SolarWinds is the leading provider of IT infrastructure monitoring and management software. The SolarWinds SIEM offering is confusingly named. The tool focuses on log files as a source of data. This activity is a characteristic of Security Information Management (SIM), a component of SIEM. The other part of SIEM is Security Event Management (SEM). The SolarWinds SIEM product is called the Security Event Manager but it is a SIM and not an SEM.
What are SIM and SEM in SIEM?
SIEM stands for Security Information and Event Management. It is a combination of SIM and SEM. SIM manages log files and uses them as a source of data for intrusion analysis; SEM watches live events on the network.
The basic terminology of SIEM is difficult to keep straight when examining the SolarWinds SIEM product because it deals with log files, not live network data. The software doesn’t include any live network monitoring, so it can’t be an SEM.
The SolarWinds Security Event Manager (SEM) is a SIM. It is a host-based intrusion detection system that examines the contents of log files for specific patterns of activities. SolarWinds has retreated from providing network traffic monitoring – the SolarWinds Log and Event Manager had that capability. The ability to integrate live NetFlow and sFlow data into the security monitor was dropped when SolarWinds rewrote the Log and Event Manager to create the Security Event Manager.
SIM systems have a number of advantages over network monitors because many types of attacks are conducted by stealth and no single piece of traffic can indicate that such an attack is going on. Typically, SIEM systems are meant to hunt down Advanced Persistent Threats (APTs), insider threats, and data loss events.
In an advanced persistent threat, a hacker group gets through traditional boundary defenses and establishes a long-term presence in the system. This could be by acquiring the credentials of a user account. Insider threats occur when an authorized user of the system decides to work against the interests of the business. This might be accidental because a hacker has duped the person into action by impersonating a superior. Other reasons for insider threats are blackmail and a sense of hostility towards the company after failing to get a promotion or being reprimanded.
A data loss event might also be accidental, the result of an employee being duped, or outright theft or malicious damage. “data loss” encompasses both the actual loss of data through deletion of files or the physical damage to servers and also the unauthorized disclosure of data.
Compliance reporting
The widespread adoption of Security Information and Event Management (SIEM) systems across various industries can largely be attributed to the growing importance of data protection standards. These standards mandate that businesses implement security measures to safeguard sensitive information, though they do not guarantee that data breaches or loss events will never occur. Instead, they focus on establishing a framework for responding to and mitigating the effects of such incidents when they do happen.
Data protection standards typically include specific reporting protocols to ensure that businesses notify individuals whose data has been compromised. Transparency about a breach is just as crucial as preventing one, as it allows affected parties to take necessary actions to protect themselves. Proper notification can help reduce potential damage and maintain trust between organizations and their customers.
A further key aspect of data protection standards involves regular system auditing, which is typically conducted by third-party auditors. These audits are designed to verify that an organization has adhered to security protocols, either by preventing data theft or by ensuring a timely and transparent response to any breach. To meet these requirements, businesses must rely heavily on the collection and management of system logs. Logs provide essential information about security events and the actions taken by the system to address them.
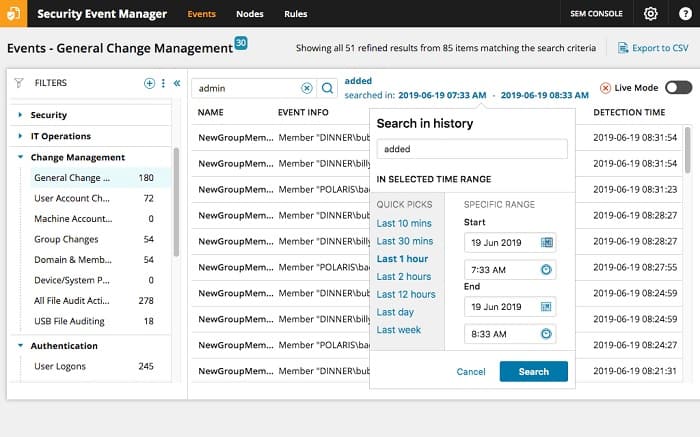
For an effective log management strategy, it’s critical to have an organized structure that allows for efficient data retrieval. A comprehensive log management system should include capabilities for easy searching, sorting, and aggregating data to assist with audits and compliance reporting.
