There is no doubt that AWS has strong security that protects its customer accounts. However, the software you install on your AWS server space might create vulnerabilities by opening connections to the outside world. You need to perform security checks on your cloud-based assets and penetration testing is one of the strategies that you could adopt.
Here is our list of the best AWS penetration testing tools:
- Invicti EDITOR’S CHOICE A vulnerability testing system that can be used for on-demand testing sweeps or a full vulnerability scanner. This system is also available for continuous testing. Available as a SaaS package or as a software package for installation on Windows.
- Acunetix This is a vulnerability scanner that can perform both external and internal tests. It is offered on the AWS marketplace and is also available as a SaaS platform or for installation on Windows, macOS, and Linux.
- Amazon Inspector This is a vulnerability manager that is offered by Amazon and so 100 percent allowed for use on the platform.
- Intruder A cloud-based vulnerability scanner that offers scanning for AWS, Azure, and GCP. Get internal and external scans for your AWS accounts plus Web application and network scanning.
- Awspx A free attack path grapher that explores your AWS identity and access management system to plot all relationships expressed within. Runs on macOS, and Linux.
- Rhino Security Labs Buckethead This free utility is offered as a program that you can cut and paste from its page on GitHub. Runs on Python.
- Prowler This security auditing tool focuses on identity and access management features in AWS and is particularly well-geared for businesses that need to comply with data privacy standards. It will run on Linux, macOS, or Windows.
You can read more about each of these tools in the following sections.
Penetration testing
Penetration testing is a largely manual process. The basic idea behind this strategy is that you get a hacker to attack your system and tell you what’s wrong with your security system. Of course, no system administrator would want to draw the attention of a bunch of hackers, but the people who operate penetration testing teams are certified and traceable. We are talking about “white hat hackers” – technicians who are excited by the challenges of trying to break into a system but aren’t interested in engaging in criminal activities.
Many of the methods that penetration testers use are laborious and repetitive. For example, trying to crack passwords requires a lot of login attempts. Hackers want to move quickly so a tool that can cycle through thousands of character combinations has a higher rate of success than an individual manually typing in all of those combinations.
There are several known attack strategies that hackers use and so penetration testers are always going to try those methods. As many of those attempts require a degree of automation, it makes sense to string that series of different strategies together in a batch file. Step up the automation a little further, and you arrive at a full package of system security tests. One launch command gets many tests carried out by these systems that are called vulnerability managers.
Does AWS allow penetration testing?
AWS performs its regular security checks and appreciates the efforts of its customers to finance their contributions to this effort. There are channels that customers can use to convey discovered vulnerabilities that require system adjustments to resolve.
You are allowed to perform penetration testing on the following services:
- Amazon EC2 instances, NAT Gateways, and Elastic Load Balancers
- Amazon RDS
- Amazon CloudFront
- Amazon Aurora
- Amazon API Gateways
- AWS Lambda and Lambda Edge functions
- Amazon Lightsail resources
- Amazon Elastic Beanstalk environments
Some problems might relate to platform security, which is beyond the control of the customer. However, you shouldn’t direct your penetration testing project towards the platform – that is not allowed. Instead, if, during testing your applications installed on the AWS platform you discover lower-level problems, you should get in touch with the AWS Security Department immediately and they will take it from there.
There are security testing strategies that AWS doesn’t allow. In some instances, you can negotiate with the team to get permission to perform a test that is listed in the regulations as not permitted. This leeway is probably only given to very large organizations from which Amazon makes a lot of money or businesses in the partner program that are developing and testing a new security tool. However, it doesn’t hurt to ask and there are contact forms for this purpose linked to in the AWS penetration testing advisory page (see below).
When your level of automation arrives at the vulnerability testing category, you could be dealing with a service that generates a lot of transactions, putting a load on the AWS system.
Penetration testers, thinking like real hackers, could try tricks that many jurisdictions classify as illegal. For example, if a hacker gets into a system by tricking administrator credentials out of technicians, shouldn’t the white hat hacker try the same tactic to properly model the activities of hackers? Getting AWS technician credentials would be very useful. However, such an approach could get you into trouble.
Other strategies that are banned are:
- DNS zone walking via Amazon Route 53 Hosted Zones
- Denial of Service (DoS) and Distributed Denial of Service (DDoS)
- Port flooding
- Protocol flooding
- Request flooding
To get the full policy of AWS toward penetrating testing, see the company’s Penetration Testing page.
Above all, to avoid legal problems as well as the risk of having your AWS account suspended, never perform penetration testing exercises on an account you do not own unless you have the account holder’s permission.
The best AWS penetration testing tools
You might be put off running a vulnerability scanner or a penetration testing exercise on your AWS-based assets. However, don’t worry. The main thing is that you shouldn’t try to break into someone else’s account or trick AWS technicians. In addition, don’t do anything that can create excessive traffic. If you avoid those actions, you should be fine.
