Penetration testing is a critical component of any cybersecurity strategy, especially for businesses utilizing cloud platforms like Microsoft Azure. It helps identify vulnerabilities, assess security controls, and simulate real-world attacks to ensure systems and data remain secure. With the increasing adoption of cloud environments, including Azure, companies must continuously evaluate and strengthen their security posture to protect against evolving cyber threats
Azure, being one of the most widely used cloud platforms, offers a range of tools and services that allow businesses to build, deploy, and manage applications. However, as with any complex infrastructure, vulnerabilities can arise, making penetration testing essential for discovering potential weaknesses before they can be exploited by malicious actors. Penetration testing in Azure involves simulating attacks on an organization’s Azure environment to assess how resilient the platform is against threats.
To help organizations perform these assessments effectively, various penetration testing tools are available, each offering unique features to analyze different aspects of Azure’s security. These tools help security professionals identify misconfigurations, detect exposed services, and validate the effectiveness of security policies in place. Choosing the right tools can be a challenging task due to the variety of options available, each with its strengths, weaknesses, and specific use cases.
This guide presents an overview of some of the best penetration testing tools available for Azure environments. Whether you are looking for tools to perform automated scans, assess network security, or test specific Azure services, this comprehensive list will help you choose the right solutions to strengthen your cloud infrastructure and improve your overall security posture.
Here is our list of the nine best Azure penetration testing tools:
- Invicti EDITOR’S CHOICE A package of testing systems that can be used for automated procedures during penetration testing, as a vulnerability manager, or as a continuous testing tool in a CI/CD pipeline. This system is available as a SaaS package or as software for installation on Windows.
- Acunetix This vulnerability scanner for Web applications and networks can be used as a penetration testing tool and it is able to scan a range of systems, including Azure. Available as a SaaS platform or for installation on Windows, macOS, and Linux.
- Intruder A cloud-based vulnerability scanner that can be launched on demand or on a schedule. On-demand scanning for continuous security monitoring of on-premises systems and cloud services.
- Azucar A free PowerShell utility that runs on Windows but probes the statuses of Azure services, particularly Azure AD and databases.
- BloodHound Offered in free and paid versions, this tool focuses on attack strategies that can hit Active Directory implementations, including Azure AD. It runs on Windows, macOS, and Linux.
- PowerZure This free PowerShell utility is built to assess the security of Azure services with permission. It runs within your Azure account.
- ROADtools A free explorer that examines Azure AD structures and assesses them for security weaknesses. It installs on your Azure account.
- Stormspotter An attack surface grapher that identifies weaknesses in Azure and Azure AD. It runs over Docker.
- Burp Suite Available in both free and paid versions, this proxy-based system offers a range of penetration tools and can be run on Azure.
You can read more about each of these tools in the following sections.
Penetration testing is a manual process. Automated security tools are called vulnerability managers. There are some tools that fall between these two categories. These are able to perform repetitive tasks, such as brute force password guessing but they don’t sequence through a full series of vulnerability checks. Some packages can be set to operate as vulnerability managers or as penetration testing tools.
Azure penetration testing ground rules
Microsoft expects customers of Azure to test the system for security weaknesses and even invites account holders to report discovered weaknesses that require system fixes to resolve.
There are just a few rules that you need to stick to when performing penetration testing on Azure. If you break these rules, you could get your Azure account shut down or even get sued.
The rules you need to follow are:
- Don’t try to break into the accounts of other Azure customers – stick to your own account.
- Don’t try to capture or alter the data of other Azure customers.
- Don’t attempt phishing, doxing, or social engineering on Azure technicians.
- Don’t perform a DDoS attack.
- Don’t use automated testing utilities that generate a high volume of traffic in a short space of time.
- Don’t break the Microsoft Online Subscription Agreement.
For more information, see the Azure guidance on penetration testing.
The rules that Microsoft imposes on testing for Azure accounts might tie the hands of many white hat hackers, who are willing to try any of the techniques used by hackers in order to test the security of a system.
It could be said that you won’t get a full assessment of your Azure account’s resilience to hacker attack if your penetration testing tool is tied by the rules laid down for the use of an Azure account.
Some independent penetration testing services might prefer to break the rules. You might think that contracting a consultancy to break into your Azure account gets around the restrictions imposed by Microsoft. However, they don’t because the service argues that you should specify the parameters of an investigation when you agree to a contract with the penetration testing service so that banned activities are prevented.
The Best Azure Penetration Testing Tools
Although penetration testing is a specialized niche in IT security management, there is a surprisingly wide definition of what constitutes a penetration testing tool. Many commonly-used network management utilities that are built into the operating system can be used for system research. Ping, for example, is often used to probe networks both by network administrators and by hackers.
This means that this guide will present a range of tools that include system probes and attack utilities.
