Cyber threats aren’t slowing down, and neither should your defenses. Vulnerability Assessment (VA) and Penetration Testing (PT) have become essential parts of a robust cybersecurity strategy. VA helps you find known weaknesses across your systems, while PT simulates how real attackers would exploit them. One identifies the “what,” and the other reveals the “how far” and “how bad”. Together, they provide you with the complete picture.
Here is our list of the best VAPT tools:
- Invicti Security Scanner EDITOR’S CHOICE This system automates security scans to identify vulnerabilities in web applications, providing detailed reports and actionable insights to mitigate risks and strengthen defenses. Available as a SaaS platform or for installation on Windows. Get access to a free demo.
- Acunetix Web Vulnerability Scanner (GET DEMO) A website vulnerability scanner and penetration testing system for websites that can be installed on-site or accessed as a cloud service. Access the free demo.
- ManageEngine Vulnerability Manager Plus (FREE TRIAL) A that includes a vulnerability scanner and automated systems to patch discovered weaknesses. Installs on Windows and Windows Server. Start a 30-day free trial.
- CrowdStrike Penetration Testing Services This is a human team of white hat hackers that can be hired through CrowdStrike to perform probing attacks on your system to discover its security weaknesses.
- Metasploit An open-source penetration testing framework that is available for free or in a paid Pro version that includes professional support. Installs on Windows, Windows Server, RHEL, and Ubuntu.
- Intruder A cloud-based vulnerability scanner with the option of human penetration testing.
- Nmap A free network vulnerability scanner with a front-end, called Zenmap. Both install on Windows, Linux, BSD Unix, and Mac OS.
- Wireshark A popular packet sniffer for wired and wireless networks. Installs on Windows, Linux, Unix, and Mac OS.
- John the Ripper Free, open-source password cracker, and hash type detector. Installs on Unix, macOS, Windows, DOS, BeOS, and OpenVMS.
- Nessus Application vulnerability assessor available in free and paid versions. Installs on Windows, Windows Server, Linux, Mac OS, and Free BSD.
- Aircrack-ng Well-known wireless network packet sniffer that is widely used by hackers. Runs on Linux.
- Burp Suite A platform for testing web application weaknesses. Installs on Linux.
- Probely A web application vulnerability scanner that is intended for use during development. Delivered as a cloud service.
- W3af A free, open-source web application scanner written for Windows, Linux, Mac OS, and Free BSD.
This guide is here to help you confidently choose the right solution for your needs. We’ve done the research, so you don’t have to. You’ll gain real-world insights into the best VAPT tools available, including their strengths, weaknesses, and the types of organizations they’re best suited for.
Our recommendations are based on hands-on testing, direct user feedback from various trusted platforms, and in-depth market research. If you’re looking to make an informed decision about which tools to trust in your security stack, you’re in the right place.
Key points to consider before purchasing a VAPT tool
Here are the key points to consider before choosing or purchasing a vulnerability assessment and penetration testing tool:
- Understand Your Environment: Ensure the tool supports the systems and platforms you work with.
- Look for Accurate Detection: You need tools that minimize false positives and negatives while reliably detecting real, exploitable vulnerabilities.
- Demand Automation and Integration: Make your life easier by choosing tools that integrate with your existing stack, such as CI/CD pipelines, SIEMs, ticketing systems, and support automation through APIs.
- Check Reporting and Risk Prioritization: You want clear, actionable reports that list findings and help you prioritize them based on severity, exploitability, and business impact.
- Consider Community and Vendor Support: Rely on tools that are actively maintained, have strong communities, and responsive vendor support. You’ll need that when new threats emerge or issues arise.
- Know the Licensing and Cost Structure: Ensure the pricing model aligns with your organization’s needs.
- Ensure Compliance Alignment: If you are responsible for meeting compliance requirements such as PCI-DSS, ISO 27001, or HIPAA, look for tools that can generate audit-ready reports and help you meet those standards.
No single tool does everything perfectly. Many security teams benefit from a hybrid toolkit that combines a few specialized tools rather than relying on just one. Always test with a proof of concept (PoC) before committing to a purchase.
Why do we need VAPT tools?
As we become increasingly reliant on IT systems, the security risks are also increasing both in terms of quantity and scope. It has become mandatory to proactively protect important IT systems so that there are no data security breaches. Penetration testing is the most useful technique adopted by companies to safeguard their IT infrastructures.
“With the cyber security landscape changing so rapidly, it’s imperative that organizations of all sizes regularly test their defenses. VAPT testing, conducted by experienced security professionals, helps to identify and address network and application-level vulnerabilities before they can be exploited by criminals.
“Avoid buying specialist VAPT tools or commissioning assessments from third parties without fully considering your business’ needs. Tests vary in focus, breath and duration so ensure that you take the time to fully scope your requirements to receive the greatest benefit and value for money.” – Mark Nicholls, CTO, Redscan.
Related post: Alternatives to Microsoft Baseline Security Analyzer
The Best VAPT Tools
This article goes over the best VAPT tools, with careful consideration for efficiency and effectiveness.
Some are available free of charge, while others will require you to loosen the purse strings.
