The Federal Information Security Management Act or FISMA is a federal law passed in the United States that requires federal agencies to implement and maintain an information security strategy. FISMA was passed in 2002 to impose regulations on how federal agencies handle data.
What is FISMA?
FISMA (Federal Information Security Management Act) is a U.S. federal law enacted in 2002 to provide a comprehensive framework for securing government information systems. The purpose of FISMA is to ensure that federal agencies and contractors implement appropriate security measures. It aims to protect the confidentiality, integrity, and availability of information systems, especially those that handle sensitive or classified data.
FISMA is part of the Clinger-Cohen Act and was updated in 2014 by the Cybersecurity Enhancement Act to reflect the increasing importance of cybersecurity in the modern digital landscape. The law applies specifically to U.S. federal agencies, their contractors, and service providers.
The FISMA rules mandate that federal agencies establish and maintain an information security program. That should include developing security policies and performing risk assessments. The requirements demand the use of automated systems to ensure continuous monitoring and improvement of security practices.
The law sets clear guidelines for how agencies should assess and manage the risks to their information systems. One of the core requirements of FISMA is compliance with the standards and guidelines set by the National Institute of Standards and Technology (NIST), particularly NIST SP 800-53, which provides a catalog of security controls and practices.
FISMA also applies to contractors, vendors, and service providers that work with federal agencies, requiring them to meet the same security standards when handling or processing government data. This ensures that the security of federal information is maintained throughout the supply chain.
Though FISMA is a U.S.-specific law, its principles have broader international relevance, particularly in countries that work closely with the U.S. government. While FISMA itself is not directly applicable to countries outside the U.S., many international organizations and governments adopt similar frameworks based on the principles established by FISMA. These include countries that interact with the U.S. government or those that follow similar cybersecurity and data protection standards.
What is NIST SP 800-53?
The National Institute of Standards and Technology Special Publication 800-53, or NIST 800-53 is a set of industry standards from NIST that set guidelines on what federal agencies and contractors need to do to comply with FISMA. NIST SP 800-53 discusses the security controls under the act.
The NIST SP 800-53 Risk Management Framework sets out a systematic process for ensuring compliance. The framework begins with an organization categorizing systems, finding the ideal security controls, implementing them, and assessing the long-term effect. The process can be divided into six steps:
- Categorize/Create an Inventory of Information Systems
- Select applicable security controls
- Implement the security controls
- Assess the security controls
- Authorize the information systems
- Monitor the security controls
Who Needs to Follow FISMA?
Although FISMA originally applied to federal agencies the act has since been expanded to include state agencies implementing federal programs. Today, state agencies managing programs like Medicare, Medicaid, and student loans are expected to follow FISMA. In addition, private enterprises that manage government contracts, provide services, or receive grant money must also comply with the act.
FISMA often catches private enterprises off guard because they are unaware that contractual relationships make them fall under the remit of the law. Unfortunately, this is a mistake that can cause tremendous financial stress as a company faces the penalties of non-compliance.
What are the Penalties for Non-Compliance?
The penalties for failing to comply with FISMA are centered around losing government support. Institutions or companies that don’t meet the requirements will lose federal funding and be barred from future government contracts. For private enterprises that rely on government contracts being barred can be financially devastating.
The act imposes harsh penalties to ensure that federal agencies and relevant private organizations have adequate controls in place to protect the data that they hold. If you have a low FISMA score then there is a reasonable risk that you will leak sensitive information. Ensuring FISMA compliance will not only help to avoid penalties but keep your data safe as well.
How often is FISMA Compliance Assessed?
To ensure that federal agencies keep security controls updated, FISMA compliance is evaluated annually and reported to the OMB. The evaluation must be conducted independently by an external auditor or the agency Inspector General. Once the evaluation has been completed a report card will be made public to show those institutions that are protecting data.
FISMA Compliance Checklist
The requirements of FISMA are vast. Being FISMA compliant isn’t just a case of paint by numbers but a meticulous process, that’s customized for your company. To comply with the legislation an agency or contractor needs to go through an entire lifecycle of taking inventory of current systems, creating a custom security policy to protect those assets, and monitoring the risks over the long term.
