Shodan, brainchild of John Matherly, is a specialized search engine that lets users find sensitive information about unprotected internet-connected devices (e.g. computers, baby monitors, printers, webcams, routers, home automation systems, smart appliances, servers) using various filters. Any device that is not protected is potentially vulnerable to anyone, including hackers, using Shodan to find it.
Wikipedia describes it as “a search engine of service banners, which are metadata that the server sends back to the client.” The difference between Shodan and traditional search engines like Google is that Shodan indexes IoT (Internet of Things) devices and returns publicly accessible information about them rather than website content.
With Shodan, anyone can find devices that use default login details—a serious, and all too common, security misconfiguration. In this article, we will learn how to take advantage of Shodan to find your vulnerable devices and block them from public scrutiny.
Shodan is sometimes given a bad rap in popular (and sensationalist) media, portrayed simply as an easy way for the bad guys to find vulnerable targets to hack. The reality is Shodan is not the only tool a hacker has in their arsenal and there are many ways for cybercriminals to breach security loopholes. Shodan is a powerful and easy-to-use tool for home users and businesses to help identify vulnerable devices. After that, it is up to you to protect your devices.
But first, let us summarize the basics of Shodan, what it is, what it does, how it works, how much it costs, and whether it deserves its controversial reputation.
How scary is Shodan?
For the home user, Shodan can seem a bit like Big Brother. It has been called “the scariest search engine on the internet.” According to CNN Business, Shodan researchers have found sensitive command and control center devices for nuclear power plants. A CT Access blog describes a scary scenario where a Shodan user managed to access a traffic control system and, with just one simple command, set the system to test mode. But the means to compromise these systems was made public by shoddy security measures in the systems themselves. According to CSO Online, “If an organization is exposing sensitive data to the Internet, blocking Shodan isn’t going to fix the problem.” Instead, users should be using Shodan proactively as a security tool to find out if information about their devices is publically accessible.
Shodan has been labeled as scary mainly because of the large number of devices out there that employ little or no security. For instance, when they use default passwords like “admin” or “0000.” Finding your device on Shodan should be a wakeup call to address your security inadequacies.
What is Shodan used for?
While Shodan is a useful tool for the digital underground and cybercriminals, it has many positive uses for home users and organizations:
- It allows in-house penetration testers and white hat hackers to identify vulnerabilities in enterprise networks
- Home users can discover vulnerabilities with their own internet-connected devices and identify if anyone else is using them. For instance, has a hacker accessed your server and what is their IP address?
- It provides valuable data about IoT (Internet of Things) devices for research purposes by data scientists, law enforcement officials, and cybersecurity professionals
- Shodan can help identify critical infrastructure networks, e.g. water treatment facilities that should not be on the public internet, internet-accessible SCADA control centers, and IoT home-network devices that are insecure, from fridges to home security systems.
- Shodan keeps track of recent exploits aimed at specific device types or using particular software. You can easily discover if your business may be vulnerable to a security exploit. (You can even set up an RSS feed to notify you of recent IoT exploits.) In 2016, an exploitable bug in IIS 6.0 in Microsoft Windows Server 2003 was reported by Github. The software is no longer supported by Microsoft. It is a simple matter to create a Shodan search to list all (at the time of writing) 597,611 unprotected devices using Microsoft-IIS/6.0.
Example of a popular search run to identify routers that use the username/password as admin/1234 in their banner (Source: Shodan)
Is Shodan legal?
One of the first questions the uninitiated ask is, “Is it legal?” CT Access’s Scott Hirschfeld, answering from a technical point of view, says it is. Because Shodan is just a “massive port scanner” and simply exposes vulnerable devices (does not actually use the information it discovers), it is legal. “Port scanning is not a violation of the Computer Fraud and Abuse Act, because it does not meet the requirement for damage concerning the availability or integrity of the device.” Popular scanners like nMap and Nessus can do pretty much the same job.
How does Shodan work?
Service banners and banner grabbing
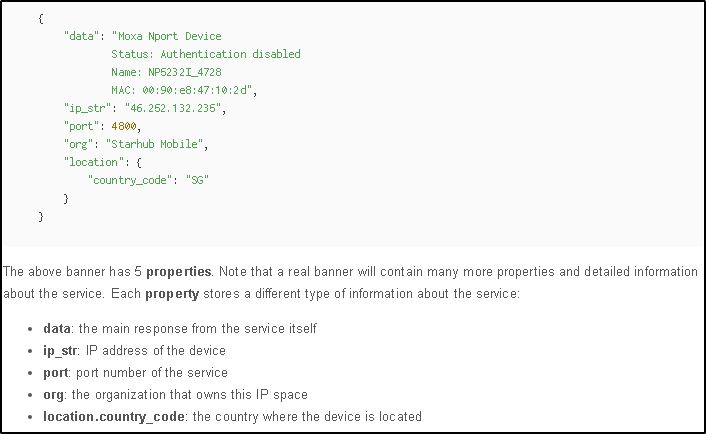
Understanding what a service banner is, helps to understand how devices can be vulnerable to Shodan. Shodan works by unleashing web crawlers (spiders) that grab service banners, which provide public information about a device’s services – e.g. HTTP, FTP, SSH, Telnet, SNMP, etc.
