Penetration testers are white hat hackers who try any means possible to break into a system. Although hacking is manual labor, it requires specialist utilities to explore and document a target system. The information gathered by those scanners provides input for an attack.
Here is our list of the best penetration testing tools:
- Intruder (FREE TRIAL) A cloud-based automated scanner that can be set to run continuously or launched on demand for penetration testing investigations. Start a 30-day free trial.
- Metasploit An open-source penetration testing framework available in free and paid versions and offers a range of attack strategies. Available for Windows, Windows Server, macOS, RHEL, and Ubuntu.
- Wireshark A highly respected packet sniffer that can capture track on LANs and wireless networks. Available for Windows, Linux, Unix, and macOS.
- Burp Suite A system tests Web applications by capturing and injecting packets between a browser and a Web server. Available for Windows, macOS, and Linux.
- Aircrack-ng A competent packet sniffer for wireless networks that includes some password cracking support. It runs on Linux.
- Autopsy and The Sleuth Kit, Sleuth Kit, is a forensic investigation utility that explores hard disks and can recover deleted content. Autopsy is a GUI front end for the tool. Available for Windows, macOS, and Linux.
- Sqlmap A command-line system can perform a range of attacks on database-supported applications, such as Web pages, and includes password cracking features. Available for Windows, macOS, and Linux.
- Zenmap A GUI version of the widely used Nmap, which is also called Network Mapper. This is a free utility that is available for Windows, Linux, BSD Unix, and macOS.
- Ettercap A traffic capture tool that implements a range of man-in-the-middle attacks. Available for Linux, Unix, Mac OS X, and Windows 7 and 8.
Where there are tools that save time, a hacker will use them because much of the success experienced by hackers is the result of dogged determination. For example, consider brute force attacks. With this strategy, you try every possible combination of username and password to guess the credentials for a user account. Even with relatively shortlists of possible values for each variable, permutations can quickly reach the thousands. But, of course, you wouldn’t want to have to type all of those in, so an automated tool for credentials cracking is necessary for any hacker’s toolkit.
A great benefit of following in the footsteps of cybercriminals is that they don’t like to pay for anything, so many of the tools they use are free. Many excellent paid tools have a free version and, it is probably the edition that costs nothing that attracts the hackers. However, if you consider buying the higher edition, you could steal a march on any hacker that might one day attack your system.
Fully automated testing
When looking for automated penetration testing tools, you wouldn’t be in the market for a fully automatic system tester – that’s a vulnerability scanner. The difference between a vulnerability scanner and penetration testing is that a vulnerability will work through a list of known system weaknesses and check on the status of each. Still, a penetration tester is a human, performing a series of probes manually. Eventually, the hacker will work through all of the exact system searches that the vulnerability manager uses.
Automated penetration testing tools don’t automate the entire test plan. Instead, they just provide fast programmatic services that save a great deal of time in each research exercise.
The best Automated Penetration Testing tools
In the search for automated penetration testing tools, you need to focus on the types of tools that cut out many repetitive tasks. There are many valuable services available and, as has already been explained, many of them are free. However, hackers are not too fussy about user-friendly interfaces, so the most frequently-used hacker tools tend to be command-line utilities.
Our methodology for selecting automated penetration testing tools
We reviewed the market for automated pen-testing systems and analyzed tools based on the following criteria:
- A tool that cuts out a lot of data entry and repetitive runs of commands
- A specialist service that can quickly attack one aspect of system security
- A utility that can perform both the research and launch an attack without the need to transpose data
- A system that can record all activities for assessment
- Tools that offer several attack strategies
- A free tool or a free trial or demo for a paid tool
- A free tool that is worth using or a paid tool that is worth the price
With these selection criteria in mind, we produced various options to suit businesses of all sizes.
