An Application Programming Interface (API) is a type of software interface that offers a service to other pieces of software or applications
There are various usages or applications of the concept of API, but for this guide, the term API is used to refer to web APIs, which of course is what most people think of when they hear the term API.
Web API is a web development concept that allows client devices to access services on a web server using the Hypertext Transfer Protocol (HTTP). Common API protocols include gRPC APIs from Google, GraphQL APIs from Facebook, SOAP APIs using XML, and RESTful APIs using JASON. For example, Twitter’s REST API allows developers to access and interact with Twitter core data such as search and trends data.
Why API Security is Important

API has become a key element of innovation in today’s app-driven world. Whether you’re working on mobile, web, or internal apps for use in your company, you are most likely going to rely on APIs to get things to work. From government, banks, and retail to IoT, APIs are a critical part of modern mobile and web applications. Although using an API brings many benefits, it also comes with inherent security risks. By nature, APIs increase an application’s attack surface and expose application and sensitive internal data to attackers. This is why API security is very important.
A secure API can guarantee the confidentiality and integrity of the information it processes from external clients and servers. API security is the systematic approach that organizations take to protect APIs from attacks. As API-based apps differ from traditional apps, so does API security differ from traditional web application security. Just like traditional web applications, APIs also have their own unique set of vulnerabilities and attack techniques. The OWASP API Top 10 offers a useful overview of common API vulnerabilities. API Security focuses on strategies and solutions to mitigate the unique vulnerabilities and security risks associated with APIs. This provides a good starting point for organizations seeking to improve their API security posture.
Common API Attack Techniques
APIs can be attacked and abused in many different ways, but some of the most common examples include:
- Man in the Middle Attack (MITM) An attacker can act as a man in the middle between a session token issuing API to an HTTP header and a user. If the hacker can intercept that session token, it would grant him access to the user’s account, which can lead to unauthorized access to sensitive data.
- API Injection Attacks API injection attacks are common with applications that do not follow secure coding practices. The attacker injects malicious code into your application to gain access to resources. Typical examples include SQL injection, JSON injection, and cross-site scripting (XSS)
- Distributed Denial of Service (DDoS) Attack A DDoS attack on a web API attempts to overwhelm its memory by crowding it with several thousand connections at the same time. Attackers can also do this by sending a huge amount of information in each request.
- Account Takeover Fraud Account takeover (ATO) fraud involves a malicious actor gaining unauthorized access to an API account and using it for some type of personal gain. After a credential theft or even an XSS attack, an API account can be taken over. Once that happens, a data breach is inevitable which can be costly for both businesses and individuals.
- Vulnerability Exploitation Underlying vulnerabilities can be exploited by threat actors which can lead to unauthorized access to sensitive data. Common API vulnerabilities that can result in unauthorized data access include broken object-level authorization (BOLA), broken user authentication, excessive data exposure, and business logic vulnerabilities, among others.
- Data Scraping Data scraping is a technique used to extract data from human-readable output coming from another application on the web. As organizations make data sets available through public APIs, bad actors may aggressively query these resources to scrape valuable data sets. Data scraping is also done to interface to a third-party system that does not provide a more convenient API. In whichever case, data scraping leads to increased system load, and loss of control of the information content, among others.
Key Components of Good API Security Program
The following are three key components of a good API security program:
1. Access Control Access control measures protect the API systems and resources from unauthorized access by ensuring that all applications, servers, and users that consume your API are those with the proper permissions to do so. The two main means of access control are authentication and authorization. For users or applications to be able to access a resource, they first must prove they are who they claim to be and have the necessary credentials, and rights or privileges to perform the actions he is requesting. Good API security requires strong access control measures including multi-factor authentication (MFA) to manage and control access to applications and resources.
2. Confidentiality and Integrity of Data Confidentiality is the assurance that information is not disclosed to unauthorized individuals, programs, or processes. This means that control mechanisms need to be in place to dictate who can access API data and what the subject can do with it once they have accessed it. These activities need to be controlled, audited, and monitored. Examples of information that could be considered confidential are health records, financial account information, source codes, and trade secrets. Some security mechanisms that would provide confidentiality are encryption, logical and physical access controls, and database views, among others.