Our methodology for selecting an AWS penetration testing tool:
We reviewed the market for AWS penetration testing systems and analyzed tools based on the following criteria:
- An external penetration platform that fully emulates the remote attack strategies of hackers
- Test automation for repetitive tasks
- Checks for the OWASP Top 10
- Systems that can run on-site
- Options to use SaaS platforms
- A free tool or a paid service that has a free trial for a cost-free assessment opportunity
- Value for money from a reliable tool or a free tool that is worth using
You will notice that one of the requirements listed above is for a tool that can be used on-site and another is for a SaaS platform. This doesn’t mean that we expect to find one tool that has both deployment options; we are saying that the final list of recommended tools should include some for on-premises hosting and some that are offered on cloud platforms.
1. Invicti
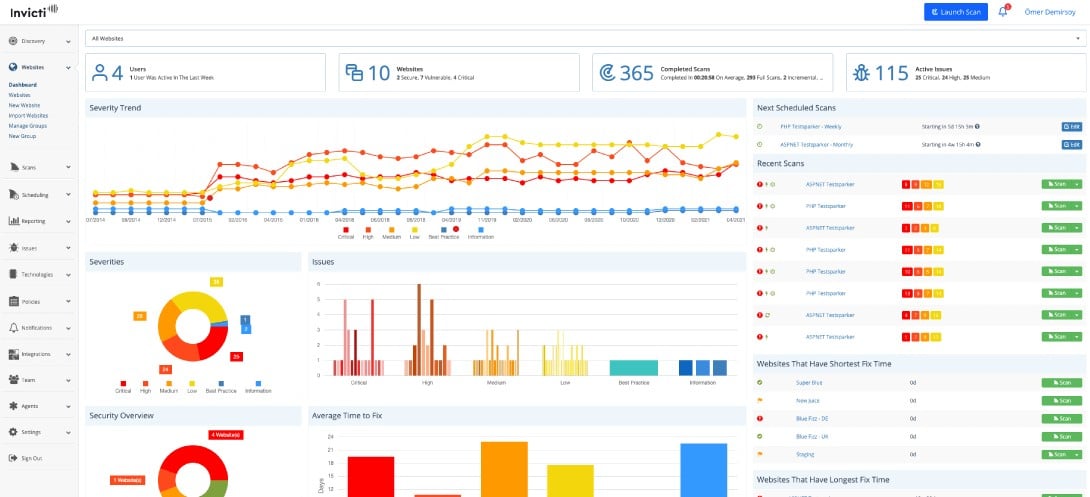
Invicti is a Web application vulnerability scanner. It can be hosted on AWS and some versions run on Windows. Wherever you host the package, it can be run against AWS packages.
The Invicti system is available in three versions and the top edition is a fully automated vulnerability scanner. All versions can be limited in the settings to just running specific tests against specific assets. For example, the package includes a password cracker, which you might want to run by itself. A full vulnerability scan of a system can take from 8 to 10 hours.
Key Features:
- Cloud Compatibility: Easily hosted on AWS for flexible deployment options.
- Customizable Testing: Choose between full system scans or specific individual tests for targeted analysis.
- Continuous Security: Offers a continuous testing option to maintain up-to-date security assessments.
- Integration Capable: Seamlessly integrates with various project management tools for efficient workflow.
- Attack Simulation: Capable of launching sophisticated attacks to test system resilience.
Why do we recommend it?
Invicti excels in providing a thorough and flexible web application vulnerability scanning solution that adapts to various deployment environments, including cloud services and Windows servers. Its blend of automation, integration capabilities, and support for team collaboration makes it a powerful tool for maintaining web application security.
The facilities in the Invicti menu include those for research and those for the attack. It is also possible to integrate other hacker tools into the interface and expand its repertoire. The system uses AI methods to identify possible attack paths.
Who is it recommended for?
This platform is best suited for organizations that require a versatile web application vulnerability scanner that supports both cloud and on-premise environments. Its scalability from individual testing to full scans makes it ideal for businesses of all sizes, especially those with development teams focused on continuous security improvement.
Pros:
- Versatile Scanning Options: Allows for both comprehensive full scans and targeted individual probes, catering to specific security needs.
- Expert Collaboration: Enables routing of discovered vulnerabilities to human pen testers for further investigation.
- Team-Friendly: Designed to support team collaboration and management of security tasks.
- Automation of Tasks: Automates repetitive security assessment tasks, enhancing efficiency.
- Documentation: Automatically generates detailed documentation of the system under examination, aiding in security compliance and analysis.
Cons:
- Time-Consuming Scans: Comprehensive scans can be lengthy, taking between 8 to 10 hours to complete.
Invicti is offered in three versions: Standard, Team, and Enterprise. You have to go up to the Teams or Enterprise versions to host on AWS. The Standard and Enterprise versions can be installed on Windows Server. You can get a look at the Invicti package by accessing a demo system.