1. Intruder (FREE TRIAL)
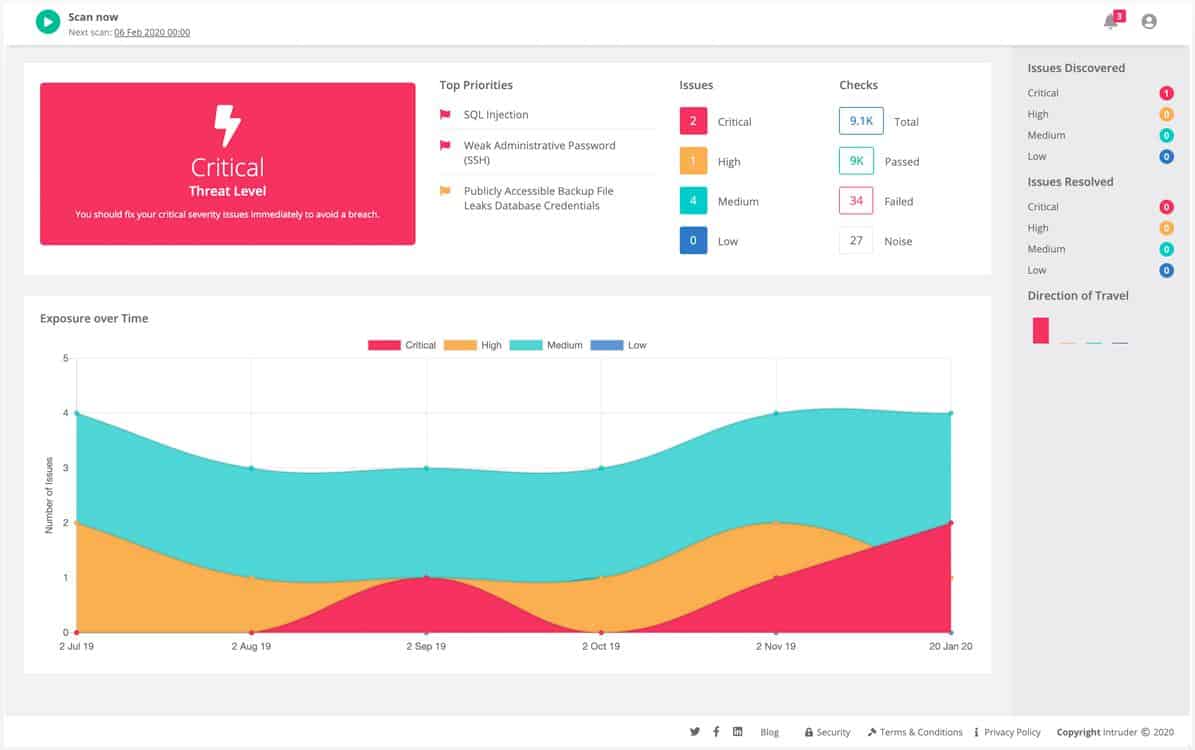
Intruder is a vulnerability scanner, which is an automated penetration testing service. The system is delivered from the cloud and it can be set to run continuously for testing development or for operations security monitoring. The service can also be launched on demand. The system performs both internal and external checks and has a battery of more than 11,000 tests.
Key Features:
- CI/CD Pipeline Integration: Seamlessly integrates with continuous integration and continuous delivery pipelines for automated security testing.
- SaaS Package: Delivered as a Software-as-a-Service, requiring no manual updates or maintenance.
- Regularly Updated: Continuously updated to include the latest vulnerability checks and security measures.
- Identifies Required Patches: Automatically detects and highlights required patches for security vulnerabilities.
Why do we recommend it?
The Intruder.io platform provides three levels of service that appeal to a broad range of businesses and budgets. The common element for all plans is the external vulnerability scanner. The frequency with which those scans occur depends on the plan you choose. Higher plans also include internal scanning.
The vulnerability scans need to be repeated frequently because changes to components in your system or additions, represent extra potential security vulnerabilities both individually and in combination with existing systems. New hacker strategies emerge all of the time and so systems that were validated as secure can suddenly be revealed as vulnerable.
The benefit of a hosted system is that the user doesn’t have to keep updating the software. The SaaS package includes all of the services of a maintenance technician team, leaving customers of the system to just use the software.
Who is it recommended for?
All businesses should consider using a vulnerability scanner and the threw plans of Intruder.io make it suitable for any size and type of business. The tool doesn’t require expertise to run because this is an automated system. However, the ad hoc scanner can be used as a penetration testing tool.
Pros:
- Continuous and On-Demand Scanning: Offers both ongoing and ad-hoc scanning options to suit different needs.
- Extensive Vulnerability Checks: Runs over 11,000 tests to ensure comprehensive vulnerability detection.
- Versatile Use: Suitable for both development testing and operational security monitoring.
- User-Friendly Results: Provides color-coded results for easy interpretation and prioritization.
Cons:
- Limited Penetration Testing Features: Primarily a vulnerability scanner, offering fewer features typical of penetration testing tools.
Pricing is based on the number of targets that need to be scanned and each target gets the same level of scrutiny. That means that the system is affordable and scaleable. You can experience the system with a 30-day free trial.
EDITOR'S CHOICE
Intruder is our top choice for a vulnerability scanner because it offers a comprehensive, automated penetration testing service delivered from the cloud. This versatile tool can be configured for continuous testing during development or for operational security monitoring, as well as on-demand scanning.
Intruder performs both internal and external checks, running over 11,000 tests to identify vulnerabilities. I personally enjoy how it seamlessly integrates with CI/CD pipelines, ensuring security is embedded in the development process. As a SaaS package, Intruder is regularly updated, providing the latest in security measures without the need for manual maintenance.
This platform is particularly recommended due to its flexibility, catering to businesses of all sizes and budgets with three different service levels. The ease of use and automated nature of Intruder make it accessible to users without deep security expertise while still offering powerful scanning capabilities.
Download: Download 30-Day Free Trial
Official Site: https://www.intruder.io/
OS: Cloud-Based
2. Metasploit
Metasploit is available in free and paid versions. This package creates a platform that allows you to research attacks and then launch them. Hackers widely use it. The free version is called Metasploit Framework, and the paid version is called Metasploit Pro. Although Metasploit is an open-source project, the cybersecurity company, Rapid7 supports the development of the systems, supplying funds and facilities to the team. In return, Rapid7 gets the right to produce its version that has more features plus professional support.
Key Features:
- Both Automated and Manual: Offers both automated tools and manual methods for penetration testing.
- Vulnerability Research: Provides extensive resources for researching vulnerabilities and exploits.
- Attack Implementation: Allows the execution of various attacks to test system security.
Why do we recommend it?
Metasploit is one of the core penetration testing tools that you will learn how to use on any penetration testing course. The two versions of the package address different audiences because while Metasploit Framework is free to use, Metasploit Pro is a paid product and is expensive.