The compliance lifecycle can be broken down into the following steps:
- Maintain information System Inventory
- Categorize Information Systems
- Maintain a System Security Plan
- Utilize Security Controls
- Conduct Risk Assessments
- Certification and Accreditation
- Continuous Monitoring
The intention behind the legislation is for you to pick security controls that are on par with the risks your organization faces, and to revise those controls periodically to make sure there aren’t any vulnerabilities that are being overlooked.
Step #1: Maintain Information System Inventory
The requirement to maintain an information system inventory dictates that federal agencies and contractors must keep an inventory of all the IT systems used within the organization. The inventory must include the following information: description, manufacturer, model number, date of purchase or lease when it was deployed when the hardware was last updated, a record of maintenance or repairs, a record of service, and disposition.
Step #2: Categorize Information Systems
The next requirement states that agencies should categorize information systems according to risk level. Risk categorization is used to identify those systems that hold the most sensitive data so that the agency can then implement the necessary security measures to protect this data from being compromised.
The Federal Information Processing Standards or FIPS 199 is the standard that determines the risk category of IT systems. FIPS 199 categorizes the risk of a system in three ways: confidentiality, integrity, and availability. Each of these measures is then rated as low, medium, or high.
Step #3: Maintain a System Security Plan
Under the legislation, organizations must create a system security plan detailing security controls and policies. The plan must include a Plan of Action and Milestones which should be reviewed periodically. In the document, there must be a range of security controls, milestones, and timetables for implementing new controls. It is critical that the document is regularly updated.
Step #4: Utilize Security Controls
Once the security plan has been created it is time to start implementing security controls. NIST SP 800-53 acts as a catalog of security controls that you can use to protect your systems. The requirements listed in NIST SP 800-53 apply to “all components of an information system that process, store, or transmit federal information.”
There is a range of security controls discussed including:
- Risk Assessment
- Certification, Accreditation and Security Assessments
- System Services and Acquisitions
- Security Planning
- Configuration Management
- System and Communications Protection
- Personnel Security
- Awareness and Training
- Physical and Environmental Protection
- Media Protection
- Contingency Planning
- System and Information Integrity
- Incident Response
- Identification and Authentication
- Access Control
- Accountability and Audit
It is important to note that the security controls you choose to implement should be most relevant to the type of systems that you’re using and you need to protect. You don’t need to apply all the controls listed in NIST SP 800-53 but you do need to make sure that those that you do apply meet the necessary security standards. Pick those controls that will protect the type of system you’re using the most.
Step #5: Conduct Risk Assessments
At this stage, it is time to assess the security controls you’re using to determine if there are any gaps in your process. NIST SP 800-30 outlines how risk assessments should be conducted. You need to protect everything from individuals to assets, and operations. Once you’ve conducted the risk assessment you should also identify if there are any other controls you need to protect data. The idea is that you scrutinize your controls to make sure that you have all the bases covered.
Step #6 Certification and Accreditation
After tweaking your controls and completing the necessary documentation you need to get your system controls certified and accredited to show that they function properly. If the review is successful then the information system will be accredited. The certification process is outlined in NIST SP 800-37 “Guide for the Security Certification and Accreditation of Federal Information Systems.”
Broadly speaking, the certification and accreditation process can be broken down into four sections: planning, certification, accreditation, and continuous monitoring.
Step #7 Continuous Monitoring
Finally, you will need to monitor the security controls and systems for modifications and changes. Types of monitoring you will need to incorporate include configuration management, file integrity monitoring, vulnerability scanning, and log analysis. Each tool has a different use case. For example, a vulnerability scanner can be used to scan devices for entry points and vulnerabilities. A file integrity monitoring system will help make sure that you can verify system files.
