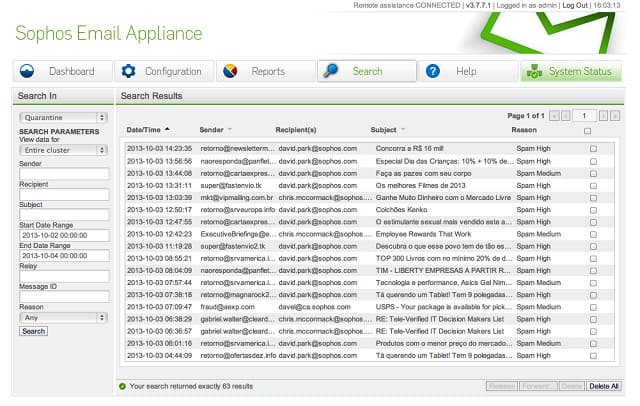
Email presents a security weakness. Attachments can contain malware and phishing scams can trick employees into disclosing passwords. Hackers are becoming increasingly sophisticated in getting into business networks through email, so you need to lock down that security weakness. Email monitoring software has developed in pace with threats, so now there are some very sophisticated email protection systems on the market.
Failure to monitor email can lose your company data protection standards accreditation and that can be a threat to winning new business. So, this is a serious issue that needs to be addressed.
Here is our list of the best email monitoring software:
- Guardz EDITOR’S CHOICE This security monitoring platform includes scanning for threats to endpoint and cloud data storage. Its email security monitoring facility automatically removes phishing attempts, malware, spam, and impersonation scams from user mailboxes. Get a 14-day free trial.
- Fortra Agari Email Security (GET DEMO) This email authentication service stamps out impersonation and phishing attempts by recording genuine emails sent on a domain. This is a cloud-based service and you can access a demo online.
- ManageEngine Endpoint DLP Plus (FREE TRIAL) This data loss prevention system includes email scanning for outbound emails through a plug-in for Outlook. Available for Windows Server. Get a 30-day free trial.
- TitanHQ Email Security (FREE TRIAL) Online service that blocks spam, malicious links, phishing, malware, and spyware. Start a 14-day free trial.
- Teramind Email Monitoring Part of the Teramind user monitoring suite of services, this tool monitors both incoming and outgoing emails for malicious activity.
- Mimecast Secure Email Gateway This cloud-based email protection system roots out malware and phishing attempts.
- Proofpoint Essentials Online security system aimed at SMB. Protects email and social media accounts.
- N-able SpamExperts Aimed at ISPs and web hosting companies, this on-premises software adds an extra security service to clients.
- N-able Mail Assure Cloud-based email security and archiving package is structured for use by MSPs when protecting the systems of their clients.
- Trustifi Inbound Shield The cloud system is a referencer service that scans all incoming emails for threats in the form of scam text, infected attachments, and malicious links.
- Topsec Email Security Blocks spam, viruses, malware, and ransomware, identifies phishing and quarantines questionable email content.
- Barracuda Email Security Gateway A hardware-based email that blocks incoming threats and outgoing data theft attempts. A cloud-based version is also available.
- modusCloud Cloud-based protection for Microsoft Outlook and Office 365. Includes archiving and email encryption as well as spam, phishing, malware, and link filtering.
- Hornetsecurity Spam and Malware Protection An online email filter that blocks spam and malware.
- Sophos Email Security Cloud-based email security solution that uses AI to block phishing attempts as well as spam and malware.
The number of email monitoring systems available has exploded in recent years, so it can take a lot of time to research the industry to find the right solution for your business. We have cut down the time that the task will take you by identifying the best email security monitoring tools available today.
The Best Email Monitoring Software
All of these solutions are cloud-based while a couple also offers an appliance-resident alternative.
Our methodology for selecting an email monitoring package
We reviewed the market for email monitoring software and analyzed tools based on the following criteria:
- Spam filters and customizable content filtering rules
- Blocks on malware
- Phishing attempt detection
- Scanning of URLs embedded in emails
- Attachment sandboxing
- A free trial or a demo for a no-risk assessment period
- Value for money is represented by a comprehensive tool offered at a fair price
With these selection criteria in mind, we have investigated a selection of tools that are excellent at monitoring emails.
