The internet is the most widely used communication network ever constructed. It’s used by millions of humans and machines every second of every day. There are positive and unpleasant things happening on the internet, and among the unpleasant things are ongoing attempts to scam innocent people out of their money or identities.
Indeed, wherever there’s a slight opportunity of making some easy money, you can be sure that criminals lay ready to pounce. The internet brings with it many such opportunities, and fraudsters appear to be waiting around every virtual corner with the latest in online scams.
While some forms of internet fraud have gotten very sophisticated, even some of the older, less advanced plays still actually work. If people know more about the types of scams taking place and what to look out for, we can hopefully save at least some people from getting swindled out of their hard-earned cash.
We’ve covered some specific types of scams in various dedicated posts, but here we’ll offer a roundup of many of the common internet scams currently in operation.
Related: Cybercrime stats and facts
What to do if you’ve fallen for an online scam
If you’ve been scammed online, don’t panic. We know it’s embarassing, but you may be able to get your money back by telling your bank what has happened. First, cease all communication with the scammer, report them to the relevant authorities (instructions at the bottom of this post), and run an antivirus scan just in case.
We recommend Norton Security and TotalAV. These are two excellent antivirus programs that can sniff out commonly-used malware and prevent scammers from using your computer without your knowledge. What’s more, they both come with a 30-day money-back guarantee, allowing you to try them risk-free.
Finally, change all of your passwords, especially for services that have your payment information saved. You can do this manually, or use a password manager to simplify the process by generating strong, unique passwords for every website.
Email-based scams
Email scams are a type of online fraud. While it’s true that a fraudulent offer can be contrived with almost any story, there are a few “tried and true” cons that seem to crop up repeatedly over time, such as:
- Advanced fee fraud
- Overpayment fraud
- Work from home scams
The broad strokes tend to remain the same, but the details of these types of online fraud change over time. There are resources to keep on top of the ever-changing scams, and steps to take to defend against them.
Email is an extremely popular format for many common internet scams for the simple fact that it’s so cheap and easy to execute. You would think that scam artists would have refined their approach by now, but many scam emails are poorly written and fairly easy to spot. Nonetheless, some are more sophisticated and people still lose a lot of money to email scams every year.
See also: How to encrypt email
Advanced-fee fraud
The advanced-fee fraud scam has many variations, and may claim that you are a beneficiary of some estate money, have won the lottery, or have an old bank account you’ve forgotten about.
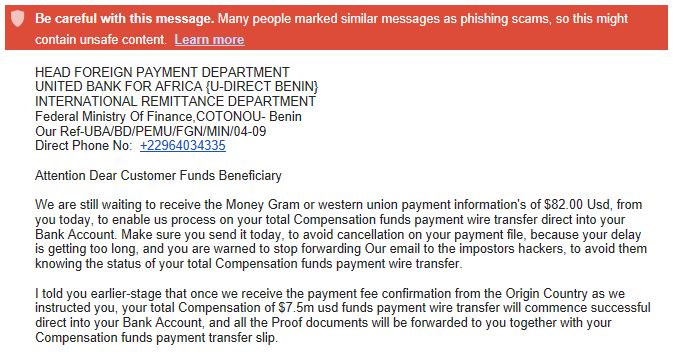
Whatever the subject, the email is requesting that you send a fee in advance before you can receive whatever is promised.
Nigerian scam (Nigerian 419 scam)
The Nigerian scam is a variation of the advanced-fee scam but deserves its own spot since it has been so prevalent. Emails typically promise large rewards for helping “government officials” move money to a US financial institution, with upfront fees required.
The scam started in Nigeria and violates penal code 419 in the country, so is often referred to as a Nigerian 419 scam.
Charity fraud
Charity scams simply play on the emotions of victims to persuade them to hand over donations to fake charities and organizations. Subjects might include puppies in danger or disaster relief efforts. The emails typically include some excuse as to why the matter is urgent and may include links to legitimate-looking websites.
Aside from sending money, victims may be handing over their debit card or credit card details to thieves.
Work-at-home job scams
Working from home has so many draws and is a major lifestyle goal for many people. Scam artists capitalize on the dreams of these would-be remote workers by luring them with fantastic yet realistic-sounding work-at-home job opportunities.
The catch? They just need to send a wire transfer or money order upfront to pay for some equipment or educational materials before they can get started, but these never arrive, and there is no actual job.
Canceled account
Some scammers spend a fair amount of time creating official-looking emails from reputable service providers. They tell the target that the account is about to be suspended and that they need to provide information to keep it open.
The email might include a link to a phishing site requesting login credentials and billing details to secure the “continuation of service”.
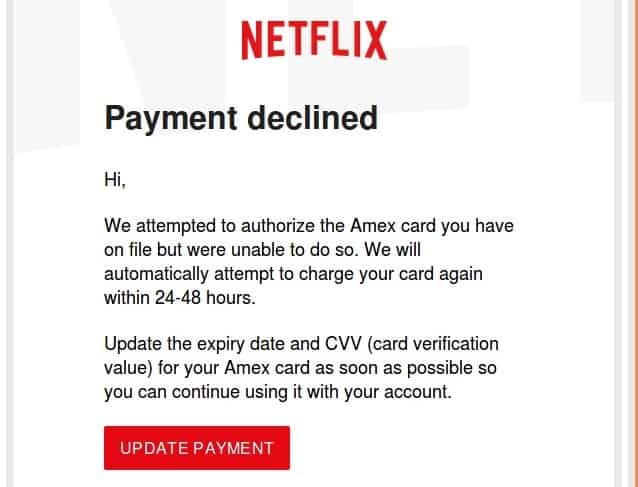
Netflix customers were recently hit by such a scam.