Software for FISMA Compliance
Working towards FISMA compliance is a hundred times easier if you have the right tools to fall back on. Given the importance of the regulations, many vendors have designed solutions specifically to comply with the requirements listed in the legislation. In this section we’re going to look at a couple of the tools you can use to help stay on top of FISMA:
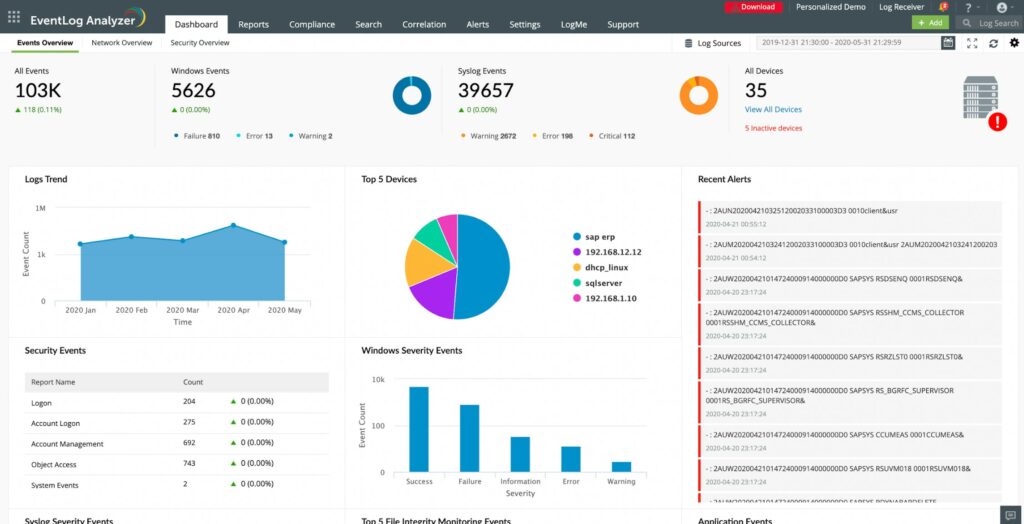
ManageEngine EventLog Analyzer (FREE TRIAL)
ManageEngine EventLog Analyzer is a log management solution that offers reports that are FISMA compliant. The software can collect, monitor, and analyze log data from your network and identify cyber-attacks. You can convert this data into reports to comply with the legislation.
Why do we recommend it?
ManageEngine EventLog Analyzer is a rival to the SolarWinds Security Event Manager. The system provides log management, threat detection, bot blocking, file integrity monitoring, and compliance management. The system will provide activity documentation for compliance with FISMA, PCI DSS, HIPAA, GDPR, SOX, and ISO 27001. The tool can cover multiple sites.
There are out-of-the-box reports for Audit and Accountability, Certification (AU), Accreditation and Security Assessments (CA), Contingency Planning (CP), Access Control (AC), Identification and Authentication (IA), and Configuration Management (CM) requirements.
For Accreditation and Security Assessments, ManageEngine EventLog Analyzer has a Windows Services report that details when a service was started and the device the service is running on. For Contingency Planning, reports provide details on the time, date, and user who initiated backup measures. All of these reports are supported with real-time email and SMS alerts which notify the user about unauthorized access to systems in the network.
Who is it recommended for?
This system will appeal to a wide range of businesses. The smallest enterprises can access the Free edition, which is limited to collecting logs from five sources. The Professional edition will monitor a single site and the Enterprise edition will cover a WAN that includes many sites.
Pros:
- Customizable dashboards that work great for network operation centers
- Multiple alert channels ensure teams are notified across SMS, email, or app integration
- Uses anomaly detection to assist technicians in their day-to-day operations
- Supports file integrity monitoring that can act as an early warning system for ransomware, data theft, and permission access issues.
- Forensic log audit features enable admins to create reports for legal cases or investigations.
Cons:
- Designed for enterprise-scale networks
There are three versions of ManageEngine EventLog Analyzer available: Free Edition, Premium, and Distributed. The Free version supports up to five log sources. The Premium version starts at $595 (£484) per year for 10-1000 log sources. The Distributed version starts at $2495 (£2,033) for 50 unlimited log sources. You can download the 30-day free trial.
