External vulnerability scanning is an essential component of a comprehensive cybersecurity strategy, helping organizations identify and mitigate potential security risks before attackers can exploit them. The process involves scanning the public-facing assets of a network, such as websites, servers, and other devices accessible from the internet. The aim is to detect vulnerabilities that could be used by malicious actors to gain unauthorized access or cause damage.
External threats come from outsiders – you also have to deal with insider threats. Cybercriminals continuously look for weaknesses in organizations’ external-facing systems. A breach in these areas can lead to severe consequences, including data theft, financial loss, and reputational damage. By conducting regular external vulnerability scans, businesses can identify weaknesses, patch vulnerabilities, and reduce the likelihood of a successful attack.
This guide to external vulnerability scanning provides an insight into using a specialized tool to scan for system security weaknesses. We will cover the techniques and best practices for protecting your organization from cyber threats. Whether you’re an IT professional, a network administrator, or a business owner, this guide will help you better understand how external vulnerability scanning works, why it’s necessary, and how to implement it effectively within your security framework.
By leveraging advanced scanning technologies and adhering to industry best practices, organizations can not only detect and address vulnerabilities but also stay compliant with security regulations and standards.
What is an External Vulnerability Scan?
An external vulnerability scan is a scan that is conducted outside of the network you’re testing. These scans target external IP addresses throughout your network, scanning perimeter defenses like websites, web applications, and network firewalls for weaknesses.
These entities face the external web and if exploited can act as an entry point into your internal network. Running an external vulnerability scan will tell what exploits these services have whether that’s known vulnerabilities or misconfigurations.
In other words, an external vulnerability scan shows you gaps in the perimeter defenses of your network that cyberattacks use to breach your network. A scan also tells you actionable remediation information such as the updates required to protect your software from being compromised.
Is an External Vulnerability Scan the Same as a Vulnerability Scan?
There are multiple types of vulnerability scans including internal, external, authenticated, and unauthenticated vulnerability scans. Each type of scan has a different purpose.
- External vulnerability scan – Vulnerability scan takes place from outside of the network to detect vulnerabilities in the perimeter of a network outside of the internal network. It can reveal vulnerable services, ports, applications, and servers.
- Internal vulnerability scan – Vulnerability scan takes place inside an organization’s perimeter defenses to detect vulnerabilities that internal attackers, such as hackers or bitter employees can exploit in the internal network. Includes computers, servers, VoIP phones, printers, and scanners
- Unauthenticated scan – Vulnerability scans to search for exploits inside the perimeter of the network without privileged access or login credentials for services in the network.
- Authenticated scans – Vulnerability scans where the scanner is given access credentials to access systems throughout the network. The scan replicates a scenario where an attacker has obtained access credentials and is probing the network for data to steal.
In short, an external vulnerability scan tells you what vulnerabilities you have in your perimeter defenses. These are the vulnerabilities we will attempt to use when trying to break into the internal network. External vulnerability scans are run by an Approved Scanning Vendor (ASV).
Why is an External Vulnerability Scan Important?
Running an external vulnerability scan is important because it allows you to identify weaknesses in your perimeter defenses, such as a firewall or website.
Vulnerabilities in your perimeter defenses make it easier for cybercriminals to break into your internal network, putting both your systems and your data at risk.
External vulnerability scans are also important for preparing for Payment Card Industry Data Security Standard (PCI DSS) compliance. According to the PCI DSS, any merchant or service provider that processes, stores or transmits credit card data needs to secure that data through measures including external vulnerability scanning. Non-compliance can result in substantial fines and penalties for merchants, including withdrawal of the ability to process credit cards.
To comply with PCI DSS requirements, it is important to note that external vulnerability scans must be performed by an Approved Scanning Vendor. ASVs are a list of vendors that have been tested and approved by the PCI Standards Council.
The testing process is vigorous with annual tests that verify the vendor’s vulnerability scanning process. You can view a list of the providers and contact information on the PCI Security Standards site.
