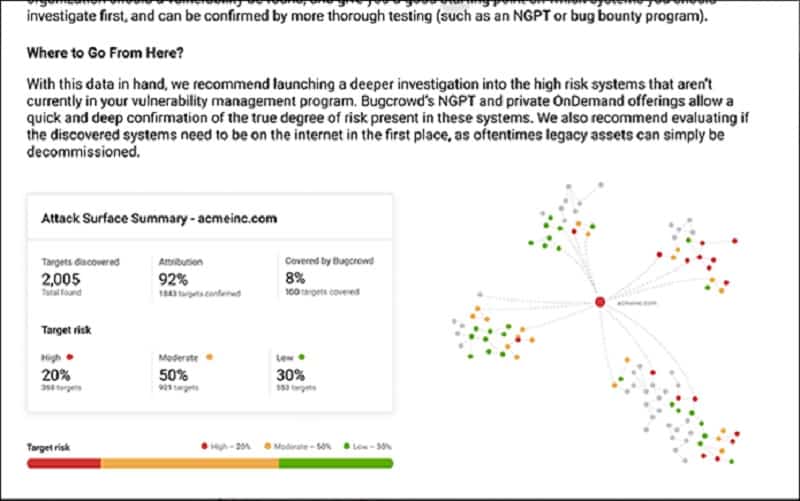
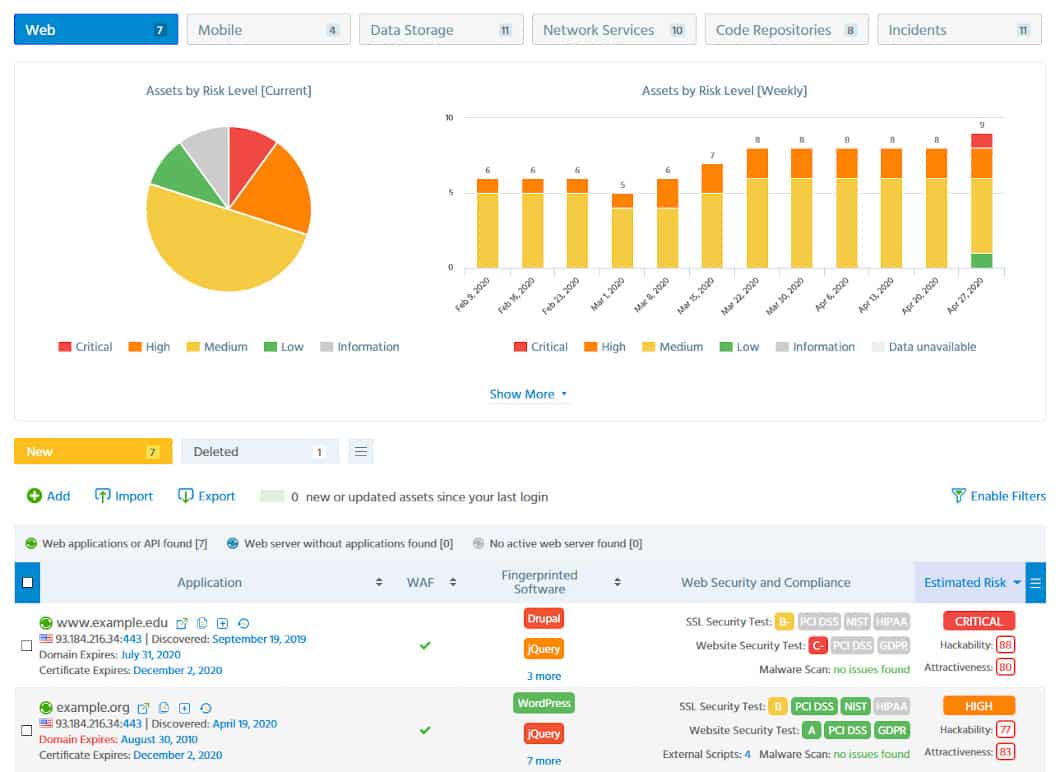
Attack surface monitoring tools help you to identify the risks that your software presents to data security.
Attack surface analysis and protection is the software equivalent of vulnerability management, which focuses on device settings and operating system exploits.
Here is our list of the best attack surface monitoring tools:
- Intruder EDITOR’S CHOICE A cloud-based vulnerability scanner that offers scanning for AWS, Azure, and GCP. Get internal and external scans for your AWS accounts plus Web application and network scanning. This service is delivered by penetration testers who verify scan results and can also be hired for manual scanning exercises. Get a 14-day free trial.
- ManageEngine Vulnerability Manager Plus (FREE TRIAL) This package of system security services bundles a vulnerability scanner with the systems needed to rectify the discovered security weaknesses. It will scan devices running Windows, macOS, and Linux while running on Windows Server. Access a 30-day free trial.
- ManageEngine ADAudit Plus (FREE TRIAL) Excels in attack surface monitoring with its advanced real-time tracking and detailed auditing capabilities. It offers comprehensive insights into user activities and system changes, helping to quickly identify and mitigate potential threats. Access a 30-day free trial.
- Rapid7 InsightVM Part of a security platform, this vulnerability manager can be supplemented by a research feed that sweeps records for third-party risk. This is a cloud-based system.
- Bugcrowd Attack Surface Management –A hacker-developed asset tracking service can read through supporting service layers and monitor their security. This is a SaaS system.
- ReliaQuest GreyMatter Digital Risk Protection A threat intelligence research service that looks through hacker message boards and other Dark Web channels to reveal planned attacks on their clients.
- CoalFire Attack Surface Management A capable asset tracking system that looks at the weak points in external systems that can provide entry points for hackers. This is a managed service.
- OWASP Zed Attack Proxy an accessible and highly regarded vulnerability scanner that a free Attack Surface Detector can enhance. Available for Windows, macOS, and Linux.
- Burp Suite Enterprise An excellent vulnerability scanner can be added to with the free OWASP Attack Surface Detector. Available for Windows, macOS, and Linux.
- ImmuniWeb Discovery A combination of a vulnerability scanner, an attack surface monitor, and a tailored threat intelligence feed based on tracking hacker intel. This is a cloud-based service.
- CyCognito Attack Surface Management A cloud-based external asset discovery service performs continuous penetration testing on exposed program units. This system also includes third-party risk assessments and system hardening recommendations.
You can read more about each of these systems in the following sections.
Attack surface monitoring tools provide Attack Surface Management (ASM). This is a continuous process because there are new exploits discovered all of the time. ASM involves two phases of research. First, you need to know what data you hold and what sensitivity ranking each piece of data holds. Secondly, you need to have an accurate software inventory.
With complete system documentation in place, an attack surface monitoring tool can start to search for the typical inroads that hackers are known to use. DevOps environments can integrate ASM into their CI/CD pipeline to head off potential problems with new functions and features.
