Sextortion is extortion involving material of a sexual nature, but it can take various forms. It’s a problem in many parts of the globe and affects a broad range of targets, including males, females, minors, and adults. Aside from the psychological and sometimes physical damage it imparts, a major problem with this crime is that many cases go unreported because victims are too embarrassed.
With the popularity of social media, messaging apps, and online dating, the exchange of explicit material online is far more commonplace. Plus, webcams make it very simple for people to record themselves (or be secretly recorded). With the prevalence of sextortion crimes, it’s important that everyone is aware of what to look out for.
In this post, we explain what sextortion is, and how it takes place, including describing some real-life examples. We’ll then provide tips to help you avoid becoming the next victim of sextortion.
What is sextortion and who are the targets?
The FBI defines sextortion as “a serious crime that occurs when someone threatens to distribute your private and sensitive material if you don’t provide them with images of a sexual nature, sexual favors, or money.”
Typically, the perpetrator has (or purports to have) some compromising images or videos or the victim. They threaten to publish them online or share them with friends, family members, or colleagues if the victim doesn’t provide more material, engage in sexual acts, or hand over money.
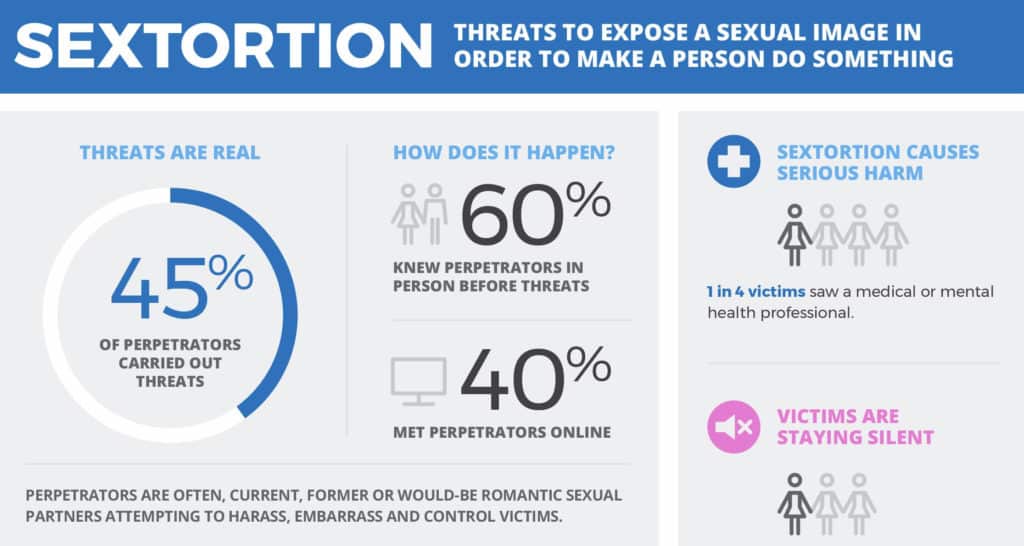
Unfortunately, these threats are far from idle. An infographic, released by Thorn, reveals that an alarming 45% of perpetrators actually carried out threats.
Although, historically, women were more likely to be the victims in adult sextortion, reports suggest that there are now more male victims of the crime.
According to a study published in the Victims & Offenders journal, men were twice as likely as women to fall victim to sextortion between 2020 and 2021 — i.e. during the COVID pandemic. While tempting to disregard this as an anomaly, there are other figures that suggest it applies more generally.
Figures from Australia’s E-Safety Commission show that, while victims of revenge porn are most often female, victims of sextortion tend to be male. In 2022, almost 60 per cent of reports to the commission were made by male victims.
In the US, the FBI issued a warning to parents and caregivers about the increase in adults posing as girls to coerce young boys into sharing sexual images with them. These are subsequently used to blackmail the boys, who are typically aged between 14 and 17 years old.
The UK’s revenge porn helpline reported in 2021 that 88% of sextortion cases involved male victims. Of these, 80% of the perpetrators were part of a criminal gang.
These operate in the Philippines, Romania, Morocco, and other parts of the globe, targeting men under the guise of women looking for a sexual relationship. The gangs even set up call center-style offices from which to operate. Other sextortion schemes are less targeted and are more like generic phishing schemes.
Sextortion is a growing concern
In the first six months of 2023, the UK’s Internet Watch Foundation (IWF) reported receiving more reports involving sextortion than in the whole of 2022.
Similarly, Lauren Coffren, the executive director of the US-based National Center for Missing and Exploited Children, said that the number of sextortion reports surpassed 2022 numbers midway through 2023.
Sextortion is thought to be rising in popularity among criminals due to the attractive nature of the crime. It’s very likely that targets will pay up instead of facing the embarrassing repercussions of having their private images and videos shared with friends, family members, colleagues, and the general public.
The ease with which victims fall prey to these schemes is a big concern for companies and governments too. Corporates employees could easily be swayed into handing over employee credentials and other information for use in future crimes.
