Malvertising is a method cybercriminals utilize to perform espionage, make money, or steal user data. In this article, we’ll take a deeper dive into how malvertising attacks are performed and the consequences for the end-user. We’ll then discuss some key statistics of how cybercriminals utilize these types of attacks. After consuming the information in this article, we hope to open your eyes to the associated malvertising threats and help you avoid falling victim to such an attack.
What is malvertising?
Malvertising (or malicious advertising) often involves an attacker paying for or hacking into a display ad campaign. Cybercriminals host malicious ads on an infected website, and these ads typically contain some form of malicious code. Due to the techniques used, unsuspecting users may not necessarily need to click the ad to fall victim to a malware infection.
As users surf the web and visit sites with ads that are infected with malware, they may unknowingly download malware onto their device. Other tactics involve sneaky prompts as a way of getting the user to click the ad.
Attacks can vary between cybercriminals, with some downloading an infected file to your device. In contrast, others pass you through a series of website redirects to get the malicious code where the attacker wants it to be.
Malvertising statistics
1. Malvertising attacks have evolved with technology
Malvertising attacks have become more sophisticated and widespread. A report by AdSecure highlights significant increases in various malvertising techniques in the first half of 2023 alone, with phishing URLs leading the charge with a 140.7% increase. These phishing attempts are not only more frequent but also more deceptive, using emotional manipulation to trick users into revealing personal information.
The rise in permission-camera attacks by 106% underscores a disturbing trend toward invading user privacy through their devices. These statistics highlight the ever-present and evolving threat of malvertising in our digital lives.
2. Malvertising cost forecasts are difficult to predict
A 2019 digital ad fraud report from eMarketer estimates that Malvertising costs are from $6.5 billion and as high as $19 billion, pointing to the difficulty in calculating the actual range of malvertising.
3. Device farming is the most prevelant for shopping app fraud
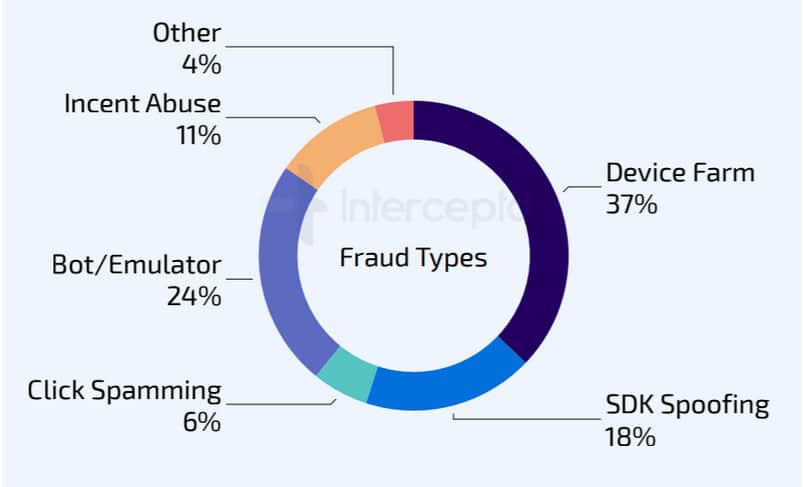
According to ad fraud research carried out by the Interceptd, 30% of app fraud in the shopping category is performed using device farming. This is closely followed by app fraud performed using bots and emulators.
4. Malvertising costs could skyrocket by 2025
Cyber Security Ventures 2019 cybercrime report estimates damages caused by cybercrimes such as malvertising are forecast to cost the world $10.5 trillion by the end of 2025.
5. Malvertising generates over $1 billion for piracy websites
A report by Digital Citizens Alliance on advertiser-supported piracy found that piracy sites make $1.3 billion due to malvertising.
6. Malicious code ad injection is on the rise
Security Gladiators reports that on average, of every 100 ads that are published, at least 1 contains malicious code.
7. Cyber attacks are unknowingly caused by staff
Whether intentional or due to human error, employees remain the root cause of successful cyber security attacks, Accenture’s 2019 the cost of security report shows.