Both systems can detect more than 1,500 exploits to use in attacks. The Pro version is aimed at businesses, but the Framework edition lends itself to manual attacks. Although the Pro edition leans more towards being a vulnerability scanner, it does have a few valuable automated services that the users of the Framework version could do with, such as an automated brute force password cracking tool.
Metasploit offers free and paid versions with enough attack strategies to test any system’s security thoroughly. The tool lets you gather intelligence about your system and spot exploits. It then assists in tricks such as password cracking to help you break in and act like a hacker.
Who is it recommended for?
Metasploit Framework is undoubtedly for use by penetration testers. As they attempt to model the mindset of hackers, penetration testers tend to use free tools, which is what makes Metasploit Framework so popular. The Metasploit Pro package has a very different corporate user group. Metasploit Framework is much more widely used than Metasploit Pro.
Pros:
- Free and Paid Versions: Offers both a free Metasploit Framework and a paid Metasploit Pro, catering to different user needs and budgets.
- Professional Support: Metasploit Pro comes with professional support from Rapid7, enhancing usability for businesses.
- Extensive Exploit Database: Detects and uses over 1,500 exploits for thorough security testing.
- Integrated Tools: Combines investigation tools with attack execution for a comprehensive penetration testing experience.
- Automated Services: Includes automated tools like brute force password cracking in the Pro version.
Cons:
- Incomplete Toolsets: Each version has valuable tools, but neither includes the full range of features available in the other.
- Costly Pro Version: The Pro edition is expensive, potentially limiting its accessibility for smaller businesses or individual users.
You can download the Metasploit Framework for free onto Windows, macOS, and Linux. Then, get a 14-day free trial of Metasploit Pro to check out the extra features. Also, check out a companion tool called Armitage. This sits in front of Metasploit Framework and helps you to gather intel and plan attacks.
Operating system: Windows, Windows Server, macOS, RHEL, and Ubuntu
3. Wireshark
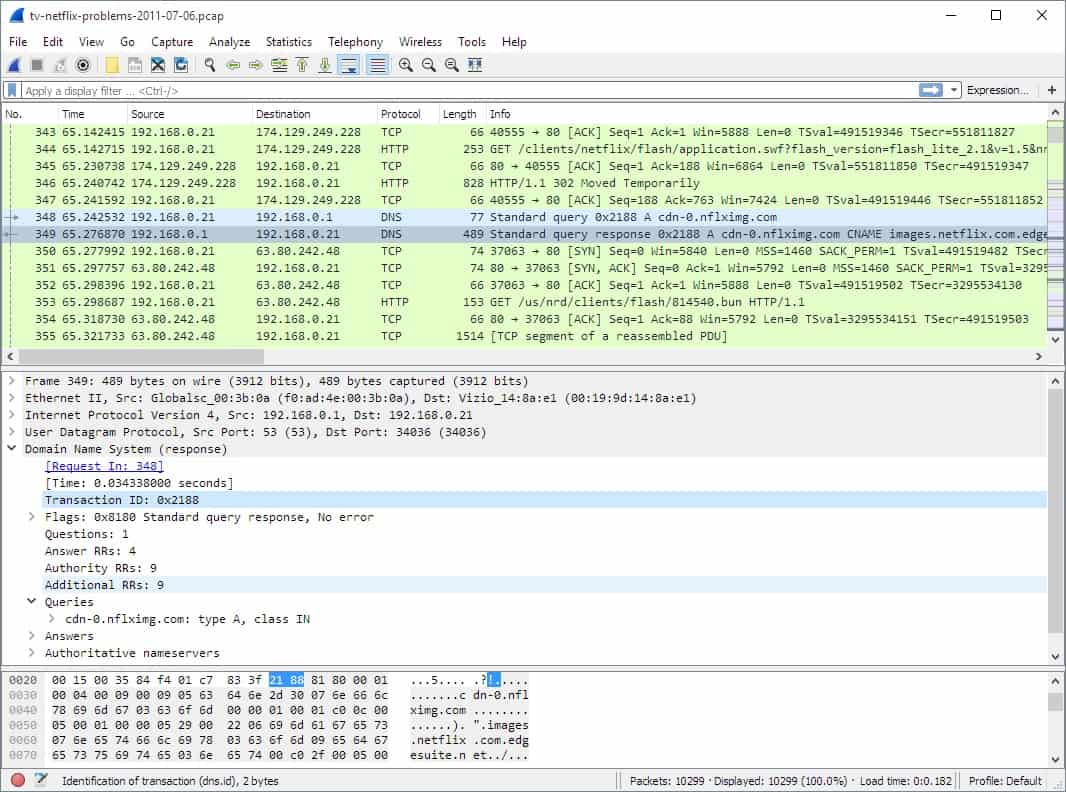
Wireshark is a packet sniffer. It lets you capture traffic and examine packet headers for intel. If you catch some unencrypted payloads, you can even get lucky and steal some passwords. Wireshark is an essential part of any hacker’s toolkit, and, unlike most hacker tools, it has a very pleasing GUI interface. The installer will also leave you with a command-line version called TShark.
Key Features:
- Capture Filters: Allows you to set filters to capture only specific types of network traffic.
- Color-Coded Packet Display: Utilizes color codes to highlight different types of packets for easier analysis.
