devices and logging them in an inventory. It records where each device is, its operating system, and its software inventory. This is the basis for all of its IT asset management functions.
Key features in Endpoint Central include configuration management, patch management, software license management, and remote access. Support technicians can use automated features in the dashboard to configure and backup devices and create standard setups for all desktop and mobile OSs. This creates the ability to set standard profiles that can be rolled out in bulk to onboard new device fleets. Each profile can also be applied individually.
Mobile device management features in the service include tracking, locking, and wiping utilities. It is also possible to blacklist apps and block facilities on each mobile device. The set-up service in the tool is part of a software management system that covers all device types, including desktops. This will keep track of licenses and install updates when they become available. Users can also onboard their own devices through a self-service portal.
Security software is available as an add-on option with Endpoint Central. This module includes constant vulnerability assessments and configuration tightening. Other security tools include browser security systems, application controls, and device controls. Datastores can be secured with BitLocker.
Who is it recommended for?
This package provides configuration management and patch management for desktops and the functions for mobile device management include tracking, locking, and wiping. It is possible to set up a standard software profile for each type of device and onboard new equipment in bulk or per device.
Pros:
- A good option for administrators who prefer on-premise solutions
- Can be installed on both Windows and Linux platforms, making it more flexible than some competing tools
- Offers in-depth reporting and inventory management – great for MSPs
- Supports mobile device management
Cons:
- Not the best choice for smaller networks
Endpoint Central is offered in four editions. The lowest of these is Free which is suitable for small businesses. The three paid versions are Professional, Enterprise, and UEM. Mobile device management is included in the UEM bundle and is available as a paid add-on in the Professional and Enterprise versions. ManageEngine offers the Enterprise edition on a 30-day free trial.
4. BlackBerry Spark UEM Suite
BlackBerry offers a unified endpoint management suite that covers desktops, mobile devices, and IoT equipment. The service is able to manage devices running Windows, macOS, ChromeOS, iOS, and Android.
Key Features:
- Asset tracking for desktops and mobile devices
- Software management
- Malware protection
Why do we recommend it?
The Blackberry Spark UEM Suite is particularly strong at managing and securing mobile devices. The package has different processes for dealing with user-owned devices and corporate fleet devices. This package includes connection security to bring mobile devices into the corporate network. The suite also provides a document copy-tracking system.
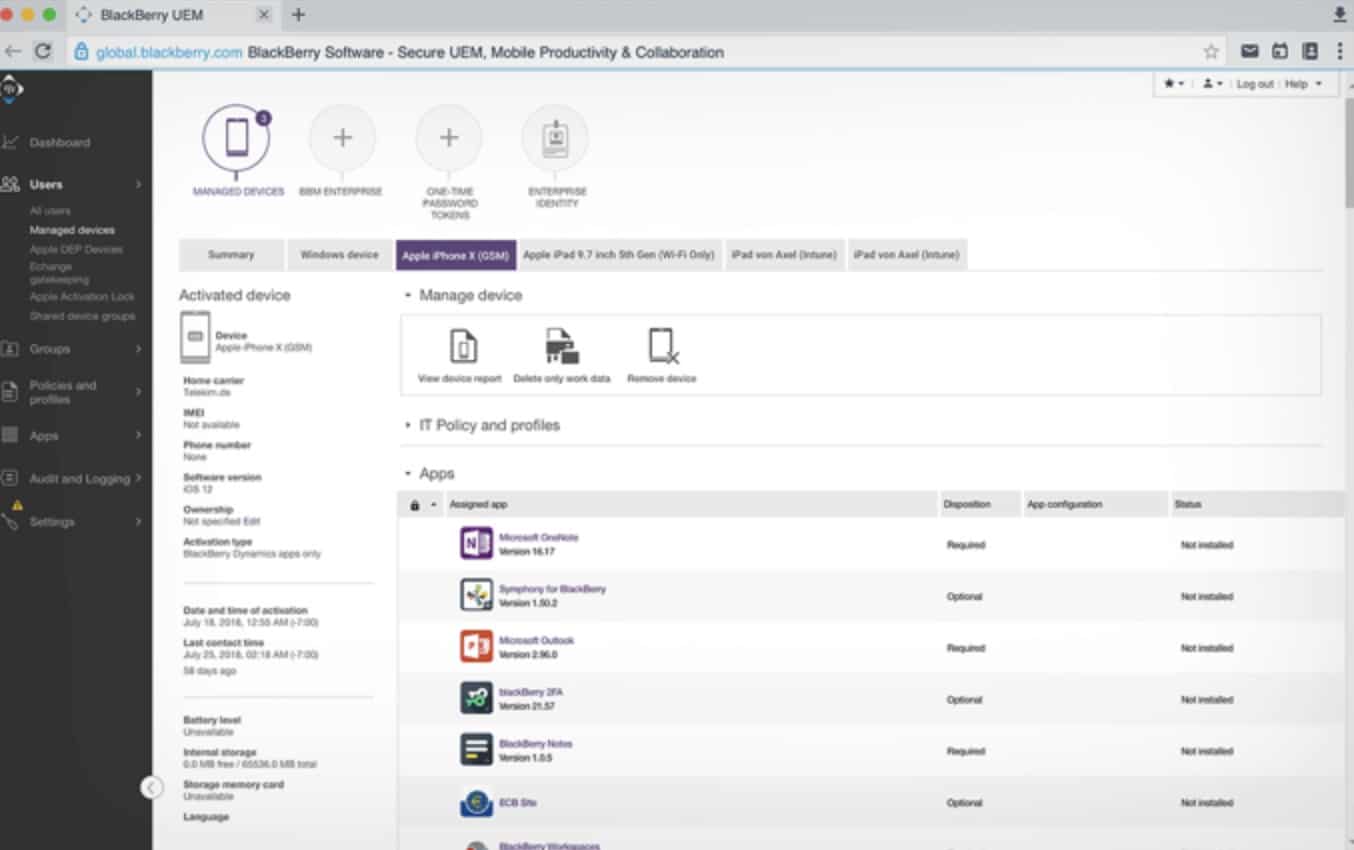
The dashboard of the service is accessed through a standard browser even if you choose the on-site installation option. The home screen on the console lists all of your enrolled devices, no matter whether they are on-premises or mobile. The monitoring list also includes user-owned BYOD devices.
The BlackBerry Spark UEM Suite system includes software management as well as hardware tracking. The service is able to manage license availability and identify where each license is deployed. This software management service also extends to the automated rollout of updates. OS patching can also be automated through the BlackBerry Spark UEM Suite system.