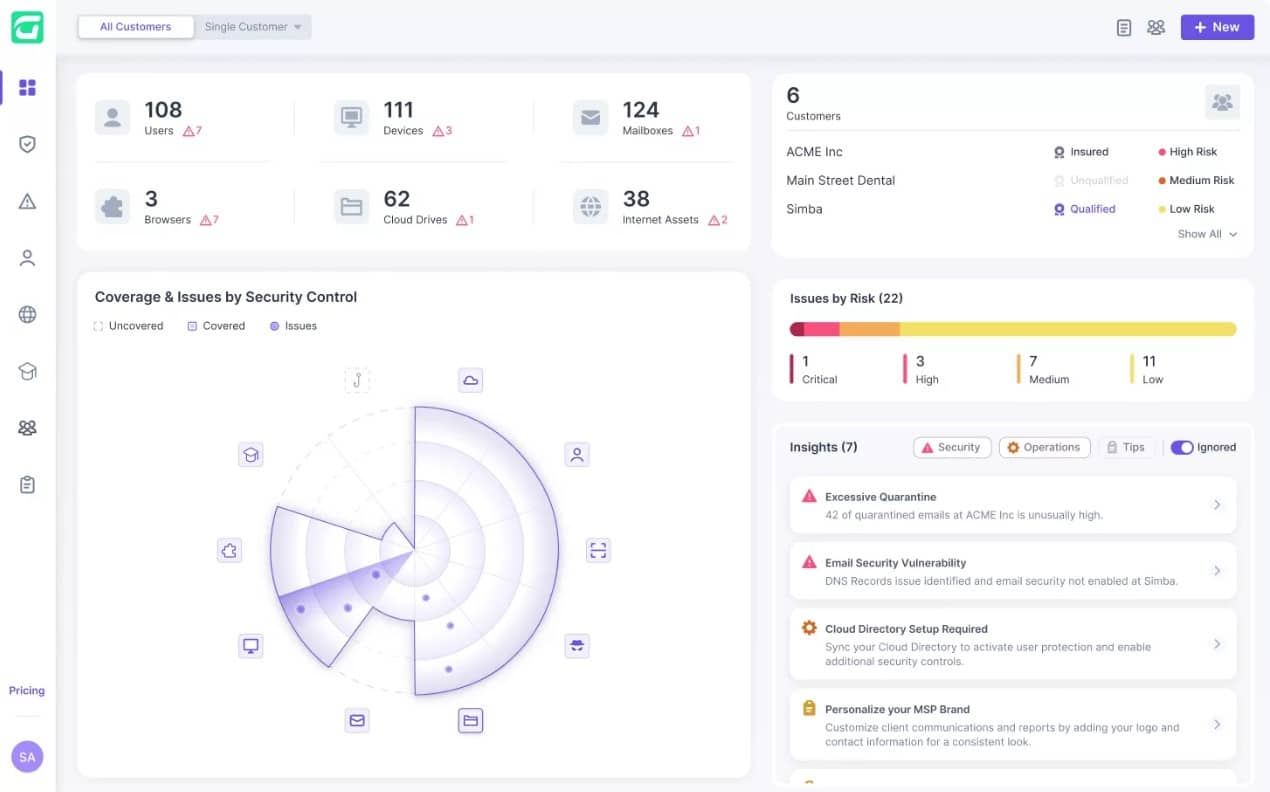
1. Guardz (FREE TRIAL)
Guardz provides email security monitoring as part of a platform of system-wide security tools. Email is a major route into business systems for malware, ransomware, and data thieves, so scanning emails for threats is a major part of the protection system offered by Guardz.
Key Features:
- Email Scanning: Scans incoming emails for potential threats.
- Quarantine Malicious Emails: Removes and quarantines malicious emails.
- Outlook/Exchange Server Protection: Guards email systems like Outlook and Exchange Server.
- Gmail Account Security: Scans and protects Gmail accounts.
- Data Protection: Safeguards data on endpoints and in the cloud.
Why do we recommend it?
Guardz protects data from theft or interference by identifying tricks and credential theft attempts that occur in email scams. Hackers will try to steal data as well by posing as a manager, and Guardz spots those campaigns. Malicious emails are moved to quarantine where they can be examined by an analyst.
The Guardz cloud platform is able to protect endpoints and also other cloud platforms. Specifically, the service monitors emails into the Gmail unit of Google Workspace and the Outlook/Exchange Server systems in Microsoft 365. The cloud storage parts of those two platforms are also monitored for security breaches – both OneDrive and Google Drive.
The dashboard for a Guardz account is accessible through any standard web browser. So, it can be accessed from anywhere. The package is intended for use by managed service providers (MSP) as part of their work to monitor and manage the systems of their clients. The screens for the dashboard can be branded with the MSP’s logos and name.
Who is it recommended for?
The Guardz system is advertised to companies for their own protection but the company insists that its services should be administered by managed service providers. An account can cater to just one user account and goes up to cover large organizations. Interested companies can choose an MSP independently or pick one from a list of recommendations on the Guardz site.
Pros:
- Cloud-Based Operation: No need for on-premise hosting, as it operates on the cloud.
- Attack Summary Screen: Provides a summary screen for viewing attack details.
- Email Attack Blocking: Effectively blocks threats originating from emails.
- Quarantine Management: Offers options to assess and manage quarantined emails.
- Automated Remediation: Provides automated solutions for threat protection.
Cons:
- MSP Dependency: Requires managed service providers to operate accounts.
Although Guardz advertises to companies on its website, it won’t accept accounts directly from them. The company will only operate through managed service providers. You can get a look at Guardz by accessing a 14-day free trial.
EDITOR'S CHOICE
Guardz is our top pick for email monitoring software because it blocks hacker access that is frequently implemented through email tricks. Data thieves will use phishing to trick users into disclosing their account credentials, con artists impersonate managers to persuade clerks to wire money, ransomware and malware get onto systems through email attachments, and inboxes get flooded by spam. The Guardz system removes all of those threats and keeps businesses safe.
Download: Get a 14-day FREE Trial
Official Site: https://guardz.com/free_trial
OS: Cloud-based
2. Fortra Agari Email Security (GET A DEMO)
Fortra Agari Email Security operates from the cloud and acts as a validator for emails that are sent from addresses on your company’s domain. The package of checks performed by this system is known as a domain-based message authentication, reporting, and conformance (DMARC) service. It records valid emails when they are sent and participating email servers check with Agari for every received email to make sure they are on that list before forwarding them to the recipient’s inbox.