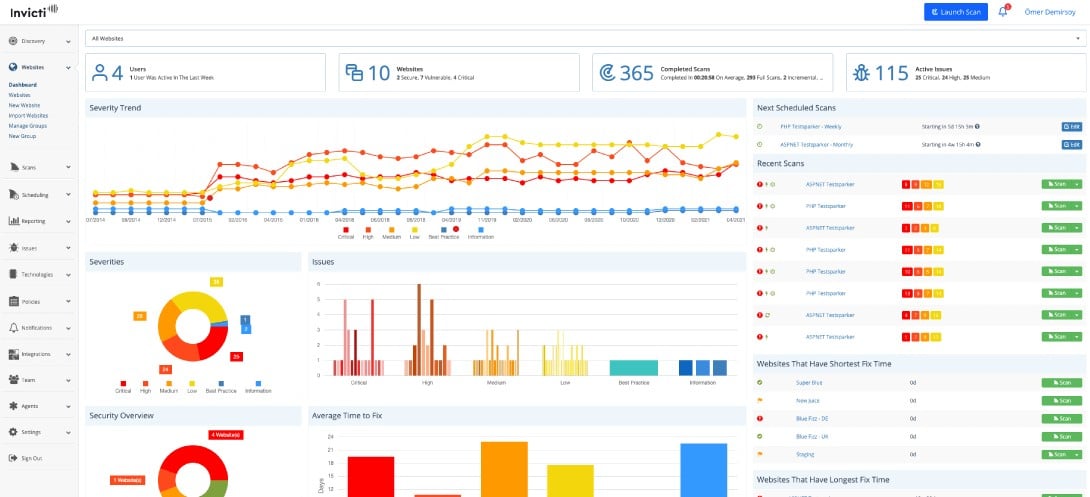
1. Invicti Security Scanner (GET DEMO)
Invicti Security Scanner (formerly Netsparker) is a web application security system that includes vulnerability scanning and penetration testing tools. The vulnerability scanner includes three phases; pre-execution, scanning, and vulnerability verification. The vulnerability checks use “proof-based scanning,” which doesn’t just examine responses to web requests but searches through the code of web applications.
Key Features:
- Proof-Based Scanning: Validates identified vulnerabilities, reducing false positives.
- Continuous Scanning: Offers round-the-clock detection of new vulnerabilities.
- Dynamic + Interactive Testing: Combines DAST and IAST for comprehensive analysis.
- Integration-Ready: Seamlessly connects with tools like Jira and GitHub.
- Comprehensive Coverage: Effectively scans HTML5, WordPress, Drupal, and more.
Why do we recommend it?
Invicti Security Scanner offers external vulnerability scanning or continuous testing for Web applications under development. This tool is specifically designed to scan Web assets for vulnerabilities and it implements dynamic application security testing (DAST) and interactive application security testing (IAST). This means it runs code through a range of scenarios.
The vulnerability checks cover standard web applications, such as HTML5, plus content applications, including WordPress and Drupal. Access control systems, such as authentication methods are also included in the vulnerability scan.
The scanner can be set to run constantly and it can feed vulnerability alerts through to bug and issue trackers, including Jira, Fogbugz, and Github. The scanner can be set to test new applications during the testing phase of development as well.
The vulnerability scanner will run constantly, so new vulnerabilities in your websites can be spotted once the system is in production. The system checks for misconfigurations in supporting technology, such as .NET and any updates in included code that arrives from other sources, such as content delivery systems.
The penetration testing tools in the package include attacks that use SQL injection and cross-site scripting. Tests can be run automatically and repeatedly as part of the vulnerability scanning schedule. This security testing automation cuts out the risk of human error and produces regulated test scripts.
The documentation produced by Invicti is compliant with PCI DSS, so retaining a documentation library from the scans is an important factor for standards conformance.
Who is it recommended for?
This system is aimed at DevOps teams that both develop Web applications and support them once they are live. This includes businesses that develop their own sites and microservices and also those that offer APIs to other businesses. Businesses that don’t have any Web systems won’t benefit from this tool.
Pros:
- User-Friendly Interface: Simplifies the process for administrators and NOCs.
- Advanced Penetration Tools: Ideal for organizations with internal security teams.
- Flexible Packages: Suits businesses of various sizes with different needs.
- Suitable for DevOps Teams: Can be integrated into a CI/CD pipeline.
- Scans Web Applications: Includes API testing.
Cons:
- Complex for Non-Professionals: Not suitable for casual or home users.
- Platform Limitation: Primarily supports Windows, which may restrict some users.
Invicti is available in three editions and can be installed on-site or accessed as a hosted service. The onsite software system runs on Windows. You can get access to a free demo system of Invicti to assess its capabilities before you buy it.
EDITOR'S CHOICE
Invicti is our top pick for a vulnerability assessment and penetration testing tool because it automates the security scanning process, making it easier for security teams to identify and address web application vulnerabilities quickly and effectively. One of the key reasons we recommend Invicti is its powerful scanning engine, which performs deep, dynamic analysis of web applications to uncover both common and complex vulnerabilities, such as SQL injection, cross-site scripting (XSS), and remote code execution. Invicti offers both automated vulnerability assessments and advanced penetration testing features, ensuring comprehensive coverage for organizations of all sizes. The tool is user-friendly, with a well laid out dashboard that allows security professionals to easily configure scans, review findings, and generate detailed reports. Invicti’s actionable reports provide clear remediation advice, helping security teams prioritize critical vulnerabilities and streamline the patching process. Its integration with various CI/CD pipelines and other security tools helps ensure ongoing vulnerability management. Invicti is an ideal solution for organizations seeking a reliable and efficient vulnerability assessment and penetration testing tool to safeguard their web applications from evolving threats.