Similarly, when a security mechanism provides integrity, it protects API data, or a resource, from being altered in an unauthorized fashion. If any type of illegitimate modification does occur, the security mechanism must alert the user or administrator in some manner. Some security mechanisms that would provide integrity are digital signatures and public-key cryptography.
3. API Availability Availability is the assurance that the API systems and resources must be available to users promptly so productivity will not be affected. Most web apps are hosted in the cloud with integrations to several other cloud and on-premises services. Your API system must be designed in a way that ensures that it is always available to respond to calls and that once it begins execution on the call, it can complete the process without any security hitch.
This can be achieved through rate limits, high availability, fault tolerance, and recovery mechanisms put into place to ensure the continuity of the availability of resources. When APIs are implemented without any limits on the number of calls that API consumers can make, attackers can overwhelm system resources, thereby leading to a denial of service (DoS). You may also want to consider ways to scale the API across multiple servers to make it more resilient to DoS attacks and hand off the processing of messages to a message broker, which will hold the message till the API has completed its processing.
API Security Best Practices
1. Build API Security into SDLC One of the best ways of developing comprehensive API security is to build it into your software development lifecycle (SDLC) from planning through development, testing, staging, and production. Using ad hoc API security toolsets and rules will almost certainly lead to gaps in security and exposure to unnecessary risks. This means adhering to secure coding practices from the onset. OWASP provides a technology-agnostic document that defines a set of general software security coding practices in a checklist format that can be integrated into your software development lifecycle. Implementation of these practices will mitigate most common application vulnerabilities, including API vulnerabilities.
2. Regularly Assess Vulnerabilities Vulnerabilities are among the common security issues that plague software. To strengthen your defenses against threats, you’ll need to regularly find and fix vulnerabilities in your API. Pay attention to the OWASP API Top 10 as it offers a useful overview of common API vulnerabilities. Vulnerability assessment and security testing provide a way for providers to identify where their API is vulnerable to take the necessary corrective action to fix the gaps.
A growing number of providers are adopting security testing measures as a way to ensure that their critical applications and infrastructure are shielded from security breaches. The more extensive an organization’s security testing approaches are, the better its overall security posture. Standard security testing techniques can be utilized to test and detect API and web application vulnerabilities.
3. Implement Access Control Measures Access control enables organizations to manage who is authorized to access API data and resources. One of the key elements of access control is authentication and authorization. There are several methods to implement authentication and authorization:
- Basic authentication— where a user needs to provide a user ID and password
- API key-based authentication—where a user needs a unique identifier configured for each API.
- Delegated authentication—where authentication and authorization are delegated to third-party Identity Providers (IdP).
OpenID and Auth0 are commonly used delegation protocols to manage authentication and authorizations. It is a token-based authentication framework that allows third-party services to access information without exposing user credentials. The consumer doesn’t input their credentials but instead gives a token provided by the third-party server. It protects the consumer as they don’t disclose their credentials, and the API provider doesn’t need to care about protecting authorization data, as it only receives tokens.
4. Adopt the Principle of Least Privilege The principle of least privilege is the idea that a user, program, or process should have only the bare minimum privileges which are essential to perform its intended function. This means that API users must have only the permissions for actions that they’re authorized to carry out and nothing more than that. The permissions can be expanded as necessary but should also be revoked when they are no longer in use. Consider separating access into different roles, and hiding sensitive information in all your interfaces. Display only the least possible information in the error messages. The less information you share via APIs, the smaller your attack surface and API security risks.
5. Use Encryption Encryption conceals information by altering it so that it appears to be random data. This makes it unintelligible to unauthorized parties. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. Encryption is an essential strategy for API security because it helps to secure the content being sent and received via the API. Encryption protocols such as TLS encrypt data in transit and make it much more difficult for sensitive API data to end up in the wrong hands.