Attack surface monitoring
The development of new attack strategies by hackers means that attack surface monitoring can’t sit still. You also have an issue with further data services and software packages to watch over. No system is static, and so attack surface monitoring needs to be an ongoing task.
The field of attack surface monitoring is relatively new. There aren’t many tools available for this task at the moment. If you are not satisfied with the few attack surface monitoring tools currently available, you could rely on a vulnerability scanner because some of these also cover software vulnerabilities.
One step back from outright attack surface monitoring and vulnerability management, you could rely on Intrusion Detection Systems (IDSs). These look for any malicious activity on your system, including data theft events. Another category of software that would come in useful as an attack surface monitoring substitute is data loss prevention (DLP). The critical aim of attack surface monitoring is to protect data stores from unauthorized access, which is the same as DLP systems.
The best attack surface monitoring tools
The blur between vulnerability management and attack surface management means that some vulnerability scanners advertise themselves as attack surface monitors. At the same time, many vulnerability managers also offer attack surface monitoring without explicitly using that term in their product descriptions.
Our methodology for selecting an Attack surface monitoring tool
We reviewed the market for attack surface monitors and analyzed the options based on the following criteria:
- A system that checks software for vulnerabilities
- A service that identifies out-of-date software versions
- A monitoring tool that logs data access by software
- A monitor that can distinguish between valid user activity and suspicious account activity
- A service that reduces the risk of sensitive data loss or disclosure
- A free trial or a demo version for a no-cost assessment
- A comprehensive tool that protects sensitive data by identifying software security weaknesses
As the term “attack surface” is relatively new. We don’t rely on that phrase being in the name or description of a security system included in our considerations.
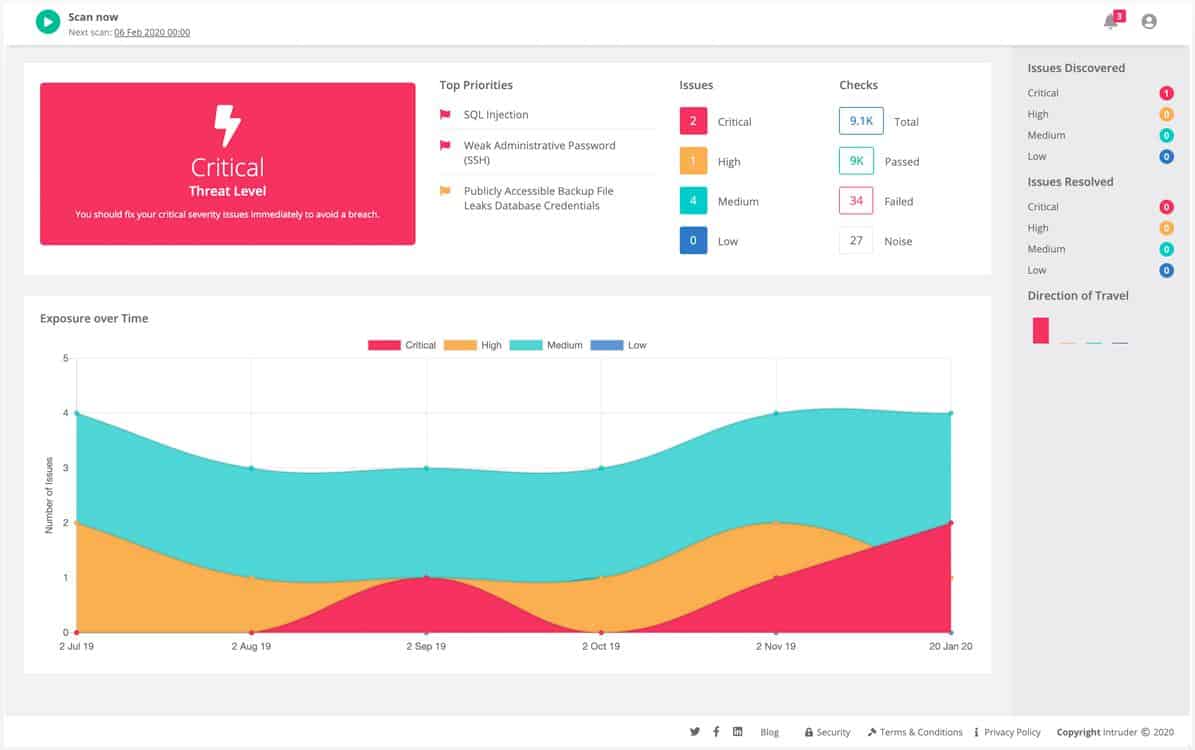
1. Intruder (FREE TRIAL)
Intruder is a versatile cloud-based vulnerability management system that caters to various implementation scenarios. The platform offers an external attack surface scanning feature, allowing comprehensive testing of both on-premises systems and cloud accounts. Additionally, it serves as a web application security tester.
Key Features:
- Comprehensive Vulnerability Scanning: Offers detailed analysis of both internal and external network vulnerabilities, enhancing system security.
- Cloud Configuration Audits: Performs meticulous checks on cloud account setups to ensure optimal security configurations.
- Secure Cloud Connectivity: Monitors and secures connections to cloud services, safeguarding against unauthorized access.
- Web Application Assessments: Provides in-depth security testing for web applications to detect and mitigate vulnerabilities.
- Professional Pen Testing Support: Access to a dedicated human penetration testing team for expert security advice and intervention.
Why do we recommend it?
Intruder stands out for its comprehensive approach to vulnerability management, blending automated scanning with expert human insight. This dual approach ensures not just detection but also actionable guidance on remediation, making it a robust security solution.
With Intruder, you have the option to perform network scanning within your own environment, examining software configurations and monitoring connections to your cloud services.
The scanner can be utilized for on-demand tests or scheduled scans. The Essential package includes one scheduled scan per month, while the higher-tier editions offer unlimited scheduled scans, enabling continuous scanning.
Who is it recommended for?
It’s ideal for organizations of all sizes looking to strengthen their security posture with both automated tools and the expertise of a human pen testing team, especially those managing complex, hybrid cloud environments.
Pros:
- Expert-Managed Service: A team of professional penetration testers offers dedicated security management and oversight.
- Detailed Remediation Guides: Comprehensive guides are available to address and fix security vulnerabilities effectively.
- Sensitive Data Protection: Advanced measures are in place to prevent data breaches and protect sensitive information.
- SSL Certificate Monitoring: Automated monitoring for SSL certificate expirations to avoid security lapses.
- Compliance Assistance: Simplifies the process of meeting compliance requirements, reducing regulatory burden.
Cons:
- Tiered Feature Access: Access to full feature set requires the highest subscription level, necessitating strategic planning on feature necessity.
The Intruder system is a comprehensive SaaS package delivered by a managed security service provider. It’s important to note that the vulnerability scanner used within the platform is based on trusted third-party tools. While you could potentially access the original vulnerability scanners directly, Intruder offers the convenience of a fully integrated solution. The Essential plan utilizes the OpenVAS vulnerability scanner, while the Pro and Premium plans include the Tenable Nessus system.
Intruder offers access to a vulnerability scanner supervision by a team of pen testers and it is also possible to hire the group for a manual pen testing exercise for a fee. Assess the Intruder system with a 14-day free trial.
EDITOR'S CHOICE
Intruder is highly recommended as an attack surface monitoring tool due to its versatile range of exploit detection options, making it applicable in various scenarios. The system functions as an automated external attack surface scanner, offering scheduled and on-demand scanning. It supports internal network scanning, as well as web application and cloud platform security testing. With the ability to set up continuous scanning, Intruder can serve as a robust security monitor or seamlessly integrate into a CI/CD pipeline as a continuous web application security tester.
Download: Get 14-day FREE Trial
Official Site: https://portal.intruder.io/free_trial
OS: Cloud-based
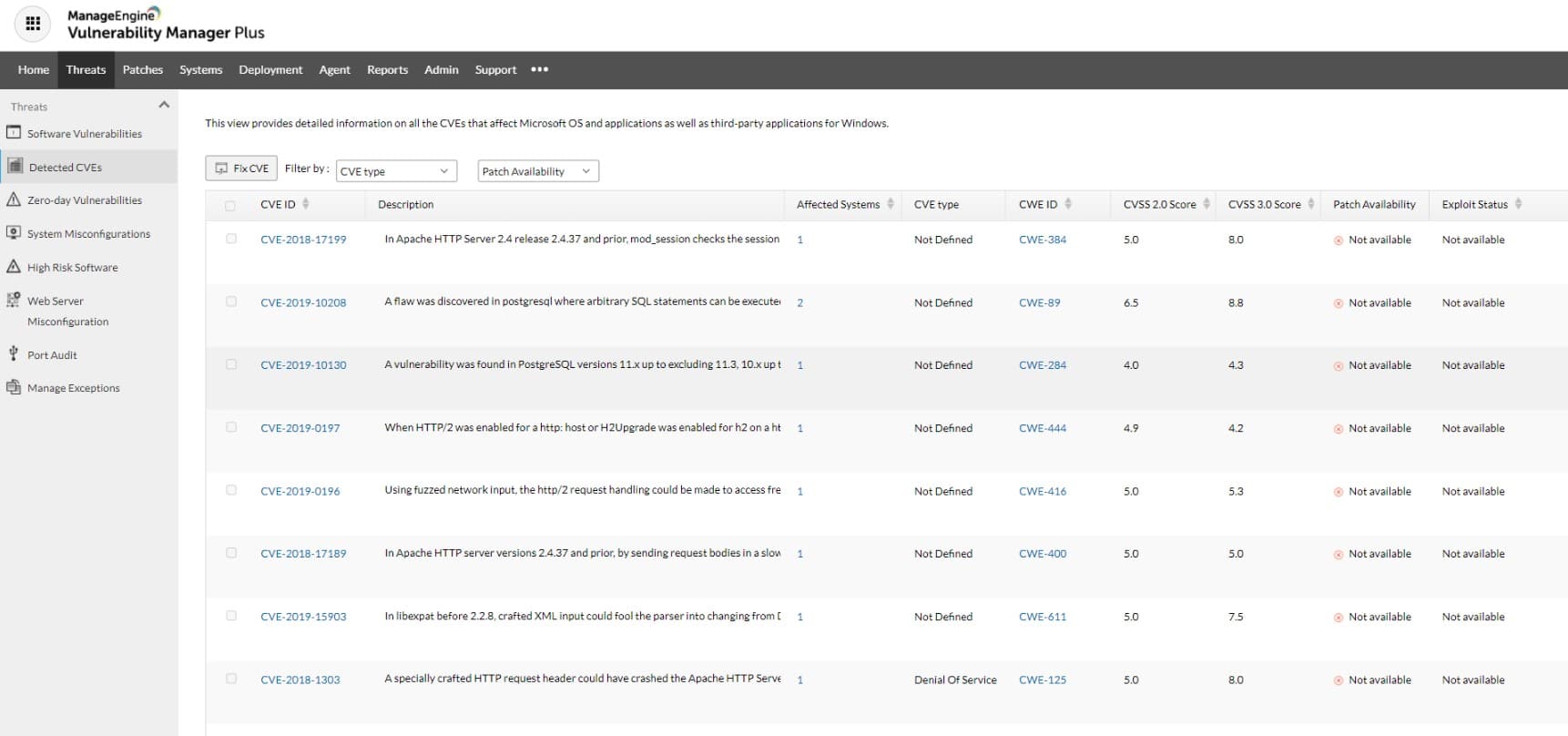
2. ManageEngine Vulnerability Manager Plus (FREE TRIAL)
ManageEngine Vulnerability Plus provides a vulnerability scanner and modules to fix the problems that the scanner identifies. This includes a patch manager. The system will protect a fleet of endpoints, operating over a network and even provide coverage for multiple sites. The protected endpoints can be running Windows, macOS, or Linux.
Key Features:
- Robust Vulnerability Scanning: Scans for system weaknesses, offering thorough security assessments.
- Efficient Patch Management: Automatically manages and applies necessary patches to fix vulnerabilities.
- Configuration Evaluation: Checks system configurations to ensure they meet security standards.
- Software Vulnerability Analysis: Assesses installed software for vulnerabilities and suggests remediations.
- Proactive Zero-day Defense: Implements measures to mitigate risks from zero-day vulnerabilities.
Why do we recommend it?
ManageEngine Vulnerability Manager Plus is a package that detects security weaknesses and also provides automated methods to close them down. As well as a vulnerability scanner, this bundle has a patch manager and a configuration manager. The system also includes a compliance manager. The system also audits your security software.
The vulnerability scanner will run on a schedule but you can also launch it intermittently on demand. The tool will look for endpoint and server misconfigurations, OS versions, software exploits, and the presence of unauthorized software packages and utilities. The full list of capabilities of the tool increases with each higher edition offered for the package.
Vulnerability Manager Plus doesn’t just spot vulnerabilities, it fixes them. The offer of a free version is a nice touch. However, you get more utilities and more automated remediation with the higher plans. Choose the Enterprise plan if you need to protect multiple sites. This tool saves time and money by providing encoded security expertise so you don’t need to keep a cybersecurity analyst on the payroll.
Who is it recommended for?
This system is suitable for businesses of all sizes. It takes care of the detection and resolution of problems, giving you all of your surface monitoring needs in one bundle. ManageEngine offers a Free edition that can manage up to 25 endpoints. Larger businesses have LAN and WAN packages to choose from.
Pros:
- Automated Remediation: Scans are followed by immediate, automated correction of detected issues.
- Patch Management Efficiency: Ensures patches are verified and properly queued for deployment.
- Custom Security Policies: Allows the creation of security policies with automated actions for detected issues.
- Software Management Controls: Provides oversight on the software permitted on endpoints, enhancing security.
- Comprehensive Configuration Management: Offers detailed management of system configurations for optimal security.
Cons:
- Deployment Limitations: Available only for on-premises installation, lacking a cloud-based SaaS option.
Vulnerability Manager Plus is offered in three editions: Free, Professional, and Enterprise. The free version will monitor 25 computers. The Professional edition covers one site and the Enterprise edition is designed for WANs. You can appraise Vulnerability Manager Plus with a 30-day free trial.
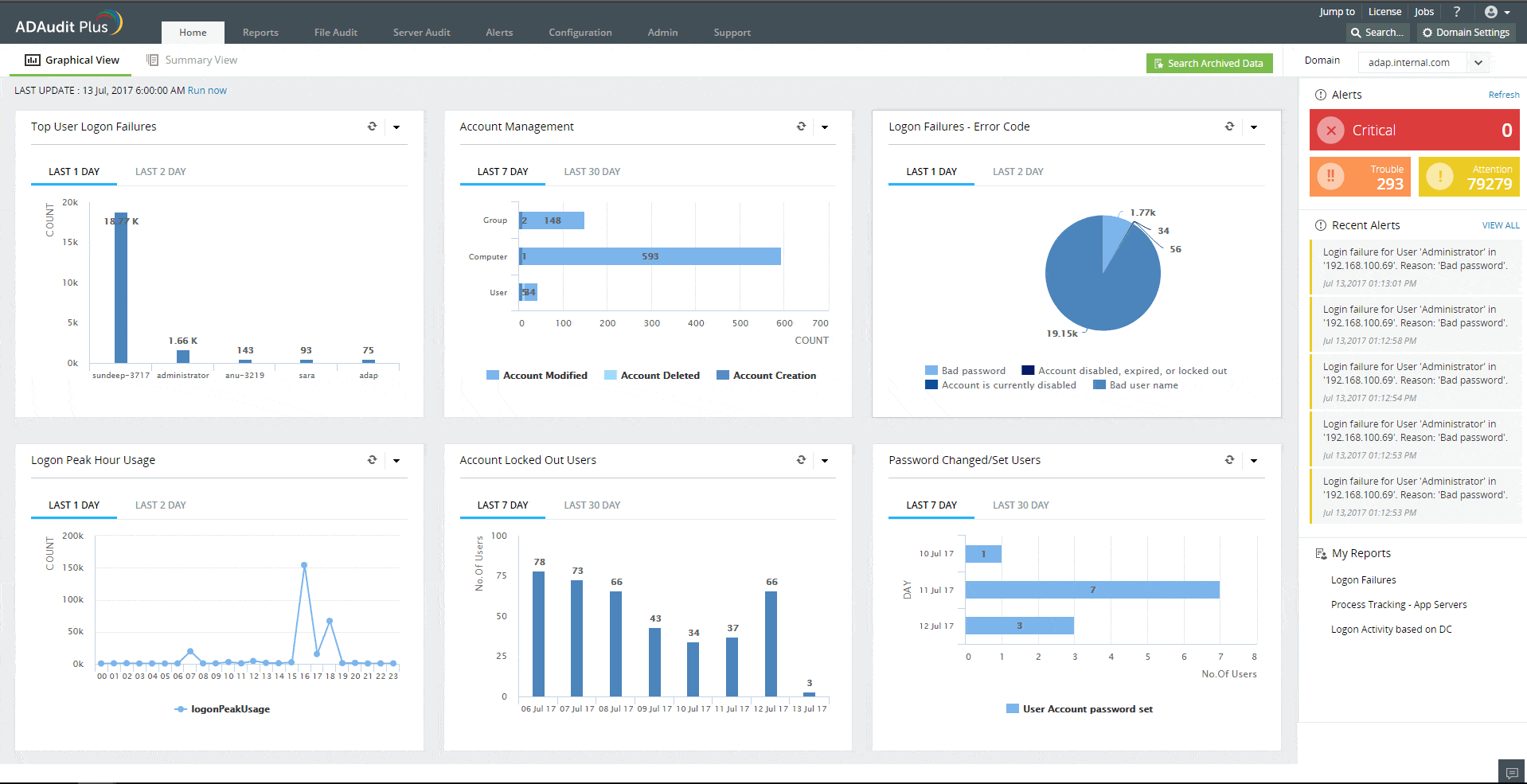
3. ManageEngine ADAudit Plus (FREE TRIAL)
ManageEngine ADAudit Plus is an excellent option for attack surface monitoring due to its comprehensive capabilities in identifying and mitigating potential threats. It monitors and analyzes vulnerabilities across your Active Directory, providing real-time alerts on over 25 types of AD attacks, including credential access and lateral movement attacks.
Key Features:
- Attack Surface Monitoring: Monitors and analyzes potential vulnerabilities across your Active Directory.
- Indicators of Compromise (IoC): Detects over 25 types of AD attacks, including Kerberoasting, Golden Ticket, and DCSync.
- Indicators of Exposure (IoE): Identifies vulnerabilities and potential security gaps in the network.
- Network and Process Attacks: Tracks and responds to network and process-based threats efficiently.
- User Behavior Analytics (UBA): Utilizes behavior analysis for risk assessment and detecting anomalies.
- Automated Incident Response: Provides swift automated responses to detected incidents to minimize damage.
- AD Backup and Recovery: Ensures robust backup and recovery solutions for Active Directory.
Why do we recommend it?
ADAudit Plus is recommended for its extensive threat detection capabilities and automated incident response features, which make it a robust solution for Active Directory security. Its user behavior analytics and comprehensive vulnerability analysis offer a proactive approach to mitigating potential risks.
The tool’s Indicators of Exposure (IoE) feature helps identify security gaps and vulnerabilities, allowing proactive measures to be taken before breaches occur. With its User Behavior Analytics (UBA), ADAudit Plus detects anomalous activities, providing an additional layer of security.
The automated incident response feature ensures swift action against detected threats, minimizing potential damage to proactively protect your attack surface. This combination of monitoring, detection, and response makes ADAudit Plus a solid solution for maintaining a secure attack surface.
Who is it recommended for?
ADAudit Plus is ideal for IT administrators and security professionals who need to monitor and protect their Active Directory environment. It’s especially useful for organizations looking to enhance their threat detection and response strategies.
Pros:
- Comprehensive Threat Detection: Effectively detects a wide range of AD attacks, enhancing security.
- Detailed Vulnerability Analysis: Identifies potential vulnerabilities through comprehensive exposure indicators.
- Behavioral Analysis: Uses user behavior analytics to detect unusual activities and potential threats.
- Automated Response: Automates incident responses, significantly reducing reaction times to threats.
- Robust AD Recovery: Provides reliable backup and recovery options for Active Directory.
Cons:
- Steep Learning Curve: May take time for users to fully understand and utilize all features.
Gain access to the 30-day free trial.
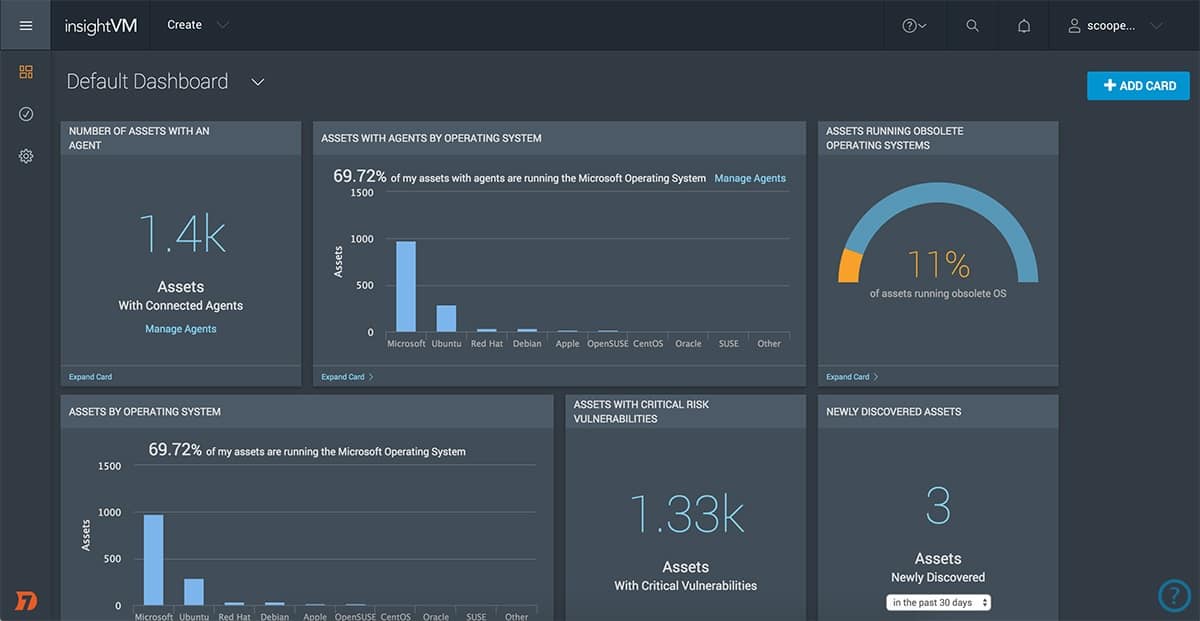
4. Rapid7 InsightVM
Rapid7 InsightVM is a vulnerability manager rather than an attack surface monitor. However, it has some beneficial features that make it a good tool for external attack surface management. This system scans cloud and virtual systems as well as the endpoints and devices on the network. The tool itself is cloud-based, so it isn’t bound to checking on just one network. It is equally suitable for checking on endpoints on remote sites and even in the homes of telecommuting staff.
Key Features:
- Cloud Deployment: Operates in the cloud, offering flexibility across various environments.
- Hybrid Environment Adaptability: Effectively scans both physical and virtual systems in mixed-use networks.
- Security Event Database: Includes a comprehensive database of data loss events for enhanced risk analysis.
- Thorough Vulnerability Scans: Identifies and assesses vulnerabilities across network devices and endpoints.
- Software Compliance Monitoring: Keeps track of software versions to ensure compliance and security.
Why do we recommend it?
Rapid7 InsightVM is a SaaS package. This vulnerability manager can scan endpoints on multiple sites in one account. This enables the centralization of system monitoring. The tool identifies assets with security weaknesses and generates a risk assessment report. This prioritizes issues to fix and supplies advice on steps to take.
Rapid7 has one other feature that can enhance the attack surface assessment capabilities of InsightVM. Project Sonar gathers data loss event notifications and additional information on security problems with different companies. This pool of data can be used to form a third-party risk assessment on the businesses that run services used by the client.
Rapid7 InsightVM with Project Sonar adds a third-party risk assessment system to a vulnerability scanner. While not being an exact match for an attack surface monitor, the high reputation of Rapid7 in the field of cybersecurity tools and the combination of all of the complementary tools that can be used alongside InsightVM make this a tempting proposition.
Who is it recommended for?
This package is suitable for mid-sized and large businesses. There is no free edition for small companies and the power of this SaaS platform lies in its ability to monitor multiple sites. Rapid7 provides other security tools on the same platform as InsightVM, which include the InsightIDR SIEM package.
Pros:
- Continuous Monitoring: Offers ongoing vulnerability scanning to maintain a secure external posture.
- External Threat Insights: Leverages an extensive attack database for comparative risk assessment.
- Renowned Origin: Evolved from the well-regarded Nexpose platform, ensuring a solid security foundation.
- Comprehensive System Coverage: Capable of assessing both cloud-based and virtualized environments.
- Integrated Patch Management: Features a patch management component to streamline vulnerability remediation.
Cons:
- No On-Premises Option: Lacks a self-hosted version, limiting deployment options for certain organizations.
InsightVM is part of a suite of tools that can protect a network from attack, and one of its services, a SIEM tool, includes a threat intelligence feed. This feed identifies any channels currently used by hackers to get into networks. This has software vulnerabilities, which provide an attack surface protection service. Rapid7 offers InsightVM on a 30-day free trial.
5. Bugcrowd Attack Surface Management
Bugcrowd Attack Surface Management is an exciting proposition. This is an automated tool developed by white hat hackers. It is a crawler that searches through linked software packages, and it is used as a pen-testing system to discover the software and services used by a client. This system particularly chains through to all of those APIs and microservices that provide plug-in services for Web page functions.
Key Features:
- Penetration Testing Automation: Utilizes an automated system designed by white-hat hackers for comprehensive security testing.
- Advanced Crawler Technology: Employs a sophisticated crawler to navigate through interconnected software ecosystems.
- Microservice & API Focus: Specifically targets microservices and APIs to uncover hidden vulnerabilities.
- Dependency Mapping: Charts the relationships between applications and their dependencies for clearer security insights.
Why do we recommend it?
Bugcrowd Attack Surface Management provides an asset discovery tool that assembles an inventory of both hardware and software. The software inventory forms the foundation for a vulnerability scanner. The company acts as an agency for independent white hat hackers and it gathers their reports on discovered exploits into this vulnerability management service.
Bugcrowd explains that a third of all attacks get into a business through software and services that the company’s IT department doesn’t even know that they are using. You can’t protect systems that you don’t see that you use. The system then watches over those newly-discovered assets and alerts the client if it detects any security risks on them.
Customers who want a tailored service can commission human-based searches of their system. This is an actual pen-testing exercise because Bugcrowd puts a bounty on your company’s systems and invites some of the leading whiter hat hackers worldwide to break in, awarding the prize to the first hacker in. This service is called Asset Risk.
Who is it recommended for?
This tool is a good choice for businesses of all sizes. The company doesn’t publish its price list, so small businesses will probably steer clear of this option lest they get stung with a large bill. The producers of Web applications will be particularly drawn to Bugcrowd Attack Surface Management.
Pros:
- Thorough Asset Discovery: Identifies and catalogs both hardware and software assets, laying the groundwork for effective vulnerability management.
- Dependency Visualization: Provides a clear mapping of application dependencies, aiding in the identification of potential security weaknesses.
- Proactive Weakness Detection: Continuously scans for vulnerabilities in software couplings, ensuring timely identification of security issues.
- Constant Vigilance: Offers ongoing assessment to monitor newly discovered assets for any emerging security threats.
Cons:
- Opaque Operations: Functions largely behind the scenes, which may leave users unclear about the specifics of its actions.
Bugcrowd Attack Surface Management is a cloud-based service, and you can request a demo to see it for yourself.
6. ReliaQuest GreyMatter Digital Risk
ReliaQuest GreyMatter Digital Risk Protection is an attack surface monitoring tool that checks a client’s software assets against circulated intel being shared by known hackers. This is a valuable service for keeping vigilant against external threats. Most threat intelligence feeds record attack strategies that have already been implemented against other companies. SearchLight alerts companies that they are about to be attacked.
Key Features:
- Innovative Attack Database: Leverages a comprehensive database of imminent hacker campaigns gathered from the Dark Web.
- Remote Operation Capability: Monitors digital assets remotely, offering protection without the need for onsite deployment.
- Hacker Technique Modeling: Utilizes advanced modeling to predict and counteract hacker strategies before they are implemented.
Why do we recommend it?
ReliaQuest GreyMatter Digital Risk Protection compiles a database of discovered attack plans, which it scrapes from the Dark Web. So, rather than scanning a client system for a list of hacker methods, such as the OWASP Top 10, it looks for vulnerabilities to attack campaigns that are about to happen.
You register your outward-facing assets on taking out this service, such as brands, product names, IP addresses, and domains. The SearchLight system then keeps a constant eye out for mentions of these names and addresses. An example of the kind of information that the service can pick up would be the contact details or even the system login credentials of an employee being circulated on the Dark Web.
SearchLight analysts, using crawler and data analysis tools, identify potential attacks on one of the clients that they protect. The type of data detected on a client indicates the direction that an attack will take. With this warning, SearchLight can inform the client of the upcoming episode and which parts of the system to harden in defense.
Who is it recommended for?
This service is an important protection system for any business but it is particularly important for very large, noticeable businesses that have well-known brands. Big companies have more assets that can be attacked and their large incomes make them bigger targets. A well-known brand is also very vulnerable to reputational damage.
Pros:
- Simplified Asset Registration: Allows for easy setup by entering brand, product, IP addresses, and domain information on a webpage.
- Proactive Campaign Tracking: Keeps tabs on current hacker campaigns, offering insights into potential threats.
- Dark Web Intelligence: Scans the Dark Web for mentions and threats related to your digital assets, providing timely alerts.
Cons:
- Limited Patch Scanning: Does not include scanning for software patches, which could leave some vulnerabilities unaddressed.
While not providing a total cybersecurity solution, this is a beneficial service that would be a valuable addition to any attack surface monitoring strategy. You can get a look at ReliaQuest GreyMatter Digital Risk Protection on a 7-day free trial.
7. CoalFire Attack Surface Management
CoalFire Attack Surface Management is on this list because the company understands that the significant risk to companies lies in those easy-to-integrate APIs and plug-ins that deliver instant functionality. However, when developing a website or Web service, no one stops to wonder precisely where those functions are run and whether or not their providers have any security in place.
Key Features:
- Web Component Identification: Pinpoints web components, including APIs and plug-ins, integral to site functionality.
- Hybrid Analysis Approach: Combines automated software with manual expert analysis for comprehensive coverage.
- API and Plugin Specialization: Specifically targets the security of third-party APIs and plug-ins to mitigate risks.
Why do we recommend it?
CoalFire Attack Surface Management is a managed security service. Not only does the package include all of the software and the servers that run it, but the bundle also provides technicians to manage the system. While the software runs continuously looking for vulnerabilities, the experts shut down all loopholes and construct a fightback strategy.
Once a website is up and running, it is tough to unpick and rewrite it. For one thing, such an exercise would be very costly and difficult to justify to the company accountant. CoalFire crawls through websites and lists all of the external services that they have integrated. While automated processes discover all of the chains of assets that contribute towards a client’s systems, human analysts verify these findings.
With the complete asset inventory in place, the business can develop a defense strategy. CoalFire doesn’t include a SIEM or an intrusion detection system. However, it gives you guidance on the correct defense software that you need for your digital profile.
Who is it recommended for?
This is a useful service for businesses that are located in places that have almost no available security talent to hire. It could also be a good proposition for small and mid-sized companies that can’t afford to set up a security operations center. The service can be tailored for compliance management.
Pros:
- Expert-Validated Alerts: Automated detection of vulnerabilities complemented by expert verification for accuracy.
- Third-Party API Insights: Delivers detailed assessments of potential security risks associated with third-party APIs.
- Precise Code Mapping: Accurately identifies the insertion points of external codes within your digital assets.
Cons:
- Premium Service Cost: The tailored nature of the service comes with a higher price tag, reflecting its specialized offering.
CoalFire assesses the risk of the connections between a company’s network and remote sites and remote workers along with the extended asset inventory. All of the different circumstances of a business’s operating procedures go into the CoalFire risk assessment, which constitutes a thorough attack surface definition.
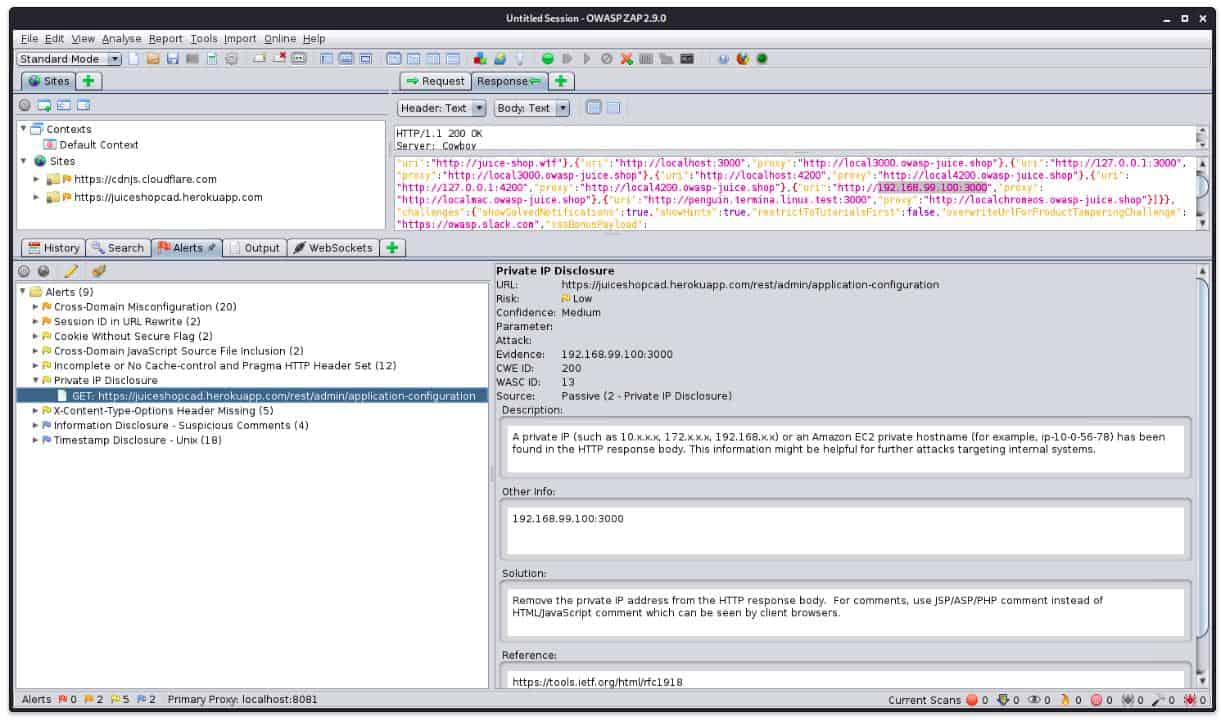
8. OWASP Zed Attack Proxy
OWASP Zed Attack Proxy is a free, open-source Web app scanner. The tool searches through a website for the OWASP Top 10 threats. This is an efficient vulnerability, and the Top 10 produced by this organization is the industry touchstone for all vulnerability scanners.
Key Features:
- Cost-Free Security Tool: Available without any fees, providing accessible web application security scanning.
- Industry-Standard Vulnerability Coverage: Targets the OWASP Top 10, ensuring scans meet high-security benchmarks.
Why do we recommend it?
The OWASP Zed Attack Proxy is completely free of charge. OWASP provides the definitive list of vulnerabilities for which to scan, which is the OWASP Top 10 and so using a vulnerability tester from the organization is a very attractive proposition. However, this is a pen-testing tool rather than a vulnerability scanner.
The second project of OWASP that can be plugged into the Zed Attack Proxy makes it an attack surface monitor. This is the Attack Surface Detector. This service can trace through APIs and Web services, making it a great discovery tool for attack surface analysis.
The Detector locates the hosts for discovered applications, and then it notes the parameters for the call and their data types. Another valuable feature of the Detector is that it will scan an app and store its code. The system can be used to regularly rescan those discovered functions and compare its code to the stored version, identifying changes that could introduce new vulnerabilities or even include new backend functions to trace through to.
Who is it recommended for?
This tool isn’t really a cost saver for small businesses because it isn’t an automated system that anyone can sign up for and set running. You need a security expert to run tests with this tool and interpret its results. So, this is a system for use by penetration testers.
Pros:
- Integrated Attack Surface Analysis: When paired with the Attack Surface Detector, it becomes a powerful tool for uncovering and monitoring web app vulnerabilities.
- Control Over Scanning: The on-premises deployment option puts you in complete command of the scanning process.
- Flexible Scanning Schedule: Offers the versatility to run scans either continuously or on a needs-based schedule.
Cons:
- Outdated User Interface: The graphical interface could use a refresh to improve user experience and efficiency.
OWASP Zed Attack Proxy and the OWASP Attack Surface Detector are available for installation on Windows, macOS, and Linux.
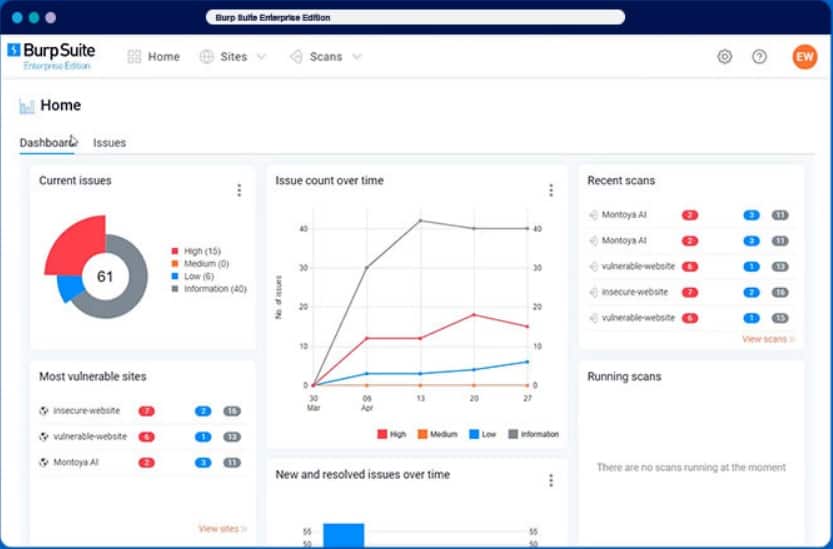
9. Burp Suite Enterprise Edition
Burp Suite is a package of penetration testing tools. The system is available in three editions. These are a Community Edition, which is free to use, a paid Burp Suite Professional package of tools, and Burp Suite Enterprise, an automated vulnerability scanner. Burp Suite Enterprise is designed for use by DevOps operations and software development companies.
Key Features:
- Renowned Penetration Testing Suite: Offers a comprehensive set of tools for thorough security testing and research.
- Multiple Editions for Different Needs: Available in a free Community Edition, a feature-rich Professional package, and an automated Enterprise version.
Why do we recommend it?
Burp Suite Enterprise Edition is a high-end vulnerability scanner. Burp Suite is available in three editions – all provide the same software package but users of the Community and Professional editions can’t access the automation features, which are disabled. The Enterprise edition is for a wider audience and is easier to use.