8. The most popular malvertising exploit is the Angler Exploit Kit
As reported by CI Security, The Angler Exploit kit uses several advanced evasion techniques to ensure it remains undetected by malware scanners on a campaign level and always-on software that searches for infections. For this reason, it has become one of the most popular malvertising exploits used in 2021.
9. Gift card scams target iPhone users in 2020
A gift card scam was used to hijack 300 million iPhone browser sessions in 2018. This shows how malvertising attacks are becoming more sophisticated.
10. Ad impressions become more dangerous in 2021
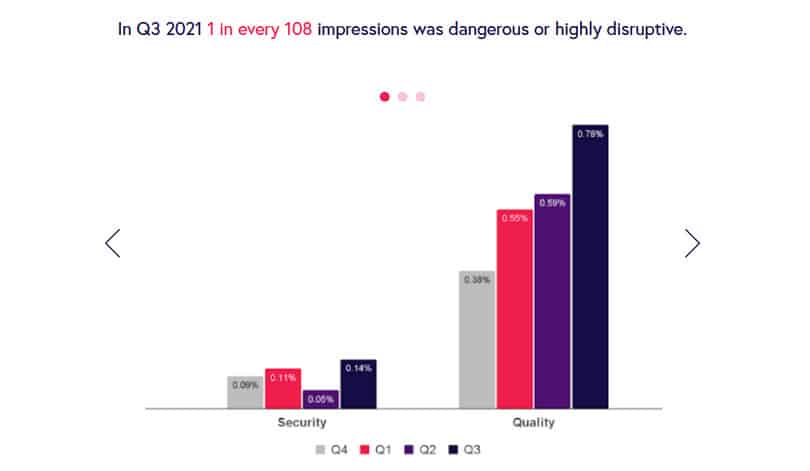
A report by Confiant found that in Q3 of 2021, 1 of every 108 ad impressions was highly disruptive or dangerous.
11. The diversity of malvertising mobile attack types expands
Malvertising attacks on mobile devices are diversifying, with attackers employing various methods to exploit vulnerabilities. AdSecure’s analysis for Q2 2023 reveals a notable increase in pop-up ads (+82.5%) and scareware (+50%), alongside more covert tactics like auto-downloads (+31.9%). This variation in attack methods indicates a strategic shift by malvertisers to use multiple avenues for infection, complicating defense mechanisms for users and security systems.
The prevalence of user experience violations, including deceptive landing pages and unauthorized permission requests, further complicates the mobile browsing experience, highlighting the need for vigilance and advanced security solutions.
12. Other redirects were the highest reported desktop malvertising attack type
In contrast, Clean.io found that the most significant attack type on desktop came from “other redirects.” Client-side injection came second.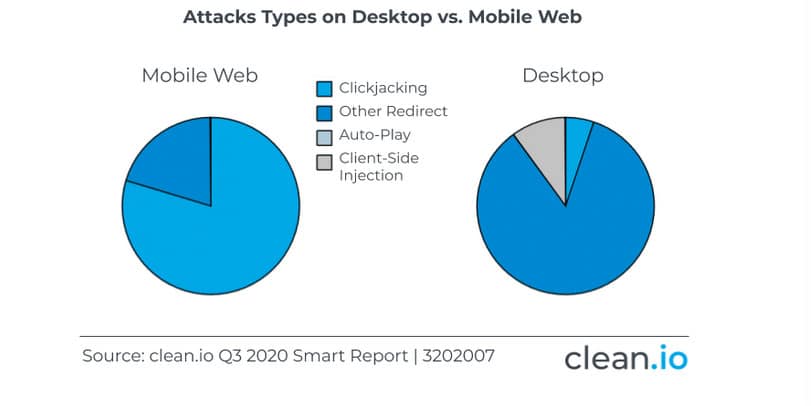
13. Malvertising and cybercrime costs $500 billion per month
Safety Detectives’ malvertising report showed that the global cost of malware was $500 billion per year in 2015, but in 2021 that figure cost an average of $500 billion per month.
