Today’s network infrastructure has become very fluid, extending to the cloud and several dispersed devices and users. This has widened the attack surface and created opportunities for cyberattacks. It’s obvious that the same factors that have driven growth, have also created the conditions for security failure. The traditional approach to security makes less sense in such highly diverse and distributed environments and with increasing regulatory mandates. There’s therefore a need for a responsive security approach to address these modern challenges.
The IBM X-Force is well-positioned to help organizations deal with these modern security challenges with an integrated security program to protect organizations from global threats. Organizations can leverage IBM X-Force expertise to prevent, detect, respond, and recover from security incidents so that they can focus on their core business priorities. X-Force provides offensive and defensive security services that are underpinned by threat research, intelligence, and remediation services along with a large pool of security experts made up of ethical hackers, researchers, and analysts, all of whom can bring a unique perspective to building and refining your security programs.
The X-Force services are grouped into three categories: X-Force Red, X-Force Incident Response (IR), and X-Force Threat Intelligence. Through offensive security services, the X-Force Red team finds security vulnerabilities exposing your most important assets. Through incident preparedness, detection and response, the X-Force IR team knows where threat actors may hide and how to stop them. X-Force researchers and analysts collect and translate threat data into actionable intelligence for managing risk.
IBM X-Force Red
X-Force Red is a global team of ethical hackers that specializes in uncovering security vulnerabilities that attackers may want to exploit. The team’s offensive security services, which include penetration testing, vulnerability management, adversary simulation, and the X-Force Red Portal platform help identify and remediate security flaws within your cloud and on-premises network environments.
X-Force Red Penetration Testing: Penetration testing helps to find and fix high-risk vulnerabilities in your applications and network that could be exploited by attackers to undermine security. The X-Force Penetration testing covers the following core areas:
- Application testing Provides manual penetration testing, source code review, binary analysis, and vulnerability assessments for your mobile, web, IoT, and back-end applications.
- Network testing Helps to identify vulnerabilities that may lead to network exploitation. X-Force Red network testing capabilities include test scoping, network reconnaissance, research, network testing and exploitation, reporting, and recommendations.
- Hardware testing Helps to find and fix hidden vulnerabilities exposing your hardware and connected infrastructure to potential attackers.
- Social engineering X-Force Red engagements put your people to the test through phishing, vishing, and physical social engineering exercises to identify the weakest security link among your employees. This involves distributing emails with malicious links and attachments to see who opens them, calling employees to trick them into divulging sensitive information over the phone, and using pretexts, disguises, and other techniques to physically enter secure areas.
Other specialty penetration testing services include cloud platform testing, IoT device testing, industrial control systems testing, ATM security, and blockchain platform testing.
Vulnerability Management: X-Force Red Vulnerability Management Services identifies ranks, and helps facilitate the remediation of vulnerabilities. The team automates the vulnerability ranking process using a proprietary, patent-pending algorithm. The X-Force Red Vulnerability Management Services capabilities cover the following areas:
- Vulnerability scanning Provides deployment, support, and premium scanning services.
- Vulnerability data validation Validates identified vulnerabilities that can be overlooked, such as input errors when data comes from untrusted sources.
- Vulnerability prioritization Automated ranking engine prioritizes findings based on weaponized exploits and key risk factors such as asset value and exposure.
- Remediation management Helps to facilitate the end-to-end vulnerability remediation process.
- Vulnerability assessments X-Force Red team can provide vulnerability management research and findings to your executive team for action.
Adversary Simulation: X-Force Red Adversary Simulation services use simulated attacks to identify and fix gaps in people. processes, and technology. This may involve assessing the effectiveness of technical controls or business processes. X-Force Red Adversary Simulation services include the following four categories:
- Red teaming Evaluates your security operations detection, response, and defense capabilities, while focusing on major business impact-driven scenarios
- Threat intelligence-based testing A testing process that uses threat scenarios obtained from Threat Intelligence (TTI) reports from external providers, with a narrow focus on specific threat actors and Tactics, Techniques, and Procedures (TTPs).
- Purple teaming A collaborative testing process that aims to validate manual and automated detections.
- Control tuning and testing A testing process that also aims to verify automated detections in your security controls against MITRE ATT&CK and TTPs.
IBM X-Force IR
A security breach can result in unauthorized access to business applications and confidential data as well as operational disruptions, and reputation damage. But, a tried and tested incident response strategy can speed recovery from unexpected security incidents and breaches. Having a responsive incident response team on standby can reduce your organization’s risk of prolonged downtime, minimize the impact of an attack, and help facilitate faster recovery.