6. Monitor and Log Relevant Data It is best practice to keep an eye on the events and activities going on on your API, log relevant information on the server, and keep that history as long as it is reasonable. In the event of a breach or compromise, you will be able to pull up those logs and audit them to find anomalies. This also helps you to meet compliance requirements. There are lots of server and application monitoring tools with dashboards to track your API consumption. Consider deploying one of those tools in your environment for efficient logging.
7. Validate Input Parameters It is a good idea to check, filter, and validate user inputs to your server, especially if they are significantly large, before accepting them. This will help you to determine if the parameters are safe and minimize your risk of exposure. JSON and XML schema validation are the two most widely used tools to find out whether or not the parameters are safe. Schema validation checks that JSON or XML messages conform to the structure or format expected by the Web Service by validating those requests against JSON or XML Schemas. JSON schema validation, for example, asserts constraints on the structure of instance data. Validating parameters also helps to minimize the risk of SQL and JSON injection attacks.
8. Use API Gateway An API gateway is a tool that sits between a client and a collection of backend services. It acts as a reverse proxy to accept all API calls, aggregate the various services required to fulfill them and return the appropriate result. The use of API gateway tools such as AWS API Gateway, Azure API Management, Mulesoft, and Akamai has become standard practice for most providers. APIs that are well managed are less vulnerable to security risks and make it easy for developers to create, publish, maintain, monitor, and secure APIs at any scale. In addition, API Management tools help you make sense of your API data to gain better insight and competitive advantage.
9. Implement API Throttling and Rate Limiting Throttling and rate limiting is a strategy for limiting network traffic. It blocks or puts a cap on how often users, bots, or applications that are abusing a web property can repeat such action within a certain timeframe. for instance, trying to log in to an account. Throttling is enforced on the server-side while rate limiting is enforced on the client-side. Throttling and rate-limiting can help protect against API overuse, reduce strain on web servers, and stop certain kinds of malicious bot activity such as brute force attacks, DoS/DDoS attacks, and web scraping.

10. Use API Firewall API Firewall is a lightweight micro-firewall that acts as the security gateway and the single point of entry and exit for all API calls. API firewalls are designed to protect your API endpoints in cloud-native environments. It is best practice to deploy your API firewall in a DMZ to prevent direct attacks and filter traffic before forwarding them to your trusted network.
Mitigating API Threats with Edge Services
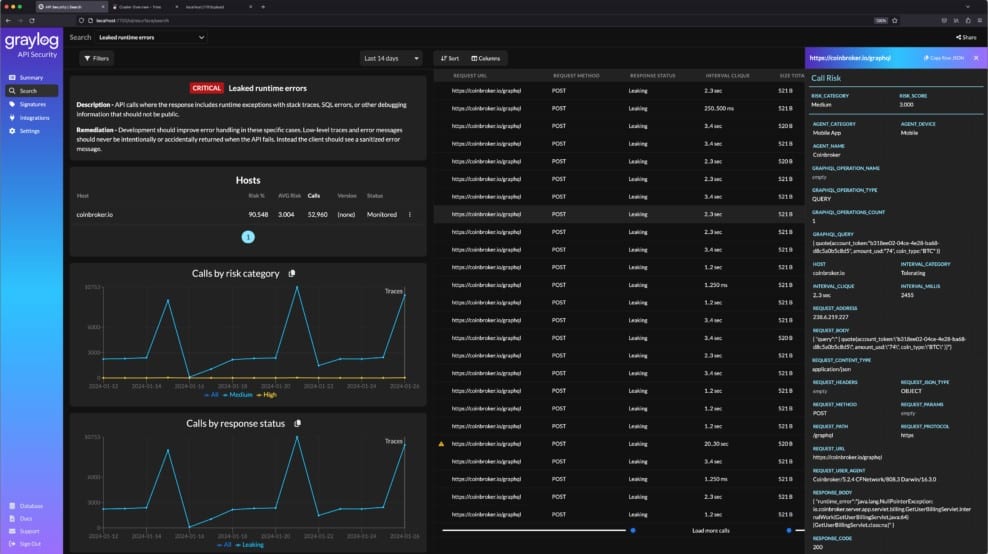
Graylog API Security EDITOR’S CHOICE
Graylog API Security is a live security monitoring service for APIs. Those APIs could be developed and hosted in house or run on a remote platform under the management of another company. The tool starts with a discovery routine that scans your own software or Web applications and drills through them, following the APIs that they integrate.