14. Cybercriminals are motivated by financial gain

The report continued, showing that 76% of attackers are motivated by the ability to obtain cash from victims of crimes such as malvertising.
How Malvertising Is Distributed
Malicious adverts can be displayed in several ways before infecting an unsuspecting user. These include the following:
- Banner ads lure users with content such as tempting 50% off offers.
- Pop-ups are random windows that appear, usually when you visit a website or try to leave.
- Animated ads may come in the form of a gif or an MP4 file, and if the attacker is sophisticated enough, they can inject malicious code into java, hiding behind what appears to be a harmless ad.
- iFrames are embedded with HTML code, allowing a hacker to insert an inline frame into any part of a web page. Users may accidentally click the iFrame, and before they know it, their device is infected with malware.
- Video ads present an attractive way to show content you’re interested in, such as a movie you’ve been looking at elsewhere. You click to play the video, and the attacker enters your system without knowing about it.
- Text-based malvertising involves the attacker sending a message via WhatsApp or Telegram, for example, containing a message for you to forward to your friends, often including a malicious link. You send to your friends, and the hacking opportunities double.
Types of Malvertising Infections
- Ransomware infections consist of a device being compromised, allowing hackers to search through and lockdown any files and folders contained on the target system. The attacker will typically ask the user to pay a ransom sum of money to access their files and folders (which is never guaranteed).
- As the name suggests, spyware can spy on your device by logging keystrokes, stealing passwords, and accessing your webcam and microphone for extortion purposes.
- Adware can install adverts on your device, and each time you click (whether intentional or by accident), the cybercriminal makes money.
- Trojans act as a way for attackers to hijack a system, allowing them to steal data, download more malware, tamper with files and take control of the target device.
- Cryptojacking installs crypto mining software on a user’s device to use computing resources to mine cryptocurrency such as Bitcoin.
How to Avoid a Malvertising Attack
Malvertising attacks are changing the landscape for cybercriminals, as an attack may not require any user input whatsoever. Just visiting a website infected with malicious ads is often enough to infect an end-user. Unfortunately, unlike malware that can be defended against using anti-malware software and other prevention methods, malvertising includes the ad network, the publisher, and end-users seeing the display ads.
Ad Network detection
At a base level, ad networks should scan ads before passing them through the network to the website hosting the ad. If malicious code is detected, the ad network should prevent the advertisement from continuing through to the publishing stages of the campaign.
Ad networks can scan ads before running them to look for specific behavioral patterns typically seen with malware variants and can also check the database signatures for malware.
Identifying malicious ads at the publisher level
Whether the ad is being hosted on Google, Facebook (which have their own ad networks), or a blog, these are known as the ad publishers, and it is up to the host to display the ad, which will then appear to visitors.
For example, a site owner hosting a blog might set up an ad on an ad network which would then produce a string of code to place in the appropriate place of the website. Before putting this code on the site, some tools can scan the ads to check whether it’s been compromised before publishing them on a live site.
Options for end-users
Although falling victim to a malvertising attack is incredibly easy, there are some ways you can give yourself a better chance of avoiding getting infected.
Malware scanning tools included with software such as NordVPN‘s CyberSec feature scan websites for malicious code and warn you when you are about to enter an unsafe website. Although it’s not guaranteed to detect a malvertising attempt, there’s a chance it’ll identify something.
If you get infected due to a malvertising attack, you can prevent harm by using desktop malware protection to detect and remove the infection. Although you can use an antivirus, we’d recommend keeping antivirus running in the background on your device to check for real-time infections constantly.
An additional option is to install ad-blocking software for your browser. We’d recommend Total AdBlock, which will continuously scan for advertisements as you browse the web, blocking any pop-ups, video, or banner ads along the way. If the adblocker detects ads (infected ads or legit versions of them), it’ll attempt to stop them from appearing. Even if you visit a compromised website, there’s a chance (although not guaranteed) that the adblocker will block the ad to prevent infection.