How to Perform an External Vulnerability Scan
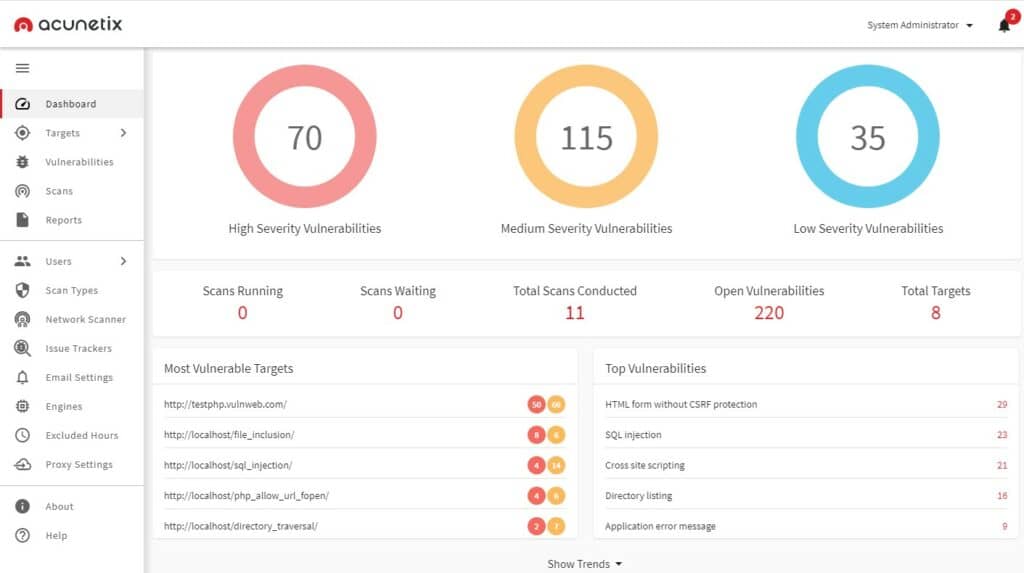
External vulnerability scans can be performed by your company or a third party with vulnerability scanning software. The quality of the scanner will determine its effectiveness at discovering vulnerabilities and open ports. In this example, we’re going to use Acunetix, but there are many vulnerability scanners you use.
We’re going to look at how to scan a web application or website for vulnerabilities with Acunetix. While this isn’t an exhaustive guide of scanning all your perimeter IT resources it gives you an idea on how to scan some of the key services that attackers will be looking to target.
- Click on the Targets tab in the Acunetix GUI, then press Add Target then enter an Address and Description for the target you want to scan.
- Click Add Target.
- [If your site doesn’t require forms authentication] Under the Target Info box, select the Site Login option and add a User Name, Password, and Retype password to enable auto-login to the site. Skip ahead to step 12.
- [If your website requires forms authentication] you need to check the Use pre-recorded login sequence option and click on the Launch Login Sequence Recorder.
- Now click on the Your Profile option and enter a Username and Password.
- Click Login.
- Press Play to double-check the steps you entered for autologin are correct then press Next.
- Click on the Logout test option and confirm the action you’d like to restrict the scanner from doing by clicking Restrict request using an exact match.
- Click Next.
- Click the OK button when the Pattern Detected box comes up and click Finish once readying Save the login sequence.
- Return to the Site Login section and click on the file icon next to the Login Sequence box and Open the login sequence you saved.
- Click Save in the top left-hand corner of the screen.
- Click Scan to select the type of scan you want to run (In this example -select Full Scan).
- Select the Affected Items report option and Instant in the Schedule box.
- Press Create Scan to start the scan.
- Monitor scan progress on the Scans tab. You can click on the Vulnerabilities tab to view vulnerabilities as they are discovered. You can also view a summary of all vulnerabilities detected by going to the Dashboard tab.
You can use a tool like Acunetix to run an external vulnerability scan yourself or rely on a third-party service/ASV to do it for you. Whether you need an ASV to run the scan will depend on what the regulations in your industry stipulate.