Information might include the device’s name and IP address, what software the service is running, what options it supports, and what services it provides. Bear in mind, banners can be faked, but what a treasure trove of information real banners provide!
Example of a simplified Shodan banner (Source: Shodan)
Loosely, a banner can be compared to a restaurant sign on the door when it opens for business announcing its opening hours, menu, etc. In this scenario, when the door is unlocked and the restaurant opens, automatically on the internet websites that feature the restaurant would update their information to Open and more than likely display the restaurant’s location and contact details. Similarly, a service banner provides information about a device that can be retrieved and displayed by Shodan.
What are Shodan filters?
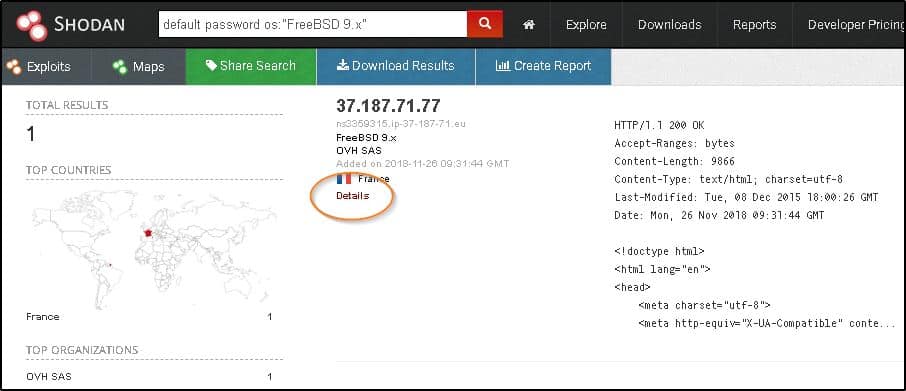
You can filter search results by country, city, organization, operating system, timeframe, host name, IP range, or product. IP range is one way to check whether your devices are vulnerable. The results page also provides a summary filter, e.g. top countries, not every country on earth. If you want to see results for a specific country, you have to use the country filter in your search string, e.g. “default password country:US”. You can deep-dive results with multiple filters.
Clicking Details provides further information about the device, e.g. the owner of the device, open ports, and the services the device is running. A black hat hacker might know of an exploit against a certain version of SSH. It is quick and easy to use Shodan to find every computer open to the web running that version. Voila, an instant list of vulnerable targets.
Example of filter for FreeBSD devices using a default password (Source: Shodan)
Public IP addresses
Home devices share one public IP address, which is (should be) protected by your ISP and assigned to your router. Unless Shodan has done a very recent internet scan and it included the IP assigned by your ISP (highly unlikely), chances are you will not show up in a search. Bear in mind Shodan only completes a crawl of the entire internet (around 500-million devices) once a month, so if you want to make an up-to-date request to confirm you are off the Shodan grid, you need to use the Shodan API for on-demand scanning (a service only available to paid subscribers.) Other devices connected to your device, e.g. your printer, identify you by your local (private) IP addresses, which will not show up in a Shodan search.
How do you perform searches?
In a similar fashion to a traditional search engine, you simply enter a search string and click on Search. Shodan’s Help Center provides a comprehensive list of filters to narrow the results of your search. Below are some simple sample queries:
- Find Cisco devices in California – Cisco city:California
- Find Apache servers in Germany – Apache country:de
- Find all devices not located in New York – city:“New York”
Note: There is no space between the colon and the search value, and if you use a string with a space, you should wrap the search value in quotes.
Who can use Shodan?
Anyone can use it and it is free for users without an account, although searches are limited to two pages of results. The most expensive subscription plan is $899 a month with unlimited results.
Tips to keep your devices off the Shodan grid – [SOLVED]
There are a number of ways to protect your devices but the best practice by far is to use a VPN to remain under the Shodan radar.
Shodan security 101
The home user should not rely on their ISP for complete protection:
- Install a VPN. It is not necessarily going to cost you big bucks; many are free.
- Never use default configurations, e.g. passwords, usernames and SSIDs
- Preferably buy a router directly from the manufacturer rather than from your ISP as manufacturers are usually more up-to-date with patches; it is, after all, their primary business
- Always configure your software correctly, and keep it patched and up-to-date
- Is information about your fridge accessible on the internet? Ask yourself whether your devices really need to be connected. Sometimes default configurations by vendors are not secure.
- Always use HTTPS on your IoT devices and multi-factor authentication where available
In addition to the above, a multi-faceted approach to security for an organization’s devices is the best way to protect it:
- Always use a VPN, particularly if you manage devices remotely, e.g. for contractors or external suppliers, or have a BYOD policy
- Review the content of service banners, and be careful what you reveal in error and welcome messages; the smallest piece of information is pay dirt for the dedicated hacker. Apache Tomcat by default publishes tons of information about the services a device is running. IBM has a quick guide to clean up Apache Tomcat, and Yeah Hub provides step-by-step instructions to harden IIS servers.
- Implement a strict security policy at your organization. Insider threats put your business at much at risk as the existence of Shodan and hacking software from the Dark Web.
- Remove legacy and unused services
- Consider open source router firmware, which is customizable and often more reliable than commercial options, created and managed as it is by volunteer IT geeks who do it for the love of it and not just for money. Two options are Tomato and DD-WRT.
- Restrict your own access to manage your router to a single IP address that is not part of the pool of addresses your network has been assigned. Practice safe management, e.g. do not allow the router to store your login details.
- Never enable port forwarding for IoT devices or servers on your LAN. If you need access to your devices through the internet, install a home VPN server and access your LAN through the VPN instead.
- Be as stealthy as a hacker is. Instead of letting intruders know you have detected them by allowing your firewall to send out an ICMP Destination Unreachable message to addresses you wish to block, let the scanner time out. Knowing whether a host exists is valuable information to hackers using Shodan.
- Employ an account lockout policy to lessen the risk of brute force attacks on your network
Find out if your devices are vulnerable
To get started, you will need your public IP address. To find it, simply type, “what is my IP address” in Google.
To find your computer in Shodan, type “net:[your public IP address]” (without the quotes) in the Shodan search box. If your ISP is doing its job, you will get a 404 Not Found status message. If you are vulnerable, Shodan will return details of your device. Hackers may not know your public IP address but if you are using a default username and password, they could find you by searching for devices that use default login details. The best way to remove yourself from the Shodan grid is by installing a VPN, e.g. OpenVPN.
Alternatives to Shodan to confirm if your devices are vulnerable:
- If Shodan does not come up with your public IP address details in a basic search, you can use an online port scanning tool, like Hide My Name to confirm your ports are protected. Enter your public IP address. All ports should be in a closed or filtered (protected by a firewall or filter) state. If you use Hide My Name to scan your local IP address, you should receive a message that the host is down or something along the lines of, “Error: Server is not willing to scan this host.”
- Censys is similar to, but newer and more user-friendly than, Shodan. Type in your IP address. If your device is protected, you should get a message along the lines of, “We haven’t found any publicly accessible services on this host or the host is on our blacklist.”
- IoT Scanner can do a port scan to discover if any of your devices are publicly reachable on the internet.
Block Shodan scanners
Strictly speaking, you do not remove your device from Shodan, you block the engine from finding it. IP Fire says Shodan uses around 16 different scanners to keep its index up to date. To block these scanners you can set up the known host definitions for Shodan scanners in your computer’s firewall. Unfortunately, these IP addresses may change at any time so you will have to keep them updated as part of your security routine. Unfortunately, VPNs are designed to evade firewalls so a firewall may alert you to a Shodan query, but may not protect you from a hacking attack. Blocking known Shodan scanners is a quick fix in situations where you can’t use a VPN and your devices need to be public-facing.
Set up a VPN
Comparitech has rounded up the best (and the worst) VPNs, including free ones:
- Best VPN Services for 2018
- 20+ free VPNs rated side by side
- 6 best free VPNs you can trust
- The best VPNs for Linux in 2018 (and the worst)
Should you panic about Shodan?
Most people do not worry too much that applications like Facebook and browsers like Google know more about them than their own mothers do, even though they should. You do not want to show up in a Shodan search but it is not, as we have seen, too difficult to protect yourself.
Devices using default configurations are at the most risk from cyber criminals using Shodan or any other software designed to sniff out unsecure device configurations. It is not just Shodan that is scary. Google dorks – SQL search queries that search a website’s index for information – were developed before Shodan arrived on the scene in 2009. These queries can also be used to find vulnerable information on your website, e.g. a document containing sensitive data.
To get started with Shodan, the Shodan Knowledge Base is comprehensive, and a useful place to learn how to use the engine and effectively protect yourself, as well as have fun learning some IoT facts and trivia.