CEO fraud
This one is more targeted toward businesses. The scammer identifies the person within a company that has control over funds. They then pose as someone with authority such as the CEO, and request money be transferred to a specified account.
With all of the information available on LinkedIn these days, it’s fairly easy for fraudsters to identify who to target and to come up with convincing stories (see also: whaling).
This type of phishing requires some preparation because the scammer needs to act convincingly like the executive he or she is purporting to be. The fraudster will then contact someone in the company who has the authority to move money and direct that person to transfer funds to the scammer.
As with most phishing scams, CEO phishing is most effective when there’s a sense of urgency or emotionalism applied to the request. Therefore, many CEO phishers will zero in on new members of the finance department in the hopes that person does not yet know all the safeguards that may be in place to prevent the scam from working.
Read more on CEO fraud here.
Greeting cards
The very simplistic greeting card scam can be used to infect your computer with malware.
The email poses as a greeting card (e-card) from a friend or family member and encourages you to click a link. Once you do, the malware is automatically downloaded and installed on your system.
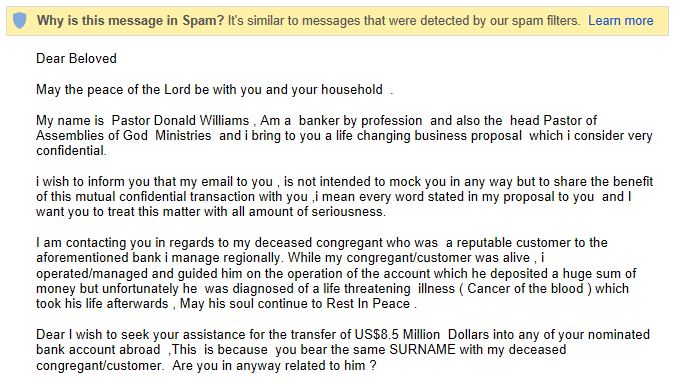
Affinity fraud
Affinity fraud refers to when someone uses a common interest or belief such as religion to lure you in. It often happens in person, especially within religious communities, but can be conducted via email too.
The above email uses faith to try to hook the reader and persuade them that it’s legitimate.
Guaranteed bank loan or credit card
In this take on the advanced fee scam, you are told that you are pre-approved for a loan or credit card but that you just need to pay some processing fees.
It could be a small amount but fraudsters might be looking for bank account info more so than the money itself.
Service provider
This one often targets businesses and involves an email containing an invoice for legitimate-sounding services. A sense of urgency is used to convince the receiver that they need to pay immediately or risk having the case transferred to a collections agency.
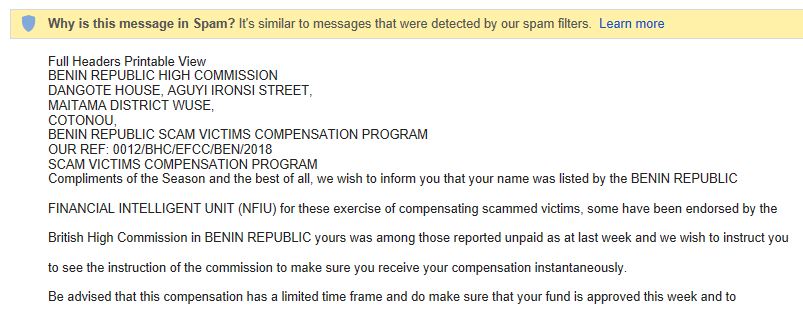
Scam compensation scam
Yes, believe it or not, this one pops up regularly in spam folders. The email explains that its sender is coordinating some compensation for scam victims, and the receivers’ name is on a list of victims.
You just need to send over some personal details before you can start collecting your compensation.
Elder fraud
While many types of internet fraud can target virtually anyone with access to a computer, many are crafted specifically with the elderly in mind. Seniors are often targeted for identity theft since they are perceived as being more susceptible to certain scams.
Here are some of the most common forms of elder fraud but you can find more about detecting and reporting these scams in our elder fraud article.
Investment scams
Elderly people seeking to invest are often looking for short-term lucrative projects to supplement their retirement income. Investment scams simply promise fantastic returns in order to get seniors to hand over their money.
Insurance schemes
The insurance scam plays on the assumption that seniors might be less focused on what they have now and more so on what they will leave behind for loved ones.
This type of scheme might involve a phone call or email persuading the senior that they need an annuity or life insurance policy.
Often the insurance firm is completely made up, but insurance scams are actually sometimes carried out by legitimate agents, including one who has been caught multiple times.
Health scams
As people age, health tends to be more likely to deteriorate and the need for prescription medication can become expensive.
Many online pharmacies have stepped in to offer drugs and other healthcare at lower than average prices. The problem is, most of these sites do not operate within the law or follow standard practices. For example, the founder of Canada Drugs is wanted in the US for selling counterfeit medicines, but the website is still very much up and running.
Without proper regulation, consumers really have no way of knowing what they are getting or if they will receive anything at all.
Grandparent scam
This one is technically a form of vishing and involves someone calling a grandparent and posing as their grandchild who needs money urgently. They might say they’re in jail or in need of medical help abroad, but that it’s imperative they get the money immediately.
Of course, the desperation tugs on the heartstrings of their “relatives” and one convicted scammer said that about one in 50 people fell for his scam.
Extortion
Extortion scams follow the basic premise that you need to hand over money urgently or face a predefined consequence, whether it be real or fabricated.
Extortion schemes can be simple or extraordinarily complex, depending on the imagination of the perpetrator involved.
Here are some of the online extortion scams to look out for.
Ransomware
Ransomware is a type of malware that involves an attacker encrypting your files with the promise of decrypting them only in return for a fee.
