
Phishing schemes typically involve a victim being tricked into giving up information that can be later used in some kind of scam. The information is often sought through an email, a phone call (voice phishing or vishing), or a text message (SMS phishing or smishing). Phishing is a very common element in many types of internet scams that can target thousands of people at once in the hopes that one or two will be fooled.
Spear phishing is a more targeted type of phishing. The perpetrator typically already knows some information about the target before making a move. When you consider how many personal details someone could uncover about you on the internet these days, it’s really not that difficult for someone to pose as a trusted party and trick you into handing over some additional info.
Thankfully, if you’re aware of these types of scams and know what to look out for, you can avoid becoming the next victim. Before we go into more detail, here is a quick overview, in case you’re in a hurry.
In short:
What is a spear phishing attack?
- Spear phishing is a targeted form of phishing attack which involves tricking an individual or business into giving up information that can be used as part of a scam.
- The attacker will usually already have some information about the intended victim which they can use to trick them into giving away more valuable information such as payment details.
In this post, we’ll go into more detail about what spear phishing is and provide some examples of phishing schemes. We’ll then offer some tips to help you ensure you don’t get caught out.
What is spear phishing?
As mentioned, spear phishing is a targeted form of phishing. Almost all online scams start with some form of phishing, but many of these attempts randomly target a large audience. For example, you might get an email telling you you’re about to receive some money, but you just need to provide some personal details first. This is a form of phishing, but it isn’t targeted.
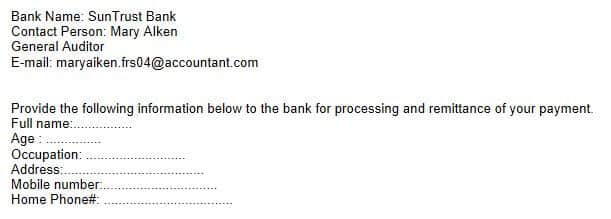
In a spear phishing attempt, a perpetrator needs to know some details about the victim. Using these details, the fraudster aims to instill trust in the victim and get as far as possible with the scam. So where do they find these details? These could be gleaned from a previous phishing attempt, a breached account, or anywhere else they might be able to find out personal data. Social media, in particular, is a hotbed of information regarding both individuals and businesses.
Spear phishing attempts can take many different forms. Some try to get you to click on a link that could lead to a website that downloads malware (for example, ransomware), a fake website that requests a password, or a site that contains advertisements or trackers. Other phishing attempts might ask you to provide your social security number, hand over credit card or banking information, or simply send some money.
Attacks on individuals
On a personal level, scammers could pose as a business you trust, for example, a bank or a store you’ve shopped at. They could offer great deals, tell you you owe or are owed money, or that an account is about to be frozen. They might even pretend to be a person you know, directly or indirectly. For example, posing as someone who went to your old school or is a member of your religious group could get you to open up.
Attacks on businesses
Spear phishing is a very common form of attack on businesses too. Because it’s so targeted, spear phishing is arguably the most dangerous type of phishing attack. According to Proofpoint’s 2020 State of the Phish (PDF) report, 65 percent of US businesses were victims of successful phishing attacks in 2019. What’s more, Verizon’s 2020 Data Breach Investigation Report found that phishing is involved in 22 percent of data breaches, more than any other threat action variety.
A 2017 report by IRONSCALES revealed that spear phishing is increasingly laser designated, with 77 percent of emails targeting ten mailboxes or fewer. What’s more, the study found that one-third of attacks targeted just one mailbox.

A common spear phishing scam in companies involves the scammer posing as a company executive and requesting that an unsuspecting employee wire money to an account belonging to the fraudster. This is often referred to as “whaling” and is a type of CEO fraud. While scammers target all sizes of businesses, attacks against small businesses are becoming increasingly popular.
Examples of spear phishing
Spear phishing attempts have been used to swindle individuals and companies out of millions of dollars. They can also do damage in other areas, such as stealing secret information from businesses or causing emotional stress to individuals.
Scammers will often take advantage of the current climate and recent events to create their phishing lures. For example, the coronavirus pandemic has prompted lots of schemes centering around government benefits and job opportunities.
Here are some examples of successful spear phishing attacks.
Spear phishing attempts targeting businesses
Scammers are targeting businesses all the time, but here are a few examples of some high-profile attacks.
Ubiquiti Networks Inc
In 2015, this company handed over more than $40 million in a spear phishing scam involving CEO fraud. Emails seemingly sent from senior executives directed employees to send funds from a subsidiary in Hong Kong to accounts belonging to third parties. The emails actually came from the fraudsters and the third-party accounts belonged to them.
Franklin, Massachusetts
In a recent scam, the town of Franklin, Massachusetts fell victim to a phishing attack and lost over $500,000 to scammers. The fraudsters persuaded a town employee to provide secure login information. The criminals were then able to use these details to steal the funds.
Epsilon
This online marketing company was targeted in 2011 as part of a scheme to harvest customer credentials, possibly for use in other spear phishing attempts.

