Every attack is unique, and sometimes the only way to spot an attack is with security analytics software that uses machine learning and anomaly detection to identify attacks based on patterns.
Here is our list of the best security analytics software:
- Graylog Security (FREE PLAN) This security package builds on log file management with search strategies that deploy machine learning to identify unusual activity. Start with access to 2GB/day for free.
- ManageEngine Firewall Analyzer (FREE TRIAL) This package gathers data from firewalls and other security software to identify better measures for security policies and firewall rules. Runs on Windows Server, Linux, and AWS. Get a 30-day free trial.
- Datadog Infrastructure monitoring software with log collection, filtering, dashboards, anomaly detection, alerts, and more.
- SolarWinds Security Event Manager Log management tool with threat intelligence, event correlation, dashboards, graphs, charts, alerts, and more.
- LogRhythm NextGen SIEM Platform Log management software with machine analytics, alarms, user and entity behavior analytics, threat scoring, automated responses, and more.
- Sumo Logic Log analysis software with security analytics, graphs, charts, alerts, integrations, and more.
- Logz.io Cloud-based SIEM with log collection, automated threat detection, real-time alerts, reporting, and more.
- Splunk SIEM software with log collection, anomaly detection, machine learning, user behavior analytics, risk scores, custom dashboards, and more.
- Rapid7 InsightIDR SIEM software with dashboards, graphs, charts, user behavior analytics, attacker behavior analytics, automation, and more.
- Elastic Stack Open-source log management software with dashboards, visualization options, log categorization, anomaly detection, and more.
The list includes tools for Windows, macOS, and Linux, with a focus on log management and SIEM tools that analytics features like threat intelligence, anomaly detection, or usage analytics. We’ve also included tools with custom dashboards and high-quality visualization options like graphs and charts.
The best security analytics tools
Our methodology for selecting security analytics software
We reviewed the market for security analytics tools and analyzed options based on the following criteria:
- Source data collection from around the IT system
- A threat detection strategy
- A list of threat indicators
- Detection strategies to spot zero-day threats
- Alerts for possible security threats
- A free trial or a demo version that provides an assessment opportunity before buying
- Good value for money from a security analyzer that is offered at a fair price.
With these selection criteria in mind, we looked for security packages that analyze system activity data to identify automated or manual threats.
1. ManageEngine Firewall Analyzer (FREE TRIAL)
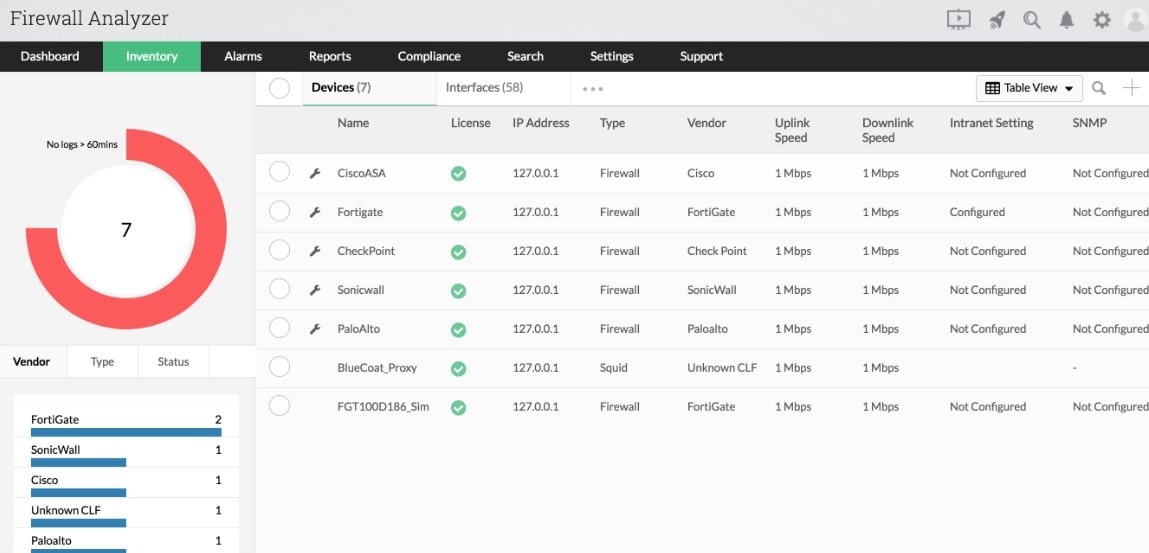
ManageEngine Firewall Analyzer helps you to perfect your network security policies and can identify cyberattacks underway and after the event. The package reads log files from firewalls and other network security tools, such as intrusion detection systems. Effectively, this is a security event manager, providing the network activity half of a typical SIEM tool.