One of the most notorious cases of ransomware was the 2017 WannaCry attack in which more than 400,000 machines were infected. Ultimately, criminals took an estimated $140,000 worth of bitcoin in exchange for decrypting users’ hijacked files.
Backing up files regularly can help protect you against the threat of ransomware.
Sextortion
In this form of extortion, victims are typically lured into sharing intimate photos or videos, often through online dating sites or social media. They may even be prompted to perform explicit acts while being secretly filmed. They are then asked to pay a fee to prevent the photos or videos from being released.
Hitman
This terrifying scam involves threats of physical violence and even death, usually sent via email. The claim is often that the person sending the email has been hired to kill you and will relinquish their role in exchange for a fee.
Emails might include personal details garnered from social media or other sources to make them seem even more threatening.
Aside from going after your money, some scammers also try to obtain your personal information for use in identity theft.
Terrorist threat
This is a variation of the hitman scam that plays on today’s societal fear of terrorist acts. Again, the basic premise is that your life will be spared only if you pay up.
Bomb threat
Another one playing on the fear of recent world events is the bomb threat scam. This is an email telling people that there is a bomb planted in their building and it can be disconnected only if a certain fee is paid.
DDoS attack
Distributed Denial of Service (DDoS) attacks are similar to ransomware attacks, except that instead of file encryption you often have whole websites or internet services taken down.
Web servers hosting these sites and services are flooded with dummy traffic that overwhelms them, slowing the site down to a crawl or even shutting it down altogether.
Victims are instructed to pay a fee to gain back control over the service. Businesses are often prime targets for this type of attack.
Phishing
We’ve touched on phishing in some of the other sections, but with this field comprising such a large portion of online scams, it’s good to know about the different types to look out for.
In fact, the common element in almost all types of internet scams is the initial “phish”. This is the act of tricking you into providing some kind of information that is later used to scam you.
The odds of pulling off a successful scam are low, so the pool of potential victims has to be very large. The easiest way to contact a large number of people with almost no effort is through email.
In some cases, phishing emails attempt to direct you to a clone of a trusted website where you’re likely to enter login credentials, or try to make you download malware.
In a dedicated phishing post, we look at how to avoid or repair the damage done by common phishing scams, some of which are explained below.
Spear phishing
Spear phishing is very targeted and the perpetrator typically knows some of your details before they strike. This could be information gleaned from social media, such as recent purchases and personal info, including where you live.
A phishing email or message might be crafted based on those details, asking for more information including payment details or passwords.
Whaling
This is geared toward businesses and targets high-level executives within corporations who have access to the email accounts of someone in authority.
Once they have access to that email account, they can use it for other means such as accessing employee information or ordering fraudulent wire transfers (see also: CEO fraud).
W-2 phishing
This is an even more targeted version of whaling where the main goal is to obtain employees’ W-2s or contractors’ W-9s.
- Schools
- Hospitals
- Tribal organizations
- Chain restaurants
- Temporary staffing agencies
- Shipping and freight companies
The email might be from an actual or spoofed executive account or might appear to be from the IRS or an accounting firm. Once provided, the documents give criminals everything they need for identity theft.
Phishing to deliver ransomware
As if the phishing itself isn’t bad enough, many emails come bundled with ransomware. This way criminals can get an increased payload for their efforts.
Vishing
Voice phishing (vishing) scams are not really online scams, but they are often linked and are becoming more sophisticated so are worth mentioning here.
They use voice solicitation to get information or money from consumers or businesses. The scammer calls the victim and attempts to use social engineering techniques to trick the victim into doing something, often to give credit or debit card details or send money.
Sending email spam and SMS spam is very easy and costs almost nothing. Calling an intended victim personally, on the other hand, takes more time and effort. For that reason, we are less accustomed to vishing and the stakes are often much higher in order to justify the scammer’s time.
One of the major benefits of vishing versus phishing via email is that criminals don’t have to worry about spam filters. Calls, in general, are far less abundant than email, so there is a higher chance of getting someone’s attention. While phone calls are more expensive than email, Voice over IP (VoIP) has made mass calling far more accessible to criminals.
To make matters worse, it is almost trivial to spoof a caller ID number these days. If a scammer wishes to present themselves as an official with your country’s tax bureau, it would be easy for them to show you a legitimate tax bureau number on your caller ID.
Bank
Bank fraud vishing scams are some of the most common you’ll come across.
Scammers will typically pose as a financial institution representative and tell you there has been suspected fraud or suspicious activity on your account. While some will then try to extract personal or bank account information, other scammers have different tactics.
One in particular involves persuading targets to install “protective software” on their computer to block any more fraudulent transactions. What the software actually does is allow remote access to the victim’s computer.
Tax
We’ll cover tax scams in a bit more detail later, but these are often carried out over the phone or through a combination of phone calls and emails.
The first contact via phone may be automated meaning scammers can reach a huge number of targets very easily. It also means they only have to actually speak with anyone who calls back. These callers would be considered “qualified leads” and easy targets at that point since they’ve already fallen for the first stage of the scam. See more tax scams.
Prize
Fake prize or contest winnings are often communicated via a phone call or automated voice message.
Promised prizes could be in the form of cash, a car, or an all-expenses-paid vacation. In reality, fraudsters are looking to find out personal details (including your address and social security number) for use in credit card fraud or identity theft.
Tech support
The tech support scam often starts as a phone call and ultimately ends up online, similar to the bank scam mentioned above. This time, a “technician,” claiming to represent a large firm like Microsoft, will tell you your computer is infected and you need to hand over remote support.