Download: Get a 30-day free trial
Official Site: https://www.invicti.com/get-demo/
OS: Windows Server and SaaS
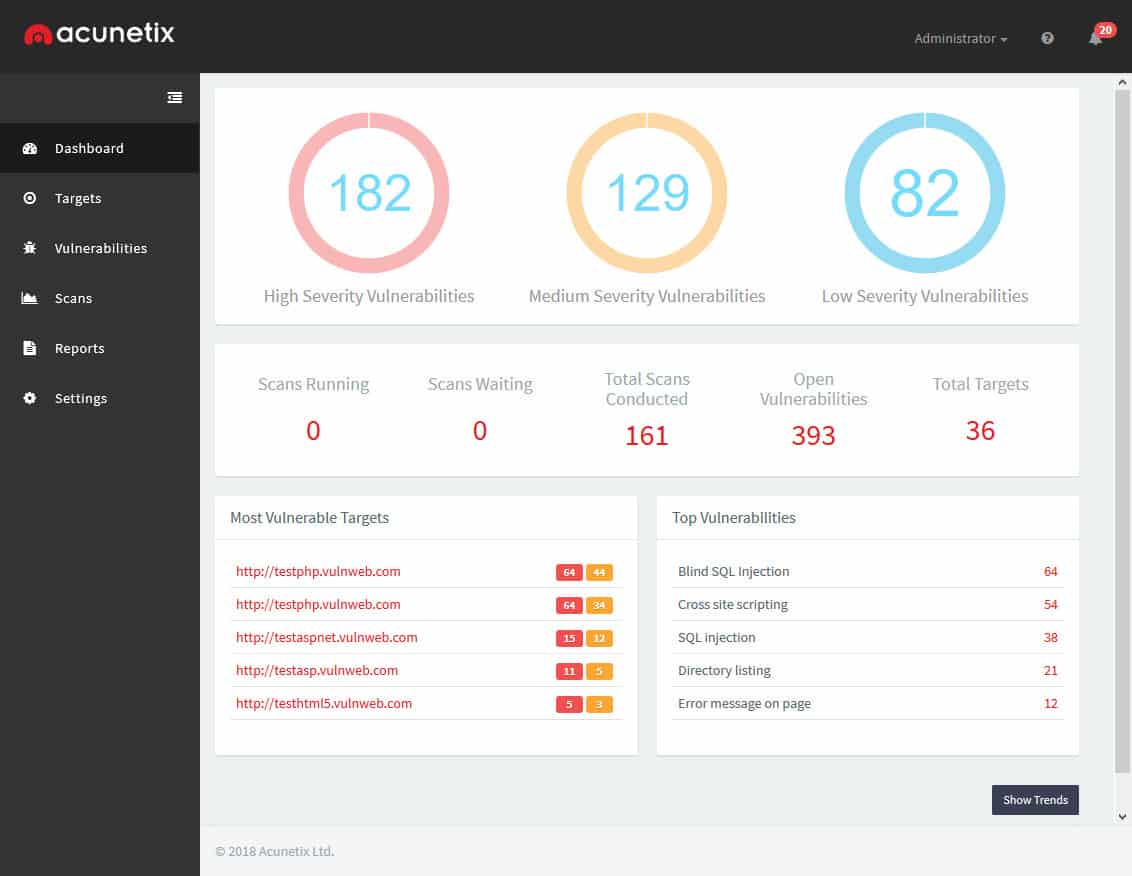
2. Acunetix Web Vulnerability Scanner (GET DEMO)
Acunetix Web Vulnerability Scanner combines its penetration testing procedures with its vulnerability scanner to create continuous automated threat detection for web pages. The system scans websites built through HTML5, JavaScript, and RESTful APIs to root out security weaknesses. The service also scans external sources of code, such as content management and delivery system, WordPress. Penetration testing procedures in the package include SQL injection and cross-site scripting. The security reports produced by the tool are compliant with HIPAA, PCI-DSS, and ISO/IEC 27001 standards.
Key Features:
- Extensive Vulnerability Detection: Identifies over 4,500 types of vulnerabilities.
- Multi-Platform Scanning: Effective on HTML5, JavaScript, RESTful APIs.
- Compliance Assurance: Meets HIPAA, PCI-DSS standards.
- Cloud or On-Premise Deployment: Offers flexibility in hosting options.
Why do we recommend it?
Acunetix Web Vulnerability Scanner is very similar to the Invicti system in that it focuses on discovering security weaknesses in websites and other Web-based systems, such as microservices and mobile apps. This package can also be used as a continuous tester in a CI/CD pipeline.
Some of the scans rely on sensors being placed within the code of a website and its applications. This inclusion could be difficult to manage for many organizations that don’t have their own web development team. The inclusion of data-gathering functions that communicate with an external system could itself become an information security weakness. However, that potential vulnerability doesn’t seem to worry the very impressive client list of Acutanix, which includes the US Air Force, AVG, and AWS.