Key Features:
- Collects data from security tools: Gathers network activity data
- Interfaces with major firewall brands: Includes connectors to firewalls from Check Point, Cisco, Juniper, Fortinet, Palo Alto, and others
- Can generate firewall rules: Get immediate threat remediation for ongoing attacks
- Generates access control lists: Implement network segmentation
Why do we recommend it?
ManageEngine Firewall Analyzer is able to manage a range of security strategies. You might just have one firewall at the gateway of your network or many firewalls positioned at different points on the LAN. Either way, this tool can gather activity records and recommend improvements to network security [policies.
There isn’t one single network security strategy but this tool can adapt to whatever configuration you use for your LAN. For example, if you implement zones of trust through switch access control lists, you can coordinate all the allow and deny rules across the network with the Firewall Analyzer.
This package can be conceptualized as a partial SIEM because it fulfills the live network activity analysis part of that package function. You can link this package through to a SIEM for additional threat hunting. However, the tool can be set up to implement automated threat remediation without having to wait for the SIEM to spot an issue.
Who is it recommended for?
This system is suitable for any business that runs its own network and, therefore, also has a network firewall. If you use a cloud firewall and other edge services, this package is still suitable because it can gather data across the internet. Coordinate the settings of multiple firewalls and security tools and ensure that they don’t implement contradictory strategies.
Pros:
- Firewall configuration management: Get alerts if firewall rules are changed
- Attack analysis: Produces reports on recent attacks for analysis
- User internet activity monitoring: Block access to inappropriate sites and spot insider threats
- VPN and proxy server monitoring: Track the performance of external and edge services
Cons:
- Doesn’t include a firewall: You have to buy a firewall in addition to this package
Unlike most ManageEngine products, the Firewall Analyzer doesn’t offer a Free edition. There are three paid editions available: Standard and Professional, each of which will support up to 60 network devices, and the Enterprise edition, which can manage up to 1,200 devices. You can get a 30-day free trial of the Professional edition to assess the Firewall Analyzer.
2. Graylog Security (FREE PLAN)
Graylog Security is a SIEM package that is built on top of the Graylog Platform. Graylog is a log management system that collects and consolidates log messages that are collected from all the endpoints and devices on a network. The tool cross-references collected data with Access Rights Manager and Firewalls to add more information to the gathered data.
Key Features:
- Deployment Options: On-premises software or a SaaS package
- Fast Data Searches: Handles large data volumes
- An Anomaly-Based Detection Strategy: Uses triage
- Follows a Chain of Events: Looks for indicators of compromise
Why do we recommend it?
Graylog Security is a SIEM tool offered by the data processing tool, Graylog. The Graylog log management system was originally free but, like Splunk, it has transitioned into a security platform. The Graylog Security system is a cloud platform. The original free package is also still available for Linux or Docker.
The Graylog Security package is a series of pre-written searches that are added to the standard Graylog system. These rules also record user activity to establish a pattern of normal behavior per user account and per device. The system extends its scrutiny to traffic that originates outside the network by adding in IP address referencing such as IP location and domain origin information.
Graylog Security subscribers also get the benefits of the standard Graylog log management service, which includes compliance auditing and reporting features. The Graylog Platform can be enhanced by installing plug-ins that are available for free from the Graylog community.
Who is it recommended for?
Cash-strapped startups could get the free Graylog Open log manager and build a SIEM tool through data searches. However, you have to weigh up whether the cost of technician time to develop such a tool would work out more expensive than just paying for the pre-written Graylog Security system.
Pros:
- Automated Speedy Threat Hunting: Scans through log messages
- Alerts on the Discovery of Unusual Activity: Provides an administrator with options
- Data Viewer: Provides opportunities for manual searches
- Automated Remediation: Through coordination with ARMs and firewalls
Cons:
- Doesn’t Run on Windows: Runs on Linux or can be taken as a SaaS package
There are three Graylog versions: Graylog Open, which is free, Graylog Enterprise, which installs on Linux, and Graylog Cloud, which is a SaaS package. Graylog Security is available with Graylog Enterprise and Graylog Cloud. The pricing is a metered service with a rate based on ingested data volume. You can get free access to the Graylog Small Business plan which gives you all the functions of Graylog Enterprise plan which is limited to 2GB/day so you can experience the product and figure out your requirements.