Once you do, the fake tech can do whatever they want with your system, including installing malware or ransomware. Typically, once they are finished “fixing the issue,” you’ll be asked to pay for the service. They then have all of your payment info and in some cases can continue to access your computer through the remote access software whenever they want.
This scam isn’t always initiated over the phone and might start via a web page popup that tells you your computer is infected and to call a support number. The popup is usually difficult to get rid of which serves as motivation to call the number provided.
Government agency
If you get an official-sounding call from a law enforcement or government agency, you’d be forgiven for being scared into handing over details. Criminals prey on this fear and often pose as police or government officers to phish for personal information.
Bear in mind, any such legitimate contact would be dealt with in person or at the very least by mail.
Social media scams
With the popularity of social media continuing to boom, it’s no surprise that it’s considered a ripe environment for scammers. While many of the other scams on this list could potentially be carried out through social media, a few very specific ones have popped up on social platforms.
“See who’s viewed your profile”
This scam takes advantage of the curiosity of Facebook users and might pop up as an ad while you’re browsing the site. You’ll be prompted to download an app with the promise of being able to see who has viewed your profile.
The thing is, Facebook doesn’t actually give this information out, even to third-party applications. All you’re actually doing is handing over access to your Facebook account, including your personal details and possibly banking information.
Facebook “dislike” button
During the last few years, the Facebook world is often abuzz with the prospect of a “dislike” button becoming available. Scammers capitalize by posting ads for such a feature. These lead to pages that look like they’re run by Facebook but that actually include links to phishing sites asking for personal information.
Fake celebrity news
This scam involves a clickbait-style headline on Facebook relaying some fake celebrity news, such as the death of a well-known star or a new relationship in Hollywood.

Once you click, you’re prompted to enter your Facebook credentials to view the article, thus giving criminals full access to your account.
Impersonation scam
When you think about how easy it is to create a social media account, you realize there’s nothing stopping someone from creating an exact replica of your public profile. They can then reach out to your friends and family with friend or follow requests and once connected, pose as you.
These trusted connections can then be used for a whole host of purposes such as spreading malware or requesting money for made-up scenarios.
Instagram Likes scam
With many users across social platforms desperate for ‘likes’ and ‘follows,’ scammers have capitalized by offering just that. One app released in 2013 called InstLike asked for usernames and passwords in return for follows and likes.
In fact, they simply collected the credentials of 100,000 users and turned them into participants in a large social botnet. Basically, the app did deliver on its promise but used the accounts of those who signed up to do so. What’s more, within the app, people were encouraged to pay fees for additional follows and likes.
Job offer scam
A job offer scam might be run through email, but is commonly conducted through professional networking site LinkedIn.
Basically, you’re offered a job from a seemingly reputable company via direct message. In some cases, these can lead to scams whereby you become the middleman for transferring funds. You deposit a cashier’s check, then wire some of the money, keeping the remainder as your fee.
Unfortunately, the initial cashier’s check bounces and you are down the amount you sent in the wire transfer or money order.
Travel scams
Many people purchase airline tickets, hotel rooms, and even entire vacation packages online these days. Scammers know this and there has been a rise in fraudulent travel sites selling fake tickets and non-existent vacations.
Travel is usually a big-ticket item, which spells big bucks for criminals. Additionally, travel is a tricky purchase because you typically pay large amounts of money upfront for something that you won’t see until the date of travel.
This type of scam can be particularly problematic because you may not find out you’ve been scammed until you arrive at your destination or the airport. There may be no record of you having a booking at all.
Now you’re out the original money and also might have to come up with more to continue on your vacation, or simply pack up and go home.
Free or discounted vacation
These scams may be initiated via phone or email, but typically the target is told that they have won a vacation. In order to claim, they either have to pay a small fee (advanced fee scam) or provide credit card details for a deposit.
In the former case, the thief takes off with the money. In the latter, the credit card details can be used in credit card fraud.
Vacation ticket re-sell scam
In this case, someone posts an ad claiming that they have purchased a ticket for a trip they can no longer go on. They then sell the (fake) tickets for a much lower price than their face value.
Some victims don’t realize the scam until they show up at the airport ready for the trip. With insurance company agencies making it so difficult to get refunds on tickets, the fact that someone might be selling tickets online is made more believable, fueling the success of the scam.
Points scheme
In a points scam, the target is called or emailed and informed that they have won a huge number of points, through a travel points card program or a travel credit card points scheme. All they have to do is provide some details to confirm the transaction. This may include account information, credit card details, or other personal information.
Vacation rental
The vacation rental scam involves fraudsters posting ads for property in desirable locations for bargain prices. The victim is required to send a deposit or the full amount upfront.
Once they arrive at their destination, they may realize the property doesn’t exist, it has been misrepresented, or it isn’t actually available for rent.
Tax scams
As if tax season isn’t already dreaded enough without scammers making life more difficult! Criminals look to exploit both taxpayers and the government using a range of tax-related scams.
Fake audit
In a fake audit scam, targets are contacted by someone claiming to be from the IRS or similar tax agency and told that an audit has identified a discrepancy. Immediate payment is demanded with the threat of additional costs, imprisonment, or even deportation if victims don’t comply.
Whether it’s through an email or recorded voicemail, this scam is easy to execute so probably won’t go away any time soon.
Oddly, in Canada, it is reported that many of these particular scams involve payment requests via iTunes gift cards. You’d think this would be a bit of a giveaway, but it’s happening.
Fake refund
This one targets people who are expecting a tax refund. Again, criminals pose as the IRS or similar agency and prompt targets to click a link through which they can claim their refund.
However, the link leads to a phishing site where the victim is asked to provide personal information such as their social security number and banking details, which can be used in identity theft.
Erroneous refund
This scam is a bit more sophisticated as it actually uses real client details stolen from accounting firms via hacking or phishing.