If you do have a web development team and your site includes a lot of custom code, then you will be able to integrate Acutanix into your development management support system. The detection system forms a part of the testing software of new code and will produce a list of loopholes, inefficiencies, and vulnerabilities as a result of its testing procedures, sending recommendations on improvements back through the project management system.
Who is it recommended for?
Like Inviciti, Acunetix is designed for use by DevOps teams. You would get the best value out of this system if you develop Web assets for others to use. Businesses that need to show compliance with HIPAA or PCI-DSS will particularly benefit from this testing package. Operations teams can extend this package to add on OpenVAS, which provides internal network vulnerability scanning.
Pros:
- Deep Integration Capabilities: Works well with diverse development tools.
- Wide-Scale Threat Library: Over 4500 threat types for comprehensive scanning.
- Versatile Implementation: Suitable for cloud and on-premise setups.
Cons:
- Lack of Free Trial: Only a demo is available, limiting initial hands-on experience.
The Acunetix system is available for on-premises installation or as a cloud service. You can get a look at how the system performs on your websites by accessing the free demo.
3. ManageEngine Vulnerability Manager Plus (FREE TRIAL)
ManageEngine Vulnerability Plus is a vulnerability scanner that is bundled together with systems to help you fix the problems that the scan reveals. This is on-premises software that installs on Windows and Windows Server. It contacts other endpoints across a network by communicating with agents installed on each monitored device. Those agents are available for Windows, macOS, Linux, and Windows Server.
Key Features:
- Integrated Patch Management: Streamlines the update process post-vulnerability detection.
- Multi-Platform Support: Compatible with Windows, macOS, Linux.
- Real-Time Threat Intelligence: Keeps defenses updated against the latest threats.
Why do we recommend it?
ManageEngine Vulnerability Manager Plus not only discovers security weaknesses but it helps to fix them. In the cases of misconfigurations and other system-level security weaknesses, the tool prioritizes problems and produces guides for fixes. The package includes a patch manager to close exploits caused by outdated software.
The main module of this package is a vulnerability scanner. This will check on all enrolled computers either periodically on a schedule or on-demand. It checks for system configuration mistakes, outdated software versions, unauthorized and risky software, and OS and service weaknesses.
The system includes a patch manager, which can be set to automatically trigger action once a vulnerability has been identified. The patch rollout process can also be held back for approval and manual launch. The service also includes a security enforcement system, which implements strong password and access management.
Who is it recommended for?
This system will scan networks, endpoints, and Web servers in its search for vulnerabilities. The system installs on Windows Server, so if you don’t have that operating system on site, you won’t be able to use this package. The patch manager is able to update operating systems and software on endpoints running Windows, macOS, and Linux.
Pros:
- Proactive Scanning and Documentation: Helps in early detection and record-keeping.
- Scalable Solution: Efficiently handles enterprise-level network demands.
Cons:
- Complex Ecosystem: Requires significant time investment to master all features.
Vulnerability Manager Plus is available in three editions and the lowest of these is Free. The free version is limited to monitoring 25 computers. The two paid editions are called Professional and Enterprise. The main difference between these two versions is that the Professional edition covers one site, while the Enterprise edition is designed for WANs. Both paid systems are offered on a 30-day free trial.
4. CrowdStrike Penetration Testing Services
CrowdStrike Penetration Testing Services isn’t a tool, it is a team. This is a consultancy service offered by cybersecurity software provider, CrowdStrike. The aim of this service is to act like hackers and see how our system will cope with an attack. Not only is this service useful for identifying vulnerabilities but it can also give you an assessment of your security systems. You can never really know whether your intrusion detection package works until your system is actually under attack. If the CrowdStrike hackers come and go and your IDS or SIEM registers no abnormal activity, then you know you need to look around for better cybersecurity systems.
Key Features:
- Expert Testing Team: Leverages CrowdStrike’s cybersecurity expertise for thorough assessments.
- Comprehensive Security Evaluation: Includes internal, external, and wireless network testing.
- Insider Threat Simulation: Provides realistic assessment scenarios.
Why do we recommend it?
CrowdStrike Penetration Testing Services are security consultancy packages offered by one of the leading cybersecurity companies in the USA. CrowdStrike started out as a consultancy and started to produce its own tools for system investigations while investigating client systems. Those tools evolved into a menu of cybersecurity products but the company still maintains its original penetration testing service.
Who is it recommended for?
Penetration testing is always more expensive than vulnerability scanning. While a company can perform vulnerability scanning with a purchased tool, penetration testing has to be performed by an expert team of external consultants. Consequently, this is a less frequent exercise than vulnerability scanning and is usually beyond the budgets of small enterprises.
Pros:
- Holistic Security Approach: Offers a complete evaluation of systems and applications.
- Renowned Expertise: Leverages CrowdStrike’s acclaimed cybersecurity knowledge.
Cons:
- Cost Prohibitive for Small Businesses: High-level service may be beyond smaller enterprises’ budgets.
The CrowdStrike team will perform internal and external attacks and, given an account, they will emulate insider threats. The team will assess your Web applications, mobile apps, and APIs and work out whether they can be broken into, corrupted, hijacked, or used as an entrance to your entire system. You can also get the Penetration Testing Service to check out the security of your wireless systems.You can also access a 15-day free trial of Falcon Prevent to assess your network requirements.
