Staying protected online isn’t a matter of deploying an antivirus and a firewall. Repelling modern threats requires a unified security strategy that can manage and mitigate security events when they emerge. Security Orchestration, Automation, and Response (SOAR) stacks are one of the best tools for managing security events. But what is SOAR exactly?
Here is our list of the best SOAR software:
- Google Cloud Chronicle Security Operations Suite – Flexible platform offering SIEM and SOAR modules, adaptable to various detection rules and external tools.
- Heimdal Threat Hunting and Action Center – Coordinates multiple on-premises Heimdal security tools with cloud-based SIEM and SOAR capabilities.
- LogRhythm Enterprise – Well-known for its comprehensive SIEM and embedded SOAR, offering advanced behavior analysis and customizable dashboards.
SOAR Explained
The term SOAR was originally coined by Gartner and is used to refer to tools that combine Security Orchestration and Automation (SOA), Threat Intelligence Platforms (TIP), and Incident Response Platforms (IRP) together to manage security threats. Essentially, a SOAR solution enables the user to take data from lots of disparate sources and view it in one location.
How SOAR Works
SOAR solutions are monitoring platforms that provide the user with a dashboard supplied with security data and metrics that have been compiled from lots of different systems within an organization. Combining data from disparate sources helps develop a more comprehensive view of threats, with automated detection and incident response.
Many of these tools use threat intelligence and AI to improve decision-making and help users respond to threats – automatically in some cases. Automated responses and more detailed diagnostics help reduce the time it takes to resolve security threats. SOAR platforms can be broken down into three main components:
- Orchestration
- Automation
- Response
Orchestration
Orchestration is the process of collecting data from different sources and putting it together inside one platform. Orchestration is useful in the cybersecurity context because it can be used to take data from different tools and technologies to provide a top-down perspective of security threats.
For example, a SOAR tool would use orchestration to generate alerts from many different data sources and put them in one list so that the user can easily manage them. Having security event data in one place makes vulnerability management much easier. Without a security orchestration tool, a security analyst would have to move between different systems to maintain a network.
Automation
The automation component of SOAR tools is designed to reduce the administrative burdens that network administrators and security analysts face when managing security events. Manually detecting and responding to cyberattacks is ineffective. One person cannot realistically monitor a dozen systems that generate thousands of alarms throughout the day.
SOAR solutions use automated workflows, alerts, and responses to enable the user to automatically respond to security events. There are many solutions that can be configured to automatically shut down a device or user account if anomalous activity is detected.
Response
The response portion of a SOAR tool is concerned with incident management and enabling users to respond to security events effectively. Features like the dashboard are where most incident management and response activity takes place. From here the user can view alerts and threat intelligence to manage threats in real time.
These tools provide root-cause diagnostics and intelligence to help the user find solutions to security events faster. In other words, SOAR tools have been designed to play a diagnostic function to help guide the user towards the best actions to take during remediation.
Why Is SOAR Important? Automated Threat Detection and Remediation
SOAR solutions have become more important in recent years as cyber threats have become more sophisticated. Cyber attackers are becoming more adept at identifying vulnerabilities and finding entry points to networks. As companies use more services like cloud services and applications there are more entry points to manage.
Managing disparate systems has been a consistent pain point for security analysts who are expected to switch back and forth between collecting data and monitoring security events. Trying to monitor all of these systems manually makes for a hefty workload that few can keep up with.
For example, a security analyst can have to wade through thousands of alarms on different infrastructure monitoring solutions. Manual tasks like managing alarms take time away from other more pressing concerns like monitoring for threats.
SOAR tools eliminate many manual tasks by automating the data collection process. Instead of changing between lots of different solutions the user can view the data compiled from TIPS and intrusion detection systems (IDS) in one location to identify cyber-attacks more efficiently.
Being able to view this data in an accessible format helps with detection and response. It also enables enterprises to become more data driven and efficient. The depth of data available to support the analysis of attacks leads to a more complete viewpoint than a security analyst could deliver (and at a lower cost).
SOAR vs SIEM: What’s the Difference and Which is Better?
As far as security tools go SOAR and security information event management (SIEM) solutions share a couple of similarities. Both are hybrid solutions that collect data from a number of sources and play an important role in cybersecurity. However, they each have distinct roles to play.