The information is used to file a fake tax refund request which is processed by the IRS, and the client receives the refund amount. The scammer then poses as the IRS or a collection agency, tells the client the refund was issued in error, and demands the money be returned. Of course, the payment is directed toward the fraudster, not the IRS.
This case spells double trouble for the client. Not only are they short their refund, but they could also be in hot water with the IRS for supposedly filing a false claim.
Tax protester scheme
A tax protester scheme involves criminals calling or emailing consumers to tell them they don’t need to pay taxes.
This is really more of a troll than an actual scam because the person running it doesn’t benefit financially. However, the victim can be negatively impacted as failing to pay taxes can result in a conviction, including fines and imprisonment.
Bitcoin and cryptocurrency scams
With bitcoin and other cryptocurrencies exploding in terms of popularity and market cap over the past few years, it’s no surprise that criminals want to get in on the action.
Indeed, there are so many methods for scammers to choose from, and scams and hacks involving bitcoin and altcoins seem to be constantly in the news.
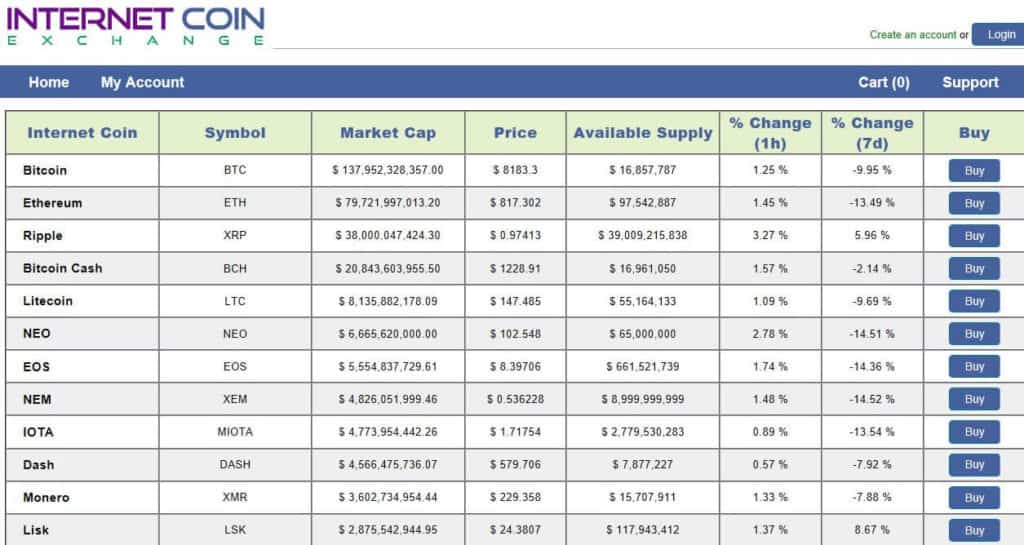
Fake coin exchanges
Since so many cryptocurrency-related businesses are relatively new, it’s difficult to know which ones are legit. Criminals have capitalized on this and simply take people’s money through fake or questionable exchanges.
One example of a blatantly fake coin exchange is Internet Coin Exchange which simply lists cryptocurrency price details alongside Buy buttons.
This one still appears to be very much up and running so we won’t be posting the link here.
Other questionable operations include Igot, which later became Bitlio. This exchange appeared to be operated inefficiently as there have been times when it simply can’t pay customers. Again, it’s still in business.
Hacked coin exchanges
Unfortunately, when exchanges are hacked by cybercriminals, both the exchange and its customers tend to lose out.
Mt Gox is probably the most famous case in which people are still waiting to find out if they’ll see their money four years on. But there have been other, more recent, high-profile hacks, including that of Coincheck to the tune of $500 million.
Pump and dump scheme
‘Pump and dump’ is a familiar term in the stock market, but it’s hitting cryptocurrencies too.
This involves the organized promotion of a particular cryptocurrency, usually a relatively unknown coin. The mass investment causes the value to spike, encouraging other investors to get in on the action. The value of the coin increases even further and when the time’s right, the first round of investors cash out, leaving the second wave with a worthless coin.
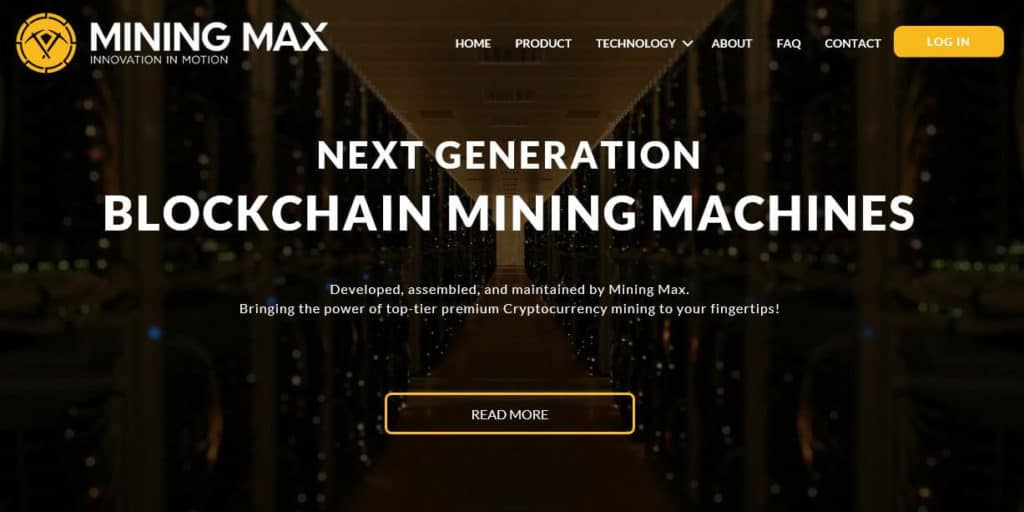
Fraudulent cloud mining companies
Mining of bitcoin and other cryptocurrencies typically involves using computational power to support the network in return for a reward. However, mining isn’t the easiest thing to get started with.
