On the surface, all DDoS protection tools look the same, as they claim to provide real-time visibility and comprehensive mitigation. But the differences become clear when an attack happens and you are left grappling with containing the damage.
For IT admins and Managed Service Providers (MSPs), finding the right DDoS protection service is often driven by the following pain points:
- Frequent DDoS attacks are causing disruptions to your service, eventually eroding customer trust.
- Your business does not have the tools to identify a DDoS attack before it causes damage.
- You need automated damage mitigation workflows to handle attacks immediately without manual intervention.
- You require logging features to meet compliance requirements.
- You need a tool that scales well across multiple environments like cloud and on-prem.
When your selected tool addresses the above pain points, your organization benefits from uninterrupted productivity and increased stakeholder trust and confidence.
In this article, we use our expertise in cybersecurity to help you identify the best DDoS protection tool that can safeguard your organization from these malicious attacks.
Our list of the best DDoS protection tools and managed services:
- Sucuri Website Firewall EDITOR’S CHOICE This WAF inspects all incoming HTTP/HTTPS traffic, blocks suspicious traffic. Utilizes advanced geo-blocking capabilities.
- SolarWinds Security Event Manager A comprehensive tool that can detect and monitor a host of network events including DDoS attacks. Maintains attacker IPs logs and even blocks IPs.
- Indusface AppTrana A web application firewall that includes vulnerability scanning, DDoS protection, and bot control detection. This edge services bundle also includes a content delivery network.
- Link11 Cloud-based protection service can detect and mitigate attacks. Easy to deploy, uses AI and dashboard gives good view of server behavior.
- CloudFlare Network capacity can handle some of the largest known attacks. Uses an IP reputation database to manage a wide range of attack types.
- AWS Shield Analyzes incoming traffic using flow monitoring, packet filtering, and prioritizing traffic in real-time.
- Akamai Prolexic Routed Block DDoS attacks such as UDP floods, SYN floods, HTTP GET, and POST floods.
If you need to know more, explore our vendor highlight section just below, or skip to our detailed vendor reviews.
Best WiFi DDoS protection tools and managed services highlights
Top Feature
Advanced Layer 7 DDoS mitigation and malware removal in a single platform
Price
Basic: $229/year, Pro: $339/year, Business: $549/year, Junior Dev: $999.98/year
Target Market
SMEs and large organizations in IT services and e-commerce
Free Trial Length
Website Firewall (WAF): 30-day free trial, Website Security Platform: 30-day money-back guarantee
Additional Benefits:
- Protects against DDoS and zero-day exploits
- Includes malware cleanup and site restoration
- Cost-effective all-in-one solution for small and mid-sized companies
- Geo-blocking and IP whitelisting support
Features:
- Malware detection and removal
- Web Application Firewall (WAF)
- Layer 7 DDoS mitigation
- Geo-blocking and IP whitelisting
- Real-time traffic inspection
Top Feature
Fully managed Web Application Firewall with automated scanning and manual pen testing
Price
Starts at $99/app/month
Target Market
Managed Service Providers (MSPs)
Free Trial Length
AppTrana Advance edition offers a 14-day free trial
Read more ▼
Top Feature
AI-powered DDoS detection and mitigation across layers 3–7
Price
Negotiated pricing: contact the vendor for details
Target Market
Enterprises requiring high-performance DDoS protection
Free Trial Length
No free trial
Read more ▼
Top Feature
Integrated DDoS protection and global CDN for high availability and performance
Price
Pro: $20/month, Business: $200/month, Enterprise: Negotiated pricing
Target Market
Businesses of all sizes and industries
Free Trial Length
Free version available
Read more ▼
Top Feature
Real-time DDoS mitigation for AWS-hosted applications
Price
Advanced plan starts at $3,000/month
Target Market
Enterprises using AWS services
Free Trial Length
No free trial (Standard edition is free)
Read more ▼
Top Feature
Carrier-grade cloud-based DDoS mitigation with zero-second response
Price
Negotiated pricing: contact the vendor for details
Target Market
Large enterprises and service providers requiring high-capacity, globally distributed DDoS protection
Free Trial Length
Free trial available upon request
Read more ▼
What is a DDoS attack?
During a DDoS attack, an attacker uses a network of compromised computers called a botnet to send traffic to your network. The traffic overwhelms consumers network resources and makes services unavailable.
For example, you may have trouble accessing the internet or using an application. Common DDoS attacks include ICMP flood, SYN flood, Ping of Death, Slowloris, and more. Each of these service attacks targets different vulnerabilities and must be defended against in different ways.
Related post: How to Stop a DDoS Attack
Key Points to Consider Before Purchasing a DDoS Protection Service Platform
Before you purchase a DDoS protection platform, here are a few aspects to consider:
- Mitigation Speed: A key consideration is how quickly can the tool detect a DDoS attack. Does it have the automation workflows to mitigate or neutralize the attack with minimal human intervention?
- Compatibility: One of the aspects that is often overlooked is compatibility with your network. Check if the tool fits well into the cloud, on-premises, and hybrid environments, and pick a DDoS protection platform accordingly.
- Real-Time reporting: Visibility is critical when you’re handling cybersecurity attacks. Select a platform that offers live dashboards and analytics to help you make data-driven decisions quickly.
- Vendor support: Excellent customer and technical support is important, so make sure the platform has robust 24/7 support. It also helps if the vendor can offer a Service Level Agreement (SLA), as this can guarantee base metrics.
- Security and Compliance: If you’re in an industry or region that requires you to adhere to strict regulations, look for a tool that meets these requirements.
How to Calculate the ROI of DDoS Protection Platforms
Investing in a DDoS protection platform can provide excellent Return on Investment (ROI), provided you accurately evaluate the cost of the platform against its anticipated returns. Below is a structured approach to calculate the ROI of DDoS protection platforms.
Step 1: Establish Your Metrics
Before moving to the tool, evaluate your current state. In particular, understand how much you are losing with every DDoS attack. Some metrics that can help you calculate this financial loss are:
- Frequency of DDoS attacks
- Average duration of downtime during each attack
- Revenue loss for every downtime hour
- Cost of incident response
- Cost of existing DDoS tool
- Larger financial impact, if any, like customers leaving due to service disruptions if it’s an eCommerce site or the penalty incurred when you don’t meet your SLAs
Step 2: Know the Cost of the New Platform
Next, calculate how much the new platform is going to cost you. Make sure to include the following costs.
- Licenses and subscriptions
- Setup and configuration time and the cost of paying an expert to handle these aspects
- Training costs for end-users of the platform
- Cost of maintaining the software
Step 3: Calculate the Benefits
Evaluate how much you will save by implementing the new tool. Some areas to look into are:
- How much downtime and the resulting revenue will it save?
- Lower incident response costs with more automation
- Reduced penalties due to non-compliance
- Savings accrued by eliminating other tools
- More income from lower disruptions and fewer SLA penalties
Step 4: Put the Numbers Together
With all this data, it’s time to crunch them to estimate the cost of a tool.
Your annual savings are (Reduced Downtime * Revenue Lost per Hour) + (Reduced IT Hours * Hourly Rate) + (Avoided Compliance Fines) + (Security Tool Consolidation Savings)
Total Investment is everything in Step 2.
ROI (%) = ((Annual Cost Savings – Total Investment) / Total Investment) * 100%
Use Our DDoS ROI Calculator
We’ve put together a calculator that can make this calculation easy for you.
Calculate Your DDoS Protection ROI
The best DDoS protection tools & anti-DDoS software
DDoS prevention software is designed to block malicious traffic from reaching your network. Each solution is different in its approach due to the variety of DDoS attacks you can encounter on a daily basis.
Let’s have a look at some of the best DDoS protection tools as well as anti-DDoS software available.
1. Sucuri Website Firewall (LEARN MORE)
Best for: Websites
Relevant Businesses/Industries: SMEs and large organizations in IT services and e-commerce.
Price: Starts at $229/year for the Basic platform, $339/year for the Pro platform, $549/year for the Business platform, and $999.98/year for the Junior Dev.
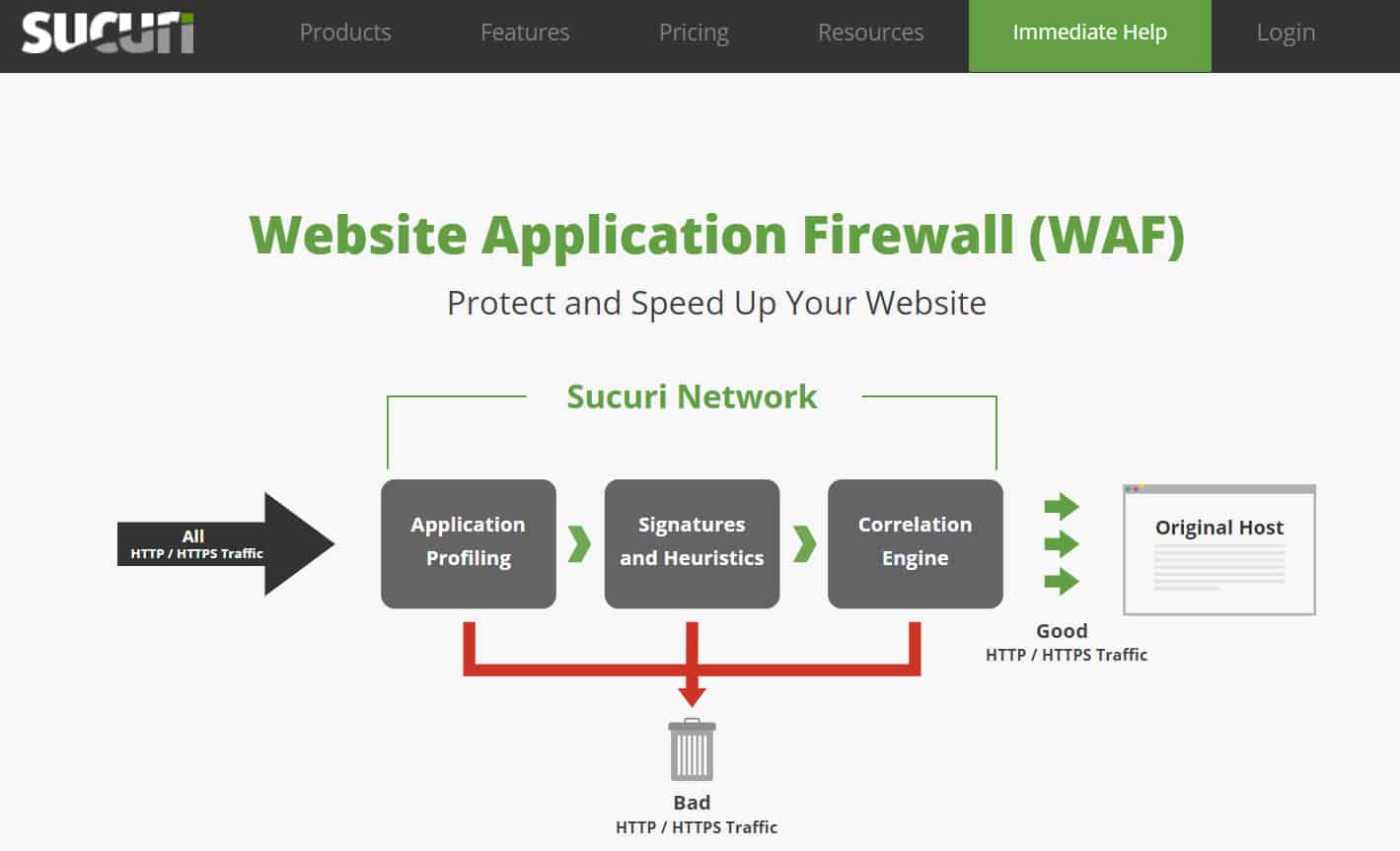
Sucuri Website Firewall is a website application firewall that can prevent DDoS attacks and zero-day exploits. Sucuri Website Firewall inspects all incoming HTTP/HTTPS traffic and blocks suspicious traffic from reaching your service. This stops botnets from being able to put your site offline.
Sucuri’s Key Features:
- Malware removal: Identifies and removes malware from your Web server
- Cleans up after hackers: Spots changes and repairs the damage
- DDoS mitigation: This is a proxy server that receives your traffic and only passes through real traffic
Unique Buying Proposition
Sucuri offers an all-encompassing website security solution that includes malware detection and removal, performance optimization, and a Web Application Firewall (WAF). Surprisingly, most major DDoS or WAF providers don’t include direct malware cleanup services or site remediation, making Sucuri a standout service, particularly for small and mid-sized companies that need a more cost-effective solution for each of these needs. Together, all these features protect companies from many cybersecurity solutions, making it a cost-effective choice for small to medium-sized businesses.
Feature-in-Focus – Layer 7 DDoS Mitigation
Sucuri’s Website Firewall provides advanced Layer 7 (application layer) DDoS mitigation by filtering malicious traffic before it reaches the origin server. This feature analyzes HTTP requests in real time to identify and block suspicious patterns like bot activity, repeated login attempts, and high request rates of specific resources.
Why do we recommend it?
Sucuri Website Firewall is a cloud-based edge service that doesn’t need to be hosted or maintained, but instead diverts all traffic on the way to a web asset and filters out attacks. The protected system only receives the valid traffic and the value of the Sucuri service is its ability to tell the difference between malicious and genuine traffic.
For additional protection Sucuri Website Firewall uses geo-blocking. Geo-blocking blocks visitors to your site from the top three countries with DDoS attacks. However, if you want to control access to a smaller degree you can whitelist IP addresses that you trust so that you can communicate with your team without them being blocked.
There are four versions of Sucuri Website Firewall available to purchase: Basic, Pro, Business, and Custom Solutions. The Basic version starts at $9.99 (£8.19) per month. The Pro version starts at $19.98 (£16.39) per month with SSL certificate support.

Who is it recommended for?
The potential market for Sucuri Website Firewall is the same as that for Indusface AppTrana. The two tools work in a very similar way and each acts as a proxy server, receiving all traffic on behalf of the protected website. So, you don’t need to dedicate any specialist cybersecurity staff to managing your site’s protection. An important difference between these two services is that the Sucuri system is significantly cheaper and so it is more likely to appeal to small businesses.
Pros:
- Emergency Repair: Sign up for the package when you are already under attack and get all threats stopped and damage repaired
- Regular Scans: Sweeps through your system every 30 minutes
- Content Delivery Network and Offloading: Sucuri serves visitors and your own site becomes a reference
Cons:
- No Self-Hosting Option: This is a cloud service
The Business version costs $69.93 (£57.35) per month with additional features. The Custom Solutions are customizable packages on their website where you can chat to an online assistant and learn more.
EDITOR'S CHOICE
Sucuri Website Firewall is our top pick for anti-DDoS software because of its advanced security features that effectively protect websites from distributed denial-of-service (DDoS) attacks. The firewall provides real-time monitoring and defense mechanisms that detect and mitigate large-scale DDoS attacks, safeguarding websites against performance degradation and downtime. By blocking malicious traffic before it reaches the website, Sucuri ensures that only legitimate users can access the site, preserving its availability even during a DDoS attack. This proactive approach is critical for businesses that rely on their websites for e-commerce, customer interaction, or service delivery. In addition to its DDoS protection, the Sucuri Website Firewall offers an impressive set of security features, including website application firewall (WAF), malware detection, and bot mitigation. The WAF filters out malicious requests, protecting websites from a range of attacks, including SQL injections, cross-site scripting (XSS), and other common web vulnerabilities. The firewall integrates seamlessly with other Sucuri tools to provide a multi-layered security strategy. Its cloud-based architecture ensures that the website’s server is not burdened by the traffic filtering process, improving overall site performance and reducing the risk of server overloads during an attack. Sucuri’s Website Firewall also provides detailed traffic analytics, giving administrators insight into attack patterns and allowing for rapid adjustments to security policies.
Download: Learn More
Official Site: https://sucuri.net/
OS: Windows Server
2. SolarWinds Security Event Manager
Best for: DDoS Threat Detection and Log Analysis
Relevant Businesses/Industries: Enterprises of all sizes and industries
Price: Starts at $3,292
SolarWinds Security Event Manager is a DDoS protection tool with event log monitoring capabilities. Event logs are a key resource for detecting when malicious entities are trying to disrupt your network.
SolarWinds SEM ‘s Key Features:
- Log Manager: Gathers, consolidates, and files log messages
- SIEM Tool: Implements automated threat detection
- Manual Analysis: Data viewer with analytics tools
- Traffic Feed: Add network traffic data to get DDoS detection
Unique Buying Proposition
SolarWinds SEM specializes in real-time log analysis and event correlation. With this information, organizations can quickly detect and respond to security threats. Its ability to centralize and analyze logs from various sources provides deep insights into network activities, making it especially valuable for enterprises that require comprehensive Security Information and Event Management (SIEM) capabilities.
Feature-in-Focus – DDoS Traffic Pattern Analysis via SIEM
SolarWinds SEM analyzes network logs to detect unusual traffic spikes and potential attacks. It also correlates data from multiple sources, like firewalls, IDS/IPS, and network traffic monitors, to identify anomalies. Based on these findings, it sends automated alerts and responses to help IT teams act quickly.
Why do we recommend it?
SolarWinds Security Event Manager is more of a DDoS detection system than a DDoS protection service. This is because the tool collects log messages and analyses them and one of the things that it looks for is a suspicious traffic surge. The tool is able to indicate that a DDoS attack is in progress and will raise an alert to attract the attention of technicians. The package doesn’t include any DDoS mitigation services, however.
To protect you from attackers SolarWinds Security Event Manager maintains a list of known bad actors so that the program can automatically block an IP from interacting with your network. The list is community-sourced so that you stay protected from the most recent threats.
During an attack, you can also configure alerts to notify you when a suspicious source is sending you traffic. The logs recorded by SolarWinds Security Event Manager can also be used for DDoS mitigation and retrospective analysis. You can filter through results to find accounts, IPs, or time periods to analyze in closer detail.

Who is it recommended for?
SolarWinds Security Event Manager is a high-capacity log management tool and security detection service. It is suitable for use by large organizations. The package is expensive and offers too much functionality for the needs of small businesses. Those organizations that need to prove compliance with data protection standards particularly need this tool.
Pros:
- Anomaly-Based Detection: Looks for unusual patterns in activity
- Zero-Day Protection: Can spot new attack strategies and irregular intruder activity
- Remediation Playbooks: Link actions to alert conditions to get threats shut down automatically
- Compliance Reporting: DISA STIG compliance
Cons:
- Only for Windows Server: Not available for macOS, Linux, or cloud platforms
SolarWinds Security Event Manager starts at a price of $4,655 (£3,819). You can also download the 30-day free trial.
3. Indusface AppTrana
Best for: Application-Layer Protection
Relevant Businesses/Industries: Managed Service Providers (MSPs)
Price: Starts at $99/app/month
AppTrana is a fully-managed WAF, DDOS, and Bot mitigation solution from Indusface. The edge service bundle includes a Web Application Firewall, vulnerability scanners, a patching service, and DDoS protection. The service can absorb extreme volumetric attacks and is able to distinguish DDoS from genuine surges in traffic.
AppTrana’s Key Features:
- Web Application Firewall (WAF): Also known as a Web Application and API Protection (WAAP) system
- DDoS Behavior-Based Detection: Identifies attacks rather than traffic surges
- Unmetered Service: Traffic floods won’t cost you more
- Application Security: Scans inbound traffic for threats
- API Protection: Prevents hackers exploiting your APIs
Unique Buying Proposition
A special aspect of AppTrana is its fully managed Web Application Firewall that includes continuous risk detection through automated scanning and manual penetration testing. This proactive approach ensures that vulnerabilities are identified and addressed quickly, which in turn, provides businesses with a high level of security without the need for extensive in-house resources.
Feature-in-Focus – Managed DDoS Protection with Adaptive Filtering
AppTrana offers continuous traffic monitoring and filtering to proactively identify attack patterns. Accordingly, it adjusts its mitigation strategies to block volumetric, protocol-based, and application-layer attacks. Unlike traditional static rules, AppTrana’s adaptive filtering dynamically responds to new DDoS tactics to keep businesses protected against sophisticated attack methods.
Why do we recommend it?
Indusface AppTrana is a Web Application Firewall and is delivered from the cloud, so it provides a range of web protection services and easily plugs into your system without you having to install any software. The tool is managed by Indusface technicians and all the user needs to know is how to access the cloud-hosted console to see whether any DDoS attacks have been attempted.
AppTrana uses its database to develop rules and alert conditions for your websites. Sites are monitored 24/7 to make sure no attack slips through the net. The software can also automatically detect botnets based on their behavior and block them. This means that the botnet cannot disrupt your site. To keep the network protected from Layer 3 attacks, AppTrana has been built on AWS to help resist common volumetric attacks.
The vulnerability scanning service in AppTrana references the OWASP Top 10 Threats and the SANS 25 Vulnerability list. The service immediately fixes any vulnerabilities that it discovers through patching. Vulnerability scans are conducted regularly and automatically. Other features in the AppTrana bundle include SSL offloading and a content delivery network for site acceleration.

There are two editions of AppTrana: Advance and Premium. The Advance service is the edge system described above, and it costs $99 per protected app per month. The Premium version is a managed website security service. This includes the services of network security analysts to identify attacks and adapt security protection strategies. While vulnerability testing is included in this plan, those checks are supplemented by human pen testers. The Premium plan costs $399 per protected app per month.
Who is it recommended for?
Any business can use AppTrana because it is a remote service and you don’t need any involvement in running the service. That means small businesses don’t need to have any technical expertise on staff or pay for expensive consultants in order to get full protection against DDoS attacks against their web assets. Large organizations also benefit from this configuration because their existing IT Department won’t be stretched by extra tasks once the WAF is in operation.
Pros:
- Security Audits: A vulnerability scanner that is tuned to local and industry requirements
- Automated Patching: Virtual patching filters out threats to known software vulnerabilities
- Traffic Scrubber: Blocks chaff while letting the real traffic through
- AI-Based Bot Detection: Looks at inbound and outbound traffic patterns to identify external controls and fake transactions
- Blacklisting: Blocks traffic from known hacker IPs and dodgy locations
Cons:
- Cloud Platform: Not available for self hosting
AppTrana Advance edition is available for a free trial.
4. Link11
Best for: AI-Driven DDoS Mitigation
Relevant Businesses/Industries: Enterprises
Price: Negotiated Pricing
Link11 is a cloud-based DDoS protection tool. The system can detect and mitigate web and infrastructure DDoS attacks through layers 3-7 in real time. The software uses artificial intelligence to detect an attack.
Link11’s Key Features:
- Proxy Service: Will protect networks and web assets
- DDoS Protection: Absorbs traffic floods
- Content Delivery Network: Speeds up website response times
Unique Buying Proposition
Link11 leverages artificial intelligence to provide real-time DDoS protection. Its AI-driven approach detects and mitigates attacks with minimal disruption to services. This cutting-edge technology is useful for organizations with modern infrastructure and next-gen applications.
Feature-in-Focus – AI-Powered DDoS Defense
Link11’s AI engine continuously learns from traffic patterns to identify malicious activity within milliseconds. It also analyzes connection requests, packet headers, and behavior anomalies to block threats without human intervention. In the process, it reduces false positives and provides uninterrupted service availability.
Why do we recommend it?
Link11 is a specialized DDoS protection system rather than a feature of a wider web application firewall or edge service bundle. The system is highly regarded and quickly spots DDoS attacks. The ability to perform at speed and accurately identify malicious traffic can make or break a DDoS protection system because no one wants genuine traffic to be held up or blocked. Link11 uses AI to sharpen its DDoS blocking service.
The AI analyzes the sequences of known-attack patterns and uses this data to compare with live usage. If a connection to the network is behaving the same way as a potential attacker the platform can respond immediately with a notification via SMS once a threat is detected.

In terms of setup, Link11 is very easy to deploy because it is run in the cloud. You don’t need to set up additional hardware and in a matter of minutes, you can configure the platform to protect your network infrastructure from an attack. The monitoring dashboard provides you with a centralized view of traffic, application and server behavior protection service can detect and mitigate attacks. Easy to deploy, uses AI and dashboard gives good view of server behavior, so you can see what’s going on.
There is also a reporting feature so you can generate reports on security events. The program enables you to schedule reports or generate them manually depending on your needs.
Who is it recommended for?
Link11 is a good choice for a large business that is dependent on the availability of its websites to maintain profitability. There are two aspects to this package that will put small businesses off. The first is that rival systems combine DDoS protection with other services, such as a content delivery service, which provides all of the edge services that a website needs. The other detraction is that Link11 doesn’t publish a price list and you can’t just sign up through an automated online process.
Pros:
- Filters Out Attack: All your inbound traffic goes to Link11 servers
- Hacker Protection: Your own IP address is kept secret, hackers can only go to the Link11 server
- Bot Detection: Identifies malicious activity by behavior or source
Cons:
- No Price List: No free trial
Link11 is one of the most widely-used DDOS protection platforms on this list because it combines simplicity with top-notch automation. The AI is excellent at navigating the latest threats. If you’d like to view the price of Link11 you will have to contact the company directly.
5. Cloudflare
Best for: Globally Distributed Networks
Relevant Businesses/Industries: Businesses of all sizes and industries
Price: Pro plan starts at $20/month, Business plan costs $200/month
Cloudflare is a high-performance DDoS protection service that has a network capacity of 30Tbps, 15 times that of the largest DDoS attack ever recorded. The high capacity makes Cloudflare resistant to even the most powerful attacks. To keep up with new forms of attack the software uses an IP reputation database which blocks new threats across 20 million different properties.
Cloudflare’s Key Features:
- Free Edition: Suitable for small businesses
- DDoS Protection: This is Cloudflare’s core service
- SSL Certificate: Includes in all plans
Unique Buying Proposition
Cloudflare combines DDoS protection with a global Content Delivery Network (CDN) to boost both security and performance. This integration supports faster load times for websites while providing better protection against attacks.
Feature-in-Focus – Automatic DDoS Attack Detection and Mitigation
Cloudflare’s DDoS protection uses an automated detection system to identify attacks of all sizes, including large-scale volumetric attacks and low-and-slow Layer 7 threats. It also taps into its global network to absorb malicious traffic before it can impact target websites. The system continuously updates mitigation techniques based on attack patterns to protect businesses against new and evolving DDoS threats.
Why do we recommend it?
Cloudflare just about invented the modern DDoS service and that makes this a very difficult service to beat. The company has massive capacity to absorb very large traffic floods and that also makes it the first choice for many businesses. Since its inception as a DDoS protection service, Cloudflare has expanded into other edge services and can combine DDoS protection with content delivery, failover protection, and malware protection.
The defenses of Cloudflare have been designed to cover a range of DDoS and data breach attacks. For example, the product uses rate limiting to block network visitors with unusually high request rates. Likewise, it uses a Content Delivery Network or CDN to ensure the network stays available. The CDN is supported by 193 data centers across 90 countries.

There are four different versions of Cloudflare; Free, Pro, Business, and Enterprise. The Free version doesn’t cost anchoring for individuals with a personal website. The Pro version costs $20 (£16) per month with a Web Application Firewall designed for professional websites, blogs, and portfolios.
Who is it recommended for?
Cloudflare is appealing to any business that runs a website. The company has created a Free plan, which includes many other edge services. So, this is probably the natural number one choice for startups and small businesses. The vast capacity of this system to absorb attacks will also appeal to very large organizations that are regularly subject to DDoS attacks.
Pros:
- Plans for Different Sizes of Businesses: All types of businesses with web assets are catered for
- PCI DSS Compliance: Included in the top two plans
- Uptime Guarantee: For the two highest plans
Cons:
- Reporting Not So Great: Analytical features could be better
The Business version costs $200 (£164) per month with the option to use custom WAF rules, 100% uptime SLA and the fastest speed. The Enterprise version is a customizable package with a named solution engineer and is priced on a case-by-case basis. You can check out their pricing plans or download the free trial version.
6. AWS Shield
Best for: Cloud-Native Protection on AWS Infrastructure
Relevant Businesses/Industries: Enterprises using AWS services
Price: Advanced plan starts at $3,000/month
AWS Shield is a managed DDoS protection solution that uses flow monitoring to analyze incoming traffic. By monitoring flow data AWS Shield can detect malicious traffic in real-time. The solution also uses other defense measures like packet filtering and prioritizing traffic to control the management of traffic in the network.
AWS Shield’s Key Features:
- Standard Edition Included with all AWS Services: You don’t need to pay anything
- DDoS Protection: Also provides a dashboard that shows attack histories
- DDoS Consultants: Human expert advice in the higher plan
Unique Buying Proposition
A highlight of AWS Shield is its deep integration with other Amazon Web Services. This seamless integration provides scalable and flexible security solutions for applications hosted on AWS.
Feature-in-Focus – Intelligent Threat Detection with AWS WAF Integration
AWS Shield integrates with AWS WAF to provide intelligent DDoS threat detection and automatic mitigation. It combines real-time traffic analysis with predefined rulesets to quickly spot unusual spikes in traffic and immediately apply countermeasures.
Why do we recommend it?
AWS Shield is available in a number of editions that offer increasingly more complicated services and capabilities. However, the basic package is enough for those seeking DDoS protection and that edition is free to use. The higher plans enable experienced cybersecurity experts to write their own firewall rules and there is also an option to get automated responses implemented.
You can also write rules with AWS WAF to defend against application-layer attacks. For more advanced protection there is AWS Shield Advanced. AWS Shield Advanced uses mitigation capacity to minimize the effect of larger DDoS attacks. There is also a dedicated response team on hand to assist with manual mitigations for more complex attacks.
There are two main versions of AWS Shield available on the market: AWS Shield Standard and AWS Shield Advanced. AWS Shield Standard is free and provides protection against common network and transport DDoS attacks.

Who is it recommended for?
AWS Shield is certainly designed as a strong rival to Cloudflare. Its free tier is a great marketing advantage when pitching for small business customers. However, there is one attribute of the AWS Shield that limits its appeal. That is, this system is only designed to protect AWS accounts, such as the EC2 system. The paid plans are quite expensive and they are suitable for large enterprises.
Pros:
- Widely Available: All AWS customers get this service
- Self-Service WAF: Included in both plan levels
- Application Protection: Blocks attempts to install malware
Cons:
- No SLA in Free Service: Service Level Agreement only in the paid plan
AWS Shield Advanced includes additional defense features for Amazon Elastic Compute, Amazon CloudFront, AWS Global Accelerator, and Elastic Load Balancing. AWS Shield Advanced costs $3,000 (£2,460) per month plus additional usage fees. You can get started with AWS Shield here.
7. Akamai Prolexic Routed
Akamai Prolexic Routed is a managed DDoS security service that can block DDoS attacks such as UDP floods, SYN floods, HTTP GET, and POST floods. Akamai Prolexic Routed has zero-second mitigation so that threats are spotted the moment they occur. However, if you require more support you have the assistance of the Security Operations Center to fall back on 24/7.
Akamei Prolexic Routed’s Key Features:
- DDoS Absorption: Protects sites and web assets
- Attack Analysis: Show attack events in the dashboard
- Cloud Platform: Offers an on-premises version from Corero
Unique Buying Proposition
Akamai offers large-scale DDoS protection to protect the most demanding web environments. Its carrier-grade infrastructure provides high availability and resilience against massive DDoS attacks, making it ideal for large enterprises and service providers requiring extensive protection.
Feature-in-Focus – Cloud-Based Scrubbing Centers
Prolexic has 32 cloud-based scrubbing centers globally accounting for 20+ Tbps defense capacity. With this arsenal, it filters out malicious traffic before it reaches enterprise networks. Also, it can absorb large-scale volumetric attacks while maintaining service availability.
Why do we recommend it?
Akamai Prolexic Routed is a cloud service that is provided by one of the leading cybersecurity firms in the world. The reputation of Akamai is itself enough to get this product on our list. However, Akamai doesn’t rest on its laurels and provides a very powerful DDoS protection service that rapidly scans all incoming traffic at a rate of 400 Gbps. The speed of the Akamai system and its global distribution in 16 centers around the world provide this service with its ability to compete with Cloudflare.
Network traffic monitoring is another feature that Akamai Prolexic Routed uses to catch attacks early on. You can view real-time traffic data through the dashboard. You can also fall back on the 8.0 Tbps of bandwidth supplied by Akamai’s global network with 19 distributed scrubbing centers distributed across the world.
Who is it recommended for?
The Akamai service is aimed at big businesses and doesn’t offer a free tier, which shows that the company realizes that Cloudflare is unbeatable in that sector. Akamai doesn’t publish a price list, which is another reason that small businesses probably won’t go for this service.
Pros:
- High Capacity: Total platform capacity is more than 250 Tbps
- Router and Firewall Rules: Provides access control lists
- Dual Stack: Operates with IPv4 and IPv6 addresses
Cons:
- No Price List: You need to contact the Sales Department
Overall, if you’re in search of a high-performance managed DDoS protection service then Akamai Prolexic Routed is worth a look. If you want to view the pricing for Akamai Prolexic Routed then you will have to contact the sales team directly. You can start a free trial here.
Our Methodology for Choosing Anti-DDoS Software
There are many anti-DDoS software available in the market today, with each having its own pros and cons. In this review, we aim to only feature the best DDoS protection service platforms that offer core protection for enterprises. We don’t discuss every criterion, but only the ones mentioned below.
1. Effectiveness Against Multi-Layered DDoS Attacks
The tool you select must defend against different types of attacks like volumetric, protocol-based, and application-layer attacks. It should also offer real-time mitigation with low false positives to avoid disrupting legitimate traffic.
2. Automated Threat Detection and Response
Given the growing advancements, it’s a good idea to look for tools that use AI and behavior-based detection to identify and mitigate attacks without manual intervention. Automated responses speed up the mitigation process.
3. Scalability and Performance
The solution must scale well to handle traffic spikes and large-scale attacks without causing service degradation. Performance metrics like latency impact and mitigation speed were used in our evaluation.
4. Security and Compliance
Security measures like encryption, access controls, and compliance with industry standards (e.g., SOC 2, ISO 27001, PCI DSS) have become mandatory for businesses that handle sensitive data. We strive to look for tools that have this built-in protection.
5. Monitoring and Reporting
Comprehensive dashboards, traffic analytics, and detailed incident reports make it easy to track attack patterns and assess the effectiveness of defenses. Real-time visibility can also help security teams to mitigate the impact of these attacks. Extensive reporting can also help meet your compliance requirements.
6. Integration with Existing Infrastructure
Integration with your existing systems is a key aspect, as it saves time and effort. Understand your existing infrastructure and look for compatible tools. We have picked tools that work across multiple environments.
7. Customer Support and Documentation
Effective customer support, including 24/7 availability, expert guidance, and well-documented best practices, can greatly provide the confidence needed to handle DDoS attacks. Our picks have good post-sale support for a good user experience.
Broader B2B Software Selection Methodology
We believe the vendor’s credibility is just as important as the software itself. When researching and reviewing Anti-DDoS platforms, we also assess:
- Cost versus the value provided
- Vendor’s track record in cybersecurity
- Customer feedback and real-world performance experiences
- Company’s transparency regarding product capabilities and limitations
- Vendor’s ability to support long-term client security needs
While we may not discuss every criterion in each review, we highlight standout strengths and potential concerns to help you make informed decisions.
For more details, check out our complete B2B software evaluation methodology.
Comparitech SupportScore Methodology
Our proprietary score calculates how well a vendor offers the required support for their DDoS protection platform. This score takes into account every touchpoint, right from the initial setup and deployment to supporting attacks and generating compliance reports.
The factors based on which we assess vendor support are:
- 24/7 support teams
- Availability of incident response teams during attacks
- Frequency with which a vendor updates the tool’s mitigation algorithm
- Self-service resources like videos and documentation
- Employee count
Using the above criteria, each vendor receives a 0-10 SupportScore, with weighted factors based on their real-world impact on security and business continuity.
For a deeper look at our evaluation criteria, visit our SupportScore Methodology page.
Why Trust Us?
At Comparitech, we take cybersecurity seriously. Our team of researchers and analysts has years of experience testing, reviewing, and evaluating security solutions across different areas, including DDoS protection platforms. We don’t just skim through vendor websites. Rather, we dive deep into product features, test real-world performance when possible, and analyze vendor transparency, security posture, and long-term reliability.
When you rely on Comparitech, you’re getting well-researched, vendor-neutral insights that help you make informed decisions about DDoS protection for your business.
Protect Yourself with a DDoS Protection Service
It only takes one attack to put your network offline and cost you thousands or tens of thousands of dollars worth of damage.
Whether you choose to use an in-house product like SolarWinds Security Event Manager or a managed DDoS protection service like Akamai Prolexic Routed, it is important to be aware of what online services you’re protecting.
For example, if you want to protect your website then a website application firewall like Sucuri Website Firewall is likely to be your best choice. Remember that not all DDoS attacks are the same, and attackers look to strike your defenses where you least expect it.
Further reading: Best WAFs Reviewed – Buyer’s Guide
DDoS Protection FAQs
Do VPNs protect you from DDoS attacks?
Yes. A VPN will protect you against DDoS attacks in two ways. First, it hides the real address of your device – all traffic goes to the VPN rather than directly to you. Secondly, the VPN has a great deal of connection capacity and so is able to absorb the volumes of traffic that would overwhelm your computer. Get a VPN service with a static IP address if you expect incoming connections.
How long can a DDoS attack last?
Commercial DDoS services offer attack durations for as little as 5 minutes. Hardcore hacker-team DDoS attacks can last 24 hours or even as long as 72 hours.
How long does it take to recover from a DDoS attack?
DDoS attacks don’t cause any physical damage, they just block legitimate users from getting access to your site or service. Technical recovery is immediate because as soon as the fake connection requests stop, legitimate requests will get through. Reputation damage can take a long time to recover from.
Can you reverse a DDoS?
In theory, you can DDoS back to an address that DDoSed you. However, there isn’t much point in doing that because the computer that attacked you is just infected by a bot. You won’t get to the real attacker. Also, a botnet that runs an attack can contain hundreds of thousands of computers so you would tie up your own resources for a long time in revenge attacks on all of them.