SolarWinds SEM offers efficient log management features and reporting tools that support compliance with various security standards such as PCI DSS, SOX, HIPAA, GLBA, and NERC CIP. By utilizing these features, organizations can ensure they meet their data protection and regulatory obligations.
SolarWinds Security Event Manager Overview
The SolarWinds Security Event Manager was originally called the Log and Event Manager. As well as gathering log messages generated by operating systems, firmware, and software, the security monitor generates its own log messages that contribute to the monitoring of a system.
Log manager
The main purpose of the tool is to collect all available log messages, consolidate them by reformatting them into a common format, and then file those messages.
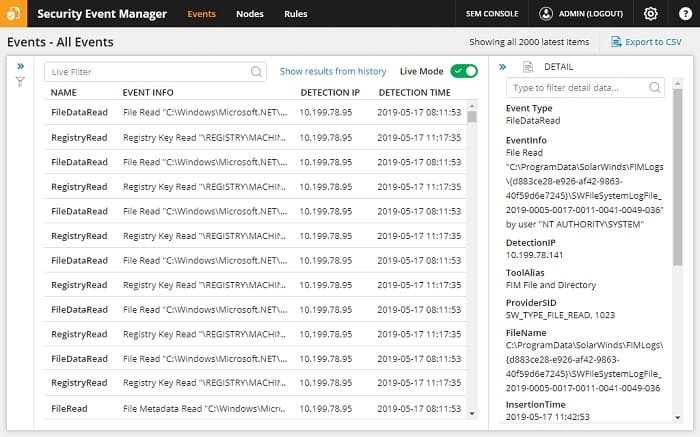
The SEM displays log messages live in the console as they are discovered. This gives the system a near-live view of events on the networks. Those files are then stored in a searchable format and the SEM includes tools to process the data in log files for analysis.
The log file manager provides facilities for instant access to recent logs and archiving for older log files with a method of restoring them whenever they are needed.
File integrity monitor
The File Integrity Monitor (FIM) built into the SolarWinds Security Event Manager is an essential facility for any business that relies on log file contents for security surveillance. Hackers who are aware of SIEM systems – and all of them are – just need to access log files and delete any evidence of their activities in order to remain hidden. FIM blocks log file tampering and can also protect any other type of file or files stored in specific directories.
The FIM records the usernames of all accessors to a protected file and logs all access events. Protection of log files is automatic and the FIM also scans for malware activity in files. The service can kill malicious processes that are detected making attempts on file access.
Threat intelligence feed
Threat intelligence is a key characteristic in the definition of a SIEM. Log searches have to have a specific purpose to qualify as a security action and a rule base of anomalies to look out for makes those searches meaningful.
SolarWinds supplies a threat intelligence feed periodically over the Internet to all running instances of the Security Event Manager. This stream comes in the form of adjustments to the search algorithms used by SEM to detect suspicious behavior when scanning through log files.
Detection rules transmitted with the threat intelligence updates include backlists of IP addresses and domains that are believed to be the bases of operations used by hackers.
Forensic analysis
The SEM correlated logs provide source data for the security system to search in relation to the anomalies highlighted by the rules passed with the threat intelligence feed. That data is also available for manual analysis, which is assisted by the data search tools and graphical data representation tools available in the Security Event Manager console.
While the automated detection system will spot an intrusion, the log analyzer gives the tech team an opportunity to search back through historical records to look for evidence of that intruder’s initial entry into the network.
Information gleaned from these root cause investigations enable the technical management team to identify system vulnerabilities so they can harden the infrastructure against repetitions of that attempt. Log analysis can also identify a hijacked user account.