Key Features:
- DMARC Protection: Implements DMARC standards to prevent email spoofing and protects your brand from phishing attacks.
- Cloud Email Protection: Advanced data science and AI to detect and block inbound threats, including BEC, spear phishing, and impersonation attacks.
- Suspicious Email Analysis: Rapidly detects, responds to, and remediates email threats.
- Threat Intelligence Service: Provides real-time threat intelligence that warns of current email cyber attack campaigns.
Why do we recommend it?
Fortra Agari Email Security combats a range of scammer tricks. It also looks into the content of emails for links to sites and rejects mail if it leads to a phishing page. Phishing commonly directs recipients to an impersonator site to enter credentials and so this can be a threat to the personal security of employees as well as a method to steal corporate account details.
When a user in your company sends out an email on your domain, that event is recorded by Agari. The receiving mail server checks with Agari if the incoming mail is on the system’s list. If it isn’t that means the email has a spoofed address on it. Agari notes the failed reference and compiles analysis data for the protected domain. The receiving email server will bin the email, so the target of the scam never learns of its existence.
Agari also updates two global scammer blacklists. The first is a list of the IP addresses that phishing emails are sent from. The second is a list of phishing websites, which the Agari system gets from the receiving email servers that scan the contents of incoming emails.
This system also examines internal emails displaying the protected company’s domain in their email addresses. This combats a major technique of business email compromise where a scammer impersonates a manager and instructs an administrator to make a payment.
Who is it recommended for?
All companies are at risk from email trickery and so this is an important tool for any enterprise. The system blocks attempts to steal credentials and fool employees into making payments to con artists. The service is hosted in the cloud and integrates easily into email server systems. It has a special integration routine for on-premises Exchange Server and the cloud-based Microsoft 365.
Pros:
- Security Integrations: Integrates with leading SIEM and SOAR platforms for enhanced threat detection and response.
- Automated Response: Automates the process of DMARC email authentication and enforcement.
- Email Authentication: Ensures all third-party senders conform to your email standards and authenticates legitimate email sources.
- Reporting & Analytics: Aggregates DMARC data and provides detailed reports and analytics to help you make informed decisions.
Cons:
- No Self-Hosting Option: Some customers, especially in the financial sector, are hesitant to use a cloud-based solution due to data privacy concerns.
Fortra Agari Email Security provides its DMARC service from the cloud. It needs to be integrated into your email server through that system’s settings. There is no free trial for the DMARC service, but you can access a demo.
3. ManageEngine Endpoint DLP Plus (FREE TRIAL)
ManageEngine Endpoint DLP Plus is a system-wide data protection system that is designed to prevent the theft, corruption, and misuse of personally identifiable information (PII). As part of this remit, the package provides an email scanner that aims to prevent PII from being mailed out of the company.
Key Features:
- Outlook Plug-In: Integrates directly with Outlook for seamless email scanning.
- Email PII Scanning: Scans emails and attachments for personally identifiable information (PII).
- Whitelisting: Allows whitelisting of approved email destinations to streamline compliance.
- Compliance Management: Supports compliance with GDPR, PCI DSS, and HIPAA.
Why do we recommend it?
ManageEngine Endpoint DLP Plus provides automated scanning of email systems to prevent PII from being sent out of the protected business. The Endpoint DLP Plus system scans and classifies PII on data stores and creates a data inventory. The tool doesn’t reference that database but reruns its PII detection methods on each email.
The email scanner looks through the body of emails as well as attachments. It performs pattern matching and data fingerprinting to look for specific types of data. The exact category of data that the system searches for depends on how you set up the package – you specify which standards you are aiming for.
The service also looks at the intended recipient of each email. The easiest way a business can manage the process of assessing recipients is to set up a whitelist. This creates a list of approved correspondents. The DLP service has three modes and one of them allows emails with sensitive data to be sent only to those whitelisted domains.
Who is it recommended for?
Any business that holds PII needs this package. The service is suitable for compliance with PCI DSS, HIPAA, and GDPR. There is a free edition of the package that has all of the features of the paid package but is limited to monitoring up to 25 endpoints.
Pros:
- Comprehensive DLP Solution: Part of a larger data loss prevention system that protects PII across all endpoints.
- Free Edition Available: Offers a free version that monitors up to 25 endpoints.
- Customizable Email Control: Options to log, block, or conditionally allow emails containing PII.
- Targeted Email Monitoring: Focuses only on emails with PII, reducing unnecessary alerts.
Cons:
- No Linux Support: Does not offer a version compatible with Linux systems.
ManageEngine Endpoint DLP Plus is available for Windows Server and you can assess the system with a 30-day free trial.
4. TitanHQ Email Security (FREE TRIAL)
Email Security is a product of TitanHQ. Its main activities block spam, malware, infected attachments, malicious links, and phishing attempts. The service also performs recipient verification and scanning of outbound emails to prevent data disclosure. The system deploys AI-based predictive technology to spot zero-day attacks without relying on a threat intelligence database.
Key Features:
- Spam, Malware, and Phishing Blocker: Effectively blocks spam, malware, infected attachments, and phishing attempts.
- Correspondent Verification: Verifies the legitimacy of email senders to prevent spoofing.
- Attachment Sandboxing: Uses sandboxing to safely examine attachments for hidden threats.
Why do we recommend it?
