Ransomware attacks have become one of the most significant cybersecurity threats facing businesses and individuals today. These malicious attacks involve cybercriminals encrypting critical data and demanding a ransom in exchange for the decryption key. As ransomware tactics evolve, it has become increasingly difficult to defend against them without the right tools in place. This is where ransomware protection tools come in – providing a vital layer of defense against these sophisticated threats.
We’ve tracked over 1,000 ransomware attacks in 2023 so far impacting millions of data records and individual victims. Investing in protection and prevention in your organization is prudent given IBM puts the average cost of ransomware attack remediation (excluding any ransom payments) at $4.54m.
In this comprehensive guide, we review some of the best ransomware protection tools available. These tools are designed to detect, prevent, and respond to ransomware attacks by offering real-time monitoring, advanced threat detection, and quick recovery options. By proactively identifying vulnerabilities and suspicious activities, these tools reduce the likelihood of a successful ransomware attack and help mitigate potential damage.
Ransomware protection tools employ various techniques such as behavior analysis, file integrity monitoring, and machine learning to recognize patterns typical of ransomware. Some tools also provide features like backup and data recovery options, ensuring that if an attack does occur, businesses can quickly restore their critical files and minimize downtime.
We analyzed a range of solutions, from endpoint protection software to comprehensive enterprise-level ransomware defense platforms. We examined their core features, ease of use, effectiveness, and pricing to help you choose the most suitable solution for your needs.
Whether you’re a small business owner or an IT administrator at a large enterprise, having a robust ransomware protection tool is crucial. By the end of this guide, you’ll be equipped with the knowledge to select the best ransomware protection software to safeguard your data and maintain business continuity.
Here is the list of the best ransomware protection:
- Guardz EDITOR’S CHOICE This cloud-based SaaS package has per-user pricing, which makes it a scalable protection package for endpoints, networks, and cloud platforms. This system detects and blocks all threats, including ransomware and other malware plus human-driven attacks. Get a 14-day free trial.
- ThreatLocker (GET DEMO) A cloud-based system that blocks all software from running, which means that any ransomware or other malware is unable to cause damage but just sits as dead files on the computer until a maintenance sweep removes them. Access free demo.
- ManageEngine Vulnerability Manager Plus (FREE TRIAL) An attack prevention system that combines a vulnerability scanner and a patch manager plus other system hardening services. Runs on Windows and Windows Server. Start a 30-day free trial.
- Acronis True Image (FREE TRIAL) This package of security services for endpoints is ideal for combating ransomware because it includes backup and recovery as well as anti-malware. Start a 30-day free trial.
- ESET Protect (FREE TRIAL) This on-device anti-malware is coordinated by a cloud-located central threat detection service. Available for Windows, macOS, Linux, iOS, and Android. Start a 30-day free trial.
- Malwarebytes Anti-ransomware Uses behavior analysis to uncover malicious intent; something no anti-virus can really accomplish.
- SpinOne This SaaS package provides data loss protection through ransomware protection, backup and recovery, risk assessment, compliance auditing, and sensitive data protection.
- Bitdefender Antivirus Plus By far one of the best anti-ransomware solutions out there. This is a full-defense suite for those who take their safety seriously – not just against ransomware.
How might a ransomware attack impact your organization?
- An attack can bring operations to a halt – with your hardware under attack, there is no way you will be able to run your processes or cater to your customers. This will result in a loss of customer trust and, eventually, a decline in profits.
- Loss of sensitive and critical data – a malware infection can result in your organization’s’ data being lost which could also stop you from continuing to work. What’s worse is that your clients’ information could also be stolen which puts them at risk.
- The spread of misinformation – an undetected malware attack could take control of your data and applications and then use it to create fake data and report incorrect results. If you unwittingly continue to use them the end-results can only be worse and might derail your business’ forecast strategy.
- Denial-of-Services (DoS) attacks – malware can be used to bring your organization to its knees by simply making it inaccessible to the outside world. On the other hand, scripts run from within your network can be used to isolate you from the data or clients you may need from the outside world. Either way, your business will be starved of input which could cause irreversible damage if, for example, your sales depend on real-time access.
The best ransomware protection software
Our methodology for selecting ransomware protection
We reviewed the market for ransomware protection systems and analyzed tools based on the following criteria:
- A protection strategy that includes backup, encryption detection, or intrusion protection
- Alerting for suspicious activity
- User and entity behavior analytics (UEBA) for anomaly detection
- A threat intelligence feed
- System hardening services
- A free trial or a money-back guarantee for a risk-free assessment
- A good deal from a system that provides solid protection at a reasonable price
With these selection criteria in mind, we the market for database diagram tools and identified systems that we are happy to recommend.
