DoS vs DDoS
A Denial of Service (DoS) attack is a cyberattack designed to overwhelm a system, server, or network by flooding it with traffic or sending information that triggers a crash. The goal is to render the target system inoperable, denying legitimate users access to services. In a DoS attack, a single system, often controlled by a malicious actor, executes the assault.
In contrast, a Distributed Denial of Service (DDoS) attack amplifies the scale by leveraging multiple systems to launch the attack simultaneously. These systems, usually part of a botnet, can flood the target with significantly more traffic, making it much harder to mitigate. Botnets consist of compromised devices that hackers control remotely, turning them into unwitting participants in the attack.
The primary difference between DoS and DDoS attacks lies in the number of sources involved. While a DoS attack originates from a single point, a DDoS attack is distributed, making it more difficult to trace and counter. DDoS attacks often involve a larger volume of traffic and are typically more sophisticated, requiring advanced tools and strategies to prevent or mitigate.
Both types of attacks aim to disrupt services, but DDoS attacks pose a greater challenge due to their scale and complexity. Effective prevention and mitigation require robust security measures such as traffic filtering, load balancing, and specialized DDoS protection services.
Further in this post, we review the two best Edge Services Vendors:
- Sucuri Edge Services (LEARN MORE) A web application firewall service implemented as a proxy located in one of 28 data centers around the world. The Sucuri solution is able to absorb any type of DDoS attack.
- Indusface AppTrana This protection system for internet-facing assets absorbs large DoS and DDoS attacks, forwarding genuine traffic to you. This is a cloud-based system.
What is a DoS Attack?
A DoS attack is a denial of service attack where a computer is used to flood a server with TCP and UDP packets.
During this type of attack, the service is put out of action as the packets sent over the network to overload the server’s capabilities and make the server unavailable to other devices and users throughout the network. DoS attacks are used to shut down individual machines and networks so that they can’t be used by other users.
There are a number of different ways that DoS attacks can be used. These include the following:
- Buffer overflow attacks – This type of attack is the most common DOS attack experienced. Under this attack, the attacker overloads a network address with traffic so that it is put out of use.
- Ping of Death or ICMP flood – An ICMP flood attack is used to take unconfigured or misconfigured network devices and uses them to send spoof packets to ping every computer within the target network. This is also known as a ping of death (POD) attack.
- SYN flood – SYN flood attacks send requests to connect to a server but don’t complete the handshake. The end result is that the network becomes inundated with connection requests that prevent anyone from connecting to the network.
- Teardrop Attack – During a teardrop DoS attack, an attacker sends IP data packet fragments to a network. The network then attempts to recompile these fragments into their original packets. The process of compiling these fragments exhausts the system and it ends up crashing. It crashes because the fields are designed to confuse the system so that it can not put them back together.
The ease with which DoS attacks can be coordinated has meant that they have become one of the most pervasive cybersecurity threats that modern organizations have to face. DoS attacks are simple but effective and can bring about devastating damage to the companies or individuals they are aimed at. With one attack, an organization can be put out of action for days or even weeks.
The time an organization spends offline adds up. Being unable to access the network costs organizations thousands every year. Data may not be lost but the disruption to service and downtime can be massive. Preventing DoS attacks is one of the basic requirements of staying protected in the modern age.
Further reading: What is ICMP?
What is a DDoS Attack?
A DDoS attack is one of the most common types of DoS attack in use today. During a DDoS attack, multiple systems target a single system with malicious traffic. By using multiple locations to attack the system the attacker can put the system offline more easily.
The reason for this is that there is a larger number of machines at the attackers’ disposal and it becomes difficult for the victim to pinpoint the origin of the attack.
In addition, using a DDoS attack makes it more complicated for the victim to recover. Nine times out of ten the systems used to execute DDoS attacks have been compromised so that the attacker can launch attacks remotely through the use of slave computers. These slave computers are referred to as zombies or bots.
These bots form a network of connected devices called a botnet that is managed by the attacker through a command and control server. The command and control server allows the attacker or botmaster to coordinate attacks. Botnets can be made up of anywhere between a handful of bots to hundreds of different bots.
See also: Understanding DoS and DDoS attacks
Broad Types of DoS and DDoS Attacks
There are a number of broad categories that DoS attacks fall into for taking networks offline. These come in the form of:
- Volumetric Attacks Volumetric attacks are classified as any form of attack where a target network’s bandwidth resources are deliberately consumed by an attacker. Once network bandwidth has been consumed it is unavailable to legitimate devices and users within the network. Volumetric attacks occur when the attacker floods network devices with ICMP echo requests until there is no more bandwidth available.