Reports indicate spear phishing emails might have contained a link to a site that downloaded malware, which in turn disabled antivirus software, provided remote system access, and could be used to steal passwords. These emails were sent to different marketing companies, but always targeted employees responsible for email operations.
Electronic Frontier Foundation
In 2015, scammers used the trusted guise of the Electronic Frontier Foundation (EFF) to direct victims to a fake site (Electronicfrontierfoundation.org). It was used to distribute keyloggers and other malware, but the EFF has since taken control of the domain.
It now simply redirects to an EFF blog post detailing the scam.
RSA
Security firm RSA was targeted in a successful spear phishing attempt in early 2011. Two groups within the company were sent spear phishing emails simply titled “2011 Recruitment Plan.” Although the emails were marked as junk mail, one employee opened an email attachment that ultimately led to a form of malware being installed on the computer. The malware gave the attacker remote access and the ability to steal sensitive data.
Alcoa
The Chinese army has been accused of multiple spear phishing attempts aimed at stealing trade secrets from US companies. One of these was reported to target aluminum company Alcoa. In 2008, it’s suspected that hackers contacted 19 senior Alcoa employees via email, impersonating a board member of the company. Once opened, the mail installed malware on the recipients’ computers, resulting in the theft of almost 3,000 emails and more than 800 attachments.
Spear phishing attempts targeting individuals
While companies see huge losses from these attacks, both directly and indirectly, the impact on an individual can be even more severe. Take, for example, the disturbing story of a reddit user we interviewed for a previous article.
She was targeted by a criminal who used social engineering to get her to hand over a password to an email account. This eventually led to the scammer taking over several social media and email accounts and blackmailing the victim with the contents.
That scam was particularly emotionally damaging, whereas others are purely financially motivated. Some larger-scale spear phishing schemes hit users of large companies, such as those below:
PayPal
PayPal users seem to be the target of endless general phishing attempts. The huge number of users means that mass general emails will have a higher chance of success. However, some PayPal users have been hit with more targeted spear phishing emails. These actually address the customer by name, making them seem more legitimate than your standard phishing email.
Amazon
Amazon is another company that has so many users, the chances of hooking one through a general phishing attempt is worth the effort. But Amazon users should watch out for spear phishing attacks too. A huge targeted attack occurred in 2015 when up to 100 million emails were pushed out to Amazon customers who had recently placed an order.
The emails looked real, with the title of “Your Amazon.com order has dispatched,” followed by an order code. But instead of a message, the email only included an attachment. Opening the attachment ultimately led some recipients to install Locky ransomware, which involved a bitcoin ransom.
Other common spear phishing scam examples
Aside from those specific cases, here are some more general example scenarios you might come across. These all use information that could be gleaned from social media posts, especially if you’re prone to divulging information about where you shop, eat, bank, and so on.
- An email from an online store about a recent purchase. It might include a link to a login page where the scammer simply harvests your credentials.
- An automated phone call or text message from your bank stating that your account may have been breached. It tells you to call a number or follow a link and provide information to confirm that you are the real account holder.
- An email stating that your account has been deactivated or is about to expire and you need to click a link and provide credentials. Cases involving Apple and Netflix were recent sophisticated examples of this type of scam.
- An email that requests donations to a religious group or charity associated with something in your personal life.
When you think about how much information can be found on social media, it’s easy to see how someone could quickly earn your trust by simply stating a common interest or posing as a company you have a history with.
How to avoid spear phishing scams
Some rather concerning statistics emerged from a 2015 Intel study, which revealed 97 percent of people were unable to identify phishing emails. Indeed, across the cybersecurity industry, the main nugget of advice to prevent successful spear phishing attempts is education.
In this section we’ll offer tips to help both individuals and businesses protect against these scams. We’ll go into these in more detail below, but below is a list of actionable steps you can take to combat successful spear phishing attempts.
Here’s how to prevent spear phishing attacks:
- Increase awareness
- Use tools for defense
- Look out for fake emails
- Avoid clicking links and attachments
- Look out for phishing sites
- Avoid sending personal information
- Verify suspicious requests
- Use strong passwords and a password manager
Now, let’s take a closer look at each of these steps.
1. Increase awareness
As with any scam, one of the top ways to avoid it is to become aware of how the scam takes place. Sharing the information with your friends, family, and colleagues can help prevent them from becoming victims too.
You can keep up-to-date on these topics by reading blogs like ours as well as those of top security software providers, such as McAfee and Norton.
If you’re a business owner, it’s crucial to ensure your employees are educated on the topic of phishing attacks, particularly spear phishing.
For businesses, you can actually run a free test to see how “phish-prone” your employees are. Based on those results, you can decide the best course of action to take to improve training and prevent successful phishing attempts.
Companies like Cofense, KnowBe4, and Webroot provide security awareness training to help prevent such attacks. In fact, businesses spend a total of over $1 billion each year on this type of training.