Automated incident response
The Security Event Manager is able to monitor other security tools, particularly firewalls. The interaction with firewalls is a two-way channel. This enables the SEM to take action on the discovery of an intrusion. The system can alter firewall rules to block access to an intruder’s IP address or block a domain that is the source of infected web pages or emails.
The other main target of automated response is Active Directory. The SEM can be allowed access to suspend user accounts that are identified as the source of the anomalous activity or repeated attempts to make unauthorized access to files. Other responses can be the sandboxing of downloads and the killing of suspicious processes.
The threat response section of the Security Event Manager is called Active Response. As well as interacting with firewalls, this module is able to implement other workflows according to the type of threat that has been detected.
The triggers for automated responses are the alerts generated by the analytical processes of SEM. The response is not automatic. The user decides whether to activate automated responses and the rules that initiate actions can be modified.
System managers that are wary of automation can reduce the extent of automation down to just a generic email that can be sent as a response to an identified attack. In any case, all alerts are shown in the system console and can also be distributed to key staff as emails or text messages.
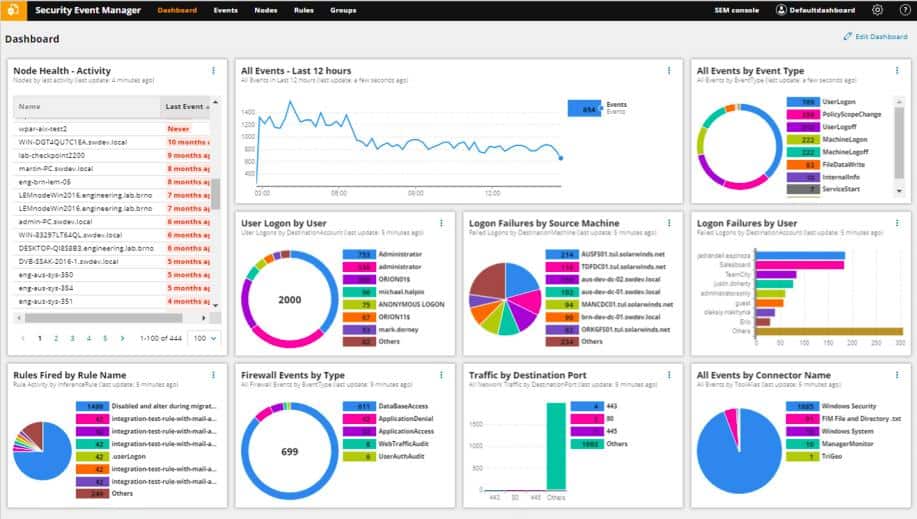
SolarWinds Security Event Manager dashboard
The dashboard for the Security Event Manager is accessed through a browser. The main screen of the console shows a busy grid of summary data, mostly represented as graphs and charts.
Log search details screens have predominately text for content rather than graphics. The main focus of these screens is the records extracted from log files.
SolarWinds SIEM configuration options
SolarWinds SIEM runs on a virtual machine – it is a virtual appliance. The software can be installed on Microsoft Azure servers and Amazon Web Services (AWS). Those who want to install SolarWinds Security Event Manager will need to run it on Hyper-V or VMWare vSphere.
SEM agents for log collection will install on:
- HPUX on Itanium
- IBM AIX 7.1 TL3, 7.2 TL1 and later
- Linux
- macOS Mojave, Sierra, High Sierra
- Oracle® Solaris 10 and later
- Windows (10, 8, 7, Vista)
- Windows Server (2019, 2016, 2012, 2008 R2)
Remote access to the console is possible with Google Chrome and Mozilla Firefox browsers.
The SEM reports module operates outside of the VM and can be installed on Windows and Windows Server environments.