A SIEM tool collects and aggregates log data from different systems within a network, including applications and devices. The SIEM then analyses the data obtained for anomalous activity and sends an alert to the user if it recognizes anything of risk to the network.
SIEM tools combine the capabilities of security event management (SEM) tools, which analyze log data in real-time and combine it with security information management (SIM), which collects and reports on security events.
The core difference between SOAR and SIEM solutions is that the former can respond to security threats whereas a SIEM can only detect them. SOAR solutions have automated responses ready to follow up whereas SIEM solutions can only issue alerts once a problem has been detected.
SOAR solutions are superior for automatic incident response and require less manual actions than a SIEM tool. While SIEM solutions are good at detecting cyber attacks, it can be challenging to keep up to date with the large volume of alerts that are generated (particularly when taking into account false positives).
Even though SOAR has better automation capabilities, it can be useful to combine SOAR and SIEM solutions together. Whenever a SIEM solution creates an alert, a SOAR solution can import that data so that it can easily be seen by an analyst. The analyst can then use the data provided by the SIEM solution to take a closer look.
SOAR Software
As with all cybersecurity solutions, SOAR platforms come in different shapes and sizes. Although the tools are built on the same foundations the experience provided by each varies tremendously. In this section we’re going to look at some of the top SOAR solutions on the market.
Our methodology for selecting SIEM and SOAR tools
We’ve broken down our analysis for you based on these key criteria:
- Integration Capabilities: Ability to work seamlessly with other tools and systems.
- Automation and Response: Level of automation for threat detection and response.
- User Interface and Usability: Ease of use and customizability of the platform.
- Scalability: Suitability for different business sizes and multi-site operations.
- Advanced Features: Inclusion of AI, machine learning, and behavior analytics.
1. Google Cloud Chronicle Security Operations Suite
Google Cloud Chronicle is a Security Operations Suite. This cloud platform has been assembled by Google Cloud through a series of purchases, which included Mandiant and Siemplify. The platform now provides a SIEM service and a SOAR. You can take either or both of these modules. While the SIEM gathers log messages from your IT assets, the SOAR coordinates the efforts of other cybersecurity tools.
Key Features:
- Third-Party Integration: Directly accesses and coordinates with external cybersecurity tools
- Automated Responses: Automates threat response workflows
- Playbook Templates: Provides pre-built playbook templates for quick setup
- Alert Merging: Combines related alerts for streamlined management
Why do we recommend it?
The Chronicle Security Operations Suite is a flexible tool because you can use the SIEM by itself or add on the SOAR to automate alert processing into responses. The SOAR can operate with a SIEM from another supplier, so you aren’t limited to using the Google Cloud SIEM.
You can partner the SOAR with the Chronicle SIEM or a SIEM from another provider. The purpose of this SOAR service is to accept alerts from one system, scan through a set of playbooks, and implement responses by sending instructions to other tools.
The Security Operations Suite has a third element, which is a Threat Intelligence feed. This would plug into the SIEM rather than the SOAR. This is because the SOAR doesn’t detect threats, but it relies on the efforts of an external system to identify attacks. The power of the SOAR lies with its rules sets and you can acquire these on the Chronicle Marketplace to save time. The package is delivered with a default set of rules and templates and connectors that help you to create your own.
Who is it recommended for?
The Chronicle SOAR is a good choice for businesses that already have a SIEM and want to improve response automation. The tool can work with alert feeds from most of the major SIEM brands, including Proofpoint, CrowdStrike, and Trellix. Businesses that don’t have a SIEM already in place should consider the Chronicle SIEM that runs on the same platform as the SOAR.
Pros:
- Versatile Integration: Can be paired with Chronicle SIEM or other SIEM systems for flexibility.
- Cloud-Based Coordination: Operates seamlessly across multiple sites and cloud environments.
- Customizable Rules: Supports both default and custom playbooks for tailored responses.
- Threat Intelligence Feed: Enhances threat detection with integrated intelligence.
Cons:
- No Free Trial: Requires a demo for evaluation without an immediate trial option.