3. Datadog
Datadog is an infrastructure monitoring tool that you can use to monitor log data. Data dog automatically collects logs from services and applications throughout your environment, so that you can search and filter for security events. Through the dashboard, you can view analytics to monitor performance trends.
Key Features:
- Automated Log Collection: Consolidates messages to a common format
- Search and Filter: Provides users with analytics tools
- SIEM Tool: Automated threat detection
Why do we recommend it?
Datadog Cloud SIEM provides an automated security monitoring service. The package also allows administrators to perform ad-hoc queries on log files, either for security analysis or for performance investigations. It is also possible for skilled security analysts to create their own security scanning apps with the data querying tool.
Threat detection gives you enhanced visibility over threats by analyzing logs in real-time and identifying malicious or anomalous patterns for you to respond to, with out-of-the-box detection rules to determine what constitutes a threat. Detection rules can also be customized according to your requirements.
Watchdog automatically detects performance anomalies with machine learning and sends you alerts to tell you to take action. For example, if latency spikes suddenly then the system identifies this and alerts you. You can then proceed to a detail page that provides additional contextual information you can use to resolve the issue.
Who is it recommended for?
This automated security analysis tool is suitable for businesses of all sizes because it is invoiced on data throughput. There are no up-front fees or minimum spend requirements so small businesses with very little data per month get all of the bells and whistles that are available to big corporations.
Pros:
- Cloud-Based SaaS Product: No server deployments or onboarding costs
- Options for Cloud Security Monitoring: The platform includes many modules
- Data Visualization: Graphs and charts
Cons:
- Short Free Trial: The trial is only two-weeks long
Datadog is recommended for enterprises that wish to automatically detect security threats. The Log Management package starts at $1.27 (£0.99) per million log events, per month. It is available for Windows, macOS, and Linux. You can launch the 14-day free trial.
Related post: The Best Threat Intelligence Platforms
4. SolarWinds Security Event Manager
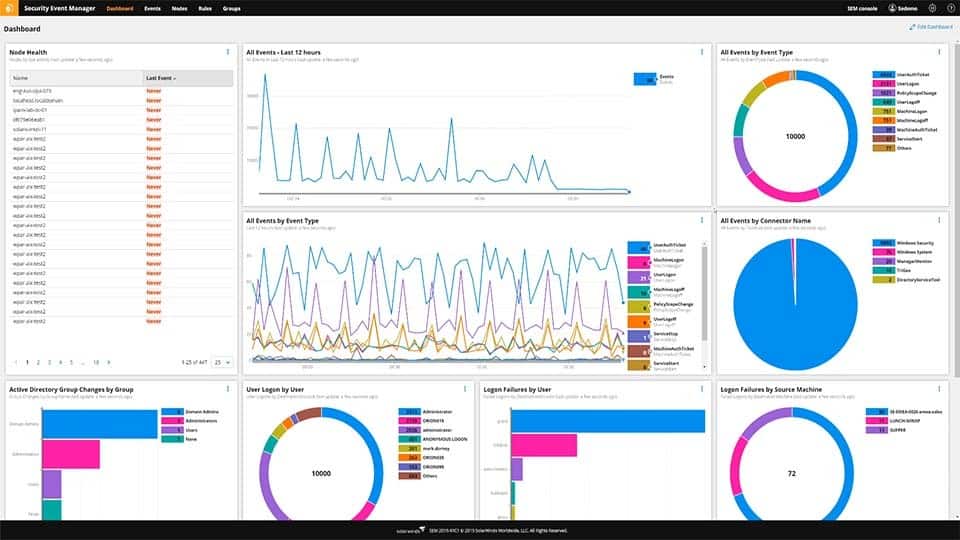
SolarWinds Security Event Manager is a log management solution that collects logs on a centralized basis. SolarWinds Security Event Manager uses threat intelligence to automatically detect and respond to network threats. The threat intelligence feed analyzes events throughout your network and compares them to known malicious threats, highlighting issues that need your attention.
Key Features:
- Centralized Log Collection: Consolidates messages into a common format
- Threat Intelligence: Takes third-party feeds
- Dashboard: Includes a data viewer with analysis tools
- Compliance Reports: HIPAA, PCI DSS, SOX, FISMA, NERC CIP, FERPA, and GLBA
Why do we recommend it?