EDITOR'S CHOICE
Invicti is our top pick for an AWS penetration testing tool because of its comprehensive and automated approach to vulnerability scanning, making it ideal for testing cloud environments like AWS. One of most useful features of Invicti is its ability to automatically detect common security flaws such as SQL injection, cross-site scripting (XSS), and misconfigured access controls that often plague cloud applications. This makes it particularly effective for organizations with large, dynamic AWS infrastructures.Invicti integrates well with AWS, allowing security teams to assess the security of AWS-hosted applications without requiring deep manual configuration. It supports a wide range of AWS services, including EC2, S3, and Lambda, helping identify vulnerabilities across multiple layers of an AWS environment. Another reason that Invicti is a good choice for AWS penetration testing is its ability to scale with the growth of an AWS infrastructure. It can handle large, complex cloud environments and provide actionable insights for risk mitigation, making it suitable for both small businesses and large enterprises. Invicti’s automated scanning saves valuable time by identifying vulnerabilities quickly and providing detailed reports with remediation guidance. This allows teams to prioritize and fix issues efficiently. Invicti’s support for both internal and external penetration testing ensures that both the external-facing and internal components of an AWS environment are tested for security weaknesses.
OS: Windows Server or cloud
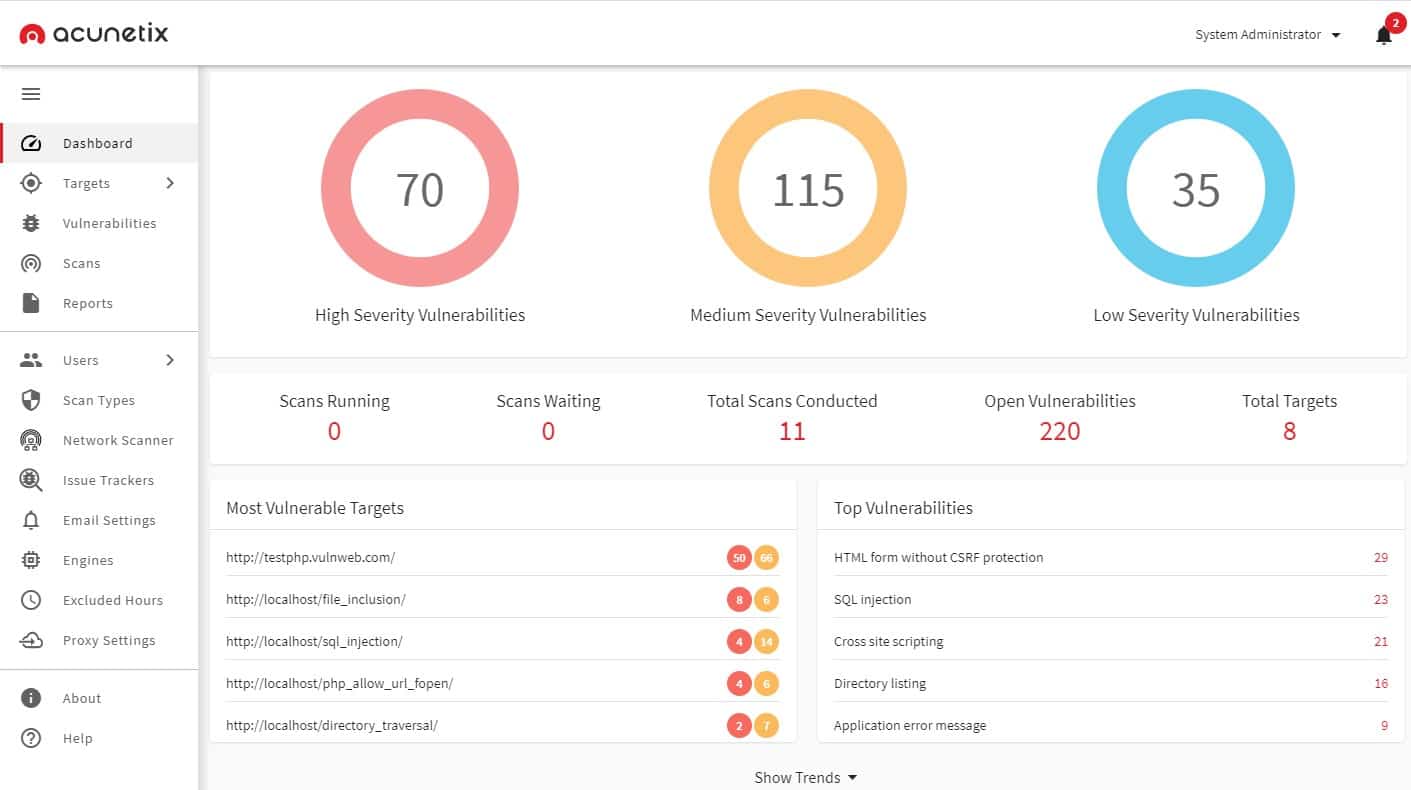
2. Acunetix
Acunetix is a vulnerability scanner and also a package of penetration testing tools. Use it as a fully automated scanner or limit it to running each test individually. The Acunetix system can be expanded by integrating the free OpenVAS system. This gives you external scans and also internal scans to see what a hacker could do once he gets into your network.
The package can test any system anywhere, including cloud platforms, such as AWS.
