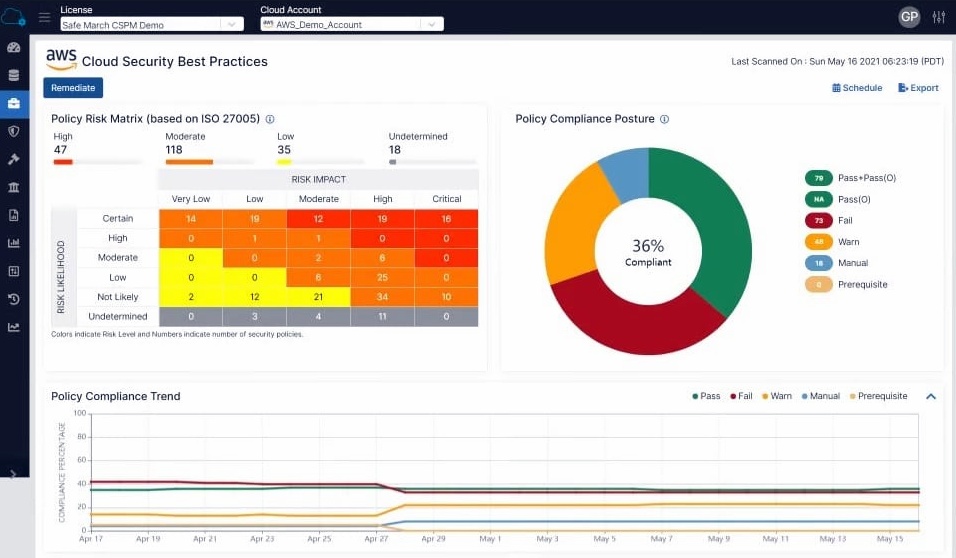
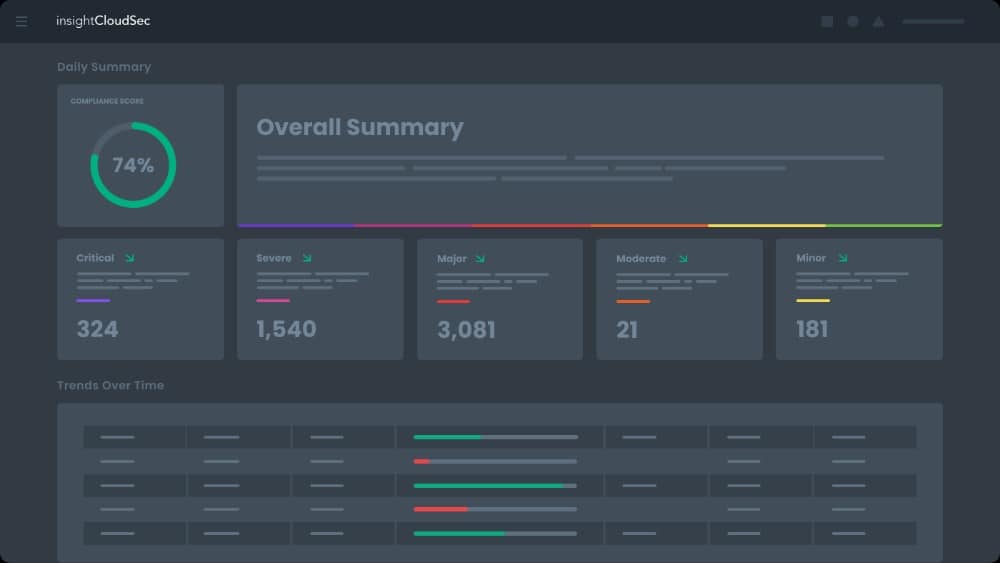
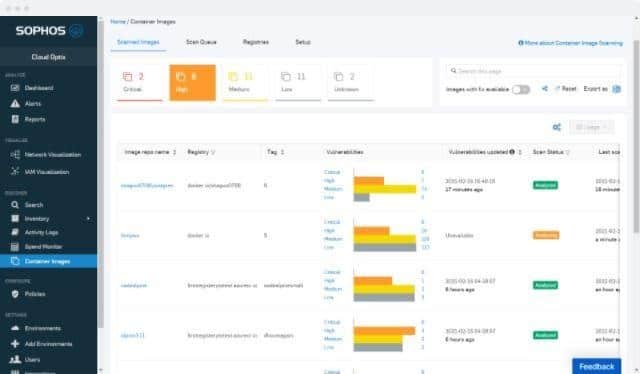
As organizations move more of their operations to the cloud, ensuring the security of cloud environments has become increasingly critical. Cloud Security Posture Management (CSPM) tools are designed to help businesses manage the security risks associated with their cloud infrastructure. These tools provide comprehensive monitoring and management of cloud environments, ensuring that configurations align with best practices, regulatory requirements, and security standards.
Here is our list of the best CSPM tools:
- CrowdStrike Falcon Horizon CSPM EDITOR’S CHOICE This service is good for use to secure operational cloud systems and also produces controls to prevent developers from creating cloud security weaknesses.
- Datadog Cloud Security Posture Management This CSPM performs continuous scans of enrolled cloud assets, looking for configuration weaknesses and any settings changes that could indicate intruder activity.
- Aikido This security testing platform can implement CSPM as part of its preventative security measures and it has a free version. This is a cloud-based system.
- Cyscale This SaaS package discovers all cloud assets and then maps them. This service not only performs security checks on cloud assets but it also identifies data stores that need strong privacy protection.
- Palo Alto Prisma Cloud This service focuses on storage account settings and user access permissions, providing compliance reporting that is great for standards auditing.
- PingSafe This cloud platform provides a range of cloud security tools for operations usage that includes a CSPM module.
- Check Point CloudGuard This platform combines workload protection and CSPM for both operations and development and can secure accounts across cloud platforms.
- BMC Helix Cloud Security This package includes automated remediation for the cloud configuration weaknesses that it discovers and also provides extensive documentation for compliance auditing.
- Zscaler Workload Posture This service includes an access rights management system as well as a CSPM service.
- Rapid7 InsightCloudSec This package includes CSPM with cloud workload protection and identity and access management plus thorough logging for compliance reporting.
- Sophos Cloud Optix This CSPM solution offers remediation guides for discovered configuration errors and documentation for compliance auditing.
With a growing number of organizations adopting multi-cloud and hybrid-cloud strategies, the need for robust CSPM solutions to prevent misconfigurations and identify potential vulnerabilities is more important than ever. CSPM tools continuously scan cloud environments for security misconfigurations. They identify compliance violations and risks that could leave an organization vulnerable to data breaches, ransomware, or other security threats.
CSPM tools help detect issues such as overly permissive access controls, unencrypted storage, and improper network configurations, offering actionable insights to rectify these vulnerabilities. By automating risk detection, CSPM solutions provide real-time visibility into security posture and allow businesses to address issues proactively before they result in costly security incidents.
This guide explores the best CSPM tools available today, evaluating each tool based on its security capabilities, ease of use, integration options, and support for different cloud platforms like AWS, Microsoft Azure, and Google Cloud. We highlight both well-established providers and newer solutions, providing a comprehensive overview of the strengths and features that set them apart.
Whether you’re looking to enhance the security of your cloud infrastructure, comply with industry regulations, or mitigate risk, this guide will help you find the right CSPM tool to safeguard your organization’s cloud environment.
Why you need a CSPM tool
CSPM tools focus on the settings of your cloud-based systems. The way you configure your cloud accounts can create opportunities for hackers. Sometimes, a security weakness is only present between services, for example in the ways they exchange data. With a CSPM tool, you can close off the vulnerabilities for each cloud service or group of cloud services.
As CSPM tools deal with cloud resources, you can expect that all of the systems that we discovered are cloud-based themselves. These security systems need to be able to cross platforms and examine multiple resources and how they operate. You need your CSPM tool to leave your cloud services in an operational state. They can be set to produce recommendations on settings rather than automatically making those changes.
CSPM tools don’t run rampant across your cloud systems. They thoroughly document all of their actions and movements. That documentation is important if you need to show standards compliance. One of the requirements of data protection standards, such as HIPAA and PCI DSS is to show that you have taken every reasonable step to protect data.
CSPM logs need to be stored because as well as proving compliance, they can be good sources of information on your total system and how different modules interact. Feeding that data through to your SIEM system can provide context to activities.
The best CSPM tools
CSPM is a relatively new field in system security, so when looking for reliable systems, there isn’t much of a service history available for any of the available systems. So, looking for a provider with a good reputation becomes an important task.
What should you look for in a CSPM tool for your business?
We reviewed the market for cloud security posture management systems and analyzed the tools based on the following criteria:
- The ability to identify underlying services
- Options for automated remediation
- CSPM activity logging
- Alerts on issue discovery
- Alert trigger tuning
- A free trial or a demo service for a no-cost assessment opportunity
- Value for money that derives from a comprehensive tool that is delivered by a reputable security software provider
1. CrowdStrike Falcon Horizon CSPM
CrowdStrike Falcon Horizon CSPM doesn’t just look for configuration weaknesses in cloud assets but searches for known targets of different hacker groups. This threat intelligence speeds up the detection of security loopholes.
Hackers like to reuse an attack strategy once they discover a weakness. They realize that they only have a narrow window of time before that weakness gets spotted and closed. They are right because CrowdStrike Horizon is onto them. As soon as an exploit is used on a resource run by one of their clients, all of their clients are hardened against it.
Key Features:
- Operates Continuously: Includes autodiscovery
- Informed by Threat Intelligence: Provided by CrowdStrike cybersecurity analysis
- Assesses Access Rights: Scans through Azure AD
- Easy to Implement: Sets itself up
The CrowdStrike system can perform an autodiscovery service once you register a cloud asset in the monitoring system. This will identify all of the supporting structures and check through the configurations of those systems as well as your primary assets.
The Horizon service will group the monitoring of assets on different cloud platforms into one dashboard. This is particularly useful if you use different services from different platforms in concert. The service can watch over virtual networks and containers as well as services on virtual servers.
Pros:
- Unifies the Monitoring of Cloud Assets Across Platforms: Also examines the platforms
- Includes the Examination of Virtual Systems: Infrastructure-as-Code and containers
- Implements Compliance Reporting: Logs discoveries and fixes for compliance auditing
- Provides Remediation Guides: Supports technicians
Cons:
- Doesn’t Fix Problems Automatically: Requires skilled technicians
On the discovery of a security weakness, the CrowdStrike system will raise an alert. The tool also examines access rights and can assess your account structure in Azure AD. The system won’t fix a problem but will give you information on what needs to be done. Security experts in the CrowdStrike support team are also on and to give you advice on the tasks that need to be performed. You can register for a free trial of CrowdStrike Horizon CSPM.
2. Datadog Cloud Security Posture Management
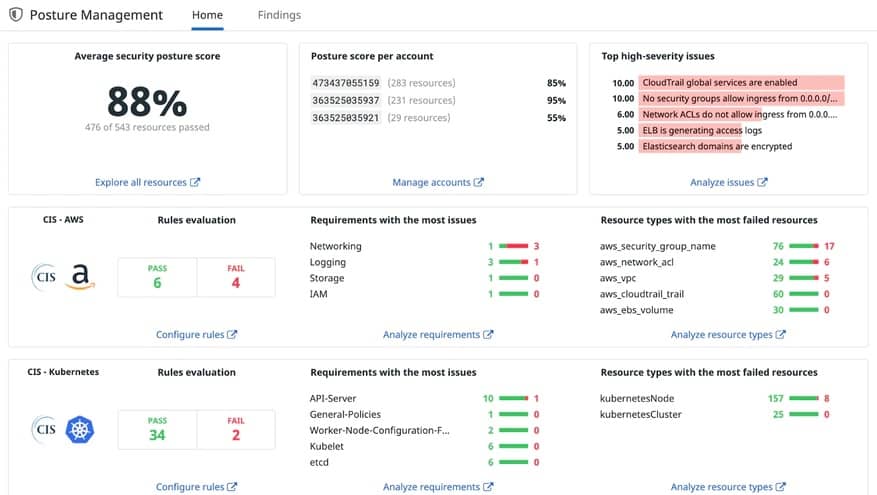
Datadog Cloud Security Posture Management can be tailored to report for compliance to CIS, PCI DSS, HIPAA, and GDPR. This tool runs continuously and it can identify changes in the settings of cloud services, which could include changes made by the provider.
Key Features:
- Easy to Set Up: Deploys pre-configured rules
- Covers Cloud Platforms and Containers: Also infrastructure as code
- Assigns a Security Score to Each Problem: Aggregates an overall score
The Datadog CSPM tool can be used by security specialists who don’t have technical knowledge of managing computer systems because the interface offers visual methods to tailor the system that don’t require any programming skills to operate.
The package includes pre-written libraries of detection rules with options for tailoring for specific data protection standards. When a misconfiguration is discovered, the Datadog system generates an alert. This notification details the specific asset configuration that needs attention and how it should be changed to tighten security.
The findings of the CSPM tool are automatically logged and corrections are also recorded. This documentation is stored and kept available for compliance reporting.
Pros:
- Screens that List Checks on Each Asset: Prioritized action list
- Scalable Pricing: Priced per host
- Cross-Modular Benefits: Can be integrated with other Datadog security systems
Cons:
- Doesn’t Provide Automated Remediation: Requires experienced cybersecurity experts
Datadog Cloud Security Posture Management is a subscription service and it can be combined with other Datadog security systems, such as its SIEM or its Cloud Workload Security package. You can get a 14-day free trial of this and any other Datadog module.
3. Aikido

Aikido is a security testing platform that can be applied to preventative scanning or Web application testing. The cloud platform includes a CSPM service and you can still use the service for SAST, DAST, and SCA as well for your DevOps pipeline.
As the Aikido service is focused on code development and deployment, its CSPM is designed for use as a pre-deployment security check. The logic behind this strategy is that there is no point using all of the tools in the Aikido platform to ensure that your Web applications and SaaS services are inviolable if you are then going to put it on top of a cloud platform that is vulnerable to attack.
Key Features:
- Validates cloud infrastructure: Checks the configurations of cloud hosting systems and platform services
- Infrastructure-as-Code scanning: Scans your delivery services for security weaknesses
- Container and Kubernetes cluster scanning: Looks for outdated runtimes within containers and validates container settings
- Severity scores: Allocates a risk score to each problem
The Aikido CSPM is not a standalone product. It is intended for use as part of the release mechanism for new SaaS products and Web applications. The platform checks can be built into the CI/CD system security testing process and can even loop back to interactions with the newly written code to ensure that all security features between the application and the infrastructure coordinate.
When the Aikido scanner checks through your cloud services, it will list any of the security weaknesses that it discovered. Each issue is given a severity score and that provides you with a prioritized list of problems that need to be addressed. Some security issues are interdependent – that is one problem in one feature will also weaken the security of another service. In such cases, the Aikido scanner “deduplicates,” which means it groups those red flags together, letting you know which is the core error that needs to be fixed to address all of the group.
Pros:
- Integrates into continuous testing: Built into the CI/CD pipeline process
- Addresses issues in context: Platform weaknesses might only become apparent in the context of the new modules that you are going to run on them
- Simultaneous application testing: The security of applications can be considered in the context of its infrastructure
- Rescanning for fix verification: Fix a problem and then run the scanner again
Cons:
- Not a standalone CSPM: Operates as part of a release mechanism for applications
Aikido is a cloud-based SaaS platform and it is available in four editions. The first plan is free to use; it includes the CSPM but will only scan one cloud account. Successively higher plans provide more capacity up to the top edition, which has no limit on the cloud services that it will scan. You can examine the entire Aikido platform by starting with the free plan.
4. Cyscale
Cyscale is a SaaS platform that offers a range of cloud security services that includes a CSPM module. The first element that you will encounter when assessing the security of your cloud assets is the Cyscale Security Knowledge Graph. This is the product of a discovery process that identifies all of your cloud-based assets and maps them.
You will be able to see which cloud assets you are using and how they interact with each other. The Knowledge Graph is, in itself an eye-opener. It can be used to properly assess your subscription and save money by ditching unused services or adjusting the reserved spaces that you have over-provisioned.
Key Features:
- Discovery and Mapping: Creates the Security Knowledge Graph
- Subscriptions Assessment: Identify underused or forgotten subscription services
- Cross-Platform Operations: Scans AWS, Azure, GCP, and Alibaba Cloud
- Provides Best Practices: For each discovered application and platform
- Cloud Security Assessments: Identifies configurations that weaken security
The Cyscale system scans across hosting platforms, including AWS, Azure, Google Cloud, and Alibaba Cloud. On identifying the purpose, host, and usage of each asset, the Cyscale service recommends security best practices for that resource. The CSPM reports on how the configuration of the asset deviates from the ideal and offers a fix for these problems that can be implemented by applying a suggested appropriate template from the Cyscale library.
The service is able to reassess your entire system if it is set up to implement a specific data protection standard. The platform offers compliance with GDPR, HIPAA, PCI-DSS, ISO 27001, and NIST. All of the discoveries and resolution actions implemented with the platform are documented to provide evidence for compliance reporting.
Pros:
- Automated Configuration Improvements: Implemented through templates
- Compliance Enforcement and Reporting: For GDPR, HIPAA, PCI-DSS, ISO 27001, and NIST
- An API is Available: Can integrate CSPM checks into CI/CD pipeline testing
Cons:
- No On-Premises Version: Only available as a cloud-based SaaS platform
There is only one edition of Cyscale – every subscriber gets full access to the entire platform with all of its features. There are three plans offered, which are sized and relate to the number of assets that the system will be required to monitor. You won’t actually know how many assets you are dealing with when you first start your engagement with the platform because the definition of what counts as a single asset is a little complicated and many new users are not completely aware of exactly what cloud assets their system incorporates – thanks to the inclusion of APIs, frameworks, and microservices. You can get a full account of that asset count by taking out the 14-day free trial of Cyscale.
5. Palo Alto Prisma Cloud
Palo Alto Prisma Cloud is a platform of security services for cloud assets and it includes a CSPM tool. Other modules available from the platform include Cloud Workload Protection for processes running on virtual servers, Cloud Network Security, Cloud Identity Security, and Cloud Code Security. Thus, by deploying the full combination of Prisma Cloud services, you can protect all of your cloud assets.
Key Features:
- Unified Security for Multiple Platforms: Can operate across cloud platforms within a scan cycle
- Tailored to Compliance Requirements: Specify a regulation to follow
- Part of a Cloud-Native Application Protection Platform: Along with Cloud Workload Protection, Cloud Network Security, Cloud Identity Security, and Cloud Code Security
After enrolling all of your cloud assets in the monitoring service, you get continuous checks performed on their configurations. This extends to a drill down through to supporting cloud infrastructure. The Prisma Cloud service will also check through your access rights and permissions and produce recommendations for security tightening.
Pros:
- Identifies Out-of-Bound Risks: Applies dynamic testing
- Provides Solution Recommendations: Doesn’t automatically fix weaknesses
- Documents Findings and Remediation: Useful for compliance auditing
Cons:
- No On-Premises Version: Only available as a cloud-based SaaS platform
The Prisma Cloud system will raise an alert if it discovers a security weakness. However, it can also be set to automate certain tasks, which amount to a holding operation to close down exploits until you have the chance to get to the dashboard and make a decision about a permanent change. You can get a 15-day free trial of Prisma Cloud.
6. PingSafe
PingSafe is a Cloud-native Application Protection Platform that includes a CSPM module. The Cloud Security Posture Management service in this system will scan compute and storage accounts on AWS, Google Cloud Platform, Digital Ocean, and Azure. It also has detection capabilities for a number of well-known cloud SaaS packages.
The core CSPM service scans the configurations of cloud accounts and SaaS packages, looking for exploits. The service acts as a vulnerability scanner for cloud assets and it has a built-in list of more than 1,400 known weaknesses. This scanner operates constantly, adding new exploits to its search patterns as soon as they are discovered.
Key Features:
- Asset Discovery: Continuous vulnerability scanning
- Alerts for Identified Weaknesses: Response automation
- Compliance Reporting: SOC2, PCI DSS, HIPAA, NIST, and ISO 27001
The PingSafe system interfaces with other applications in order to automate threat detection, reporting, and response. These include Slack, Jira, Webhooks, PagerDuty, Splunk, and Sumo Logic. For example, the alerts that are raised by PingSafe can be channeled through Slack or PagerDuty and log records can be sent to Splunk for deeper analysis.
When the system detects a vulnerability, it generates a record in the service’s cloud-based console as well as raising an alert. The record of the exploit explains which asset was being scanned, what the weakness is, and how to fix it. Automatic remediation can be set up for the system. However, some problems might require manual actions or changes to corporate policy and working practices.
Pros:
- An Exploit Database: Contains more than 1,400 vulnerabilities
- Advice for Manual Fixes: Optional automated responses
- User Account Auditing: In conjunction with infrastructure code scans
Cons:
- No Free Trial: Access a demo instead
The PingSafe platform contains other security modules and you get access to these as well with your subscription. These systems include an Offensive Security Engine, which tests suspected vulnerabilities by running attacks. The tool will also scan through Infrastructure-as-Code. It looks through your cloud-hosted software looking for code injection and strips it out on discovery, leaving the original code in place. The service also provides a Cloud Workload Protection Platform for live threat detection. You can request a demo to find out more about PingSafe.
7. Check Point CloudGuard
Check Point CloudGuard is an impressive cloud security system from one of the world’s leading cybersecurity providers. The CloudGuard platform includes a menu of cloud security services that includes a Cloud Security Posture Management module. The other units in the platform are Cloud Application Security, Cloud Workload Protection, Cloud Intelligence, and Threat Hunting, and Cloud Network Security and Threat Prevention.
Key Features:
- Cross-Stack Scanning: Networks, applications, and workloads
- Access Rights Auditing: Permissions management
- Part of a CNAPP: Along with Cloud Application Security, Cloud Workload Protection, Cloud Intelligence, and Threat Hunting, Cloud Network Security and Threat Prevention
The CSPM tool in the plan includes a continuous threat protection service that examines account takeover attempts and behavior anomalies. So, this is a combined service that provides threat detection as well as cloud security posture management.
The Check Point system is heavily geared toward compliance enforcement and it can be tailored to specific standards. The CloudGuard system will operate across platforms, identifying configuration management issues and raising alerts to draw your attention to those weaknesses.
Pros:
- Cross-Platform Scanning: AWS, Azure, and GCP
- Continuous Monitoring: Includes autodiscovery
- Alerts for Discovered Weaknesses: Remediation is a manual process
Cons:
- Doesn’t Cover On-Premises Systems: Cloud only
The CloudGuard service can integrate into the major cloud platforms, such as AWS, GCP, and Azure, which enables it to automatically adjust settings and clean out abandoned accounts to keep your cloud assets shipshape. You can get a demo of the CloudGuard system.
8. BMC Helix Cloud Security
BMC Helix Cloud Security is a comprehensive configuration scanner for AWS, GCP, and Azure services. The package includes automated remediation actions and it is easy to set up without the administrator needing any programming of operating system command-line utility knowledge.
This system can cover multiple accounts on different platforms in one security management service account. The system is also able to examine the settings and operations of containers.
Key Features:
- Cross-Platform Supervision: IaaS and PaaS from AWS, Azure, and GCP
- Automated Remediation: No coding required
- Cloud Server Security: For AWS EC2 and Azure VMs
As well as managing the settings of cloud resources, this system can observe the operations of computing accounts, such as AWS EC2, and Azure VMs. this makes the service a cloud workload protection system as well as a cloud security posture management tool.
The CSPM tool can be tuned to enforce specific data protection standards through the application of out-of-the-box templates for PCI DSS, CIS, and GDPR. On discovering a system configuration weakness, the tool will raise an alert, which can be channeled through ITSM systems as a ticket, or trigger a remediation playbook.
Pros:
- Options Over Responses: Choose to automate or just notify
- Integrates with ITSM Ticketing Systems: Automated ticketing for security weakness discoveries
- Compliance Management: For CIS, PCI DSS, and GDPR
Cons:
- Doesn’t Include Development Testing: It is an operation and asset management tool
The BMC system is a reliable service from a strong, well-supported brand. You can contact the BMC Sales Team to learn more.
9. Zscaler Workload Posture
Zscaler Workload Posture is provided by a major player in the SASE field so this tool can be combined with a virtualized network or secure application access controls to create a very secure combination of cloud assets that work seamlessly into your corporate infrastructure.
As a standalone module, the Workload Posture service offers access controls as well as CSPM services. Both strands of this module operate continuously, so the package doesn’t just verify the security of your cloud assets, it also ensures tight security on an ongoing basis.
Key Features:
- Implements Zero Trust Access: Combines CSPM and access controls
- Integrates Virtual Assets: Virtual networks and application access
- Cross-Platform Supervision: Can include on-premises systems in its protection services
The Zscaler system operates as an API that you add to the settings of your cloud accounts. This sets the service running in the background for those assets. The tool will crawl each registered asset and discover related cloud systems, checking through the configuration of those hidden supporting systems as well as the cloud assets that you know about.
The package also performs risk assessment for sensitive data stores and it can be tailored to specific data protection standards.
Pros:
- Sensitive Data Protection: Restricts access to files
- Compliance Management: CIS, NIST, PCI DSS, and HIPAA
- A DevOps Service: Includes development scans, release testing and operations security scanning
Cons:
- Silent Operations: The background nature of the system might make you wonder whether it is running
Zscaler is an easy-to-use and unobtrusive service that provides a dashboard to display all discovered issues. The service also provides remediation workflows that you choose to implement or can decide to bypass. You can request a demo of Zscaler Workload Posture.
10. Rapid7 InsightCloudSec
Rapid7 InsightCloudSec is a CSPM tool that forms part of a wider platform of system security modules. Rapid7 puts all of its stable cybersecurity systems on its cloud-based Insight platform.
Key Features:
- Ongoing CSPM: Continuous operations
- Cloud Access Controls: Assesses device posture as well as user authentication
- Workload Protection: Scans live events
The InsightCloudSec unit itself contains three modules: Cloud Security Posture Management, Cloud Workload Protection, and Cloud Identity and Access Management. These three tools together provide security checks and ongoing monitoring for both static and dynamic assets, covering both processors and storage space.
The InsightCloudSec service can also be integrated with other Insight products, which include InsightIDR, an XDR, and SIEM package. The InsightCloudSec service can be applied to development environments as well as to operations. This security system will operate across platforms and will supervise the security and operations of containers as well.
Pros:
- Suitable for DevOps Protection: Development assurance, release testing, and operations security
- Covers Container Security: Also Infrastructure-as-Code
- Integrates with Other Rapid7 Tools: Part of a wider platform of security services
Cons:
- No Free Trial: Get a demo
The InsightCloudSec system offers options over the automation of remediation both for CSPM issues and for workload protection tasks. Request a demo to see how the InsightCloudSec system works.
11. Sophos Cloud Optix
Sophos Cloud Optix is a new product from a leading cybersecurity systems provider. The Cloud Optix package is a CSPM tool that provides system hardening and compliance reporting. This service will unify the security monitoring of assets on many platforms – including containers. It is suitable for both development environments and operations usage.
Key Features:
- Cross-Platform Monitoring: AWS, Azure, and GCP
- Compliance Reporting: For FFIEC, GDPR, HIPAA, PCI DSS, and SOC2
- Cloud Configuration Management: Includes Kubernetes scanning
The Cloud Optix service operates continuously and offers live risk assessment in its dashboard. It works through access rights issues and will spot combined anomalies across assets.
Pros:
- Continuous Risk Assessment: Also assesses cloud spend for possible savings
- Thorough Issue Documentation: Provides remediation guides
- A DevOps System: Suitable for development, release testing, and operations
Cons:
- Doesn’t Automate Remediation: You still need cybersecurity experts on the payroll
The Cloud Optix system will alert you if it spots a security issue. This leaves the responsibility for fixing problems in your court. You can get a 30-day free trial of Sophos Cloud Optix.