Email Security is one of a series of email protection services that are offered on the TitanHQ platform. This tool, as the name suggests, focuses on identifying and removing spam emails. This system also blocks malware and ransomware. It verifies URLs in emails and removes malicious links.
The service is created through several different security tactics, which include the use of blacklists that automatically block emails that arrive from known hacker and scammer addresses. The system is able to spot spoofing and includes sandboxing to protect against advanced email attacks. The service can also be set to implement your company’s content policies, blocking emails that contain inappropriate text or images.
Who is it recommended for?
Email Security is offered as an appliance for on-premises deployment and there is also a cloud-based edition. The service is available in a version just for SaaS Microsoft 365 email protection. TitanHQ offers a version of Email Security for managed service providers. A higher plan, called Email Security Plus, will also block phishing attempts.
Pros:
- Informative Dashboard: Simple yet informative dashboard displaying key email metrics.
- Comprehensive Protection: Protects against malicious links and attachments.
- Payload Sandboxing: Can ‘detonate’ payloads in a sandbox environment to reveal hidden viruses.
Cons:
- MSP Limitations: Not ideally suited for resellers or managed service providers (MSPs).
- 2FA Enforcement: Would benefit from enforced two-factor authentication (2FA) for added security.
- Outlook Plugin Stability: The Outlook plugin may occasionally cause the application to crash.
TitanHQ offers Email Security on a 14-day free trial.
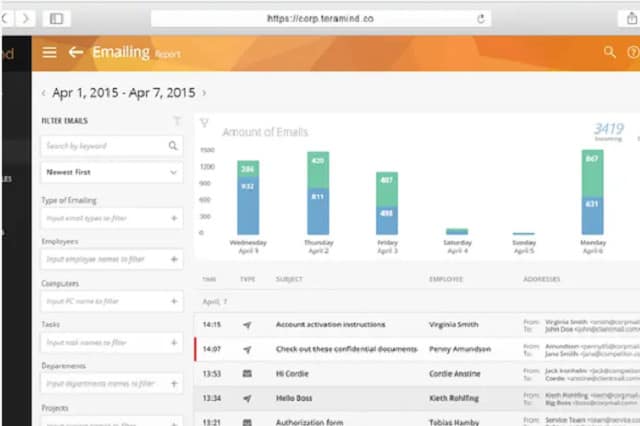
5. Teramind Email Monitoring
Teramind is an insider threat protection system that can be accessed as a cloud service or installed as on-premises software. The Teramind system is available in three editions: Starter, UAM, and DLP. The email monitoring system is included in the UAM and DLP packages.
Key Features:
- Outgoing Email Monitoring: Tracks and analyzes all outgoing emails.
- Data Transfer Blocking: Prevents unauthorized data transfers via email.
- Comprehensive Data Controls: Implements various data control policies.
- Insider Threat Detection: Identifies and mitigates internal threats.
Why do we recommend it?
Teramind Email Monitoring is part of the Teramind Data Loss Prevention platform. This package tries to lock down data movements and applies different rules for different user accounts. That is, an account that is authorized to handle specific types of data will not be blocked for that type of data.
As an employee monitoring system, this email threat detector is completely different from all of the other email protection services on this list. Rather than looking for spam and phishing, this system blocks disclosure. So, if a phishing email comes in, the response containing a password gets blocked rather than the original scam request.
The main focus of this email tool is to prevent data disclosure in outgoing emails. As an extra feature, not included with the other systems in this list, this service detects subterfuge and employee sabotage. The service can also measure response times of client-facing staff to incoming customer emails.
Who is it recommended for?
Email monitoring is not available as a separate unit. Instead, it is integrated into the top three of the four Teramind plans, which provide user activity monitoring and data loss prevention. The software for these subscription plans can be run on your server, on a cloud platform, or accessed as a SaaS package.
Pros:
- User-Friendly Interface: Intuitive and easy to navigate.
- Visual Reporting: Provides highly visual reports and real-time monitoring.
- Compliance Focused: Designed to help meet regulatory compliance requirements.
- Comprehensive Monitoring: Includes advanced features like keylogging and activity monitoring.
Cons:
- Overwhelming Feature Set: The platform’s extensive features can be overwhelming for those needing only specific functionalities.
- Invasive Features: Some capabilities, such as keylogging, may be considered invasive.
- Steep Learning Curve: Initial setup and learning phase can be challenging.
Both the on-premises software and the hosted service are priced on a subscription basis with charges levied per month per monitored endpoint. Bills can be paid monthly or annually. However, charges have to be paid in advance. Customers paying annually get two months for free. All cloud-based editions are available on 7-day free trials and Teramind’s on-premises software can be had on a 14-day free trial for any edition.
6. Mimecast Secure Email Gateway
The Mimecast Secure Email Gateway scans all incoming emails for malicious URLs, infected attachments, and other malware intrusion tactics. It is also able to spot spam, phishing scams, and impersonators. Mimecast compiles a live threat intelligence database from records of previous attacks experienced by all of its customers and the gateway references this information source as it processes each incoming email.
Key Features:
- Email Security Monitoring: Scans all incoming and outgoing emails for threats.
- Blocks Malware: Prevents malware through detection and quarantine.
- Identifies Phishing Attempts: Detects and blocks phishing scams and impersonators.
Why do we recommend it?
The Mimecast Secure Email Gateway is an edge service that is hosted in the cloud. Incoming and outgoing emails are channeled through the Mimecast proxy server where inbound emails are scanned for threats and outbound emails are assessed for data disclosure. The tool can also examine internal corporate emails.