Our methodology for selecting Azure penetration testing tools:
We reviewed the market for Azure penetration testing packages and analyzed tools based on the following criteria:
- A probe or a hacking utility that can examine an Azure resource from an external location.
- A degree of automation
- A tool that can speed up checks for the OWASP Top 10
- Systems that can run on Linux or Windows
- Cloud-based options
- A free tool or a free trial period to assess the tool without paying
- Value for money from a useful utility or a free tool that is worth getting to know
As penetration testing models the behavior of hackers, tools for the job don’t need you to log into the system first. This also means that these penetration testing systems are versatile and not limited to probing one specific system. They can usually test on-site systems and a range of cloud platforms, such as Azure and AWS.
This list includes both free and paid tools. You should expect to get a better interface and more capabilities from the paid tools than from the free systems. However, you can put together your own penetration toolset by selecting a number of these recommended utilities.
1. Invicti
Invicti is a web application vulnerability scanner. It runs from an external viewpoint, so it is able to test applications no matter where they are hosted because the scanner focuses on individual packages rather than hosting systems.
The scanner can be of use to penetration testers because it gives an automated assessment of an application. The package has three modes, enabling it to be run on-demand, on a schedule, or continuously as part of a CI/CD pipeline.
Key Features:
- Flexible Deployment: Provides various deployment options to accommodate different testing environments and needs.
- External Evaluation: Conducts external assessments to identify vulnerabilities from an outsider’s perspective.
- Dual Functionality: Serves both as an automated penetration tool and a continuous tester, integrating into CI/CD pipelines.
- Azure Boards Integration: Enables findings to be directly reported to Azure Boards for efficient issue tracking and resolution.
Why do we recommend it?
Invicti stands out for its advanced web application vulnerability scanning capabilities, providing precise external evaluations from an outsider’s perspective. Its flexibility in deployment allows for on-demand, scheduled, or continuous integration into CI/CD pipelines, making it a powerful tool for maintaining rigorous security standards. The integration of AI enhances its ability to detect complex vulnerabilities, setting it apart as a forward-thinking solution in web security.
When used for automated testing, the Invicti environment can be set up to report findings through to Azure Boards. This enables the use of the test to quickly check through an application, flag issues through Azure Boards, and automatically route those issues through to a pen tester for further investigation.
As well as checking for standard exploits, the Invicti system uses AI to identify potential run conditions that could compromise the security of an application. It can also spot combinations of events that would create a security loophole.
Who is it recommended for?
Invicti is ideal for development teams and security professionals who require a reliable and efficient tool to integrate security testing seamlessly into their development processes. It’s particularly useful for organizations that utilize Azure Boards, as it can automatically communicate findings for swift issue resolution. This scanner is well-suited for those looking to automate the early stages of penetration testing and maintain a continuous assessment of web application security.
Pros:
- Penetration Testing Aid: Streamlines the initial scanning process in penetration testing scenarios, quickly identifying potential vulnerabilities.
- Efficient Issue Flagging: Automates the flagging of issues for further investigation, enhancing the efficiency of penetration testing efforts.
- Integration with DevOps: Seamlessly integrates with team and project management tools, improving the coordination of security efforts.
- Advanced AI: Utilizes AI to detect complex security issues, including potential run conditions and event combinations that could pose risks.
Cons:
- Limited Scope: Primarily functions as a vulnerability management tool rather than offering the full depth of penetration testing services.
Invicti is offered as a SaaS platform and also for installation on Windows and Windows Server. It can be assessed by accessing a demo system.