Key Features:
- Dual Scanning: Conducts both external and internal scans to uncover vulnerabilities from all angles.
- AWS WAF Testing: Specializes in testing AWS Web Application Firewalls for robust security.
- OpenVAS Integration: Enhances capabilities with OpenVAS for comprehensive security assessments.
- Project Management Sync: Integrates smoothly with project management systems for streamlined team collaboration.
Why do we recommend it?
Acunetix is highly regarded for its comprehensive approach to vulnerability scanning, covering both internal and external aspects, and its integration with key tools like OpenVAS and project management systems. This makes it a versatile choice for organizations prioritizing thorough security analysis and team collaboration in their operations.
You can set off your pen testing project by running a vulnerability scan and then routing issues through a team management tool to human pen testers for investigation.
Who is it recommended for?
This tool is particularly suited for businesses adopting DevOps practices, requiring continuous security testing, and those who value the integration of their security tools with project management systems. Its ability to conduct parallel scans and test for OWASP Top 10 vulnerabilities also makes it an excellent option for teams focused on maintaining high security standards in their web applications.
Pros:
- DevOps Ready: Ideal for continuous testing within DevOps environments, ensuring constant security.
- Flexible Tooling: Offers both automated and manual tools, catering to different testing preferences.
- OWASP Top 10 Coverage: Checks against the critical OWASP Top 10 vulnerabilities, ensuring top-tier security standards.
- Efficient Scanning: Supports parallel scanning, maximizing efficiency and reducing time spent on security assessments.
Cons:
- Hosting Restrictions: Unlike some competitors, it cannot be hosted directly on AWS, potentially limiting deployment options.
Acunetix is available as a SaaS platform, called Acunetix Online, or as a package for installation on Windows, macOS, and Linux. Examine the demo system to assess Acunetix.
3. Amazon Inspector
The Amazon Inspector vulnerability scanner is a product of the AWS team and so there is no doubt that you can use it without breaking the rules. The scanner runs continuously on your EC2 and ECR accounts.
Key Features:
- AWS Compliant: Designed specifically for AWS environments, ensuring full compliance with their policies.
- Continuous Operation: Operates around the clock, providing ongoing security assessments.
- Weakness Detection: Identifies security vulnerabilities, including outdated software and network exposures.
Why do we recommend it?
Amazon Inspector is recommended for its seamless integration with AWS services, offering continuous and automated vulnerability scanning that helps users identify and prioritize security weaknesses within their AWS environment. Its focus on compliance and system enhancement makes it a crucial tool for AWS users.
The scanner looks for out-of-date software and also network exposure. The system reports can be accessed directly from within your AWS dashboard and it can also be set up to send you an alert if a problem is encountered. Results are ordered by severity so you can tackle the biggest security weaknesses first.
Who is it recommended for?
This tool is ideal for AWS users looking to enhance their security posture through continuous vulnerability scanning. It’s especially beneficial for those prioritizing compliance and seeking to harden their systems against potential threats without the need for penetration testing capabilities.
Pros:
- Automated Scans: Conducts security testing automatically, saving time and resources.