Mobile defense management tools in the UEM include AI-based malware protection. The mobile security system also checks apps for malicious activity and allows the system administrator to block the installation of unauthorized software. Remote access features include tracking, locking, and wiping functions. BYOD devices can access corporate services through a portal that keeps personal and business activities separate on the device.
Who is it recommended for?
This system provides a content network for sharing corporate data securely on any device. This makes it possible to allow employees to use their own devices without the risk of losing sensitive data. That strategy also helps to security include the computers of remote workers into the business’s network.
Pros:
- Sleek highly customizable interface
- Cross-platform support with Windows, Mac OS, Linux, Android, and iOS
- Available on-premise and as a cloud service
- Uniquely supports IoT devices – great for networks that rely on IoT sensors
Cons:
- Would like to see more options for mobile security
- Better suited for enterprise networks
BlackBerry Spark UEM Suite is available as on-premises software that installs on Windows Server. BlackBerry also offers the system as a SaaS platform hosted on its own servers. There is a BlackBerry Spark UEM Suite account option in AWS as well. You can access Spark UEM Suite on a free trial.
5. Citrix Endpoint Management
Citric is one of the leading virtualization providers and its Endpoint Management service is a SaaS platform based on its thin-client service, called Workspace Premium. The kernel of this UEM is a virtual desktop for each company user. The hardware element is a managed system that acts as an agent for the VM. So, A user can log in on any desktop and get access to the same environment.
Key Features:
- User-linked desktop
- Supports device switching
- Good for BYOD management
Why do we recommend it?
Citrix Endpoint Management is a virtual desktop system that attaches to the user account rather than to the device. Thus, a user can access any endpoint in the office, log in, and get access to a personalized computer. That computer is actually a slice of a central server rather than the local device. The package applies the same strategy to mobile devices.
The Citrix Endpoint Management system includes asset management. Devices running Windows, macOS, Chrome OS, Android, and iOS can be enrolled into the system. Once a device is registered, the management service keeps its operating system patched. Everything else on the device is virtual.
The software requirements of each type of user get set up on a central server and then made available as a VM. When a new user gets registered in the system, a VM copy gets allocated to that account by linking it to a profile.
On mobile devices, access to corporate services is managed through a portal app. This makes wiping very easy if a device gets lost or stolen – the administrator just blocks access to the service from that device. Onboarding devices just requires the user to install the portal app. This means that switching to a replacement device is a very quick process and it also makes BYOD access a straightforward process.
Who is it recommended for?
This system is a good choice for companies that have a roaming workforce and also have remote users. The company can create guest profiles for temporary workers and visiting consultants to deal with BYOD or even to allow visitors to use a spare office computer.