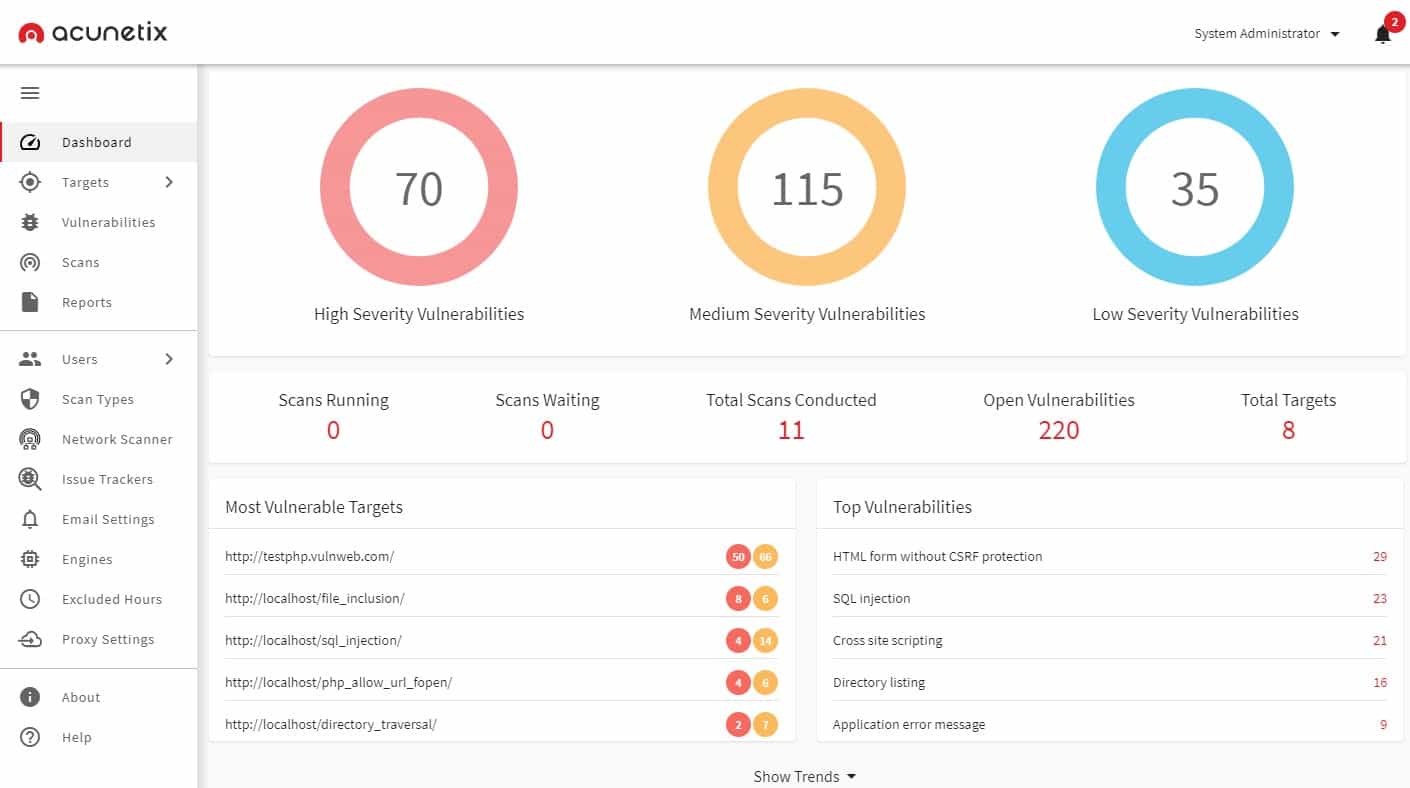
2. Acunetix
Acunetix is a vulnerability scanner that runs both internal and external checks. This automated tester can be used for an initial sweep of a system and it can also be launched on demand, focusing on specific strategies, making it a pen-testing tool..
The secret weapon of Acunetix is that it can integrate OpenVAS into its runs, including reports from that tool into its own assessments. This gives it a strong internal vulnerability report that can tell you what a hacker could do once he got inside your system.
Key Features:
- Comprehensive Scanning: Executes both internal and external vulnerability scans to ensure thorough security coverage.
- Integrated Testing: Incorporates OpenVAS for enhanced internal vulnerability assessments, offering detailed insights into potential internal threats.
- Efficiency Tools: Features a triage tool to expedite the vulnerability investigation process, streamlining security workflows.
- Project Integration: Seamlessly integrates with project management tools, enabling automated task allocation and tracking.
Why do we recommend it?
Acunetix is highly recommended for its comprehensive and automated vulnerability scanning capabilities that combine internal and external assessments. The integration of OpenVAS enhances its ability to provide detailed insights into potential internal threats, making it a formidable tool for identifying vulnerabilities that could be exploited by an attacker. Its efficiency tools, such as the triage system, streamline the security workflow, making it easier and quicker to manage and remediate vulnerabilities.
Acunetix can be triggered by project management tools and feed results through to bug trackers, letting you use the package to pre-scan a system and then automatically allocate investigation tasks to human pen-testers. This greatly cuts down the time that a penetration testing exercise can take and reduces the number of white hat hackers that you need on staff.
Who is it recommended for?
Acunetix is particularly well-suited for organizations that integrate security testing into their CI/CD pipelines and require a dynamic, flexible scanning solution that can be triggered on demand. It’s also ideal for companies looking to optimize their security resources by reducing the reliance on large in-house penetration testing teams, thanks to its ability to automate initial scans and integrate findings directly into project management and bug-tracking systems. This makes it a valuable asset for development teams that prioritize fast and efficient security assessments.
Pros:
- CI/CD Pipeline Compatibility: Perfectly suited for integration into continuous integration/continuous deployment workflows, facilitating automated security testing.
- Flexible Deployment: Offers on-demand scanning capabilities, allowing for targeted testing based on specific security concerns.
- Resource Optimization: Reduces the need for a large in-house penetration testing team by automating initial vulnerability scans.