Burp Suite is presented here as an alternative to the OWASP Zed Attack Proxy. Both tools have excellent reputations, and both are ideal vulnerability scanners. Like the Zed Attack Proxy, Burp Suite Enterprise can be enhanced by the OWASP Attack Surface Detector for free. So, the benefits described above are also available for users of Burp Suite Enterprise.
Who is it recommended for?
Burp Suite Enterprise Edition can be run as a vulnerability scanner and it can also be set up as a continuous tester in a CI/CD pipeline. While the Community edition is aimed at independent penetration testers, the paid plans are suitable for corporate use. Web application providers should opt for the Enterprise edition.
Pros:
- Versatile Testing Options: From manual penetration testing tools to an automated scanner, it caters to a wide array of security testing needs.
- Compatibility with OWASP Tools: Supports integration with the free OWASP Attack Surface Detector for enhanced vulnerability assessment.
- Suitable for DevOps and CI/CD: Ideal for integration into development testing and continuous security monitoring pipelines.
Cons:
- Lacks Cloud-Based Offering: Does not provide a Software as a Service (SaaS) option, requiring on-premises deployment.
Burp Suite Enterprise is a sophisticated tool, and it is not free. The service is offered in three packages: Standard, Grow, and Accelerate, with from five to 50 scanning agents, depending on the plan. Burp Suite Enterprise installs on Windows, macOS, or Linux, available for a free trial.
10. ImmuniWeb Discovery
ImmuniWeb Discovery includes various security services that amount to both a vulnerability scanner and an attack surface monitor. This system discovers all software assets on-premises and through to cloud services. It can trace through APIs to find the hosts of the code. It also includes a vendor risk management service by tracking any disclosures or security events experienced by them.
Key Features:
- Comprehensive Hybrid Discovery: Identifies software assets across both on-premises and cloud environments.
- Dark Web Monitoring: Actively scans the Dark Web for mentions and threats related to corporate assets.
- Vendor Risk Analysis: Evaluates third-party vendors for potential security vulnerabilities and incidents.
Why do we recommend it?
ImmuniWeb Discovery is a cloud-based system that combines external vulnerability scanning with Dark Web intelligence. The tool identifies all of a company’s assets that are visible to hackers and spots well-known exploits. It also discovers mentions of corporate identities on hacker information exchanges.
The ImmuniWeb system also scans the Dark Web looking through regular hacker communication channels for credentials sales or intelligence gathering attempts that concern the assets of the service’s clients.
So, the ImmuniWeb service covers both internal weaknesses and external threats. It produces system-hardening recommendations and alerts businesses to the shortcomings in their code suppliers.
Who is it recommended for?
The ImmuniWeb system is easy to use, needs no installation, identifies and explains vulnerabilities, and reports on hacker plans. This package is suitable for any company but it is going to appeal more to large companies with a lot to lose. Small businesses can access free tools on the ImmuniWeb site.
Pros:
- Internal and External Insights: Provides a detailed view of both internal vulnerabilities and external threats, enhancing security posture.
- Flexible Scanning Options: Offers both scheduled scans for regular monitoring and on-demand assessments for immediate needs.
- Comprehensive Service Coverage: Tracks security from internal systems to external services, offering a full spectrum of risk management.
Cons:
- Cost Consideration for On-demand Scans: Charges per transaction for on-demand scans could become costly for frequent use.
The ImmuniWeb service is offered in three levels: Express Pro, Corporate, and Corporate Pro. These systems are provided on a monthly subscription, with Corporate Pro being the complete feature package at the highest price. The Corporate Pro system is also available for on-demand scans of third-party systems, which h are charged per assessment. ImmuniWeb Discovery is delivered from the cloud, and you can get a demo of the system.
11. CyCognito Attack Surface Management
CyCognito offers a cloud platform of security tools that include a vulnerability manager and the Attack Surface Manager.
Key Features:
- Comprehensive Vulnerability Scanning: Offers a detailed vulnerability scanner for thorough security assessments.
- External Attack Surface Evaluation: Specializes in assessing external attack surfaces to identify public-facing IT vulnerabilities.
- Vendor Risk Analysis: Includes tools for evaluating the security risks associated with third-party vendors.
Why do we recommend it?
CyCognito Attack Surface Management is an external vulnerability scanner. This tool operates continuously from its cloud platform. The company also offers a plan that also includes internal asset scanning alongside the external vulnerability management system. The platform also offers threat intelligence and continuous testing.
The CyCognito system is an external attack surface monitor. It identifies your public-facing IT assets, principally websites and Web services. The service traces from those initial assets through to the APIs and services that contribute to them. This is a valuable tool in itself because it lets you know exactly what code is contributing to your websites and what companies are behind them.
The system includes third-party risk assessment and an attack surface monitor that operates as an automated vulnerability scanner. The CyCognito system constantly attempts hacks on each point in the chain of services that contribute to your websites, probing them for weaknesses, which can change over time. It ranks each unit’s risk and prioritizes recommendations for hardening the most vulnerable systems that it discovers.
Who is it recommended for?
The CyCognito platform offers a range of modules, each of which appeals to a slightly different audience. The Attack Surface Management package with both internal and external scanning is suitable for use by any business. However, it will appeal more to mid-sized and large businesses.
Pros:
- In-Depth Asset Discovery: Traces connections from external assets to underlying modules, revealing the full extent of the attack surface.
- Vulnerability Prioritization: Analyzes and ranks vulnerabilities to help focus on the most critical issues first.
- Recommendations for Strengthening: Provides actionable insights for hardening systems against potential threats.
Cons:
- Lacks On-Premises Deployment: Exclusively cloud-based, offering no option for self-hosted implementation.
The CyCognito service includes automated processes supported by expert security analysts. You can request a demo of the Attack Surface Management system.
Attack Surface Monitoring FAQs
What is an attack surface management?
Attack surface management examines your systems from the perspective of an outside. Could a remote miscreant break into your system? How would that be done? Where are the weak links in your external digital edifice? An attack surface manager first identifies all of your digital assets that can be reached without insider privileges and maps all discoverable dependencies. It then looks for ways in and will also keep an ear to the ground to detect whether a hacker group is currently on the hunt for a specific type of system or organization.
How is attack surface measured?
An attack surface is the external digital profile of a business – anything that can be accessed without authorization. There is no benchmark for the success of an attack surface manager and no definitive list of weaknesses to look out for. However, any weak points should be logged and ranked for severity.
What is attack surface analysis?
Attack surface analysis requires the application of assessments with projections for possible weaknesses rather than a checklist of known vulnerabilities. For example, a module might be secure, but that strength might be compromised when combined with specific actions or associated data exchanging facilities. Attack surface analysis requires heuristics, which can best be applied through a combination of automated and human assessments.