- Network Monitoring: Examines network exposure, offering insights into potential vulnerabilities.
- Security Enhancement: Aims to fortify systems, making it a valuable tool for system hardening efforts.
Cons:
- Limited Scope: Does not offer penetration testing capabilities, focusing solely on vulnerability scanning.
Although this package doesn’t qualify for the title of penetration testing tool, it is a useful service to have in place for defense. You can’t launch attacks with this package but you can make sure that you have done all you can to protect your AWS account by keeping it up to date.
4. Intruder
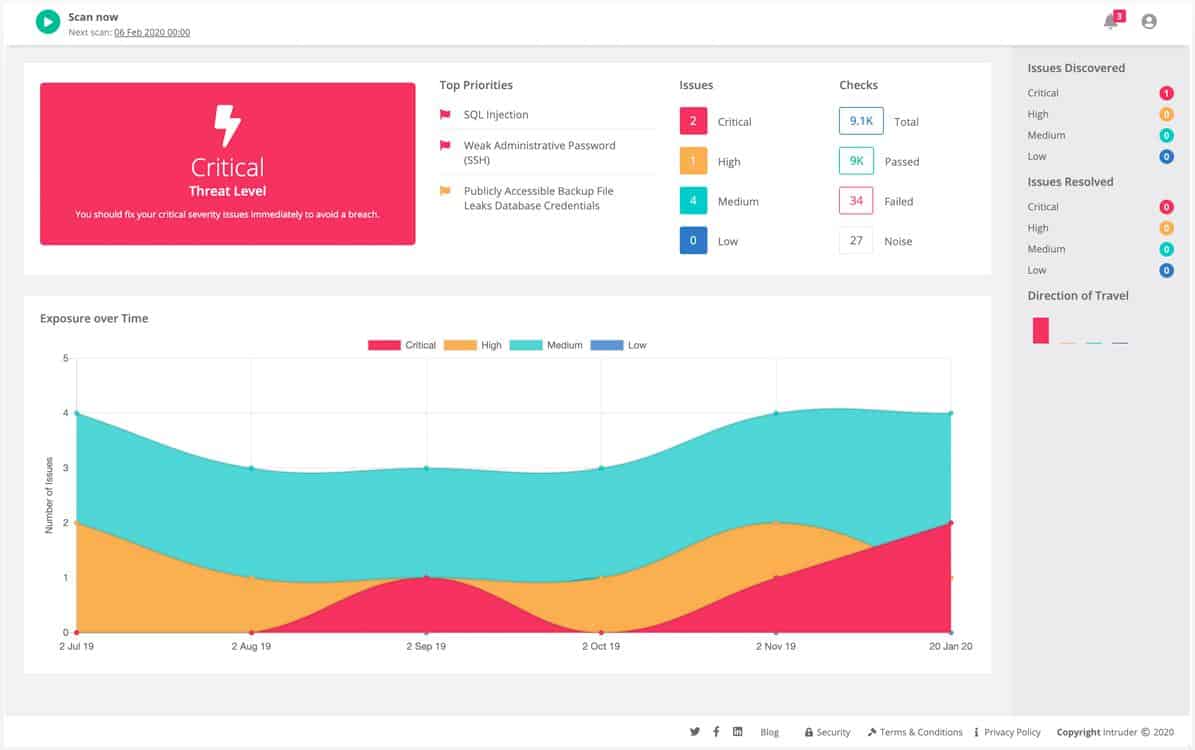
Intruder is a cloud-based vulnerability management system that includes a powerful vulnerability scanner. The system offers continuous scanning, effectively functioning as a security monitor. One of the notable features is the seamless AWS integration, which eliminates the need to install CloudBot in your AWS account. Instead, Intruder’s AWS integration allows for hourly checks to detect new IP addresses or hostnames, automatically adding them to Intruder for security monitoring and scanning. This simplifies the tracking of cloud assets. Similar integration options are available for Azure and GCP.
Key Features:
- Cloud Integration: Seamlessly integrates with AWS, Azure, and GCP for effective cloud asset monitoring.
- Comprehensive Scanning: Offers external, network, and web application scanning capabilities.
- Continuous Monitoring: Allows for ongoing vulnerability testing to ensure security.
- Expert Support: Access to a human pen-testing team for advanced vulnerability assessment.
- Adaptable Plans: Service plans range from basic to premium, catering to various testing frequencies and needs.
Why do we recommend it?
Intruder stands out for its cloud-first approach, offering deep integration with major cloud providers and continuous monitoring that adapts to the dynamic nature of cloud environments. This makes it an invaluable tool for maintaining a robust security posture in cloud-based infrastructures.
The specific services included in this SaaS package vary based on the chosen plan. All plans offer unlimited ad-hoc scans. The Essential plan provides one scheduled scan per month, while the Pro and Premium plans have no limitations on the number or frequency of scans, enabling continuous testing.
The Intruder system comprises more than just the scanning tools. In addition to its comprehensive vulnerability management features, Intruder delivers a range of additional benefits that go beyond what these tools alone provide. Access to all features is available in the top-tier plan, offering a complete and enhanced vulnerability management solution.
Who is it recommended for?
This system is ideal for organizations leveraging cloud services from AWS, Azure, or GCP, looking for an all-in-one vulnerability management solution that includes continuous scanning and expert penetration testing support.
Pros:
- Expertise on Demand: Provides a managed service complemented by a professional penetration testing team for thorough security checks.
- Remediation Guidance: Offers detailed guidance on fixing vulnerabilities, enhancing security posture.
- Secure Connections: Specializes in scanning and securing connections to cloud services.
- Tool Integration: Easily integrates with project management and CI/CD pipeline tools for streamlined operations.
Cons:
- Plan Limitations: Full access to all features and capabilities requires subscription to the top-tier plan.
Intruder is easy to set up and manage through its cloud-resident console, which can be reached from anywhere with any standard Web browser. Try out the system with a 14-day free trial.