SolarWinds Security Event Manager is an on-premises SIEM system that includes a log manager. The logs can be viewed as they arrive and also by loading a file into the viewer. That utility includes analytical tools, such as search, sort, and filter functions. The package also provides user activity tracking and file integrity monitoring.
Through the dashboard, you can view an overview of security and performance events throughout the network with the help of graphs and charts. For example, you can view a chart of All Events over the last 12 hours so you can identify if there is an unusual spike in activity that could indicate a cyber attack.
The alerts system allows you to configure triggers to determine when you are notified about security events by email or SMS. Out-of-the-box compliance reports for HIPAA, PCI DSS, SOX, FISMA, NERC CIP, FERPA, GLBA, GPG13, and more, allow you to prepare for regulatory compliance.
Who is it recommended for?
This system provides automated security monitoring through its SIEM, user analytics, and file integrity monitoring. It also offers opportunities to custom build automated scanning by setting up searches and getting them to run periodically or continuously. Ad-hoc manual security analysis is also supported. So, this package is useful for corporate security management by an experienced analyst.
Pros:
- Enterprise-Focused SIEM: Includes a library of integrations
- Simple Log Filtering: No need to learn a custom query language
- Historical Analysis Tool: Helps find anomalous behavior and outliers on the network
Cons:
- Not Suitable for Small Businesses: Works best when supported by a team of technicians
SolarWinds Security Event Manager is a great choice for enterprises that require threat intelligence and streamlined event correlation. Prices start at $2,525 (£1,972.19). It is available on Windows, macOS, and Linux. You can start the 30-day free trial here.
5. LogRhythm NextGen SIEM Platform
LogRhythm NextGen SIEM Platform is a log management software with machine learning and scenario-based analytics. With LogRhythm NextGen SIEM Platform you can use LogRhythm DetectX’s machine analytics to detect malicious activity and trigger alarms to notify you about the problem. Machine analytics uses a combination of machine learning, behavior profiling, statistical analysis, blacklisting, and whitelisting to identify threats.
Key Features:
- Log Collection: Consolidation and filing
- Automated Analysis: SIEM threat hunting
- User and Entity Behavior Analytics: Discovers insider threats
Why do we recommend it?
LogRhythm is a cloud-based SIEM that includes user and entity behavior analytics. That UEBA mechanism records a pattern of typical behavior for each user account and endpoint. The threat detection service looks for deviations from that standard. The security analysis then focuses on subsequent actions by that user or endpoint.
Similarly, UserXDR can detect anomalous user behavior with user and entity behavior analytics (UEBA). A risk-based prioritization algorithm calculates a risk-based score to all issues detected. Threat scoring helps you to identify which issues pose the most risk to your environment so you can remediate them first.
The integrated Security Orchestration, Automation and Response (SOAR) tool LogRhythm RespondX automatically responds to incidents based on playbook actions or approved-based response actions. For example, RespondX can automatically disable a port, suspend a user account, or kill processes.
Who is it recommended for?
This is a good solution for large businesses with many endpoints and users because the platform has a very large capacity for high-speed data processing. The tool can collect logs from cloud platforms as well as from endpoints on your site and it also extracts network activity data.
Pros:
- Easy Onboarding: Uses simple wizards to set up log collection and other security tasks
- Cloud-Based Console: Sleek interface, highly customizable, and visually appealing
- Leverages Artificial Intelligence: Machine learning for behavior analysis
Cons:
- Hybrid Support Would be a Welcomed Feature: This tool focuses on on-premises systems
LogRhythm NextGen SIEM Platform is suitable for automating threat detection and response in enterprise environments. The company offers a custom pricing model so you need to request a quote to view pricing information. Schedule a demo from this link here.
