Overview of OpenText Enterprise Security Manager
OpenText Enterprise Security Manager (ArcSight) is a comprehensive SIEM platform designed to help organizations detect, analyze, and respond to security threats in real time. Originally developed by ArcSight and later acquired by OpenText, the platform provides powerful tools for monitoring network activities, user behavior, and security events.
By aggregating and correlating data from across the enterprise, OpenText Enterprise Security Manager (ESM) helps organizations quickly identify potential security breaches, enabling faster response times and improved security posture. The platform supports a wide range of log sources, including network devices, endpoints, and cloud services, providing visibility across diverse IT environments.
OpenText Enterprise Security Manager offers deep insights into security events through advanced correlation rules and analytics. These capabilities enable security teams to focus on high-priority incidents while minimizing false positives. The platform leverages machine learning and behavioral analytics to identify anomalous activities and emerging threats, providing more accurate and timely alerts.
The platform’s flexibility allows organizations to customize and fine-tune correlation rules, reporting, and dashboards according to their specific needs. OpenText Enterprise Security Manager also integrates seamlessly with other security tools, such as threat intelligence platforms and vulnerability management systems, to enhance overall security operations.
Its key features include:
- Provides advanced analytics and correlation to identify security threats and vulnerabilities in real-time.
- Aggregates and centralizes logs from various sources, such as network devices, endpoints, and applications.
- Uses pre-configured and customizable correlation rules to detect complex attack patterns and link seemingly unrelated security events.
Leverages machine learning to detect anomalous behaviors by analyzing user and network activities. - Processes high volumes of security data with minimal performance impact, ensuring effective monitoring across complex infrastructures.
- Provides pre-built and customizable reports to help organizations meet industry regulations such as GDPR, HIPAA, PCI-DSS, and SOX, streamlining compliance efforts.
- Facilitates efficient incident response through automation of security workflows, helping teams prioritize and resolve issues faster.
- Integration with other security tools, including threat intelligence platforms, vulnerability management systems, and SIEM solutions.
Overview of Splunk Enterprise Security (ES)
Splunk ES is a popular SIEM tool that enables security teams to gain end-to-end visibility into malicious activities and business risks across your hybrid network environment. Splunk ES is built on the Splunk operational intelligence platform and supports the activities of a Security Operations Center (SOC) in a variety of ways such as threat monitoring and detection, search and correlation, incident response, and reporting activities on data from security devices and applications. As issues are identified, security analysts can leverage the Splunk ES modern SIEM capabilities to investigate and resolve the security threats across the network.
Splunk ES key features include:
- Splunk ES provides ready-to-use intelligence from Splunk’s user and entity behavior analytics (UEBA) and threat research team that you can leverage to enhance detection and response efforts.
- Dashboards for visual display and security metrics support your continuous security monitoring strategy.
- Investigate, correlate, aggregate, and analyze activities context across multi-cloud and on-premises all from one unified view.
- Machine data from the cloud and on-premises sources helps you gain full visibility for faster detection of malicious threats in your environment.
- Splunk ES cloud SIEM delivers faster time to value, allowing security teams to focus on other pressing security tasks.
Splunk was named a leader in the 2021 Gartner Magic Quadrant for Security Information and Event Management (SIEM). Many organizations around the world use Splunk ES as their SIEM and SOC automation tool for security event monitoring, threat detection, and response, and other security analytics and operations use cases. The application can be deployed on-premises, or in a cloud service (SaaS—public or private cloud) together with Splunk Cloud or any combination of these.
A free 60-day trial is available for Splunk Enterprise and a free 14-day trial is available for Splunk Cloud Platform.
OpenText ESM vs Splunk ES: How They Compare
Systems Requirements and Deployment
OpenText ESM installation process can be anything from medium difficulty to very complex depending on the use case. The application is built to run on 64-bit Linux OS such as Red Hat Enterprise Linux (RHEL), CentOS, and SUSE Linux Enterprise Server (SLES) with a minimum of 8 cores processors and 48GB RAM. ESM is sensitive to the operating system and version. OpenText supports both centralized and distributed deployment models and can be deployed on-premises as an appliance or as software, or in the cloud (SaaS or PaaS, or IaaS).