Pros:
- Supports a wide range of monitoring environments from Windows 10 to Citrix
- Monitors user behavior to identify insider threats and block high-risk users proactively
- Best suited for large environments that have to support multiple types of devices
- Can monitor and report on devices as well as certain users – great for asset tracking
Cons:
- Better suited for enterprise networks
6. VMware Workspace ONE
VMware is a major rival to Citrix in the virtualization market and it offers a UEM that is very similar to Citrix Endpoint Management. VMware Workspace ONE works through a virtual desktop system that grants each user access to a virtual desktop that can be accessed from any company device. The desktop version of the user’s worktop applies to computers running Windows and macOS.
Key Features:
- Virtual desktops
- Containerized protection on user-owned devices
- Self-service enrollment
Why do we recommend it?
VMware Workspace ONE is a similar system to the Citrix Endpoint Management package because it creates a virtual desktop for each user, which can be accessed from anywhere. The service is secure, so a user has to have an account on the virtual system. However, you can make that access portal available on the internet, which provides secure remote access.
Mobile devices running iOS and Android get access to a virtual desktop through a portal app. The app can easily be installed on user-owned devices, keeping business and private usage of the device separate. That mobile access can be easily revoked in the case of lost or stolen devices. The user then just needs to install the corporate app and log in to get access resumed.
Each supported desktop device needs to be enrolled in the system with agent software that can be installed remotely. Workspace ONE keeps the operating systems of those devices up to date but all other functions that users access on each desktop are really held on a central server and accessed over the network. Centralizing the hosting of software makes license management and updating a very straightforward process.
Who is it recommended for?
This package is suitable for any business, however, it will particularly appeal to those network managers that already understand how VMware virtualizations work. The tool makes the entire computer that each user gets out of a VM and applies the same method to mobile devices.
Pros:
- Leans heavily on virtualization for mobile devices (great for scaling across many devices)
- Highly visual interface – easy-to-see high-level insights
- Easy installation – uses a simple install portal to manage devices
- Ideal for data centers and larger network deployments
Cons:
- Smaller networks might not benefit from all of Workspace ONE’s virtualization features
7. Cisco Meraki
Cisco Meraki is able to extend the BYOD concept out to the desktops used by remote workers in their own homes. Meraki covers desktops, laptops, smartphones, and tablets. It includes software license management and patch management as well as IT asset management functions.
Key Features:
- Desktop virtualization
- Good for BYOD
- Cloud-based console
Why do we recommend it?
The Cisco Meraki approach to unified endpoint management relies on network security. Effectively, devices are included in the corporate network even if they are off-site. So this technique can be applied to the computers of hombre-based workers, the mobile devices of roaming staff, or to IoT devices.
This is a SaaS platform, so you don’t need to install and maintain the Meraki software on your own servers. The console can be accessed from anywhere through any browser or a Meraki console app. The delivery of a user environment is based on containerization. That is, each user gets access to a desktop or an app locker for the device, according to its type. This ensures that each user environment is consistent across devices and it also prevents company data from being accessed by others outside of the containing application.
The containerized solution makes it easy to control which apps can access corporate resources from outside the building and wiping the phone through remote processes isn’t necessary because the systems administrator just needs to blacklist a lost or stolen device.
Who is it recommended for?
The Cisco solution will appeal to network managers who are familiar with Cisco Systems technology and have had Cisoc training. This is a virtual network solution that can bridge to cloud platforms as well, which is a great choice for businesses that provide applications from their own servers and cloud accounts.
Pros:
- Protects communications with AES-256 bit encryption
- Supports BYOD enrollment – great for WFH environments
- Supports remote wipes for stolen devices
Cons:
- Better suited for small to medium-sized networks
- Would like to see a longer 30-day trial period
Cisco offers a 14-day free trial of Meraki.
Choosing a Unified Endpoint Management Tool
When examining the market for UEM tools, we focused on SaaS systems. Cloud-based services charge for their software by subscription and include all supporting hardware and services, so they are very easy to afford – there are no upfront costs involved in acquiring the system.
Unified Endpoint Management FAQs
What is a unified endpoint management system?
Unified Endpoint Management (UEM) is the process of managing desktops and mobile devices in a single console. UEM systems include a high degree of task automation to onboard devices, manage software inventories, and track device locations. Wiping devices in the event of loss or end of service is also a common feature of UIEM tools.
What is the difference between UEM and MDM?
MDM stands for Mobile Device Management and, as the name implies, it is concerned with including mobile devices in the corporate network. MDM systems include automated processes for onboarding and monitoring devices and often include tracking, locking, and wiping functions. Unified Endpoint Management (UEM) systems provide management functions to look after mobile devices and also desktops. These tools extend content and application management to devices running Windows, macOS, and Linux.
What is endpoint management?
Endpoint management refers to the administration of desktop computers and servers. These are computers that are connected to the same network. Functions of endpoint management include the maintenance of software inventories, configuration management, and patch management.