- Follow Conversations: Enables you to track entire communication sessions between network devices.
Why do we recommend it?
Wireshark is the leading packet analyzer. The system uses the libpcap/WinPcap system to collect packets and then displays them in the Wireshark console. Packet capture can generate very large files very quickly but the Wireshark system lets you apply capture filters that will reduce that problem.
The capabilities of Wireshark extend to wireless networks, such as WiFi and Bluetooth. Use Wireshark to collect packets and then sort and filter them in the packet viewer. Then, scour for information that you can use in attacks.
Wireshark is available for Windows, Linux, Unix, and macOS.
Who is it recommended for?
All penetration testers are taught how to use Wireshark. The tool is free to use and unbeatable in the packet analysis field because of its built-in filtering and query language. That language is very extensive and takes a long time to learn, so this is not a tool for occasional usage.
Pros:
- Research Tool: Excellent for detailed network traffic analysis and research.
- Versatile Capture: Can capture traffic from both wired LANs and wireless networks like WiFi and Bluetooth.
- Export Capability: Allows captured traffic to be exported to files for later analysis.
- Cross-Platform: Available for Windows, Linux, Unix, and macOS, making it widely accessible.
Cons:
- No Integrated Attack Tools: Lacks built-in tools for executing attacks, focusing solely on packet analysis.
- Complexity: Requires extensive knowledge of its filtering and query language, which can be time-consuming to learn.
4. Burp Suite
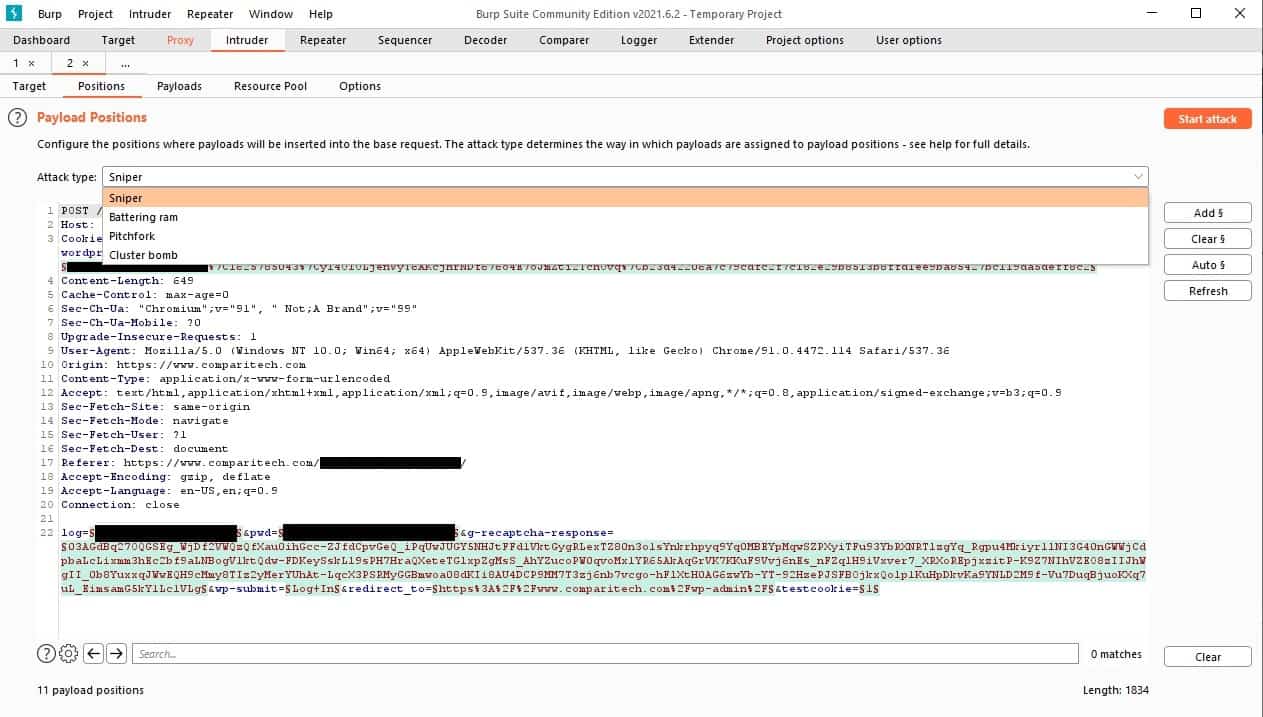
Burp Suite, from PortSwigger, is a paid tool but is also available for free in the form of a Community Edition. The paid version is called the Professional Edition. There is a lot of process automation in Burp Suite Community Edition and more in the Professional Edition. That paid tool has vulnerability scanning sections in it, which you can see in the Community Edition, but you can’t use it. The entire Home screen of the Burp Suite interface is inoperative for those who don’t pay.
Key Features:
- Runs on Windows, macOS, and Linux: Compatible with major operating systems for flexibility.
- ARP Poisoning: Supports ARP poisoning for intercepting network traffic.
- Proxy Format: Functions as a proxy, allowing for interception and modification of web traffic.
Why do we recommend it?
Burp Suite is very similar to Metaspolit only not quite as extensively used. You will learn about the free version of this tool on a penetration testing tool and you might encounter the paid version if you go to work for a cybersecurity consultancy. The paid version is more of a vulnerability scanner.