- Fragmentation Attacks Fragmentation attacks are any kind of attack that forces a network to reassemble manipulated network packets. During a fragmentation attack the attacker sends manipulated packets to a network so that once the network tries to reassemble them, they can’t be reassembled. This is because the packets have more packet header information than is permitted. The end result is packet headers which are too large to reassemble in bulk.
- TCP-State Exhaustion Attacks In a TCP-State Exhaustion attack the attacker targets a web server or firewall in an attempt to limit the number of connections that they can make. The idea behind this style of attack is to push the device to the limit of the number of concurrent connections.
- Application Layer Attacks Application layer or Layer 7 attacks are attacks that target applications or servers in an attempt to use up resources by creating as many processes and transactions possible. Application layer attacks are particularly difficult to detect and address because they don’t need many machines to launch an attack.
Related Posts: Best Anti-DDoS Tools & Protection Services
Most Common Forms of DDoS Attacks
As you can see, DDoS attacks are the more complex of the two threats because they use a range of devices that increase the severity of attacks. Being attacked by one computer is not the same as being attacked by a botnet of one hundred devices!
Part of being prepared for DDoS attacks is being familiar with as many different attack forms as you can. In this section, we’re going to look at these in further detail so you can see how these attacks are used to damage enterprise networks.
DDoS attacks can come in various forms including:
- Ping of Death During a Ping of Death (POD) attack the attacker sends multiple pings to one computer. POD attacks use manipulated packets to send packets to the network which have IP packets that are larger than the maximum packet length. These illegitimate packets are sent as fragments. Once the victim’s network attempts to reassemble these packets network resources are used up, they are unavailable to legitimate packets. This grinds the target network to a halt and takes it out of action completely.
- UDP Floods A UDP flood is a DDoS attack that floods the victim network with User Datagram Protocol (UDP) packets. The attack works by flooding ports on a remote host so that the host keeps looking for an application listening at the port. When the host discovers that there is no application it replies with a packet that says the destination wasn’t reachable. This consumes network resources and means that other devices can’t connect properly.
- Ping Flood Much like a UDP flood attack, a ping flood attack uses ICMP Echo Request or ping packets to derail a network’s service. The attacker sends these packets rapidly without waiting for a reply in an attempt to make the target network unreachable through brute force. These attacks are particularly concerning because bandwidth is consumed both ways with attacked servers trying to reply with their own ICMP Echo Reply packets. The end result is a decline in speed across the entire network.
- SYN Flood SYN Flood attacks are another type of DoS attack where the attacker uses the TCP connection sequence to make the victim’s network unavailable. The attacker sends SYN requests to the victim’s network which then responds with a SYN-ACK response. The sender is then supposed to respond with an ACK response but instead, the attacker doesn’t respond (or uses a spoofed source IP address to send SYN requests instead). Every request that goes unanswered takes up network resources until no devices can make a connection.
- Slowloris Slowloris is a type of DDoS attack software that was originally developed by Robert Hansen or RSnake to take down web servers. A Slowloris attack occurs when the attacker sends partial HTTP requests with no intention of completing them. To keep the attack going, Slowloris periodically sends HTTP headers for each request to keep the computer network’s resources tied up. This continues until the server can’t make any more connections. This form of attack is used by attackers because it doesn’t require any bandwidth.
- HTTP Flood In a HTTP Flood attack the attacker users HTTP GET or POST requests to launch an assault on an individual web server or application. HTTP floods are a Layer 7 attack and don’t use malformed or spoofed packets. Attackers use this type of attack because they require less bandwidth than other attacks to take the victim’s network out of operation.
- Zero-Day Attacks Zero-Day attacks are attacks that exploit vulnerabilities that have yet to be discovered. This is a blanket term for attacks that could be faced in the future. These types of attacks can be particularly devastating because the victim has no specific way to prepare for them before experiencing a live attack.
DoS vs DDoS: What’s the Difference?
The key difference between DoS and DDoS attacks is that the latter uses multiple internet connections to put the victim’s computer network offline whereas the former uses a single connection. DDoS attacks are more difficult to detect because they are launched from multiple locations so that the victim can’t tell the origin of the attack. Another key difference is the volume of attack leveraged, as DDoS attacks allow the attacker to send massive volumes of traffic to the target network.
It is important to note that DDoS attacks are executed differently to DoS attacks as well. DDoS attacks are executed through the use of botnets or networks of devices under the control of an attacker. In contrast, DoS attacks are generally launched through the use of a script or a DoS tool like Low Orbit Ion Cannon.