5. Metasploit
Metasploit is a well-known compilation of different VAPT tools. It comes at the top of this list due to its prominence and reliability. Digital security experts and other IT specialists have utilized it for a considerable length of time to achieve different goals, including finding vulnerabilities, overseeing security risk assessments, and defining barrier approaches.
Key Features:
- Extensive Security Framework: Offers a wide range of penetration testing tools.
- Community-Driven Updates: Regularly enhanced by a large open-source community.
- Flexible Use Cases: Suitable for servers, applications, and network testing.
Why do we recommend it?
Metasploit is a highly respected penetration testing tool that is available in free and paid versions. The free option is called Metasploit Framework and it has a rudimentary interface that makes the package difficult to use. This edition can be extended by third party tools, creating a package of investigation and attack utilities.
You can utilize the Metasploit tool on servers, online-based applications, systems, and other areas. If a security weakness or loophole is discovered, the utility makes a record and fixes it. In the event that you have to assess the security of your framework against more established vulnerabilities, Metasploit will also have you covered.
In our experience, this tool proved to be the best penetration testing tool against large-scale attacks. Metasploit is especially adept at locating old vulnerabilities that are concealed and not able to be located manually.
Who is it recommended for?
Metasploit Framework is frequently used by professional penetration testers. The system is difficult to master and is not regarded as a system for occasional use by network managers., Metasploit Pro has a lot more automation and guidance and so could be used for internal testing as well as a tool for penetration testers.
Pros:
- High Customizability: Numerous open-source applications for tailored security testing.
- Strong Community Support: Benefits from a large, active user community.
Cons:
- Technical Proficiency Required: More suitable for users with advanced security knowledge.
Metasploit is available in both free and commercial versions; you can choose one based on your requirements.
6. Intruder
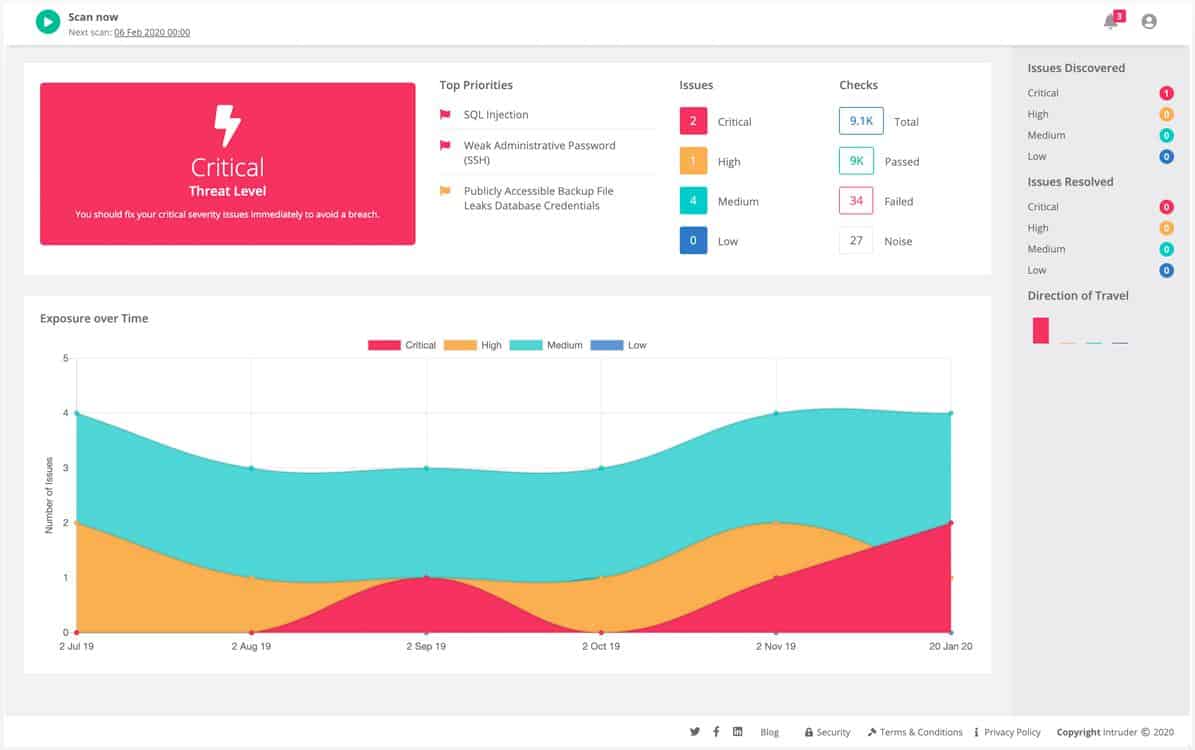
Intruder is a cloud-based vulnerability scanner. The service is a permanent security tool that can also be launched on-demand.
Key Features:
- Cloud-Based Flexibility: Enables accessible, scalable security solutions.
- Adaptable Scanning Modes: Choose from on-demand, scheduled, or continuous scans.
- Comprehensive Coverage: Includes both internal and external scans.
Why do we recommend it?
The Intruder.io system provides several modes of vulnerability scanning from its cloud location. You can get a regular monthly scan performed from an external viewpoint that ensures your network and cloud assets cannot be penetrated. Higher plans also provide more frequent internal scanning that looks for opportunities for lateral movement.