The lack of those highly automated systems means that you keep away from the temptation of using a vulnerability scanner. Instead, there is a third edition, called Enterprise, which is a full-on vulnerability scanner.
The great thing about the Burp Suite system is that the interface ties together your tests’ research and attack phases. Use the Intercept service to gather information and get that automatically available in the Intruder screen to set up attacks.
Who is it recommended for?
Like Metasploit, it is the free version, called the Community Edition, that most penetration testers use. The paid versions are very expensive and provide vulnerability scanning services rather than penetration testing tools. Every penetration tester will have already used Burp Suite and will have the free system installed.
Pros:
- Consistent Interface: Both free and paid versions use the same user-friendly GUI, making it easy to upgrade.
- Integrated Tools: Research tools seamlessly integrate with attack tools, streamlining the penetration testing process.
- Effective Password Cracker: Includes robust password cracking capabilities.
- Versatile: Suitable for both manual penetration testing and automated vulnerability scanning with the Professional and Enterprise editions.
Cons:
- Costly Paid Versions: The Professional and Enterprise editions are expensive, which may be prohibitive for some users.
- Vulnerability Scanner Focus: The paid editions emphasize vulnerability scanning, which may detract from hands-on penetration testing.
Burp Suite is built for Windows, macOS, and Linux. Download the Community edition for free or request a free trial of the Professional edition.
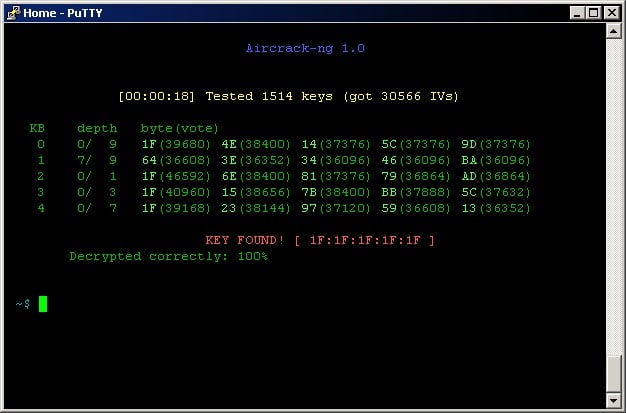
5. Aircrack-ng
Aircrack-ng gathers intelligence on wireless networks and provides the ability to capture packets in transit. This tool lets you see different channels currently in use and all wireless access points within range.
Key Features:
- Wireless Scanner: Scans and identifies all wireless access points and channels within range.
- Password Cracker: Capable of cracking WEP, WPA1, and WPA2 passwords.
- Can Replay Traffic: Allows for the injection and replay of captured traffic on the network.
Why do we recommend it?
Aircrack-ng is a wireless network scanner. The unusual feature of this tool is that it can insert traffic back onto the wireless network, not just capture packets. The password cracker can operate on WEP, WPA1, and WPA2 systems, The interface for this tool is a little basic but it has no rival.
The service shows the name of each AP and presents tools that could help you run attacks. The type of attacks that you can implement with this command-line tool includes deauth injection, man-in-the-middle attacks, and replay capacity overload attacks. It also has some password-cracking abilities.
Aircrack-ng is free to use, and it installs on Linux.
Who is it recommended for?
If you want to perform penetration testing on wireless networks, there really isn’t any alternative to Aircrack-ng. The tool pretty much has that market all to itself. The system isn’t very user-friendly, but once you have mastered its command language, the tool can be very powerful. Specialists in wireless security will use this tool a lot.
Pros:
- Hacker Tool: Frequently used by hackers, making it a valuable tool for penetration testers to understand potential threats.
- Fake WiFi Hotspots: Useful for setting up fake WiFi hotspots to test security.
- Network Access: Can potentially grant access to an entire network through its wireless segment.
- Powerful Command-Line Tool: Despite its basic interface, it offers robust functionalities for wireless network penetration testing.
Cons:
- No GUI: Lacks a graphical user interface, making it less user-friendly and requiring command-line proficiency.
- Linux Only: Only available for Linux, limiting its use on other operating systems.
