Breach detection systems (BDSs) are an emerging and important aspect of system security, designed to identify and respond to potential threats in a timely manner. As organizations increasingly rely on digital systems to store sensitive data, it becomes essential to protect both private user information and critical business data.
Here is our list of the best breach detection systems:
- ManageEngine Endpoint DLP Plus EDITOR’S CHOICE This package discovers and categorizes sensitive data according to given protection standards and then implements user activity tracking and file protection to prevent the misuse of that important information. The software runs on Windows Server and you can get it on a 30-day free trial.
- ESET Protect This series of threat detection and response plans build up from an on-device unit through to cloud-based, centralized threat hunting with automated responses. The product family also includes vulnerability management and a managed security service. The endpoint protection system runs on Windows, macOS, Linux, iOS, and Android. Get a 30-day free trial.
- UpGuard BreachSight A cloud-based risk assessor and system breach scanner from UpGuard.
- Trend Micro Deep Discovery Detector A highly-rated threat protection hardware device that includes constant port and protocol monitoring plus software event tracking.
- Imperva Data Security Monitoring Protects data in databases and files, on-premises and on the cloud.
- Fortinet FortiSandbox A proactive advanced threat detection system that is available as an appliance, as a VM, or as a cloud-based service.
- Netwrix Change Tracker Spots unauthorized alterations to a system that might correspond to an expected alteration that is part of a change management process.
- CrowdStrike Falcon Prevent A cloud-based endpoint protection platform that is termed a next-generation antivirus system.
- InsiderSecurity A Singapore-based threat protection monitor. Available from the cloud or for on-premises installation.
- SpyCloud Locks down system user accounts and particularly highlights abandoned but live accounts.
Breach detection plays a vital role in safeguarding this information, as it enables the early detection of unauthorized access or attempts to exploit vulnerabilities. Understanding how breach detection fits into an organization’s overall security strategy is crucial for businesses aiming to protect their operations from cyber threats.
While many may be familiar with Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS), it’s important to note that breach detection systems serve a different purpose and should not be confused with them. IDS and IPS have long been fundamental in network security.
IDS primarily monitors network traffic for suspicious activity and alerts administrators when potential threats are detected. IPS, on the other hand, takes it a step further by not only detecting threats but also actively blocking or preventing them from causing harm.
Breach detection systems, however, are specifically designed to identify when a breach occurs, often focusing on detecting advanced, hidden, or slow-moving threats that may evade traditional IDS and IPS systems. BDSs work by constantly analyzing data across various points of a system and looking for signs of abnormal behavior or patterns indicative of a potential security breach.
Unlike IDS and IPS, which primarily deal with detecting and preventing network-based intrusions, BDS focuses on ensuring that no unauthorized access or data compromise occurs across the entire infrastructure.
In conclusion, while IDS and IPS systems are critical components of network defense, breach detection systems provide an additional layer of protection by identifying threats that may otherwise remain undetected until they have already caused significant damage.
How do BDSs work?
While intrusion detection systems try to prevent network break-ins by outsiders, breach detection systems look for malicious software activity on the network. Breach detection is a new term for an old problem. The difference between BDS and a firewall is that breach detection operates within the network, whilst firewalls are boundary tools that try to block malware at the point of entry.
The definition of BDS sounds a lot like an antivirus system. It is. However, an antivirus program checks on a single computer for known malware but a BDS watches activity on a network and throughout an IT system. A BDS can be implemented as software or as a hardware device.
The security threats detected by BDS are a little wider in behavior than the activities detected by a typical anti-malware system. The malicious software that the BDS looks for could be part of a suite of attacking software, launched manually by an intruder.
Each individual program run might seem compatible with the normal activities of the business. It might be the execution of legitimate software already resident on your system. BDS doesn’t just look at each individual process but detects combinations of programs that could be combined for malicious purposes.
The best breach detection systems
The definition of BDS is new and so there aren’t many suppliers for this type of system yet.
Our methodology for selecting a breach detection system
We reviewed the market for breach detection packages and analyzed tools based on the following criteria:
- Malware detection systems on endpoints and network equipment
- The ability to coordinate malware detection from a central controller
- Detection of Trojan and lateral movement utilities
- The ability to stop and delete malicious software
- A mechanism to stop and clear out system utilities that have been hijacked
- A free trial or a demo package that enables a risk-free assessment
- Value for money from a comprehensive protection system that is offered at a fair price
With these selection criteria in mind, we surveyed the market for breach detection services and noted systems that are worth considering.