The IBM Security X-Force Incident Response provides a subscription-based retainer service that gives organizations access to a team of experts trained to help you effectively respond to threats. This service enables security teams to gain visibility into the threats landscape and minimize the impact of a breach with faster response and recovery times. Organizations can choose from a variety of incident response service offerings designed to meet their most pressing business and security needs:
- Incident response and threat intelligence services Provides organizations with X-Force global intelligence expertise and skills to proactively manage and respond to security threats.
- Offensive security services Provides organizations with offensive security experts such as ethical hackers and penetration testers to help to uncover flaws and expedite remediation efforts. The services include penetration testing, vulnerability management, adversary simulation, and a host of others.
- Security command centers Provides hands-on simulations exercises and realistic breach scenarios to help develop your team’s capacity in incident response.
- Mobile incident training A fully operational mobile service housed in a unique tractor-trailer that empowers your incident response team to deal with security incidents with confidence and speed.
- Incident Response Emergency Support A 24×7 global incident response support and investigation services.
- Cyber Crisis Management Services Prepares your business team to respond to crisis-level attacks through plan and playbook development and tabletop simulated exercises.
- Ransomware Readiness Assessment Services Enables security teams to identify and fix gaps in their response plans to ransomware attacks.
- Incident response and threat intelligence program assessment An assessment service that reviews your existing incident response and threat intelligence program to deliver a comprehensive Incident response and threat intelligence roadmap containing priorities for improvement.
IBM X-Force Threat Intelligence
Cyber threat intelligence is a compilation of information an organization uses to understand the threats that have, will, or are currently targeting the organization to mitigate them. Threat data is organized, refined, and augmented to make it actionable and allow your cybersecurity team to prepare, prevent, and identify cyber threats looking to take advantage of valuable and vulnerable resources. It also provides information to identify and understand their adversary, create a response plan, and allocate resources strategically. Threat intelligence can be categorized into tactical, operational, and strategic intelligence that can be used to drive low and high-level organizational strategy.
IBM Security X-Force Threat Intelligence solution provides organizations with actionable cyber threat data from a variety of sources such as technical intelligence, device log files, open-source intelligence, social media intelligence, human intelligence, dark web intelligence, forensically acquired data, or intelligence from the internet traffic. The solution is designed to simplify your intelligence management efforts while improving detection and response with the ability to share the information with your organization, industry, and communities. IBM Security X-Force Threat Intelligence delivers the following threat intelligence offerings to help improve your cybersecurity posture:
- Premier Threat Intelligence Premier Threat Intelligence provides organizations access to the latest threat intelligence information via IBM curated, human and machine-readable threat intelligence extracted from real-time IBM security operations, investigations, and research to help improve mitigation capabilities.
- Enterprise Intelligence Management Enterprise Intelligence service provides the tactical structure to automate and optimize the exchange of threat data and fuse intelligence efficiently with your existing security systems.
- The X-Force Exchange and Threat Intelligence Insights This service helps organizations leverage the latest and historical threat information worldwide to drive their security decision-making.
- Strategic Threat and Cyber Threat Intelligence Assessments Provides an understanding of threat actors and their techniques and how they may accomplish their objectives to ensure effective security decision-making.
Other threat intelligence offerings include IBM Advanced Threat Protection Feed, IBM X-Force Exchange API, Dark Web Analysis and Malware Reverse Engineering, Premium Threat Intelligence Reports, IBM X-Force Exchange, among others.
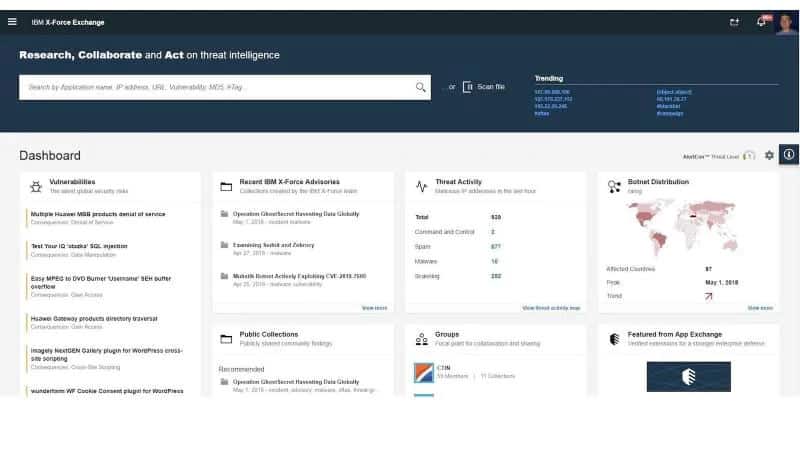
The IBM X-Force Exchange is a cloud-based threat intelligence platform that gives organizations access to actionable and shareable threat intelligence to help them stay ahead of emerging threats. It is supported by human and machine-generated intelligence including vulnerabilities, malware, malware families, IP reputation, URL reputation, Web applications, DNS, Whois information, malicious domains, and higher-order intelligence. With this platform, organizations can research the latest global security threats, aggregate actionable intelligence, consult and collaborate with experts and peers.