- Workflow Automation: Enhances efficiency by automating the flow of information to project management and bug-tracking systems.
Cons:
- Limited Penetration: Focuses on identifying vulnerabilities without actively exploiting them, limiting the scope to potential security risks rather than confirmed breaches.
Acunetix is available as a SaaS platform or as a software package for Windows, macOS, and Linux. Assess Acunetix through its demo system.
3. Intruder
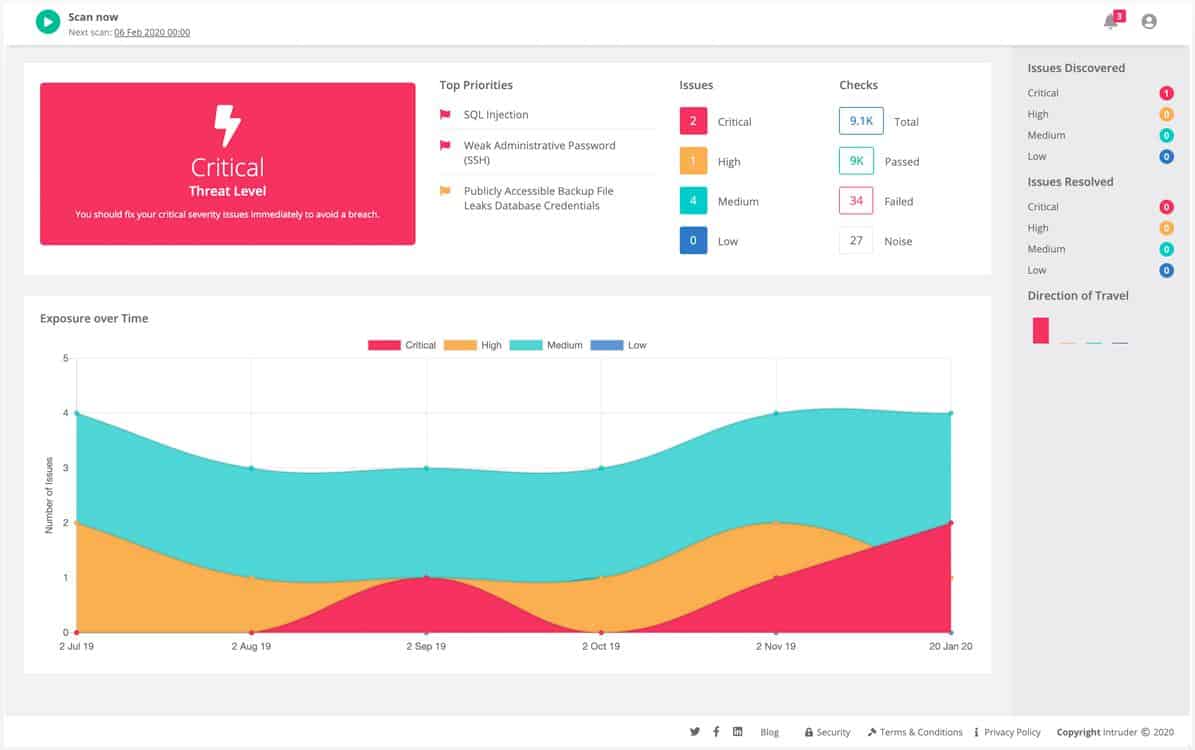
Intruder is a SaaS vulnerability scanner that is built around a vulnerability scanner and managed by experienced penetration testers. This system offers options for monthly scheduled scans and continuous testing. You also get access to the controls of the vulnerability scanner, giving you the option to launch a scan whenever you want.
The Intruder system is an external scanner, which is able to check on cloud systems, such as Azure. Integrations with the cloud platforms enable the scanner to fully document its findings of configuration weaknesses in terms of the services that the customer subscribes to. Web application scanning is also included with all of the plans of the Intruder service and higher plans also get internal scanning for networks and on-site applications.
Key Features:
- Continuous Monitoring: Offers both scheduled and on-demand scans, allowing for consistent security oversight.
- Cloud Integration: Specifically designed to assess Azure and other cloud platforms, ensuring comprehensive cloud security.
- Web Application Focus: Includes thorough scanning capabilities for web applications to detect vulnerabilities.
- Collaboration Tools: Integrates seamlessly with project management and collaboration platforms for efficient workflow.
Why do we recommend it?
Intruder is recommended for its comprehensive vulnerability scanning capabilities that blend automated technology with human expertise. The platform excels in identifying and documenting security weaknesses across cloud infrastructures, web applications, and internal networks. Its flexibility in scheduling and initiating scans ensures that security monitoring is both proactive and responsive, adapting to the unique needs of each business.