The detection system used by Mimecast is a hybrid of many different scanning measures. The email filter uses pattern detection as well as threat intelligence. These autonomous detection methods aim at spotting zero-day attacks that have yet to be recorded in the threat intelligence database. Mimecast references DNS servers to authenticate the domains on the addresses in incoming emails against the IP address of origin. This enables the system to spot spoofing attempts and block the emails of those fake senders.
Who is it recommended for?
This is an easy system to implement because the service is hosted off site and mirrors all of your email accounts. This has a double benefit because those cloud-based copies will continue to function if your email server goes down. So, it provides a business continuity service.
Pros:
- Comprehensive Email Security: Acts as a full email gateway, ensuring complete email security.
- Advanced Threat Detection: Uses pattern recognition and behavior analysis to detect new and unknown threats.
- DNS Security Checks: Helps identify emails that do not use proper DNS security measures (DKIM, SPF, DMARC).
Cons:
- SaaS Only: Available exclusively as a Software-as-a-Service (SaaS).
- Complex Admin Console: The admin console can be challenging to navigate and use effectively.
- Whitelisting Limitations: Whitelisting process could be more intuitive and user-friendly.
The Mimecast Secure Email Gateway is delivered on a Software-as-a-Service model, so you don’t need to install any software. While most of the services on this list are aimed at SMBs, Mimecast is definitely suitable for large organizations.
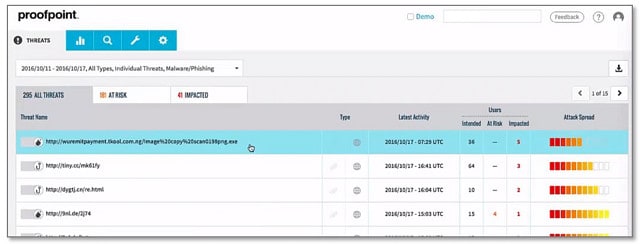
7. Proofpoint Essentials
Proofpoint Essentials is a complete email solution that includes archiving and social media protection as well as email filtering. This is a cloud-based service that is charged on a subscription model. This solution is aimed at small and middle-sized businesses.
Key Features:
- Email and Social Media Security: Monitors and protects email and social media channels.
- Archiving and Recovery: Provides archiving services with recovery options.
- Threat Intelligence: Utilizes AI for detecting threats and maintaining a threat intelligence database.
Why do we recommend it?
Proofpoint Essentials is an AI-based email protection system that detects spam, BEC, and phishing attacks. Once the proxy system is set up, it copies your email account structure and passes emails to each account through its own filters before forwarding them. This also provides a continuity service if your own email server becomes unavailable.
Another bonus included in Proofpoint Essential is a continuity service. This provides a hosted replacement for your regular email service should your email server go down or get damaged. The email archiving service can store emails for up to 10 years.
Email protection includes a threat intelligence database, URL validation, spam protection, and malware filtering. The system can protect cloud-based email systems as well as on-premises mail servers.
Who is it recommended for?
This tool is marketed for small and middle-sized businesses. Proofpoint produces a very similar system with the same AI engine for larger businesses. You need to alter your mail DNS records so that all emails for your domain go to the Proofpoint server instead of your own.
Pros:
- Comprehensive Solution: Combines email security and archiving in a single package.
- Long-Term Email Retention: Stores emails for up to 10 years, aiding in compliance efforts.
- SMB Focus: Tailored for small to medium-sized businesses, ensuring accessibility and usability.
- Phishing Protection: Offers URL validation to prevent phishing attacks.
Cons:
- Limited Customization: Lacks extensive customization options for specific needs.
- No Encryption Feature: Missing encryption capabilities needed for compliance with standards like HIPAA.
You can get a 30-day free trial of Proofpoint Essentials, but you will have to meet a sales representative in order to get it. The company doesn’t reveal its prices online.
8. N-able SpamExperts
N-able SpamExperts email protection is offered to ISPs and web hosts so that they can improve their services to their customers. Another incentive for hosting companies to implement this protection is that a malicious email on a hosted system could damage that network as well as the customer.
Key Features:
- ISP and Web Host Focus: Specifically designed for ISPs and web hosting providers.
- Spam Filtering: Includes robust spam filtering capabilities.
- Traffic Monitoring: Monitors both inbound and outbound email traffic for threats.
Why do we recommend it?
N-able SpamExperts provides inbound and outbound email filtering and also offers an email archiving service. The core of the system is an AI-based detection system, which is hosted on the N-able cloud servers. However, the outbound package can be downloaded for self-hosting or you can get it as a SaaS package.
The email filtering procedures cover both inbound and outbound emails. Inbound emails are checked for spam, malware, and phishing content, while outbound emails are checked for data disclosure. Malicious threats are detected by reference to a central threat intelligence database that SolarWinds maintains by recording events encountered by its customers around the world. The package also includes an email archiving service.
Who is it recommended for?
This package is marketed for use by service providers, such as internet service providers or web hosting platforms. The idea is that the buyer will offer the service to their clients and each of those customers will get a subaccount. Clients get a cloud-based console to manage their email accounts.
Pros:
- Service Provider Design: Tailored for managed service providers (MSPs) and ISPs.
- Scalable Cloud Service: Cloud-based service that easily scales with business growth.