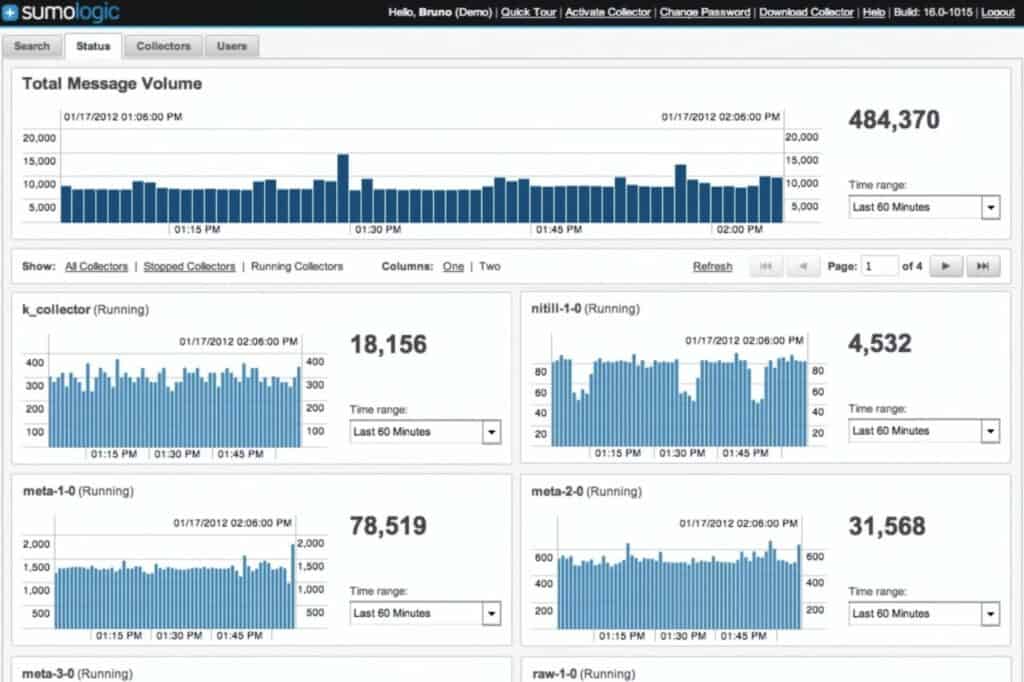
6. Sumo Logic
Sumo Logic is a log analysis tool you can use to monitor logs in real-time. Sumo Logic comes with security analytics and Adaptive Signal Clustering, which automatically identify potential security incidents and provide contextual information that human users can use to resolve the issue.
Key Features:
- Real-Time Log Monitoring: Gathers logs from many sources
- SIEM Operations: Security analytics
- Automated Prioritization: Identifies urgent events
Why do we recommend it?
Sumo Logic is an on-premises package that offers a range of system monitoring services. The package collects log messages and uses them for source data that pre-written queries implement for infrastructure performance monitoring and security analysis. The platform’s subscription packages include a SIEM and there is also a Log Management unit.
Visualization displays like graphs and charts allow you to view performance trends in real-time. LogReduce breaks down high volumes of logs into basic patterns to help you make sense of what’s going on.
Alerts notify you about any problematic activity when it occurs. Configure alert conditions to generate email alerts that highlight real-time error conditions. Whenever you discover a problem, integrations with ticketing systems help you to manage the incident with your existing tools.
Who is it recommended for?
Sumo Logic offers a lot of options for security analytics and it has a wide potential market. The Cloud SIEM will give you automated security scanning but that comes at a price and smaller businesses might decide they can get away with making their own security queries with the Log Management package.
Pros:
- Integrations: Gathers activity data directly from applications
- Uses AI: Automatically groups suspicious events for analysis
- Intelligent Alerting: Reduces duplicate notifications
Cons:
- Requires Technical Skills to Set Up: Integrations and initial onboarding can be complex
Sumo Logic is a good solution for automatically compiling contextual information on malicious events and anomalies. Pricing starts at $3.00 (£2.34) per GB logs for the Essentials version. It is available for Windows, macOS, and Linux. You can sign up for the free trial here.
7. Logz.io
Logz.io is a cloud-based SIEM with automated threat detection. Logz.io automatically identifies threats from log data taken from services like CloudTrail, CloudFront, EC2, Microsoft Active Directory, Microsoft Defender, HashiCorp Vault, Okta, and Palo Alto Networks. The platform’s threat intelligence compares collected logs to public and private data feeds to identify security risks.
Key Features:
- Log Analysis: Acts as a log server
- SIEM Security Scanning: Automated threat detection
- Real-Time Alerts: Notifications by email, Slack, and PagerDuty
Why do we recommend it?
Logz.io is a Cloud SIEM. Τhis tool scans log messages that come from cloud platforms and on-premises systems. As well as getting operating system messages, the package can extract event information directly from applications through integrations. The platform has a free library of these and there are 350.
Through the dashboard, you can view a top-down perspective of your infrastructure and then drill down into user data to investigate threats. Analytics displays like graphs and pie charts help you to understand what’s going on. You can schedule reports to periodically check up on the latest security trends. Reports can be customized to display the information that’s most important to you.