Military personnel are prime targets because they’re more likely to try and form online relationships while away from home. Furthermore, their conduct is closely monitored so they’re more likely to comply with demands. This is especially troubling when you consider they could provide a back door to classified information and even compromise national security.
The increase in suicide cases related to sextortion highlights the very serious nature of these crimes. These criminals are ruining and ending lives, so the social impact is immense.
Methods of sextortion
Sextortion can happen through a variety of methods, but here are a few general scenarios:
Email phishing schemes
An email arrives in your inbox stating that the sender has one of your passwords (which they will include in the email). They threaten to publish your intimate photos or videos unless you send money or nude photos, or perform sexual acts. Many of these scams are based on password harvesting, and unless you still have sensitive media on an old site, this could be a bluff.
Social media
A sextortion campaign might start with a seemingly harmless encounter over social media or a dating site. Eventually, the perpetrator will coerce the victim into sending explicit images, getting naked on camera, or performing sexual acts while on camera. The resulting images and videos can then be held to ransom.
Related: How to protect your privacy on Facebook
Hacked accounts
If you’ve ever sent explicit images or videos via social media or a chat app, or have them stored on one of those platforms, someone could get their hands on them by hacking into your account. They could also use your account to share the images with friends, family members, and colleagues if you don’t comply with demands.
Hacked webcams
Some of the most creepy cases of sextortion involve malware being downloaded onto the victim’s device. Once there, it can allow a hacker to take control of cameras and microphones, and install keyloggers. This means someone could monitor your every move (in the vicinity of your computer). And through keyloggers, they can discover the credentials for all of your accounts. This might sound far-fetched, but it happens more often than you might think.
Related: How to secure your webcam
Real examples of sextortion
As if that’s not enough to make you more wary about your online (and offline) activities, here are some real life examples of sextortion cases.
Jordan John DeMay: Seventeen-year-old high school student, Jordan John DeMay, committed suicide after being extorted through Instagram with compromising pictures he had taken of himself. The perpetrators — alleged to be two Nigerian hackers — requested money in exchange for not sharing the images with the boy’s social media followers. Investigators from Michigan’s Marquette County Sheriff’s Office said the time between the threats and the teenager’s death was less than six hours.
Luis Mijangos: In 2010, Luis Mijangos pled guilty to computer hacking and wiretapping in a case that involved the sextortion of hundreds of women, including dozens of minors. He created his own malware which victims unknowingly downloaded, giving him control of their computers. Mijangos recorded videos of his targets undressing, taking a shower, and having sex, and threatened to share the videos if they didn’t send him more pornographic images and videos. He was eventually sentenced to six years in prison, but the effects of his crimes on his victims will no doubt last a lot longer than that.
Lucas Michael Chansler: This man terrorized almost 350 girls from the US, Canada, and the UK. He posed as various teenage boys and persuaded the girls to send nude images. He threatened to share these images with the girls’ friends if they didn’t send more, and followed through on some of those threats. Chansler was eventually sent to prison for 105 years.
Romanian gang: Irish teenager, Ronan Hughes, was tricked by a Romanian gang posing as a potential love interest “Emily Magee.” They persuaded him to send intimate images and then asked him to pay a ransom of €3,000 ($3,471). When he couldn’t pay, the images were shared online, prompting the 17-year old to commit suicide.
Filipino gang: A young UK man, named only as Simon, admitted feeling embarrassed when he was the victim of sextortion. He was duped into being recorded masturbating and a gang in the Philippines tried to extort him for £600 ($782). The gang had the contact details of his friends, family, and work colleagues, so he paid them part of the ransom.
Old passwords: A popular scam that is doing the rounds right now involves old passwords. These passwords may have been involved in data breaches years ago, so chances are that victims don’t even use them anymore. However, seeing your old password in an email could be enough to make you wonder if the sender does indeed have anything compromising. Fraudsters claim to have intimate images or videos and threaten to share them with contacts or post them online, although they are often bluffing and have nothing to reveal. Nonetheless, this is proving to be a very profitable tactic.
Celebrity Sextortion: In the UK, a well-known TV presenter, Dan Lobb, was extorted after he was secretly filmed masturbating. Rather than let it go, Dan decided to make a film, called Celebrity Sextortion, documenting his journey to find out how the tape was recorded in the first place. Other celebrities to have been involved in sextortion cases include Gene Simmons, John Stamos, and Cameron Diaz.
Anton Martynenko: This case impacted the lives of more than 150 boys, mainly in the US Midwest. Martynenko preyed on young male athletes by posing as attractive women on social media and persuading his victims to send nude images. He then threatened to publish the images online if they didn’t send more, and in some cases tried to get the boys to engage in sexual acts with him. Two of his victims are thought to have ended their own lives. He has been sentenced to 38 years in prison.
Justin Bieber poser: In 2017, Bryan Asrary was arrested on suspicion of sextorting a nine-year old girl by posing as popstar Justin Bieber. He reportedly admitted to the crime and implicated himself in several other similar cases.