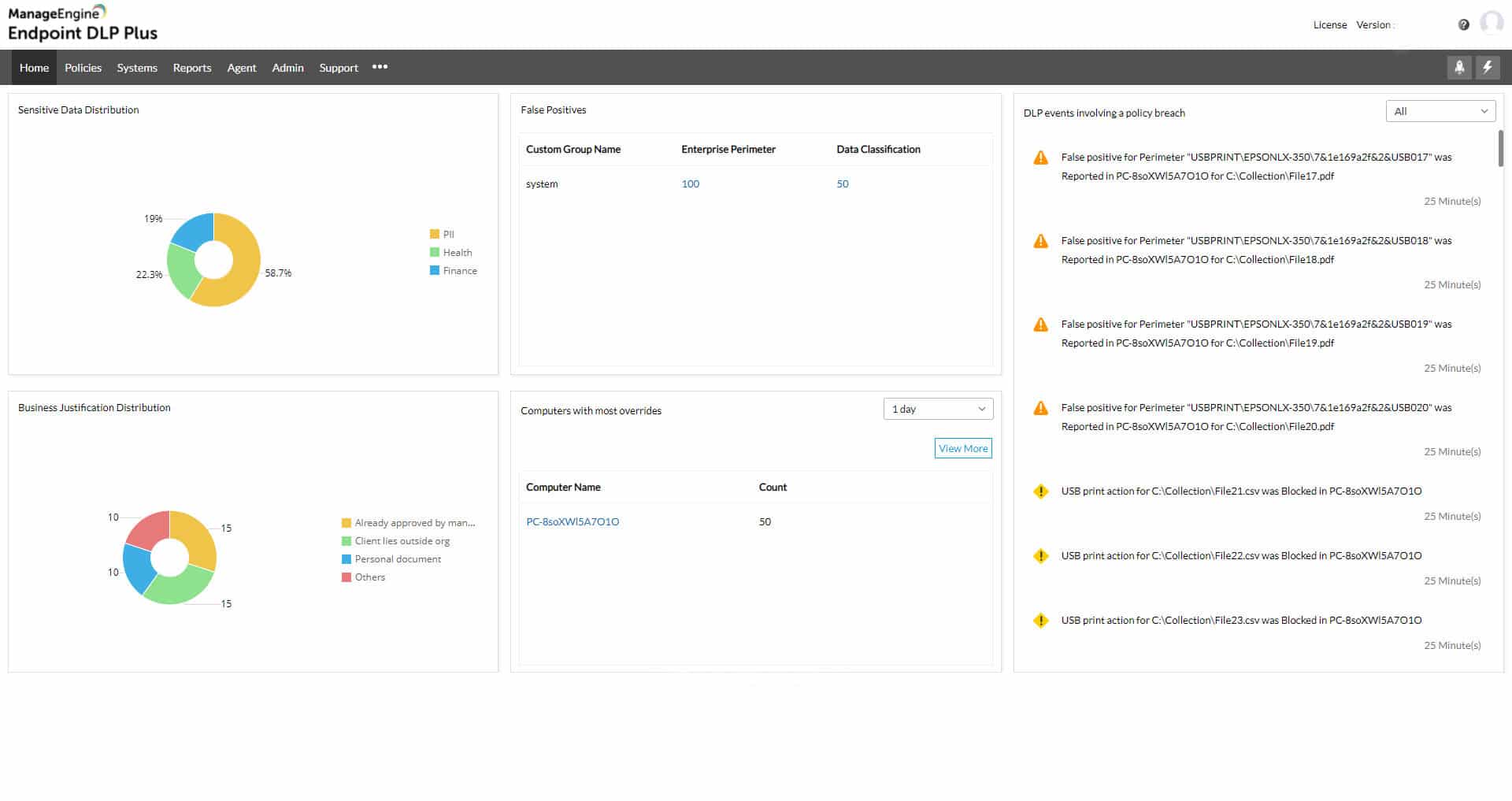
1. ManageEngine Endpoint DLP Plus (FREE TRIAL)
ManageEngine Endpoint DLP Plus is an on-premises package that discovers and categorizes instances of sensitive data and then implements protection procedures. Each phase of the data protection task involves in-depth research and constant scanning. The exact type of data that the system looks for depends on the standards that you have to follow, for example, it could look for credit card information for PCI DSS or clinical data (PHI) for HIPAA. The tool will even scan images for data.
Key Features:
- Data Discovery: Sensitive data classification
- Option to Centralize Data: Also possible to leave data in its current locations
- Compliance Auditing: GDPR, CPRA, PCI DSS, HIPAA
- Fingerprinting: Identifies sensitive data that is spread over nearby fields
- User Behavior Analytics: Spots insider threats
Why do we recommend it?
ManageEngine Endpoint DLP Plus is a comprehensive package that includes discovery and classification as well as protection methods. The controls that the system imposes don’t block data access completely – some staff need that data otherwise you wouldn’t hold it. The system blocks inappropriate use and unauthorized access or movement.
Once the service discovers instances of sensitive data it lists their locations in the system dashboard, giving you the option to reorganize your storage strategy to centralize those files. When new files are created, Endpoint DLP Plus scans them for sensitive data. The tool will also scan files that are being uploaded to cloud drives and storage accounts.
The package watches file transfer attempts and connections to peripheral devices, including the USB ports on endpoints. It also scans all emails for contents and attachments.
Curiously, this system doesn’t interact with Active Directory or provide its own access rights manager. Instead, the tool scans all software on endpoints and identifies those trusted applications that are needed to access the particular types of data files, such as Excel for spreadsheets or Word for documents. The tool relies on the access controls already in place for data access through endpoint access controls or software user accounts.
One way an intruder could gain access to a file without going through those controlled applications would be to install an alternative software package that is able to read the file formats. Endpoint DLP Plus blocks unauthorized software. The lock that binds approved applications to specific data sources can be enforced through containerization.
Who is it recommended for?
Any business that has to handle sensitive data would benefit from using Endpoint DLP Plus. ManageEngine provides a Free edition that is limited to scanning 25 computers. This is very appealing for small businesses. The charge rate increases with more capacity and goes right up to suitability for large enterprises.
Pros:
- Discovery of Shadow Copies and Local Stores of Data: Deletes temporary backups
- Deduplication of Data and Centralization: Saves on storage
- Containerization of Files: Blocks unauthorized access
- Clamp down on Unauthorized Software: Prevents malware
- Data Transfer Channel Control: Watches data movements
Cons:
- Not a SaaS Package: Available for Windows Server
ManageEngine Endpoint DLP Plus is a software package that runs on Windows Server. It is available for a 30-day free trial.
EDITOR'S CHOICE
ManageEngine Endpoint DLP Plus is our top pick for a breach detection system because it simplifies activity scanning towards the really important assets, which are related to sensitive data. You should have firewalls and antivirus in place and also a SIEM but if an intruder or a disgruntled insider touches that sensitive data, you will know about it. This is the last line of defense that ensures your company won’t be ruined by a data breach.
Download: Get a 30-day FREE Trial
Official Site: https://www.manageengine.com
OS: Windows Server
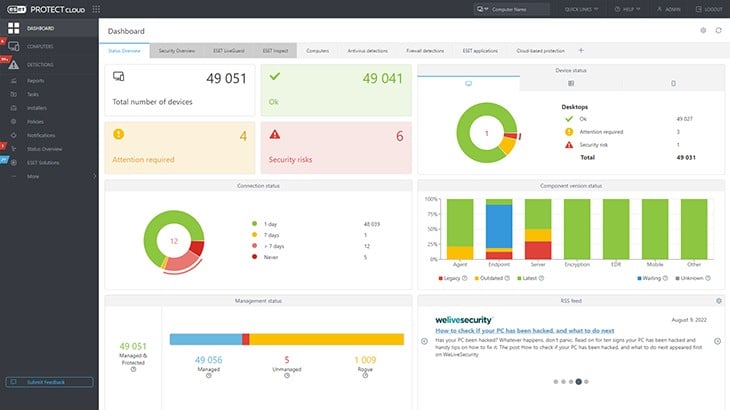
2. ESET Protect
ESET Protect starts its breach detection work at the device level. This looks like a classic anti-virus that you install on each endpoint. That AV is available for mobile devices as well as for computers and it will run on Windows, macOS, Linux, iOS, and Android. Buyers of this layer of protection also get a cloud-based console that reports on the activity of endpoint protection units.
Key Features:
- On-Device Breach Detection: Runs on Windows, macOS, Linux, iOS, and Android
- A Central Coordinator: Keeps activity logs
- Pooled Threat Detection: SIEM-based system
- Multi-Level Approach: Endpoint units communicate with a cloud-based server
Why do we recommend it?
ESET Protect is a quick and easy way to get a fully coordinated enterprise-wide cybersecurity system up and running. Everyone understands the importance of having on-device antivirus systems in place but implementing corporate security can be complicated. ESET Protect simplifies that task by joining up the AV systems into a multi-layered defense system.
The base package of the ESET system is ESET Protect Entry. This provides local protection with an overview delivered to the cloud console. From that point, uploaded activity data can be used for a second line of threat detection on that cloud server. This is the added value of the ESET Protect Advanced plan. With its unified view of system activity across the enterprise, this package can spot actions, such as lateral movement, and stop it by warning all endpoint units of what is going on elsewhere.
The cloud-based facilities of the Advanced plan are extensive and they include sandboxing on that cloud server to trial a downloaded software package while keeping endpoints safe from harm. The endpoint unit will continue to detect threats and block them, while the cloud-based component discovers extra threats and communicates responses back to the endpoint units.
The private threat intelligence network created by the Advanced plan provides a form of system hardening. The ESET Protect Complete plan includes a vulnerability scanner and a patch manager, which assesses the settings of each endpoint to ensure that the device is not open to attack. An included patch manager helps with that work. This edition also extends protection to cloud systems, such as SaaS packages. It will scan email servers both on the cloud and on your site.
ESET Protect Elite is the top plan and it extends response actions to third-party tools. All of the plans of the ESET Protect brand are available in a multi-tenanted architecture for use by managed service providers. ESET offers a managed security service, called ESET Protect MDR – Managed Detection and Response – as an option.
Who is it recommended for?
This package is suitable for businesses of all sizes, thanks to its edition levels. Any small business can get full cybersecurity protection without hiring technical staff, simply by installing the AV on each endpoint and accessing the cloud-based console to link all of those AVs into a unified system.
Pros:
- A Central Activity Monitoring Console: Provides insights into system activity
- Additional Prevention and Defense Features: Disk encryption, patch management
- Options to Protect Cloud Systems: Microsoft 365
- Cloud Sandboxing for Suspicious Software: Provides an option for manual approval
Cons:
- Minimum Order Quantity: At least five licenses have to be purchased
You need to sign up for a minimum of five devices for all of the plans except for the Elite plan, which starts with 26 devices. ESET Protect is available for a 30-day free trial.
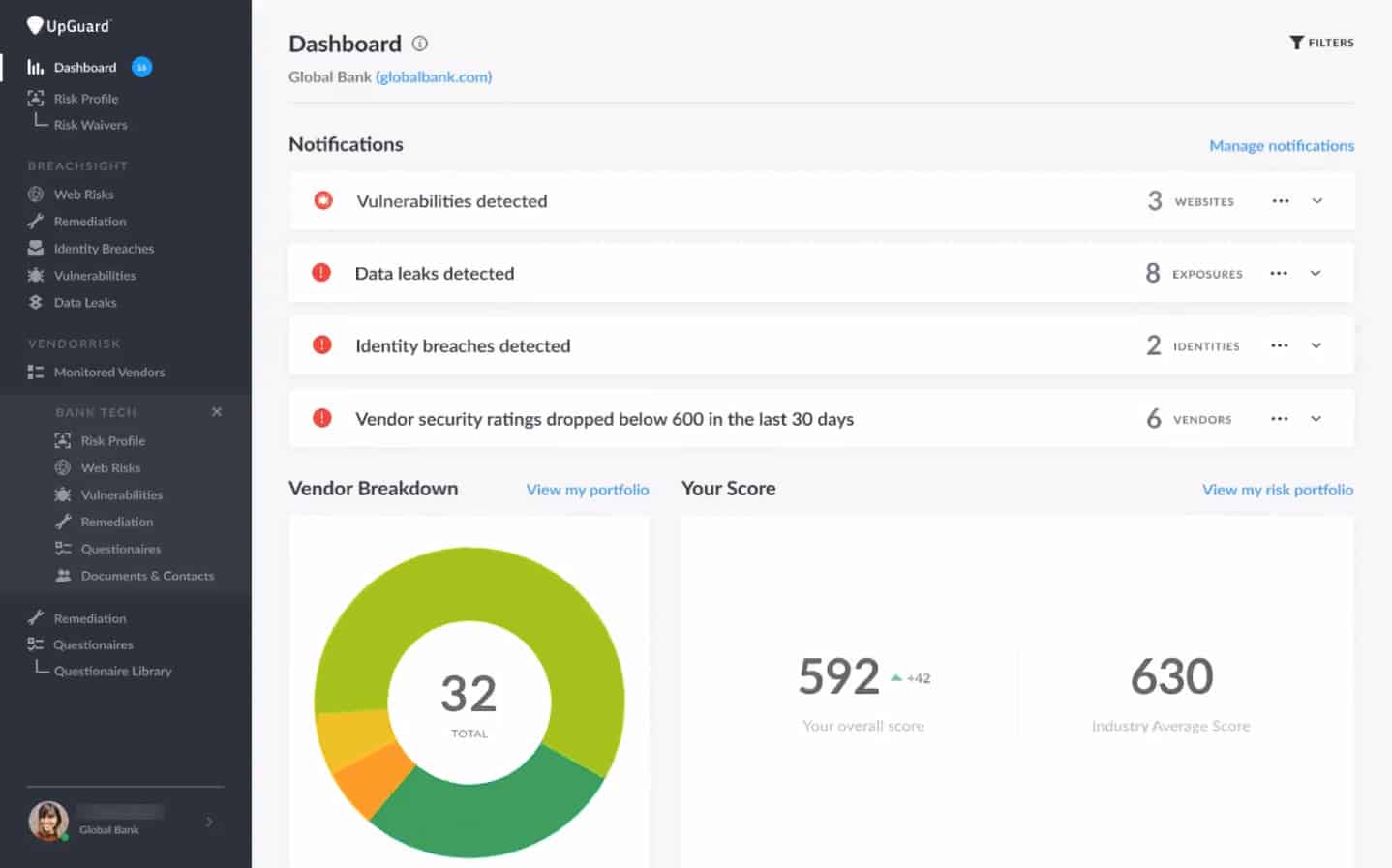
3. UpGuard BreachSight
BreachSight is a very competent data breach system from UpGuard, which produces a range of security products that are ideal for online retailers.
The BreachSight system has an attractive management console that is accessible online. The whole system is delivered from the cloud so you don’t need to worry about server space to host the cybersecurity system.
Key Features
- Addresses all Threats: Intrusion and insider threats
- Data Loss Prevention: Credentials protection
- Vulnerability Scanner: Preventative security measures
Why do we recommend it?
UpGuard BreachSight protects businesses from intrusion attacks and insider threats through vulnerability scanning and risk assessments. The tool operates from the cloud and acts as a preventative measure rather than looking for breaches in progress. The UpGuard platform has a Vendor Risk unit, which is bundled in with most plans.
The security system tackles data protection from two angles:
- Data leak vulnerability
- Credentials disclosure
The vulnerability scanner runs continuously. It alerts the data manager of any suspicious data access attempts. It will also highlight system security weaknesses that need to be closed off. The scanner looks for running processes and scans the code for the programs, looking for malicious intent.
BreachSight is able to detect when employee credentials have been disclosed. The credentials protector checks for unexpected activity and alerts the company’s systems administrator to revoke credentials that are suspected of being compromised.
The BreachSight system includes automated remediation scripts. All steps are fully documented. The records of breach detection and remediation form a valuable archive, which you will need in order to demonstrate compliance to data protection security standards.
The package of breach detection measures includes access to cybersecurity experts at the UpGuard offices. These consultants will guide your system administration team in interpreting the data raised by the application. That breach event log is even able to identify the parties responsible for the breach, enabling your company to sue for the recovery of losses or at least, to get the authorities to deal with the perpetrator.
Who is it recommended for?
This service is a system hardening tool rather than a live security monitor. It examines the attack surface of a business – the assets of the businesses that could give intruders a way in. Although there is an edition for small businesses, this service is expensive and more suitable for large enterprises.
Pros:
- Cloud-Based Product: Reduces infrastructure costs
- Includes File Protection: Protect against accidental deletion and ransomware
- Risk Assessments: Includes third-party risk analysis
Cons:
- No Free Trial: Get a demo
This is an excellent breach detection system, but you will need to check it out for yourself before in order to understand how it will fit into your data protection strategy. You can get a free demo of the system over at the UpGuard website.
4. Trend Micro Deep Discovery Inspector
Trend Micro is a major antivirus brand. All AV providers are currently moving forward to provide more comprehensive cybersecurity services. Trend Micro has developed a breach detection system that will help it pull ahead of the competition.
Key Features
- Implemented as an Appliance: Physical or virtual
- Blocks Trojan Activity: Also detects ransomware and intrusion
- Zero-Day Protection: Looks for anomalous activities
Why do we recommend it?
Trend Micro Deep Discovery Inspector looks for both intruder and malware attacks. This is a hardware device that you plug into the network. You can connect to the console for the system easily over the network. The service doesn’t require much manual intervention but will automatically block detected intruders.
This is an appliance that you plug into your network, much as you would a firewall. Don’t replace your boundary protection services with the Deep Discovery Inspector because this appliance’s attention is drawn toward activity within the network.
The strength of this tool lies in its ability to catch the interactions between Trojan software and its external controllers.
A very distinctive feature of attacks that breach detection systems are designed to block is that seemingly unrelated software gets manipulated to work in concert for malicious purposes. Deep Discovery Inspector aims to detect the controlling force that commands legitimate software to contribute to data breaches.
This system operates at the network level and looks for suspicious combinations of events. It covers endpoints, web and email applications and network traffic to build up threat analysis profiles. It does not use the traditional AV tactic of reference to a malware-characteristic database. Thus, it is able to detect “zero-day” attacks. It reaches into applications, including email and web servers to fish out attack strategies before they have a chance to reach targets.
This is an innovative breach detection system from one of the world’s leading cybersecurity operations.
Who is it recommended for?
The great thing about this Trend Micro tool is that it automates threat remediation. You don’t need to install any software on any endpoints and you don’t need to know how to respond to threats. It also sandboxes all software entering your system so it can spot malware before it gets onto any device.
Pros:
- Breach Response Automation: Can implement actions or send notifications
- Documents Breaches: Useful for auditing and investigations
- Scans Behavior: Looks at activity on endpoints and the network
Cons:
- No Price List: Must contact for pricing
5. Imperva Data Security Monitoring
Data security monitoring covers every type of data storage from databases to files and this suite of system security measures covers all of them.
Key Features
- Creates a Security Fabric: Protects all data stores on premises and on the cloud
- Risk Assessments: Standards compliance
- Live Threat Intelligence Feed: Warns of current campaigns
Why do we recommend it?
Imperva Data Security Monitoring is implemented by the Imperva Data Security Fabric. This package of data protection systems includes threat detection and response. The tool gathers activity data from many assets, such as on-premises endpoints, storage servers, cloud platforms, and SaaS packages. This is a flexible package with many components.
Imperva stresses the importance of its service’s ability to prove data security standards compliance. As a systems administrator, you have two data protection priorities: protection of data and proving that you have done everything possible to protect that data. The proof is important if you need to demonstrate compliance to data security standards in order to win new business and keep your enterprise profitable.
The system monitors events that relate to data stores and reports on suspicious activity live in the console screen. The monitor pulls in live feeds from Imperva Data Risk Analytics to continuously update its remediation of attack vectors.