The service performs an initial vulnerability scan when a client sets up a new account. Once that audit has been completed, the Intruder system waits for an update to its attack database to come in. Once a new threat has been identified, the service scans the system again, focusing on elements that provide exploits for the new attack technique. If new equipment or services get added to the monitored system, the system administrator will need to launch a new scan to make sure that the addition does not have any vulnerabilities.

Who is it recommended for?
Vulnerability scanning is an increasingly essential security measure that all businesses should implement. The three plans for Intruder.io creates a lower price for businesses that just want to insure that their networks can’t be broken into. However, this service is still quite expensive and might prove beyond the budgets of small businesses.
Pros:
- Automated Scheduling: Simplifies the process of regular vulnerability scanning.
- In-depth User Interface: Provides detailed insights for better security management.
- Penetration Testing Service: Adds human expertise to the digital scanning process.
Cons:
- Advanced Features Learning Curve: May require time for users to fully utilize its capabilities.
Intruder is a subscription service. Subscribers have the option of three plans. These are Essential, Pro, and Verified. Scans occur automatically once a month with the Essential plan. On-demand scans aren’t available with that plan, but they are included with the Pro plan. The Verified plan has all of the features of the Pro plan and it also includes the services of human penetration testers. The Intruder service is available for a free trial.
7. Nmap
Nmap, an abbreviation of Network Mapper, is a totally free and open-source tool for checking your IT systems for a range of vulnerabilities. Nmap is useful at overcoming different tasks, including observing host or administration uptime and performing mapping of network assault surfaces.
Key Features:
- Robust Network Mapping: Efficiently identifies devices and services on a network.
- Command-Line Interface: Allows for scriptable, automated scanning processes.
- Free and Open Source: Accessible to all users without cost barriers.
Why do we recommend it?
Nmap is one of the tools that can be slotted into the Metasploit Framework. It is a command line system that detects all devices connected to a network. Network professionals will find the GUI front end for Nmap easier to use – that is called Zenmap. Both Nmap and Zenmap are available for free.
Nmap keeps running on all the major working frameworks and is reasonable for checking both huge and small networks. Nmap is compatible with all of the major operating systems, including Windows, Linux, and Macintosh.
With this utility, you can understand the different attributes of any objective network, including the hosts accessible on the network, the kind of framework running, and the type of bundled channels or firewalls that are set up.
Who is it recommended for?
Nmap is an internal tool for penetration testing and it is frequently used by hackers as well. Although command line systems are harder to use than GUI utilities, they have the advantage that they can be launched from within scripts. Nmap has been around for a long time, so it is bug free and reliable.
Pros:
- Comprehensive Discovery Capabilities: Thoroughly explores network infrastructures.
- Strong Community Support: Regular updates and enhancements from users.
Cons:
- Lacks GUI in Base Version: Command-line focus may deter less technical users.
You can download it from their official website on Nmap.
See also: Definitive Guide to Nmap
8. Wireshark
Wireshark is an open-source system analyzer and troubleshooter. It has a streamlined feature that lets you monitor what is being done on your system network. It’s the de facto standard for corporate use as well as small agencies. Wireshark is also being used by academic institutes and government offices. Its development was started in 1998 by Gerald Combs. You can download it from Wireshark.
Key Features:
- Detailed Packet Analysis: Captures and analyzes network traffic in-depth.
- Extensive Filtering Options: Helps isolate relevant network data for analysis.
- Free and Open Source: Ensures accessibility and community-driven improvements.
Why do we recommend it?
Wireshark is a free tool that is widely used by network managers, penetration testers, and hackers. This utility captures packets and displays them in a viewer. You can just get a burst of packets and turn off the capture function, leaving packets visible in the viewer for analysis.
You can read in packets live from the network, save them to file, and then load them back into the Wireshark interface. The data analyzer includes its own query language that can filter packers and identify specific streams or conversations. It is possible to apply filters to packet captures as well, which reduces the volume of data that you need to weed through to find relevant information.
Who is it recommended for?
Although Wireshark costs nothing, it isn’t advisable for infrequent, casual use. It is difficult to learn because it has its own query language, which is extensive. The many filter conditions that you can set up to reduce the number of packets that get read in can also be used to analyze packet header contents.
Pros:
- Industry-Standard Tool: Widely trusted and utilized in various sectors.
- In-Depth Data Capture: Provides granular insights into network traffic.
Cons:
- Complex Data Analysis: May overwhelm users not versed in network analysis.
There is a command line version of Wireshark available, called TShark. Wireshark is available for Windows, Linux, macOS, and NetBSD. You can download the tool for free.
9. John the Ripper
Disturbingly, many people use easy-to-guess passwords such as admin123, password, 123545, etc. Password cracking is the most common cybersecurity breach, and usually, this occurs due to soft passwords that can be trivially cracked in under a second by a modern password cracker running good hardware. Accounts with such passwords are therefore easy prey for hackers; they can delve with reckless abandon into your system’s network and steal information like credit card numbers, your bank passwords, and sensitive media.
Key Features:
- Password Cracking Efficiency: Excels in identifying weak passwords across systems.
- Command-Line Operability: Allows for flexible and scriptable use.
- Free Tool: Accessible without any cost, fostering widespread use.
Why do we recommend it?