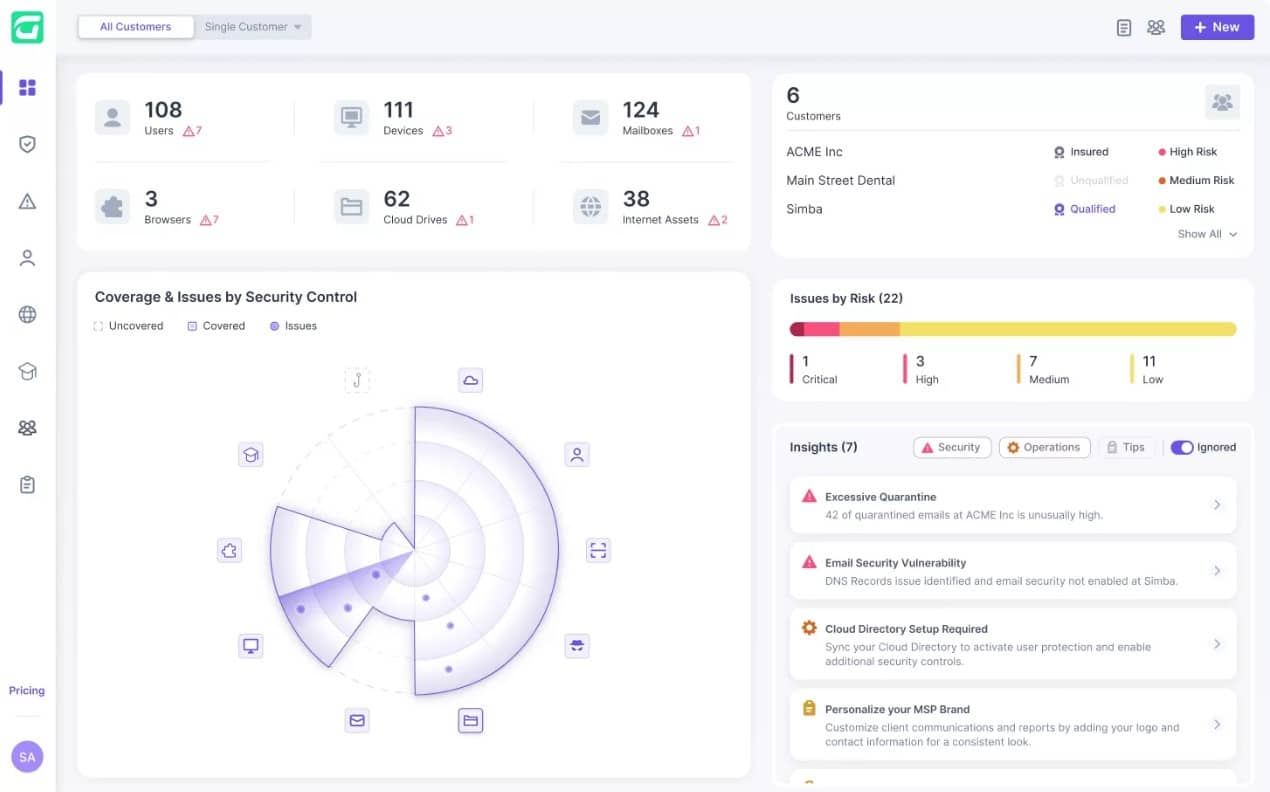
1. Guardz (FREE TRIAL)
Guardz provides security scanning for endpoints, cloud data accounts, and email systems. The endpoint protection service looks for malware, including viruses, ransomware, Trojans, keyloggers, spyware, adware, and file-less malware. The package can also identify advanced persistent threats. In an APT, a hacker gains long-term access to an IT system by stealing account credentials.
Key Features
- Cloud-Based Security: Offers flexible, scalable protection for various digital assets.
- Proactive Malware Identification: Detects malware before activation to prevent damage.
- Dark Web Monitoring: Alerts users to potential compromises of corporate identities.
- Security Training Resources: Includes courses for employee cybersecurity awareness.
Why do we recommend it?
Guardz offers protection against ransomware and many other types of malware. The system focuses on blocking the entry point of malware, which is through emails. The package scans the attachments of emails and also examines email contents for credentials theft attempts. If your email addresses have already been stolen, the Dark Web scanner in the Guardz plan will tell you about it.
The Dark Web scanner in the Guardz package needs to be set up with a list of corporate identities, such as domains. It will then add that information to its regular sweeps of message boards and forums on the Dark Web where email account details are usually sold. An alert will appear in the management dashboard if email account compromise is detected.
Another feature of the Guardz system is a library of security awareness training courses. Each of these are made from a series of videos and the administrator is able to allocate a course to one or many employees. The management dashboard shows progress through an assigned course and how many employees have completed their training. This information is stored and can form part of compliance reporting.
You need to ensure that your system is hardened against credentials theft and the Guardz package provides scanning against phishing, which is the main method that hackers use for account takeover. Ransomware can be manually installed or dropped by an installer that could be disguised as an email attachment.