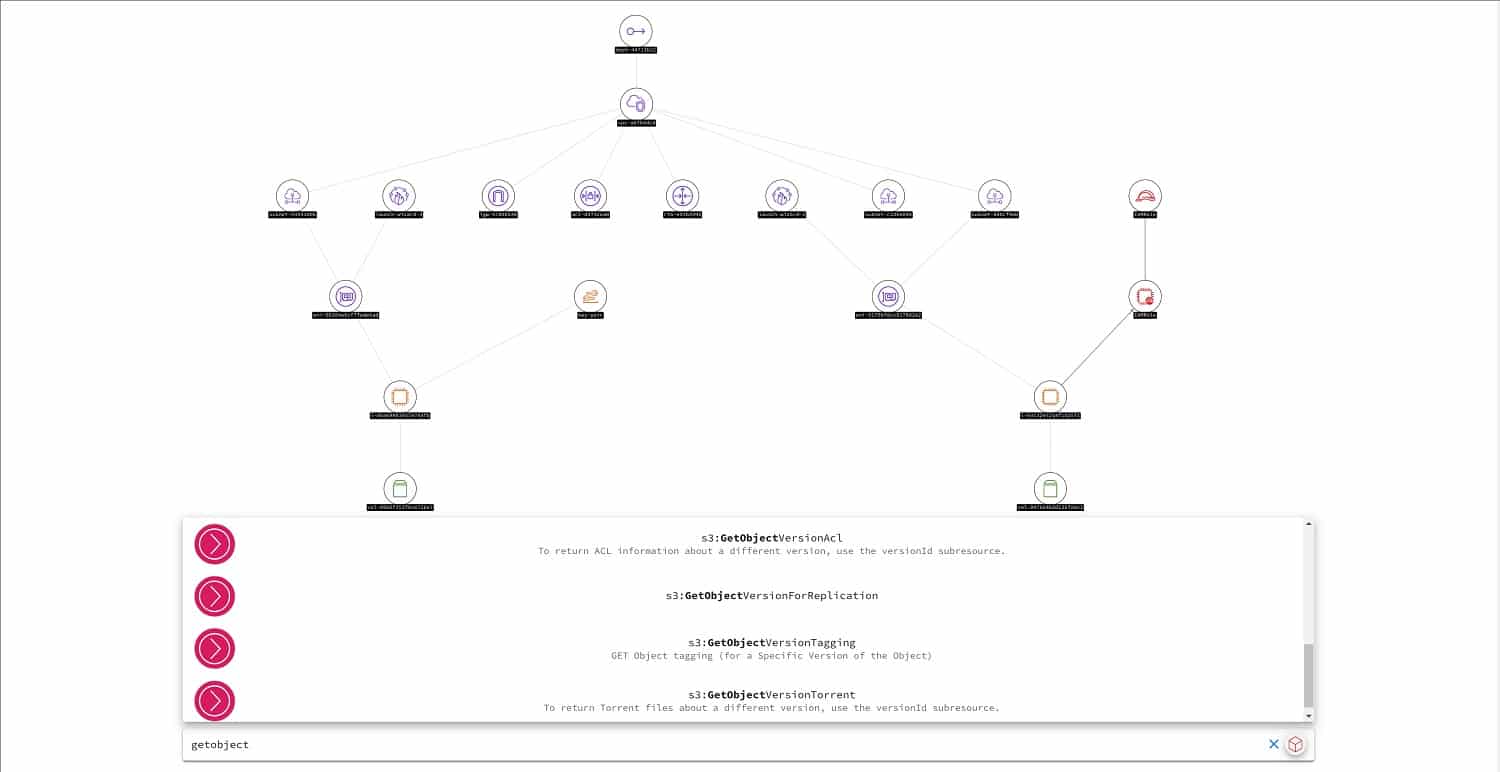
5. Awspx
Awspx is an on-premises system but it is designed to explore AWS accounts. You need to give this utility access credentials, so it is not an attack tool. It can be used to harden defenses against attack.
This package is an attack path mapper and it creates a visualization of all of the objects and user access rights in your AWS accounts.
Key Features:
- Visual Insights: Offers a graphical representation of access rights within AWS environments.
- User-Friendly Interface: Comes with a GUI front-end, making navigation and usage straightforward.
- Security Focused: Aimed at enhancing system defenses through comprehensive visibility.
Why do we recommend it?
Awspx is highly recommended for its unique ability to map out AWS access rights and potential attack paths through a user-friendly graphical interface. This clarity and ease of use make it an invaluable tool for identifying and mitigating security vulnerabilities within AWS environments.
The awspx system makes it much easier to see the attack paths that a hacker could use to gain access to your AWS services and move laterally to explore and steal the data within.
Who is it recommended for?
This tool is ideal for security professionals and system administrators tasked with securing AWS environments. Its visual mapping capabilities make it particularly suited for those looking to gain a comprehensive understanding of their AWS access rights and potential vulnerabilities, aiding in the development of robust defense strategies.
Pros:
- Intuitive Operation: Its ease of use facilitates a smooth experience even for those new to security analysis.
- Clarity in Visualization: Produces clear and detailed visual maps of AWS access rights, aiding in security assessments.
- No Cost: Available for free, making it an accessible option for users looking to improve their AWS security posture.
Cons:
- Limited Application: Primarily serves as a tool for security research and system hardening rather than active attack simulation.