- Email Archiving: Supports comprehensive email archiving for compliance and recovery.
- Multi-Tenant Support: Allows for multiple client sub accounts with individual management consoles.
Cons:
- Risk of Misconfiguration: Misconfiguration can lead to significant email outages.
- Navigation Challenges: User interface could be more intuitive and easier to navigate.
The service is cloud-based, so there is no need to install any software. The pricing is kept private and is only disclosed per customer by a sales agent. You can get a no-obligation 30-day free trial of Spam Experts.
9. N-able Mail Assure
SolarWinds has two email security solutions on our list. The first is a cloud-based service offered by the N-able division. N-able Mail Assure is marketed as a service that MSPs can add on as an extra income stream to offer to clients, but there is nothing stopping companies from subscribing to the service directly.
Key Features:
- MSP-Oriented: Designed specifically for managed service providers.
- Email Traffic Monitoring: Monitors and filters email traffic for threats.
- Spam Filtering: Effectively blocks spam, BEC, and phishing attempts.
Why do we recommend it?
N-able Mail Assure is a cloud-based email scanning service that detects and blocks spam, BEC, and phishing attempts. This is a proxy service that mimics the email accounts of the protected company. That is, emails are scanned and clean mails are deposited in the MailAssure user email accounts. These are then replicated to the destination user inboxes.
The email filtering service is complemented by an archiving facility. The company maintains a threat database from the experiences gleaned from serving all of its clients. The threat database is just one technique that Mail Assure uses to block threats. This analysis means that the system is able to detect phishing and impersonation attempts as well as root out malicious links, malware, spoofing, and spam. The system also examines outbound mail for data disclosure.
Who is it recommended for?
This service is marketed to managed service providers for the protection of the email systems of their clients. It can integrate into the SaaS version of Microsoft 365 as well as on-premises servers. The Mail Assure user email accounts can act as a business continuity service.
Pros:
- Cloud-Based Service: No need for additional infrastructure, reducing costs and complexity.
- Multi-Tenant Support: Ideal for MSPs, allowing multiple client accounts with individual management.
- Cloud and On-Premises Protection: Supports protection for both cloud-hosted email servers like Office 365 and on-premises servers.
Cons:
- Feature-Rich Platform: The extensive features may require time to fully explore and utilize.
- Pricing Transparency: Requires contacting the sales team for a customized quote, as prices are not disclosed online.
N-able Mail Assure is able to protect cloud-based mail servers such as Office 365, as well as your own on-premises mail servers. The company is cagey about its prices and each potential customer needs to contact the sales team for a customized quote. However, you can get a 30-day free trial first to put the system to the test.
10. Trustifi Inbound Shield
Trustifi Inbound Shield is one of three modules offered by Trustifi, all of which monitor emails for malicious activity. The other two units available are Outbound Shield, which is a data loss prevention system, and Account Compromise Detection, which looks for account takeover. All three modules are hosted on the cloud.
The Trustifi system integrates into email servers through a plug-in. This is available for on-premises mail servers and also for Microsoft 365 and Google Workspace.
Key Features:
- Cloud-Based: Operates entirely in the cloud for seamless integration and scalability.
- Malware Detection: Scans email bodies and attachments for malware.
- Spam Filtering: Identifies and roots out spam emails.
- Masquerading Detection: Spots and blocks impersonation and spoofing attempts.
Why do we recommend it?
Trustifi Inbound Shield is a cloud-based reference system that operates on emails through a plug-in. The tool scans an email and then communicates a pass or a fail, which tells your email system to make the email available to the recipient or hold it back. An outbound email scanner is available on the same platform.
Inbound Shield uses AI-based routines to spot impersonation and spoofing. It can also identify spam by looking at the contents. This method is supplemented by a blacklist of known spam email sources. The system checks links in email bodies for fake and infected sites.
The protection system extends to attachments. Emails and attachments that are suspicious can be held back and quarantined for investigation. The exact actions performed by the Trustifi system can be adapted according to your wishes, expressed in the settings of your account.
Who is it recommended for?
This tool can be used by any business. It does not require any technical knowledge to install because the integration of the necessary plug-in is guided through the cloud-based console of Trustifi. The service detects spam, BEC, and impersonation, which means that the tool will more than earn its price in theft avoidance.
Pros:
- Easy Installation: Simple to install with an API and plug-in integration for on-premises, Microsoft 365, and Google Workspace.
- Comprehensive Malware Protection: Effectively detects and blocks emails and attachments containing malware.
- Advanced Spam Detection: Uses AI and blacklists to identify spam and suspicious emails.
- Link Validation: Checks links in emails for authenticity and safety.
Cons:
- No Free Trial: Lacks an option for a free trial, which might deter some potential users.
The Trustifi service can be adapted by applying security policies. These are available as templates that can be applied or they can be created individually. There are templates in the Trustifi library that create compliance with specific data protection standards, such as PCI DSS, HIPAA, and GDPR.
11. Topsec Email Security
Topsec Email Security is a web-based service that checks both inbound and outbound emails. Inbound emails are filtered to strip out malware and spam. Companies can also implement policies over email content, and block those that have illicit content from reaching their destinations. It also scans all attachments for malicious content.
Key Features:
- Cloud-Based Service: Operates entirely in the cloud for easy access and scalability.
- Email Traffic Monitoring: Monitors and filters both inbound and outbound emails.