Why do DoS and DDoS Attacks Occur?
Whether it is a DoS or DDoS attack, there are many nefarious reasons why an attacker would want to put a business offline. In this section, we’ll look at some of the most common reasons why DoS attacks are used to attack enterprises. Common reasons include:
- Ransom Perhaps the most common reason for DDoS attacks is to extort a ransom. Once an attack has been completed successfully the attackers will then demand a ransom to halt the attack and get the network back online. It isn’t advised to pay these ransoms because there is no guarantee that the business will be restored to full operation.
- Malicious Competitors Malicious competitors looking to take a business out of operation are another possible reason for DDoS attacks to take place. By taking an enterprise’s network down a competitor can attempt to steal your customers away from you. This is thought to be particularly common within the online gambling community where competitors will try to put each other offline to gain a competitive advantage.
- Hacktivism In many cases, the motivation for an attack won’t be financial but personal and political. It is not uncommon for hacktivist groups to put government and enterprise sites offline to mark their opposition. This can be for any reason that the attacker deems to be important but often occurs due to political motivations.
- Causing Trouble Many attackers simply like causing trouble for personal users and networks. It is no secret that cyber attackers find it amusing to put organizations offline. For many attackers, DDoS attacks offer a way to prank people. Many see these attacks as ‘victimless’ which is unfortunate given the amount of money that a successful attack can cost an organization.
- Disgruntled Employees Another common reason for cyber attacks is disgruntled employees or ex-employees. If the person has a grievance against your organization then a DDoS attack can be an effective way to get back at you. While the majority of employees handle grievances maturely there are still a minority who use these attacks to damage an organization they have personal issues with.
How to Prevent DoS and DDoS attacks
Even though DOS attacks are a constant threat to modern organizations, there are a number of different steps that you can take to stay protected before and after an attack. Before implementing a protection strategy it is vital to recognize that you won’t be able to prevent every DoS attack that comes your way. That being said, you will be able to minimize the damage of a successful attack that comes your way.
Minimizing the damage of incoming attacks comes down to three things:
-
-
- Preemptive Measures
- Test Run DOS Attacks
- Post-attack Response
-
Preemptive measures, like network monitoring, are intended to help you identify attacks before they take your system offline and act as a barrier towards being attacked. Likewise, test running DoS attacks allows you to test your defenses against DoS attacks and refine your overall strategy. Your post-attack response will determine how much damage a DoS attack does and is a strategy to get your organization back up and running after a successful attack.
Preemptive Measures: Network Monitoring
Monitoring your network traffic is one of the best preemptive steps you can take. Monitoring regular traffic will allow you to see the signs of an attack before the service goes down completely. By monitoring your traffic you’ll be able to take action the moment you see unusual data traffic levels or an unrecognized IP address. This can be the difference between being taken offline or staying up.
Before executing an all-out attack, most attackers will test your network with a few packets before launching the full attack. Monitoring your network traffic will allow you to monitor for these small signs and detect them early so that you can keep your service online and avoid the costs of unexpected downtime.
See also: 25 best network monitors
Test Run DoS Attacks
Unfortunately, you won’t be able to prevent every DoS attack that comes your way. However, you can make sure you’re prepared once an attack arrives. One of the most direct ways to do this is to simulate DDoS attacks against your own network. Simulating an attack allows you to test out your current prevention methods and helps to build up some real-time prevention strategies that can save lots of money if a real attack comes your way.
Post-Attack Response: Create a Plan
If an attack gets off the ground then you need to have a plan ready to run damage control. A clear plan can be the difference between an attack that is inconvenient and one that is devastating. As part of a plan, you want to designate roles to members of your team who will be responsible for responding once an attack happens. This includes designing procedures for customer support so that customers aren’t left high and dry while you’re dealing with technical concerns.
Edge Services Vs DDoS Attacks
Undoubtedly one of the most effective ways to meet DDoS attacks head-on is to utilize an edge service. An edge service solution like StackPath or Sucuri can sit at the edge of your network and intercept DDoS attacks before they take effect. In this section, we’re going to look at how these solutions can keep your network safe from unscrupulous attackers.
Our methodology for selecting a DDoS protection system
We reviewed the market for DDoS protection services and analyzed the options based on the following criteria:
- A service that will host your IP address
- Large traffic volume capacity
- A VPN to pass on clean traffic
- A cloud-based service that hides your real IP address
- A reporting system that will show you the attacks that occurred
- A free trial or a demo service that will allow a no-cost assessment
- Value for money represented by an effective DDoS attack blocker at a reasonable price
Using this set of criteria, we looked for edge services that mean malicious traffic surges don’t even make it to your own Web server. The DDoS protection system should also have high speeds for passing genuine traffic.