The software for awspx installs on Docker over Linux and macOS and you can install it at the command line with the commands:
git clone https://github.com/FSecureLABS/awspx.git cd awspx && ./INSTALL
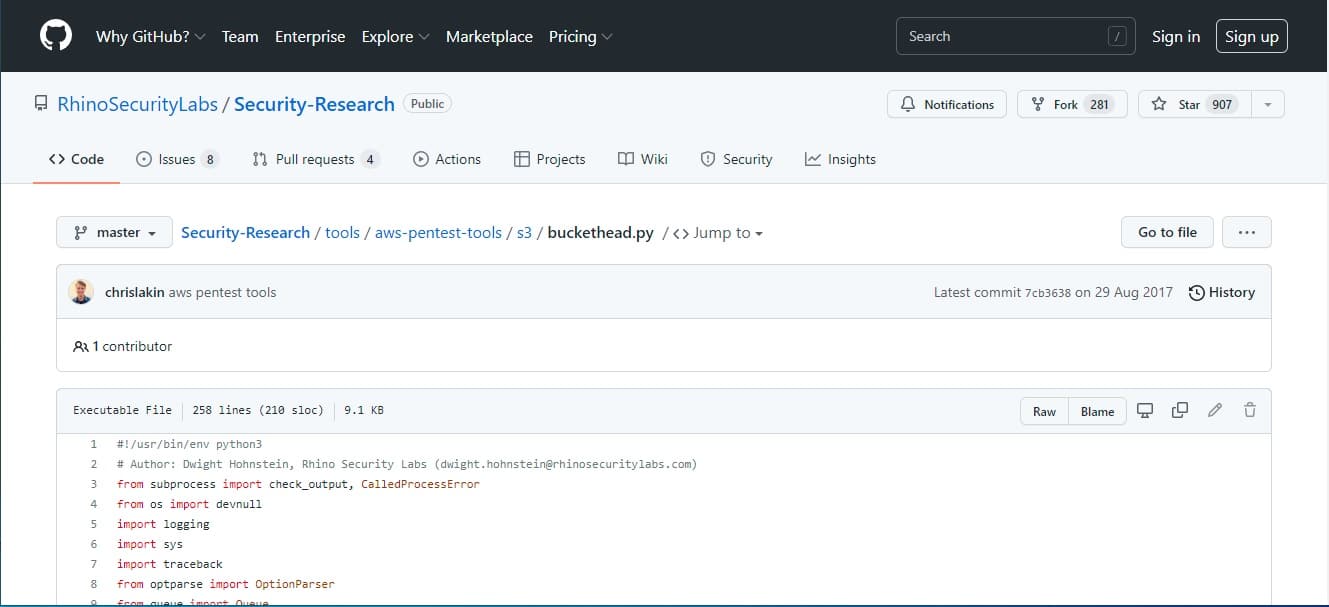
6. Rhino Security Labs Buckethead
Not to be confused with Apache Buckethead, Rhino Security Labs Buckethead is a python script that checks through Amazon S3 buckets. The tool searches the Web for sites that use Amazon S3 and then probes that space to see whether files can be uploaded to them. This research could then lead you to formulate an attack by uploading and executing a script.
Key Features:
- Python-Based: Developed as a Python script, making it widely accessible for those with Python installed.
- Command-Line Operation: Designed to be run from the command line, catering to users familiar with terminal interfaces.
- Low Detection Risk: Operates stealthily, minimizing the chances of detection during security assessments.
Why do we recommend it?
Rhino Security Labs Buckethead is recommended for its specialized capability to discreetly identify and assess the security of Amazon S3 buckets, offering valuable insights into potential vulnerabilities without leaving a trace. This makes it a potent tool for security professionals aiming to enhance their defensive strategies against data breaches.
Buckethead is a Python script, so you need to have the Python environment to run it. You also need to make sure that the computer you run it on has an internet connection.
Who is it recommended for?
This tool is ideally suited for cybersecurity researchers and professionals who require a straightforward, efficient means of evaluating the security of Amazon S3 buckets. Its stealthy nature and ability to pinpoint vulnerable targets without necessitating credentials make it especially valuable for preemptive security assessments and research.
Pros:
- Untraceable: Executes operations without leaving evidence, ideal for discreet security testing.
- Vulnerability Identification: Effective at uncovering significant security vulnerabilities in Amazon S3 buckets.
- Target Discovery: Aids in identifying potential easy targets for further security analysis or testing.
Cons:
- Basic Output: Provides output that may lack aesthetic appeal, focusing solely on functionality.
Buckethead is just a script. You can copy and paste it from the GitHub repository that stores it, which just displays the code. This is a research tool that will make an attack very easy to formulate. It looks for vulnerable S3 accounts and doesn’t require credentials to get into targets – it’s either blocked or it’s in.