John the Ripper is very well known as a hacker tool. So much so that your anti-virus will kick up a stink when you install it and try to run it. The system can be used to crack passwords. However, a straightforward password policy should render the system useless. So, run this system to check that your passwords are strong enough.
John the Ripper is the best tool for analyzing your entire system for easily guessable/crackable passwords. It actually launches a simulated attack on the proposed system to identify password vulnerabilities.
Who is it recommended for?
This tool is free but difficult to use and many network managers that are attracted by this package would opt for the paid Pro version, which is easier to use and, in its unsupported version is very cheap. Frequent users, such as hackers and penetration testers will have no problems using the free tool.
Pros:
- Effective Password Auditing: Helps in strengthening password security policies.
- Lightweight and Versatile: Easy to deploy across various environments.
Cons:
- No GUI in Free Version: Lack of graphical interface can challenge less tech-savvy users.
Its free version comes in the shape of source code, which you will obviously need a developer to integrate for your company’s use. The pro version, however, is easy to embed. It is distributed in native packages (unique for every operating system) and is easy to install.
10. Nessus
Nessus is another vulnerability-finding tool, but it’s also a paid tool. It’s very easy to use and works smoothly. You can use it for assessing your network, which will give you a detailed summation of the vulnerabilities in your network.
Key Features:
- Comprehensive Vulnerability Scanning: Identifies a wide range of security weaknesses.
- User-Friendly Interface: Simplifies the process of vulnerability assessment.
- Configurable Templates: Over 450 pre-set templates for various network scenarios.
Why do we recommend it?
Nessus is known to all in the cybersecurity community and its free version had a large user base. However, now, the only free option is called Nessus Essentials, which is only for use on home networks and not for business – many home-based small businesses could get away with using it.
Prominent vulnerabilities in which Nessus is specialized include misconfiguration errors, common passwords, and open ports.
Who is it recommended for?
Nessus Professional and Nessus Enterprise are very expensive tools and so they are out of reach for cash-strapped small businesses and startups. Even professional penetration testers traditionally favor free tools and individual consultants would be reluctant to pay the high price for Nessus. Cybersecurity consultancies and very large businesses are the most likely buyers of this tool.
Pros:
- Intuitive Use: Easy for beginners to navigate and operate.
- Scalable Solutions: Adequate for both small and large network environments.
Cons:
- Cost for Advanced Versions: More comprehensive versions can be expensive for smaller organizations.
As of this writing, 27,000 organizations are using it worldwide. It has three versions—the first one is free and has fewer features, with only basic level assessments. We suggest you go for the paid versions if you can so that your network or system will be properly protected against cyber threats.
11. Aircrack-ng
Aircrack-ng specializes in assessing vulnerabilities in your WiFi network. When you run this tool on your computer system, it runs the packets for assessment and gives you the results in a text file. It can also crack WEP & WPA-PSK keys.
Key Features:
- Wireless Network Analysis: Specializes in WiFi security testing.
- Password Cracking Capabilities: Can crack WEP and WPA-PSK keys.
- Free and Open Source: Available to users at no cost.
Why do we recommend it?
Aircrack-ng is one of the few hacker tools that is able to operate on wireless networks. The utility is able to detect active channels, trace transmitting devices, and attempt to crack passwords. This tool can also be used to trick receivers with replay attacks and cause havoc by sending a deauth instruction.
Who is it recommended for?
Aircrack-ng does pose a serious threat to wireless networks and it is worthwhile for penetration testers to check whether systems are vulnerable to attacks with this tool. The system is free and it is available for all the major operating systems. However, it takes time to learn how to use the utility effectively.
Pros:
- Dedicated to WiFi Security: Focuses specifically on wireless network vulnerabilities.
- Wide Tool Support: Compatible with a range of wireless network adapters.
Cons:
- Not a Comprehensive Tool: Primarily focused on WiFi, less versatile for other security aspects.
12. Burp Suite
A popular tool for checking the security of online applications.
Key Features:
- Integrated Security Testing: Combines different tools for web application security testing.
- User-Friendly GUI: Facilitates ease of use for various testing activities.
- Free and Paid Versions: Offers options based on user needs and expertise.
Why do we recommend it?
Burp Suite is similar to Metasploit in that it is highly respected as a penetration testing tool and it is available in free and paid versions. However, Burp Suite has the edge over its rival because it has one GUI interface and free users get the user-friendly interface but with many functions disabled.
Burp Suite comprises different devices that can be utilized for completing distinctive security tests, including mapping the assault surface of the application, investigating solicitations and reactions happening between the program and goal servers, and checking applications for potential threats.
Who is it recommended for?
Burp Suite makes penetration testing enjoyable because it presents a menu of services that are divided into research and attack systems. Data gets copied over from investigation tools to attack systems. The free edition gives you penetration testing tools while the paid features are more automated and should be described as a vulnerability scanner.
Pros:
- Versatile Testing Tools: Supports a broad spectrum of security testing requirements.
- Community Edition Accessibility: Free version available for basic testing needs.
Cons:
- Complex for Novices: Can be overwhelming for users new to security testing.
Burp Suite comes in both a free and paid version. The free one has basic manual devices for carrying out checking exercises. You can go for the paid version in the event that you need web-testing capabilities.