There is no free trial for the Google Cloud Chronicle platform. However, you can watch a demo to learn more about the Security Operations Suite.
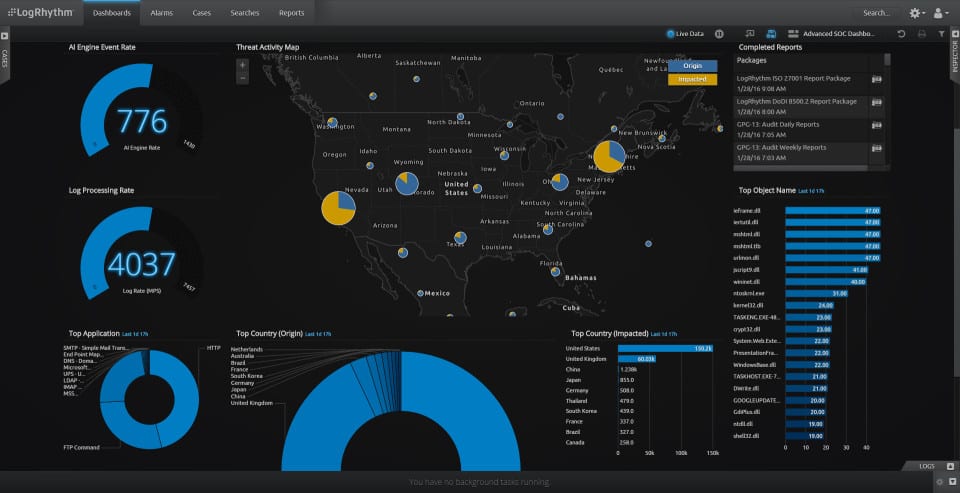
2. LogRhythm
LogRhythm is one of the most well-known SOAR solutions in the world. LogRhythm uses SmartResponse automation to automatically respond to security events after an alert. For instance, you can use an automated endpoint quarantine feature to identify network ports with suspicious devices and then remotely disable them.
Key Features:
- Cloud-Based SIEM: Provides comprehensive security monitoring from the cloud.
- Automated Threat Response: Automatically kills malicious processes and quarantines suspicious endpoints.
- Third-Party Integration: Interacts seamlessly with external cybersecurity tools.
Why do we recommend it?
LogRhythm SIEM includes an embedded SOAR. The platform also offers an optional user and entity behavior analytics (UEBA) service and a network detection and response (NFR) module. The distinction of “Next Generation SIEM” is a SIEM tool that includes UEBA and SOAR. The SOAR isn’t available as a standalone unit.
Other automated responses include the option to suspend user accounts that are acting suspiciously or kill abnormal processes on critical devices. Having automatic threat response is useful because it means that your security analysts don’t have to resolve issues manually every time.
The visibility offered by LogRhythm is also second to none. You can create custom dashboards and view investigation and response activity in real-time. This perspective provides you with enough clarity to detect significant security events. If you see something suspicious you can click to view additional threat intelligence.
Who is it recommended for?
The LogRhythm system is expensive and could be beyond the budgets of small and mid-sized businesses. This is more of a solution for large organizations. The service is hosted on the cloud as a SaaS package, so it is ideal for protecting multiple sites, which makes it a tool for a Security Operations Center (SOC).
Pros:
- User-Friendly Setup: Simple wizards make log collection and security tasks easy for beginners.
- Customizable Interface: Sleek, visually appealing, and highly adaptable dashboards.
- Advanced Behavior Analysis: Uses AI and machine learning for sophisticated threat detection.
Cons:
- No Trial Option: Requires direct inquiry for evaluation without an immediate trial available.
- Limited Cross-Platform Support: Expanding cross-platform compatibility would enhance usability.
LogRhythm is a complete incident response solution built to make remediation as painless as possible. To view a quote for LogRhythm, you will have to contact the company directly. You can sign up for a demo.
3. Heimdal Threat Hunting and Action Center
Heimdal Threat Hunting and Action Center is a cloud-based unit that is an add-on service available for the buyers of Heimdal on-premises cybersecurity packages. Businesses can create a cybersecurity fabric by combining three Heimdal products with the SIEM and SOAR services of the Threat Hunting and Action Center package. Using more than three Herimdal products improves the power of the Heimdal SOAR solution.