SolarWinds Security Event Manager
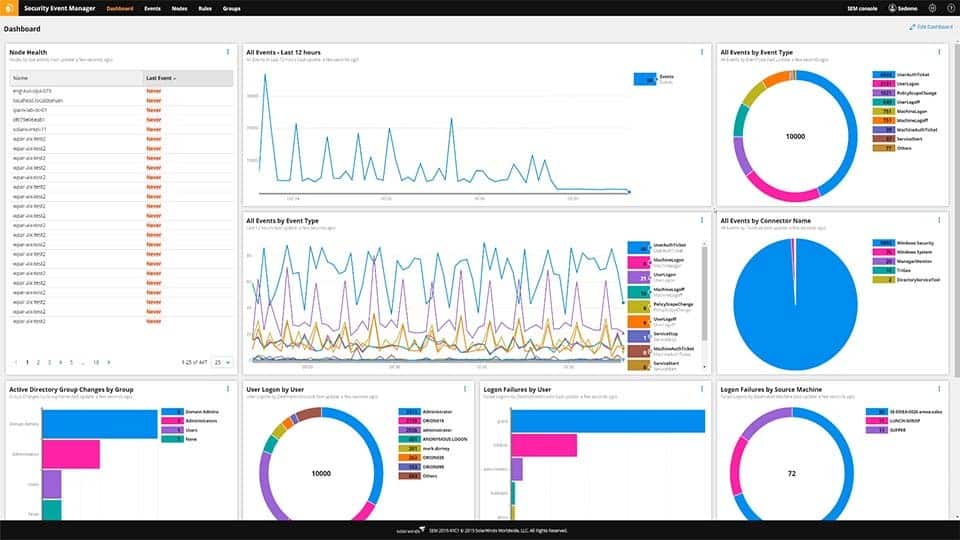
SolarWinds Security Event Manager is a log and event management solution with integrated compliance reporting tools. The event processing capabilities of the software help you to manage IT assets and risks by identifying security events. You can control the type of events you screen for with a rule-based log and event correlation.
Why do we recommend it?
SolarWinds Security Event Manager provides log management, a SIEM, and file integrity monitoring. The security features in this tool make it a good choice for companies that need to be compliant with FISMA. Its features also include privileged account management. The tool also supports DISA STIG and NIST compliance.
Once you’ve collected log data you can generate FISMA audit reports to document network events. All you need to do is check the FISMA-compliant box on the Manage Categories page and you’re good to go. These reports are customizable to make sure you can view all the necessary information.
Who is it recommended for?
This tool is suitable for use by large organizations. It is capable of processing a lot of log data and its log management rules can both parse and consolidate logs. The system will perform threat detection and you can set it up to protect specific files from unauthorized access.
Pros:
- Built with enterprise in mind, can monitor Windows, Linux, Unix, and Mac operating systems
- Supports tools such as Snort, allowing SEM to improve your overall security posture
- Over 700 pre-configured alerts, correlation rules, and detection templates provide instant insights upon install
- Threat response rules are easy to build and use intelligent reporting to reduce false positives
- Built-in reporting and dashboard features help reduce the number of ancillary tools you need for your IDS
Cons:
- Feature dense – requires time to fully explore all features
For auditing compliance and continuous monitoring, SolarWinds Security Event Manager is ideal. SolarWinds Security Event Manager starts at a price of $4,665 (£3,800). You can download the 30-day free trial.
FISMA Compliance: A Long-Term Effort
Managing security procedures and staying FISMA compliant is an uphill battle but this FISMA compliance checklist should set you off on the right foot. Both government agencies and contractors will benefit from applying the standards outlined in FISMA and NIST SP 800-53.
By making a conscious effort to protect systems from malfunction, unauthorized users and attackers, entities can ensure that confidential data stays that way. Complying with the regulations is a long-term effort.
Whether you choose to go the route of ensuring compliance with an in-house contractor or specialist consultant is up to you. If you want to minimize potential liabilities then working with a consultant is one of the best ways to verify that your security measures are up to scratch.
While the cost of designed security controls compliant with the act is vast, it is worth remembering the cost of non-compliance. The short-term investment is well worth the long-term gain of retaining government contracts.
FISMA compliance FAQs:
What is the purpose of FISMA?
FISMA implements the Department of Homeland Security’s enforcement role in creating information security policies for federal Executive Branch civilian agencies.
What nine items must be included in the agency information security programs?
The nine reporting categories for the agency information security program are:
- Personnel security
- Physical security
- Classification management
- Declassification
- Protection and maintenance for classified information systems
- Operations security and technical surveillance countermeasures
- Professional education, training, and awareness
- Security management, oversight, and planning
- Unique items
What is FISMA FedRAMP?
FedRAMP pertains specifically to cloud services and managed services. It authorizes these cloud services for use by government agencies, like a stamp of approval.