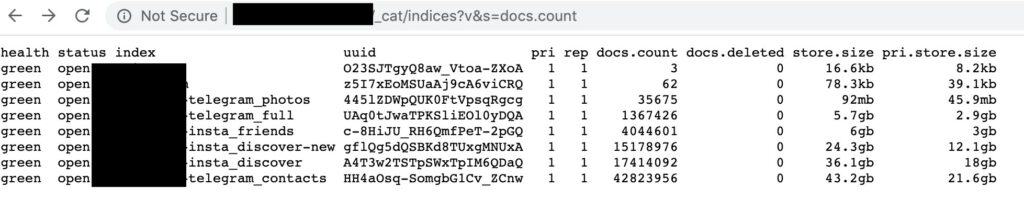
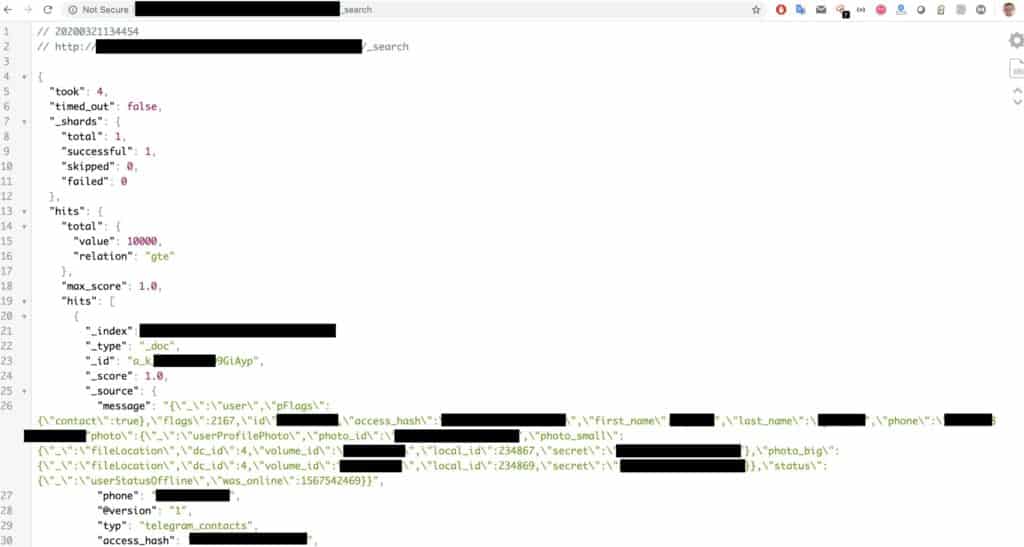
42 million records from a third-party version of messaging app Telegram used in Iran was exposed on the web without any authentication required to access it. Comparitech worked with security researcher Bob Diachenko to uncover and report the exposure, which included usernames and phone numbers, among other data.
The data was posted by a group called “Hunting system” (translated from Farsi) on an Elasticsearch cluster that required no password nor any other authentication to access. It was removed after Diachenko reported the incident to the hosting provider on March 25.
Telegram says the data came from an unofficial “fork” of Telegram, a version of the app unaffiliated with the company. Telegram is an open-source app, allowing third parties to make their own versions of it. Because the official Telegram app is frequently blocked in Iran, many users flock to unofficial versions.
A Telegram spokesperson told Comparitech, “We can confirm that the data seems to have originated from third-party forks extracting user contacts. Unfortunately, despite our warnings, people in Iran are still using unverified apps. Telegram apps are open source, so it’s important to use our official apps that support verifiable builds.”
The incident follows a similar one in 2016 when Reuters reported 15 million Telegram user IDs, phone numbers, and one-time verification codes were identified by Iranian hackers, resulting in more than a dozen compromised accounts.
Timeline of the exposure
The data was exposed for about 11 days before it was removed.
- March 15: The database was indexed by search engine BinaryEdge
- March 21: Diachenko discovered the exposed data and began investigating
- March 24: Diachenko sent an abuse report to the hosting provider
- March 25: The Elasticsearch cluster was deleted.
It looks like other unauthorized parties were able to access the data while it was exposed. We found at least one user had posted the data to a hacker forum.
What data was exposed?
The database contained more than 42 million records consisting of user data originating from Iran.
- User account IDs
- Usernames
- Phone numbers
- Hashes and secret keys
The hashes and secret keys from the database can’t be used to access accounts. They only work from inside the account to which they belong, according to a Telegram spokesperson.
Dangers of exposed data
The information contained in this exposed database poses a clear risk to users. Not only does it reveal who in Iran uses Telegram (or a Telegram fork), it also opens them up to attack.
SIM swap attacks are one example. A SIM-swap attack occurs when the attacker convinces a phone carrier to move a phone number to a new SIM card, allowing them to send and receive the victim’s SMS messages and phone calls. The attacker could then receive their one-time access verification codes, granting full access to app accounts and messages.
Affected users could also be at risk of targeted phishing or scams using the phone numbers in the database.
A brief history of Telegram in Iran
Telegram is the most popular messaging app in Iran with more than 50 million users nationwide. It’s favored for its security, which provides end-to-end encryption for messages. That means the government and other third parties can’t spy on conversations that they happen to intercept.
In 2016, hackers identified the phone numbers of 15 million Telegram users in Iran. Experts say national phone carriers likely intercepted the text messages used to activate new accounts on Telegram. The phone companies then handed those messages and phone numbers over to hackers, who used them to break into more than a dozen accounts.
Iranian authorities ordered telecoms to temporarily block access to Telegram on several occasions between 2015 and 2017. It was blocked permanently in early 2018 following nationwide anti-government protests and civil unrest.
Despite that, Telegram remains the most popular messaging app in the country. Many users access it through proxies and VPNs. Some, however, opt for third-party forks of Telegram, unnofficial versions of the app that the Iranian government might not have blocked.
Telegram apps are open source so that anyone can independently verify the code is authentic. This has, however, also led to several forks, alternative versions of Telegram run by third parties. The operators of these forks are not affiliated with Telegram even though they share the apps’ code, and they do not necessarily use adequate security measures or even care about users’ privacy.
How we discovered this exposure and why we reported it
Comparitech teams up with security researcher Bob Diachenko to find databases on the web that are not properly secured. When we find exposed data, we immediately report the incident according to responsible disclosure guidelines.
We then investigate the data to determine to whom it belongs and what it contains. Our aim is to evaluate the potential harm to end users.
Once the data has been removed or secured, we then publish a report like this one to raise awareness. We hope to mitigate negative consequences, such as further attacks against those users whose personal information was exposed.
Previous reports
Comparitech and Diachenko teamed up on a number of data exposure reports impacting millions of people, including:
- 8 million UK shopping records exposed
- 250 million Microsoft customer service and support records exposed
- 267 million Facebook user IDs and phone numbers exposed online
- 2.7 billion exposed email addresses from mostly Chinese domains, 1 million of which included passwords
- Detailed personal records of 188 million people found exposed on the web
- 7 million student records exposed by K12.com
- 5 million personal records belonging to MedicareSupplement.com exposed to public
- 2.8 million CenturyLink customer records exposed
- 700k Choice Hotels customer records leaked