The Vulnerability Assessment Process
Running a vulnerability scan is just the beginning of the vulnerability assessment process. To efficiently and successfully remediate vulnerabilities you need to:
- Identify vulnerabilities
- Evaluate the level of risk presented by those vulnerabilities
- Remediate the discovered vulnerabilities
- Report on the vulnerabilities discovered and how they were resolved
Identifying vulnerabilities with the scan tell you where your current perimeter defenses are failing. However, there may be so many vulnerabilities that you struggle to know which to address. Evaluating the level of risk presented by vulnerabilities is critical for determining, which issues to fix first.
If you run your own scan then your scanner may allow you to search for vulnerabilities by severity, or an expert will let you know what to address first via documentation if you run a scan through an ASV.
The key to prioritizing is to estimate the impact a successful exploit would have on the business, how likely it is that the vulnerability will be exploited, and what security controls you could implement to fix the problem. You should also keep an eye for false-positive vulnerabilities so you don’t try and fix something you don’t need to.
After estimating the impact of threats throughout your environment it’s a good idea to focus on fixing those vulnerabilities that present the greatest level of risk to your environment. Fixing these vulnerabilities can be as simple as installing a new patch or so complex that there isn’t a direct solution.
If you discover a vulnerability that cannot be resolved then it’s important to evaluate whether it’s worth using that system despite the risk. Sometimes you can mitigate low-risk vulnerabilities just by being aware of their presence and making some security changes.
How Often Should I Run an External Vulnerability Scan?
A one-off scan isn’t enough to verify that your network is secure. Conditions change all the time and performing regular scans is critical to making sure that you catch new vulnerabilities. There is a wide variation amongst recommendations in the industry as to how often you should be scanning. Recommendations range from monthly to quarterly.
If you’re working toward complying with a particular regulation then it’s vital you look up the requirements and run vulnerability scans as often as is required. Quarterly scans (through an ASV) are sufficient for complying with PCI DSS.
External Vulnerability Scanners ASV (PCI DSS)
Above we mentioned Acunetix, which lets you run your own external vulnerability scans, but in this section, we’re going to look at some ASVs that will run scans on your behalf. The PCI SSC defines an ASV as “an organization with a set of security services and tools to conduct external vulnerability scanning services.”
All ASVs are tested and approved by the PCI DSS. You can find a list of ASVs on the
PCI Security Standards site. Some of the top ASVs include:
For PCI DSS compliance, working with an ASV is advantageous because it allows you to outsource your scanning to a vendor who has been approved by the PCI SSC. The PCI SSC has verified that an ASV has the ability to sufficiently detect vulnerabilities so that you can become PCI DSS compliant.
In addition, years of experience running vulnerability scans means they have the necessary expertise to discover vulnerabilities and will be able to explain to you how to remediate vulnerabilities in your environment.
Why Running An External Vulnerability Scan is Essential
Completing a vulnerability scan is just half of the battle. When the results of the scan come back and you see there are vulnerabilities in your environment it’s important that you act on that information to resolve those weaknesses. If you run the scan and then fail to fix the changes then your organization isn’t going to become more secure.
External Vulnerability Scan FAQs
What is the difference between external and internal vulnerability scanning?
The main difference between external and internal vulnerability scanning is whether you give the scanner permission to enter your network. An external scanner will try to break into your network from a remote location. An internal scanner can also be launched from a remote location but its intention is to test security within the network and so requires you to enter credentials to let it into the network, past your perimeter security.
What is PCI DSS external vulnerability scan?
An external vulnerability scanner needs to test whether a system security setup can block hackers. A scanner that has been tailored to check for PCI DSS compliance could be described as a PCI DSS external vulnerability scanner.
What entities may conduct external vulnerability scans?
Anyone can conduct an external vulnerability scan on any system – even ones that they don’t own. However, for the purposes of proving compliance with PCI DSS, you need to get the scan performed by a certified auditor. The PCI Security Standards Council maintains a searchable database of Approved Scanning Vendors.