How to avoid and deal with sextortion
It may sound simple to avoid finding yourself in one of these situations, but it’s surprising the number of people who accidentally get caught up in these schemes. This is especially true given the increased number of relationships that are forged through social media and online dating sites. Here are some tips to stay safe.
Have your wits about you
Although we all want to believe that true love exists, if a suitor seems too good to be true, chances are, it’s a scam. We’re not saying you need to take a completely cynical view of the online dating world, but you need to be savvy. Educate yourself about common scams and always try to think rationally about the encounters you’re having online.
Do some background checks
If you have any doubts, it doesn’t hurt to dig a little deeper to find out who you’re really talking to. Many scammers create fake profiles, a practice known as “catfishing,” to lure in their prey. There are websites such as Romance Scam and Scamdigger dedicated to calling out these fraudsters, but it’s so easy for scammers to set up new ones.
Some lazy criminals will keep using the same photo under multiple pseudonyms, and there are even tools you can use to check if an image has been used before. However, even if someone passes these checks, it doesn’t mean they’re legit.
Never send intimate videos or photos
This should go without saying, but you should always avoid sending intimate images or videos to anyone you don’t completely trust. But as they say, love is blind, and criminals can be extremely manipulative. Similarly, you should avoid keeping intimate photos or videos on your internet-connected devices. If you’re duped into downloading certain types of malware, you could be giving criminals full access to your machines.
Use strong passwords
Sextortion victims are often targeted after an account has been hacked. The criminal can use images or videos stored within the account, plus they can use the contacts if they follow through on their threats. It’s important to protect all of your accounts with strong passwords. This reduces the chance of a perpetrator guessing the password in a brute force attack.
Plus, you should always use a different password for every account. If you’ve been involved in a data breach, knowingly or unknowingly, your credentials could be doing the rounds on dark web marketplaces. All someone has to do is use the harvested credentials to try to log into popular platforms and hope for the best. If you use a different password for every account, they’ll be out of luck.
Don’t open attachments from people you don’t know
Most email platforms and messaging systems have pretty decent spam filters. However, there could be some emails that slip through the cracks. If you happen to receive a message from someone you don’t know, make sure you don’t open any attachments. This is an easy way for hackers to infect your computer with malware that could enable them to install keyloggers and even take control of your device.
In the same vein, you should avoid following links in emails unless you’re sure of where they’re coming from. These can lead to fake websites that prompt you to enter credentials that can then be used to hack into your real accounts.
Turn off or cover cameras when not in use
Hopefully, no one has control of your webcam or microphone, but it’s better to be safe than sorry. It’s always best to shut off or cover your camera and turn off your microphone when not in use, just in case someone can see what you’re doing.
If you’re concerned you may have malware installed on your computer, you could use a malware removal tool to get rid of it. It’s also prudent to use an antivirus software, although these aren’t guaranteed to detect and block all forms of malware.
Monitor your child’s online activity
As you can see from the examples above, victims are often minors. If you’re a parent, you clearly want to protect your child from the psychological and even physical harm that can result from sextortion. If your child uses the internet, then they are a potential target, so it’s important that they understand the risks.
Where appropriate, you should monitor their online activity, or at the very least keep an open discussion about this topic and take steps to help them protect their privacy online. Perhaps most importantly, you can let them know that they should tell you or another trusted adult if they become embroiled in a suspected case of sextortion.
Encrypt your devices
If you store any type of sensitive data on your device, whether they’re work documents or explicit images or videos, then you should definitely consider encrypting your device, or at least the files and folders in question. This means that if anyone were to get their hands on your PC, laptop, or mobile device, they wouldn’t be able to recover the encrypted information without your password (or PIN or similar lock).
Use a VPN
A Virtual Private Network (VPN) encrypts your internet traffic and tunnels it through an intermediary server. Encrypted traffic is unreadable to anyone who intercepts it. This means that if a hacker is spying on your internet traffic, such as in the case of a man-in-the-middle attack, they won’t be able to uncover any information.
Reporting sextortion
As mentioned, one of the huge issues with sextortion is that it’s an embarrassing topic, and probably not talked about as much as it should be. However, if you are asked to send explicit images or videos, or have become involved in a case of sextortion, it’s important to report it. Not only can law enforcement help you, but you can also help prevent the perpetrator from targeting more victims.
Call local police to reports these crimes, or if you are a minor who doesn’t feel comfortable calling the police, you can tell a parent or trusted adult. In the US, minors can also report sextortion to the National Center for Missing & Exploited Children’s CyberTipline. One more option, if you’re not ready to contact law enforcement or tell someone you know, is to contact the charity, Thorn, by texting “THORN” to 741741.
While it’s rare, if the perpetrator has control of your device or accounts, they may be able to read your online correspondence or monitor phone calls. As such, it may be best to use a “safe” phone — such as a home phone or someone else’s cell phone — to report such incidences.