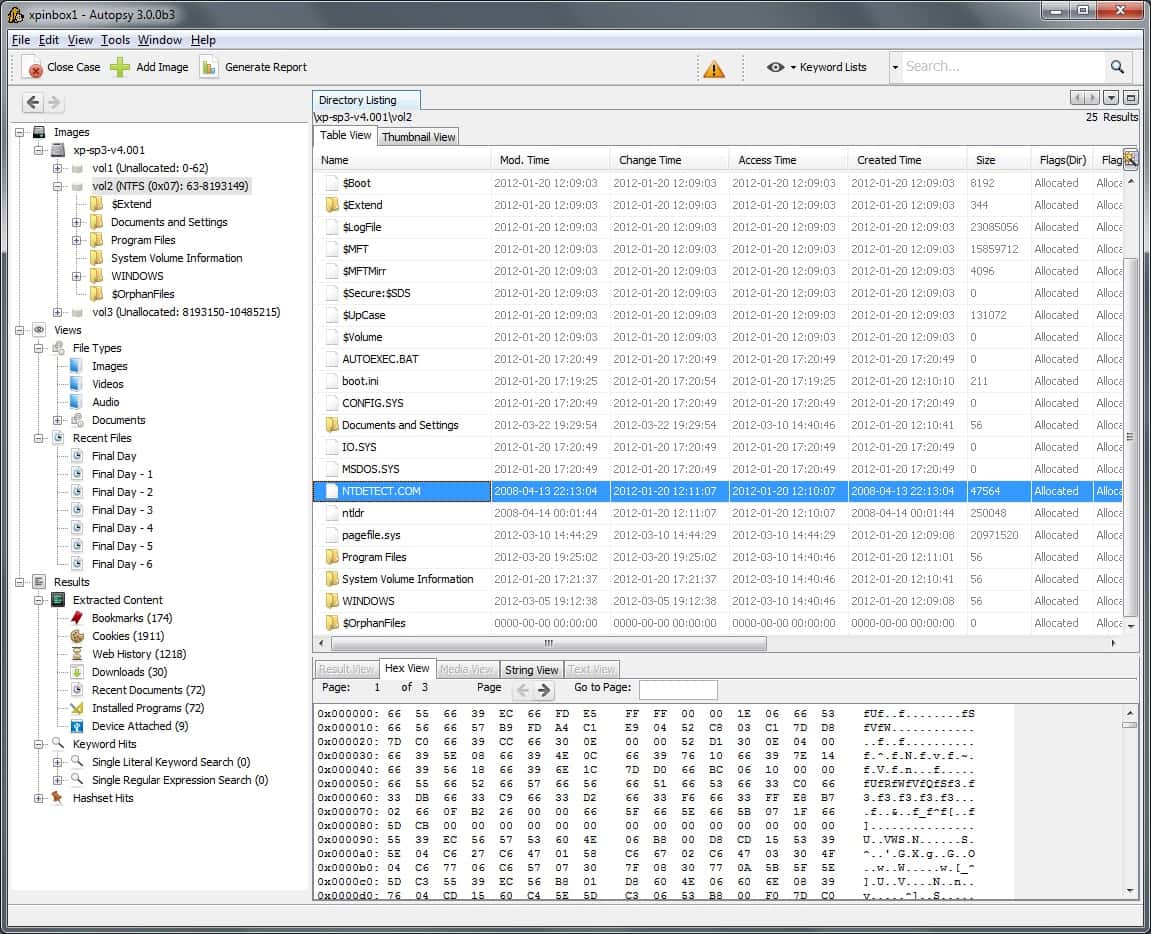
6. Autopsy and The Sleuth Kit
The Sleuth Kit is a helpful tool for searching hard disks for deleted data. It is also able to recover files from a damaged disk. The system will also give you a complete copy of a disk for later examination so that this tool can be used for data exfiltration. Another helpful task you can perform with The Sleuth Kit is extracting deleted images from phone memory cards. This is a very effective system, and it is used by law enforcement agencies and data thieves, and spies.
Key Features:
- Forensics Tool: Designed for digital forensics, allowing for detailed disk and memory card analysis.
- Bit-Level Data Viewer: Provides the ability to view and recover bit-level data, including deleted or damaged files.
- Free to Use: Both tools are available for free, making them accessible to a wide range of users.
Why do we recommend it?
Autopsy and The Sleuth Kit are digital forensics tools, which makes them a little bit different from all of the other tools on this list. This is a free tool and it implements examinations of disks and memory cards to view bit-level data and discover features such as deleted files or even broken files on corrupted disks for recovery.
The system is a command-line tool, and so you would probably want to install Autopsy, which provides a graphical front end to The Sleuth Kit. Both of these tools are free to use; law enforcement agencies and data thieves use them, and both are available for Windows, macOS, and Linux.
Who is it recommended for?
Autopsy and The Sleuth Kit are the same tool except that The Sleuth Kit is a command line system and Autopsy provides a GUI front end. Both services are free to use. Rather than being used by penetration testers, the main audience for these tools are law enforcement and security agencies.
Pros:
- Widely Used: Trusted by law enforcement agencies, spies, and data thieves for its effectiveness in uncovering hidden data.
- Data Recovery: Capable of recovering deleted files and extracting data from damaged disks.
- Comprehensive Disk Copy: Allows for creating complete disk copies for thorough examination and analysis.
- Cross-Platform: Available for Windows, macOS, and Linux, offering broad compatibility.
Cons:
- Initial Access Required: Requires initial access to the target computer, which can be a significant hurdle.
- Command-Line Complexity: The Sleuth Kit is command-line based, which can be complex; however, Autopsy provides a more user-friendly GUI.
- Forensics Focus: More geared towards digital forensics than typical penetration testing tasks.
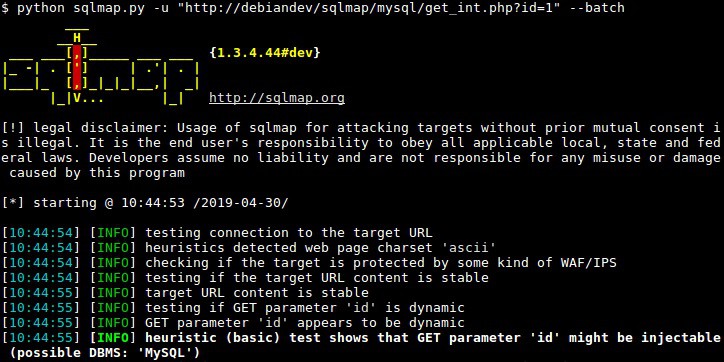
7. Sqlmap
Sqlmap is a command-line utility that focuses on extracting information from databases and also attacking them. Although this seems like a niche tool, there are an awful lot of systems that rely on a backend database, including just about every function on a website. Sqlmap also includes brute force username guessing and password cracking utilities.