2. Use tools for defense
While education and awareness are some of the best defenses out there, tools are available to help defend against phishing attacks. These are especially useful for businesses where a lot is at stake should an attempt be successful. One of the useful tools available is Cofense (formerly PhishMe).
For individuals, major email providers are stepping up their game when it comes to anti-phishing tactics. With the help of machine learning techniques, Gmail claims to block 99.9% of spam emails.
3. Look out for fake emails
We have a whole post dedicated to spotting phishing emails, but here are the main takeaways:
- Don’t trust display names as these can be anything a scammer wants them to be.
- Check for fake email domains; they’ll often be slightly different versions of the real thing.
- Look at the logo and other images; low-resolution images can be a giveaway.
- Review links carefully by hovering over the link text (without clicking). A link that is different from the one in the link text is a sign of a malicious link.
- Look out for bad spelling and grammar, as this can be a tell-tale sign that it’s not a legitimate message.
Spear phishing emails and messages are highly targeted, so it becomes worth the effort on the part of the criminal to spend time making them look like the real deal. As such, they are becoming increasingly sophisticated and difficult to spot. You may have to do multiple checks and even then, they could have all bases covered.
4. Avoid clicking links and attachments
As mentioned earlier, links can lead to websites containing malware, spammy advertisements, and trackers. Similarly, an attachment may contain viruses or malware and should never be opened unless you’re absolutely sure of the source.
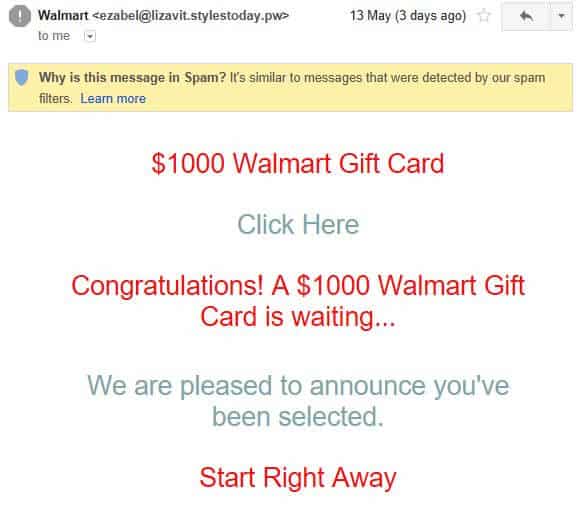
Some emails will only contain a link or an attachment with no other message, possibly targeting the reader’s sense of curiosity to prompt them to click.
The best advice? Simply don’t click links or attachments if you have any suspicions whatsoever.
5. Look out for phishing sites
If you do happen to click a link in an email and end up going through to a website, you can do some checks to detect an imposter. Again, we have a whole post dedicated to spotting fake websites, but here are the main pointers:
- Check the URL to see if it matches what is on the page.
- Check for an SSL/TLS certificate (a green padlock symbol and/or “https” in the address bar).
- Look for a navigation page or footer, including an “About” page, privacy policy, terms of use or service, and contact details.
- Check for proper spelling and grammar; as with emails, poor writing can be an indicator of a fake site.
- Be wary of “too-good-to-be-true” claims; they are often just that.
- Search elsewhere for reviews about unknown companies.
- Check the copyright is up-to-date; if not, it’s probably a fake site.
In other cases, clicking a link may simply take you to a blank page. If you’ve clicked a link and suspect that malware may have been downloaded, various tools can detect and remove it.
6. Avoid sending personal information
Legitimate businesses very rarely ask for personal information via email. If you receive an email or SMS asking you to give details such as your address, social security number, or banking info in the body of an email or text message, it is very likely a phishing attempt.
A genuine email will typically either provide the address of a site to go to (with no link), provide a link to click, or give you a number to call. Bear in mind, all of these scenarios could also be more sophisticated phishing tactics, so should be verified (more on that below).
7. Verify suspicious requests
If you have suspicions about an email or other message, don’t visit the site or call the number provided. If you think it may be authentic but are unsure, you can try to verify it first.
One way to do this is to simply run a search for the email or phone number provided. If it’s a known scam, chances are you’ll see results stating as much.
Another, more reliable, method of verification is to simply call or email the company to check if it’s a real request. However, you should contact the company via a phone number or email from its actual website, not the contact information found in the email.
8. Use strong passwords and a password manager
If you suspect you may have been a victim of a phishing attempt or you are notified as such (by a definitely trusted source), then you should consider changing your password. Utilizing a strong password is important as it can help prevent other attacks such as brute force attacks.
If remembering passwords seems too difficult, a password manager can help. Another benefit of these tools is that they can help you detect a phishing site by default. Password managers work by auto-filling your information in known sites, so they won’t work on unknown (including fake) domains. This isn’t something that should be relied upon, but it can act as a backup.
If you’re ever asked to change a password, never follow the link in the email or text message. Go to the website directly and change it there. This way, you’re covered whether the message is legitimate or not.
See also:


