Bot management isn’t about managing your array of bots; it is about blocking attacks from bots. A “bot” is a front for hackers. Rather than launching an attack from their assets, exposing their IP addresses and locations, hackers infect other computers and use those to launch attacks. Those infected computers are called bots. They are also known as zombie devices. The collection of devices that a hacker controls is called a botnet.
Here is our list of the best bot management systems:
- MailWasher EDITOR’S CHOICE On-premises email previewer that intercepts mail between the server and the client. This package installs on Windows and is compatible with all of the major email clients. Start a 30-day free trial.
- TitanHQ Email Security (FREE TRIAL) Cloud-based system that is an edge service that filters out malware, phishing links, and spam email in general. It also scans outgoing emails to prevent data disclosure. Access a 14-day free trial.
- Cloudflare Bot Manager A protection system for web assets that can fine-tune responses to different types of bot by analyzing their functions. A Cloudflare subscription includes a proxy service that filters out DDoS attacks and other bad actors.
- DataDome This SaaS service assesses incoming requests and blocks them when it detects bot activity. This service acts as a gateway and will also operate as a web application firewall. In addition, it blocks hacker attempts as bot-based automated attacks.
- Radware Bot Manager This protection service for web applications, mobile devices, and APIs, operates as a plug-in or an API and assesses connection requests for validity. This is a cloud platform.
- Hornetsecurity Spam and Malware Protection A cloud-based edge service that receives all incoming mail for a business and filters it for signs of phishing or malware. This system will also monitor outgoing mail.
Bot attacks
A botnet is used to implement distributed denial of service (DDoS) attacks. A DDoS attack requires many computers. It is an act of overwhelming a web server’s ability to process connection requests. When a server receives more requests than it can handle, it creates a queue and intends to get to those requests.
The connection requests sent by a botnet are malformed and will never lead to an actual connection. However, even those failed attempts take up web server time and fill up queues. The browsers of web surfers hoping to visit a site will only wait so long before timing out. This means that a DDoS attack effectively removes access to a site, making it no longer operational.
Although a DDoS attack might last only for a short time, the long-term effects can be very damaging. For example, a website that is uncontactable seems to be defunct. Anyone trying to access the site while under attack will go elsewhere, so that site has lost a potential customer, benefiting its rivals. A place sent offline also suffers reputational damage – a visitor finding a location is inaccessible will assume the business has shut down forever.
Bot scams
Bots are also used for email scams. Remember, an essential survival strategy of fraudsters is to be untraceable. There are two ways that a hacker can hide a valid location. One is to spoof the source address of an email. However, an analyst can still trace the IP address of the mail’s origin. So sending that fake email out from a bot computer hides the actual IP address of the hacker.
Spamhaus maintains a trace of bots used for email fraud, which is called “spam-bots.” India is currently at the top of that is with 726,984 live bots. China is in the second position with 686,023 bots, and the USA is in third place with 440,726 bots.
Although the Spamhaus system records the location of the bots, that is no indication of the location of the con artists that use those conduits to send emails. According to Statista, 306.4 billion emails are sent worldwide, and around half of those are spam. As all spam emails are issued from bots, these infected computers send approximately 153 billion emails per day.
Block bots
A typical person will ask why doesn’t someone trace the sources of these fake connection requests and spam emails and shut down those computers? The answer is that botnets are constantly moving targets. The owners of those bot computers are not criminals; they are innocent victims. Of course, if more people installed proper software to prevent infections or block communication from the bot system to and command and control (C&C) server, the problem of bots should reduce. However, hackers are alive to that threat and now use IoT devices, such as intelligent domestic devices connected to the internet. Businesses that sell these devices are now also becoming aware of the need for more robust security.
Bots have been around for a long time, and they will likely be a threat for many years to come. Unfortunately, the only way to combat bots is to block them. The bot management sector is another name for bot blockers. Usually, these systems are implemented as a service rather than a software package.
As the attacks of bots are sent across the internet, the best services that block bot traffic are also based on the internet. So, when you are looking for a solution to the problems created by botnets, you are looking for bot management platforms.
Bot management systems that block DDoS attacks operate by absorbing large amounts of traffic. They immediately detect genuine traffic and forward that on to the customer. Most free spam bot management systems work on global blacklists.
Spam emails tend to use generated source addresses, and the combinations that they use can be spotted. Unfortunately, some spam filters also record the IP addresses of the senders and block those – which inconveniences the owners of the infected computers. More complex spam filters scan each email for keywords in the content.
The best bot management systems
DDoS bot management systems and email bot management systems called spam filters operate in different ways. Any business will need both types of bot management services.
Our methodology for selecting a bot management system
We reviewed the market for bot management tools and analyzed the options based on the following criteria:
- A system that operates as a proxy and channels all of your inbound traffic
- A reliable service that you can trust to hold the IP addresses of your business
- A rapid service that can forward genuine traffic to your Web servers
- Load balancing services
- A spam filter that won’t be over-zealous and block genuine customer emails
- A free system or a free trial for a no-cost assessment
- A seamless service that does not cause service disruptions and offers value for money
With these selection criteria in mind, we have some very reliable DDoS blockers and spam filters.
You can read more about each of these options in the following sections.
1. MailWasher (FREE TRIAL)
MailWasher operates as a companion to email clients. It will work with Outlook, Outlook Express, Incredimail, Thunderbird, Windows Live Mail, Gmail, Hotmail, EM Client, and Yahoo. The client version needs to be installed on each computer that accesses email. There is also a server version that will pre-filter all email traffic before it reaches each endpoint.
Key Features:
- Blacklist Management: Allows you to block emails from specific senders or domains, potentially including known botnet sources.
- Control Over Email Policies: Provides administrators or individuals with the opportunity to control email policies, allowing for customized email filtering and management.
- Keyword Filtering: You can set up filters based on keywords or phrases commonly found in bot-generated emails, helping to block some bot activity.
- Quarantining: Includes a quarantining feature, enabling users to quarantine suspicious or unwanted emails before they reach the inbox.
Why do we recommend it?
MailWasher is an email blocker that changes the way your emails are delivered. This system leaves the emails on the mail server but you can see them through a client program that acts as a console. The tool blocks spam and phishing emails before they are downloaded.
There are three editions of MailWasher; the MailWasher Free and MailWasher Pro versions work with the email client and install on Windows. The MailWasher Server edition accepts all emails coming through your email server, and that version is available for Windows and Linux.
The server version is more comprehensive and removes extra processing from being needed on endpoints. Whichever version you go for, MailWasher can spot spam bot emails and scan for specified test strings. The service will also build up its email address blacklist.
Who is it recommended for?
This tool is suitable for small businesses and home offices. It requires a client to be installed on each computer that emails are accessed on. The user has to open the interface and manually download emails once this tool is in operation. That function means that it can’t be managed by remote IT support teams.
Pros:
- Mobile Companion App: MailWasher Pro can be used in conjunction with the desktop version for seamless email management on the go.
- Free and Paid Versions: Offers both free and paid versions, providing users with options based on their budget and needs.
- On-Premises Package: Offers an on-premises package, allowing organizations to have full control over their email security within their infrastructure.
- Preview Option: Includes a preview option that allows users to preview emails before they are delivered to the endpoint, ensuring that only safe and desired emails are accessed.
Cons:
- Limited Scope: Primarily focuses on spam filtering and doesn’t offer comprehensive bot management features like real-time analysis, behavioral analysis, or challenge-response systems.
There is a 30-day free trial available for MailWasher Pro and also for MailWasher Server.
EDITOR'S CHOICE
Mailwasher is our top pick for bot management software because this on-premises system offers protection for email systems against spam bots. The spam filter is available in a version for email clients, such as Outlook, Incredimail, and Thunderbird. This is Maiwasher Pro and it scans arriving emails, moving suspected spam into a quarantine area. The user can examine the emails in the quarantine and choice to restore the mail, letting it go to the inbox. This tool is only available for Windows. An alternative strategy is provided by Mailwasher Server. This interacts with email servers and performs the same service as Mailwasher Pro but for multiple email accounts. The server version will run on Windows or Linux. Mailwasher Pro is available in a mobile version for iOS or Android devices and that tool is free to use.
Download: Get a 30-day free trial
Official Site: https://www.firetrust.com/products/mailwasher-pro/download
OS: Windows, Linux, iOS, and Android
2. TitanHQ Email Security (FREE TRIAL)
TitanHQ Email Security is a gateway service that acts as a channel for both incoming and outgoing emails. It works as both a firewall and a reverse firewall, controlling the contents of emails that it processes.
Key Features:
- Email Protection: Provides robust email protection, safeguarding organizations against various email-borne threats such as phishing attacks, malware, and spam.
- Blocks Phishing and Spam: Employs advanced techniques to detect and block phishing attempts and unwanted spam emails, ensuring a secure email environment.
- Data Loss Prevention: Includes data loss prevention (DLP) capabilities, helping organizations prevent unauthorized disclosure of sensitive information via email.
- DDoS Protection: The DDoS protection component adds another layer of defense against botnet attacks.
Why do we recommend it?
Email Security is an email protection system. So, this tool will filter out spam and phishing attempts and block viruses. The system has a special service for Microsoft 365 email systems (Outlook and Exchange Server). TitanHQ also produces a higher plan, called SpamTitan Plus, which uses AI and verifies or blocks links in emails.
This service scans contents for malicious activity, such as damaging links or specific keywords, when dealing with incoming mail. Emails are also blocked according to a universal blacklist that the owner of Email Security, TitanHQ, maintains for all of its customers.
Incoming mail can be sandboxed to prevent infection from attachments, and it is also possible to block emails that contain specific texts. In addition, the system uses behavior analytics to prevent false-positive detection from hampering regular business activity.
Who is it recommended for?
Email Security deals with a specific type of bot threat. There are an estimated 320 billion spam emails sent every day, so a large corporation is going to have to deal with a lot of superfluous traffic to its mail server. Email Security Plus, WebTitan, and Email Archiving, are available as a package, called TitanSecure.
Pros:
- Integration with Office 365: Integrates seamlessly with Office 365, enhancing email security and protection for organizations using Microsoft’s productivity suite.
- IP Reputation Filtering: Blocks traffic originating from known botnet IPs and malicious sources.
- AI-Based Email Activity Analysis: Leverages AI methods to analyze regular email activity, identify suspicious patterns, and enhance detection of email threats, including zero-day attacks.
Cons:
- Limited Scope: Primarily focused on email-based bot threats, not a comprehensive solution for website or application bot management.
Outgoing mail can be scanned as part of a data loss prevention strategy. It asses the destination addresses of both incoming and outgoing emails to spot address spoofing. SpamTitan is available for a 14-day free trial.
3. Cloudflare Bot Manager
Cloudflare offers a range of proxy-based edge services to protect web assets. The service assumes your website’s IP address, and you then get a secret address for your site. Effectively, from that point, anyone going to your site gets sent to Cloudflare instead by the DNS service. Finally, the Cloudflare system connects back to your web server through a secure VPN connection.
Key Features:
- Bot Detection: Utilizes machine learning and behavioral analysis to identify malicious bots from legitimate visitors.
- Challenge-Response Systems: Employs CAPTCHAs, honeypots, and other methods to distinguish humans from automated bots.
- Customizable Rules: Allows you to define specific rules to block or challenge suspicious traffic based on IP addresses, user behavior patterns, or other criteria.
- Real-Time Analytics: Provides insights into bot activity, including types of bots detected, their origin, and their attempted actions.
- Integration with Other Cloudflare Services: Works seamlessly with other Cloudflare offerings like DDoS protection and web application firewalls for a layered security approach.
Why do we recommend it?
The Cloudflare Bot Manager is part of a package that also includes a DDoS protection service. This is called the Application Services system and there are flour plan levels. All plans include bot mitigation, which uses a range of detection systems that ultimately feed into a blacklist.
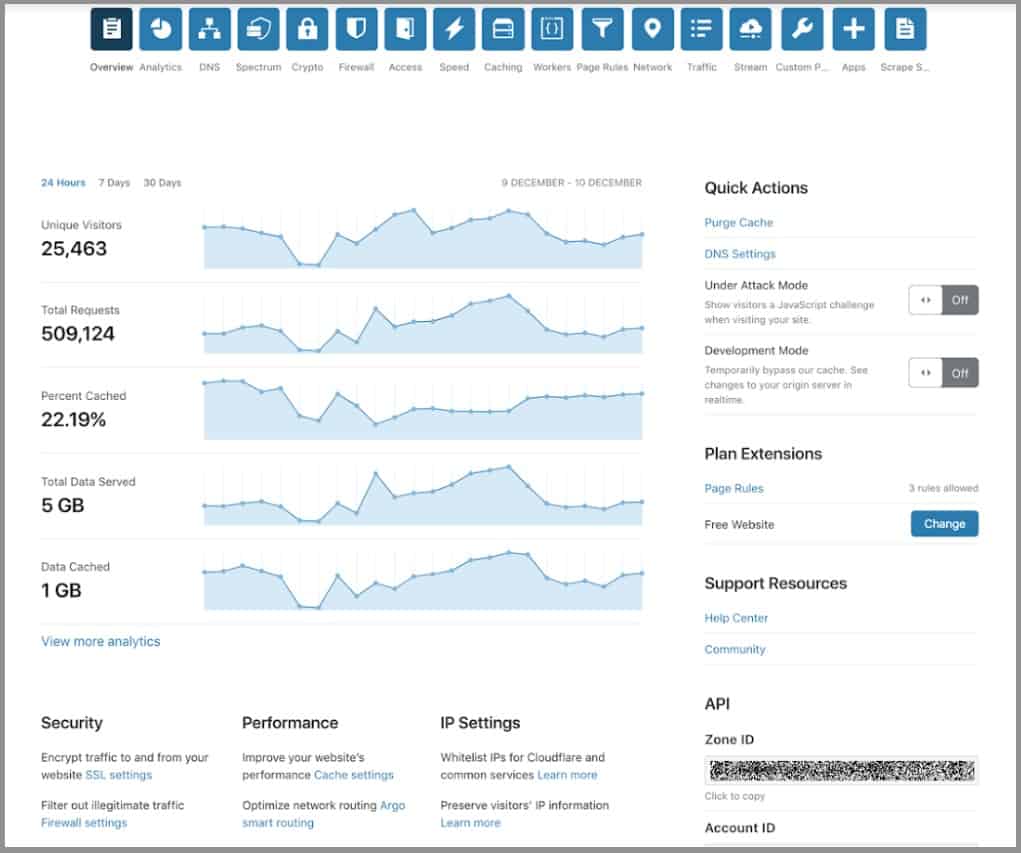
The Cloudflare service first made its name with its DDoS protection service. This is the primary bot management service that you get with this package. The Cloudflare system has enormous capacity and just absorbs all of the fake connection requests that botnets throw at it. Thus, the system never gets overwhelmed.
While Cloudflare takes on all malicious traffic, it lets through all genuine connection requests to your web server. Traffic doesn’t always go to your host because Cloudflare also includes a content delivery network. It takes a copy of your entire site and stores it on servers located strategically around the globe. This enables your site to transfer to faraway browsers much faster.
As well as blocking DDoS bots, the Cloudflare system can spot spam email, inventory hoarding, content scraping, and credentials stuffing bots. Cloudflare is available in four plans, and the first of these is Free. The other three offer more traffic throughput capacity and extra features, such as a web application firewall, a failover service, image optimization, and transfer speed enhancement.
Who is it recommended for?
This system is suitable for all sizes of businesses. The lowest plan is free and it is aimed at hobby websites. This provides basic bot protection. However, as this refers to the Cloudflare blacklist, this is probably very effective. The lowest paid plan is affordable for small businesses.
Pros:
- Improved Website Performance: By blocking malicious bots, it reduces strain on your servers and resources, leading to a smoother user experience for real visitors.
- Enhanced Security: Protects against automated attacks like credential stuffing, scraping, and click fraud.
- Easy to Use: Offers a user-friendly interface for management and configuration, even for users with limited technical expertise.
- Scalability: Cloud-based solution scales automatically to handle fluctuating traffic patterns.
- Integration Benefits: Integrates well with other Cloudflare services for a comprehensive security posture.
Cons:
- Can Sometimes Delay Access to Your Site: One potential drawback of using Cloudflare Bot Manager is that it can occasionally delay access to your site. This may occur due to the processing time required for bot detection and mitigation.
Cloudflare Bot Management is delivered by a leading provider that offers DDoS protection, among other benefits. The first plan from Cloudflare is free, including up to 90 Tbps capacity for DDoS protection. Other services in this plan include a content delivery network to speed up your web page transfers and a free SSL certificate.
Get started for free: cloudflare.com/plans/free/
Operating system: Cloud-based
4. DataDome
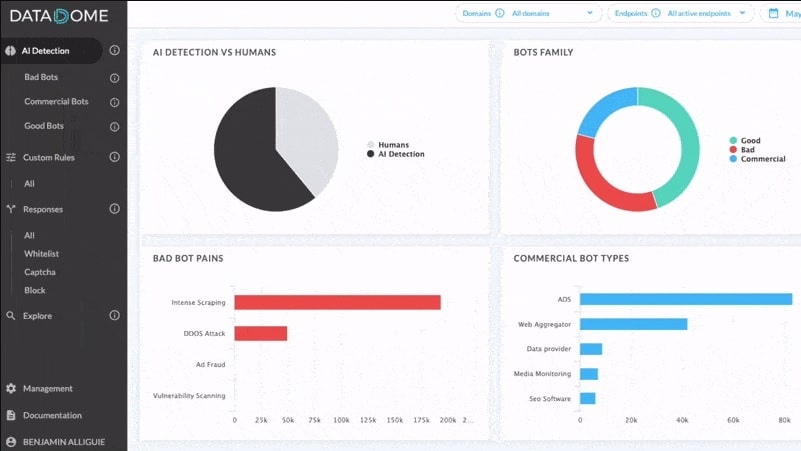
DataDome is a web application firewall that works as an advisory service rather than as a proxy. This system examines each incoming transaction and uses AI processes to decide whether the request should be served. In addition, it detects hacker activity as well as automated botnet attacks.
Key Features:
- Behavioral Analysis: Analyzes user behavior patterns to identify anomalies and suspicious activity that might indicate bots, even if they attempt to mimic human behavior.
- Customization Options: Offers a high level of customization for bot detection and challenge rules, allowing you to tailor protection to your specific website or application needs.
- Multi-Platform Protection: Provides protection for websites, APIs, and mobile applications, ensuring comprehensive security across various digital assets.
- eCommerce Fraud Protection: Offers eCommerce fraud protection features, helping businesses prevent fraudulent transactions and safeguard their revenue streams.
- Strong Technical Support: DataDome provides robust technical support to assist users in implementing and optimizing their security measures effectively.
Why do we recommend it?
DataDome is a high-end web application protection system. The system is based in the cloud and it catches all incoming requests, assesses it, and blocks the bot traffic, DDoS attacks, and reconnaissance attempts. This system is able to protect websites, mobile apps, and APIs.
The DataDome system constantly analyzes traffic for all of its clients, and spots sources that are contacting many different destinations, indicating bot activity. Whenever new attack strategies are detected, the traffic assessment algorithms used by the traffic manager are updated automatically. As it is a hosted service, all software updates are applied centrally and immediately serve all clients.
The bot systems that this tool can detect include scaping, account takeover, and click fraud, as well as DDoS attacks. It can protect mobile apps as well as websites. The system is hosted and is implemented by loading in a plug-in.
Who is it recommended for?
DataDome is priced for large businesses. You would need to be running a number of websites to justify the price of the service. Even mid-sized companies would find this tool out of their budgets. The package is particularly useful for online stores because it can detect purchase fraud.
Pros:
- Detects and Blocks Malicious Bot Activity: Effectively detects and blocks malicious bot activity, including scraping, credential stuffing, DDoS attacks, and other bot-related threats, ensuring the integrity and security of digital assets.
- Identification of Hacker Actions: The platform employs processes to identify hacker actions, allowing businesses to proactively defend against cyberattacks and unauthorized access attempts.
- Full Logging and Event Tracking: Offers comprehensive logging and tracking of all detected bot-related events, providing visibility into security incidents and enabling informed decision-making.
Cons:
- Lack of Pre-Transaction Filtering: One limitation of DataDome is that it doesn’t filter out fake transactions before they reach your server. This can potentially increase server load and processing overhead, especially during peak transaction periods.
The DataDome system is offered in three plans; Starter, Business, and Corporate. The difference between these plans lies in the throughput capacity and data retention offered. You can get any of these plans on a 30-day free trial.
5. Radware Bot Manager
Radware Bot Manager is a cloud service that assesses incoming connection requests and identifies malicious bot traffic. The service simply gives the web server an accept or reject message for each incoming connection request.
Key Features:
- Mobile Device Risk Assessment: Offers mobile device risk assessment, ensuring comprehensive protection for mobile apps against bot-related threats.