For optimum performance, higher system resources are recommended and the OS should be installed using at least the Web Server option with added compatibility libraries and development tools. Once it’s up and running, you can start adding devices for monitoring. Although the setup process is a bit tedious depending on the use case and your expertise. However, OpenText provides enough documentation and setup instructions to guide you through the installation and configuration process.
Splunk ES supports on-premise, cloud, and hybrid deployment models. On-premises deployment requires 64-bit Windows 10, Windows Server, Linux, or macOS with a minimum of 16 cores processors and 32GB RAM for the search head and indexer. In contrast to OpenText OS requirements, Splunk ES gives you more flexibility rather than being restricted to just one type of OS. The installation process is also pretty straightforward and less cumbersome. You can deploy Splunk ES in a single instance deployment or a distributed search deployment.
Splunk ES is also delivered as a cloud service in the Splunk Cloud Platform for Splunk Cloud customers. The Splunk Cloud Platform deployment architecture varies based on data and search load. Splunk Cloud Platform customers work with Splunk Support to set up, manage, and maintain their cloud infrastructure which makes the entire process less cumbersome.
Dashboards and Visualizations
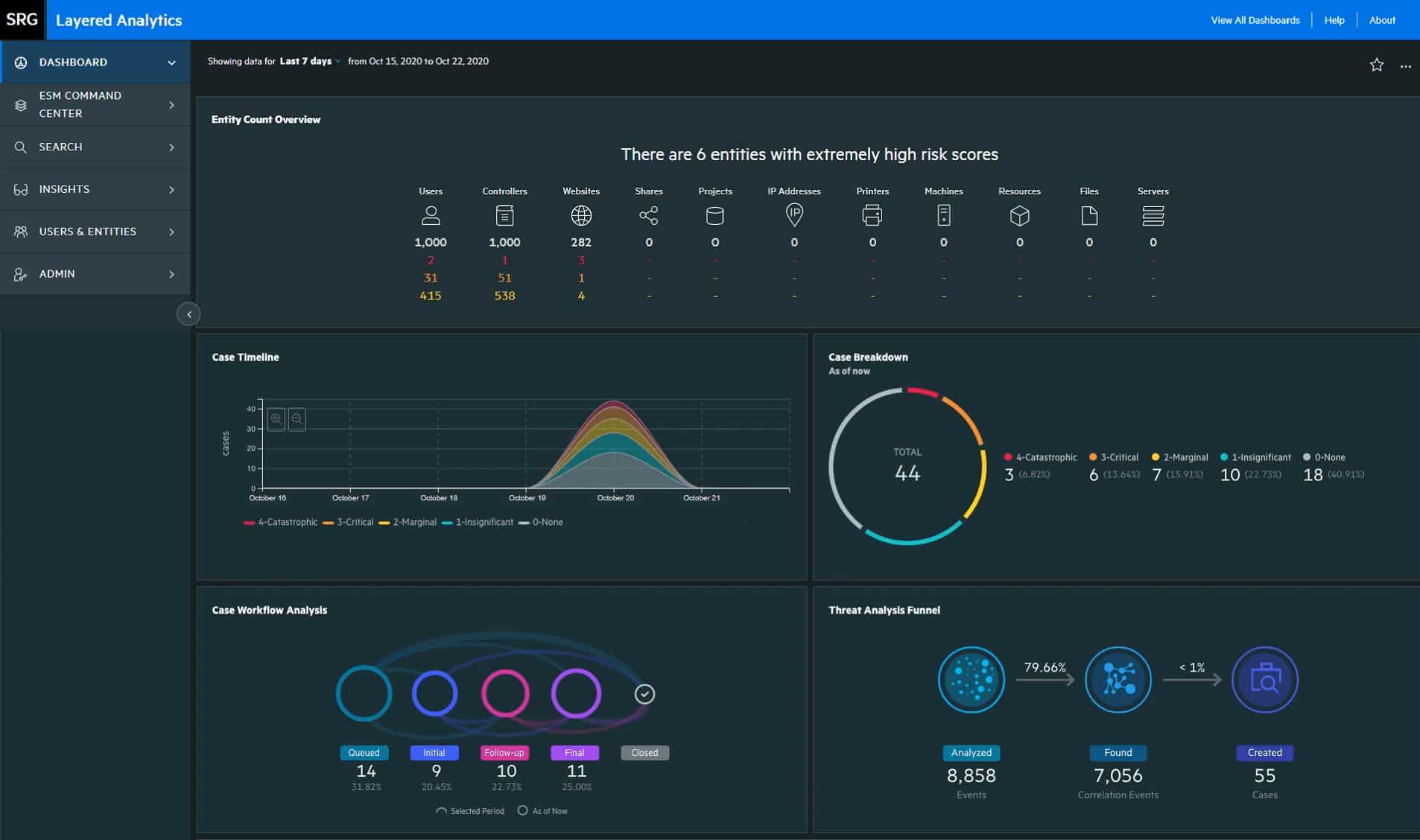
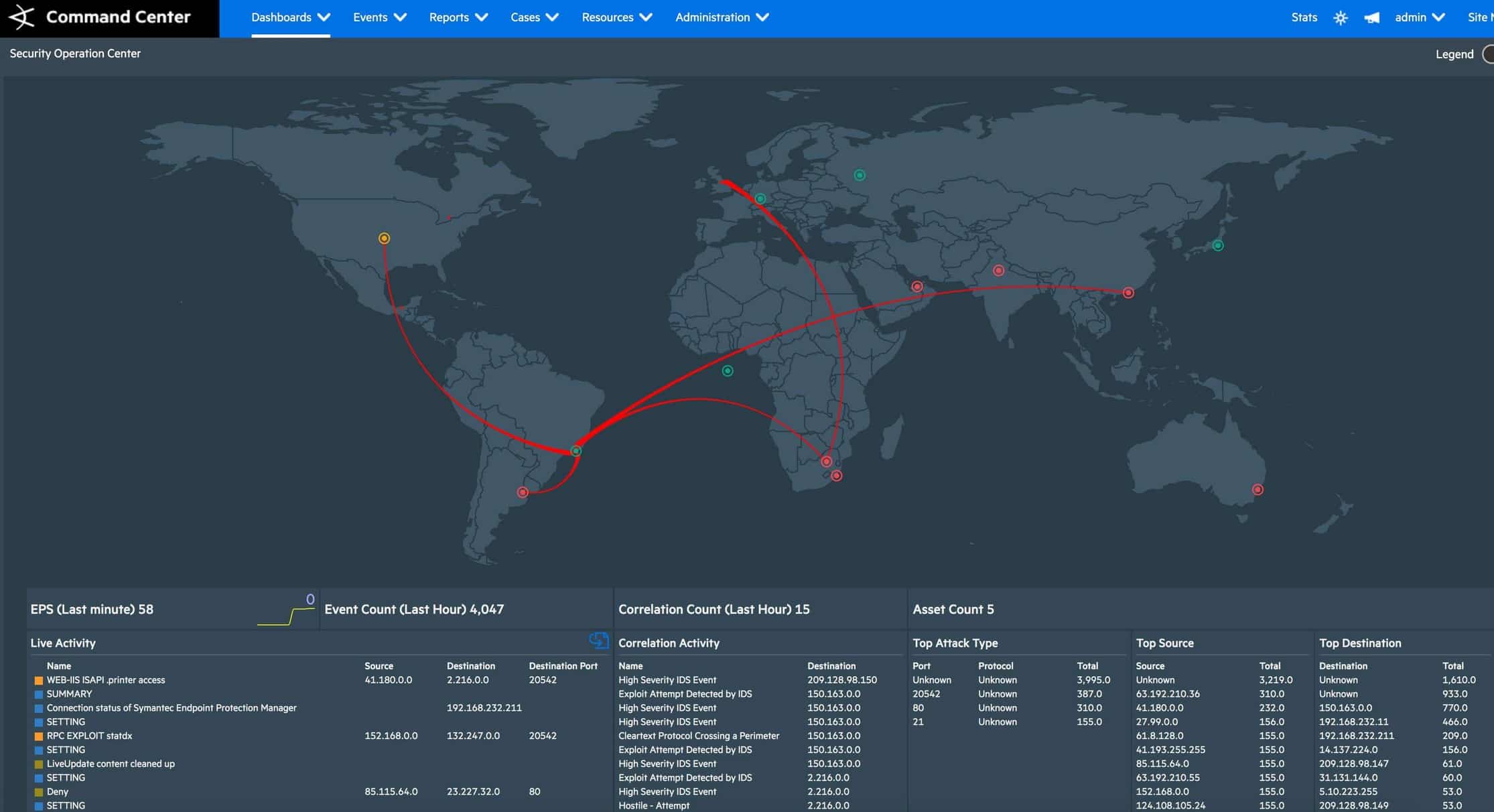
The OpenText ESM comes with a dashboard that enables you to visualize and analyze potential threats. The dashboard incorporates intelligence from multiple sources within your environment including real-time event monitoring and correlation with data from OpenText ESM. ESM provides out-of-the-box dashboards available only to the dashboard administrator. OpenText allows the dashboard administrator to customize dashboards with associated widgets and a vast library of visualization tools. On the flip side, the dashboard and user interface are not particularly fun to look at when compared to more modern-looking interfaces. But if you look beyond that, you’ll see it’s well organized.
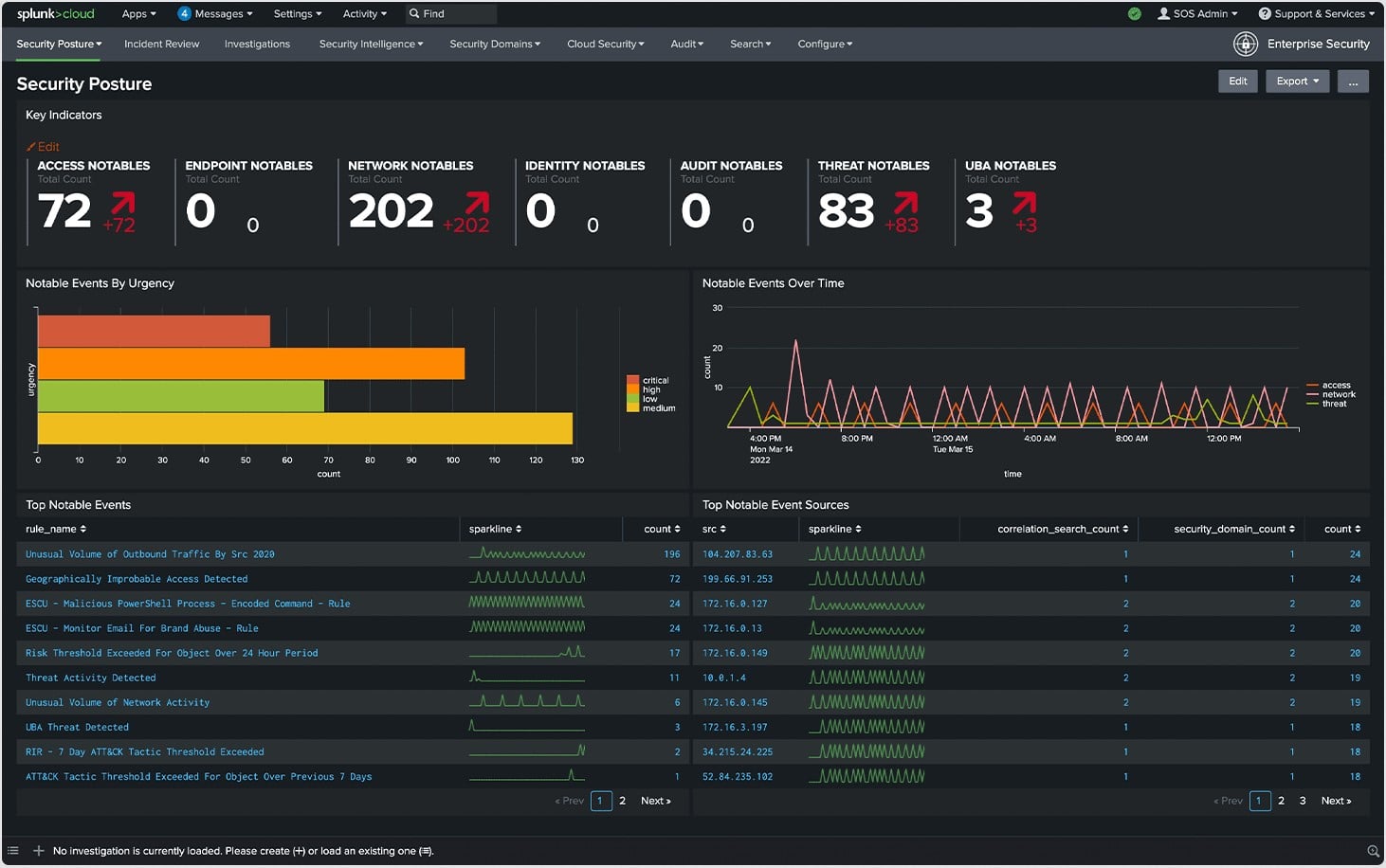
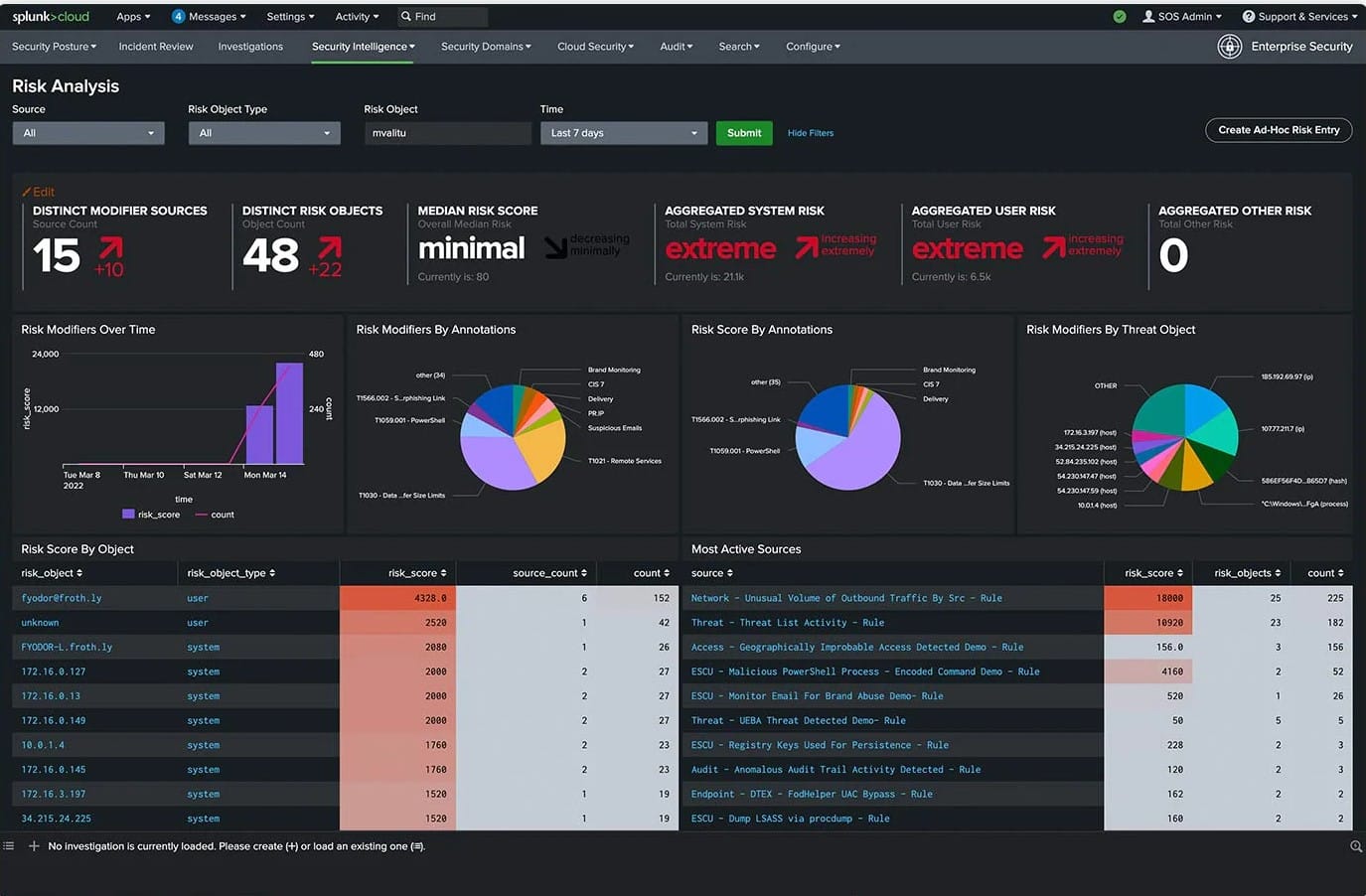
Splunk ES also comes with predefined dashboards and Custom Glass Table views that enable security teams to visualize the network security posture including insights on the status of various security domains, security and performance metrics, trending indicators, and static and dynamic thresholds, among others. Splunk ES is also easily customizable, which means that you can make changes to dashboards and the searches behind dashboard panels to make them more relevant to your organization, environment, or security use cases. Overall, Splunk ES’s modern dashboard design makes it stand out aesthetically among its contemporaries.