Intruder provides a CloudBot for Azure, AWS, and GCP that constantly checks for abandoned connections and requests from illogical sources. You might have many accounts on each platform because, technically, each service operates on its own separate system even though a single sign-on mechanism makes it seem that they are all added to your core platform subscription. The Intruder system isn’t blocked by service account segmentation and scans across services.
The Intruder service provides a comprehensive hosted vulnerability scanning solution, leveraging the expertise of third-party tools to enhance its capabilities. The base package, known as the Essential plan, incorporates the powerful OpenVAS scanner. For advanced features, the Pro and Premium plans include the Tenable Nessus vulnerability scanner. The SaaS package also includes storage for comprehensive details on detected vulnerabilities, which are carefully overseen by the dedicated team of penetration testers. Additionally, users have the option to request a manual pen testing exercise from our experienced professionals.
Who is it recommended for?
Intruder is particularly beneficial for organizations that utilize cloud services extensively, such as Azure, AWS, and GCP. It is well-suited for businesses that need continuous security oversight and are looking for a solution that integrates easily with existing project management tools, enhancing both security and operational efficiency.
Pros:
- Versatile Scanning Options: Provides flexibility with continuous or scheduled vulnerability scanning to suit various monitoring needs.
- Expert Oversight: Combines automated scanning with the expertise of experienced penetration testers for enhanced security analysis.
- Cloud Service Scanning: Effectively identifies configuration weaknesses across cloud services, enhancing cloud infrastructure security.
- Web App Security: Capable of pinpointing vulnerabilities in web applications, facilitating robust web security.
- Integration Capabilities: Offers project management integration, streamlining the vulnerability management process.
Cons:
- Feature Access: Advanced features are reserved for higher-tier plans, potentially limiting for users on lower-tier plans.
Intruder is a SaaS platform with three plan levels. You can assess the system with a 14-day free trial.
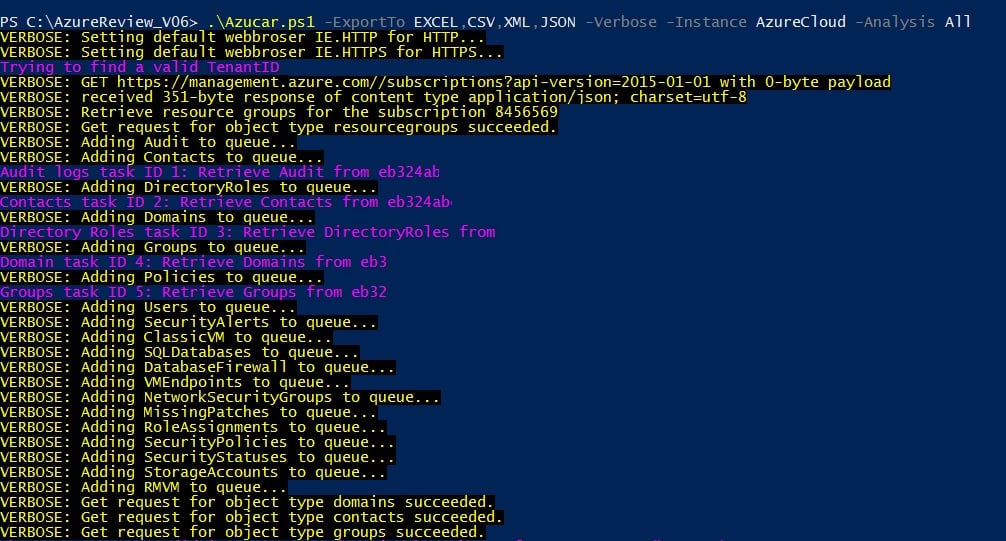
4. Azucar
Azucar is a PowerShell utility that assesses Azure accounts to which it is given access. This package won’t try to break into your Azure security, it will explore it from the inside and let you know where potential problems lie.
If you want to perform a full red team exercise, you could run this tool first and then hand a list of issues to your hacker team to see if they can use them to break in.
Key Features:
- Azure-Specific Analysis: Designed to thoroughly assess Azure environments without violating Microsoft’s security policies.
- Active Directory Insights: Evaluates the setup of Azure Active Directory (AD) for potential vulnerabilities.
- Database Security Checks: Reviews the security posture of Azure’s database services to identify possible weaknesses.
Why do we recommend it?
Azucar is recommended for its specialized capability to assess Azure environments comprehensively without breaching Microsoft’s stringent security policies. This tool is adept at providing deep insights into Azure Active Directory and database services, pinpointing potential vulnerabilities with precision. Its efficiency in scanning and detailed reporting makes it an invaluable tool for Azure account owners looking to enhance their security posture quickly.
The areas covered by this tool include general virtual server security, Azure AD, and the database services offered by the platform. Use this system for an initial research phase.
Who is it recommended for?