Key Features:
- Coordinated Security: Integrates with on-premises Heimdal security software.
- Cloud-Based: Operates from the cloud for centralized management.
- Threat Detection: Identifies and responds to threats using SIEM.
- Automated Responses: Implements playbook-driven automated actions.
- MDM Option: Includes mobile device management for Android and iOS.
Why do we recommend it?
Heimdal Threat Hunting and Action Center is a cloud-based system that coordinates the efforts of on-premises security packages supplied by the company. The service requires the presence of at least three different Heimdal systems; three different products, not three instances of the same tool. One of those systems must be the Heimdal Next-Generation Anti-Virus.
One of the on-premises systems that link into the SOAR must be the Heimdal Next-Gen Anti-Virus package, which installs on each endpoint. It is available for Windows, macOS, and Linux. That service also provides a mobile device management (MDM) system that manages devices running Android, and iOS.
The other two systems for the Heimdal security environment need to be taken from the list of Heimdal products, which includes Network Security, Email Security, Patching & Asset Management, and Endpoint Security.
The Threat Hunting part of the Heimdal platform is implemented by the XTP Engine, which stands for Extended Threat Protection. This is a SIEM, and will search through activity data that the on-premises units upload to the cloud server. Responses are implemented by playbooks that are stirred in the Action Center. These involve sending instructions back to the on-premises systems.
Who is it recommended for?
The Heimdal Next-Generation Anti-Virus system is the key partner to the Threat Hunting and Action Center package. The AV needs to be installed on each endpoint on the network – a task that can be implemented remotely. This makes the service easy to expand: simply install the AV on another endpoint to expand the area covered by the threat-hunting SIEM.
Pros:
- Integrated Security Coordination: Effectively manages multiple Heimdal on-premises cybersecurity tools.
- SIEM Inclusion: Provides comprehensive threat detection and response capabilities.
- Vulnerability Scanning: Offers system hardening instructions to improve security posture.
- Automated Playbook Responses: Ensures rapid response to identified threats.
Cons:
- No Free Trial: Requires a demo for evaluation, with no immediate trial available.
The Threat Hunting and Action Center platform is part of a bundle of tools and you can choose which Heimdal products feed into it. There isn’t a free trial available and Heimdal doesn’t publish a price list. However, you can investigate the system by requesting a free demo.
The Challenges of SOAR Implementation
While onboarding a SOAR solution is worth it, the challenges of implementation can be steep. A key challenge is finding a tool with a level of complexity that meshes with the experience of your employees. Some platforms are aimed at non-technical users and others are more advanced that require the expertise of an analyst to use.
It isn’t uncommon for some programs to require the user to have knowledge of programming languages like Perl or Python to integrate external data sources. Trying to deploy a technical solution in an environment without an experienced analyst would be a waste of time and money.
To adopt a new solution smoothly it is critical that you choose a platform that matches the technical abilities of your employees. Look for a tool that has a graphical user interface (GUI) and an integrated development environment (IDE). The former will allow non-technical users to interact with the platform and the IDE will allow analysts to write their own scripts.
Another massive challenge that companies run into is trying to automate everything at once. You can’t automate every manual task that your security analysts do. Trying to automate everything will complicate your entire threat resolution process. A much more effective strategy is to start automating smaller tasks that would usually be done by your analyst.
You should also be aware you will need to create a new incident response process from scratch. Onboarding a new monitoring tool drastically changes the incident response process.
When onboarding a SOAR platform, the incident response process has to be redesigned so that employees can respond to security breaches quickly. The incident response process will need to be periodically revised so it stands up to the latest threats.
What is SOAR? An Automated Approach to Cybersecurity
Automation has become a must-have for larger organizations with large workloads. Modern networks are becoming too diverse and complex for security analysts to keep up with while relying on manual solutions. SOAR and other automation solutions are making network monitoring more efficient so that companies can stay protected.
Even companies using traditional network monitoring tools are struggling to manage the alerts they generate. When one missed alert could be the difference between a normal day at the office or a DDoS attack a serious update is needed. Switching to a SOAR solution can help to improve your incident response process and free up your security analysts!