Enter cloud mining companies, which enable you to invest in mining without having to actually deal with the setup yourself.
When you invest in cloud mining, you’re putting a whole lot of trust in the mining company. Of course, where there are investors, there are scammers ready and waiting. For example, Mining Max raised $250 million for its operation, all but $70 million of which was reportedly pocketed.
In another case, the CEO of GAW Miners pleaded guilty to $9 million in fraud as an outcome of some very dodgy dealings, including selling more hashing power than was available.
Mining malware
Mining requires a huge amount of computational power, and that doesn’t come cheap. As such, criminals have developed mining malware that can enable them to exploit users’ computational power.
Known as malicious cryptomining or cryptojacking, the malware is usually spread by a trojan virus. Infected computers then form a larger botnet that mines cryptocurrencies.
Examples of mining malware include “Digmine”, spread via Facebook Messenger, and WannaMine, which uses EternalBlue, the leaked NSA exploit.
ICO exit scam
An Initial Coin Offering (ICO) is a little like an Initial Public Offering (IPO) for a company, the major difference being the coin is really worthless until investors perceive value.
ICO exit scams are similar to the pump and dump scams we talked about earlier except it’s usually the coin creators doing the heavy promotion followed by a quick sell-off.
Investors are wooed with whitepapers and promises of superior security and broad application potential. They buy coins in exchange for fiat currency, hoping to get a return on their investment.
Some of the biggest exit scams we’ve seen so far are Plexcoin, which gathered $15 million in investments before it was suspended, and Benebit, the team behind which ran off with between $2.7 million and $4 million early in 2018.
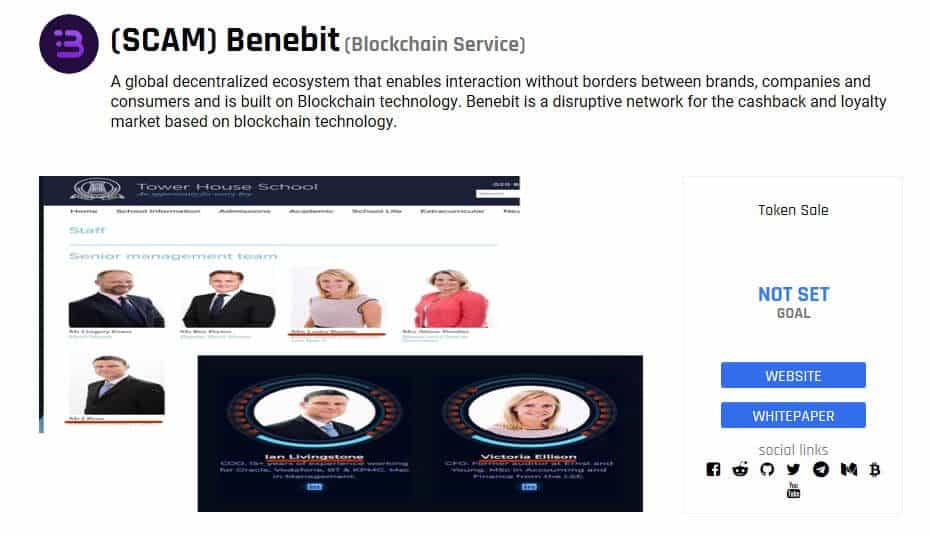
ICOs in general are viewed as such a problem that China has banned them and other countries are imposing heavy regulation.
ICO impersonators
Another issue among ICOs is not with the ICOs themselves, but with scammers impersonating them.
For example, the legitimate Seele ICO had their Telegram channel hijacked by people posing as admins. Investors were persuaded to pay for tokens before the sale had actually started and the funds were pocketed by the criminals.
Other fraudsters used a phishing scam centered around the Bee Token ICO as a means to dupe investors out of $1 million worth of ether.
Cryptocurrency investment schemes
With the cryptocurrency market being so volatile, it’s not uncommon to hear about massive gains over a short period of time. This makes classic pyramid or Ponzi schemes an easier sell to investors as people are less likely to view them as “too good to be true”.
Austrian investment scheme Optioment promised a whopping 4 percent weekly return to some investors and ended up reportedly stealing more than 12,000 bitcoins.

Other suspicious schemes include BitConnect, which shut down after receiving multiple cease and desist letters, and OneCoin, a reported global Ponzi scheme that is still going strong.
Wallet fork scams
Coin wallets are used as “safe” places for people to secure their cryptocurrency, basically somewhere to safeguard the private keys that can enable access to coins.
When a cryptocurrency forks and a new coin is created, it can be difficult to find a wallet that can accommodate the new coin.
Enter scammers. When Bitcoin Gold was first released, the mybtgwallet.com website popped up, promoting users to hand over their private keys and subsequently lose their coins.
This one wallet scam reportedly resulted in total losses worth over $3 million.
Wallet impersonators
More impersonators are taking advantage of the cryptocurrency market, this time in the form of wallet clones.
Criminals make people believe they are depositing their coins into a legitimate wallet but are actually keeping them for themselves.
Hacker group Coinhoarder used such a scheme to steal more than $50 million worth of bitcoin and other cryptocurrencies. It used domains impersonating the reputable Blockchain.info and even used paid Google ads to attract more victims.