Azucar is particularly beneficial for Azure account administrators or security teams who need an in-depth evaluation of their Azure infrastructure. It’s ideal for those planning to conduct red team exercises, as it can serve as the preliminary step to identify vulnerabilities before testing them through simulated attacks. This tool is also suited for users comfortable with command-line interfaces and looking to integrate detailed Azure security assessments into their security protocols.
Pros:
- Owner-Driven Scans: Operates exclusively within the boundaries of the owner’s Azure account, ensuring compliance and security.
- Comprehensive Reporting: Delivers detailed reports on Azure account configurations, aiding in swift vulnerability identification.
- Efficiency: Performs quick scans, allowing for rapid assessment of Azure environments.
Cons:
- User Interface: Primarily a command-line tool, which may present a learning curve for users unfamiliar with PowerShell.
Azucar is free to use and you can download it from GitHub. The utility runs on Windows through PowerShell.
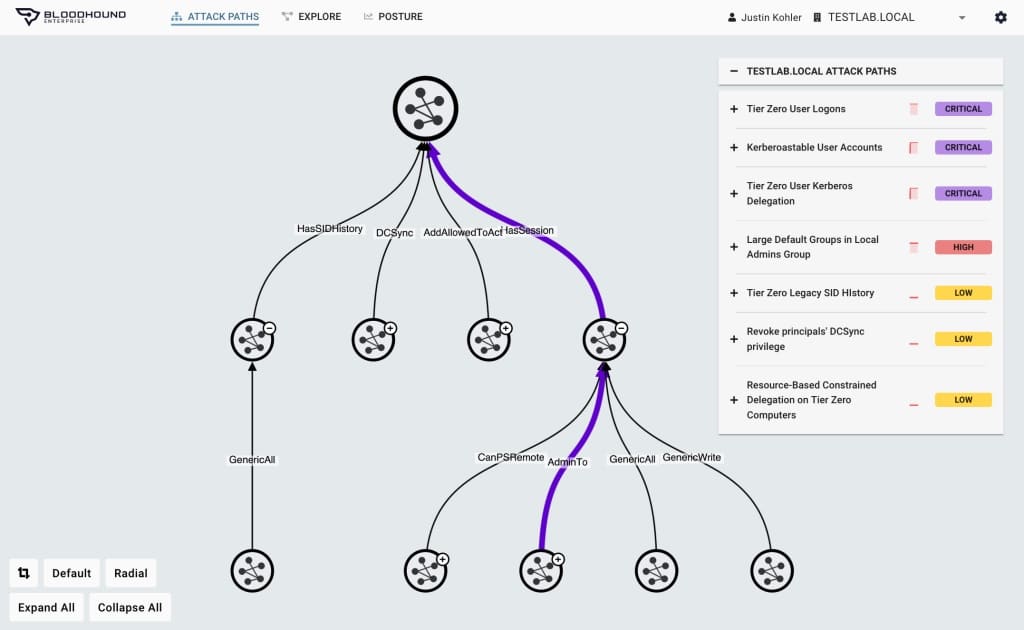
5. BloodHound
BloodHound is a free tool that focuses on all implementations of Active Directory no matter what applications they govern, or where they are hosted, so it will work for Azure AD.
This system uses a graphing system to map through permissions in AD and identify weaknesses.
Key Features:
- Access Path Analysis: Utilizes advanced graphing techniques to uncover potential attack paths within Active Directory environments.
- Visual Interface: Features an intuitive front-end design, making it easier to navigate and interpret complex relationships.
- Dual-Use Application: Equally beneficial for offensive (red team) and defensive (blue team) security strategies.
Why do we recommend it?
BloodHound is highly recommended for its sophisticated analysis capabilities that leverage advanced graphing techniques to expose potential attack paths within Active Directory environments. Its dual-use functionality makes it an invaluable asset for both red team (offensive) and blue team (defensive) security operations. The visual interface simplifies the navigation and interpretation of complex permissions and relationships, making it accessible to a wide range of users.
You can use BloodHound to proactively defend a system or to find a route for attack. It is able to spot very complicated attack paths that the human eye could not possibly assess.
Who is it recommended for?
BloodHound is ideal for security professionals engaged in enhancing organizational security, whether by identifying vulnerabilities (blue team) or exploiting them in simulated attacks (red team). Its ability to provide deep insights into intricate network relationships makes it a powerful tool for anyone responsible for securing Active Directory environments. BloodHound’s free availability also makes it accessible to a broad audience, including security enthusiasts and smaller organizations without large security budgets.
Pros:
- User-Friendly: Despite its powerful capabilities, it remains accessible and easy to use for various skill levels.
- Versatility: Offers valuable insights for both attack planning and defense strengthening, enhancing overall security posture.
- No Cost: Available for free, making it an accessible tool for security professionals and enthusiasts alike.
Cons:
- Analysis Expertise Required: While the tool provides comprehensive data, interpreting the results effectively requires a certain level of expertise.
The paid version of this system is called BloodHound Enterprise and you can get a demo of it. There is a free version called BloodHound Open-Source, which can be downloaded from GitHub.
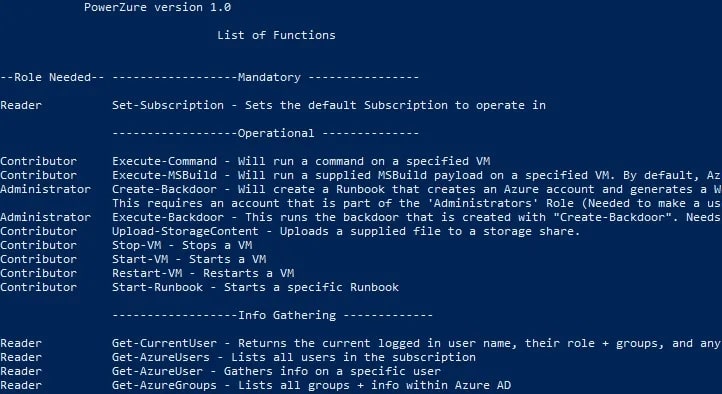
6. PowerZure
PowerZure is a free tool that is written in PowerShell. This package won’t help you break into an Azure account because you need to give it an access credentials token before it can extract data from your Azure resources.
Key Features:
- Azure Compliant: Ensures operations stay within Azure’s security guidelines, providing a safe framework for analysis.
- Permission Mapping: Offers detailed mappings of AD permissions, aiding in the identification of potential attack vectors.
- Strategic Insights: Provides valuable information for both offensive and defensive security strategies regarding Azure AD.
Why do we recommend it?
PowerZure is recommended for its specialized focus on Azure environments, providing a secure and compliant method to analyze and map permissions within Azure Active Directory. This tool generates actionable data that can guide both offensive and defensive strategies, making it invaluable for understanding and improving Azure AD security configurations. Its adherence to Azure’s security guidelines ensures that analyses are conducted safely, without risking the integrity of the system.
The PowerZure package includes routines for mapping access rights that are extracted from Azure AD. This information can help your red team to plan an attack strategy or let your blue team see which permissions need to be tightened in order to defend the system.
Who is it recommended for?
PowerZure is particularly beneficial for system administrators and security teams focused on Azure environments. It offers strategic insights that are crucial for strengthening defenses and preparing for potential attack scenarios. The tool is also ideal for organizations that prioritize compliance and secure data handling, as it operates strictly within Azure’s prescribed security frameworks.
Pros:
- Actionable Data: Generates exportable results for further analysis or reporting, enhancing usability for security teams.
- In-depth AD Analysis: Delivers a thorough examination of permissions within Azure AD, aiding in pinpointing security gaps.
- Administrative Utility: Especially useful for system administrators aiming to strengthen security measures.
Cons:
- Limited Scope: Focuses on information gathering rather than including functionalities for active penetration testing or exploitation.
PowerZure runs from within Azure or remotely from a device running Windows. Download the package from GitHub.
7. ROADtools
ROADtools is a library of procedures that can be used to assess Azure AD security issues. The package requires you to create a program of your own in order to run these processes. However, that doesn’t need to be much more than a basic script.
The processes extract AD data and put them into a database. You can then use a querying front end, provided with the library, to access the database’s entries. The system doesn’t break into the Azure account but as it is a set of procedures, you could add in functions from other sources to create an attack utility.
Key Features:
- DIY Security Toolkit: Offers a customizable approach to Azure AD security, allowing for tailored security assessments.
- Data Organization: Automatically structures extracted AD data into a database for systematic analysis.
- Active Directory Focus: Concentrates on dissecting Active Directory configurations to unveil potential security issues.
Why do we recommend it?
ROADtools is highly recommended for its customizable toolkit approach to Azure AD security, offering a powerful platform for tailored security assessments. It allows users to create programs that specifically meet their security analysis needs, providing a flexible framework that can be adapted as necessary. The ability to organize extracted AD data systematically into a database and analyze it through a sophisticated querying front-end makes it exceptionally valuable for identifying and understanding security vulnerabilities within AD configurations.
The database that ROADtools creates isn’t just a copying over of Active Directory records. The entries in the database include a structure index, which shows you the relationships between records. The querying interface is also more than just a data viewer because it is able to reassemble the recorded structure into a hierarchy and identify security weaknesses in the configuration.
Who is it recommended for?
ROADtools is ideal for security analysts, developers, or IT professionals who are comfortable with scripting and wish to engage deeply with Azure AD’s security architecture. It’s particularly beneficial for organizations that require a detailed, customizable analysis of Active Directory environments and prefer a hands-on approach to security assessments. This tool is best suited for those who are looking to augment their security processes with a versatile, insightful utility capable of adapting to complex and evolving security landscapes.