Sucuri Edge Services
Another leading provider of DDoS prevention solutions is Sucuri’s DDoS Protection & Mitigation service. Sucuri is adept at handling layer 7 HTTP floods but can also prevent TCP SYN floods, ICMP floods, Slowloris, UDP floods, HTTP cache bypass, and amplified DNS DDoS to name a few.
Key Features:
- DDoS Protection & Mitigation
- Layer 7 HTTP flood handling
- TCP SYN, ICMP, UDP flood prevention
- Globally distributed network
- No attack size cap
Sucuri has a website application firewall approach that has a globally distributed network with 28 points of presence. There is also no cap on attack size so no matter what happens you stay protected. The Sucuri WAF is a cloud-based SaaS solution that intercepts HTTP/HTTPS requests that are sent to your website.
Why do we recommend it?
Sucuri Edge Services is a very similar package to the StackPath system. This service is a proxy and it receives all of the traffic intended for your Web server. The tool filters out malicious traffic and blocks traffic floods while passing through genuine traffic.
One particularly useful feature is the ability to identify if traffic is coming from the browser of a legitimate user or a script being used by an attacker. This ensures that everyday users can still access the site and its online services while malicious users are blocked from launching their attacks. Sucuri offers various plans for its edge services according to your network needs.
Who is it recommended for?
Businesses that run websites should trial both the StackPath service and the Sucruri edge package. Both of these tools offer comprehensive protection against DoS and DDoS attacks.
Pros:
- Can prevent numerous attacks such HTTP, TCP, ICMP, UDP, and SYN floods
- Uses simple visuals and reporting to help illustrate risk and threats
- Leverages a cloud-based WAF to stop application layer attacks
- Can distinguish between automated and real user behavior
Cons:
- Designed specifically for businesses, not home users or small labs
Indusface AppTrana Edge Services
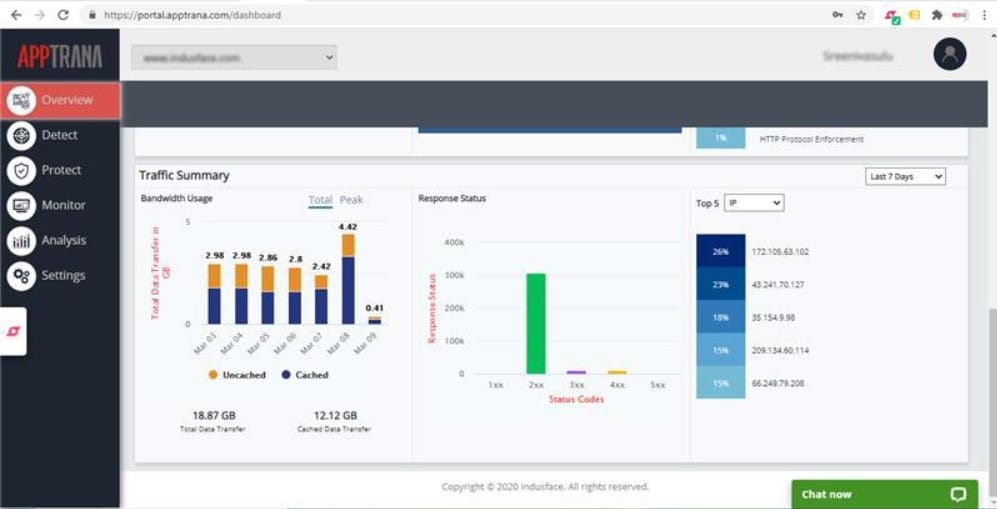
Indusface AppTrana is a proxy-based firewall that blocks DoS and DDoS traffic before it gets to your servers. It is able to filter out attacks implemented at Layers 3, 4, and 7. This system is particularly useful for protecting websites because it is integrated into a Web application firewall service.
Key Features:
- Proxy-based firewall
- Protects against Layers 3, 4, 7 attacks
- Integrated Web application firewall
- 2.3 Tbps AWS server capacity
- Handles 700,000 requests/second
The most impressive mechanism that Indusface AppTrana uses to block DoS and DDoS attacks is capacity. The service is hosted on AWS servers and has a 2.3 Tbps capacity to absorb the largest traffic attacks without losing the ability to accept new connection requests. It can serve 700,000 requests per second.
Why do we recommend it?
Indusface AppTrana competes well with Sucuri and StackPath. As with those two rival systems, AppTrana provides a package of edge services that protects your internet-facing systems against attack.