Alerts and Notifications
OpenText ESM security alerts are intended to warn users of threats and elicit a response and accelerate issue resolution. It correlates events and alerts to identify the high-priority threats within environments. The default means of OpenText ESM alerts is via email notifications, which can be very useful especially if you have a small team. The only challenge is that the email format is hard to read and forces you to search for the information you need to work the event. Nevertheless, OpenText ESM provides custom notification templates that can be configured to deliver alerts tailored to your specific needs and context. This approach helps organizations keep the Mean Time To Resolution (MTTR) as low as possible.
Splunk ES provides a library of alerts that proactively notifies the security teams about security events, malicious behaviors, resource availability, utilization information, and other potential problems when data passes certain thresholds. The service can be configured to deliver alerts in real-time via email or HTTPS POST requests. Alerts can be configured to varying levels of granularity according to various conditions such as data thresholds, behavioral pattern recognition, and trend-based conditions. Alerts can also be configured to initiate an application or a custom action. Splunk’s unique high fidelity, risk-based alerting functionality triggers alerts when the risk exceeds thresholds thereby eliminating alert fatigue.
Reporting and APIs
OpenText ESM allows you to generate and export out-of-the-box reports on the dashboard. The reports can also be customized to meet specific regulatory requirements. Its API feature allows for extensive integration in SOC environments. With this level of flexibility, there’s no limit to the number of things that ESM can monitor.
On the other hand, Splunk ES provides a variety of built-in reports designed to meet specific regulatory requirements such as PCI DSS compliance and others. Splunk ES also supports integration with other third-party tools with its add-on features. The ServiceNow Security Operations add-on feature for example allows Splunk to create security-related incidents and events in ServiceNow.
Licensing and Price Plans
When it comes to pricing and licensing, OpenText provides a flexible model to cater to the needs of everyone. This includes ingestion-based pricing, events per second (EPS ) pricing, Gigabyte per day. However, OpenText does not offer a free trial or free version and pricing details can only be obtained on request from OpenText.
Splunk offers two pricing plans for its customers: workload pricing and ingest pricing.
- Workload Pricing Workload licensing model offers a license allocation based on computing capacity consumed by your infrastructure or search and analytics workloads.
- Ingest Pricing Ingest licensing model is based on data volume consumption calculated according to GB/day data ingestion (how much data you send into your Splunk installation in a day).
These pricing options apply to on-premises term licenses. The license period can be an annual or multi-year term license. Your license comes with support which includes software updates and customer support for on-premises term licenses.
Concluding Remarks
OpenText ESM is a powerful modern SIEM tool designed for large-scale enterprises. MSPs and organizations committed to minimizing security incidents and keeping mean time to resolution (MTTR) as low as possible will find it very appealing. However, depending on the use case, the application can be a bit pricey and difficult to set up and configure. But once you get past that, you will appreciate the power that it brings to your security operations center (SOC) activities.
Similarly, Splunk ES is positioned to meet the security and compliance needs of highly regulated organizations. Splunk ES customers can effectively detect and respond to security incidents, and streamline compliance reporting in a single, unified platform with a minimal signal-to-noise ratio (false positives) without needing to switch tools. This saves your team significant time. However, just like OpenText ESM, the application is more suited for large enterprises. This means that SMBs with a low-security budget would have to look elsewhere.
Overall, OpenText ESM and Splunk ES are two leaders in next-generation SIEM applications.
Organizations can leverage modern technologies such as Security Orchestration Automation and Response (SOAR), User and Entity Behavior Analytics (UEBA), cloud-based analytics, and machine learning integrated into these applications to automate SOC activities and other security incident detection, analysis, and response procedures.