Key Features:
- Database Probes: Extracts and explores data from backend databases.
- Discovers Well-Known Usernames: Identifies commonly used usernames to facilitate further attacks.
- Test Automation: Automates various SQL injection techniques and database takeover strategies.
Why do we recommend it?
Sqlmap is a powerful tool that is implemented as one command. You might think that this is a quick little tool that you might use once in a while. However, all of the options for the tool make it an extensive penetration testing and hacking system that can reveal account names and passwords and even expose admin accounts.
The sqlmap service focuses on documenting and breaking into web servers to get at their databases and contents. A typical research run will try several different exploits in sequence. If you launch one of the many attack strategies built into the sqlmap system, it will conduct related research first and feed the results into the attack.
One problem with this otherwise excellent utility is that it isn’t possible to use its commands in a program and pass data from one command to another. Sqlmap installs on Windows, macOS, and Linux.
Who is it recommended for?
This is a free tool and it is very useful for reconnaissance. You can easily build up a list of accounts and then get passwords with this system. So, Sqlmap is useful for hackers as well as for penetration testers. You can learn more about this system by reading the Sqlmap Cheat Sheet.
Pros:
- Extensive Attack Library: Offers a wide range of SQL injection and database attack methods.
- Detailed Database Exploration: Capable of thoroughly documenting and investigating database contents.
- Password Cracking: Includes utilities for brute force username guessing and password cracking.
- Cross-Platform: Available for Windows, macOS, and Linux, making it versatile for different operating systems.
- Free to Use: No cost for usage, making it accessible for both hackers and penetration testers.
Cons:
- No Graphical Interface: Operates entirely through command-line, which can be less user-friendly.
- Limited Programmability: Lacks the ability to use commands in a programmatic way and pass data between commands.
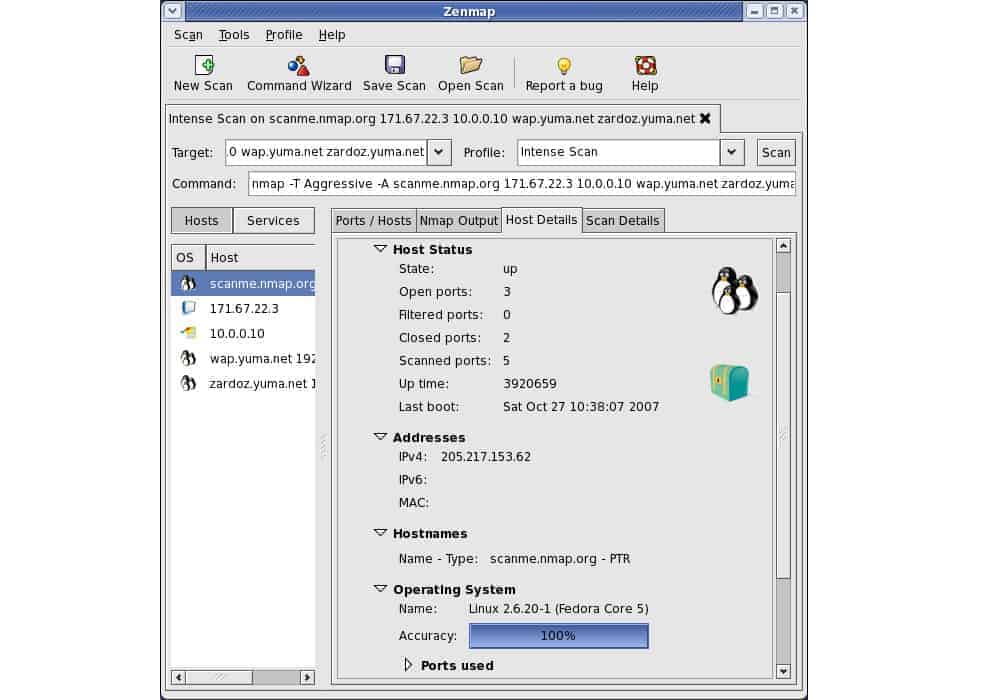
8. Zenmap
Zenmap is a graphical version of Nmap. When you install Zenmap, you also get Nmap to either use the graphical interface or dive to the command line. Having both options offers more flexibility. The pair will capture packets and display their headers and payload. The Zenmap display then interprets that information into an entire network discovery system.
Key Features:
- Creates a Network Map: Visualizes the network, showing connected devices and their relationships.
- Research Tool: Gathers detailed information about each device and interface on the network.
- Based on Nmap: Combines the graphical interface of Zenmap with the powerful command-line capabilities of Nmap.
Why do we recommend it?
Zenmap and its command line component Nmap are very widely used by penetration testers and hackers. On one level, this tool can give you an actual map of a network. However, the tool can provide much deeper information about each device on a network and each interface on each device.
The underlying Nmap is also called Network Mapper. This shows why you would use this tool as part of your hacking toolkit in a penetration testing exercise. The system can document an entire network, providing helpful information on the hostnames and addresses of connected devices. However, you need to break into an endpoint on the network before this tool is of use.