Real-time alerts continuously update you on the latest security threats. Configure trigger conditions to determine when you receive notifications and receive alerts by email, Slack, or PagerDuty. For example, you can configure an alert to notify you whenever there is a failed authentication attempt.
Who is it recommended for?
The package is aimed at businesses that run hybrid systems with both on-premises assets and cloud services that need to be monitored for threats. The company also offers a Log Management service, an Infrastructure Monitoring system, and Observability tools for Web applications, such as distributed tracing and code profiling.
Pros:
- Operates in the Cloud: No need to download or maintain software
- Threat Intelligence Feed: From both public and private sources
- Flexible Alerting Integrations: Channel alerts through collaboration suites and messaging apps
Cons:
- Short Retention Period: Only 40 days
Logz.io is worth evaluating if you require automated threat detection. The Community version is available for free and supports up to 1GB of log data with one day of log retention. Paid versions start at $1.08 (£.84) per indexed GB for the Pro version. You can request a demo from this link here.
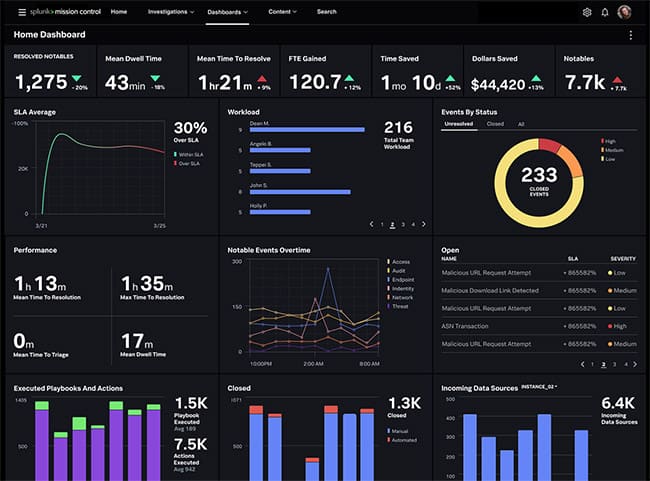
8. Splunk
Splunk is a SIEM tool that you can use to collect and analyze logs throughout your network. With Splunk you can monitor the security of your infrastructure in real-time with anomaly detection and machine learning, which detect indicators of compromise. Similarly, user behavior analytics uses machine learning to identify anomalous user, device, and application behavior.
Key Features:
- Real-Time Log Analysis: Security and performance monitoring options
- User Behavior Analytics: Spots insider threats
- Incident Response: Uses security orchestration, automation, and response
Why do we recommend it?
Splunk is a data analysis tool onto which its creators have added an ever-expanding menu of services. The system is available as an on-premises package or as a SaaS platform. Its security systems are presented in a division called Splunk Enterprise Security, which includes a SIEM.
When security events are detected, you can use risk scores to identify, which to remediate first. Customizable dashboards allow you to monitor log data through the dashboard with the assistance of graphs and charts. You also have the option to use the Adaptive Operations Framework to conduct automated responses after a threat is detected.
The software is fully-equipped with compliance reports to help prepare for regulatory compliance for the GDPR, PCI DSS, HIPAA, FISMA, and SOX. Schedule reports to make sure that you stay up to date on your compliance status, and generate on-demand reports to share with auditors.
Who is it recommended for?
Splunk is probably a little too expensive for small businesses but mid-sized and large organizations would find Splunk Enterprise Security suitable as a security analytics service. This platform is a little more complicated than rivals, such as Graylog because of the many modules that the security platform contains.
Pros:
- Great User Interface: Can be customized
- Alerts with Severity Levels: Easy prioritization of events
- Splunk Enterprise Security Deployment Options: On premises software or a SaaS platform
Cons:
- Complicated Pricing: Calculated from a formula of many elements
Splunk is recommended for enterprises that require a state of the art SIEM solution with anomaly detection capabilities. Splunk Enterprises starts at $1,800 (£1,406) per year. You can sign up for a trial here.