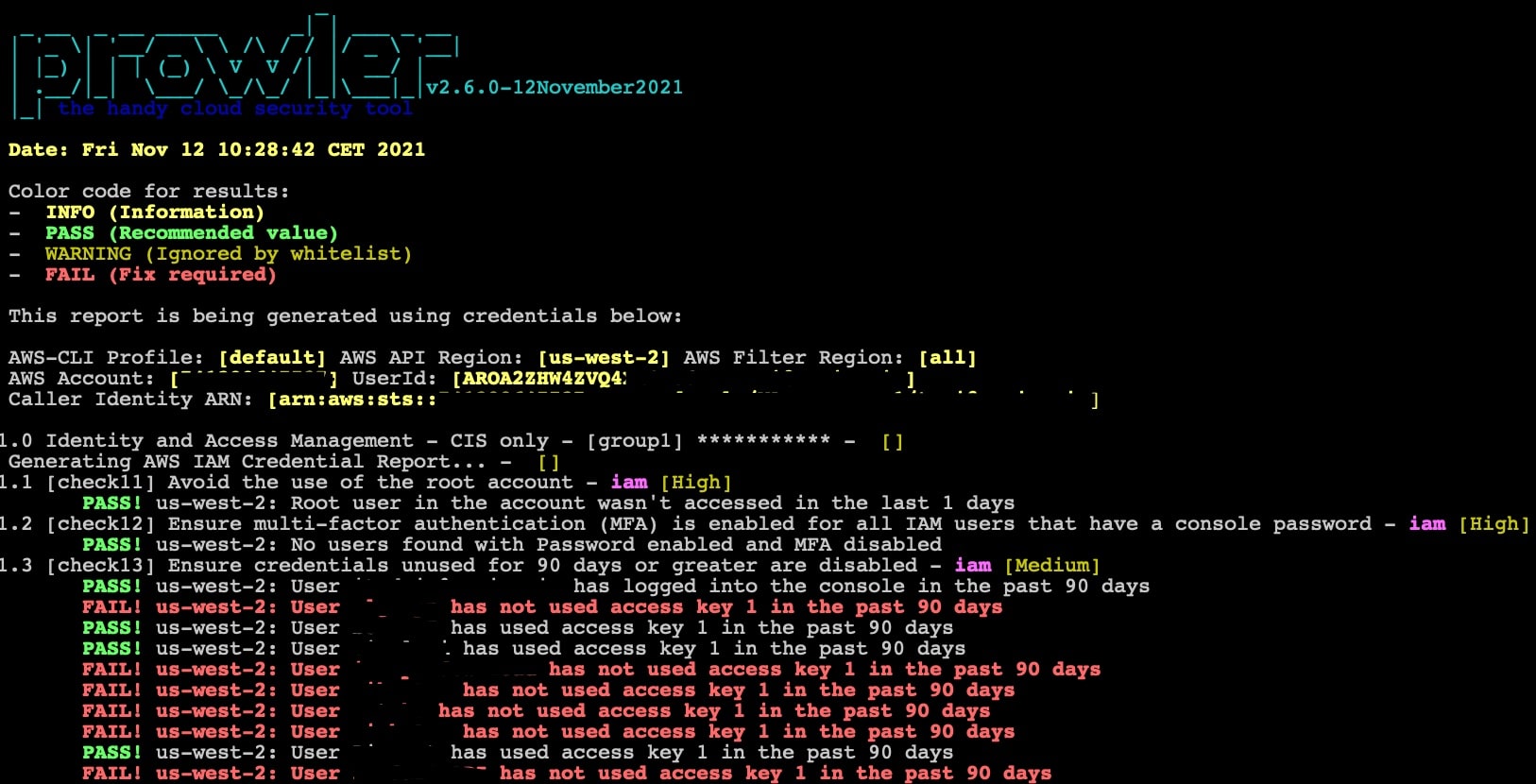
7. Prowler
Prowler is an open-source command-line utility that implements authorized searches through an AWS account, looking for vulnerabilities. It can be used to identify weaknesses that need to be fixed for data protection standards compliance.
Key Features:
- Compliance Focus: Optimized for verifying adherence to HIPAA, GDPR, and PCI-DSS standards.
- Authorized Access: Designed to operate with explicit permission, ensuring ethical use.
- Quick Scans: Capable of rapid mapping and assessment of AWS account vulnerabilities.
Why do we recommend it?
Prowler is recommended for its comprehensive and efficient approach to assessing AWS environments against stringent compliance standards like HIPAA, GDPR, and PCI-DSS. Its ability to perform a wide array of security tests rapidly, coupled with its no-cost availability, makes it an invaluable resource for organizations prioritizing security and compliance.
The tool searches through the identity and access management systems of an AWS account and ensures that they don’t provide access paths for hackers. You can’t use this tool on an account that you don’t own because it requires login credentials before it can operate.
The tool performs more than 200 security tests, including the 49 checks specified in the CIS Amazon Web Services Foundations Benchmark.
Who is it recommended for?
This tool is ideally suited for IT security professionals and compliance officers who manage AWS accounts and need to ensure their configurations and practices comply with industry standards. Prowler’s fast, in-depth assessments and focus on compliance make it a critical tool for organizations aiming to safeguard their data while adhering to regulatory requirements.
Pros:
- Ensures Compliance: Aids in ensuring that AWS environments meet critical data protection and compliance standards.
- Cost-Effective: Available at no cost, providing a budget-friendly option for security assessments.
- Efficient Performance: Executes over 200 security tests quickly, including those specified in the CIS AWS Foundations Benchmark.
Cons:
- Basic Reporting: Outputs results in a format that may require additional formatting for clarity or presentations.
Prowler is free to use. You can get some impressive output from the tool but you would need to feed it into a third-party front end to get the best visualizations because the command line output by itself is not so hot. Try Quicksight for a good GUI front end for this tool.
Prowler runs on Linux or macOS. It can be uploaded to an Amazon account (Amazon Linux) and run there. It can run on Windows, but only through the mediation of Cygwin. You can also run it over Docker.