- Attachment Scanning: Scans all attachments for malicious content.
- Archiving Add-On: Optional email archiving service for additional functionality.
Why do we recommend it?
Topsec Email Security is a managed security service with spam, phishing, and BEC protection for inbound emails and data loss protection implemented on outbound emails. This service acts as a proxy, filtering incoming emails on a different server before forwarding cleared mails to the client’s email server.
As the Email Security system is an edge service, all of this activity takes place away from the network. Thus, the Topsec Email Security system reduces traffic on your own network and also lessens the load on your email server.
The reduction of spam also improves worker productivity because each employee spends less time scanning through spam emails.
Topsec offers a number of add-on services that will enhance your email system. These include mail archiving and a continuity service that will provide a secondary host for your mailboxes if your main email server goes down or gets damaged.
Who is it recommended for?
The Topsec service can be contracted directly by corporations or it can be offered as an extra service by MSPs. In the latter case, MSPs simply act as a marketing partner for the Topsec service, passing through all responsibility for email management while continuing to support the other systems of their clients.
Pros:
- Easy Onboarding: Web-based service simplifies the setup process.
- Edge Service Operation: Processes emails on a different server, reducing network traffic and email server load.
- Optional Add-Ons: Allows customization with optional services like mail archiving and continuity.
Cons:
- Configuration Challenges: Filtering can be time-consuming, and more bulk configuration options are needed.
- Spam Release Process: The process to release emails from spam could be more user-friendly.
The Topsec price list is only available to potential customers who contact the sales office. However, it is possible to get a 30-day free trial of the system to try before buying.
12. Barracuda Email Security Gateway
Barracuda Email Security Gateway is a physical appliance that plugs into your network. The full service also involves remote elements provided by Barracuda, so this is a hybrid cloud/appliance solution.
Key Features:
- Physical Appliance: Implemented as a physical device within your network.
- Hybrid Cloud/Appliance Solution: Covers both on-site and cloud-based email systems.
- Email Encryption: Offers encryption for secure email communications.
Why do we recommend it?
Barracuda Email Security Gateway pre-processes emails with the intention of preventing malware from touching your servers. The service also detects spam, phishing attempts, and business email compromise (BEC). When deployed as a physical appliance the system will also absorb DDoS attacks. Outbound filtering manages data loss prevention.
The appliance gathers all of your inbound email traffic before it hits the network, so it is able to absorb DDoS attacks as well as blocking malicious emails. The email filtering system will strip out viruses, spam, phishing attempts, and infected attachments.
The service also includes email encryption for security and a stand-in email server in case your own mail server becomes unavailable. Outbound content checking looks for unwanted data disclosure to enable your business to stay in compliance with data protection standards.
If you don’t want to have to install a physical piece of equipment, you can opt to get the email security gateway as a virtual appliance or as software that you can run on your own virtual servers in AWS or Azure.
Who is it recommended for?
This package is a physical or virtual appliance. The virtual appliance options are to run it over a hypervisor on your own server or on cloud accounts run by AWS or Azure. The tool performs encryption offloading, so it will manage encryption with remote endpoints, enabling local inspection of plain text packet contents.
Pros:
- Flexible Deployment: Available as a physical appliance, virtual appliance, or software for AWS/Azure.
- DDoS Protection: Redirects DDoS attacks away from your network infrastructure.
- Enhanced Security: Includes email encryption to protect sensitive communications.
Cons:
- Limited Data Visualization: More data visualization features could benefit network operation centers (NOCs).
- Port Mapping Complexity: Port mapping could be more user-friendly.
There is a hosted cloud-based version of this service, which is called Barracuda Essentials. Barracuda Networks makes the Email Security Gateway available on a free trial for evaluation.
13. modusCloud
Vircom offers a range of email security systems, including modusCloud, which is a cloud-based system. The company’s on-premises equivalent is called modusGate. The modusCloud system will block spam and also phishing attempts. It seeks out malware hidden within email and attachments and verifies links in emails to ensure that they do not lead to infected or fake web pages.
Key Features:
- Cloud-Based Delivery: Provides email security as a cloud-based service.
- Spam and Phishing Blocking: Effectively blocks spam and phishing attacks.
- Malware Detection: Identifies and removes malware in email bodies and attachments.
Why do we recommend it?
Vircom modusCloud is a proxy service that filters emails before they reach your mail server. The system will also root out phishing attempts, scan for malicious links, and strip out malware. The service scans attachments as well as email bodies. This service will reduce the load on your email server.
Other services from Vircom can be added to the modusCloud package to provide a full email protection service. These extra services include content filtering to enforce company policies. The cloud service can also provide continuity email servers in case your own server goes down. Another extra that can be added is an email archiving service. Email encryption for the transmission of sensitive data is another option.
Who is it recommended for?
This is an interesting service that would be suitable for any business. Vircom offers a version for on-premises Exchange Server and another for the SaaS Microsoft 365 but the standard tool can protect other email systems. You can also set up the cloud account to provide a business continuity service.
Pros:
- User-Friendly Interface: Simple interface makes it easy to identify patterns and issues quickly.
- Comprehensive Protection: Provides link verification and attachment scanning to ensure email safety.
- Email Archiving: Offers optional email archiving alongside email monitoring.
Cons:
- Training Time: Can take some time to train the system to reduce false positives.