Coin-mixing service phishing scam
Coin-mixing services are used to mix coins in order to break the connection between the sender and receiver, making transactions more anonymous.
While coin-mixing services can aid illegal activity, they can have legitimate use cases, too. Popular sites include Bit Blender and the now-defunct Helix by Grams.
These two were involved in a phishing scam on the dark web where a coin-mixing tutorial used links to fake websites for both of the services. Users following the steps and visiting the links simply handed over their coin to the thieves.
Coin mixing service Ponzi schemes
It’s not just phishing schemes that affect users of coin-mixing services. Bitpetite ran a mixing operation but also asked for investors to hand over money with the promise of 4 percent daily returns! This was clearly unattainable and the site disappeared in November 2017 after stealing an unknown amount from investors.
Other online scams
Aside from all of the above, there are many more online scams to look out for. Here are some of the most popular plays making the rounds right now.
Fake anti-virus software popup windows
We mentioned popups in the tech support scam earlier. A common occurrence you might have already seen are popup windows prompting you to download anti-virus software. However, when you follow the prompt, you could end up with malware instead.
Fake websites
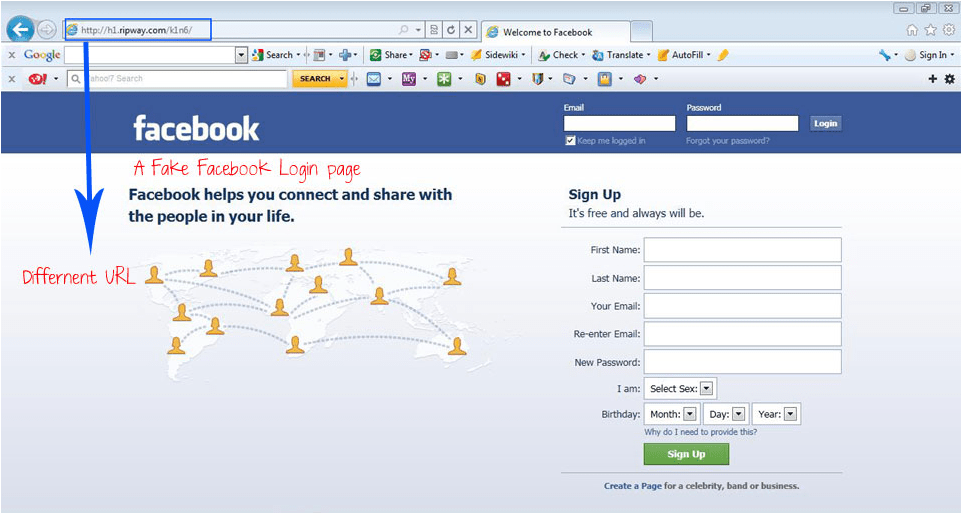
Fake websites are usually used in phishing scams. Typically, a replica of a legitimate website is used to encourage targets to enter details such as credentials, banking information, and personal details.
For example, the above image from the Expr3ss blog shows a very convincing fake Facebook login page.
Counterfeit goods sites
This is a more specific example of a fake website and is a big problem. Replicas of reputable websites may be used to make counterfeit goods seem legitimate. For example, brands like Ugg, Coach, and Michael Kors have had their websites copied almost exactly to make consumers believe they are purchasing genuine goods from the real brand.
Online dating and romance scams
Dating and romance scams are some of the oldest in the book, but as long as people are looking for love, they won’t be going away. In fact, in the US, romance scams account for the largest financial losses of all internet crimes. Fraudsters may contact targets through:
- Phone
- Text
- Social media
- Dating sites
They typically pose as a different person, including creating completely fake profiles (this is called catfishing), and often work in groups. The ultimate goal might be to get victims to pay money, hand over personal information, or even aid in illegal activities.
Ticket scams
We mentioned travel ticket scams earlier, but would-be concertgoers and sporting event attendees are also common targets of ticket scams. They purchase tickets online and show up to the event to find out they’re holding fakes.
Rental scam
The rental scam preys on those desperately searching for a place to call home.
Rental ads are posted with below-average prices, attracting plenty of buyers. Would-be landlords explain that viewings are not available since they are overseas but they will happily issue a refund if you’re not satisfied.
First and last month’s rent are typically required to secure the rental property. The fake landlord may also have renters fill out a form that includes banking information along with other personal details.
SMS scams
SMS scams (smishing scams) are variations on phishing and vishing scams and involve the use of a text message.
SMS, or text messaging, is built into just about every phone on the planet. As phones become more internet-connected, many of us have transitioned to instant messaging apps like WhatsApp and Facebook Messenger. But good old SMS messaging is almost always available. Scammers know that and can use it to target you.
A smishing text message will usually have much the same aims as any other kind of fraud. Scammers may want you to click a link to download malware or adware, or bring you to a convincing-looking phishing page in order to trick you into providing your login credentials for a website. Others might provide a number to call as a transition to a vishing scamming method.
While these often follow similar plays to email and voice scams, there are some more specific cases, such as trying to get you to activate a new credit card or telling you an account is expiring.
Amazon phishing scam
In this rather complex scheme, targets order products on Amazon from third-party sellers. They don’t receive the item so call the seller to inquire. The seller prompts the buyer to complete the transaction outside of Amazon, so gets paid and has access to payment information.
Amazon delivery scam
This is a slightly different angle to the one above, but is also orchestrated by third-party sellers.
In this case, they ship empty packages to wrong addresses where they are signed for by someone who is in on the scam. Since the package is signed for, the victim often has problems when trying to make a claim with Amazon.