After documenting your APIs, the tool implements continuous monitoring. This monitoring takes two forms. The first is a vulnerability scanner that operates as a dynamic application security testing (DAST) service by exercising each API with a range of inputs, looking for boundary conditions and points of failure. This maps the vulnerabilities of your APIs. If you don’t own those units, there isn’t much you can do about the discovered weaknesses other than put in a call to the provider.
Key Features:
- API discovery: Drills through your known applications to discover and document their APIs
- Application inventory list: Keeps a record of each API
- Vulnerability scanning: Exercises each API to test for security weaknesses
- Constant activity monitoring: Records and assesses the actions of users
- Automated response: Shuts down suspicious activity
If you can’t get the vulnerabilities fixed, you will have to make the decision over whether to ditch the APIs or proceed with caution. Using internet-delivered services that are known to have security weaknesses seems to be a stupid decision. However, practical considerations sometimes mean that the ideal solution isn’t always possible. Companies could decide to proceed as is while a replacement for the vulnerable API is under development.
Fortunately, the second strand of security monitoring offered by the Graylog API Security package will help. It provides constant activity monitoring looking for attempts to trigger the weakness that the API scanner detected. While this isn’t exactly virtual patching, it is a form of protection that makes up for the unavoidable weakness that you know about. The API Security service will automatically cut off any connection that starts to display probing and malicious behavior.
The API discovery and vulnerability assessments reoccur continuously. This is because the code behind the API could change without any notification and these changes might resolve a discovered weakness or create a new one.
Pros:
- Continuous retesting: Rechecks APIs for vulnerabilities to spot fixes or new weaknesses
- Security logs: Stores records of monitoring efforts
- Activity logging: Records outsider actions on the APIs
- Preventative solution: Find and fix weaknesses or find and shield them
- Multi-platform: Host the software on the cloud or on one of your endpoints
Cons:
- Not a SaaS package: You need to budget for hosting space for the software and its logs
The Graylog API Security system is a software package that you have to host yourself. Its regular environment is on cloud platforms, such as AWS, Azure, GCP, and IBM Cloud. You can install on one of your own endpoints over the MicroK8s hypervisor. This will run on Windows, macOS, or Linux. The minimum plan for Graylog API Security monitors two nodes. You can opt for the Free edition, which is limited to monitoring one node.
Even if you know that you aren’t going to stick with the Free edition, that version is available as a free trial opportunity for the potential buyers of the full version.
EDITOR'S CHOICE
Graylog API Security is our top pick for an API Security system because it provides both preventative scanning to discover weaknesses and live activity monitoring to spot connections that look like they are going to try to exploit those weaknesses. Automated responses in the package nip malicious activities in the bud before they get a chance to discover that API security loophole or use prior knowledge to head straight for it. The discoveries of the scanner will help you to negotiate with the provider of the API to get a fix or provide a bug alert for an API that you developed in house and need to recode.
Download: 1 node and 16GB of local rolling storage FREE Access
Official Site: https://go2.graylog.org/api-security-free
OS: MicroK8s, AWS, Azure, GCP, or IBM Cloud
Indusface AppTrana
An alternative API firewall deployment strategy lies with edge services. By pre-filtering all traffic before it gets anywhere near your network, these cloud-based proxy systems block the overwhelming traffic flood strategies of DDoS attacks, freeing up your servers to deal with genuine traffic. An example of such an edge service package can be found in Indusface AppTrana.
This Web application firewall protects APIs as well as websites. It blocks DDoS attacks and scans packet contents for malicious activity. Using an edge service, such as Indusface keeps malicious traffic away from your APIs. You can start with a free trial.