The full AppTrana package is a Web application firewall that protects APIs, serverless systems, and mobile apps as well as websites. You can opt to get access to the WAF alone or sign up for a managed service. In either case, you get full performance statistics in the system console.
The Indusface system provides you with all the tools you need to protect your Web assets. The tool takes two or three minutes to set up when you take out a subscription and the backend connections from the edge service to your servers are protected by encryption. The service hosts your SSL certificate and deals with connection encryption for external requests, which enables the threat scanner to look inside all the contents of incoming packets as well as their headers.
Who is it recommended for?
Indusface AppTrana Premium Edition is a good solution for businesses that have Web assets but no cybersecurity analysts on the payroll to manage their protection. The Advanced Edition makes the package accessible to businesses that already have a cybersecurity support team.
Pros:
- Blocks ICMP/UDP, SYN, and HTTP flood attacks, reflection attacks, and slow/low attacks
- Integrated into a WAF
- Includes intelligent bot detection and management
- Web content caching
Cons:
- No self-hosted option
Indusface offers three plans with a platform of tools, called the Advanced Edition, and a fully managed service on top of those tools in the Premium Edition. The third option, called the Enterprise Edition, is a custom package. Indusface offers the AppTrana Advanced service on a 14-day free trial.
See also: The Best Edge Services Providers
DoS vs DDoS Attacks: A Manageable Menace
There are few service attacks as concerning as DoS attacks to modern organizations. While having data stolen can be extremely damaging, having your service terminated by a brute force attack brings with it a whole host of other complications that need to be dealt with. Just a day’s worth of downtime can have a substantial financial impact on an organization.
Having a familiarity with the types of DoS and DDoS attacks that you can encounter will go a long way towards minimizing the damage of attacks. At the very least you want to make sure that you have a network monitoring tool so that you can detect unusual data traffic that indicates a potential attack. However, if you’re serious about addressing DoS attacks then you need to make sure that you have a plan to respond after the attack.
DoS attacks have become one of the most popular forms of cyber-attack in the world because they are easy to execute. As such it is incredibly important to be proactive and implement as many measures as you can to prevent attacks and respond to attacks if they are successful. In doing so, you will limit your losses and leave yourself in a position where you can return to normal operation as quickly as possible.
Dos Vs DDoS Attacks FAQs
How to improve security using a Content Delivery Network (CDN)?
A content delivery network (CDN) stores copies of website content, including entire web pages on servers around the world. Visitors to the site actually get those web pages from a CDN server and not your infrastructure. So, Denial of Service attacks get directed at the CDN server. These servers have a great deal of capacity and are able to absorb large volumes of bogus connection requests.
What is the detection process for a DDoS attack?
A DDoS attack involves high volumes of traffic from a large number of sources. DDoS detection software will notice a surge in connection requests. DDoS defense system sample connection requests randomly rather than inspecting each one. When typical DDoS strategies are detected, mitigation processes will be triggered.
Can you trace a DDoS attack?
The devastating tactics of a DDoS attack lie in its ability to overwhelm a web server with more connection requests than it can handle. Thus, there is little time during an attack to trace the source of attacks. Also, there is little point in doing that as each zombie computer usually only sends one request. Thus, if you got to the source of a malformed connection message, you wouldn’t prevent thousands of other computers sending requests at that moment. Most of the source IP addresses on DDoS connection requests are genuine, but they do not belong to the computer of the real attacker.
Does a DDoS attack damage hardware?
No. DDoS attacks are designed to push routers, load balancers, and servers to their performance limits. Those limits mean that a device can never be forced into a physical failure through factors such as overheating.
See also: 100+ Terrifying Cybercrime and Cybersecurity Statistics & Trends
Further Reading:






The role of DOS attack, single attacker target single system or single server at time this called dos attack.
The role of DDOS attack, the malicious users tries to make a machine or network resource which is unviable to user.
During a DoS attack, multiple systems target a single system with a DoS attack. is it wrong?? ( During a DoS attack or DDoS). – what is right?
Hi Prajjwal,
A DoS attack uses a single computer to launch an attack, and a DDoS uses multiple computers. So it’s during a DDoS attack that multiple systems target a single system. I hope that helps.
“A DoS attack is a denial of service attack where a computer (or computers) is used to flood a server with TCP and UDP packets. A DDoS attack is where multiple systems target a single system with a DoS attack. The targeted network is then bombarded with packets from multiple locations.”
Just a quick point, as soon as a DoS attack uses more than one computer doesn’t it then automatically become DDoS just by simply by your own definition?
Thanks for the heads-up! We’ve changed that now.