Pros:
- Customizable Approach: Provides a flexible toolkit that can be adapted or expanded based on specific security needs.
- Analytical Depth: Enables comprehensive research into access paths and relationships within Azure AD structures.
- Weakness Identification: Assists in uncovering and understanding security vulnerabilities within AD configurations.
Cons:
- Requires Additional Effort: Not a standalone solution; demands user input to create and run analysis scripts, potentially increasing complexity for less technical users.
The ROADtools library is written in Python, so you can run the functions on any operating system that has Python installed on it – including on Azure. Download the package for free from GitHub.
8. Stormspotter
Stormspotter is a free utility that has a nice graphical front end and shows the relationship between records in Azure AD. It is also able to query Azure Resource Manager. This isn’t an attack system because it requires you to give it access credentials for your Azure account.
Key Features:
- Azure AD Visualization: Graphically represents Azure AD relationships, enhancing comprehension.
- ARM Queries: Capable of querying Azure Resource Manager, broadening its utility.
- Free Utility: Offers its services without charge, increasing accessibility for users.
Graphical Interface: Features an intuitive graphical interface, simplifying navigation and use.
Why do we recommend it?
Stormspotter is recommended for its effective visualization capabilities that greatly simplify the understanding and analysis of Azure AD relationships. Its graphical representation of AD connections and the ability to query Azure Resource Manager enhances its utility as a comprehensive investigative tool. Being a free utility, it provides valuable services without cost, making it accessible to a wide range of users who need to conduct thorough security investigations within Azure environments.
Who is it recommended for?
Stormspotter is particularly beneficial for system administrators, security analysts, and IT professionals who require a clear visual mapping of Azure AD structures to enhance their security protocols. Its compliance with Azure’s security guidelines ensures that it provides safe and authorized access for analysis, making it an ideal tool for organizations prioritizing thorough, compliant security assessments. The tool’s ease of use and detailed visual output make it suitable for those who need an intuitive way to navigate complex AD relationships and configurations.
Pros:
- Azure Compliance: Adheres to Azure’s security guidelines, ensuring safe and authorized access for analysis.
- Investigative Tool: Designed to aid in security investigations, providing a detailed visual representation of Azure AD relationships.
- Visual Mapping: Creates a comprehensive graphical map that illustrates access rights and permissions, facilitating easier analysis and decision-making
Cons:
- Limited Functionality: Primarily a defensive tool; it does not include capabilities for conducting offensive security tests or penetration attempts.
You would use Stormspotter for blue team defense rather than to attack Azure instances. This system runs over Docker and you can download it for free from GitHub.
9. Burp Suite
Burp Suite is available for free with a Community Edition. There is a paid version, called the Professional Edition. The free version offers penetration testing tools, while the paid system also has automated testing systems that can be used for vulnerability scanning. There is also a higher plan, called the Enterprise Edition, which is a full vulnerability scanner.
Key Features:
- Versatile Use: Suitable for both research purposes and active penetration testing, offering flexibility in cybersecurity tasks.
- Integration Features: Automates the transfer of variables between screens, streamlining the testing process.
- Azure Specific Version: Provides functionalities tailored for Azure environments, enhancing its utility for Azure-based security assessments.
Why do we recommend it?
Burp Suite is highly recommended for its versatility and depth in cybersecurity tasks, especially in penetration testing and vulnerability scanning across different environments, including Azure. It stands out for its integration features that automate the testing process, significantly enhancing efficiency and accuracy. The proxy-based operation allows it to simulate external attacks effectively, providing a comprehensive suite of tools for detailed security assessments.
BurpSuite operates by launching a proxy and then using that as a launch pad for external attacks. This enables the system to act as an external attack tool even though it is hosted on the system that is being tested.
Who is it recommended for?
Burp Suite is ideal for security professionals, from beginners to experts, due to its user-friendly interface and extensive documentation. It’s particularly beneficial for teams conducting regular security testing and assessments, offering both a free version for basic penetration testing and advanced paid versions for more comprehensive vulnerability scanning. This makes it suitable for organizations of all sizes that are looking to strengthen their security posture against a variety of attack vectors.
Pros:
- User-Friendly: Known for its ease of use, making it accessible for security professionals of varying skill levels.
- Comprehensive Attack Suite: Includes a wide array of attack simulations, allowing for thorough security testing and vulnerability identification.
- Automation Capabilities: Facilitates the automation of attack variables, reducing manual input and increasing efficiency in penetration testing scenarios.
Cons:
- Upgrade Caution: While the free version offers significant utility, users should carefully consider the benefits before moving to the paid version for vulnerability scanning features.
Burp Suite runs Windows, macOS, Linux, and also Azure. Download the Community edition for free or get a free trial of the Professional edition.