Imperva Data Security Monitoring is available as on-premises software or as a cloud-based service. The company does not offer a free trial, but you can get a demo of the system to assess whether or not it meets your company’s data security needs.
Who is it recommended for?
The Imperva solution isn’t a one-size-fits-all service. Instead, an interested company would get a consultation over which elements of the Data Security Fabric range would be appropriate. The threat detection system is one of these services and it can be extended by data loss prevention and user activity tracking.
Pros:
- Security Assessments: Combines in-depth audits and compliance tests
- Live Security Monitoring: Breach detection features
- Threat Remediation: Automated responses
Cons:
- No Free Trial: This is a custom package
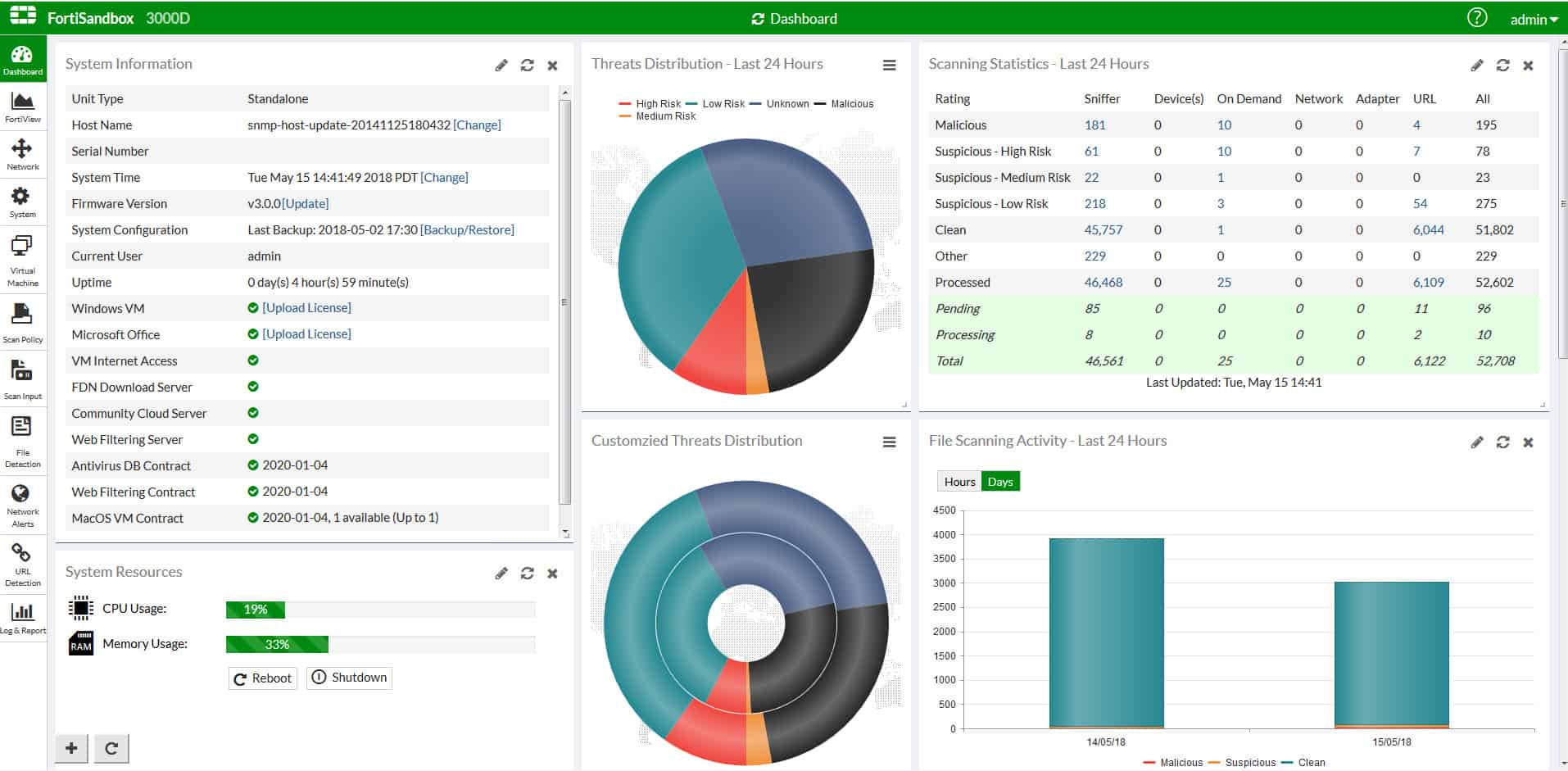
6. Fortinet FortiSandbox
Fortinet specializes in network security against incoming Internet-bound threats. The FortiSandbox is available as an appliance, as on-premises software run over a virtual machine, or as a cloud-based subscription service.
Key Features
- Available as a Network Device: Physical and virtual appliance options
- Monitors the Network: Catches the transfer of executables
- Quarantines New Software: Assesses new software for threats
Why do we recommend it?
The Fortinet FortiSandbox system is a component of the next-generation firewalls offered by Fortinet. The system is an inline sandbox, which gathers traffic as it arrives at the FortiGate firewall and then performs static and dynamic analysis on any software that is passing through. Suspicious files are blocked and quarantined.
Breach detection systems start with the assumption that network access security can be defeated. The FortiSandbox strategy involves isolating new software and monitoring its reaction with the resources and services of the network. This is a quarantine approach that allows the software to function fully but establishes savepoints to enable full system rollback.
Who is it recommended for?
This sandboxing system would be acquired as part of a Fortinet firewall product. Different deployment options give the Fortinet range a wide market. The hardware device is Fortinet’s signature product but it is expensive and will interest large companies. The cloud-based option has a wider appeal.
Pros:
- A Respected Brand: A leader in network security
- Integrates Nicely with FortiGate Firewalls: Load it onto the firewall appliance along with other extra services
- Multi-Cloud Support: Covers AWS or Azure
Cons:
- WAN Management Features are Not Native: They are only available through the companion tool called FortiManager
FortiSandbox interacts with all levels on your networks from firewalls and gateways over to endpoints. The package includes mitigation services as well as threat detection. This is the software equivalent of “Trust but verify.” Fortinet offers a free demo of FortiSandbox.
7. Netwrix Change Tracker
Netwrix Change Tracker is particularly concerned with exploits that can be slipped into system change processes. The tool is designed to enforce the demands of IT system management standards, especially ITIL.
Key Features
- Traps Malware in System Updates: Spots fake updates
- Good for Development Environments: Records changes to configuration settings
- Configuration Manager: Blocks unauthorized changes
Why do we recommend it?
Netwrix Change Tracker is a vulnerability scanner for device configurations. It looks for system weaknesses that can be exploited by hackers and scores all IT assets for security, detailing work that needs to be done to raise those scores. It continues to scan those hardened assets, identifying and undoing unauthorized configuration changes.
Improvement projects are always undertaken with a positive attitude. System change is only for the better. However, while the team is working to a bright new future, others might have malicious intent and use the upgrade project as a smokescreen for an intrusion opportunity.
Change Tracker keeps an eye on exploits that might arise during a development project. It keeps control of device configurations while everyone’s attention is directed towards development. The tool looks at unauthorized configuration changes, generates an alert when one is detected and automatically rolls back to authorized configurations when any change is detected.
Who is it recommended for?
This tool is particularly useful for any business. However, the compliance management feature in the package makes it doubly appealing for businesses that manage sensitive data and need to follow a data security standard in order to keep in business. Netwrix doesn’t publish a price list.
Pros:
- Ideal for Tracking Change: Performs configuration monitoring
- Helps Prevent Misconfigurations: Automatically resets settings
- Can Prevent Accidental Configuration Errors: Also identifies malicious insider threats
Cons:
- No Free Trial: You can get a demo
NNT offers a free trial of Change Tracker.
8. CrowdStrike Falcon Prevent
CrowdStrike Falcon Prevent is a range of packages in four service levels: Pro, Enterprise, Premium, and Complete.
CrowdStrike markets the Falcon Prevent range as a “next-generation antivirus.” The term is accurate, but CrowdStrike Falcon goes a lot further than just a malicious software scanner. It is a breach detection system. Falcon doesn’t just scan for known malware. It has detection systems that can catch software that is performing unexpected actions even if that program hasn’t previously been spotted and marked as malware. It is also able to detect combinations of authorized, valid software that could indicate intrusion when executed in a specific sequence.
Key Features
- Endpoint Protection: A next-generation anti-virus
- Central Coordination of All Instances Possible: Cloud-based management with other Crod
- Audit Trail for Standards Compliance: Forward logs to a SIEM
- Doesn’t Rely on Network Connections: An autonomous endpoint unit
- Part of a Suite of System Protection Services: Upgrade to an XDR
Why do we recommend it?
CrowdStrike Falcon Prevent is an anti-virus system but it works through anomaly detection. This method also catches intrusion and insider threats, which are both manual activities. The Falcon package can be scaled up to a company-wide, cloud-coordinated XDR that performs extensive threat hunting in addition to the local protection.
The philosophy behind all breach detection system is not to prevent malicious software from getting on the network – edge services are supposed to do that. The purpose of these systems is to catch malware that manages to dodge firewalls and access controls.
Falcon Prevent retreats from the network all the way to its endpoints. You shouldn’t abandon firewalls and access controls, but you should use Falcon as a fallback in case those systems fail.
Although this is a cloud-based service, its protection isn’t broken if the internet gets disconnected. The Falcon Prevent software includes on-site agents that don’t cut off when they can’t reach the controller on the CrowdStrike servers.
The system includes automated protection actions and audit trails to help users understand a concerted and repeated attack vector. The audit trail is also a good source of data protection standards compliance evidence.
Who is it recommended for?
This product is useful for constant protection because it will operate independently if the device is disconnected from the network. You would need to install Falcon Prevent on every endpoint. Adding on the Falcon Insight cloud system improves company-wide threat detection. This is a solution for large companies.
Pros:
- Doesn’t Rely on Only Log Files for Threat Detection: Uses process scanning to find threats right away
- All-in-One Tool: Acts as a HIDS and Endpoint Protection Tool
- Can Track and Alert Anomalous Behavior Over Time: Improves the longer it monitors the network
- Multi-Platform: Windows, Windows Server, macOS, and Linux
Cons:
- Only a 15-Day Trial: Would benefit from a longer trial period
9. InsiderSecurity
InsiderSecurity is a SaaS breach detection system based in Singapore. The service is a blend of software and human expertise because the company offers real expert analysis of threat event records that are raised on your network.
Key Features
- Cloud-Based Service: A SaaS platform
- Backed by Expert Security Consultants: On-call assistance
- Monitors All Activity: Scans within the network
Why do we recommend it?
InsiderSecurity is an insider threat detection system, which will also spot account takeovers. It focuses on the misuse of services in the Microsoft 365 platform and in databases. The system deploys user behavior analytics (UBA) to establish a baseline of regular activity and then it alerts when deviations in behavior occur.
The platform offers quick breach detection and automated remediation as well as online human analysis who give security guidance. In addition to the detection of rogue software, this service monitors the activities of authorized users to detect insider attacks. Basically, any execution of software on your system gets examined for intent and the security system chains back to the originator of any malicious activity.
Who is it recommended for?
This package is used by large organizations, including the government of Singapore. InsiderSecurity doesn’t publish a price list, so it is difficult to assess the platform’s appeal for small businesses. The service provides controls on privileged accounts as well and can be used to monitor administrators as well as general system users.
Pros:
- Searches for Suspicious Account Activity: Insider threats or account takeovers
- Offers an Expert Consulting Service: Ideal for larger businesses
- Provides Automated Remediation: Works with playbooks
Cons:
- No Free Trial: Designed more for large enterprises
This online service could save you from prosecution in the event of a system breach. You can get a look at how it works by requesting a demo.
10. SpyCloud
SpyCloud focuses on the activity of authorized accounts and makes sure that they don’t get hijacked. In these days where phishing scams are prevalent, it is difficult for any monitoring software to block malicious activities. If software gets installed by an authorized user or if a valid user account launches a series of legitimate programs, it is almost impossible for traditional AV systems to protect your system.
Key Features
- Scans for Hijacked Accounts: Identifies user and customer account takeovers
- Intent-Based Detection: Looks at user account actions
- Identifies Illogical Activity: Suspends suspicious accounts
Why do we recommend it?
SpyCloud is an account takeover prevention and detection system. It provides preventative account auditing to tighten up security and remove the usual methods that hackers can use to gain access, such as obvious credentials and abandoned accounts. The system also implements phishing detection. The package includes many other protection methods.
Who is it recommended for?
Any business would benefit from this package. It includes mostly preventative measures but also provides the identification of imminent or ongoing threats through measures such as Dark Web scanning. The package includes an analytics service that warns you if your company access credentials are up for sale.
Pros:
- Scans for Infrequently-Used Accounts: Suspends abandoned accounts
- Dark Web Scanning: Gets a warning if company identities are circulating on the Dark Web
- Lateral Movement Detection: Can identify attacks that are coordinated through multiple accounts
Cons:
- Actions can be Held up for Approval: Does require some manual assessments
SpyCloud gets around the problem of deciding which running processes are valid and which have malicious intent. Rather than monitoring all events on the network, it focuses on the activities of user intent. It checks on factors such as the login location matched against the known location of the user and also spots unfeasible simultaneous access by the same account.
Protecting data
Data protection is becoming increasingly more difficult every day. You can’t rely solely on a firewall and traditional antivirus to prevent data disclosure or system breaches.
These days, hackers know how to trick employees into giving away their login credentials, so it isn’t enough to just look at outsider access to your system in order to protect your company’s data stores. You need more sophisticated data protection software, such as a breach detection system.
Breach Detection Systems FAQs
What is breach detection tools?
Breach detection systems specifically look for signs of data theft. These scans can be an intrusion detection system that runs internally but it can also be implemented through Dark Web scans that look for examples of company data for sale – this would include employee credentials or customer personal information.
What are 4 methods of threat detection?
There are four methods for threat detection:
- Configuration tampering, which identifies unauthorized changes to device settings that weaken system security
- Anomaly detection, which looks for unusual network or processor activity
- Indicators of compromise, which is also called signature-based detection and looks for a sequence of actions that are known to be common to hacker activity
- Behavioral analytics, which establishes a baseline of normal activity per user account and then looks for deviations from that standard to spot account takeover or insider threats
What are the three main detection types?
There are three areas that detection systems focus on, which creates three categories of threat detection systems:
- Host-based intrusion detection systems: HIDS services look through log files
- Network-based intrusion detection systems: NIDS services scan network traffic for malicious activity and can include deep packet inspection
- Application-based intrusion detection systems: AIDS services that examine the activities of user in relation to Web applications