Zenmap and Nmap are helpful for research rather than for launching attacks. Both tools are free, and both will run on Windows, Linux, BSD Unix, and macOS.
Who is it recommended for?
The use of Nmap is included in every penetration testing course, so if you are a trained penetration tester, you are probably already using that command line system. Zenmap will appeal to occasional users because it is a little easier to use, thanks to its GUI front end.
Pros:
- Comprehensive Network Mapping: Quickly and accurately maps out the entire network, providing detailed information about each endpoint.
- User-Friendly Interface: The GUI front end of Zenmap makes it easier for occasional users compared to the command-line Nmap.
- Versatile Tool: Useful for both research and documentation of networks, widely used by penetration testers and hackers.
- Cross-Platform: Available for Windows, Linux, BSD Unix, and macOS, offering broad compatibility.
- Free to Use: No cost for using either Zenmap or Nmap, making it accessible to everyone.
Cons:
- Internal Use Only: Requires access to the internal network to be effective, limiting its use for external reconnaissance.
- Non-Attack Tool: Primarily designed for research and documentation, not for launching attacks.
9. Ettercap
Ettercap is a packet capture tool that can inject traffic and masquerade as servers by faking SSL credentials. This is a command-line utility that has an extensive library of commands. Ettercap has a rudimentary interface. This is not a graphical interface, just a replacement for the Terminal window, so you would probably just end up using it at the command line.
Key Features:
- DDoS Attack: Facilitates distributed denial-of-service attacks to overwhelm and disrupt network services.
- DNS Spoofing: Intercepts and alters DNS requests to redirect traffic to malicious sites.
- ARP Poisoning: Manipulates ARP tables to redirect network traffic to the attacker’s machine.
Why do we recommend it?
Ettercap is probably a second-tier penetration testing tool and not as widely used as Burp Suite, Metasploit, and Nmap. However, for those that master this package, it is a “must have” tool. The system sets up a proxy to intercept traffic and then gives the user a range of tools to manipulate packets and transmit them.
The system works by ARP poisoning and can divert traffic from a server to the pen tester’s workstation. This allows you to then track all endpoints into disclosing important information. It is possible to use Ettercap to reap usernames and passwords in a network.
This tool needs to be inside the target network because its attack strategies all rely on manipulating traffic management systems, such as ARP and the domain name service. One option for its use would be to breach the system through an open RDP port and then transfer Ettercap onto it for remote execution.
Other attack strategies that are possible with Ettercap are DNS spoofing and Denial of Service. The tool itself would need to be supplemented by some other traffic generator if you wanted to use it to overwhelm a Web server completely. It could be possible to form a reflection attack with the Ettercap tool.
Ettercap is free to use, and it will run on Linux, Unix, Mac OS X, and Windows 7 and 8. Unfortunately, it will not work on macOS or Windows 10.
Who is it recommended for?
This is a free tool and is much loved by many penetration testers and hackers. The interface for the system is a little clunky. However, that can be said about many of the pen tester favorites. As with most penetration testing tools, you need to use it a lot to fully master its capabilities.
Pros:
- Variety of Attack Methods: Supports multiple attack strategies, including ARP poisoning, DNS spoofing, and DDoS attacks.
- Effective Man-in-the-Middle Tool: Excellent for executing man-in-the-middle attacks, allowing interception and manipulation of network traffic.
- Free to Use: Available at no cost, making it accessible for penetration testers and hackers.
- Cross-Platform Compatibility: Runs on Linux, Unix, Mac OS X, and Windows 7 and 8.
Cons:
- Outdated Interface: The interface is rudimentary and not very user-friendly, often requiring command-line usage.
- Limited Compatibility: Does not work on macOS or Windows 10, limiting its usability on newer systems.
- Internal Network Requirement: Must be inside the target network to be effective, restricting its use for external attacks.
Automated penetration testing FAQs
What are the 3 types of penetration testing?
There are three formats that are regularly used in penetration testing exercises:
- Black-box assessment – The pen tester is given no information about the target system other than its external IP address. The tester needs to start from scratch, like a hacker discovering a network for the first time.
- White-box assessment – The pen tester is given full system information, including a network map and credentials. The purpose of this disclosure is to skip the research phase and get straight to launching attacks.
- Gray-box assessment – The pen tester is given access credentials, which might have admin privileges. This scenario models an insider threat or credentials theft through phishing.
Why automate penetration testing?
Penetration testing involves human testers because real people are more able to make quick assumptions and heuristic judgments that a computer program. Despite this human ingenuity, there are methodical steps that every penetration tester follows, which includes following a test plan. That same plan is probably going to be reused for every project. So, given that there are known steps to go through, why not let a script perform them and save the cost of expert testers? There is a rationale to this approach and this is why vulnerability scanners were created, which are automated penetration testing systems.
What is the difference between automated and manual penetration testing?
A completely automated test is known as a vulnerability scan. Although vulnerability scanners are effective, they are not as good as human teams of manual penetration testers. It is advisable to commission a periodic penetration test and perform vulnerability scans in between those major events. A good compromise is an automated penetration testing tool that a pen tester can use to gather information and speed up attacks. This is an assistance to a manual penetration testing exercise.