A web application firewall (WAF) protects web applications from various types of cyber threats, vulnerabilities, and attacks.
It acts as a barrier between the web application and the internet, monitoring and filtering incoming and outgoing HTTP/HTTPS traffic to identify and block malicious or suspicious activities.
Web application firewalls play a crucial role in protecting web applications, ensuring data integrity, preventing unauthorized access, and maintaining the availability of web services.
With a number of WAF solutions on the market, our buying guide will help you choose the right one for your organization.
Here is our list of the best web application firewalls:
- Sucuri Website Firewall EDITOR’S CHOICE This is a cloud-based security solution designed to protect websites from a variety of threats, including DDoS attacks, malware, and hacking attempts while enhancing site performance through caching, load balancing, and content delivery optimization.
- Fortinet FortiWeb An edge service bundle that offers a web application firewall, an SSL off-loader, and a load balancer in a cloud service, an appliance, or VM.
- Imperva Cloud WAF A cloud-based web application firewall with an onsite equivalent appliance called Imperva WAF Gateway.
- Barracuda Web Application Firewall Available as a SaaS system, a private cloud, an appliance, or a VM, this WAF also includes vulnerability scanning and data loss prevention.
- Prophaze Web Application Firewall Customizable, all-in-one Multi/Hybrid/Private/SaaS/
Kubernetes based WAF with Bot Protection, RASP, DDoS, CDN solution. Fast on-boarding, unlimited SSL Certs and 24/7 support. - MS Azure Web Application Firewall A cloud-based WAF that can protect web servers anywhere. This is a metered service.
- F5 Essential App Protect A cloud-based WAF that is aimed at non-technical customers, so it is easy to set up and manage.
- Cloudflare WAF Cloud-based solution that can be combined with DDoS protection.
- Akamai Kona Site Defender Combines an offsite WAF and DDoS protection.
The Best Web Application Firewalls
Many web application firewall providers try to capture as much of the market as possible by offering their WAF systems in as many configurations as possible. So, in many cases, the same WAF can be provided as a software package that runs on a virtual machine, as a network appliance, or as a cloud-based SaaS system. It is also possible to get a cloud-based WAF as a fully managed service.
Our methodology for selecting a Web application firewall
We reviewed the market for WAFs and analyzed the options based on the following criteria:
- A cloud-based system
- Integrated DDoS protection
- Cloaking for a business’s true IP address
- Secure channel for traffic forwarding
- Fast data processing that doesn’t slow down regular traffic
- A free trial or a demo option that enables an assessment without payment
- Value for money from a multi-purpose protection system at a reasonable price
Using this set of criteria, we looked for edge platforms that provide Web application firewall functions among other services, and offer subscription pricing with no setup costs.
1. Sucuri Website Firewall (LEARN MORE)
The Sucuri Web Application Firewall is part of a suite of website protection measures. The Sucuri cloud-based protection system is an online service. Your website’s address is hosted at Sucuri’s server, also all of your Web traffic goes there first.
Key Features:
- Accelerated Content Delivery: Implements caching and optimization for improved website performance.
- Proactive DDoS Protection: Actively safeguards websites against distributed denial-of-service attacks.
- Plan Levels to Suit Different Sizes of Businesses: Basic, Pro, and Multi-Site.
- Virtual Patching: Protects vulnerable Web systems.
- SSL Protection: Checks for SSL certificate validity and warns when it is about to expire.
Why do we recommend it?
Sucuri Website Firewall is a very close rival to the StackPath system. This cloud-hosted edge service platform includes a firewall and DDoS blocking to protect Web servers. Rather than including a content delivery network, this tool provides transfer optimization with caching on the Sucuri server.
The Sucuri service filters out malicious traffic through a range of techniques. The company maintains a database of attack signatures, which is constantly updated, so your website benefits from protection strategies learned by Sucuri when it is defending other sites.
The service package includes performance optimization and DDoS protection. The Sucuri server blocks malicious traffic and forwards all bona fide requests onto your Web server. This process happens so quickly that visitors will not notice any slowing in the delivery of your Web pages.
Delivery performance is enhanced by caching, which means even if your site is down for maintenance, visitors will still be able to access your Web pages.
Who is it recommended for?
Website owners should asses the Sucuri service alongside the StackPath option because both are similar services and are suitable for use in exactly the same scenarios.
Pros:
- Enhanced Traffic Filtering: Effectively differentiates between legitimate and malicious traffic for website protection.
- Intelligence-Driven Security: Leverages an extensive database of threat intelligence for up-to-date protection.
Cons:
- Self-Setup Requirement: Users need to configure their connection to the service, which may be challenging for some.
The Sucuri Web Application Firewall is available as a subscription service, and pricing starts from $9.99/month for their basic package. View plan details on their website.
EDITOR'S CHOICE
Sucuri Website Firewall is our top pick for a Web application firewall because of its strong security features, ease of use, and performance enhancements. As a cloud-based solution, it offers comprehensive protection against a wide range of web threats, including DDoS attacks, SQL injection, cross-site scripting (XSS), and zero-day vulnerabilities. One of Sucuri’s most impressive features is its virtual patching and hardening capabilities, which automatically apply security updates to protect against known vulnerabilities. This ensures continuous protection without requiring manual intervention, a critical advantage for businesses without dedicated security teams. In addition to security, the Sucuri Website Firewall enhances website performance. It leverages global content delivery network (CDN) integration and caching to improve page load times, reduce server load, and ensure consistent uptime, even during high-traffic periods or attacks. This combination of security and performance optimization makes it ideal for businesses prioritizing both user experience and protection. This system is compatible with all major CMS platforms, including WordPress, Joomla, and Magento. Sucuri also provides a user-friendly dashboard with detailed reporting, enabling administrators to monitor traffic, block threats, and analyze incidents in real-time. The 24/7 customer support ensures that any issues are quickly addressed, enhancing its reliability. Unfortunately, Sucuri doesn’t offer a demo or a free trial. However, you can sign up for the system and you get your money back if you cancel within the first 30 days.
Download: Get a 30-day moneyback guarantee
Official Site: https://sucuri.net/website-security-platform/signup/#firewall
OS: Cloud based
2. Fortinet FortiWeb
The FortiWeb WAF from Fortinet is offered as a SaaS system, as a VM-based software package or as an appliance. The software for the WAF is also available for private cloud hosting and can be implemented as a container-based system.
Key Features:
- Versatile Deployment Options: Available as SaaS, VM, appliance, or in private cloud environments.
- AI-Driven Threat Intelligence: Utilizes advanced AI techniques for real-time threat detection and mitigation.
Why do we recommend it?
Fortinet FortiWeb is a Web application firewall that has more deployment options than most of the other options on this list. It is available as an appliance, as a virtual appliance, or as a SaaS package. Fortinet is famous for its signature appliance firewalls, which are custom built for the provider with its own design of microchips in them. The provider is a little behind the pack in the FWaaS field, though. However you buy it, Fortinet supplies the firewall with a threat intelligence feed.
The FortiWeb system operates a DDoS protection service when accessed as the cloud service or as an appliance. The web application firewall examines all traffic traveling to the network and deploys AI-based machine learning to detect suspicious activity. FortiWeb also uses a threat intelligence feed to keep up to date with the latest hacker attack strategies and looks for patterns of behavior that deviates from the calculated norm and seems to be leading towards a typical attack.
The WAF can be combined with an SSL off-loader and a load balancer.
Who is it recommended for?
Fortinet offers the best value for money when its products are combined. The optimized hardware devices from the company can be loaded up with multiple security software and this is where the Fortinet brand excels. If you don’t want to buy all of your cybersecurity systems from Fortinet, the advantages of the Fortinet FortiWeb service reduces considerably.
Pros:
- Flexible Implementation: Offers a range of deployment options to suit various organizational needs.
- Integrated Security Solutions: Allows for seamless integration with other Fortinet security products for comprehensive protection.
- Self-Managed System: Empowers organizations with full control over their web application firewall settings.
Cons:
- Dependent on Fortinet Ecosystem: Optimized for use within the Fortinet security suite, which might not appeal to users of other security solutions.
The cloud service is charged for by subscription and its dashboard can be accessed through any standard browser from anywhere. The network appliance version is available in eight models that vary in capacity from 25 Mbps to 20 Gbps.
3. Imperva Cloud WAF
Imperva is a major player in the cybersecurity industry and its WAF services are comprehensive. The online version of Imperva’s web application firewall acts as a proxy server, catching all incoming traffic and cleaning it up before passing it on to the protected web server.
Key Features:
- Proxy Service Integration: Channels traffic through a secure proxy for enhanced protection.
- Continuity Assurance: Ensures website availability with robust failover mechanisms.
- Virtual Patching Capability: Offers immediate patching solutions for newly identified vulnerabilities.
Why do we recommend it?
The notable feature of the Imperva Cloud WAF is that the edge service package that it is part of provides virtual patching of your system. The platform also scans incoming traffic for harmful actions, blocks DDoS attacks, and implements continuity through a content delivery network.
The Imperva Cloud WAF service is partnered by other web enhancement services, such as a content delivery network (CDN), which speeds up the delivery of web pages and also provides constant availability should the main server go down for maintenance or get damaged in some way. The WAF includes a virtual patching service, which applies all patches needed on the protected system and provides site availability while the web server is bounced.
Who is it recommended for?
Imperva offers this system as a FWaaS as part of an edge services package. You can also opt to get it on a hardware appliance. The system is also available as a managed service for businesses that don’t have their own cybersecurity experts on staff.
Pros:
- Comprehensive Web Hardening: Strengthens web server security to prevent attacks and unauthorized access.
- Advanced DDoS Protection: Effectively mitigates distributed denial-of-service attacks, safeguarding website operations.
- Speed Enhancement: Implements mechanisms to accelerate content delivery, enhancing user experience.
Cons:
- Hardware Requirement for On-Premise: Requires investment in physical hardware for on-site deployment, which could be costly.
Imperva offers a managed service option for its Cloud WAF, which includes specialists and technicians to run the security software. An on-site version of the Imperva security service is available on a range of network appliances, called Imperva WAF Gateway.
4. Barracuda Web Application Firewall
The Barracuda Web Application Firewall is available as a SaaS system, an appliance, as a virtual appliance, or for installation on a private cloud account. This flexibility of implementation means that the WAF could be suitable for businesses of any size.
Key Features:
- Flexible Deployment Models: Available in various formats including SaaS, appliance, and virtual appliance.
- Malware and Infected Page Blocking: Actively identifies and blocks malicious content and compromised web pages.
- Enhanced Traffic Security: Provides robust protection against harmful web traffic and potential breaches.
Why do we recommend it?
Barracuda Web Application Firewall is a cloud-based system that scans traffic traveling both into and out from a Web server. This system offers protection from attack and also blocks data theft, so it is both a WAF and a data loss prevention (DLP) service. The service is also available as a virtual appliance or a physical network device.
The WAF channels all traffic for a web server – both inbound and outbound. It is able to spot and block traffic-based attacks, malware, and on-page attack attempts. The service uses both blacklisting, to block hackers, and whitelisting, to allow access to valid users only from specific devices.
The traffic monitoring system of the Barracuda WAF also provides data loss prevention. This enables businesses to comply with data protection standards, such as PCI DSS. Inbound traffic is blocked if malformed connection requests are detected, signifying a DDoS attack. In these circumstances, the WAF server absorbs and discards volume attacks, allowing genuine connection requests through.
Who is it recommended for?
This service is best suited for large businesses that need to comply with PCI DSS because it has compliance auditing and reporting built into it. Data loss prevention forms an important incentive for choosing this tool.
Pros:
- Comprehensive Data Protection: Offers strong safeguards against data theft, aiding in compliance with data protection standards.
- Effective DDoS Mitigation: Implements advanced strategies to prevent and counter DDoS attacks.
- Versatile Implementation Options: Suitable for a wide range of business sizes due to its diverse deployment methods.
Cons:
- Cost of Physical Appliances: The investment in physical appliances for on-premises deployment may be significant.
The network appliances offered by Barracuda vary in capacity from 25 Mbps to 10 Gbps.
5. Prophaze Web Application Firewall
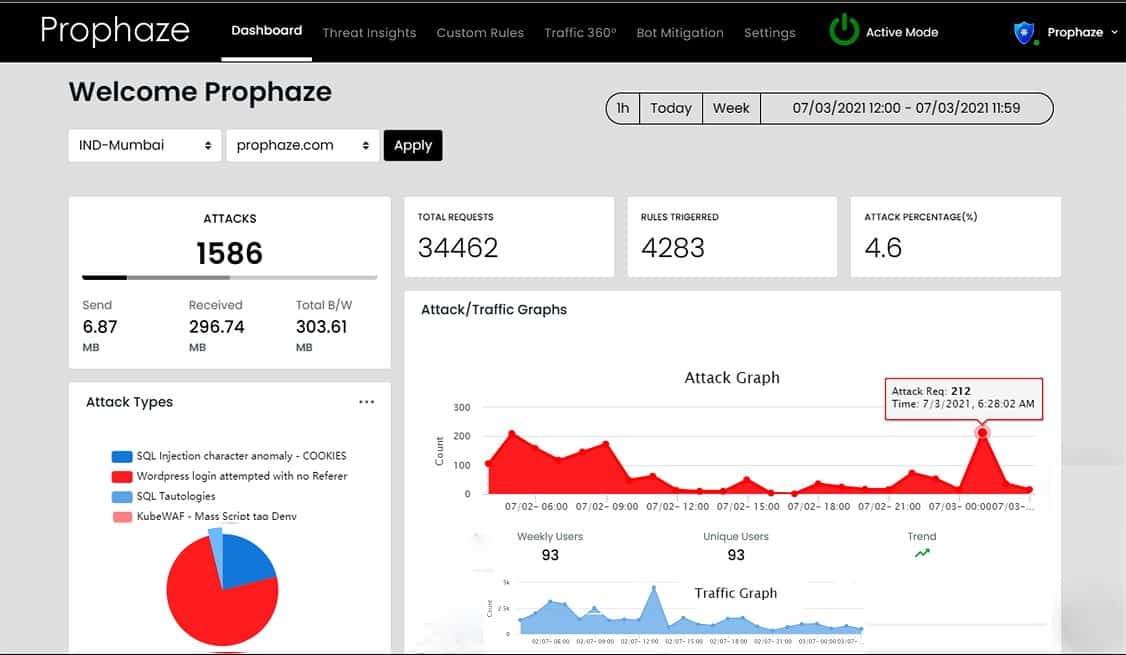
Prophaze WAF-as-a-Service is a cloud-based proxy server that acts as a web application firewall. The Prophaze service includes AI routines that refine detection rules by adjusting the baseline of standard behavior. This feature helps to reduce the number of false alarms and helps to give genuine site visitors unrestricted access.
Key Features:
- AI-Driven Traffic Analysis: Utilizes artificial intelligence to refine detection and reduce false positives.
- Rapid Onboarding: Promises setup and deployment within just 15 minutes.
- Comprehensive Bot and DDoS Protection: Offers extensive safeguards against automated threats and distributed denial-of-service attacks.
Why do we recommend it?
The Prophaze Web Application Firewall uses AI-based baselining, which is a typical feature of intrusion detection systems. When applied to traffic, the behavior analytics in the Prophaze package will adjust its treatment of specific traffic types and redefine its definitions of malicious traffic. This function makes pre-written security policies more attractive because companies that have traffic patterns and request expectations that diverge from the standard rules, that unusual traffic will not be blocked by the firewall.
The Prophase system itself operates with Kubernetes containers and is also able to monitor the performance and security of your own system’s Kubernetes activities as well as performing traditional hacker activity detection.
You don’t need to be an expert to use the Prophaze WAF. The company aims its product at small businesses, so it is designed with non-technical users in mind. The screens in the dashboard are accessed through any standard browser and they are clear and well laid out.
Who is it recommended for?
Prophaze is a good choice for businesses that want to manage their WAFs themselves but don’t have high-quality security expertise to precisely define security policies. As these policies get adjusted over time by the WAF’s behavior analysis, mistakes made in the definition of security policies will eventually be corrected.
Pros:
- Flexible Protection Mechanisms: Adapts to unique traffic patterns, offering customized security.
- User-Friendly Interface: Designed for ease of use, even for non-technical users.
- Robust Multi-Platform Support: Compatible with a variety of hosting environments, including Kubernetes.
Cons:
- Lack of On-Premise Version: Does not offer an on-site deployment option, which might be a limitation for certain use cases.
Features include DDoS protection and virtual patching. It hardens the protected system and prevents data loss, aiding towards compliance to GDPR, HIPAA, CCPA, PCI-DSS, and SOC2.
6. MS Azure Web Application Firewall
Microsoft Azure is a well-known hypervisor system that is one of the most successful cloud platforms available. Like AWS, the Azure division of Microsoft doesn’t just offer the platform system for cloud services, it also produces a range of software that provide utilities to other systems. The Web Application Firewall is one of these products.
Key Features:
- Robust Brand Reputation: Backed by Microsoft’s extensive expertise in cloud services.
- Comprehensive Traffic Filtration: Thoroughly scrutinizes incoming and outgoing web traffic for security threats.
- Data Protection Focus: Emphasizes safeguarding data, particularly useful for organizations with strict data security requirements.
Why do we recommend it?
Microsoft Azure Web Application Firewall is a competent service that both protects Web assets from hacker attacks and scans outgoing traffic to block data theft. Although hosted on Azure, this system is not just for protecting Azure and you don’t need to host your Web assets on the Azure platform in order to benefit from this tool.
As with any WAF, this service acts as a proxy. All of your inbound traffic flows through the Azure server first, it is inspected, and suspicious traffic gets blocked, with all other traffic passed on to your web server. This edge service model also makes the Azure WAF an excellent facility for DDoS protection and load balancing. All outbound traffic from your web server also gets routed through the WAF, which examines traffic for data loss events. So, this is a complete two-way web traffic security service.
The system automatically tracks for the top ten vulnerabilities as logged by the Open Web Application Security Project (OWASP). It has standards rules embedded in it, but your server administrator can adjust these and add on custom rules as well.
What makes Azure different from the other edge services in this list is that it isn’t charged for by subscription. Instead, it has a metered charge rate. This fact and the absence of setup charges make this an excellent service for startups and small businesses as well as the largest corporations in the world.
Who is it recommended for?
While most cloud-based WAFs are charged for by an advanced payment-based subscription and hardware AF require a big upfront purchase, this system is billed retrospectively on actual data throughput. This means that the Azure WAF is a good choice for small businesses with low throughput volume because their monthly bill may well work out cheaper than the price they would pay for a subscription service.
Pros:
- Data Loss Prevention: Includes features that help prevent unauthorized data exfiltration.
- Flexible Charging Model: Offers a pay-as-you-go pricing model, making it attractive for businesses with variable web traffic.
- DDoS and Vulnerability Scanning: Provides robust protection against volumetric attacks and scans for common vulnerabilities.
Cons:
- Potential for Unexpected Costs: The retrospective billing model could lead to unpredictable expenses, especially for high-traffic sites.
The price tariff of Azure WAF is calculated on a combination of an hourly rate and a data throughput rate and charged monthly in arrears. That’s a much lower upfront cost than other cloud-based subscription WAFs, which expect the subscription fee to be paid in advance. What’s even better is that the first 10 TB of data per month is free for all but the lowest traffic levels and businesses with a lot of traffic gets up to 40 TB of throughput per month for free. The Azure Web Application Firewall can be examined as part of a 12-month Azure free trial.
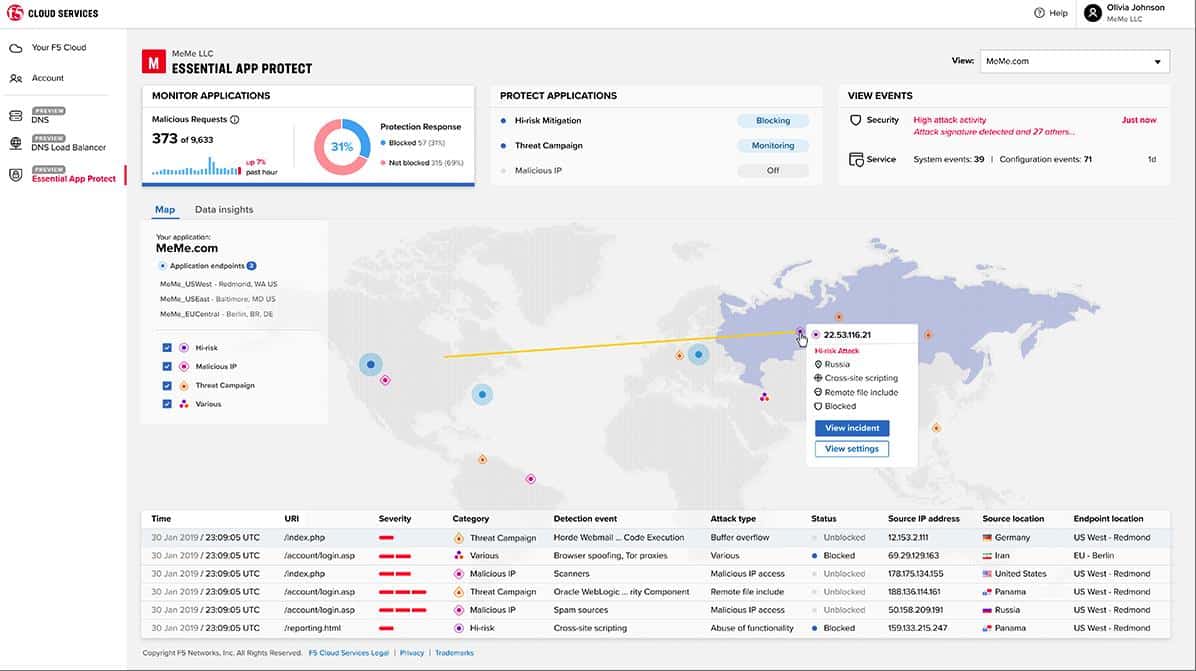
7. F5 Essential App Protect
F5 is a long-established cybersecurity service provider and it owns NGINX, Inc, the producer of the widely-used Nginx web server system. F5 and NGINX expertise contributed to the joint production of the F5 Essential App Protect cloud-based web application server.
Key Features:
- NGINX Integration: Seamlessly integrates with the widely-used NGINX web server for enhanced protection.
- Simplified Setup: Designed for ease of deployment, particularly beneficial for organizations with limited technical resources.
- Diverse Deployment Options: Available as a cloud service, physical appliance, or software plugin for flexibility.
Why do we recommend it?
F5, like Fortinet, is renowned for its network appliance firewalls. The Essential App Protect is a cloud delivery of the software that is usually offered on those appliances, which makes it a more affordable service.
The technology behind F5 Essential App Protect came from an adaptation of the F5 Application Security Manager – a pre-existing WAF that was delivered on a network appliance. The appliance version of the firewall still exists and it is now called the BIG-IP Advanced WAF. The NGINX version is an add-on for the Nginx Plus web server system and so is delivered as a software download.
F5 Essential App Protect has been designed with non-technical users in mind, so it is easy to set up and manage through a dashboard that is accessed through any browser.
Who is it recommended for?
While larger companies might be attracted by the physical appliance version of the F5 firewall, which is called BIG-IP. This cloud service will appeal to small businesses. The package is easy to set up and manage and can be run by an administrator who is not a fully qualified cybersecurity expert.
Pros:
- Threat Intelligence Inclusion: Incorporates up-to-date threat data from F5 Labs for proactive security.
- API and Web Services Protection: Offers comprehensive safeguarding for both traditional web pages and modern APIs.
- NGINX Plus Compatibility: Ideal for businesses already utilizing NGINX Plus infrastructure.
Cons:
- Service Transition: Currently undergoing changes, which might affect stability or feature availability temporarily.
Features of the Essential App Protect WAF include a threat intelligence feed from F5 Labs and full protection for APIs, pages, and web services. F5 offers a 15-day free trial of Essential App Protect which has processing volume limits placed on it.
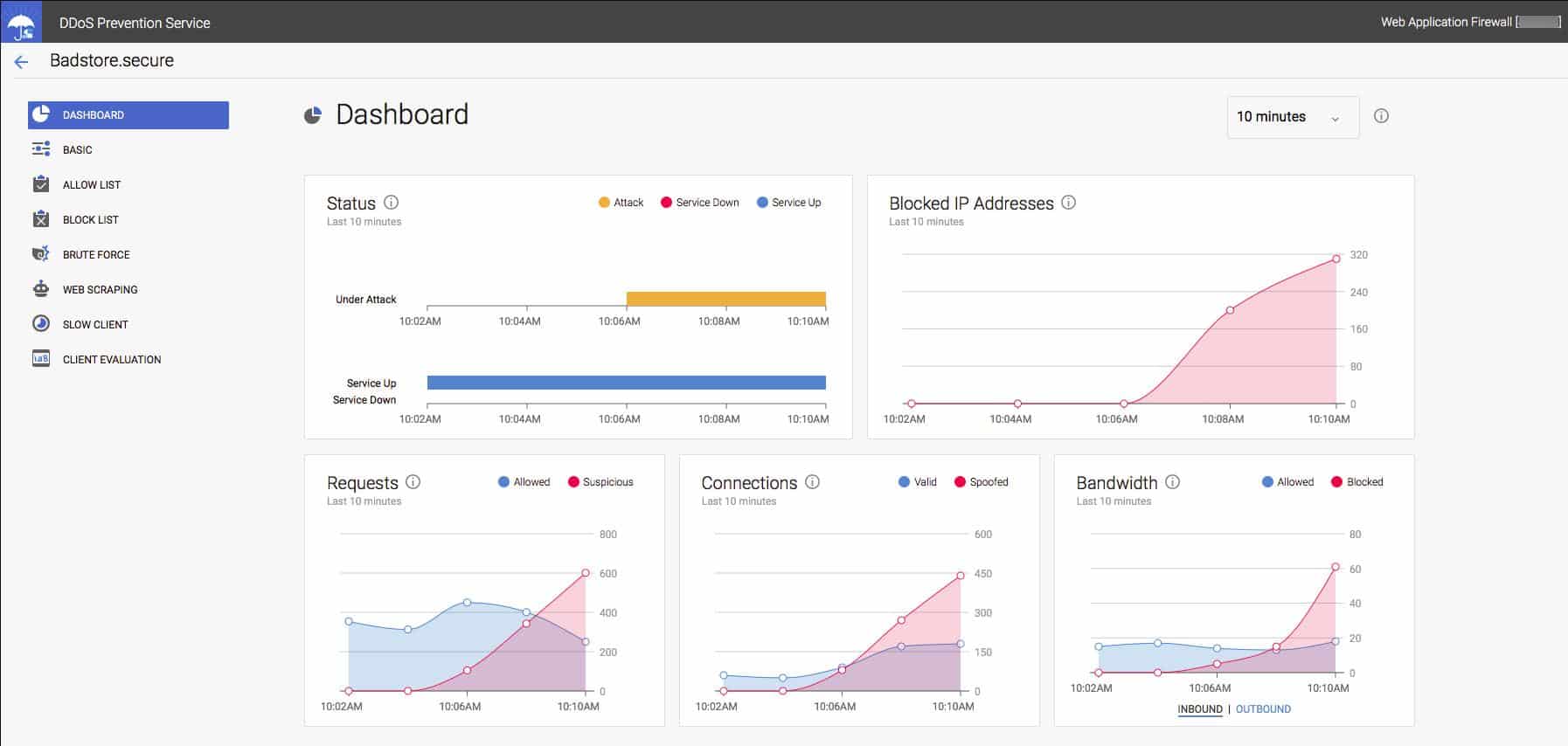
8. Cloudflare WAF
Cloudflare has become very successful at protecting web hosts from DDoS attacks and they extend their protection with a web application firewall. This is an online service that is very widely used. Their servers manage 2.9 million requests every second on behalf of their large customer base.
Key Features:
- No-Cost Entry Plan: Offers a free version suitable for small businesses or trial use.
- Integrated CDN Services: Enhances website performance with Cloudflare’s renowned content delivery network.
- Automated Failover Mechanisms: Provides reliability through automatic failover in case of server issues.
Why do we recommend it?
The Cloudflare WAF is an offer that is hard to beat because it has a free version and it can be combined with other free services, such as a content delivery network and DDoS protection. Businesses that need high throughput would need to look at the paid versions.
The benefit of subscribing to a widely-used cloud WAF like Cloudflare is that the company can apply economies of scale to its threat research. An attack attempt on one customer instantly ripples through to a blacklist entry for all web servers protected by Cloudflare. If you have a cloud-based server central to your enterprise or as a content delivery system included in your web presentation, then Cloudflare can cover that as well. Integrating full Cloudflare DDoS protection alongside your WAF subscription is a very simple task.
Who is it recommended for?
The free Cloudflare service is very tempting for small businesses and the quality of this service is hard to beat.
Pros:
- Shared Threat Intelligence: Benefits from Cloudflare’s vast network of clients for rapid threat identification and response.
- Comprehensive DDoS Protection: Equipped to handle large-scale distributed denial-of-service attacks efficiently.
- Performance Optimization: Utilizes caching and other technologies to improve website loading times.
Cons:
- Complex Service Options: The array of available options and plans can be overwhelming and confusing for new users.
9. Akamai Kona Site Defender
Akamai is a world leader in DDoS mitigation and it integrates full DDoS protection with its web application firewall in a cloud service called Site Defender. A great benefit of combining both of these services in one security product is that you won’t need to have your traffic routed through two different companies in order to get genuine requests arriving at your web server.
Key Features:
- DDoS protection
- Threat intelligence
- Combined services
Why do we recommend it?
Akamai Kona Site Defender is worthy of consideration. It competes well with all of the excellent options on this list but it would be nice if the company could give potential customers a free trial.
As one of the leaders in online security products, Akamai often is the first to discover new exploits. As a customer of Site Defender, you benefit from this “ahead of the curve” information immediately with tighter and smarter blocks on hacker traffic.
Who is it recommended for?
Akamai offers a reliable service that offers DDoS protection, malware detection, and attack blocking. This is a service that competes well with Cloudflare for big business customers but isn’t the best choice for small enterprises.
Pros:
- Combines malware filtering with DDoS protection
- Attack analysis
- Hosted system
Cons:
- No self-hosted option
What Attacks do WAFs protect against?
A web application firewall, or WAF, needs to protect your web server and its content from the following categories of attacks:
- Cross-Site Scripting (XSS) – malicious HTML code inserted into a web page input field by a hacker
- Hidden field manipulation – hackers rewrite the source code of a web page to alter values held in hidden fields and then post the amended code back to the server
- Cookie poisoning – altering parameter values held in cookies to corrupt data passed between web pages
- Web scraping – automated data extraction from web pages
- Layer 7 DoS attacks – overwhelming a web server by recursive application activity
- Parameter tampering – altering values in the parameters to a web page call
- Buffer overflow – user input that overwrites the code in memory
- Backdoor or Debug options – developer feedback reports for web page testing that can be used by hackers for access to the processor
- Stealth commanding – an attack on the operating system of a web server
- Forced browsing – the hacker gains access to backup or temporary folders on the webserver
- Third-party misconfigurations – manipulation of content inserts provided by other companies
- Site vulnerabilities / SQL injections – queries entered in user authentication fields
Although a WAF works as a front end to a website, a number of essential access control functions that your web host needs are not provided by this technology. WAFs focus on HTTP code and the request procedures for other internet applications, such as FTP. In these cases, the secure versions of these application protocols, HTTPS and SFTP, are also covered.
Here’s how WAFs Work
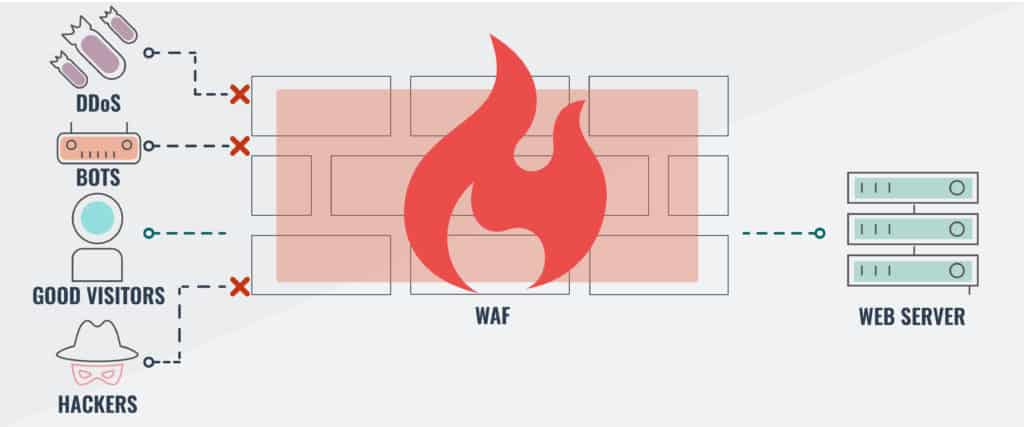
WAFs look for irregularities contained in incoming requests and block malformed or devious constructs. A WAF is not responsible for load balancing between a cluster of servers. Although some types of DDoS attacks use HTTP, most use lower-level methods. So, a WAF will protect you against HTTP and FTP application-level/layer 7 DDoS attacks, but not those carried out by other strategies.
WAF configurations
A WAF needs to be a part of your web hosting protection strategy. It can be implemented as a hardware solution or as software.
Proponents of software WAFs argue that you already have sufficient hardware available, you just need to extend the capabilities of your existing equipment in order to get a Web application firewall. However, the ideal location for the WAF is in front of your servers, and most software solutions are installed directly on the Web server.
WAF Placement
The best place to put your WAF is on the router that acts as a gateway between your network (and thus, your server) and the internet. This strategy implies that the best option would be a router that has an integrated WAF. This would be a standalone piece of equipment and it would prevent damaging traffic or hacker exploration reaching your precious server.
Software vs Hardware WAF Considerations
So, which should you choose to control costs? Software WAFs are cheaper than hardware solutions. However, don’t think that there are no hardware costs to installing WAF software on your servers. You probably planned your server hardware capacity and so adding on an extra function will take up disk space, use memory and tie up CPU processors. You may have to extend your server capacity in order to host a WAF, so there are hardware costs involved.
Onsite skill sets are also a consideration. It is probable that your system administration staff are all familiar with your server’s operating system, but would be clumsy around a new device’s firmware. Users of hardware WAF tend to treat them as black boxes and intervene in their operations a lot less than they do with software WAFs — which could be a good thing.
Both hardware and software WAFS come with patches and update support. However, updating the software versions usually requires your consent and management for each install, whereas hardware WAFs tend to get updated directly by the provider, leaving you without time-consuming patch management issues.
Generally speaking, both hardware WAF and software WAFs perform the same tasks. Hardware WAFs keep extra load off your servers and they can continue to work even when you want to take one of your servers down. A hardware WAF is more reliable and can be left alone to do its job. Although hardware WAFs are probably better options than software WAFs, administrators tend to prefer the accessibility and customizability of software WAFs.
Web application firewall functions
Not only should you scan all user activity when a web page is live, but you need to check the code of your web pages, including off-the-shelf plug-ins provided by external companies. Coding errors and validation oversites are known as zero-day vulnerabilities. They are non-standard paths that could allow a hacker access to your web server. If hackers discover these security flaws before you or the provider of inserted code sees the problem, you will be subjected to a zero-day attack that might not be covered by your WAF.
The value of a WAF lies in the rules that it applies to user responses. These rule settings execute validation procedures that protect your web server from malicious activity by laying out activities to spot and dictating actions to take when an exploit is discovered. Rules will be written to specifically block well-known attack strategies. However, extra, more flexible rules in the WAF’s routines are useful for identifying zero-day threats.
See also: Best free port scanners
Related: Best intrusion detection security tools
WAF vs NextGen Firewalls vs Intrusion Prevention Systems (IPS)
Hackers are getting increasingly more sophisticated and, thankfully, so are cyber defense systems. However, you might be confused about the different categories of network protection that are now available.
The distinction between an intrusion prevention system (IPS) and any type of firewall is very easy to spot. The firewall defends the boundary of a system, whereas the IPS monitors traffic within the network. An IPS is an advanced form of an Intrusion Detection System (IDS). While an IDS spots suspicious activity, an IPS includes procedures to shut it down.
Next-generation Firewalls usually include many of the techniques used by IPSs. That is, they record all activity rather than just examining each packet as it passes through the gateway. However, NGFWs sit at the gateway between the network and the outside world, while IPSs focus on traffic within the network. A WAF specifically examines Web traffic, carried through the HTTPS and SSL protocols. In short, the NGFW looks at traffic entering the network, while the WAF guards the webserver.
Hardware-based vs Cloud-based WAFs: Pros and Cons
The choice of your own piece of equipment or a cloud infrastructure solution can often come down to your own preferences for each configuration. For example, some people are uncomfortable outsourcing elements of their network and the security functions of a web host are particularly sensitive topics.
Cloud-based WAFs Cons
The WAF stands in front of all of your other devices and so it has to be the target of your URL. That means that you no longer have direct control over your traffic because all DNS records will direct website visitors to the cloud infrastructure first.
Where cloud WAFs are offered by companies that include other front-end security services, combining these into one package makes sense. For example, if your chosen WAF provider doesn’t have a DDoS protection service, you will need to forward your traffic to a second cloud service in order to get fully covered from all threats. Taking out a WAF cloud service can lock you into one online security company for all of your online protection and limit your options.
WAFs examine the contents of packets, so they have to strip off all encryption protection first before they can perform their main task. This means that you have to hand over your SSL certificate to the cloud WAF provider, effectively surrendering all of the data security functions that protect your web host, your content, and the safety of your customers.
You need to have a lot of faith in your cloud WAF provider in order to be prepared to let this third party stand in between you and your customers.
Cloud-based WAFs Pros
On the other hand, the reputation and expertise of the top cloud WAF providers means that you don’t need to be worried about being let down. The companies on our list specialize in networking and security services. Their accumulated expertise is a lot greater than you could get for your own company in-house. There is probably more risk to your website’s availability and security if you try to cover all of the complicated tasks that these issues involve.
Cloud-based solutions can be paid for on a monthly basis, spreading the cost of your web application security. In some cases, you only get charged for your web throughput, so you can defer paying for your protection until the end of the month when the service level has been calculated and invoiced.
If you already outsource parts of your operation, you have already come to terms with the cloud-based method of operation and so it would not be too difficult to outsource your WAF as well. You may need to switch from existing providers if combining other services, such as DDoS protection and load balancing, with your new WAF makes better logistical and economic sense.
Hardware-based WAFs Cons
When considering the cost of a hardware WAF, you need to add on the expenses of installing, housing, protecting, and maintaining it. Online WAFs get updated automatically, so they are always up-to-the-minute and ready to tackle the latest emerging threat. Getting that level of preparedness on your own WAF device can be expensive.
Most hardware WAF vendors offer an update service. The fixes to new threats are sent to your WAF device over the internet automatically and it will renew its firmware without your intervention. In the case of some new threats, other equipment and software on your network may need updating, and the support service of your WAF provider will give you those, too.
This process is called “virtual patching” and it is the WAF version of classic firewall database updates. However, although all of the hardware suppliers in our list provide virtual patching, not all of them include that service for free. Where the update service is included, it is usually only free for the first year. After that, you must pay extra for support of your in-house WAF.
The upfront cost of buying a hardware WAF can be an inconvenient expense when struggling to get your new web company operational. If you forgo this application security solution initially, you may get lulled into the belief that it is an unnecessary extra even when you get to the point where you have cash to spare. This is a dangerous scenario, because you will only realize that you need WAF protection once you have been hit by an attack. By then, your website will be blocked by search engines for containing malicious code and you will be sent out of business.
Hardware-based WAFs Pros
If you are running your own web server, you probably already know a lot about networking and internet systems. You may need a load balancer once you put on extra servers to deal with demand. If that is the case, you could buy a combined web cache, load balancer, and WAF combined and get all of your front-end requirements dealt with by one device.
Having your own WAF means you don’t have to surrender your web address to a third party. If at some point you do need extensive DDoS protection, then your URL will have to go to the DDoS mitigation provider. However, in this case, you won’t need to limit your choice of DDoS protection to that provided by your cloud WAF company. You won’t be committed to directing your URL to provide your WAF.
Choosing a Web Application Firewall Solution
Whether you prefer to have your own WAF on your network, or you think it would be better to go for a cloud-based WAF solution, this review has given you five options to consider. Selecting new equipment, software, and services for your company can be very time-consuming. In this guide, we have taken care of that first phase for you.
Your next task is to narrow down your options. The added extras that each of these WAF vendors offer will direct you towards that choice. The capacity of each service is also an important consideration and you should factor in scalability so that your future expansion plans are accounted for.
Make the decision on whether to go for a dedicated hardware or cloud-based WAF and then check out each of the five listed in that category. Overlooking the protection that a dedicated web application firewall offers your organization would be a mistake. Don’t wait until it is too late and your site has already been attacked. Get a WAF in place now to keep your website online.
Web Application Firewall FAQs
What is the difference between a normal firewall and a WAF?
Network and endpoint firewalls operate at a lower stack level than web application firewalls. As the name suggests, WAFs examine attributes at the Application Layer (Layer 7), whereas typical firewalls work at the Network Layer (Layer 3). So, each looks at different characteristics of incoming traffic. Another major difference between these two services is that a typical firewall integrates into the architecture of a network gateway (or computer network interface) but WAFs have a reverse proxy configuration.
What are WAF rules?
WAF rules are a list of things that the firewall needs to look out for. They are specific characteristics in web traffic and the specific places to look for them in the data stream. Rules are also called “policies.” They include the action to take on detection of an attack attempt, which usually just involves not passing that traffic on to the server being protected.
What are the 3 types of firewalls?
The three types of firewalls are packet filters, stateful packet inspection, and proxy server firewalls.
- Packet filters look at the technical features of all packets traveling in and out of a network and drop those that don’t match a given pattern or do match a list of blacklisted characteristics.
- Stateful packet inspection (SPI), also, known as dynamic packet filtering, also operates at the Network Layer, but it records individual packet characteristics so it can spot attacks that are split across several packets.
- A WAF is a proxy server firewall because all traffic is directed through the WAF on its way to the server. It operates at the Application Layer and substitutes the protected server’s IP address with its own.














AppTrana a cloud based WAF from Indusface is missing from the list. it is ideal for SMB and provides enterprise grade security for small business including a- scanning the application for vulnerabilities b- patching them instantly c- providing managed custom rules for new threats d- central view co-relating your application risk with protection status e- 24×7 support and managed service. All of this starting @ $99 per month and a 14 day free trail.
Yes, I too suggest AppTrana.
Galo – try ModSecurity WAF, its open source.
Hi. Small business dont have $5000 or something. I can see only Incapsula gives a monthly basis for $59 per month. Amazon services is only for amazon. So, I cant find any good alternative for very small business in this post. Maybe WAF is expensive in all cases 🙁