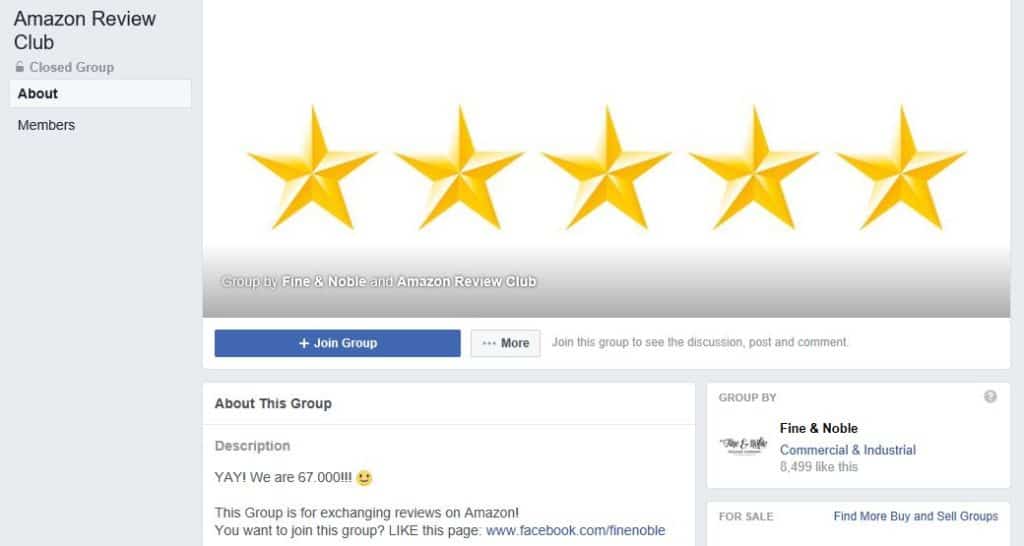
Astroturfing (advertising scam)
Astroturfing has been around for a long time and its definition can be loosely defined as a company creating fake support around its product in order to attract customers.
One famous example was McDonald’s paying employees to stand in line to create buzz around the release of the Quarter Pounder in Japan. With the persuasive power of online reviews, these have become a means for digital astroturfing.
Companies simply pay people to write fake glowing reviews on supposedly unbiased review sites. There are even Facebook groups dedicated to swapping online reviews for specific sites like Amazon or specific product types, for example, books.
Consumers rely heavily on these reviews when making purchases and ultimately end up with a subpar product or service or nothing at all.
Continuity scams
There is a broad range of continuity scams out there but they typically follow similar patterns.
Popups for surveys offering free gifts or amazing deals lead victims to enter credit card details to pay for minimal fees or shipping. Often hidden in the small print are exorbitant ongoing monthly fees that can be near impossible to cancel. In this case, you’ll likely have to contact your card issuer to stop future fees, but it’s unlikely you get reimbursed for those already paid.
This is another reason to always check your statements as these could easily go unnoticed.
Stock market scam
This scam is along the same lines as astroturfing and is conducted very much out in the open.
It involves articles or other methods and materials that persuade potential investors to contribute funds based on exaggerated predictions. In March 2021, the SEC enforced actions against a California trader that was posting false stock tweets.
Buyer scams
Most of us have sold something online at some point, but it’s seller beware.
Some scammers are using a tactic whereby they fake a pending payment to encourage the release of goods. This might be a bogus PayPal or email transfer message to say that payment will be released once tracking information is received. Once you do actually send the goods, no payment is ever received.
Overpayment
The overpayment is another one for sellers to watch out for. It usually relates to the sale of items or services, often through classified ads.
The scammer sends you payment for whatever you are selling but sends too much. They ask you to refund the difference. In the meantime (hopefully for them, it’s after you send the money) their payment is canceled or retracted. So you’ve received no payment at all but have issued them a partial refund.
How to recognize scams
Since online scams are popping up so frequently, with many probably yet to be uncovered, it’s impossible to list them all here. This just makes it even more important that you watch out for tell-tale signs.
Recognizing secure sites
Many scams require a legitimate-looking website for victims to interact with and provide the information the scammer is looking for.
Since virtually anyone can purchase almost any domain name and then visually re-create any site on the planet, how can anyone be sure they’re using a safe site? This is a good question which we cover in detail in a post about recognizing scam or fake websites.
Some techniques are technical, such as checking that the domain name shown in your browser’s address bar matches the site you think you’re visiting. Others are more holistic such as verifying the site has legitimate contact information on it and isn’t riddled with spelling errors.
There is no single silver bullet that can indicate the trustworthiness of a site, but there are a number of things you can check that will help you make a judgment call.
Spotting a fake or spoof phishing email
As Mr. Miyagi said in the movie Karate Kid, “best block, no be there”. In internet scams, the best defense is to simply not get tricked in the first place. Scammers can be clever, though, and it can be hard to spot the fake phishing emails sometimes.
In a dedicated post, we cover tips to help you spot a fake, spoof, or phishing email.
How to report a scam
In the best case scenario, you realize you’re being scammed before it’s too late. If this happens, you should get in touch with the operators of the platform on which you encountered the scammer, if applicable. This way, they can at least kick them off the site and hopefully prevent someone else from being scammed.
Depending on the nature of the scam, it may also be worth reporting it to your local police division. This should definitely be a port of call if you’ve lost money, have been coerced into doing something illegal yourself, or are being extorted.
Another action you should take is to report the incident to the fraud center in your country of residence:
- US: FBI’s Internet Crime Complaint Center
- Canada: Canadian Anti-Fraud Centre
- Australia: ACCC Scamwatch
- UK: Action Fraud
Victims of online scams are often too embarrassed to come forward. However, the more of these incidents that are reported, the better the chance law enforcement will have of shutting down the perpetrators, and the more aware others will be of the dangers lurking online.
Popular articles: