Wi-Fi Protected Access 2 (WPA2) is a security certification program developed by the Wi-Fi Alliance to secure wireless computer networks. Depending on the type and age of your wireless router, you will have a few encryption options available. The two main ones for WPA2-Personal (the edition used by home or small business users) are Advanced Encryption Standard (AES) and the older Temporal Key Integrity Protocol (TKIP), or a combination of both.
In this article, we will explain what AES and TKIP are and suggest which option you should choose for your WPA2-supported devices. You need to choose the best encryption mode — not only for security reasons — but because the wrong mode can slow your device down. If you choose an older encryption mode, even if your wi-fi router supports a faster encryption type, data transmission will automatically slow down to be compatible with older devices it connects with.
We will also explain some wi-fi security terms related to WPA2. For instance, the terms certifications, standards, protocols, and programs are sometimes (confusingly) used interchangeably, and often incorrectly. Is AES a protocol or an encryption type? Is WPA2 a protocol or a standard? (Spoiler alert: AES is a standard and WPA2 is a certification.) It is OK to be a little lenient about wi-fi terminology, as long as you know what these terms really mean. This article sets the record straight. And yes, we use the term “mode” very loosely to describe WPA2 encryption and authentication settings.
WPA2 101 – a (very) brief overview
There are two versions of WPA2: Personal (for home and office use) and Enterprise (for corporate use) editions. In this article, we will focus on the former but will compare it to the Enterprise version, which will help illustrate what WPA2-Personal does not do.
How reliable are common wi-fi security certifications?
Unfortunately, wireless networks can never be 100% secure. Indeed, according to Comparitech security researcher, Lee Munson: “The best you can hope for is security that is good enough [to deter hackers], or at least better than an alternative target.”
Part of the problem is historical. When wireless networking was first introduced, manufacturers of networking equipment tried to make things as easy as possible for inexperienced consumers. This resulted in out-of-the-box configuration that made connecting wirelessly easy, but also insecure.
So, exactly how secure is WPA2 compared to other commonly-used wi-fi certifications? Until WPA3 came long, WPA2 was considered, KRACKs and all, the most secure option. WPA2’s current vulnerabilities may be effectively patched, but you still need to choose the best encryption type for your wi-fi device and your usage requirements. If you are a small business with older devices, for instance, you may need to sacrifice speed for security, or upgrade your devices. If you are a large organization, you may decide to ditch WPA2 altogether and start planning to roll out WPA3 as soon as possible.
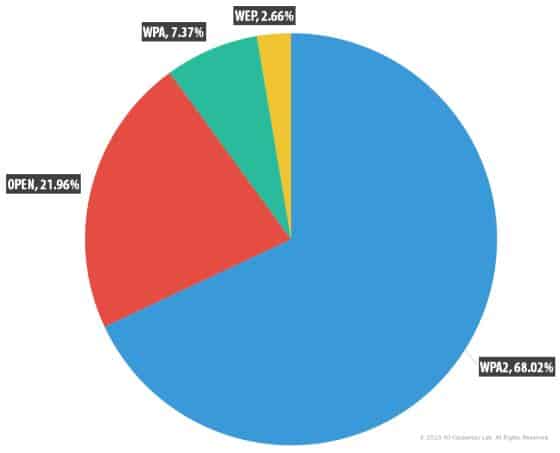
Wi-fi encryption connection standards used in public wi-fi hotspots globally (Source: Kaspersky Security Network (KSN))
Which certifications are the most secure?
There are several wi-fi certifications currently in use. These provide varying levels of security:
- Open – No security at all
- Wired Equivalent Privacy (WEP) – Very unreliable and uses the RC4 cipher, initially embraced for being very fast and simple to implement. Once popular – according to WayBack Machine, Skype used a modified version around 2010 – it has since been deemed very insecure. WEP uses an authentication method where users all share the same key, so if one client is compromised, everyone on the network is at risk. WPA-PSK (Pre-Shared Key) has the same problem. According to Webopedia, WEP is insecure as, like other wi-fi broadcasts, it sends messages using radio waves which are susceptible to eavesdropping, effectively providing security tantamount to a wired connection. Encryption does not stop hackers from intercepting messages and the problem with WEP is it uses static encryption (one key for all packets for all devices on a network), putting all devices at risk, a potentially nice big haul for hackers. The thieves can then attempt to decrypt the data at their leisure offline. One of the things WPA does is generate a unique key for each device, limiting the risk to other clients when one device on a network is compromised.
- WPA – Uses the ineffective TKIP encryption protocol, which is not secure. TKIP itself uses the RC4 cipher, and AES is optional for WPA. A good metaphor for how WPA works comes from a Super User post: “If you think of a foreign language as a kind of encryption, WPA is a bit like the situation where all machines connected to this WPA network speak the same language, but it’s a language that’s foreign to other machines. So, of course, machines that are connected to this network can attack each other and hear/see all packets sent/received by all the others. The protection is only against hosts which are not connected to the network (e.g. because they don’t know the secret password).”
- WPA2 – Reasonably secure but vulnerable to brute-force and dictionary attacks. Uses AES encryption and introduces Counter Mode with Cipher Block Chaining Message Authentication Code (CCMP), strong AES-based encryption. It is backwards-compatible with TKIP. Vendors have released patches for many of its vulnerabilities, e.g. KRACK. One of WPA2-Personal version’s major security drawbacks is Wi-Fi Protected Setup (WPS), which allows users to quickly set up a secure wireless home network. According to US-Cert, “Freely available attack tools can recover a WPS PIN in 4-10 hours.” It advises users to check for updated firmware from their vendor to plug this vulnerability. WPA2-Enterprise is more secure but there are some drawbacks.
- WPA3 – The most secure option, though not immune to attack (see “WPA3 security” later in the article).
AES, TKIP, or both, and how do they work?
The two main WPA2 encryption methods have several important differences beyond just using different key lengths. Let’s look at each in turn:
TKIP
According to Wikipedia, TKIP was designed to “replace” the then vulnerable WEP “standard” without having to make changes to the hardware that was running the Wired Equivalent Privacy (WEP) standard. It uses the RC4 cipher.
Network World explains TKIP does not actually replace WEP; it is a “wrapper”. Unfortunately, it is wrapped around the fundamentally unsafe WEP, the reason being it was intended as a temporary measure, because nobody wanted to throw away all the hardware investments they had made, and it was able to be quickly deployed. The lattermost reason was enough for vendors and business managers to embrace it enthusiastically. In its day, TKIP hardened WEP security by:
- Mixing a base key, the MAC address of an Access Point (AP), and a packet serial number – “The mixing operation is designed to put a minimum demand on the stations and access points, yet have enough cryptographic strength so that it cannot easily be broken.”
- Increasing the key length to 128 bits – “This solves the first problem of WEP: a too-short key length.”
- Creating a unique 48-bit serial number which is incremented for each packet sent so no two keys are the same – “This solves another problem of WEP, called “collision attacks,” which can occur when the same key is used for two different packets.
- Reducing the risk of replay attacks with the expanded initialization vector (IV) mentioned above – “Because a 48-bit sequence number will take thousands of years to repeat itself, no one can replay old packets from a wireless connection — they will be detected as out of order because the sequence numbers won’t be right.”
How vulnerable is TKIP really? According to Cisco, TKIP is vulnerable to packet decryption by an attacker. However, only the authentication key can be stolen by an attacker, not the encryption key.
“With the recovered key, only captured packets may be forged in a limited window of at most 7 attempts. The attacker can only decrypt one packet at a time, currently at a rate of one packet per 12-15 minutes. Additionally, packets can only be decrypted when sent from the wireless access point (AP) to the client (unidirectional).”
The problem is, if the white hats are discovering discover larger vectors for inserting attacks, so are the black hats.
There is a downside when TKIP is used with PSK. “With 802.1X authentication, the session secret is unique and transmitted securely to the station by the authentication server; when using TKIP with pre-shared keys, the session secret is the same for everyone and never changes — hence the vulnerability of using TKIP with pre-shared keys.”
AES
AES (based on the Rjiandael algorithm) is a block cipher (the “S” actually stands for standard and is another instance of confusing terminology) used by the protocol called CCMP. It converts plaintext into ciphertext and comes in key lengths of 28, 192, or 256 bits. The longer the key-length, the more inscrutable the encrypted data by hackers.
Security experts generally agree AES has no significant weaknesses. AES has only been successfully attacked a few times by researchers, and these attacks were mainly side-channel ones.
AES is the encryption of choice for the US Federal government and NASA. For more reassurance, visit Stack Exchange’s Crypto forum. For well-explained technical details about how AES works, which is out of the scope of this article, visit our “What is AES encryption” guide.
Wi-fi terms and acronyms you should know
Certifications and standards
Although WPA2 is a certification program, it is often referred to as a standard and sometimes as a protocol. “Standard” and “protocol” are descriptions used often by journalists and even the developers of these certifications, but the terms can be a little misleading when it comes to understanding how standards and protocols relate to wi-fi certification — if not downright incorrect.
We can use the analogy of a vehicle being certified as roadworthy. The manufacturer will have guidelines that specify safety standards. When you buy the car, it will have been certified as safe to drive by an organization that specifies the standards for vehicle safety.
So, while WPA2 should be called a certification, it could loosely be called a standard. But, to call it a protocol confuses the meaning of actual protocols – TKIP, CCMP, and EAP – in wi-fi security.
Protocols and ciphers
Another layer of confusion: AES is the acronym for Advanced Encryption Standard. And, according to a Stack Exchange user, TKIP is not actually an encryption algorithm; it is used to ensure data packets are sent with unique encryption keys. The user, Lucas Kauffman, says, “TKIP implements a more sophisticated key mixing function for mixing a session key with an initialization vector for each packet.” Incidentally, Kauffman defines EAP as an “authentication framework”. He is correct in that EAP specifies the way messages are transmitted; it does not itself encrypt them. We will touch on this again in the next section.
WPA2, and other wi-fi certifications, use encryption protocols to secure wi-fi data. WPA2-Personal supports multiple encryption types. WPA and WPA2 are backwards-compatible with WEP, which only supports TKIP.
Juniper refers to encryption protocols like AES and TKIP as encryption ciphers. A cipher is simply an algorithm that specifies how an encryption process is performed.
According to AirHeads Community:
“You often see TKIP and AES referenced when securing a WiFi client. Really, it should be referenced as TKIP and CCMP, not AES. TKIP and CCMP are encryption protocols. AES and RC4 are ciphers, CCMP/AES and TKIP/RC4. You can see vendors are mixing a cipher with a encryption protocol. If taking an exam an easy way to remember the difference is to remember TKIP and CCMP end in ‘P’ for encryption protocol. [sic]”
As does EAP, although it is an authentication, not an encryption protocol.
The bottom line:
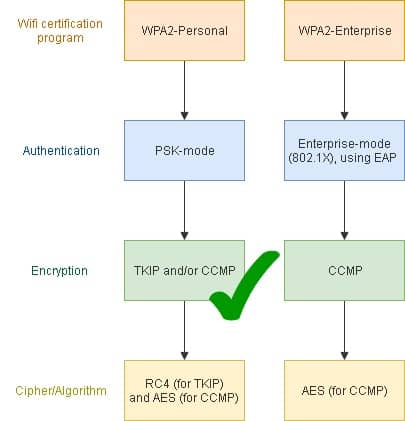
- WPA2-Personal – Supports CCMP (which most people call AES) and TKIP.
- WPA2-Enterprise – Supports CCMP and Extensible Authentication Protocol (Extensible Authentication Protocol (EAP).
WPA2 encryption and authentication
Authentication – PSK versus 802.1X
Like WPA, WPA2 supports IEEE 802.1X/EAP and PSK authentication.
WPA2-Personal – PSK is the authentication mechanism used to validate WPA2-Personal users making a wi-fi connection. It was designed primarily for general home and office use. PSK does not need an authentication server to be set up. Users log in with the pre-shared key rather than with a username and password as with the Enterprise edition.
WPA2-Enterprise –The original IEEE 802.11 standard (the “roadworthy” standard for wi-fi certification) was released in 1997. Later versions were often developed to improve the speed of data transmits and catch up with new security technologies. The latest WPA2- Enterprise versions conforms with 802.11i. Its underlying authentication protocol is 802.1X, which enables wi-fi devices to be authenticated by username and password, or using a security certificate. 802.1X authentication is deployed onto an AAA server (typically RADIUS) that provides centralized authentication and user management functionality. EAP is the standard used to transmit messages, and authenticate client and server authenticator before delivery. These messages are secured via protocols such as SSL, TLS and PEAP.
Encryption – “seeds” and PMK
WPA2-Personal – PSK combines a passphrase (pre-shared key) and an SSID (which is used as a “seed” and is visible to everyone in range) to generate encryption keys. The generated key – a Pairwise Master key (PMK) – is used to encrypt data using TKIP/CCMP. The PMK is based on a known value (the passphrase), so anyone with that value (including an employee who leaves the company) could capture the key and potentially use brute force to decrypt traffic.
A few words on seeds and SSIDs.
- SSIDs – All the network names that appear in your device’s list of wi-fi hotspots are SSIDs. Network analyzing software can scan for SSIDs, even those supposedly hidden. According to Microsoft’s Steve Riley, “An SSID is a network name, not — I repeat, not — a password. A wireless network has an SSID to distinguish it from other wireless networks in the vicinity. The SSID was never designed to be hidden, and therefore won’t provide your network with any kind of protection if you try to hide it. It’s a violation of the 802.11 specification to keep your SSID hidden; the 802.11i specification amendment (which defines WPA2, discussed later) even states that a computer can refuse to communicate with an access point that doesn’t broadcast its SSID.”
- Seeds – The SSID and SSID length are manipulated before being roped into becoming part of the generated PMK. The SSID and SSID length are used as seeds, which initialize a pseudorandom number generator used to salt the passphrase, creating a hashed key. That means passwords are hashed differently on networks with different SSIDs, even if they share the same password.
A good passphrase can mitigate the potential risk associated with using an SSID as a seed. A passphrase should be generated randomly and changed often, particularly after using a wi-fi hotspot and when an employee leaves a company.
WPA2-Enterprise – After the RADIUS server has authenticated the client, it returns a random 256-bit PMK that CCMP uses to encrypt data for the current session only. The “seed” is unknown, and every session requires a new PMK, so brute force attacks are a waste of time. WPA2 Enterprise can, but does not ordinarily, use PSK.
What encryption type is best for you, AES, TKIP, or both? (Solved)
The original question posed in this article was should you use AES, TKIP, or both for WPA2? For routers made before 2018, you should use WPA2 with AES. However, even this may not be possible with very old devices. If this is the case, use one of the options below.
Selecting an encryption type on your router
Your choices (depending on your device) may include:
- WPA2 with TKIP – You should only select this option if your devices are too old to connect to the newer AES encryption type
- WPA2 with AES – This is the best (and default) choice for newer routers that support AES. Sometimes you will only see WPA2-PSK, which usually means your device supports PSK by default.
- WPA2 with AES and TKIP – This is an alternative for legacy clients that do not support AES. When you use WPA2 with AES and TKIP (which you may want to do if communicating with legacy devices), you could experience slower transmit speeds. AirHead Community explains this is because “group ciphers will always drop to the lowest cipher.” AES uses more computing power, so if you have many devices, you could see a reduction in productivity around the office. The maximum transfer rate for networks using WEP or WPA (TKIP) passwords is 54 Mbps (Source: CNet).
- WPA/WPA2 – Similar to the option directly above, you can select this if you have some older devices, but it is not as secure as the WPA2-only option
On your device, instead of WPA2, you may be shown the option “WPA2-PSK”. You can treat this as the same thing.
Routers — and other wi-fi devices — certified after July 2020 are required to support WPA3. This is more secure than WPA2, so is the preferred option when available.
Tips to harden PSK security
Terrence Koeman’s comments on Stack Exchange make for enlightening reading about why WPA2-Enterprise is more secure than WPA2-Personal. He also provides the below tips:
- Set your SSID (the PMK “seed”) to a random string of as many digits as you are allowed which will make the PMK less vulnerable to brute-force attacks
- Create a long random PSK and change it regularly
- A unique SSID may make you vulnerable to thieves who can more easily look you up on Wigle. If you are really paranoid, you should consider using a VPN instead.
What’s next? WPA3 has been released
According to NetSpot, “Probably the only downside of WPA2 is how much processing power it needs to protect your network. This means more powerful hardware is needed to avoid lower network performance. This issue concerns older access points that were implemented before WPA2 and only support WPA2 via a firmware upgrade. Most of the current access points have been supplied with more capable hardware.” And, most vendors continue to supply WPA2 patches.
WPA2 is gradually being phased out and replaced by WPA3. It was released in June 2018 after the identification of a security vulnerability called KRACK in WPA2 the previous year. Although patches for the KRACK vulnerability have been released, WPA2 is not nearly as secure overall as WPA3. Dion Phillips, writing for InfiniGate, thinks, “… it is doubtful that current wireless devices will be updated to support WPA3 and far more likely that the next wave of devices will be put through the certification process.”
You got it; in the end, it is likely you will have to buy a new router. In the meantime, to stay safe, you can patch and secure WPA2.
There have been no documented reports of KRACK attacks yet but WPA3 certification provides far more security than just plugging the KRACK vulnerability. Currently an optional certification program, it will in time become mandatory as more vendors adopt it. Learn more about WPA2 and 3 with Comparitech’s article on What is WPA3 and how secure is it?
WPA3 security
While WPA3’s security upgrades patched up many of WPA2’s holes, it wasn’t perfect. In 2019, researchers published findings that showed how an attacker within range of their victim could recover the victim’s password. The attack worked despite WPA3’s underlying Dragonfly handshake, which aimed to make it impractical to crack a network’s password.
The attack is worrying, because it means that an attacker could access sensitive data such as login details if they were being entered without a HTTPS connection (you should always make sure you have a HTTPS connection whenever you enter your password or other sensitive information into a website, otherwise the data is vulnerable).
The details of the attack are explained by the researchers in their Dragonblood: Analyzing the Dragonfly Handshake of WPA3 and EaP-pwd paper. Alongside the Wi-Fi Alliance and CERT/CC, they notified the affected vendors and helped them implement countermeasures.
WPA3 security guidelines
In late 2019, the Wi-Fi Alliance released a set of security guidelines for WPA3 to minimize the risks of attacks:
- Strong passwords – This is pretty standard security advice, but passwords used with WPA3-Personal should be complex. They should also be long and unique. The implementation should also limit the number of authentication attempts to prevent hackers from brute-forcing the password.
- Denial of service protection – Access point implementations should handle Simultaneous Authentication of Equals (SAE) operations on non-privileged processing queues. If overwhelmed, they must not result in the failure of the entire basic service set through CPU resource consumption (see the Denial of service section of the above link for further details).
- Recommended Diffie-Hellman groups – Only Diffie-Hellman groups 15-21 should be used (see the Suitable Diffie-Hellman group section from the link above) in SAE implementations. Group 19 is mandatory, while the other groups are optional. The selected Diffie-Hellman group’s strength must be equal to or greater than the strength of the encryption cipher that is offered.The SAE implementation’s security parameter k must be a value of at least 40.
- Side-channel attacks – SAE implementations must avoid code execution differences that release side channel information and can be collected through cache.
- WPA3-Personal Transition Mode – If this does not meet the security requirements for a deployment, WPA3-Personal and WPA-2 Personal should be deployed on their own individual SSIDs. They should use passwords that are unique and logically separated (see the WPA-3 Personal Transition Mode section at the above link for further details).
The security guidelines state that failure to implement them correctly may leave the vendor implementation open to an attack or network compromise.
Learn more about wi-fi security
- An excellent, if long-winded, technical introduction to TKIP, AES, and the problematic use of misleading terminology is The TKIP Hack.
- If you are concerned about WPA2 and your devices only supports TKIP, then it’s worth considering purchasing a new router that supports WPA3. Alternatively, choose a trusted VPN.
- Understand the basics of cryptography. This prevents you becoming bamboozled by jargon and helps you make informed security decisions.
- Learn how to secure your wi-fi router. There are plenty of easy improvements you can make, such as changing factory-issued passwords, manually updating firmware, and disabling unused devices.