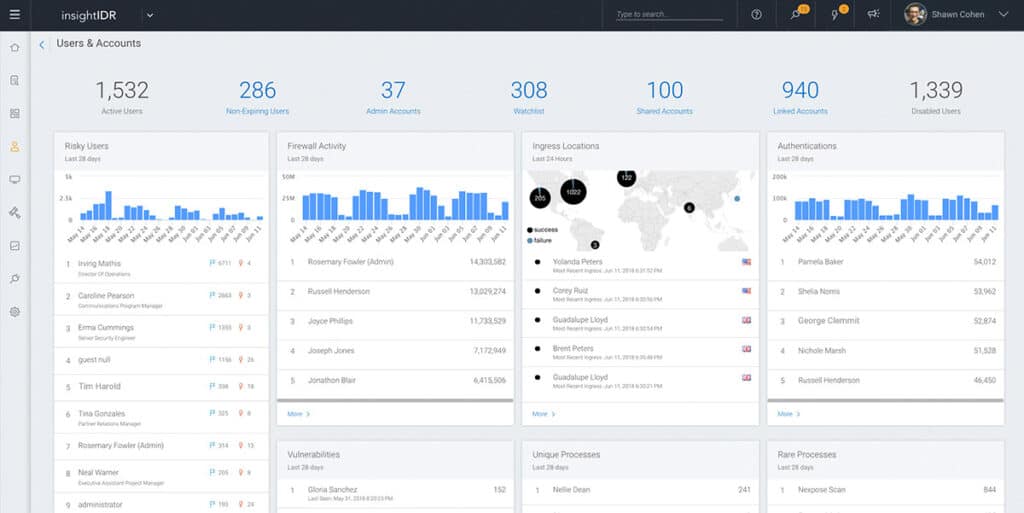
9. Rapid7 InsightIDR
Rapid7 InsightIDR is a SIEM solution that you can use to monitor log data and detect security insights. General monitoring can be conducted through dashboards that include charts and graphs. Rapid7 InsightIDR offers User Behavior Analytics you can use to monitor for malicious activity. For example, user behavior analytics uses machine learning to identify anomalous activity, assigns a Risky User Ranking, and raises an alert.
Key Features:
- Collects and Monitors Logs: Consolidates and stores them
- User Behavior Analytics: Looks for insider threats
- Attacker Behavior Analytics: Speeds up threat discovery
Why do we recommend it?
Rapid7 InsightIDR is a very similar service to the LogRhythm SIEM except that costs a lot less – the LogRhythm system is very expensive. This tool includes UEBA for standard behavior baselining and anomaly detection for suspicious activity. The system can also be set up to implement responses automatically.
The platform also offers attacker behavior analytics to protect against external threats. Attacker behavior analytics detects security events based on real-world attacks, using detection methods created by Rapid7’s team of security analysts. Context-rich alerts let you know the cause of an alert so you can take action to address the root cause.
Automation enables the system to automatically respond to security events. For example, the software can automatically suspend user accounts or follow a prebuilt workflow.
Who is it recommended for?
This service is more accessibly priced than LogRhythm and competes in the same price bracket as SolarWinds and Splunk. However, it is still probably out of the reach of small businesses, where Datadog or Elastic Stack would probably be more suitable. Rapid 7 InsightIDR is a cloud-based service with log storage included.
Pros:
- Dual Detection Strategy: Anomaly and signature-based detection
- Uses Multiple Data Streams: Up-to-date threat analysis methodologies
- Allows for Robust Automated Remediation: Can involve third-party security systems
Cons:
- Expensive: Pricing is higher than similar tools on the market
Rapid7 InsightIDR is a SIEM tool that’s a fit for large organizations looking for an advanced log management solution. Prices start at $2,156 (£1,683) per month. You can start the free trial here.