The package includes a phishing simulator that lets you check whether your malicious email checker is working. The whole system is only available for use by managed service providers in their task of managing the systems of their clients. Companies that don’t have a deal in place with an MSP can get a list of recommended providers. Another option is to hire Guardz as a security service provider.
The dashboard for the system reports ob all discoveries and remediation actions, which can be stored for compliance reporting. The data on attacks can also be useful for threat intelligence analysis.
Who is it recommended for?
Although IT managers reading about Guardz might be interested in subscribing to the service, they will be disappointed because the company only sells to MSPs. The subscription rate is levied per user and there is no minimum team size. Companies that need a full service with technicians included can opt for the Ultimate plan, which is a managed security service.
Pros:
- Comprehensive Email Protection: Effectively scans emails to prevent malware and phishing attacks.
- Dark Web Surveillance: Provides an extra layer of security by monitoring potential data breaches.
- User Awareness Enhancement: Helps in educating employees about cybersecurity risks.
Cons:
- Limited Availability: Exclusively accessible to managed service providers, not direct users.
- Dependence on Cloud Connectivity: Relies heavily on internet connectivity for its functionalities.
As it is a cloud platform, there are no geographical limitations on the system’s reach, so you can remotely protect any system anywhere with the service. Access a 14-day free trial to investigate Guardz further.
EDITOR'S CHOICE
Guardz is our top pick for a ransomware protection package because it implements preventative vulnerability scanning to tighten up system weaknesses and scans emails for the tricks that hackers use to drop malware installation packages on endpoints. This bundle implements live scanning of endpoints and spots unusual activity, which could be the beginning of a ransomware attack. The service can be allowed to implement automated responses, so you don’t have the delay of risk between a detected threat and a manual decision to take action. These strategies protect against all other malware types as well and it also detects human threats. An account can protect multiple sites and also the devices of work-from-home workers.
Download: Start a 14-day FREE Trial
Official Site: https://app.eu.guardz.com/signup
OS: Cloud-based
2. ThreatLocker (ACCESS FREE DEMO)
ThreatLocker offers a very straightforward method of dealing with the detection and remediation of ransomware – it just blocks all programs from running. This prevention method is called a closed security stance and it can be applied to a range of resources, such as networks. This default deny strategy is applied by ThreatLocker at many levels and it removes the need to back up data. Authorized software is registered in a whitelist and allowed to execute.
Key Features:
- Closed Security Stance: Employs a ‘default deny’ strategy, effectively blocking all unauthorized programs.
- Whitelisting System: Enables specific authorization of programs, enhancing security controls.
- Resource Access Management: Controls access to files and network resources for added security.
Why do we recommend it?
ThreatLocker blocks all software from running on all endpoints unless a central administrator has specifically authorized it by putting it on a system-wide Allow List. This strategy blocks the possibility of any type of malware ever running on your system – including ransomware. Malware with the name of an approved program still won’t work.
Of course, if all software is prevented from running, your users would never be able to get any work done. So, ThreatLocker has a whitelisting system, called the “allow list.” you create an allow list that can be applied to groups of endpoints or to an individual computer. This not only keeps your endpoints safe from unexpected installs but it also enables you to control your software inventory and implement license management.
The ThreatLocker strategy blocks all types of malware and it also removes the danger of users installing their own preferred software on company endpoints. This isn’t the only tool in the ThreatLocker box. Approved applications are only allowed to access certain resources, so you can restrict file access and the service includes network access controls, which block rogue and insecure devices from getting onto the network.
The idea behind the ThreatLocker strategy is that it helps you to assemble a Zero Trust Access (ZTA) strategy and focuses security controls on applications. This is a suitable method to use if your users need to access a lot of services in the cloud, such as Microsoft 365 or Google Workspaces. It also helps you to assemble a virtual network or to segment your network along functional lines rather than grouping network segments by location.
Who is it recommended for?
The ThreatLocker system is suitable for businesses of all sixes. The full package includes a method for implementing Zero Trust Access – a new and innovative system-wide security strategy that ThreatLocker simplifies so that anyone can set it up even without deep cyber security expertise.
Pros:
- Enhanced Malware Blockade: Offers robust protection against all types of malware, including ransomware.
- Software Inventory Control: Helps manage software licenses and prevents unauthorized installations.
- Network Access Controls: Prevents unauthorized devices from accessing the network, enhancing overall security.
Cons:
- Restricted Application Execution: Can limit functionality if legitimate applications are not whitelisted.
- Complex Setup for Non-Experts: Setting up and managing whitelists may require technical expertise.
ThreatLocker only allows specifically listed software to run. This means that all of your authorized systems have no problems and will execute as usual but any software that isn’t on the whitelist is useless. That strategy blocks users from running their own preferred software – a situation that could get your company into trouble for pirated software. You also automatically block all types of malware, not just ransomware. The whitelist of approved software provides the ThreatLocker endpoint cleanup system with an inventory to compare each endpoint to. Thus, it knows which files to delete. Access a demo of the ThreatLocker platform to learn how this system works.
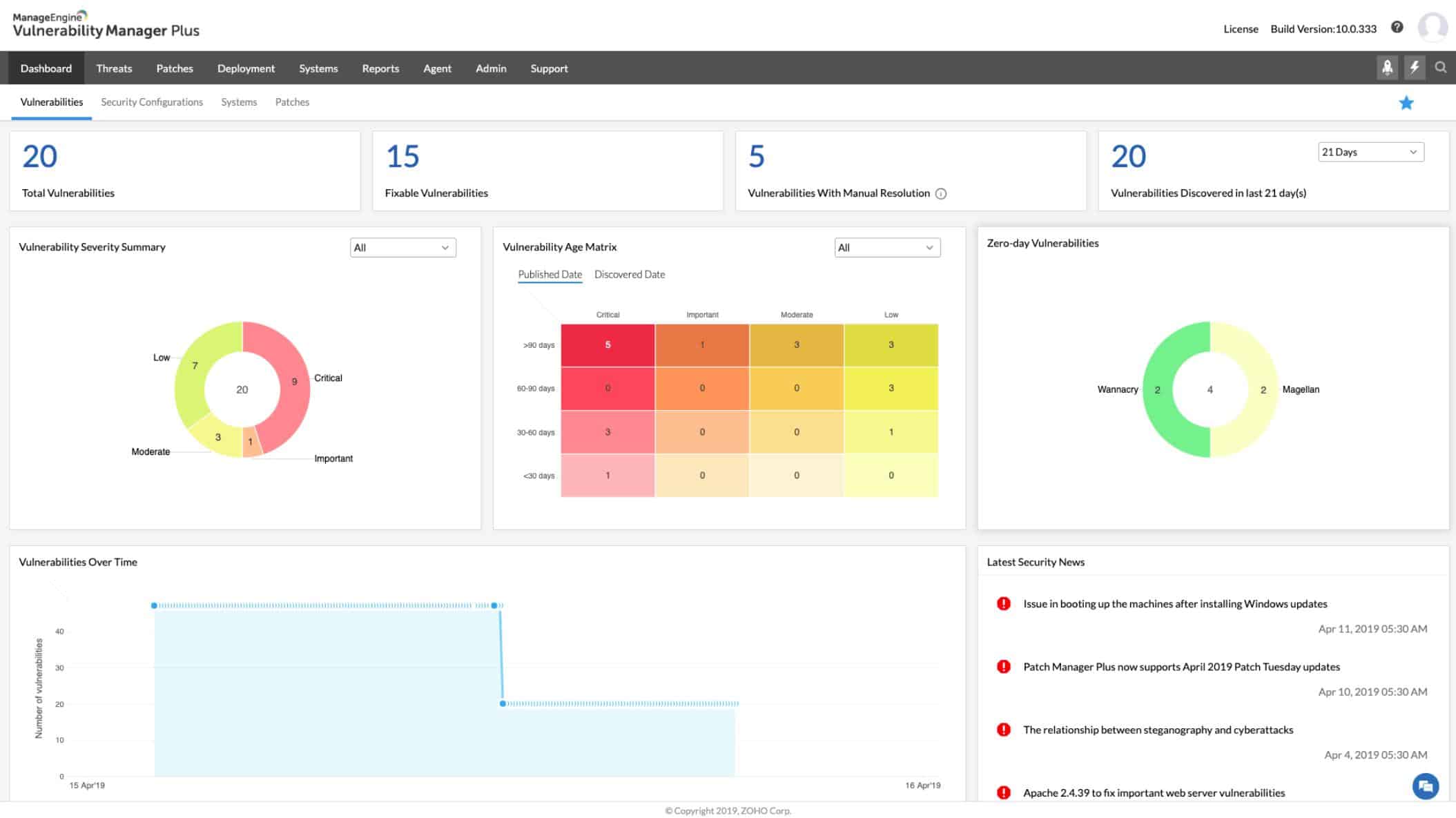
3. ManageEngine Vulnerability Manager Plus (FREE TRIAL)
ManageEngine Vulnerability Manager Plus offers services that prevent ransomware attacks by shutting down entry points that allow access to hackers. This is a system-hardening tool that will protect endpoints, network appliances, and web applications.
Key Features
- Automated Vulnerability Scanning: Regularly checks systems for potential security gaps.
- Patch Management: Streamlines the process of applying necessary software updates.
- Configuration Oversight: Ensures systems are configured for optimal security.
Why do we recommend it?
ManageEngine Vulnerability Manager Plus isn’t a conventional ransomware protection system. It is a system hardening package that identifies all of the ways malware and intruders can get onto your system and guides you into closing them down. The package includes software to implement system repairs, such as a patch manager.
The key elements of this package are a vulnerability scanner and a patch manager. Patches for operating systems and software packages are often issued because the software house has been notified about security weaknesses in their products. Not applying patches whenever they become available leaves your system exposed to attack by a range of malicious activity, not just ransomware.
The vulnerability scanner is constantly updated by a live threat intelligence feed. After an initial sweep, the scanner keeps working, kicking off a system sweep every 90 minutes, and performing extra investigations whenever a threat intelligence update arrives.
The system discovers all devices connected to the network and then scans each in order to compile a software inventory. This list of operating systems and applications with their version numbers is the basis of a patch management routine.
The patch manager keeps a lookout for patches and updates to its registered list of resources. When one appears, it readies the installers for rollout. System administrators can set up the patch manager so that it will apply all patches at the next available install time window.
Vulnerability Manager Plus is implemented as on-premises software and uses a distributed approach. Each endpoint on the network gets an agent program installed on it – there are agents available for Windows, macOS, and Linux. A central server, that installs on Windows and Windows Server coordinates agent activities and channels threat intelligence actions to them. It also summarizes feedback from each agent for analysis in the system console.
Who is it recommended for?
Every business needs to perform vulnerability scanning to prevent intrusion and malware. Small businesses will probably prefer the Free edition, which is able to scan up to 25 computers and includes the patching module. The paid versions are packaged to be accessible to SMBs with higher prices for larger businesses.
Pros:
- Preventive Security Measures: Focuses on closing potential entry points for malware.
- Continuous Monitoring: Offers round-the-clock scanning for vulnerabilities.
- Multi-platform Support: Compatible with Windows, macOS, and Linux systems.
Cons:
- Lack of Cloud Solution: No SaaS version available, limiting remote management capabilities.
- Complex for Small Businesses: May be overwhelming for smaller organizations without dedicated IT staff.
Vulnerability Manager Plus protects endpoints, network appliances, and web applications. It is available in three editions: Free, Professional, and Enterprise. The free version is limited to monitoring 25 computers. The Professional edition operates for one site and the Enterprise edition caters to WANs. Both paid systems are offered on a 30-day free trial.
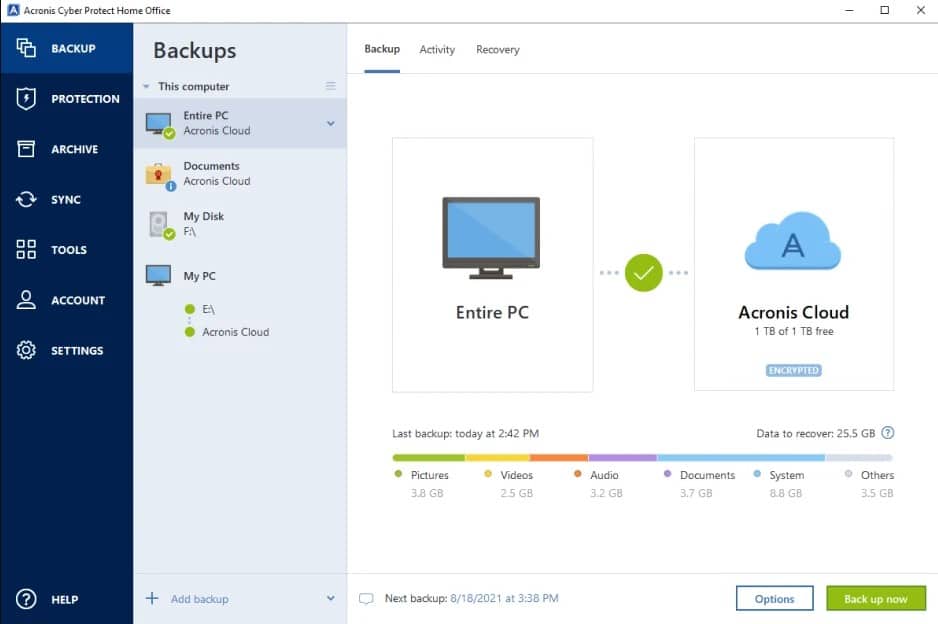
4. Acronis True Image (FREE TRIAL)
Acronis True Image is an on-device protection system for desktops and laptops. This service, previously known as True Image, has been revamped and renamed in order to cater to the “work from home” market. The system will protect your leisure activities on the Web as well as your remote work connections.
Key Features
- Integrated Anti-Malware: Protects against various forms of malware, including ransomware.
- Diverse Backup Options: Offers flexibility in data backup and recovery solutions.
- Cloud Storage Inclusion: Comes with an option for additional cloud storage.
Why do we recommend it?
Acronis True Image package is one tool in a range of Cyber Protect versions that cater to different types of businesses. All of these packages include the combination of anti-malware and backup services, which is ideal for protecting against ransomware. All files are scanned for malware when moving in and out of backup.
The anti-malware system in the package detects infection from a range of malicious processes, including ransomware. However, no anti-malware system is infallible and, just in case a new strain gets through, the Acronis service will have already backed up all of your data. This means you don’t need to bother paying the ransom to get your data back, you just restore it through the Acronis console. All files are pre-scanned for infection before uploading to backup.
You can choose to backup to removable storage, to a private cloud or public cloud systems, such as Azure or AWS, or to the Acronis Cloud servers. There are three plans for Acronis Cyber Protect Home Office and, apart from the base plan, these include cloud storage space – 1 TB included for free with the top plan.
Who is it recommended for?
Acronis True Image is for use by people who work at home – those who run their own small businesses or those who work telecommute for large businesses. The tool will protect computers running Windows and macOS but not those running Linux. It also covers mobile devices.
Pros:
- Versatile Data Protection: Suitable for both work and leisure activities on the web.
- Comprehensive Backup Service: Includes cloud and local backup options for data security.
- User-Friendly Interface: Designed for easy use by home office workers.
Cons:
- Limited Free Features: Full range of services available only in the paid version.
- No Linux Support: Does not cater to users operating on Linux platforms.
Acronis True Image installs on Windows and macOS. The service also includes some cloud-based elements, such as threat intelligence updates for anti-malware. The system is available for a 30-day free trial.
5. ESET Protect (FREE TRIAL)
ESET Protect provides on-device protection for all types of malware, including ransomware. The package is installed on each endpoint of your company and that includes mobile devices. The protection software will run on Windows, macOS, Linux, iOS, and Android.
Key Features:
- Broad Anti-Malware Coverage: Protects against a wide range of digital threats.
- Private Threat Intelligence: Offers tailored security insights for better protection.
- Managed Service Flexibility: Provides an option for comprehensive managed security.
Why do we recommend it?
ESET Protect provides immediate protection on the device. The installed unit looks for suspicious behavior, which includes file renaming and the start of encryption. It will block these activities immediately. The central controller will warn all other devices to block lateral movement. A vulnerability manager reduces the danger of infection.
There are four plan levels for ESET Protect, which are called Entry, Advanced, Complete, and Elite. The company also offers ESET Protect MDR, which is a managed security service that includes the services of security technicians.
Each higher plan has more features, expanding individual device protection to a coordinated XDR. Other benefits of upgrading include a vulnerability scanner and a patch manager. The top two plans cover storage devices and cloud applications as well as endpoints and they will also protect email systems both on your site and on the cloud.
Who is it recommended for?
The progression from device protection up to company-wide threat protection and intelligence sharing means that this package is suitable for businesses of all sizes. The minimum device count for a protection package is five for all plans except for the Elite edition, which will protect at least 26 devices.
Pros:
- Immediate On-Device Protection: Delivers real-time security directly on devices.
- Extensive Plan Options: Catering to businesses of various sizes with different needs.
- Collective Threat Intelligence: Enhances security through shared insights and responses.
Cons:
- Excludes Home Business Solutions: Not tailored for very small or home-based businesses.
- Device Count Restrictions: Minimum device requirements may limit accessibility for smaller entities.
The Entry edition is affordable for small businesses and ESET Protect Advance, the next plan up, doesn’t cost much more. You can investigate the ESET Protect system with a 30-day free trial.
6. Malwarebytes Anti-Ransomware
Although it started out in beta mode, this anti-ransomware tool has transformed into one of the best options on the market today. Being a tool created for a specific purpose, it doesn’t eat up processing power and, in fact, has a small digital footprint. Besides, Malwarebytes uses it as part of its bigger, more complete Malwarebytes Endpoint Protection & Response solution. This means, they are sure it is a great tool and have confidence in its performance.
Key Features
- Innovative Rollback System: Offers unique capabilities to reverse ransomware damage.
- Zero-Day Attack Protection: Guards against newly emerging threats effectively.
- Minimal Processor Impact: Operates efficiently without heavy system resource usage.
Why do we recommend it?
Malwarebytes Endpoint Detection and Response uses a similar method to the cloud-synching strategy used by Microsoft 365. That is, each file on an endpoint is copied up to a cloud copy as seen as any change is made. The tool keeps rollback versions of each file, which means that any ransomware encryption can easily be reversed.
Once installed, it runs in the background without the need for even an initial scan – it simply starts protecting the device and reacts in real-time. The beauty of Malwarebytes is its Ransomware Rollback technology. Any changes that were made to files – like being encrypted by a malware – can be reversed. This is done using backups that this anti-malware protection solution keeps for exactly this purpose.
Malwarebytes keeps an eye on all that is going on around it and keep tracks of which program or process did what change. When it realizes that something awry has happened it can easily roll back time and reverse any changes that were made regardless if it were a modification, deletion, or even encryption.
Thus, for those who might think that this is a lightweight tool, we can only say, “Do not underestimate it”.
Who is it recommended for?
This package is available in two plan levels. Both plans provide an anti-malware service and the upper plan adds on the backup system. The tool is priced per endpoint, which makes it scalable and suitable for businesses of all sizes. However, it is considerably more expensive that the Acronis tool.
Pros:
- Efficient Real-Time Protection: Operates unobtrusively in the background, providing continuous security.
- Powerful Rollback Capability: Can reverse various types of file alterations including encryption.
- Comprehensive Malware Coverage: Includes protection against a broad spectrum of malware.
Cons:
- Part of Larger Suite: May necessitate the purchase of additional tools not required by the user.
- Higher Cost: More expensive compared to some other standalone ransomware protection solutions.
The thing that makes Malwarebytes one of the best anti-malware tools out there is that it was designed to protect against the latest online security threats. It, therefore, has the ability to target the most recent malware threats that even some of the other “big league” antimalware solutions haven’t been able to flag yet.
7. SpinOne Ransomware Protection
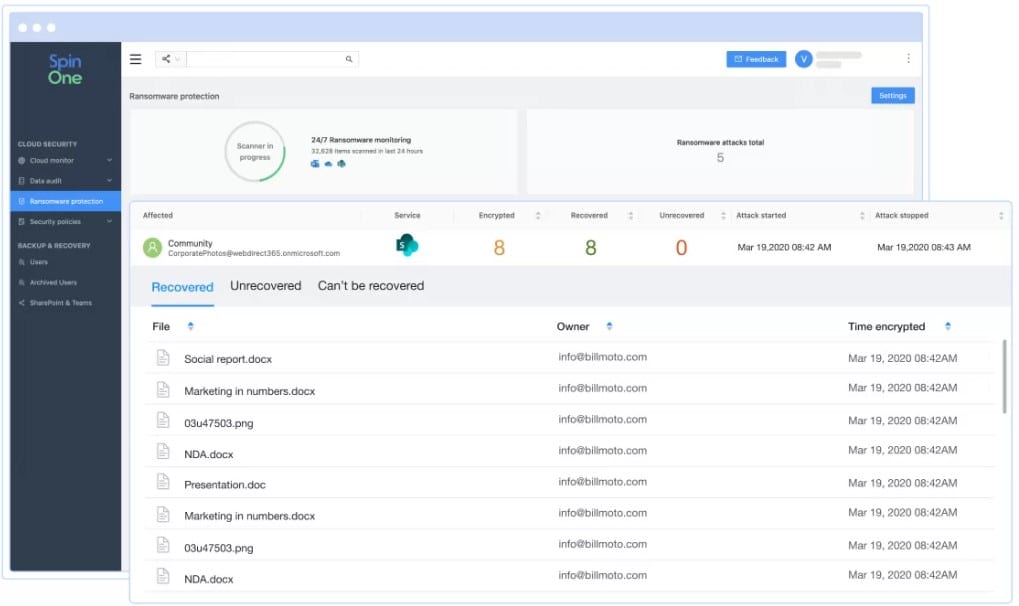
SpinOne from Spin.ai is a package of SaaS protection systems that are delivered from the cloud. This service integrates into a specific business productivity system with flavors for Microsoft 365, Google Workspace (Google G Suite), and Salesforce. The platform provides two strategies to defeat ransomware – ransomware activity detection and data backup.
Key Features:
- Automated Malware Detection: Identifies ransomware activity efficiently.
- Backup and Recovery Integration: Facilitates quick data restoration post-attack.
- Cloud Service Compatibility: Seamlessly works with major cloud platforms.
Why do we recommend it?
Spin.ai offers three system security packages and SpinOne is a bundle of all of them. This system specifically protects SaaS systems, so it would protect your data files in Google Drive and OneDrive. The wider package manages access to applications, which would include the productivity tools in Google Workspace and Microsoft 365.
Luck favors the prepared, and so SpinOne takes regular backups of your cloud storage space, which enables a rapid recovery in the event of any disaster, including a ransomware attack. Spin.ai technicians manage your data recovery and the company offers a 2-hour recovery deadline in its service level agreements (SLA). Backups can be stored on Azure, GCP, or AWS.
The protection system identifies compromised assets and then immediately revokes all API access to your cloud storage space. It then isolates the encrypted files to prevent the ransomware from spreading. The tool scans back through its records to see which applications recently accessed those damaged files to identify the source of the attack. It then raises an alert, restores the damaged files, and delivers a report of the event.
SpinOne has its own connection security systems so that the link between the Spin.ai system and your cloud platform does not provide a security weak point. The data transfers for backup and recovery are protected by encryption.