14. Hornetsecurity Spam and Malware Protection
HornetSecurity’s Spam and Malware Protection is a cloud-based service. The company boasts the highest spam detection rate in the industry, filtering out 99.99 percent of all spam. Hornetsecurity points out that 50 percent of all the world’s emails are spam and so blocking these before they get to your network seriously reduces the traffic that it has to deal with, freeing up capacity for productive activity.
Key Features:
- Cloud-Based Service: Provides email security as a cloud-based service, ensuring easy scalability.
- Spam and Phishing Filters: Effectively filters out spam and phishing attempts.
- Malware Blocking: Blocks email-borne malware in email bodies, images, and attachments.
Why do we recommend it?
Hornetsecurity Spam and Malware Protection also includes the Zerospam system, which Hornetsecurity took over. This is a cloud-based proxy service that acts as a front-end for your mail server and then passes on clean and valid emails to your mail server over an encrypted link.
The email security service is also able to spot phishing attempts and block them. All email-borne malware whether in the email body, in images, or in attached documents. It will also detect links that lead to false or infected web pages. The service provides effective DDoS protection for your email servers.
Hornetsecurity ensures that the link between its cloud system and your home network cannot be interfered with or spied on by encrypting traffic in either direction. Spam and malware filters are also applied to outbound traffic.
Who is it recommended for?
You can use this tool to block spam, phishing attempts, BEC, malware, and malicious links. The service will also absorb DDoS attacks. The package is suitable for businesses of all sizes but Hornetsecurity does not offer a free trial or publish a price list, which will deter small businesses.
Pros:
- High Detection Rate: Boasts a 99.99% spam detection rate, significantly reducing email traffic.
- Phishing and Spoofing Protection: Effectively stops phishing attempts and spoofed domain attacks.
- Robust Threat Database: Maintains an up-to-date threat database for accurate scanning.
- Multi-Tenant Support: Suitable for businesses with multiple clients or users.
Cons:
- Support Response Time: Support could be more responsive with faster resolution times.
- Knowledgebase Resources: More comprehensive knowledge base articles for new users would be beneficial.
15. Sophos Email Security
Sophos is one of the world’s leading cybersecurity companies and its Email Security product is very powerful. This protection system is available as an appliance, a virtual machine, or as a cloud service. The Email Security service controls both inbound and outbound emails. Inbound traffic gets checked for spam and viruses and outbound filters apply data loss prevention strategies.
Key Features:
- Flexible Deployment: Available as a physical device, virtual appliance, or cloud platform.
- Comprehensive Monitoring: Monitors both on-site and cloud-based email systems.
- Data Loss Prevention: Implements data loss prevention strategies for outbound emails.
Why do we recommend it?
Sophos Email Security is a security system for both inbound and outbound emails. It will scan incoming emails for threats, such as spam, BEC, phishing attempts, and malware. It will also scan for and block malicious links. The tool will apply data loss prevention policies to outbound emails.
While the appliance protects your on-premises email server, the cloud service can protect your own email server on-site and also cloud-based servers, such as Office 365. The service also includes email and/or attachment encryption and phishing defenses.
Who is it recommended for?
Sophos aims its products at mid-sized businesses, although this product would be suitable for enterprises of all sizes. The deployment options will appeal to different market sectors. The option to run the service as a network appliance is a solution for larger businesses and the virtual appliance option will appeal to smaller businesses.
Pros:
- Versatile Installation: Can be installed virtually, on-premises, or in the cloud, catering to various business sizes and needs.
- Dual Protection: Provides robust protection from both inbound and outbound email threats.
- Email Recovery: Acts as a DLP tool by recovering lost emails and preventing data leaks.
Cons:
- Active Directory Integration: Improved integration with Active Directory for user management would be beneficial.
- Limited Reporting Customization: Reporting options are somewhat limited and could benefit from more customization.
- Integration Options: More integration options would enhance its overall utility.
Sophos offers Email security on a 30-day free trial.
Choosing email monitoring software
Your decision to monitor your company’s email will be driven by a need for spam filtering, data loss protection, or both. Your security priorities will dictate which of these products suit you best. You might also consider whether an appliance would be of more interest to you or whether you think that you would prefer an edge service cloud solution.
The options on our list of recommendations are all excellent email security services. Whichever you choose, getting protection from attack or data theft through email should be your priority.
Email monitoring software FAQs
How do I monitor email activity?
All emails pass through your email server and so that is the place to implement email monitoring – for both performance and security monitoring. You don’t need to monitor email clients, but you do need to ensure that your users don’t have clients that communicate with external email servers. As long as you have your corporate email activity locked down to run through your own central server, you can implement data loss prevention by scanning outgoing emails, and cybersecurity protection by scanning incoming emails.
What is e mail monitoring?
Email monitoring operates both performance checks for email servers and security monitoring for cyber protection. Performance monitoring needs to ensure that your mail service keeps running efficiently and cyber protection blocks malware and scams and also data disclosure. Some email monitoring packages operate as plug-ins for your email server and they have integration procedures built into their service dashboards to make adoption easy. Other email monitoring systems work as proxy services and run on the cloud, catching all of your inbound and outbound email traffic.
Can emails be monitored?
Legally, all work emails can be monitored by the business. While private emails can’t legally be monitored by the company’s IT department, the use of corporate resources for private use can be blocked. It is important to prevent employees from using their own email accounts at work because they could be used for data theft and also indicates that workers are not focused on their jobs.