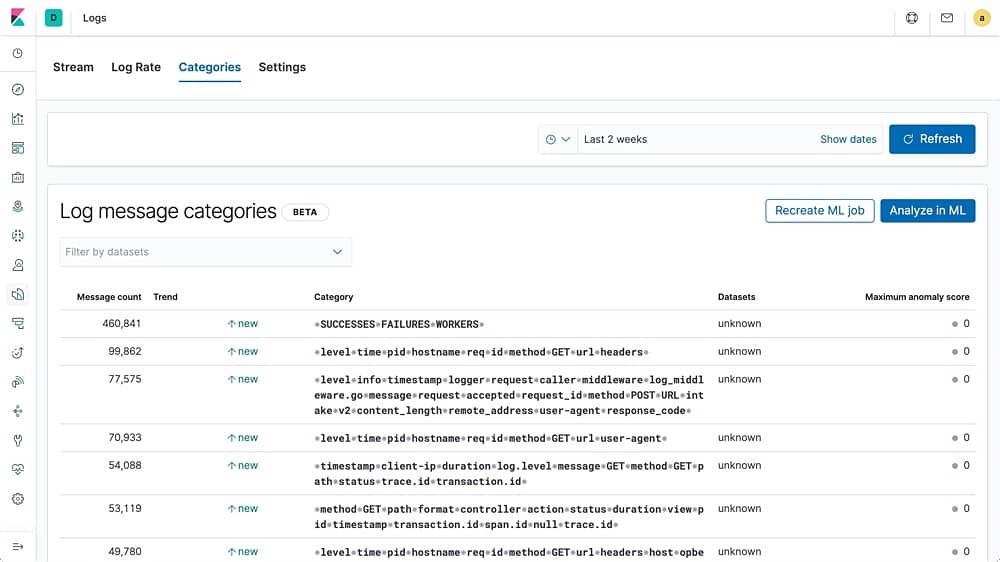
10. Elastic Stack
Elastic Stack is an open-source log management tool that you can use to collect logs from services like Kubernetes, Amazon CloudWatch, Apache, AWS, Azure, Docker, MySQL, and more. For example, to monitor Kubernetes you can view a breakdown of logs by host, pod, or other custom metadata.
Key Features:
- Free Tools for Download: Create your own security analytics system
- Cloud-Hosted SaaS Platform: Includes a SIEM
- Anomaly Detection: Scans log messages
Why do we recommend it?
Elastic Stack is a very competent suite of data handling tools that many other log analysis and data processing systems use behind the scenes. The suite has three particularly important tools for log analysis, which are Logstash, Elastic Stack, and Kibana. These three tools are available for free if downloaded individually. The cloud platform includes a SIEM.
Through the dashboard, you can monitor key performance with graphs and charts. For example, you can view a pie chart of Syslog hostnames and processes for ECS. Log categorization helps you to search for logs more efficiently, grouping events together based on message content and format.
An anomaly detection feature uses machine learning to monitor log data and notify you about security events. There is also a detection engine that you can use to configure custom detection rules to determine when the platform responds to events, and integrates with other products so you can receive alerts wherever you require.
Who is it recommended for?
Elastic Stack is hard to beat and many of the package’s rivals warn of hidden charges in the platform. However, many of those rivals actually rely on the Elastic Stack tools themselves. For example, Logz.io is actually a hosted Elastic Stack service and Datadog has Elasticsearch at its core.
Pros:
- Customizable Dashboard: Create your own screens with Kibana
- Easy to Learn Scripting Language: The popular Elasticsearch
- Active User Community: A source for tips and plugins
Cons:
- Schema Changes Can Require Reindexing: That can take a lot of time to run
Elastic Stack is one of the top open-source log management solutions on the market. Pricing starts at $16 (£12.50) per month. It is available as a hosted version or a download for Windows, macOS, and Linux. You can start the free trial from this link here.
Choosing security analytics software
Security analytics is worth making a part of your cybersecurity strategy if you want to maximize your detection and remediation capabilities. The right solution will help you to identify threats faster and avoid the perils of alert fatigue, so you don’t spend hours managing false alarms.
Tools like Graylog Security, ManageEngine Firewall Analyzer, and LogRhythm NextGen SIEM Platform are all superb choices for enterprise users. Each tool is easy to use with threat intelligence, anomaly detection, and machine analytics you can use to mitigate security risks. We highly recommended researching and trying out multiple tools to find the tool that’s best for your environment.
Security Analytics FAQs
What are security analytics tools?
Security analytics tools take a longer look at system event data to spot patterns of behavior. This is different from traditional security software which examines each event in isolation. Modern cyberattacks utilize authorized user accounts and pore-existing system services to move around the network causing damage or stealing data. Security analytics tools aim to stop those activities and they can perform that search automatically or support manual investigations.
What is a soar tool?
SOAR stands for Security Orchestration, Automation, and Response. This type of system collects activity data from security systems, such as firewalls, assess it for indicators of compromise, and then sends out instructions to system management services to shut down threats. These systems also provide compliance reporting.
Is splunk a SIEM or soar?
Splunk is a real-time data analysis tool. The package can be used for a range of applications, such as marketing data analysis, or security scanning. The Splunk organization provides pre-written searches that create packages to adapt Splunk to specific needs and threw is an extensive library of security functions available for the tool. Mong the security services that you can implement with a Splunk package are a Security Information and Event Management (SIEM) package and a Security Orchestration, Automation, and Response (SOAR) service.