13. Probely
Probely is also a web application assessor; companies use it to find vulnerabilities in their web apps in the development phase. It lets clients know the lifecycle of vulnerabilities and also offers a guide on fixing the issues.
Key Features:
- Web Application Scanning: Specializes in identifying vulnerabilities in web applications.
- Extensive Vulnerability Database: Checks against a vast array of known security weaknesses.
- Integration with Development Tools: Facilitates seamless inclusion in CI/CD pipelines.
Why do we recommend it?
Probely is a cloud-based service that performs vulnerability testing for Web applications. Te tool can check on live websites, APIs, mobile apps, and APIs from an external viewpoint. It can also test your Web applications that are under development, before they go into your code repository, operating as a continuous tester for CI/CD pipelines.
Who is it recommended for?
The Probely service is very similar to Invicti and Actunetix, so if you are looking for Web application testers, you should consider all three of these services side by side. Although this system can be used purely as a vulnerability scanner for live systems, it is DevOps teams that will really benefit from using Probely.
Pros:
- Intuitive User Interface: Simplifies monitoring and managing web application vulnerabilities.
- CMS Integration: Effectively works with popular content management systems.
Cons:
- Primarily for Web Applications: Less suitable for broader network or system security testing.
Probely is arguably the best testing tool for developers.
14. W3af
W3af is a web application known for its ‘hack and review’ system. It has three sorts of modules—disclosure, review, and assault—that works correspondingly for any vulnerabilities in a given website. For example, a discovery plugin in w3af searches for various URLs to test for vulnerabilities and then forwards it to the review module, which at that point utilizes these URLs to scan for vulnerabilities.
Key Features:
- Web Application Audit: Focuses on discovering vulnerabilities in web applications.
- Modular Architecture: Offers discovery, audit, and attack modules for comprehensive testing.
- User-Friendly Interface: Simplifies the process of web application security testing.
Why do we recommend it?
W3af is a fun tool that will appeal to penetration testers. Like Burp Suite, the package has separate utilities for investigation and attack and data gets copied over automatically from research to testing. This system has a nice GUI front end, which makes it easy to use.
It can likewise be designed to keep running as a MITM intermediary. Any solicitation that is caught could be sent to the solicitation generator; after that is done, manual web application testing can be performed utilizing varying parameters. It also points out vulnerabilities that it finds and describes how these vulnerabilities could be exploited by malevolent entities.
Who is it recommended for?
W3af is free and easy to use, which should make it very appealing to a typical penetration tester. This is a good team for freelance independent penetration testers and big cybersecurity consultancy would use it, too. The system is specifically for testing Web applications and not internal systems.
Pros:
- Targeted Web Security: Provides in-depth testing for web applications and websites.
- Flexible and Lightweight: Easy to use without heavy resource requirements.
Cons:
- Web-Centric Focus: May not cater to broader security needs beyond web applications.
Choosing the right VAPT tool
Choosing the right VAPT tool really depends on your precise needs. All the tools have their own strengths based on the types of users they are catering to. Some are dedicated to a specific task, while others are broader in scope. As such, you should opt for a tool according to your requirements, whether you want to assess your entire environment, focus on Wi-Fi security, or concentrate on web application testing.
Our methodology for choosing VAPT tools
When putting together this VAPT toolset, we focused on what matters most to pen testers and security professionals like you. Our evaluation methodology focused on breadth of coverage, specialization, usability, and industry reliability. You need tools that uncover vulnerabilities and also help you validate and exploit them when necessary.
We also ensured that we balanced enterprise-grade platforms with open-source and community tools. We selected these tools for their proven effectiveness in real-world environments, such as hybrid infrastructures, cloud services, web applications, and internal networks.
Check out our detailed B2B software methodology page to learn more.
VAPT Tools FAQs
How often should I run a VAPT audit?
Run a VAPT audit once a month. Most VAPT tools include a scheduler, so this task can be repeated without anyone having to remember to launch it manually.
How long does a penetration test take?
There is no set length of time for a penetration test because some systems are larger than others and so have more tests that need to be performed. A test schedule can span anywhere from a week to a month, but small businesses would get their tests finished a lot faster.
How do you prepare for a penetration test?
Set clear goals and limits on the test by producing a scope document and itemizing expected deliverables. Distribute this information to everyone involved in the test.
- Set a date for the penetration test and allocate human resources to the task.
- Stabilize the current environment by applying all pending patches.
- Backup current equipment settings, files, and data.
How do you perform a VAPT test?
A VAPT test involves several stages:
- Define the scope and method of the test, specifying goals.
- Execute the test with a vulnerability scanner and pen-testing tools.
- Analyze the results of the tests for weaknesses.
- Report on the results of the test and agree on a remediation strategy with stakeholders.
- Implement remediation tasks.
A vulnerability management system will perform the entire test cycle for you, providing templates for standard goals and assessment strategies, implementing tests, and reporting on results.
What is network VAPT?
A network VAPT is a vulnerability assessment exercise that has its scope set to just examining network devices for security weaknesses. This focuses on switches, routers, firewalls, and load balancers.
Do hackers use VAPT tools?
VAPT tools emulate the strategies of hackers. Penetration testing is a manual task performed by white hat hackers, using tools that hackers frequently deploy to break into systems. So, rather than saying that hackers use VAPT tools, it is more accurate to say that VAPT systems use hacker tools.