Pros:
- Enterprise focused SIEM with a wide range of integrations
- Simple log filtering, no need to learn a custom query language
- Dozens of templates allow administrators to start using SEM with little setup or customization
- Real-time analysis tool helps find anomalous behavior and outliers on the network
Cons:
- SEM Is an advanced SIEM product built for professionals, requires time to fully learn the platform
SolarWinds offers the Security Event Manager on a 30-day free trial.
Alternatives to SolarWinds Security Event Manager
It is unusual that SolarWinds decided to remove the live network traffic monitoring capabilities of the Log and Event Manager when it created the Security Event Manager. This means that the SolarWinds SIEM isn’t really a full implementation of the classic SIEM definition.
For more detailed information about how SIEM systems work, please see The Best SIEM Tools. If you don’t have time to read that article, but would like recommendations on other SIEM systems, here is our list of the best alternatives to SolarWinds SIEM.
- ManageEngine Log360 (FREE TRIAL) This super-bundle ties together many of the security systems offered by ManageEngine and that includes the SIEM system offered by the EventLog Analyzer. The package also provides Active Directory auditing, file integrity monitoring, and cloud service protection. Runs on Windows Server and is available for a 30-day free trial.
- ManageEngine EventLog Analyzer (FREE TRIAL) This is the SIEM core and log management module of the Log360 bundle, so if you find that you don’t need all of the extra features of the wider package, you could just get this tool for threat hunting. It installs on Windows Server and Linux and you can get it on a 30-day free trial.
- Datadog Security Monitoring This SIEM-based security system is an option on a cloud-based network monitor.
- McAfee Enterprise Security Manager A highly-regarded SIEM tool that includes user and entity behavior analysis to automatically adjust alert thresholds. It runs on macOS as well as Windows.
- Heimdal Threat Hunting and Action Center This cloud-based scans data uploaded by on-device AV units for threats and sends back threat response instructions, including system hardening steps for as-yet-unaffected endpoints. The hybrid package protects computers running Windows, macOS, and Linux and mobile devices running Android and iOS.
- Splunk Enterprise Security Security features available with a well-known network analyzer. It installs on Windows and Linux.
- OSSEC A free open-source host-based intrusion detection system that excels at log analysis. This can be enhanced with a feed from NetFlow to give live traffic analysis as well. It runs on Windows, Mac OS, Linux, and Unix.
- LogRhythm NextGen SIEM Platform This tool includes AI-based machine learning methods to adjust alert thresholds and reduce the number of false positives. It installs on Windows and Linux.
- AT&T Cybersecurity AlienVault Unified Security Management Long-running SIEM that draws its threat intelligence from an open-source register of indicators of compromise. It runs on macOS as well as Windows.
- RSA NetWitness A network traffic monitor with analytical tools to detect intrusion. Suitable for large businesses. It runs on a VM.
- IBM QRadar A security intelligence platform that includes a SIEM module. The SIEM includes vulnerability scanning, a threat intelligence feed, live traffic analysis, and log management functions. It runs on Windows Server.
SolarWinds SIEM FAQs
Is SolarWinds SEM a SIEM?
SolarWinds Security Event Manager (SEM) is a SIEM. Despite the name, this tool is mainly a Security Information Manager (SIM) because it explores log messages for signs of system breaches. It is possible to make the tool a full SIEM by channeling live SNMP data into it, thus providing the SEM part of the SIEM formula.
What does SIEM stand for?
SIEM is a combination of two security scanning techniques. The first of these is Security Information Management (SIM), which scans system log messages for security threats. The second element is System Event Management (SEM), which looks through live network activity records for signs of threats. Together, these two scanning methods form Security Information and Event Management (SIEM).
What is the difference between SIM SEM and SIEM?
The emergence of SIEM, which stands for Security Information and Event Management has created confusion about the meaning of the two technologies that formed SIEM. These two original services were SIM, which stands for Security Information Management, and SEM, which means Security Event Management. SIM involves searching through log files for signs of threats and SEM involves reading live activity data, which is usually network traffic information.