Leading IBM X-Force Alternatives
- ManageEngine Vulnerability Manager Plus This is a bundle of vulnerability detection and remediation services. It is able to examine systems running Windows, macOS, and Linux, assessing their software inventories for unauthorized and out-of-date packages. The bundle includes a patch manager to update OSs and software. It also produces system hardening measures to close open ports and re-align system configurations to block entry points for hackers and malware. This software runs on Windows Server and there is a free version that covers 25 computers. ManageEngine offers the paid versions of Vulnerability Manager Plus for a 30-day free trial.
- CrowdStrike Falcon Intelligence Designed for organizations that want to boost their response efforts to cybersecurity incidents and alerts but lack the expertise to do so. CrowdStrike Falcon Intelligence delivers the critical intelligence organizations need to turn the tables on attackers by gaining knowledge about them before they attack. CrowdStrike also provides security teams with one unified detection and response tool known as Falcon XDR. You can register for a free trial of Falcon Intelligence is available on request.
- Recorded Future Intelligence Platform Specializes in the collection, processing, analysis, and dissemination of threat intelligence on its intelligence platform. The Recorded Future Intelligence Platform applies machine learning techniques to collect and analyze data from the open web, dark web, and technical sources to deliver insights for proactive risk mitigation. A free online demo is available on request.
- Kaspersky Threat Intelligence Services Gives you access to technical, tactical, operational, and strategic threat intelligence you need to mitigate cyberthreats. The Kaspersky Threat Intelligence portfolio includes Threat Data Feeds, CyberTrace (a Threat Intelligence Platform), Threat Lookup, Threat Analysis (Cloud Sandbox and Cloud Threat Attribution Engine), a range of Threat Intelligence Reporting options, and services providing threat intelligence expertise on demand. A free online demo is available on request.
- McAfee Threat Intelligence Exchange McAfee Threat Intelligence Exchange (TIE) provides a framework personalized to your environment where your security products collectively pinpoint threats and act as a unified threat defense system that enables adaptive threat detection and response. McAfee combines local intelligence from security solutions across your organization with global threat data to create an effective intelligence exchange platform that can be shared with your security ecosystem.
- Cisco Talos One of the largest and most trusted providers of security research data that provides intelligence information used by Cisco security products and services to take action. Cisco Talos leverages the sheer size and breadth of the Cisco Security portfolio and the telemetry data from Cisco’s customers and products to provide actionable intelligence.
- SentinelOne Singularity Signal A data-driven threat intelligence platform that harnesses data at scale to predict attackers’ behaviors and help you stay ahead of emerging threats. It combines AI & machine learning models with human-enriched intelligence, and the Singularity Marketplace and Threat Intel API to give you visibility into the evolving threat landscape. SentinelOne also provides an autonomous detection and response tool known as Singularity XDR. A free online demo is available on request.
- Group-IB Threat Intelligence & Attribution Provides organizations with insight into the threat landscape and threat trends and anticipates attacks with thorough knowledge of past, present, and future attacks. Group-IB empowers business executives to make data-driven strategic decisions with tailored and reliable information. A free online demo is available on request.
- Symantec DeepSight Intelligence A cloud-based cyber threat intelligence platform that provides access to cyber intelligence. DeepSight Intelligence leverages data collected via Symantec endpoints and other security products which is then analyzed to provide attribution and other intelligence information.
- McAfee MVISION Endpoint Security suite delivers centrally managed endpoint protection with integrated capabilities such as endpoint detection and response (EDR), extended detection and response (XDR), machine learning behavioral analysis, exploit prevention, firewall to protect your Windows, Mac, and Linux systems. McAfee is also recognized as a Leader in the 2021 Gartner Magic Quadrant for Endpoint Protection Platforms. A free online demo and a free trial are available on request.
- Sophos Intercept X One of the industry-leading endpoint security solutions that combine EDR, extended detection and response (XDR), managed threat response (MTR), anti-exploit, anti-ransomware, and deep learning AI with real-time threat intelligence from SophosLabs to prevent, detect and remediate threats before they impact your systems. Sophos is recognized as a Leader in the 2021 Gartner Magic Quadrant for Endpoint Protection Platforms. A free trial is available on request.