- Multi-Platform Protection: Protects websites, APIs, and mobile applications, providing holistic security coverage across digital assets.
- DDoS Protection: Includes DDoS protection features, safeguarding businesses against distributed denial-of-service attacks and ensuring uninterrupted service availability.
Why do we recommend it?
Radware Bot Manager is part of the Application Protection division of services on the Radware platform. This service will block account takeover attempts, DDoS attacks, web scraping, click fraud, and payment fraud. The tool will protect websites, mobile apps, and APIs.
The Radware system monitors activity on a site to work out what constitutes a valid transaction. It also offers the option of sending back fake data to confound bots. The service also provides a reCAPTCHA challenge for web visitors to filter out automated bot traffic easily.
Radware hosts the service, and you access it by loading a plug-in into your web server or cloud platform. It is also available through an API that you can call from a custom process. Another deployment option is to set it up as a virtual appliance that will filter all of your incoming traffic.
Who is it recommended for?
Radware is a very strong service that operates as a plug-in for your web server. Although the service says it provides DDoS protection, as all traffic goes straight to your web server and isn’t intercepted, your system can still get flooded. The plug-in checks each incoming request and issues a pass or fail judgment.
Pros:
- Adaptable Behavior Tracking: Employs adaptable behavior tracking mechanisms, allowing it to detect and mitigate evolving bot threats effectively.
- Traffic Assessment for Bot Identification: Utilizes traffic assessment techniques to accurately identify and differentiate between human traffic and bot traffic, enabling precise bot detection and mitigation.
- Option for Sending Fake Data to Confound Bots: Provides options to send back fake data to confuse and confound bots, enhancing security measures and thwarting malicious bot activities.
Cons:
- Lack of Complete Independent Front-End: One drawback of Radware Bot Manager is the absence of a complete independent front-end for the service. This may limit customization options and user control over certain aspects of the platform.
Radware also offers a web application firewall, and the Bot Manager can be taken as an additional service integrated into that product. Radware Bot Manager is available on a 15-day free trial.
6. Hornetsecurity Spam and Malware Protection
Hornetsecurity Spam and Malware Protection, previously called Zerospam, is an email manager that is offered as an edge service. All of your incoming and outgoing email traffic is channeled through the Hornetsecurity system for inspection. The cloud service can also substitute for your cloud server if it goes offline. In addition, this system blocks bot activity such as DDoS attacks and spam email campaigns.
Key Features:
- Block Spam and Phishing Attempts: Effectively blocks spam emails and phishing attempts, ensuring a clean inbox for users.
- Attachment Scanning: Scans email attachments for malicious content, providing an additional layer of security against malware and viruses.
- Option to Approve Blocked Emails: Users have the option to review and approve emails that were initially blocked, adding flexibility and control over email filtering.
- Machine Learning-Based Threat Detection: Utilizes machine learning algorithms to detect new and emerging email threats, potentially including some bot-related attacks.
Why do we recommend it?
Hornetsecurity Spam and Malware Protection detects automated emails, which includes a range of threats and annoyances. The service blocks incoming emails that have been detected as generated and stores them in a quarantine space. Administrators can check through that list and unblock emails that are seen to have been blocked in error.
Incoming emails are scanned for contents with the bot blocker looking for specific text patterns, phishing links, and infected attachments. Outgoing emails are scanned to prevent malware from being forwarded. The service can also impose encryption on outgoing emails to protect sensitive data in transit.
Who is it recommended for?
This is a very comprehensive email filter with a series of checks and an option to check through blocked emails. The system will also filter out “address not contactable” automated emails. The system also checks outbound emails but it only scans for spam, phishing, and malware, so it doesn’t offer a data loss prevention service.
Pros:
- Easy Implementation as an Edge Service: Easy to implement as an edge service, minimizing setup complexities and allowing for quick deployment.
- Behavior Analytics for Reduced False Positives: Leverages behavior analytics to reduce false-positive detection, ensuring that legitimate emails are not mistakenly blocked.
- Data Loss Prevention (DLP) Capabilities: Blocks data loss by preventing unauthorized disclosure of sensitive information via email.
Cons:
- Reliance on Hornetsecurity Suite: To access bot mitigation features, you need the entire Hornetsecurity email security suite, which might not be necessary if you have other email security solutions in place.