You get a range of options over data storage, which includes a local store on your site. The system offers a range of retention periods from 6 months to indefinite backups. However, each file is re-copied if it is updated on your primary cloud storage system.
Who is it recommended for?
SpinOne is a good choice for businesses that keep all of their data on cloud platforms and provide SaaS solutions for their users. It isn’t a good choice for companies that process and store data on their own servers because these data storage locations aren’t covered by the Sim.ai system.
Pros:
- Robust Cloud Integration: Ideal for businesses heavily reliant on cloud services.
- Guaranteed Recovery Time: Ensures minimal downtime in case of ransomware attacks.
- Comprehensive Data Protection: Includes both detection and recovery solutions.
Cons:
- Excludes On-Premises Servers: Not suitable for businesses relying on in-house servers.
- Niche Market Focus: Best suited for SaaS-dependent organizations, limiting its broader appeal.
You can get a 15-day free trial of SpinOne for G Suite, SpinOne for Microsoft 365, or SpinOne for Salesforce.
8. Bitdefender Antivirus Plus
This is, arguably, one of the best anti-ransomware software solutions out there. Again, although Bitdefender Antivirus Plus is a full anti-virus suite, and as a full-fledged defense system, it can keep your network safe from various sorts of attacks, it is the protection against potential ransomware that is quite remarkable.
Key Features
- Endpoint and Network Antimalware: Provides thorough protection for individual devices and networks.
- Sensitive Data Access Control: Enhances security for critical files and information.
- Phishing and Fraud Blocker: Offers additional layers of protection against online threats.
Why do we recommend it?
Bitdefender Antivirus Plus is an on-device AV that is able to detect and block a range of malware types, including ransomware. This package doesn’t offer any data protection process, such as backup, it relies on its dexterity to identify ransomware to keep your data safe. The package also gives you a VPN service.
This is mainly thanks to Safe Files, a feature that prevents sensitive documents and data storage from being accessed by unauthorized users. Bitdefender also has its own antimalware scan engine and multi-layered anti-ransomware protection.
Apart from fighting ransomware, Bitdefender Antivirus Plus also serves as an anti-phishing and anti-fraud protection tool and has an anti-tracking extension to seek and block web trackers. Are you worried about someone spying on you in the privacy of your office or living room? This suite’s Webcam Protection prevents apps from taking over your camera while Microphone Monitor alerts you when an application tries to access your microphone.
All of this is backed up by features like a password manager, banking protection, VPN, safe online shopping and much more. Surprisingly, although it is a heavy-duty antimalware solution, Bitdefender remains unobtrusive and doesn’t tie-up the resources of the machine it is supposed to be protecting.
Who is it recommended for?
This package is suitable for home users and small businesses. The AV software needs to be installed on each device and there is no central controller module for administrators. The package is only available for Windows and it protects PCs rather than servers. The tool is very affordable for small businesses.
Pros:
- Versatile Malware Protection: Effectively blocks a variety of digital threats.
- Data Safety Measures: Prioritizes the security of sensitive and personal data.
- Comprehensive Online Security: Extends protection to include phishing, fraud, and web trackers.
Cons:
- Single Device Focus: Lacks a central management system for broader network control.
- Limited to Windows PCs: Not suitable for servers or non-Windows operating systems.
Should a small business worry about ransomware?
Yes. SMBs are increasingly being targeted by ransomware gangs.
This is primarily for two reasons:
Being the perfect target: SMBs present juicier targets than individuals, they are also less secure than bigger businesses – they sit in a sweet spot.
No consequences: SMBs don’t have the power to track down or pursue hackers; even if they find out who was responsible for a ransomware attack they still won’t be able to do much about it – this encourages the attackers.
Anti Ransomware FAQs
What are the types of ransomware?
The two types of ransomware are called locker ransomware and crypto-ransomware. Locker ransomware attacks hijack access rights systems, preventing a user of a seized device from gaining access. A crypto-ransomware attack is a classic strategy that encrypts files to make them inaccessible.
Should I pay the ransomware gang to get the decryption key?
About 58 percent of ransomware victims pay to get the decryption key. On the one hand, you might not have a choice and can’t afford to lose important files. However, a company that pays the ransom encourages hackers and makes another attack more likely. A survey in 2018 discovered that 42 percent of victims that paid the ransom didn’t get the decryption key.
Does a small business need ransomware protection?
Yes. SMBs are increasingly being targeted by ransomware gangs.
This is primarily for two reasons:
- Being the perfect target: SMBs present juicier targets than individuals, they are also less secure than bigger businesses – they sit in a sweet spot.
- No consequences: SMBs don’t have the power to track down or pursue hackers; even if they find out who was responsible for a ransomware attack they still won’t be able to do much about it – this encourages the attackers.